Session Code CLI 312 Windows Longhorn Enhancements For













- Slides: 23

Session Code: CLI 312 Windows “Longhorn: ” Enhancements For A Trustworthy Application Experience Jude Kavalam Group Program Manager Microsoft Corporation judej@microsoft. com

Agenda Application experience on Windows XP Customer feedback Innovation in “Longhorn” for existing applications Call to action

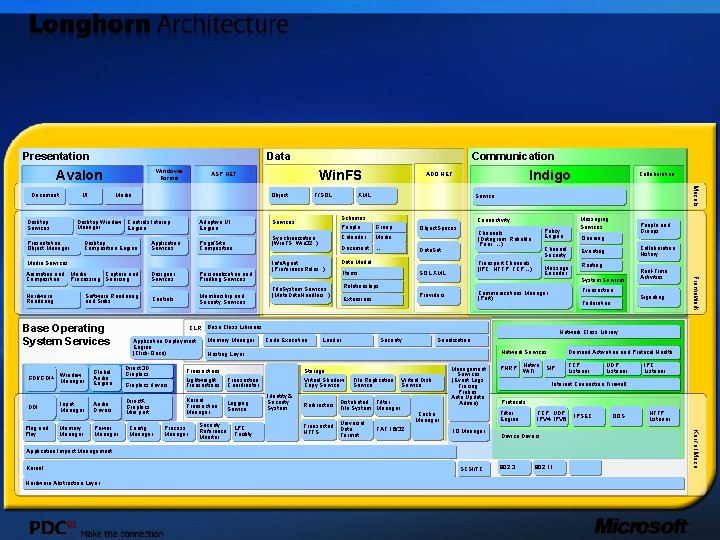
Presentation Data Windows Forms Avalon UI Object Media Desktop Window Controls Interop Manager Engine Desktop Services Adaptive UI Engine Designer Services Personalization and Profiling Services Hardware Rendering Controls Membership and Security Services Media Services Software Rendering and Sinks Base Operating System Services GDI/GDI+ DDI Input Manager Memory Manager Global Audio Engine Audio Drivers Power Manager Direct 3 D Graphics Direct. X Graphics Mini port Config Manager Group Calendar Media Document … Memory Manager Data. Set Data Model Transport Channels (IPC, HTTP, TCP…) SQL XML Items Relationships Channel Security Eventing Message Encoder Routing Security Reference Monitor LPC Facility System Services Transaction Hardware Abstraction Layer Real-Time Activities Signaling Federation Loader Security Serialization Demand Activation and Protocol Health Network Services Storage Virtual Shadow Copy Service Identity & Security System File Replication Service Virtual Disk Service Filter Redirectors Distributed File System Manager Transacted NTFS Universal Data Format FAT 16/32 Management Services (Event Logs, Tracing, Probes, Auto Update, Admin) PNRP IO Manager TCP Listener SCSI/FC UDP Listener IPC Listener Internet Connection Firewall Protocols Filter Engine Cache Manager Native SIP Wi. Fi TCP, UDP IPV 4, IPV 6 IPSEC Device Drivers Application Impact Management Kernel Collaboration History Network Class Library Code Execution Transaction Coordinator Logging Service People and Groups Queuing Communications Manager (Port) Providers Extensions Policy Engine Channels (Datagram, Reliable, Peer, …) Hosting Layer Kernel Transaction Manager Messaging Services Connectivity Object. Spaces Base Class Libraries Lightweight Transactions Process Manager Schemas People File. System Services (Meta. Data. Handlers. . ) Transactions Graphics drivers Service 802. 3 802. 11 . . QOS HTTP Listener Kernel Mode Plug and Play Window Manager CLR Application Deployment Engine (Click-Once) Info. Agent (Preference. Rules. . ) Collaboration Framework Animation and Media Capture and Composition Processing Sourcing Indigo ADO. NET XML Synchronization (Win. FS, Win 32. . ) Page/Site Composition Desktop Composition Engine T/SQL Services Application Services Presentation Object Manager Win. FS ASP. NET Models Document Communication

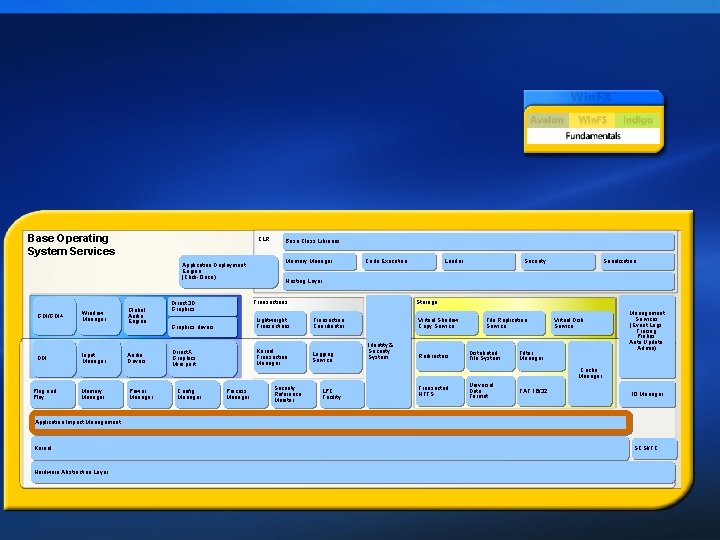
Base Operating System Services CLR Application Deployment Engine (Click-Once) GDI/GDI+ DDI Plug and Play Window Manager Input Manager Memory Manager Global Audio Engine Audio Drivers Power Manager Base Class Libraries Memory Manager Loader Security Serialization Hosting Layer Transactions Direct 3 D Graphics Storage Graphics drivers Lightweight Transactions Transaction Coordinator Direct. X Graphics Mini port Kernel Transaction Manager Logging Service Config Manager Code Execution Virtual Shadow Copy Service Identity & Security System File Replication Service Redirectors Distributed File System Transacted NTFS Universal Data Format Virtual Disk Service Filter Management Services (Event Logs, Tracing, Probes, Auto Update, Admin) Cache Manager Process Manager Security Reference Monitor LPC Facility FAT 16/32 IO Manager Application Impact Management Kernel Hardware Abstraction Layer SCSI/FC

Introduction Windows XP significantly improved the OS experience Application experience still needs work Application fragility is caused by the negative impact of applications on the system or other applications Fragility is revealed by Internet Explorer crashes and hangs Application and system crashes and hangs Inability to remove undesirable applications (ad-ware, spy-ware, grenade-ware) Loss of application or system functionality Application performance degradation Slow down in boot time

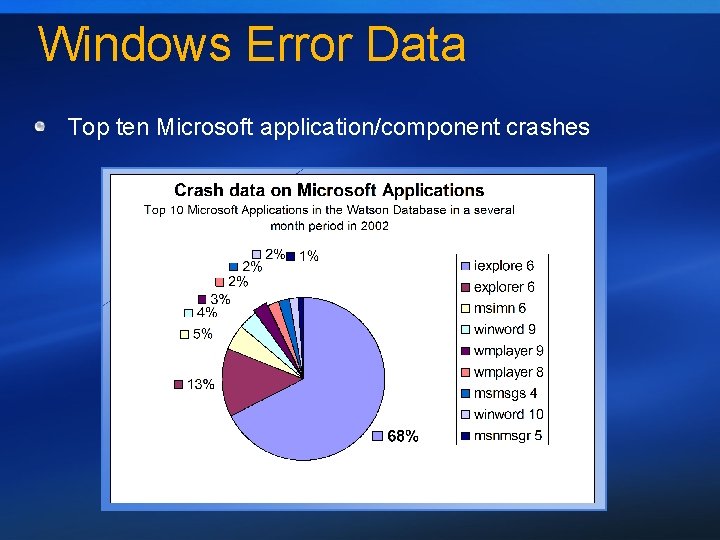
Windows Error Data Top ten Microsoft application/component crashes

So What’s Up With IE/Explorer? !! Probably the world’s most frequently run applications They are both highly extensible applications At least 75% of the crashes are in extension code Active. X controls, Browser Helper Objects, Shell Extensions, etc. Rank 1 2 3 4 5 6 7 8 Description Crash in extension code Extension over release of IE COM objects IE security fix or service pack regression Crash due to extension, not on stack Unknown IE bug Crash with extension on the stack Extensions unloaded window proc

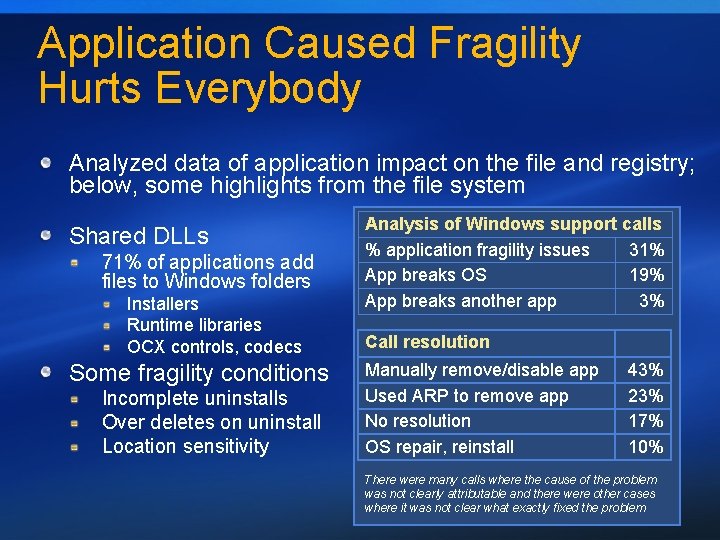
Application Caused Fragility Hurts Everybody Analyzed data of application impact on the file and registry; below, some highlights from the file system Shared DLLs 71% of applications add files to Windows folders Installers Runtime libraries OCX controls, codecs Some fragility conditions Incomplete uninstalls Over deletes on uninstall Location sensitivity Analysis of Windows support calls % application fragility issues 31% App breaks OS 19% App breaks another app 3% Call resolution Manually remove/disable app Used ARP to remove app No resolution OS repair, reinstall 43% 23% 17% 10% There were many calls where the cause of the problem was not clearly attributable and there were other cases where it was not clear what exactly fixed the problem

“Run As Admin” Makes It Worse Administrator privilege makes everything more dangerous Scope of attack Surface area Users have no choice Applications don’t install or run in LUA System functionality does not degrade in a helpful way

So What Do Customers Want? Make applications and drivers less dangerous Application undo Make “limited user” feasible Make administrators run as administrators only when needed Protect the system

Innovations In "Longhorn" By design managed applications have low impact Win 32 applications need supervision Manage and attribute application impact Protect the system Applications can be completely uninstalled Installing and loading drivers Make it easy for ISVs to install drivers the right way Only signed drivers will be loaded Drivers can be attributed and fully uninstalled Protect COM hosts Administrators: the right privilege at the right time

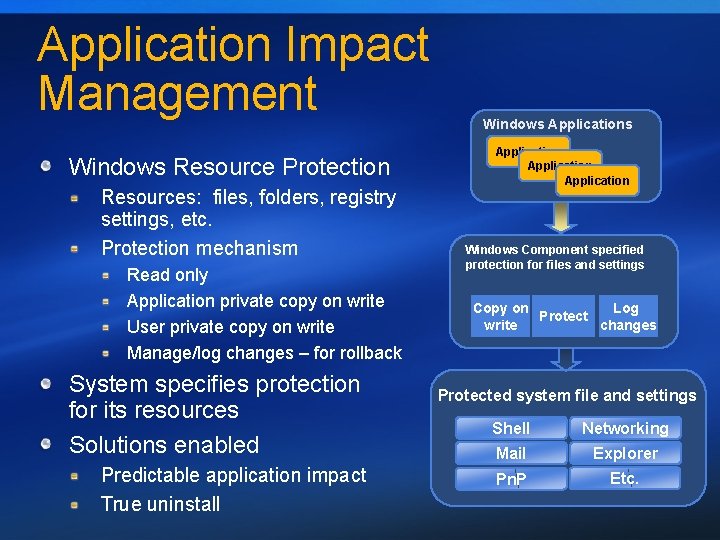
Application Impact Management Windows Resource Protection Resources: files, folders, registry settings, etc. Protection mechanism Read only Application private copy on write User private copy on write Manage/log changes – for rollback System specifies protection for its resources Solutions enabled Predictable application impact True uninstall Windows Application Windows Component specified protection for files and settings Copy on Log Protect write changes Protected system file and settings Shell Networking Mail Explorer Pn. P Etc.

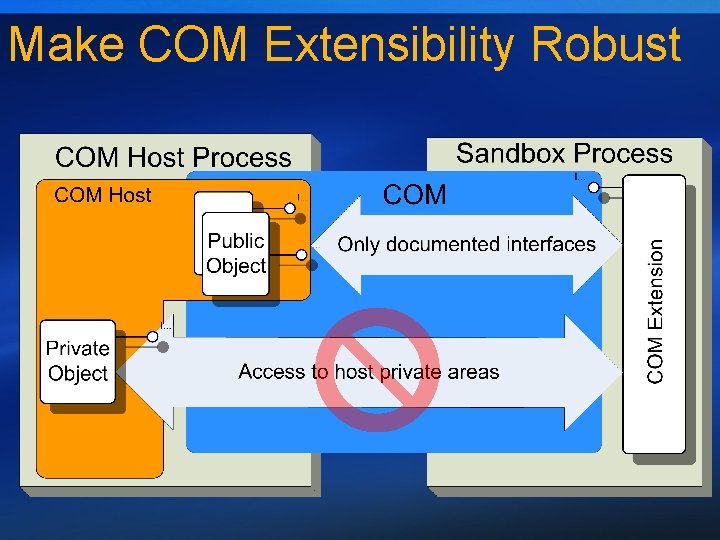
Make COM Extensibility Robust

Installing And Loading Drivers Must be installed via Pn. P mechanisms App/driver tying Cleaner install/uninstall rollback For beta tools contact – DIFx. Beta@microsoft. com Driver packages must be signed Goal is security independent of quality Signing methods Authenticode Signature Domain/Local Administrator

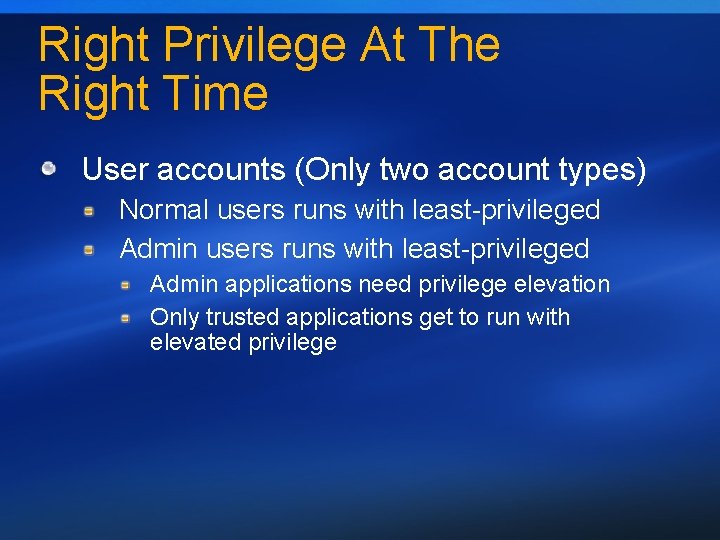
Right Privilege At The Right Time User accounts (Only two account types) Normal users runs with least-privileged Admin applications need privilege elevation Only trusted applications get to run with elevated privilege

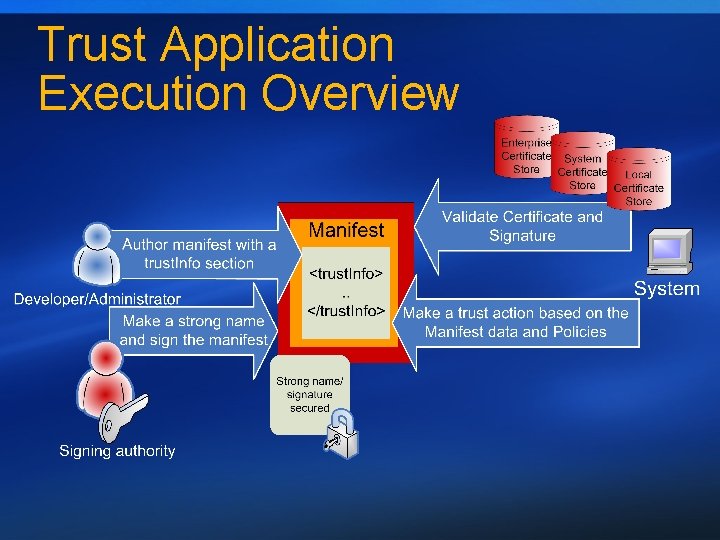
Trust Application Execution Overview

Trust Evaluation Process Code validation is a human decision Authenticode signed manifests Certificate in the store Domain administrators signed Deployment manifest Local administrators blessed All machine have a signing key Default behavior changed by policy

Impact On Applications Compatibility: majority of applications will work Application impact management exception mechanism Running apps under LUA will have limitations Virtualization of protected keys and files will help Some applications will break

What You Can Do Create a signed manifest Update your installer technology Perform complete uninstalls Least privileged user access Active. X controls - don’t assume full access Published extensibility mechanisms only Windows ISV Lab Pre-certification and compatibility testing and performance analysis Access to technology experts To schedule a visit contact your Microsoft account manager or e-mail isvlab@microsoft. com All ISVs are eligible

Windows Application Verifier Detect run time issues in Win 32 applications Memory corruptions Hangs Security issues Reduces crashes 67. 8% of 3 rd party user mode crashes could have been detected using the App. Verifier Aids in Logo/Certification testing Non-administrator scenarios Resource management Version checking Available in the Application Compatibility Toolkit 3. 0 http: //www. microsoft. com/windows/appcompatibility/

Summary Remove the fear of using applications Application experience on “Longhorn” More reliable and robust Applications and drivers are safer Non Admin users are safer COM hosting is more stable Your to-dos Test and run as LUA Check Active. X controls and shell extensions Use manifests Logo program and App. Verifier

© 2003 -2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.
