Chapter 15 Linux Operating Systems Understanding Operating Systems







- Slides: 37

Chapter 15 Linux Operating Systems Understanding Operating Systems, 8 e © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 1

Learning Objectives After completing this chapter, you should be able to describe: • How the Linux operating system is designed • How the Linux community keeps the software up-to-date • The roles of the Memory, Device, File, Processor, and Network Managers • How the strengths and weaknesses of Linux compare • The role of software creator Linus Torvalds © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 2

Introduction • Linux • Originally based on a version of UNIX • Powerful • Inexpensive or free to use • Portable • Versions for cell phones, supercomputers, and computing systems in between • Open source • Source code freely available to anyone for improvement • Under constant development • Contributors around the world: not paid for their work © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 3

Brief History (1 of 3) • Developed by Linus Torvalds (1991) • Original purpose • Maximize Intel 80386 microprocessor’s limited capabilities • Roots - MINIX: miniature UNIX with more functionality • First version meant for small microcomputer • Expensive commercial computer features - Flexibility and functionality • Brought UNIX features to small computer © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 4

Brief History (2 of 3) • User interface • First Linux operating systems: command-driven interface - Sometimes cryptic commands • Recent years - Graphical user interfaces (GUI) • Written and distributed under the GNU General Public License • Fedora Project responsible for the open-source development of the Linux kernel • Common popular distributions: Fedora, Ubuntu, Cent OS, etc. • The foundation of Android operating system (most popular mobile OS) © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 5

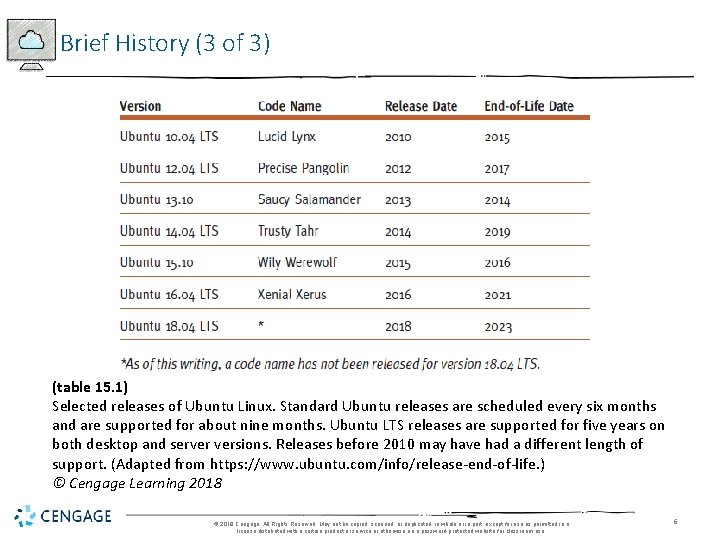
Brief History (3 of 3) (table 15. 1) Selected releases of Ubuntu Linux. Standard Ubuntu releases are scheduled every six months and are supported for about nine months. Ubuntu LTS releases are supported for five years on both desktop and server versions. Releases before 2010 may have had a different length of support. (Adapted from https: //www. ubuntu. com/info/release-end-of-life. ) © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 6

Design Goals (1 of 3) • Three goals • Modularity • Simplicity • Portability • Numerous standard utilities • Eliminate need to write special code • Used in combination for specific tasks • Numerous functions • IEEE POSIX (Portable Operating System Interface) specifications conformity • Programs’ portability © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 7

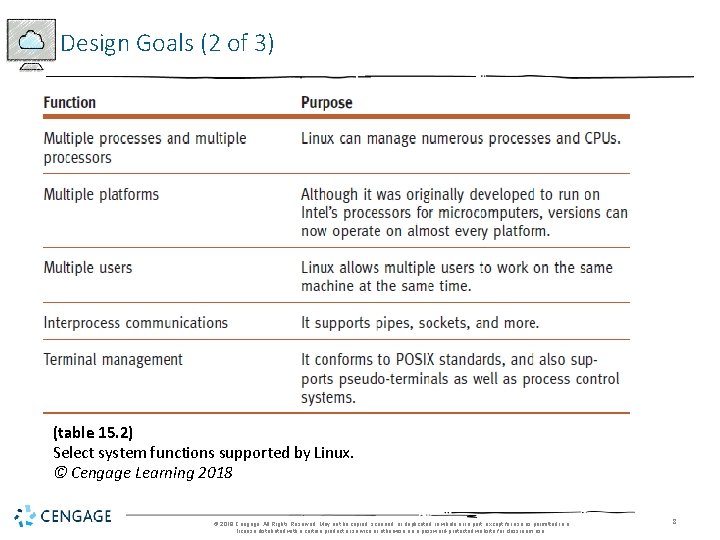
Design Goals (2 of 3) (table 15. 2) Select system functions supported by Linux. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 8

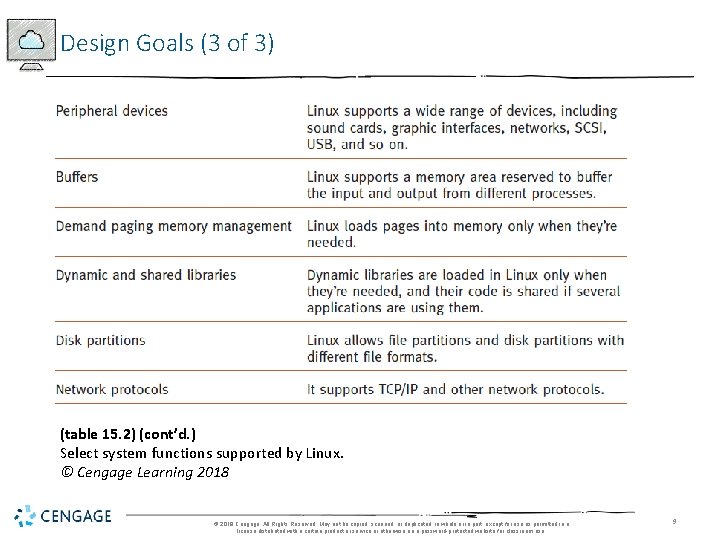
Design Goals (3 of 3) (table 15. 2) (cont’d. ) Select system functions supported by Linux. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 9

Memory Management (1 of 5) • Memory space allocation • Kernel: 1 GB high order memory • Executing processes: 3 GB memory • Process execution • Fixed-size segment • System calls change segment size • Memory protection • Based on information type stored in address space region for process © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 10

Memory Management (2 of 5) • Page loading • Least recently used algorithm (LRU) • Maintains a dynamically managed memory area and page cache (new and old pages inserted and deleted) • System page tables • Track free and busy pages • Added flexibility with swap devices • Virtual memory • Managed using multiple-level table hierarchy - 64 - and 32 -bit architectures © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 11

Processor Management • Uses same parent-child process management design found in UNIX • Supports “personality” concept • Allows processes from other operating systems to be executed © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 12

Device Management • Linux is device independent • Improves portability • Device drivers • Supervise data transmission - Between main memory and peripheral unit • Devices are assigned • Name • Descriptors - Further identify each device - Stored in device directory © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 13

Device Drivers (1 of 3) • Support for standard classes introduced by UNIX • Allow new device classes supporting new technology • Device classes are not rigid • Creating large, complex, and multiple function drivers is discouraged because: - Users share code: wider demand for simple drivers - Modular code supports system scalability and extendibility goals • Encouraged: drivers maximizing system’s effective device usage • Notable feature • Accept new device drivers on the fly - System up and running - No reboot necessary © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 14

Device Classes (1 of 5) • Three standard classes • Character devices • Block devices • Network devices © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 15

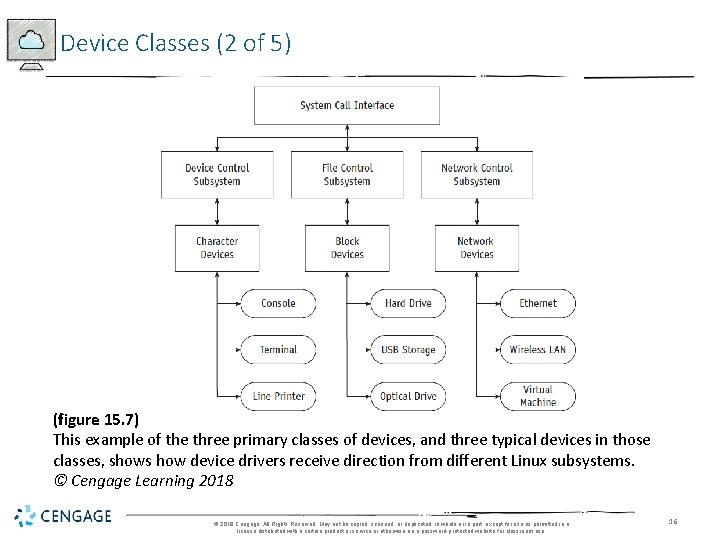
Device Classes (2 of 5) (figure 15. 7) This example of the three primary classes of devices, and three typical devices in those classes, shows how device drivers receive direction from different Linux subsystems. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 16

Device Classes (3 of 5) • Character devices • Accessed as a stream of bytes - Communications port, monitor, or other byte-stream-fed device • Implement open, release, read, and write system calls • Accessed by file system nodes - Look like ordinary data area • Drivers treated as ordinary files - Exception: drivers are data channels accessed sequentially © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 17

Device Classes (4 of 5) • Block devices • Host a file system (e. g. , hard disk) • Accessed by file system nodes in /dev directory - Transfer in blocks of data • Similarity to char driver - Appear as ordinary files • Dissimilarity to char driver - Access file system in connection with device (not possible with char device) © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 18

Device Classes (5 of 5) • Network devices • Function - Send and receive information packets - Directed by network subsystem • Network device functions - Relate to packet transmission • System device handled by device driver • Under Linux subsystem’s direction © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 19

File Management • Very similar to UNIX • Easy transition for programmers and administrators who are familiar with one operating system to move to the other • Files organized in directories • Connected in treelike structure © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 20

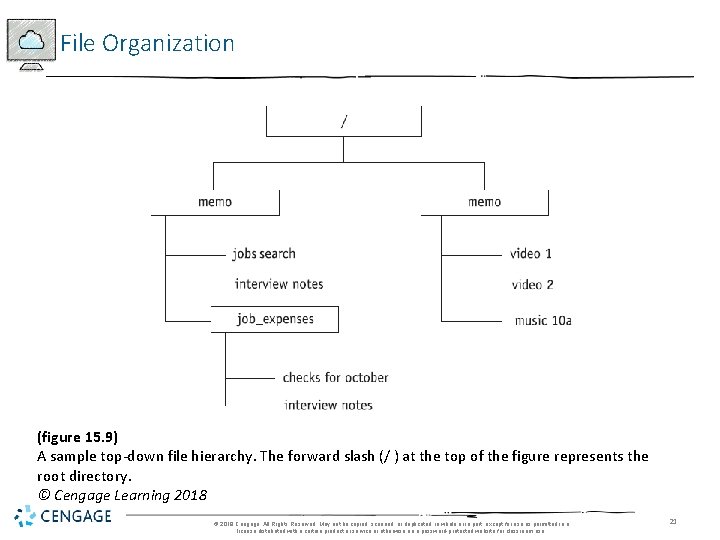
File Organization (figure 15. 9) A sample top-down file hierarchy. The forward slash (/ ) at the top of the figure represents the root directory. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 21

Filename Conventions (1 of 3) • Case sensitive • Recognizes uppercase and lowercase letters • Up to 255 characters long • Contain alphabetic characters, underscores, and numbers • File suffixes: optional • Can include space • Complications if running command-line programs • File hierarchy • First slash indicates an absolute path name © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 22

Filename Conventions (2 of 3) • Path name rules 1. Path name starting with slash: begins at root directory 2. Path name - One name or list of names separated by slashes - Last name on list: name of file requested 3. Two periods (. . ) in path name - Move upward in hierarchy: closer to root - Only way to go up the hierarchy © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 23

Filename Conventions (3 of 3) • Virtual File System (VFS) • Kernel - Allows processes to access files in a consistent manner - Maintains interface between file-related system calls and file management code • Virtual file system layer - Receives process-initiated system call to files - Performs file operations independent of file system format - Redirects request to module managing the file © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 24

Updates and New Versions (1 of 2) • Linux operating systems: patched between version releases • Downloaded on request or • System setup checks for available updates • Patch management • Replaces or changes parts of the operating system that need to be enhanced or replaced © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 25

Updates and New Versions (2 of 2) • Reasons for operating system patches • Security precautions: constantly changing system threats • System compliance: government regulations regarding privacy and financial accountability • Peak efficiency • System manager must: • Maintain vigilance: security vulnerabilities • Assess patch’s criticality - If important, apply immediately © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 26

User Interfaces • Early Linux versions • Required typed commands - Thorough knowledge of valid commands required • Current versions • Include powerful and intuitive menu-driven interfaces • Can still use Terminal mode - Type commands similar to those used for UNIX • Several graphical user interfaces available • Many Linux versions • Equipped with Windows-compatible word processors, spreadsheet, and presentation applications © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 27

System Monitor • System Monitor window • Moment-by-moment system status - Immediate history: CPUs, memory, and network usage • Other information - Supported file systems - Currently running processes information © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 28

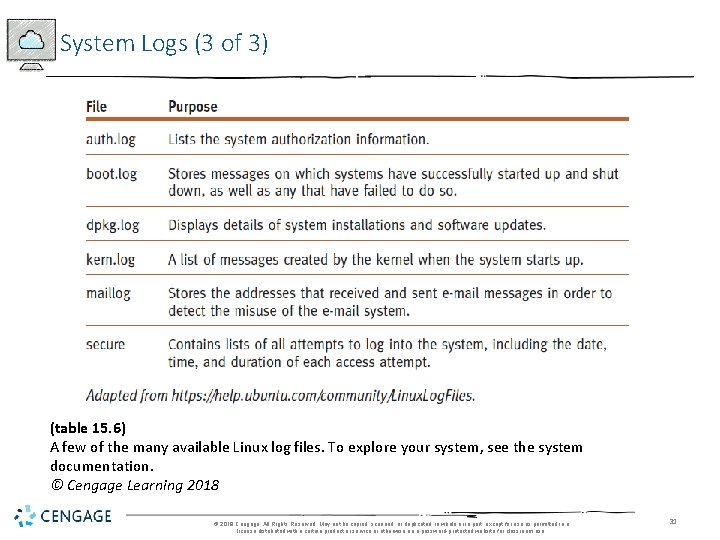
System Logs (1 of 3) • Provide detailed description of activity on system • Invaluable to administrators • Tracking system malfunction • Firewall failure • Disabled device • Found in /var/log directory • Seen using a log viewer © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 29

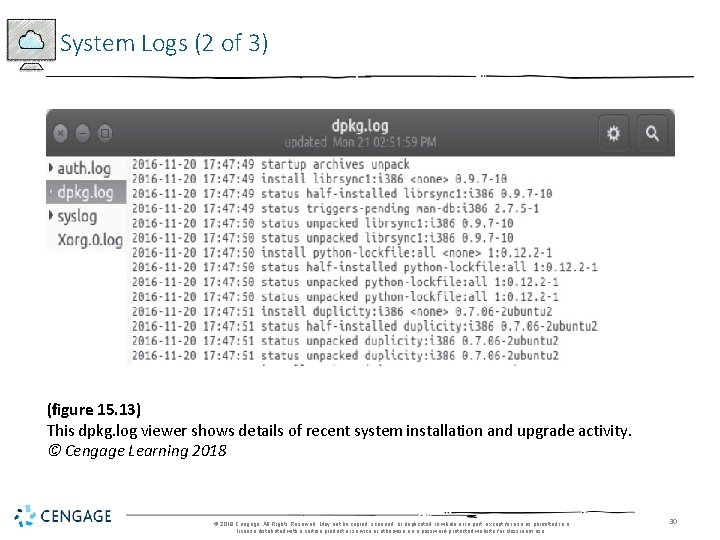
System Logs (2 of 3) (figure 15. 13) This dpkg. log viewer shows details of recent system installation and upgrade activity. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 30

System Logs (3 of 3) (table 15. 6) A few of the many available Linux log files. To explore your system, see the system documentation. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 31

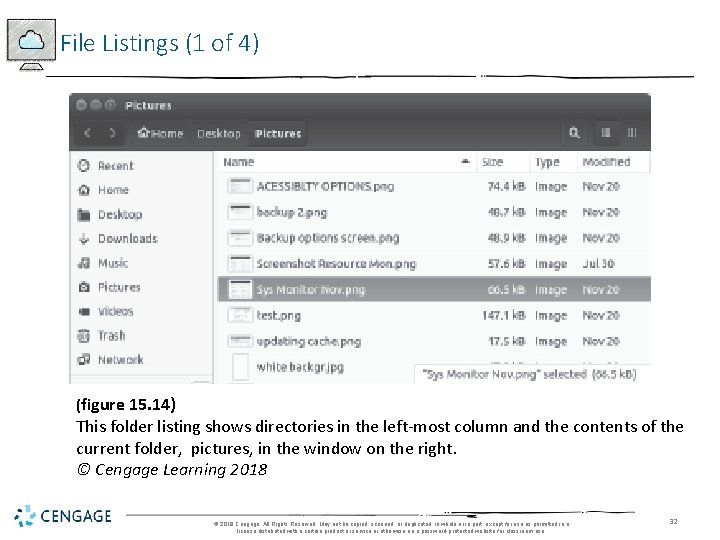
File Listings (1 of 4) (figure 15. 14) This folder listing shows directories in the left-most column and the contents of the current folder, pictures, in the window on the right. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 32

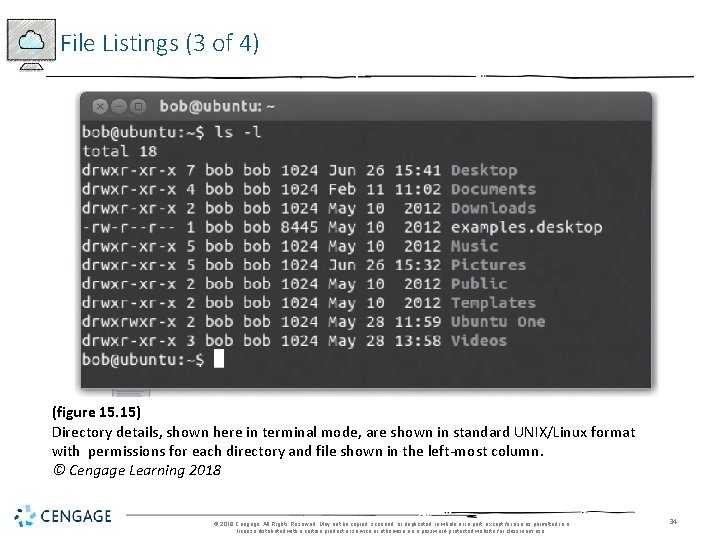
File Listings (2 of 4) • Explore directory’s or file’s contents • Double click its icon • Establish the directory’s or file’s access control settings • Right click on item’s icon • Terminal window • Display directory details: type command ls -l • Network administrators • Full control: manage access to files and directories © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 33

File Listings (3 of 4) (figure 15. 15) Directory details, shown here in terminal mode, are shown in standard UNIX/Linux format with permissions for each directory and file shown in the left-most column. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 34

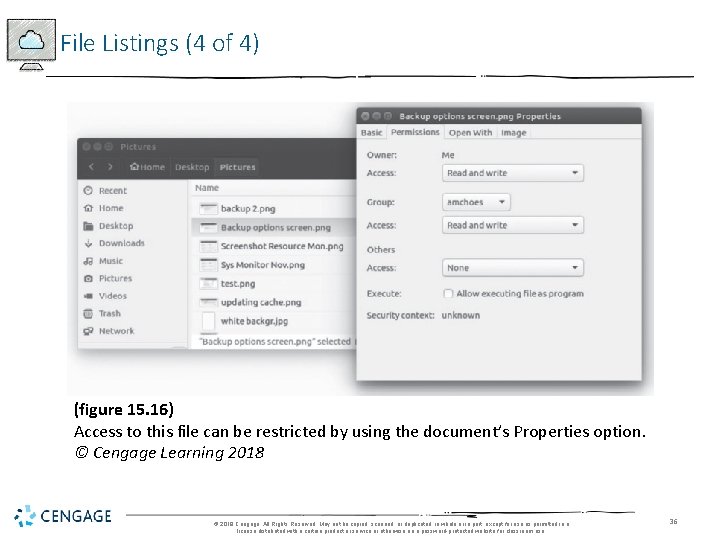
Setting Permissions • Three levels of access • Owner • Group • Others • Access level settings: under properties option • Access types • Create and delete files, list files only, access files, and none 35 Understanding Operating Systems, 7 e 35

File Listings (4 of 4) (figure 15. 16) Access to this file can be restricted by using the document’s Properties option. © Cengage Learning 2018 © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 36

Conclusion • Originally designed to gain more power from a 1990 s computer • Evolved into powerful, flexible operating system: runs supercomputers, cell phones, and many other devices • Unparalleled popularity among programmers • Contribute standard code set enhancements • Supports broad range of applications • Available for minimal cost and easy to install • Growing acceptance among non-programmers • Large organizations • Commercial Linux products available • Viable marketplace player • Popularity expected to grow for many years • Android operating system foundation © 2018 Cengage. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. 37