SSECMM Security Metrics George Jelen Chairman Profiles Assurance









































- Slides: 67

SSE-CMM Security Metrics George Jelen, Chairman Profiles, Assurance and Metrics Committee International Systems Security Engineering Association

Briefing Outline • A brief review of the history of the • • SSE-CMM project A look at the SSE-CMM appraisal as a metric Description of three specific project efforts – 1999 conference paper – Ongoing document drafting effort – IATAC current research effort 2

Brief History of the SSE-CMM Project

Why was the SSE-CMM developed? • Objective: – advance security engineering as a defined, mature, and measurable discipline • Project Goal: – Develop a mechanism to enable: • selection of appropriately qualified security engineering providers • focused investments in security engineering best practices • capability-based assurance 4

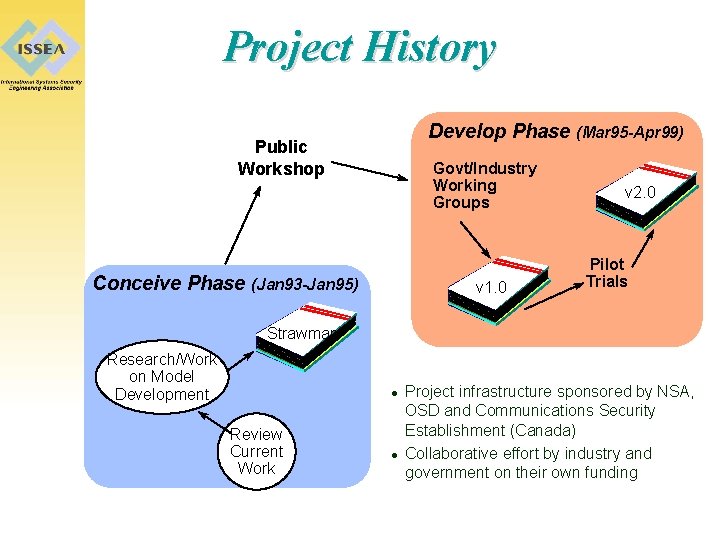
Project History Develop Phase (Mar 95 -Apr 99) Public Workshop Govt/Industry Working Groups Conceive Phase (Jan 93 -Jan 95) v 1. 0 v 2. 0 Pilot Trials Strawman Research/Work on Model Development l Review Current Work l Project infrastructure sponsored by NSA, OSD and Communications Security Establishment (Canada) Collaborative effort by industry and government on their own funding

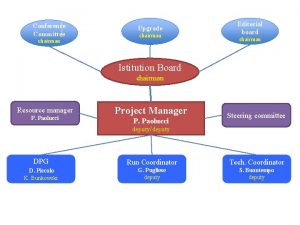
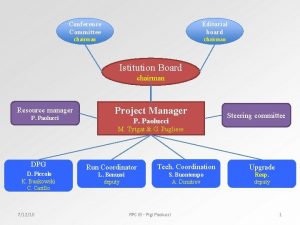
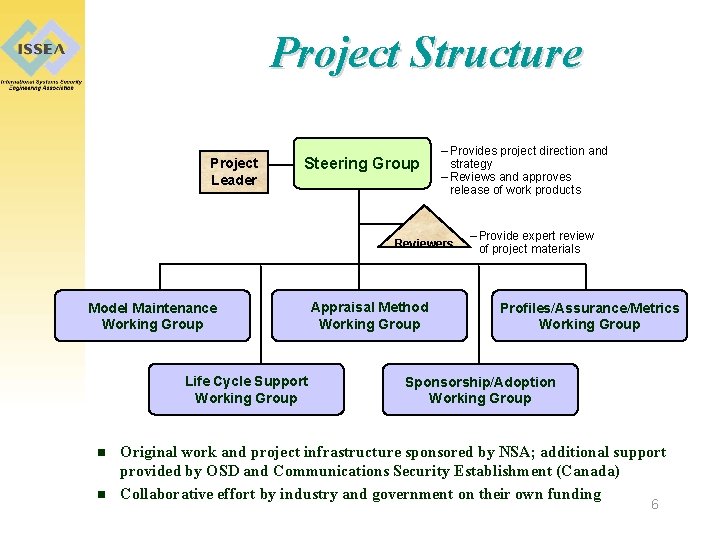
Project Structure Project Leader Steering Group – Provides project direction and strategy – Reviews and approves release of work products Reviewers Model Maintenance Working Group Life Cycle Support Working Group n n Appraisal Method Working Group – Provide expert review of project materials Profiles/Assurance/Metrics Working Group Sponsorship/Adoption Working Group Original work and project infrastructure sponsored by NSA; additional support provided by OSD and Communications Security Establishment (Canada) Collaborative effort by industry and government on their own funding 6

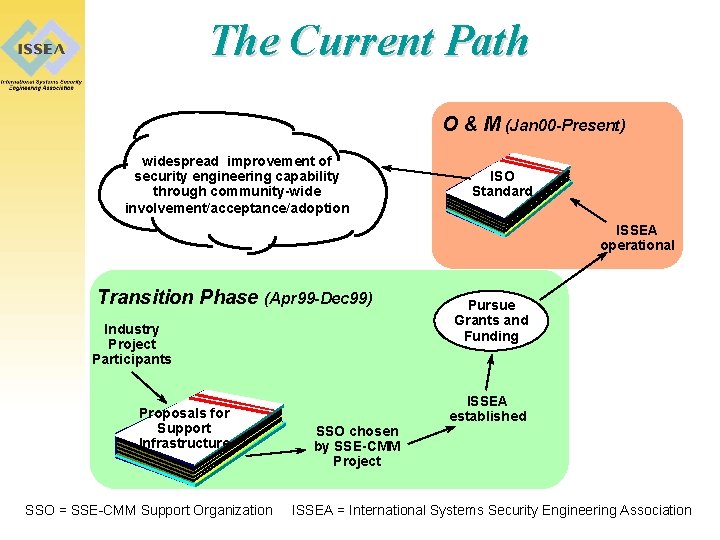
The Current Path O & M (Jan 00 -Present) widespread improvement of security engineering capability through community-wide involvement/acceptance/adoption ISO Standard ISSEA operational Transition Phase (Apr 99 -Dec 99) Industry Project Participants Proposals for Support Infrastructure SSO = SSE-CMM Support Organization SSO chosen by SSE-CMM Project Pursue Grants and Funding ISSEA established ISSEA = International Systems Security Engineering Association

ISSEA Objectives • Establish systems security engineering as a • • • defined and measurable discipline Accomplish ISO standard to gain worldwide acceptance of the SSE-CMM Provide for maintenance of the SSE-CMM Promote the adoption of the SSE-CMM 8

What is the ISSEA? • Not for profit professional organization • Oversees SSO in furthering development and • use of the SSE-CMM Receives advice and guidance from Advisory Council and Board of Sustaining Members 9

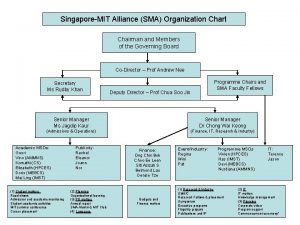
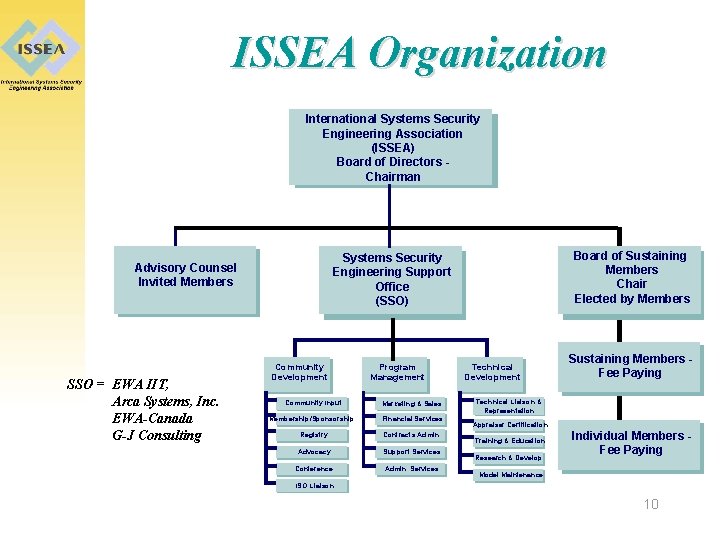
ISSEA Organization International Systems Security Engineering Association (ISSEA) Board of Directors Chairman SSO = EWA IIT, Arca Systems, Inc. EWA-Canada G-J Consulting Board of Sustaining Members Chair Elected by Members Systems Security Engineering Support Office (SSO) Advisory Counsel Invited Members Community Development Program Management Community Input Marketing & Sales Membership/Sponsorship Financial Services Registry Contracts Admin. Advocacy Support Services Conference Admin. Services Technical Development Sustaining Members Fee Paying Technical Liaison & Representation Appraiser Certification Training & Education Research & Develop. Individual Members Fee Paying Model Maintenance ISO Liaison 10

The SSE-CMM Appraisal as a Metric

What is the SSE-CMM? • Describes those characteristics of a security • • engineering process essential to ensure good security engineering Does not prescribe a particular process or sequence Captures industry’s best practices 12

How does the SSE-CMM define best practices? • Domain Aspect – process areas – base practices • Capability Aspect – implementation of process areas – institutionalization of process areas 13

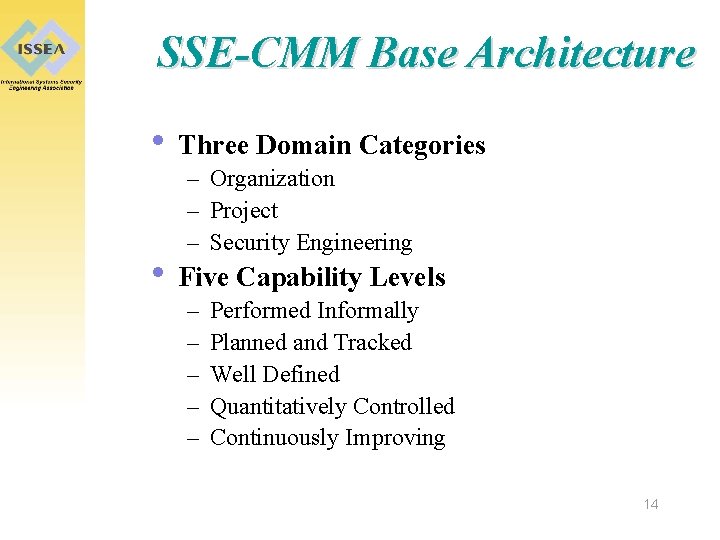
SSE-CMM Base Architecture • Three Domain Categories – Organization – Project – Security Engineering • Five Capability Levels – – – Performed Informally Planned and Tracked Well Defined Quantitatively Controlled Continuously Improving 14

SSE-CMM Organization Process Areas • • • Define Organization’s Security Engineering Process Improve Organization’s Security Engineering Process Manage Security Product Line Evolution Manage Security Engineering Support Environment Provide Ongoing Skills and Knowledge Coordinate with Suppliers 15

SSE-CMM Project Process Areas • Ensure Quality • Manage Configurations • Manage Program Risk • Monitor and Control Technical Effort • Plan Technical Effort 16

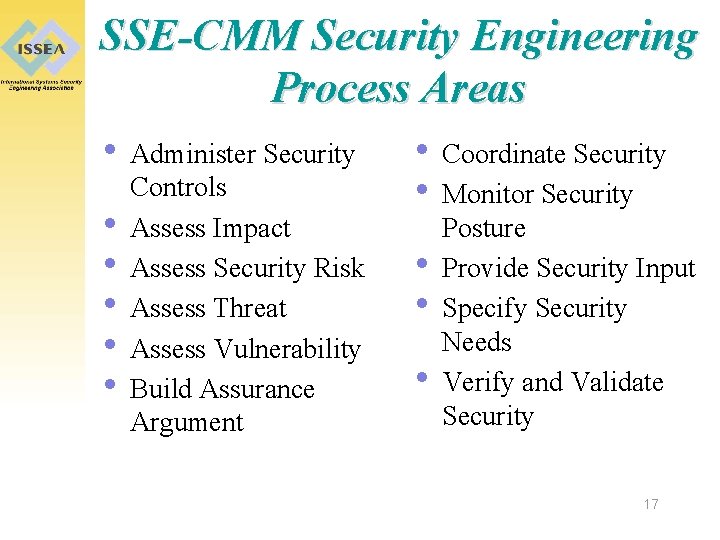
SSE-CMM Security Engineering Process Areas • Administer Security • Coordinate Security Controls • Monitor Security • Assess Impact Posture • Assess Security Risk • Provide Security Input • Assess Threat • Specify Security Needs • Assess Vulnerability • Verify and Validate • Build Assurance Argument Security 17

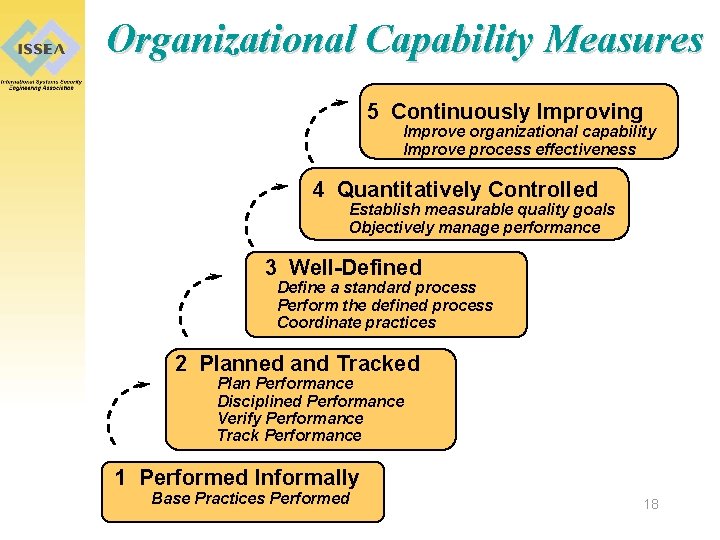
Organizational Capability Measures 5 Continuously Improving Improve organizational capability Improve process effectiveness 4 Quantitatively Controlled Establish measurable quality goals Objectively manage performance 3 Well-Defined Define a standard process Perform the defined process Coordinate practices 2 Planned and Tracked Plan Performance Disciplined Performance Verify Performance Track Performance 1 Performed Informally Base Practices Performed 18

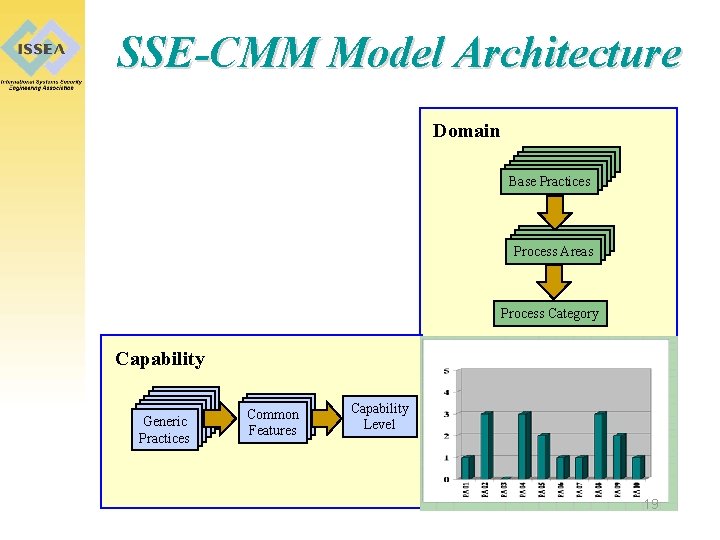
SSE-CMM Model Architecture Domain Base. Practices Base Process. Areas Process Category Capability Generic Practices Generic Practices Common Features Capability Level 19

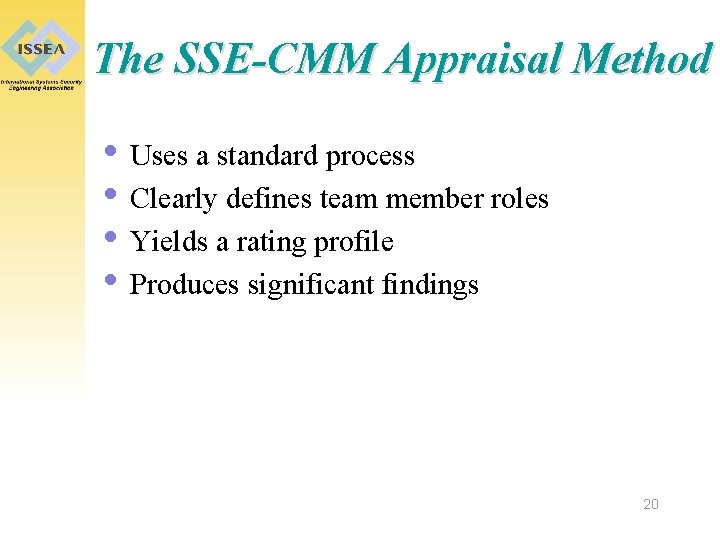
The SSE-CMM Appraisal Method • Uses a standard process • Clearly defines team member roles • Yields a rating profile • Produces significant findings 20

Appraisal Method Phases • Planning phase • Preparation phase • Onsite phase • Reporting phase 21

Appraisal Process • Administer questionnaire • Conduct targeted interviews • Fill in data tracking sheet • Develop preliminary findings • Perform follow-up interviews • Produce rating profile and final findings 22

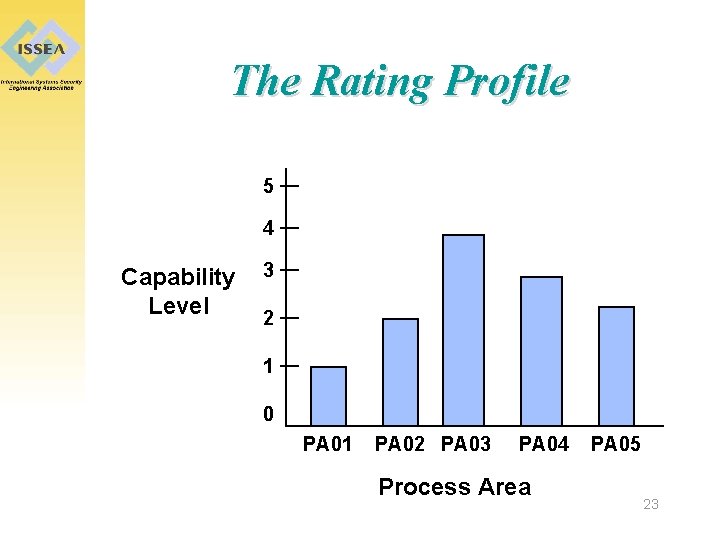
The Rating Profile 5 4 Capability Level 3 2 1 0 PA 01 PA 02 PA 03 PA 04 Process Area PA 05 23

Major Uses of the SSE-CMM Appraisal • Third-party appraisals for source selection purposes • Internal self appraisals for self improvement 24

Internal Metrics Efforts of the SSE-CMM Project

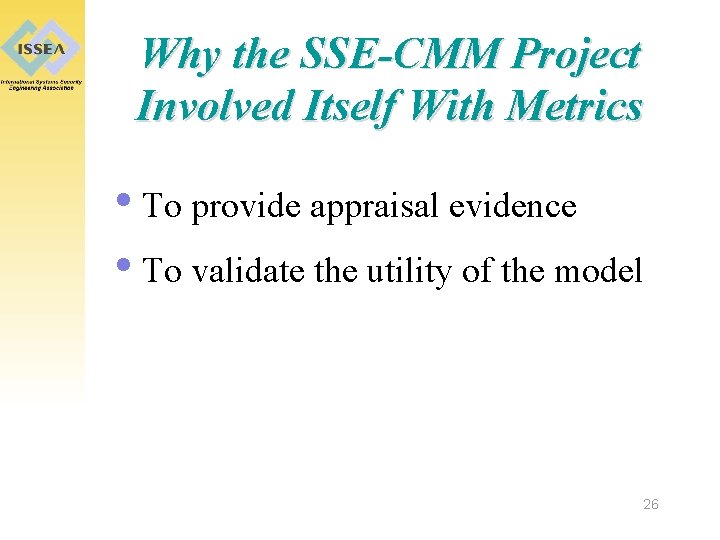
Why the SSE-CMM Project Involved Itself With Metrics • To provide appraisal evidence • To validate the utility of the model 26

Guiding Principles • You have to do it before you can manage it • Understand what's happening on the project before • • • defining organization-wide processes You can't measure it until you know what “it” is Managing with measurement is only meaningful when you're measuring the right things A culture of continuous improvement requires a foundation of sound management practice, defined processes, and measurable goals 27

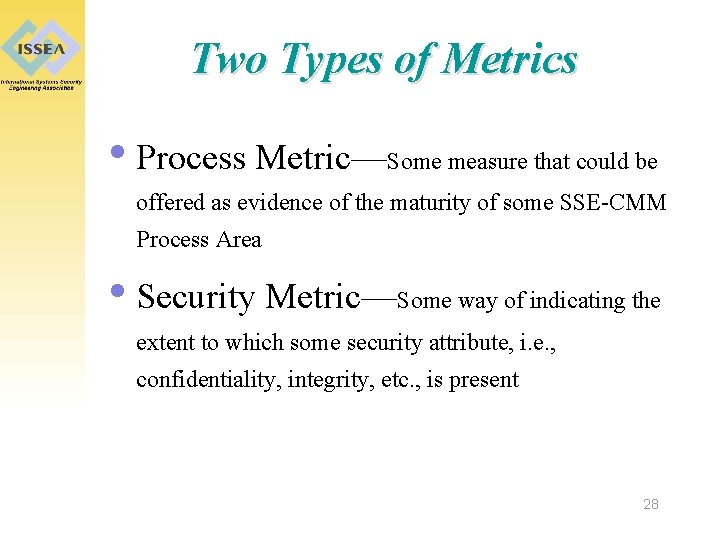
Two Types of Metrics • Process Metric—Some measure that could be offered as evidence of the maturity of some SSE-CMM Process Area • Security Metric—Some way of indicating the extent to which some security attribute, i. e. , confidentiality, integrity, etc. , is present 28

Internal Metrics Efforts • 1999 conference paper • Ongoing document drafting effort • IATAC current research effort 29

1999 Conference Paper • Systems Security Engineering Conference, • • • February 3 -4, 1999 Paper Title – “Developing and Applying System Security Engineering Metrics” Authors – Nadya Bartol, Lisa Gallagher, and Natalie Givans Paper summarized the Metrics Action Committee’s early work and presented an approach to metrics development 30

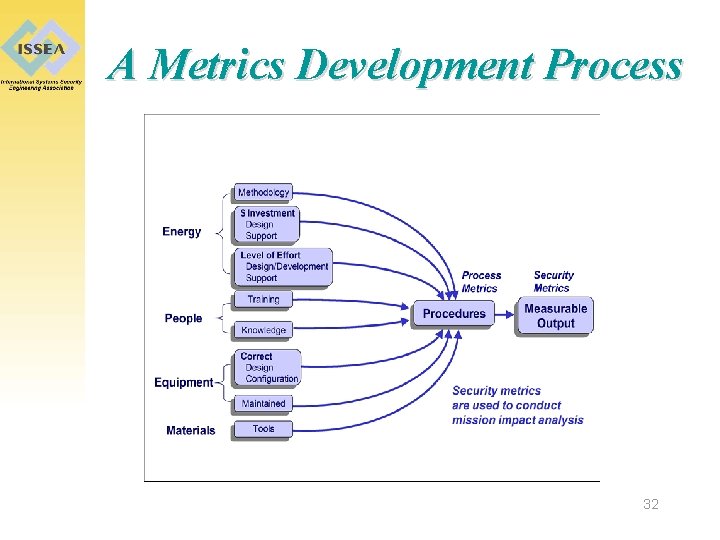
Committee’s Definition of Process “The logical organization of people, material, energy, equipment, and procedures into work activities designed to produce a specified end result. ” 31

A Metrics Development Process 32

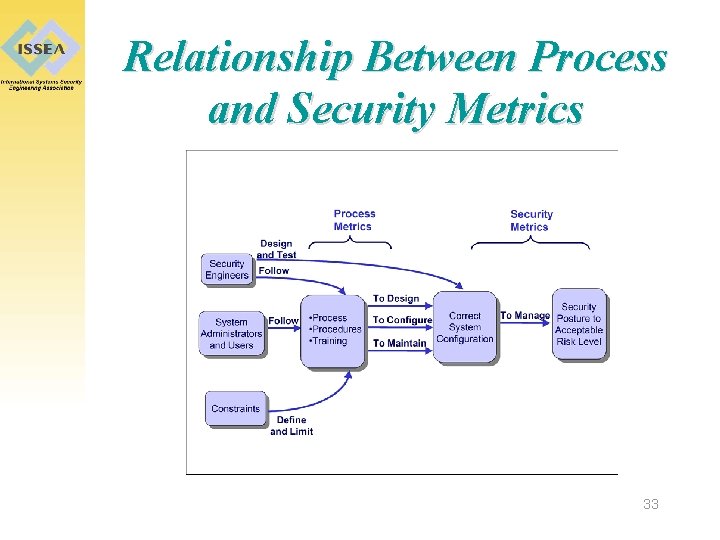
Relationship Between Process and Security Metrics 33

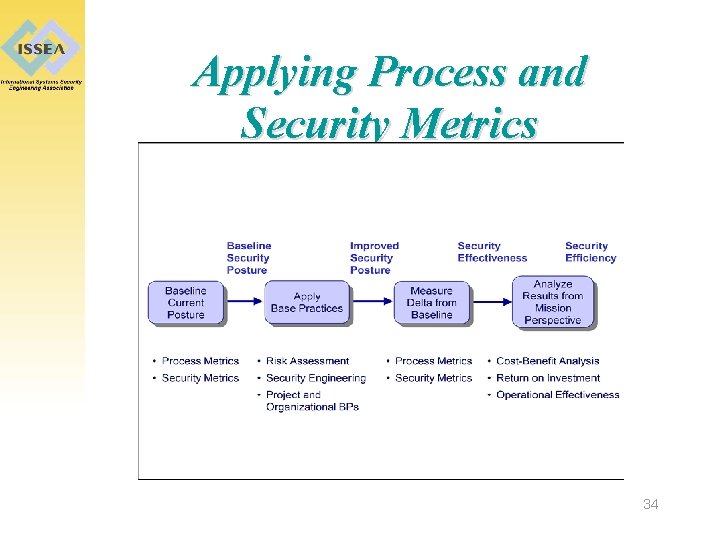
Applying Process and Security Metrics 34

Top-Down Tree 35

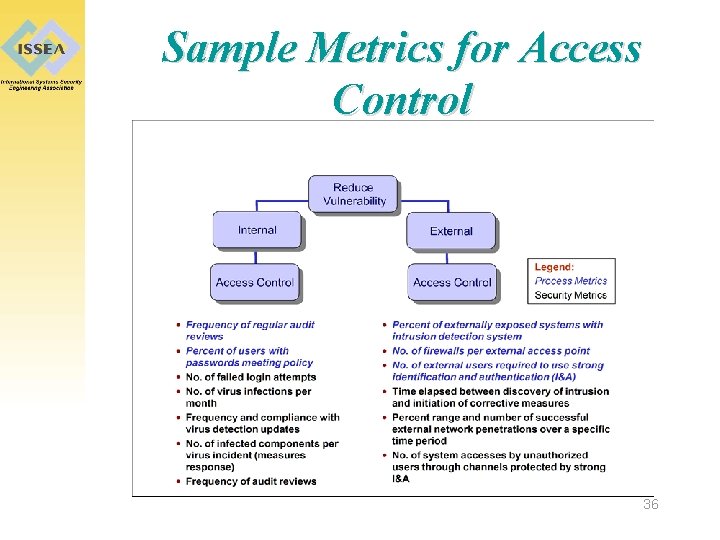
Sample Metrics for Access Control 36

One Company’s Experience • Process metrics are more useful than security • metrics in assessing process maturity Performing a self assessment, using measurements, does yield quantifiable efficiencies and cost savings 37

Specific Realized Process Efficiencies • Decreased the time required to conduct a • Security Test and Evaluation (ST&E) of identical network components at different sites eight times between the first and nth efforts Reduced site visits by three people lasting five days in Phase 1 of a large three-phase risk assessment effort to visits by two people for three days in Phase 2 38

Ongoing Document Drafting Effort

Documents in Preparation • “CIO Metrics for Information Assurance” • “SSE-CMM Practitioners Guide to Applying Metrics in Support of Business operations” 40

Both Documents Based Upon GMITS • Corporate Information Assurance Metrics – • • traced to Corporate Security Policy Corporate IT Information Assurance Metrics – traced to Corporate IT Security Policy IT System Information Assurance Metrics – traced to IT System Security Policy 41

CIO Document • Intended for Chief Information Officers • Aimed at a broad understanding • Based on the application of widely available standards and procedures 42

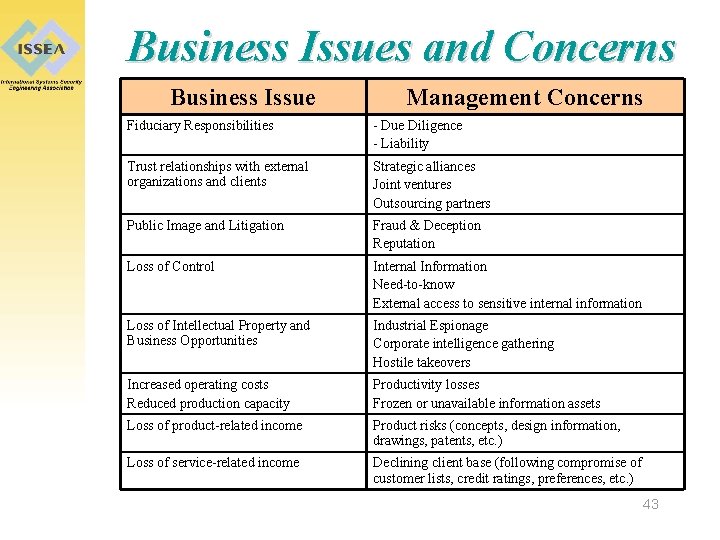
Business Issues and Concerns Business Issue Management Concerns Fiduciary Responsibilities - Due Diligence - Liability Trust relationships with external organizations and clients Strategic alliances Joint ventures Outsourcing partners Public Image and Litigation Fraud & Deception Reputation Loss of Control Internal Information Need-to-know External access to sensitive internal information Loss of Intellectual Property and Business Opportunities Industrial Espionage Corporate intelligence gathering Hostile takeovers Increased operating costs Reduced production capacity Productivity losses Frozen or unavailable information assets Loss of product-related income Product risks (concepts, design information, drawings, patents, etc. ) Loss of service-related income Declining client base (following compromise of customer lists, credit ratings, preferences, etc. ) 43

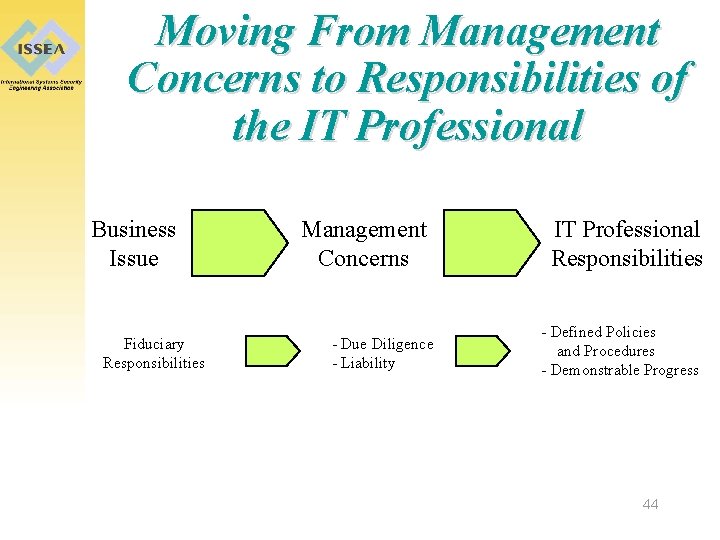
Moving From Management Concerns to Responsibilities of the IT Professional Business Issue Fiduciary Responsibilities Management Concerns - Due Diligence - Liability IT Professional Responsibilities - Defined Policies and Procedures - Demonstrable Progress 44

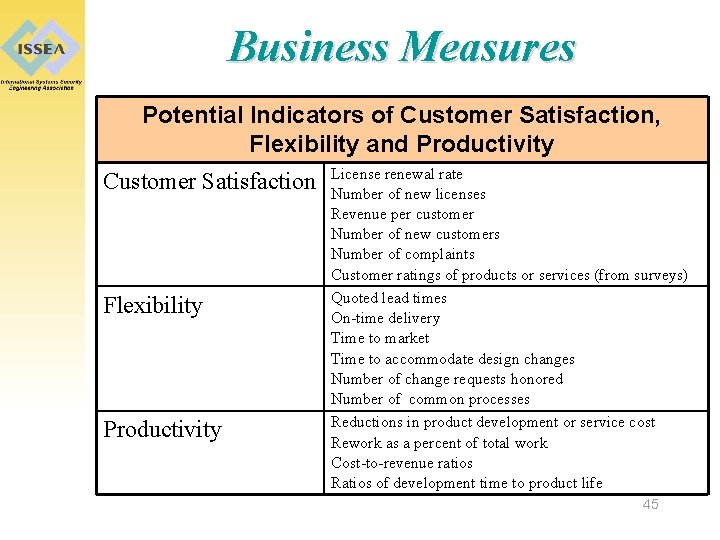
Business Measures Potential Indicators of Customer Satisfaction, Flexibility and Productivity Customer Satisfaction Flexibility Productivity License renewal rate Number of new licenses Revenue per customer Number of new customers Number of complaints Customer ratings of products or services (from surveys) Quoted lead times On-time delivery Time to market Time to accommodate design changes Number of change requests honored Number of common processes Reductions in product development or service cost Rework as a percent of total work Cost-to-revenue ratios Ratios of development time to product life 45

Practitioners Guide • Intended for systems security engineering • • • professionals Provides some perspectives for process measurement and lists several desired qualities of performance measures Defines measurable entities and associated measurable attributes for software processes Identifies a number of specific metrics for each of the SSE-CMM process areas 46

Perspectives of Process Measurement • Performance • Stability • Compliance • Capability • Improvement and investment 47

Process Performance Measures Should: • Relate closely to the issue under study • Have high information content • Pass a reality test • Permit easy economical collection of data • Permit consistently collected, well defined • • data Show measurable variation As a set, have diagnostic value 48

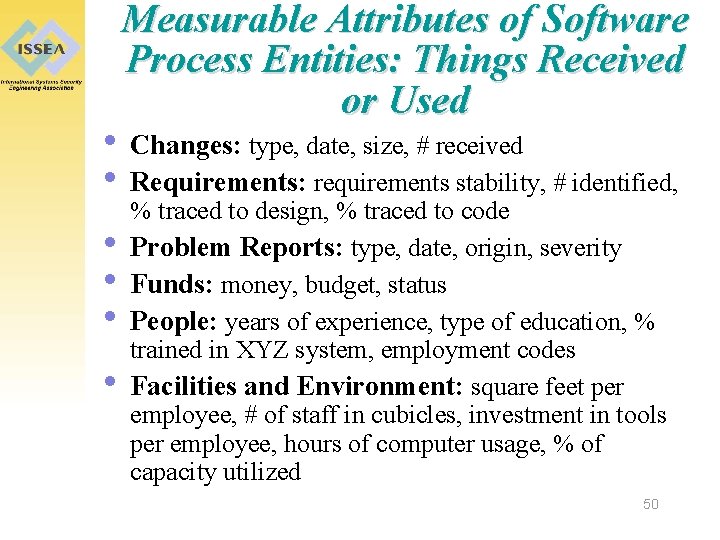
Measurable Entities in a Software Process • Things received or used • Activities and their elements • Things consumed, i. e. resources • Things held or retained • Things produced 49

Measurable Attributes of Software Process Entities: Things Received or Used • Changes: type, date, size, # received • Requirements: requirements stability, # identified, • • % traced to design, % traced to code Problem Reports: type, date, origin, severity Funds: money, budget, status People: years of experience, type of education, % trained in XYZ system, employment codes Facilities and Environment: square feet per employee, # of staff in cubicles, investment in tools per employee, hours of computer usage, % of capacity utilized 50

Mapping of Process Areas to Metrics • Process Area Title • Process Area Description • Base Practices • Related Metrics 51

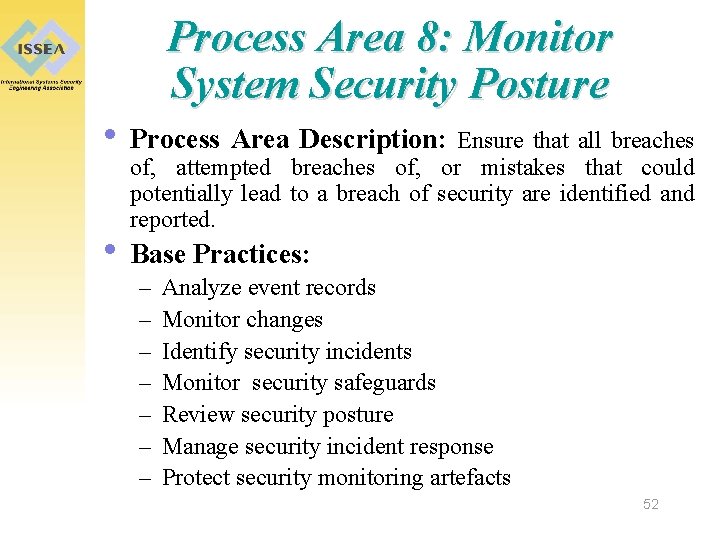
Process Area 8: Monitor System Security Posture • Process Area Description: Ensure that all breaches of, attempted breaches of, or mistakes that could potentially lead to a breach of security are identified and reported. • Base Practices: – – – – Analyze event records Monitor changes Identify security incidents Monitor security safeguards Review security posture Manage security incident response Protect security monitoring artefacts 52

Process Area 8: Monitor System Security Posture • Related Metrics: – – – – – number of false positives number of false negatives number of incidents reported number of security policy violations this period number of policy exceptions percentage of expired password number of guessed passwords number of incidents cost of monitoring during this period 53

Research Effort on the Part of the Information Assurance Technology Analysis Center (IATAC)

Aims of the IATAC Effort • • A means for uniformly monitoring and objectively documenting the organization’s security posture A means of determining appropriate corrective measures for specific areas that were identified as needing improvement and for justifying investments in those areas A means of tracking IA investments and their effectiveness An objective way of comparing strategies for deploying security measures and solutions and instituting and implementing security processes, policies, and procedures 55

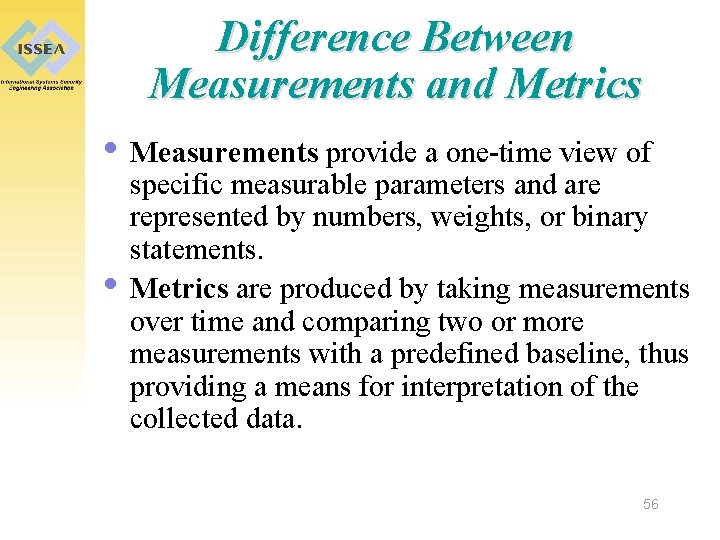
Difference Between Measurements and Metrics • Measurements provide a one-time view of • specific measurable parameters and are represented by numbers, weights, or binary statements. Metrics are produced by taking measurements over time and comparing two or more measurements with a predefined baseline, thus providing a means for interpretation of the collected data. 56

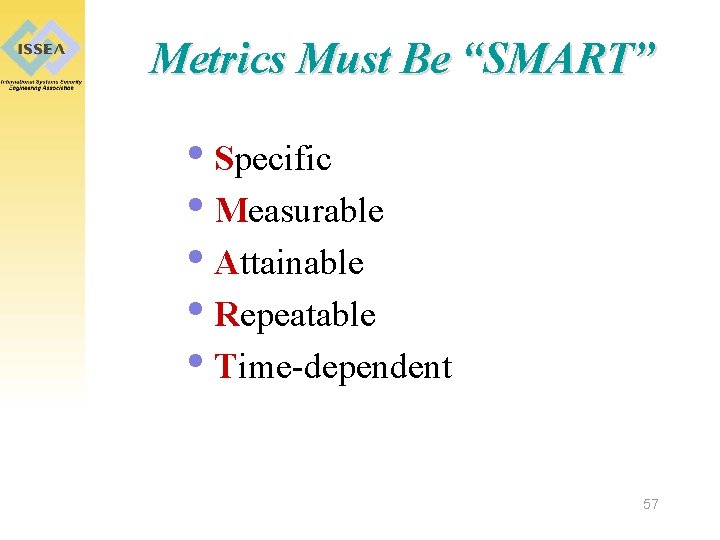
Metrics Must Be “SMART” • Specific • Measurable • Attainable • Repeatable • Time-dependent 57

Metrics Development Methodology Embodies: • Do. D IT Performance Assessment • • Methodology Stakeholder-Based Model IA Capabilities-Based Model 58

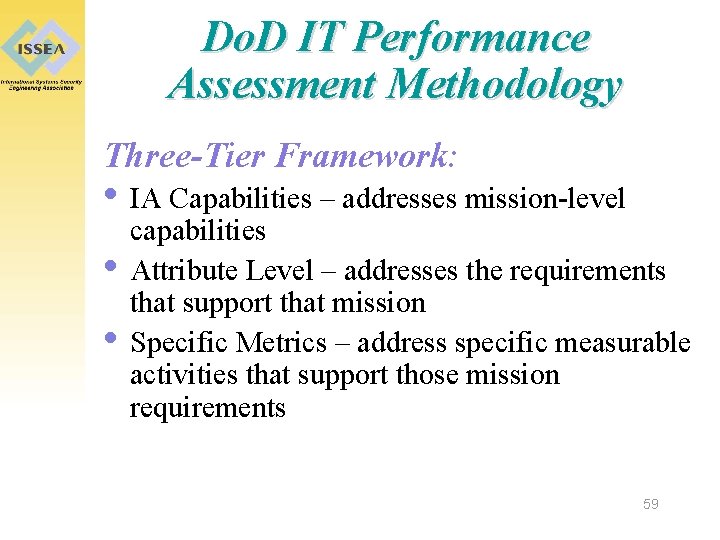
Do. D IT Performance Assessment Methodology Three-Tier Framework: • IA Capabilities – addresses mission-level • • capabilities Attribute Level – addresses the requirements that support that mission Specific Metrics – address specific measurable activities that support those mission requirements 59

Stakeholder-Based Model Views IA metrics from an organizational role perspective: • Program Manager • Funding Sponsor • Senior Security Manager • Operational User 60

Capabilities-Based Model Addresses the functional IA capabilities: • Protect • Detect • Respond 61

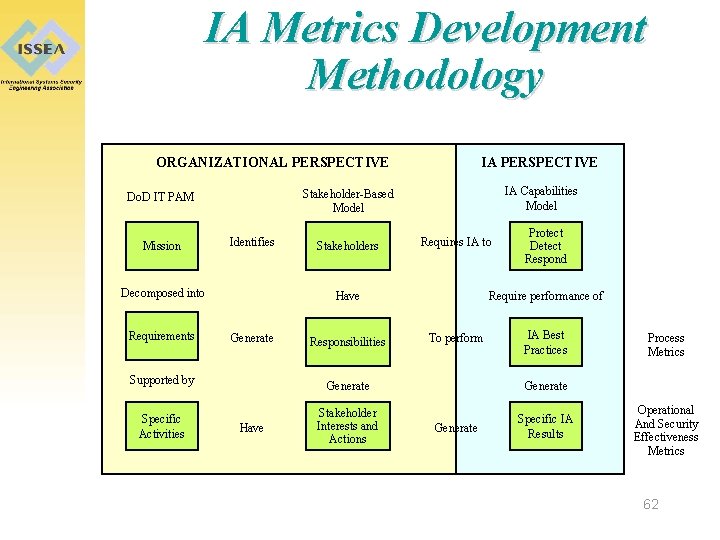
IA Metrics Development Methodology ORGANIZATIONAL PERSPECTIVE Identifies Decomposed into Requirements IA Capabilities Model Stakeholder-Based Model Do. D IT PAM Mission IA PERSPECTIVE Stakeholders Requires IA to Have Generate Responsibilities Protect Detect Respond Require performance of To perform IA Best Practices Supported by Generate Specific Activities Stakeholder Interests and Actions Specific IA Results Have Generate Process Metrics Operational And Security Effectiveness Metrics 62

IA Program Establishment Process Develop Organization’s IA Metrics Identify Data Collection Methods for Each Metric Update and Improve Metrics Assign Collection Analysis and Reporting Responsibility No Execute Metrics Program as Planned Changes in mission, risks, or funding? Yes 63

The IATAC Report • Outlines an organization-specific metrics • • development process Lists a number of source documents and tools Presents and describes a sample IA metrics database 64

Data Collection Methods • Automated tools • Document review • Survey and interviews • System configuration verification • Observation 65

Observations and Conclusions • Developing metrics requires substantial • discipline and commitment Meaningful results accrue only if – Performance is measured repeatedly over time – Metrics are actively used to drive process improvement 66

Current State of Security Metrics Research • Security metrics research is a very hot topic • Yet, funding is extremely hard to obtain • Most current effort is unfunded • Therefore, progress is quite slow • Much of the current effort tends to be preliminary and somewhat superficial – Each environmental setting is different, making it hard to generalize – There isn’t the support to go deeper 67
 Ssecmm
Ssecmm Backlog management index formula
Backlog management index formula Privatesecurity
Privatesecurity Agatsy
Agatsy Chairman agenda
Chairman agenda Chairman chart
Chairman chart Willes little flower school chairman
Willes little flower school chairman Bhore committee
Bhore committee Coh chairman scout
Coh chairman scout Chairman 25
Chairman 25 Components of agriculture renewal action plan
Components of agriculture renewal action plan Welcome speech for chairman
Welcome speech for chairman Sme chairman
Sme chairman Toyota chairman of the board
Toyota chairman of the board Lic chairman club member benefits
Lic chairman club member benefits Software security metrics
Software security metrics Oracle software security assurance
Oracle software security assurance Security assurance framework
Security assurance framework George washington x king george iii
George washington x king george iii Venn diagram ghent
Venn diagram ghent Kad bi drveće hodalo analiza pjesme
Kad bi drveće hodalo analiza pjesme Bijeli jelen ispitna pitanja
Bijeli jelen ispitna pitanja Alenka jelen
Alenka jelen Lesné cicavce
Lesné cicavce čím se živí jelen
čím se živí jelen Kviz bijeli jelen
Kviz bijeli jelen Jelen nižší klasifikace
Jelen nižší klasifikace Bijeli jelen pitanja za ponavljanje
Bijeli jelen pitanja za ponavljanje Sarna a jeleń
Sarna a jeleń Bijeli jelen lektira
Bijeli jelen lektira Anyegin szereplők
Anyegin szereplők Bijeli jelen likovi
Bijeli jelen likovi This is to certify that
This is to certify that Rumcajs jelen
Rumcajs jelen Bijeli jelen lutkarski film
Bijeli jelen lutkarski film Pravljica jelen jarko
Pravljica jelen jarko Bijeli jelen vrijeme radnje
Bijeli jelen vrijeme radnje Vladimir nazor najpoznatija djela
Vladimir nazor najpoznatija djela Jeleń ireneusz rodzinna tragedia
Jeleń ireneusz rodzinna tragedia Bijeli jelen lektira 3 razred
Bijeli jelen lektira 3 razred Iteration workflows in software project management
Iteration workflows in software project management Netsh show profiles
Netsh show profiles Ghost profiles
Ghost profiles Voice translation profile
Voice translation profile Npv profiles
Npv profiles Tectonic hazard profiles
Tectonic hazard profiles Cultural intelligence profiles
Cultural intelligence profiles Payback chapter 8
Payback chapter 8 H.264 profiles and levels
H.264 profiles and levels Mainstreamers psychographics
Mainstreamers psychographics Corporate traveler profiles
Corporate traveler profiles Profitability index ba ii plus
Profitability index ba ii plus Jem finch description
Jem finch description Alma publishing profiles
Alma publishing profiles Capital budgeting
Capital budgeting Specific flashing profiles
Specific flashing profiles Tkam character profiles
Tkam character profiles Npv profiles
Npv profiles Maureen neihart keynote revised profiles of the gifted
Maureen neihart keynote revised profiles of the gifted Onf profiles
Onf profiles Asee profiles
Asee profiles Mining company profile doc
Mining company profile doc Npv profiles
Npv profiles Unacceptable weld profile
Unacceptable weld profile Aitsl leadership profiles
Aitsl leadership profiles Npv profiles
Npv profiles Wireless security in cryptography and network security
Wireless security in cryptography and network security E commerce security meaning
E commerce security meaning