Windows Vista And Windows Server Codename Longhorn Security























- Slides: 39

Windows Vista And Windows Server Codename “Longhorn” Security Enhancements Avi Ben-Menahem Lead Program Manager Windows Security Microsoft Corporation Chris Corio Program Manager

Agenda Windows Vista and Windows Server codenamed “Longhorn” Security Overview Isolated Desktop Kernel Mode Driver Signing Crypto Next Generation (a. k. a CNG) Base Smart Card CSP Architecture Win. Logon Architecture User Account Control and You

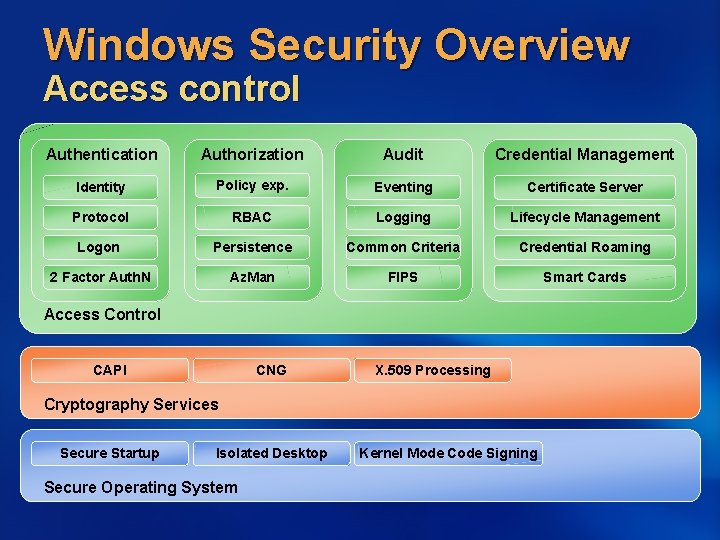
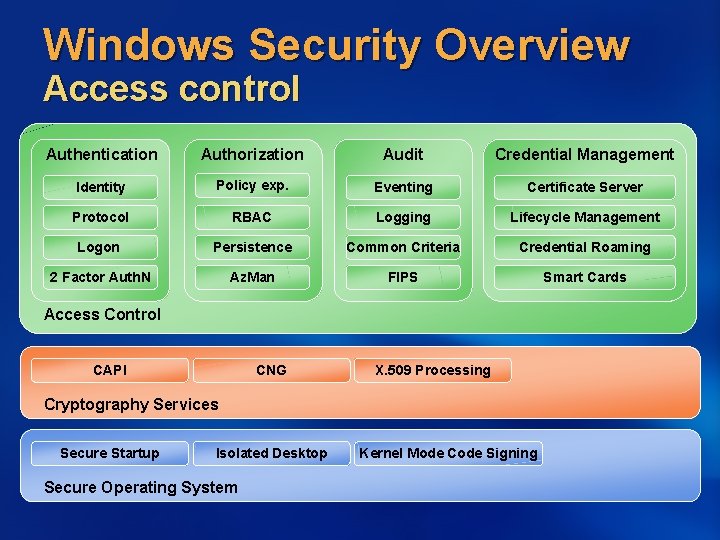
Windows Security Overview Access control Authentication Authorization Audit Credential Management Policy exp. Eventing Certificate Server Protocol RBAC Logging Lifecycle Management Logon Persistence Common Criteria Credential Roaming 2 Factor Auth. N Az. Man FIPS Smart Cards End User Tools Identity Access Control CAPI CNG X. 509 Processing Cryptography Services Secure Startup Isolated Desktop Secure Operating System Kernel Mode Code Signing

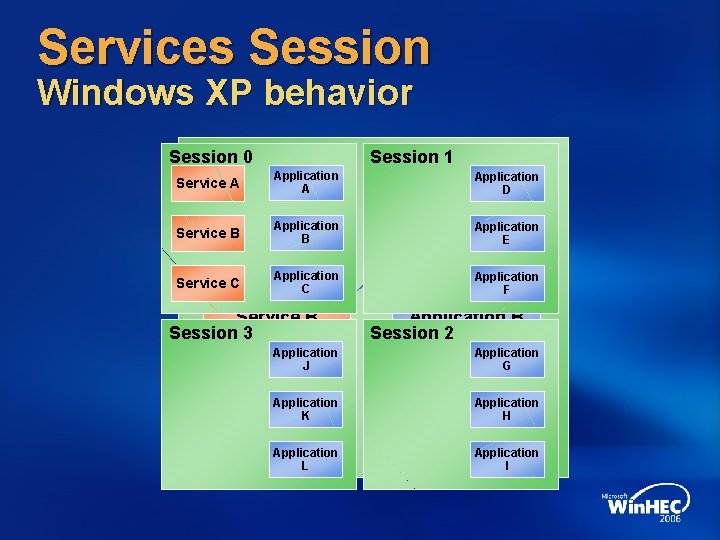
Services Session Windows XP behavior Session 00 Session 1 Application A Application D Service A Application Service A Service B B Service C Application C Service B Session 3 E Application F Application B Session 2 Application J Application G Application Service KC Application. HC Application L Application I

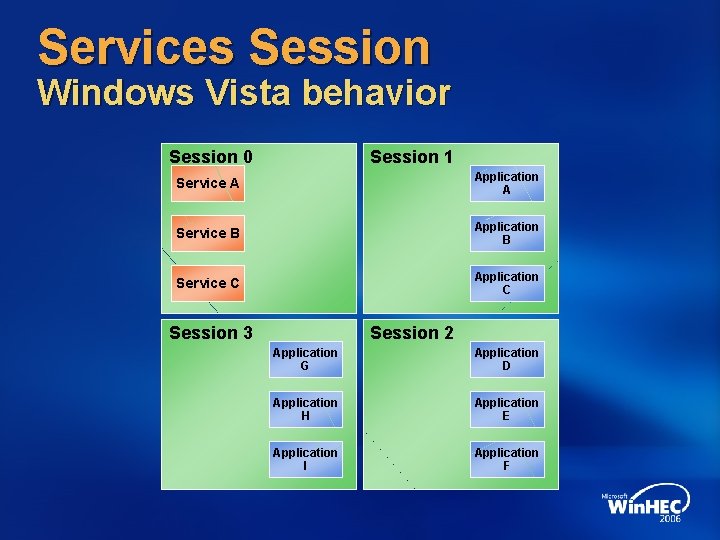
Services Session Windows Vista behavior Session 0 Session 1 Service A Application A Service B Application B Service C Application C Session 3 Session 2 Application G Application D Application H Application E Application I Application F

Services Session Technology introduction Separation of Services from User Sessions Desktop is the security boundary for Windows user interfaces Interactive Services are vulnerable to compromise through Windows Messaging Currently users can not see or interact with interactive service UI from their session Interactive Services Detection Service is available in the interim

Services Session Implementation guidelines Services should never open a window on the interactive desktop Services which need user input can Use WTSSend. Message to pop up a simple message box on user’s desktop Inject process into the target session by using Create. Process. As. User API

Motivation For Kernel Mode Code Signing Trustworthy computing built on a trusted kernel Windows Vista has an identifiable kernel state Secure kernel loads only signed binaries Reduce platform vulnerability from unknown binaries Identifiable kernel enables new scenarios Access next generation premium content Address growing threat of malicious rootkit attacks Improve reliability by identifying and working with kernel mode software publishers

Code Integrity Verification Signature checks by OS loader and kernel On x 64 64 -bit platforms All kernel mode code must be signed in order to load Identity of all kernel mode binaries is verified System audit events for integrity check failures On x 86 32 -bit platforms Administrator prompted and accepts to install unsigned kernel mode code Load-time checks done on all kernel mode binaries, unsigned code allowed to load Next generation premium content may not be accessible, depending on content protection policy

Developer And Test Support For developers and testers Options to disable code verification policy Active kernel debugger attached and turn on debugging F 8 key, Advanced Boot Option to disable driver signing enforcement for current boot Boot configuration option to not fail driver load if the integrity check fails (Beta 2 only) For pre-release testing WHQL Test signing Bcdedit option to enable load of Test Signed drivers

Signing Boot Critical Drivers Boot critical drivers are loaded by OS Loader Start Type = 0, loaded by Winload Boot critical driver files must be embedded signed Signature contained in the binary file Avoids boot time degradation locating catalog file Embedded sign before submitting to WHQL Sign individual driver files, then submit package This is a new WHQL Logo requirement

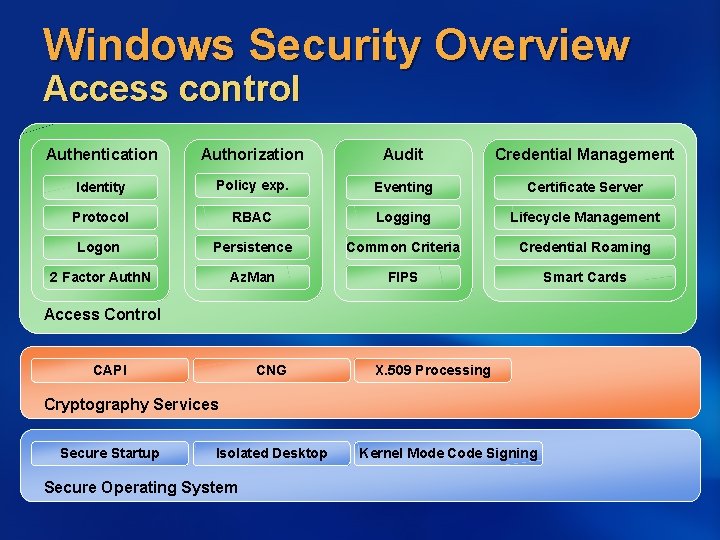
Windows Security Overview Access control Authentication Authorization Audit Credential Management Policy exp. Eventing Certificate Server Protocol RBAC Logging Lifecycle Management Logon Persistence Common Criteria Credential Roaming 2 Factor Auth. N Az. Man FIPS Smart Cards End User Tools Identity Access Control CAPI CNG X. 509 Processing Cryptography Services Secure Startup Isolated Desktop Secure Operating System Kernel Mode Code Signing

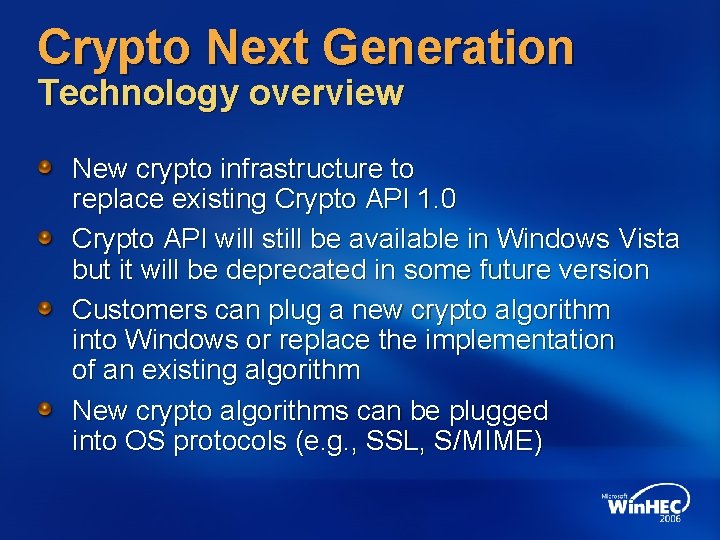
Crypto Next Generation Technology overview New crypto infrastructure to replace existing Crypto API 1. 0 Crypto API will still be available in Windows Vista but it will be deprecated in some future version Customers can plug a new crypto algorithm into Windows or replace the implementation of an existing algorithm New crypto algorithms can be plugged into OS protocols (e. g. , SSL, S/MIME)

Crypto Next Generation Feature highlights Crypto agility Flexible configuration system that includes machine and enterprise level settings Simple and granular plug-in model that supports both kernel and user mode Support a super set of the algorithms in Crypto API, including elliptic curve crypto (ECDH, ECDSA) and “Suite-B” compliance Private key isolation for Common Criteria compliance Improved performance

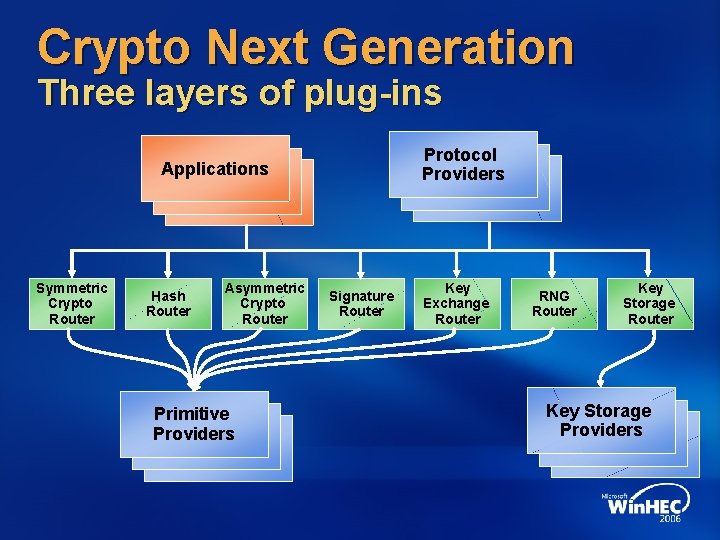
Crypto Next Generation Three layers of plug-ins Protocol Providers Applications Symmetric Crypto Router Hash Router Asymmetric Crypto Router Primitive Providers Signature Router Key Exchange Router RNG Router Key Storage Providers

Windows Security Overview Access control Authentication Authorization Audit Credential Management Policy exp. Eventing Certificate Server Protocol RBAC Logging Lifecycle Management Logon Persistence Common Criteria Credential Roaming 2 Factor Auth. N Az. Man FIPS Smart Cards End User Tools Identity Access Control CAPI CNG X. 509 Processing Cryptography Services Secure Startup Isolated Desktop Secure Operating System Kernel Mode Code Signing

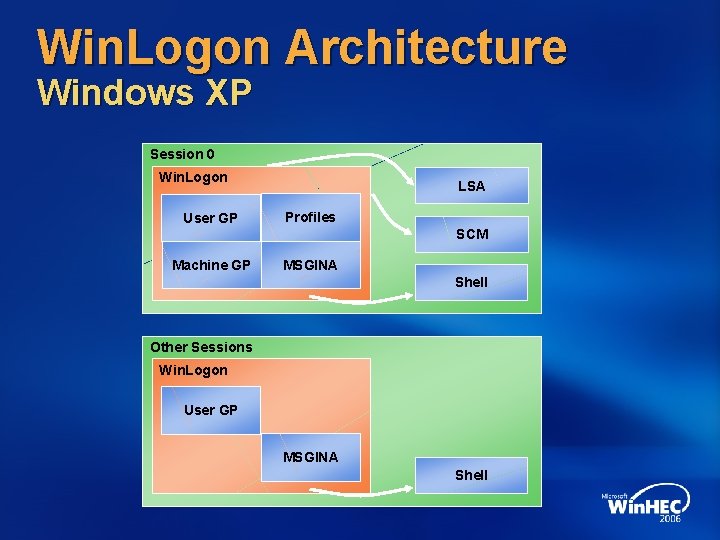
Win. Logon Architecture Windows XP Session 0 Win. Logon User GP LSA Profiles SCM Machine GP MSGINA Shell Other Sessions Win. Logon User GP MSGINA Shell

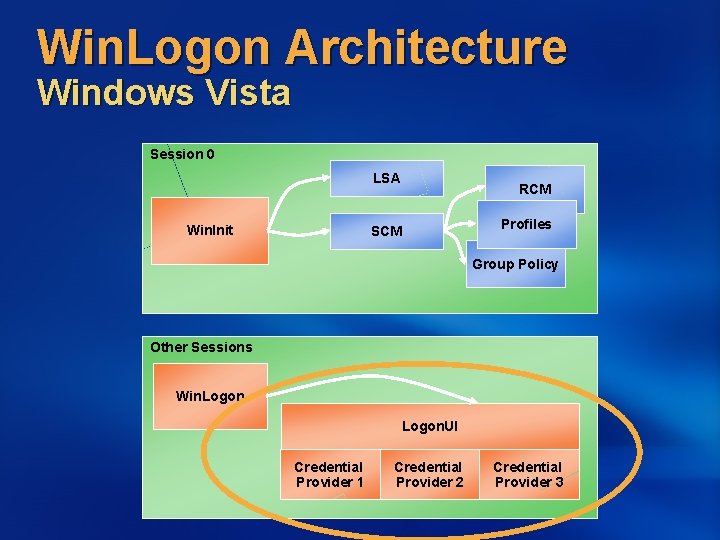
Win. Logon Architecture Windows Vista Session 0 LSA Win. Init RCM SCM Profiles Group Policy Other Sessions Win. Logon. UI Credential Provider 1 Credential Provider 2 Credential Provider 3

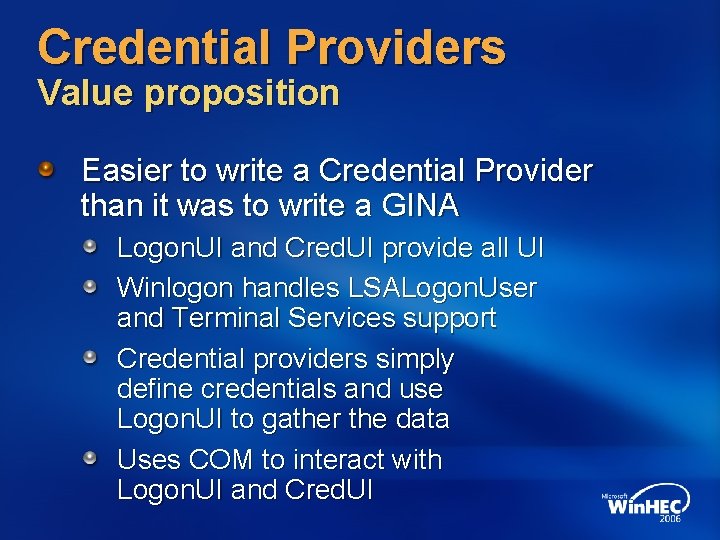
Credential Providers Technology introduction Credential Providers replace GINA Credential Providers “plug in” to Logon UI can interact simultaneously with multiple credential providers Credential Providers can be user selected and/or event driven Inbox Credential Providers Password Smart Card What Credential Providers cannot do Replace the UI for the logon screen

Credential Providers Value proposition Easier to write a Credential Provider than it was to write a GINA Logon. UI and Cred. UI provide all UI Winlogon handles LSALogon. User and Terminal Services support Credential providers simply define credentials and use Logon. UI to gather the data Uses COM to interact with Logon. UI and Cred. UI

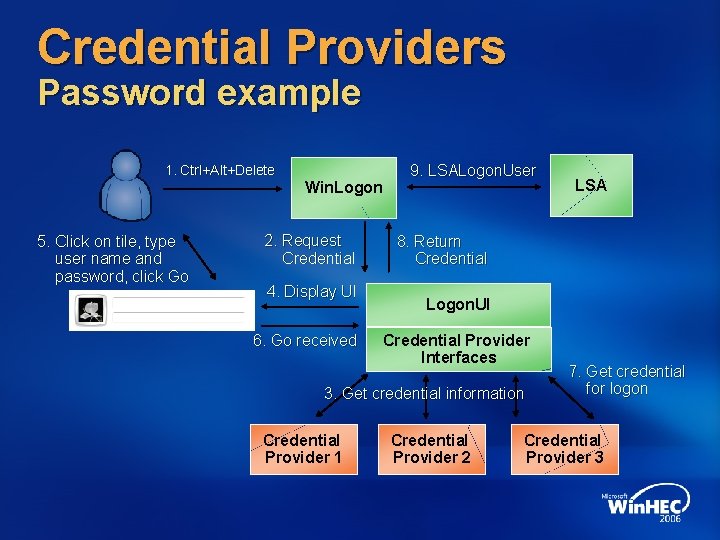
Credential Providers Password example 1. Ctrl+Alt+Delete Win. Logon 5. Click on tile, type user name and password, click Go 2. Request Credential 4. Display UI 6. Go received 9. LSALogon. User 8. Return Credential Logon. UI Credential Provider Interfaces 3. Get credential information Credential Provider 1 LSA Credential Provider 2 7. Get credential for logon Credential Provider 3

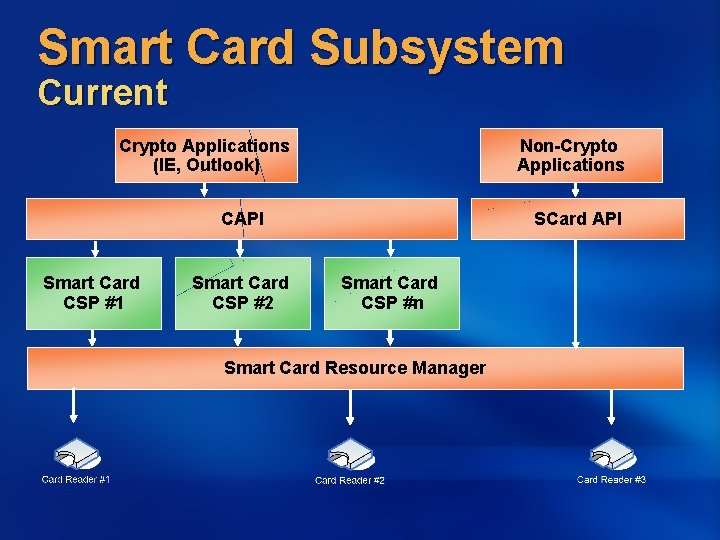
Smart Card Subsystem Current Crypto Applications (IE, Outlook) Non-Crypto Applications CAPI Smart Card CSP #1 Smart Card CSP #2 SCard API Smart Card CSP #n Smart Card Resource Manager

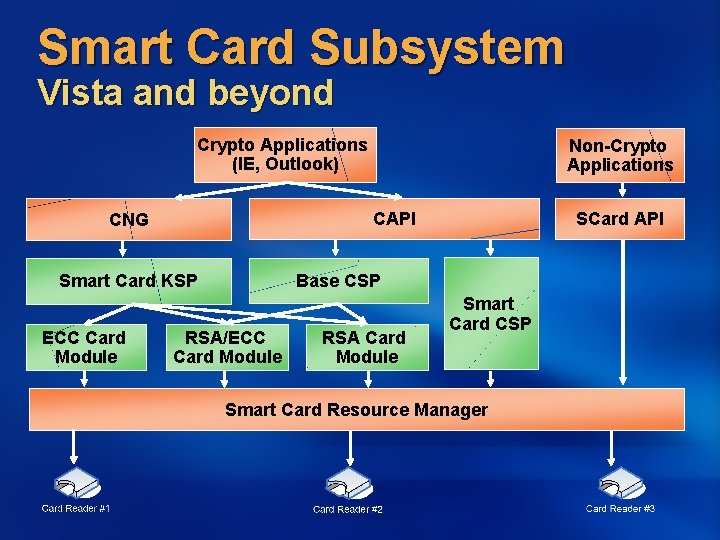
Smart Card Subsystem Vista and beyond Crypto Applications (IE, Outlook) CAPI CNG SCard API Base CSP Smart Card KSP ECC Card Module Non-Crypto Applications RSA/ECC Card Module RSA Card Module Smart Card CSP Smart Card Resource Manager

Smart Card Subsystem Simplified Software Development Common crypto operations handled in the platform API for card manufacturers Enhanced User Experience Planned Certification and Testing Program for Smartcard middleware on Windows Update Pn. P support for Smart Cards Enhanced Smart Card Logon Scenarios Root certificates propagation Integrated Smart Card unblock

Service Hardening Motivation Services are attractive targets for malware Run without user interaction Number of critical vulnerabilities in services Large number of services run as “System” Worms target services Sasser, Blaster, Code. Red, Slammer, etc…

Service Hardening Developer guidance Move to a least privileged account Use “Local Service” or “Network Service” Grant Service Sid access via ACLs on service specific resources Use Service-SID, ACLs and “writerestricted token” to isolate services Supply network firewall rules

User Account Control Motivation Everybody runs as an administrator on XP There is tremendous security benefit to running as a “Standard User” Most software doesn’t need Administrator privileges to run

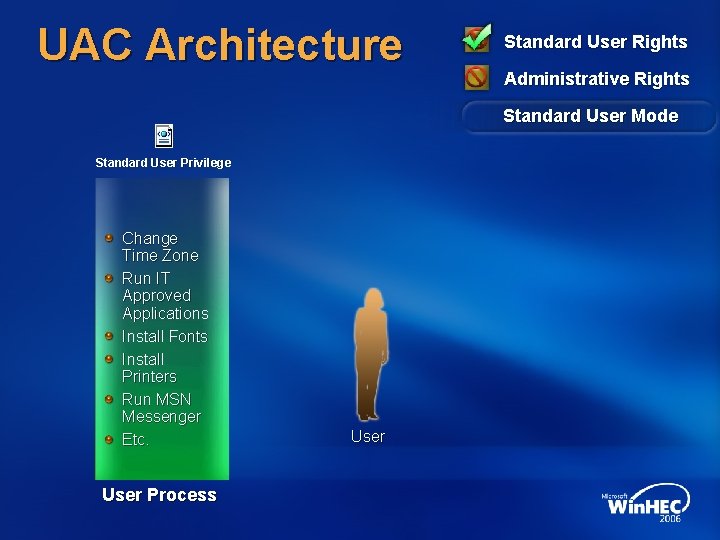
Windows Vista UAC goals All users run as Standard User by default Filtered token created during logon Only specially marked apps get the unfiltered token Explicit consent required for elevation Predictable shell elevation paths High application compatibility Data redirection Enabling legacy apps to run as standard user Installer Detection

UAC Architecture Standard User Rights Administrative Rights Admin logon Abby Admin Token “Standard User” Token

UAC Architecture Standard User Rights Administrative Rights Standard User Mode Standard User Privilege Change Time Zone Run IT Approved Applications Install Fonts Install Printers Run MSN Messenger Etc. User Process User

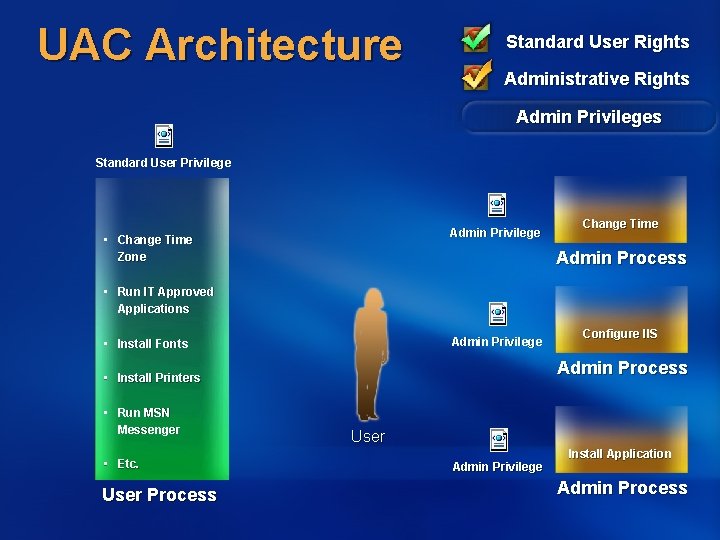
UAC Architecture Standard User Rights Administrative Rights Admin Privileges Standard User Privilege Admin Privilege • Change Time Zone Change Time Admin Process • Run IT Approved Applications Admin Privilege • Install Fonts Admin Process • Install Printers • Run MSN Messenger • Etc. User Process Configure IIS User Admin Privilege Install Application Admin Process

Guidance For Application Developers Installation Best Practices Use MSI 3. 1 for Install and Update Alternate to MSI 3. 1 – call Update. exe marked as admin to do the update Self Updating Code – Don’t Do It! This is our largest App Compat problem Home consumer user applications Examples of what not to do Do not assume the user is an administrator Run Custom Actions in right context! Click. Once is a great deployment technology for Standard User apps

Guidance For Developers Application Data Best Practices Your apps per user setup is performed at first run Place per-user data into %LOCALAPPDATA% Roaming into %APPDATA% Place Per-Machine (Shared) data into %ALLUSERPROFILE% Examples of what not to do Do not perform admin configuration at first run Do your admin operations during setup Do not perform explicit Admin checks for Standard User applications UAC and Code Access Security (CAS) can be used together for defense in depth

User Account Control In Windows Vista Chris Corio Program Manager Windows Security

Call To Action Ensure that your device and driver work on ALL 64 -bit enable Windows operating systems Test your applications soon; understand the difference that UAC will make

Additional Resources CNG API documentation – currently only available with signed NDA and EULA Smart Card Subsystem Base CSP and Card Module specifications have been published to over 20 card vendors – ask if your card vendor has a card module Card module developer kit including card module spec, Base CSP binary, test suite, etc. is currently only available with signed NDA and EULA Card module developer information will be made public via MSDN in the coming months A whitepaper on the new smart card infrastructure will be released at the same time as the Base CSP Windows Service Hardening Email: wsh @ microsoft. com User Account Control Getting Started with UAC: http: //www. microsoft. com/technet/windowsvista/ evaluate/feat/uaprot. mspx UAC Developer Guidelines: http: //msdn. microsoft. com/library/default. asp? url=/ library/en-us/dnlong/html/Acc. Prot. Vista. asp UAC Blog: http: //blogs. msdn. com/uac

Additional Resources Kernel Mode Code Signing White paper titled “Digital Signatures for Kernel Modules on x 64 -based Systems Running Windows Vista” http: //www. microsoft. com/whdc/system/ platform/64 bit/kmsigning. mspx 64 -bit and kernel mode http: //www. microsoft. com/whdc/ driver/kernel/64 bit_chklist. mspx Vista Logo requirements http: //www. microsoft. com/whdc/ winlogo/hwrequirements. mspx

© 2006 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
