Session Code ARC 343 Introducing the Longhorn Identity
















- Slides: 33

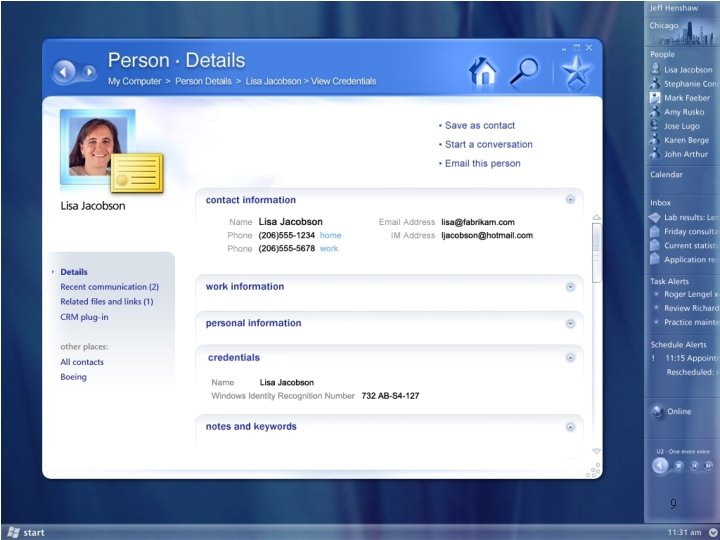
Session Code: ARC 343 Introducing the “Longhorn” Identity System Stuart Kwan (skwan@microsoft. com) Product Unit Manager Microsoft Corporation 1

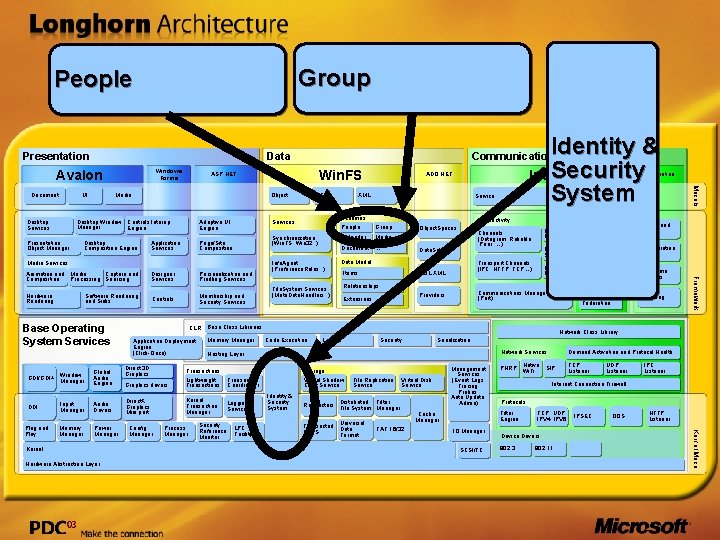
Group People Presentation Data Windows Forms Avalon UI Object Media Desktop Window Controls Interop Manager Engine Desktop Services Adaptive UI Engine Designer Services Personalization and Profiling Services Hardware Rendering Controls Membership and Security Services Media Services Software Rendering and Sinks Base Operating System Services GDI/GDI+ DDI Input Manager Memory Manager Global Audio Engine Audio Drivers Power Manager Kernel Hardware Abstraction Layer Direct 3 D Graphics Direct. X Graphics Mini port Config Manager Group Calendar Media Document … Memory Manager Data. Set Data Model Transport Channels (IPC, HTTP, TCP…) SQL XML Items Relationships Channel Security Eventing Message Encoder Routing Security Reference Monitor LPC Facility Collaboration History System Services Transaction Real-Time Activities Signaling Federation Network Class Library Code Execution Loader Security Serialization Demand Activation and Protocol Health Network Services Storage Virtual Shadow Copy Service Transaction Coordinator Logging Service People and Groups Queuing Communications Manager (Port) Providers Extensions Policy Engine Channels (Datagram, Reliable, Peer, …) Hosting Layer Kernel Transaction Manager Messaging Services Connectivity Object. Spaces Base Class Libraries Lightweight Transactions Process Manager Schemas People File. System Services (Meta. Data. Handlers. . ) Transactions Graphics drivers Service Identity & Security System File Replication Service Virtual Disk Service Filter Redirectors Distributed File System Manager Transacted NTFS Universal Data Format FAT 16/32 Management Services (Event Logs, Tracing, Probes, Auto Update, Admin) PNRP IO Manager SCSI/FC TCP Listener UDP Listener IPC Listener Internet Connection Firewall Protocols Filter Engine Cache Manager Native SIP Wi. Fi TCP, UDP IPV 4, IPV 6 IPSEC Device Drivers 802. 3 802. 11 . . QOS HTTP Listener Kernel Mode Plug and Play Window Manager CLR Application Deployment Engine (Click-Once) Info. Agent (Preference. Rules. . ) Collaboration Framework Animation and Media Capture and Composition Processing Sourcing ADO. NET XML Synchronization (Win. FS, Win 32. . ) Page/Site Composition Desktop Composition Engine T/SQL Services Application Services Presentation Object Manager Win. FS ASP. NET Models Document Identity & Security Indigo System Communication

Agenda A taxonomy of digital interactions The “Longhorn” Identity System “Information Cards” Usage scenarios Summary and call to action 3

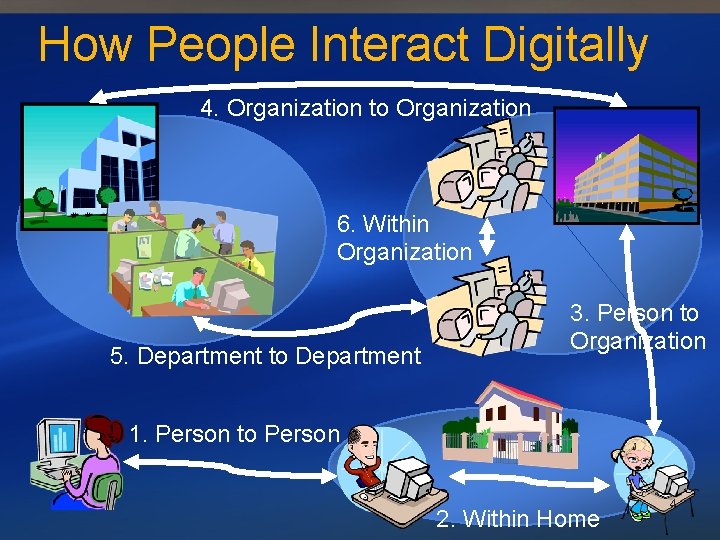
How People Interact Digitally 4. Organization to Organization 6. Within Organization 5. Department to Department 3. Person to Organization 1. Person to Person 2. Within Home 4

Common Challenges 1. Name resolution Addresses are dynamic DNS namespace is global but not universally updateable and sometimes disjoint 2. Intentional connectivity barriers Organizations behind firewalls Home networks behind NATs and firewalls 3. Recognizing identities outside your system To enable secure communication To grant access to your stuff 5

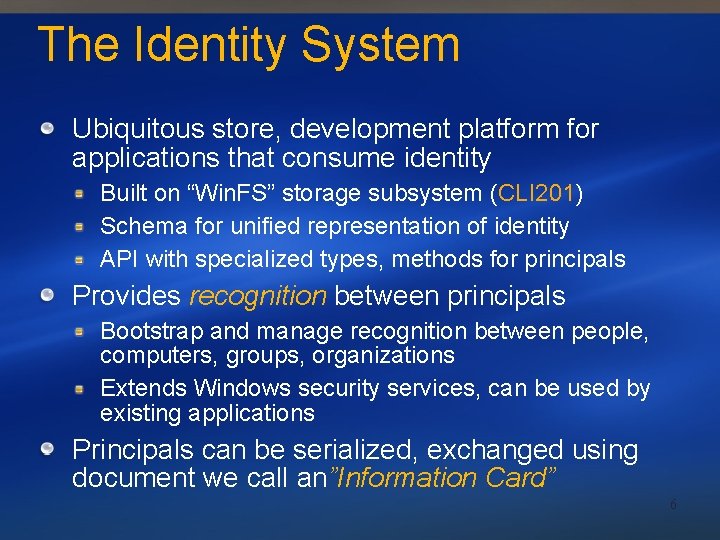
The Identity System Ubiquitous store, development platform for applications that consume identity Built on “Win. FS” storage subsystem (CLI 201) Schema for unified representation of identity API with specialized types, methods for principals Provides recognition between principals Bootstrap and manage recognition between people, computers, groups, organizations Extends Windows security services, can be used by existing applications Principals can be serialized, exchanged using document we call an”Information Card” 6

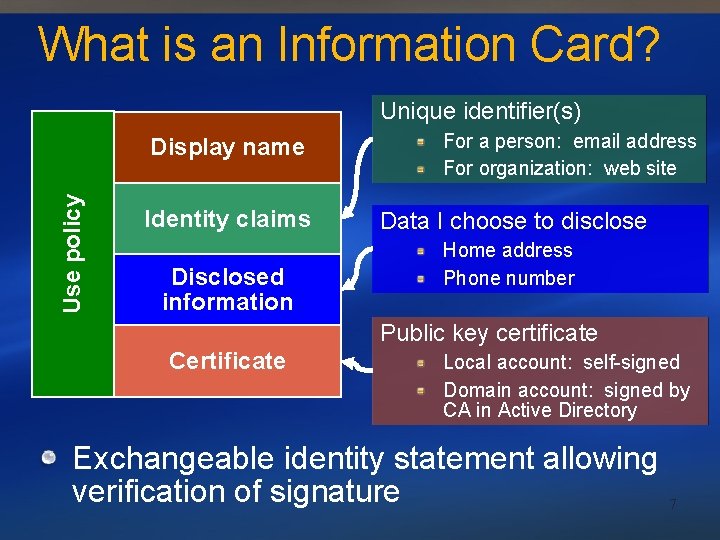
What is an Information Card? Unique identifier(s) Use policy Display name Identity claims Disclosed information For a person: email address For organization: web site Data I choose to disclose Home address Phone number Public key certificate Certificate Local account: self-signed Domain account: signed by CA in Active Directory Exchangeable identity statement allowing verification of signature 7

How Are Information Cards Used? Information Cards are used to manage secure digital relationships with people and organizations When an Information Card is imported, it becomes a contact in the contact explorer Can be recognized using Windows security services (SSPI) Can be granted access to shared spaces Will seek broad adoption of Information Card, encourage others to implement 8

9

Person to Person Scenario Chris Macaulay Program Manager Directory and Identity Services 10

Person to Person Bob’s computer can look up address of Alice’s computer using info from contact Share: File: \alice@example. netpartypictures Name resolution: alice@example. net public key PNRP name IPv 6 address Bob’s computer traverses NAT using IPv 6 For more information: ARC 382 Internet 11

Identity-Based Host Firewall Only people you recognize and to whom granted access can make inbound connections to your computer Other callers see IPSEC negotiation port, nothing else Greatly reduces exposed attack surface of a Windows computer on a network 12

Authentication Versus Authorization Accepting an Information Card does not grant a contact access to the computer Recognition only – clear separation of authentication, authorization A contact must have no implicit access To revoke someone’s access to computer Remove from access policies on resources Optionally, delete contact object, no longer recognize that person 13

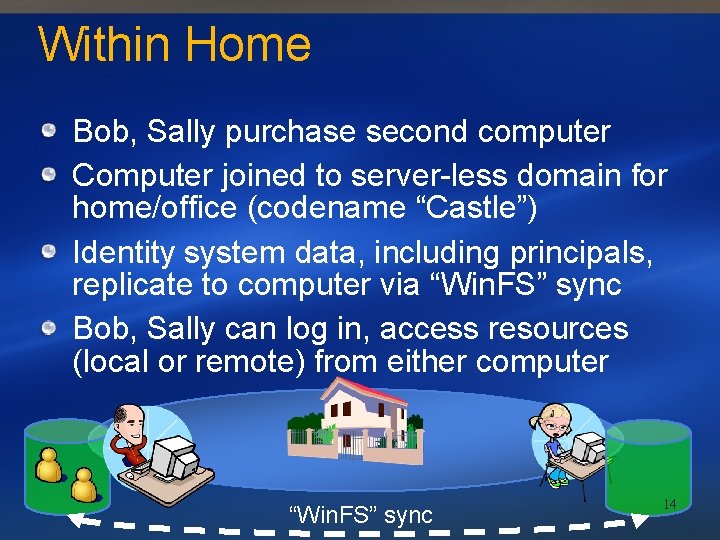
Within Home Bob, Sally purchase second computer Computer joined to server-less domain for home/office (codename “Castle”) Identity system data, including principals, replicate to computer via “Win. FS” sync Bob, Sally can log in, access resources (local or remote) from either computer “Win. FS” sync 14

Within Home Scenario Chris Macaulay Program Manager Directory and Identity Services 15

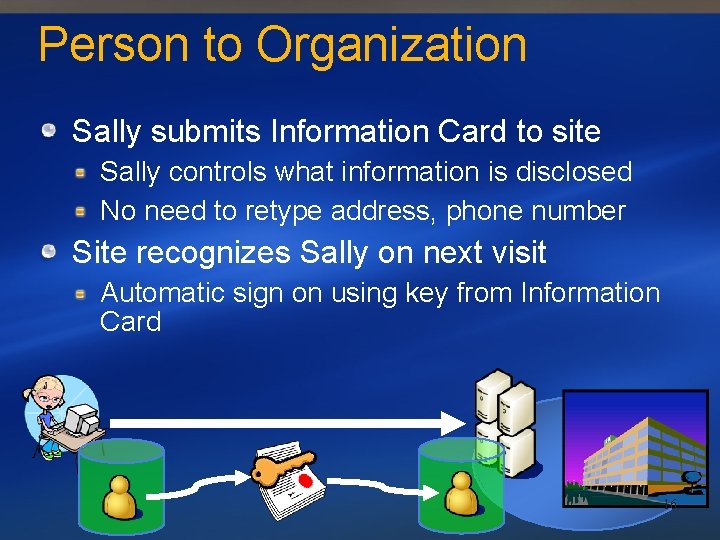
Person to Organization Sally submits Information Card to site Sally controls what information is disclosed No need to retype address, phone number Site recognizes Sally on next visit Automatic sign on using key from Information Card 16

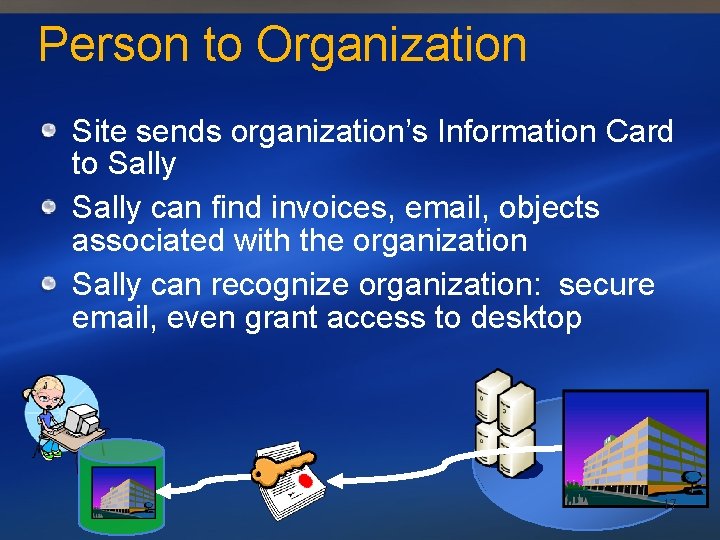
Person to Organization Site sends organization’s Information Card to Sally can find invoices, email, objects associated with the organization Sally can recognize organization: secure email, even grant access to desktop 17

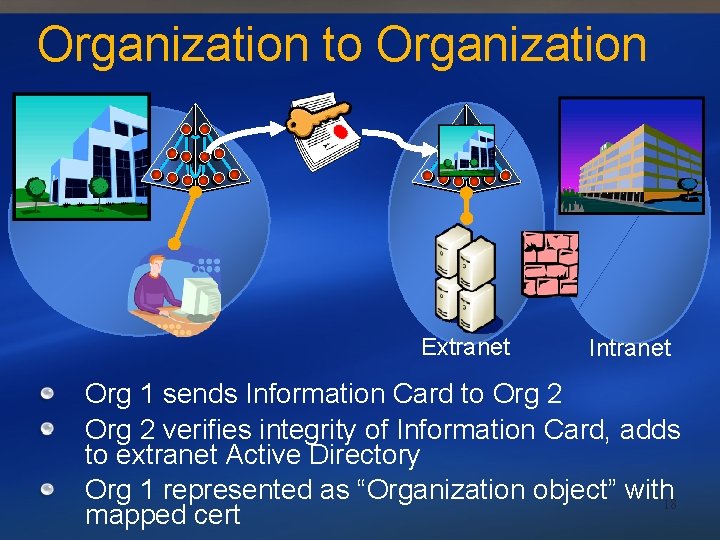
Organization to Organization Extranet Intranet Org 1 sends Information Card to Org 2 verifies integrity of Information Card, adds to extranet Active Directory Org 1 represented as “Organization object” with 18 mapped cert

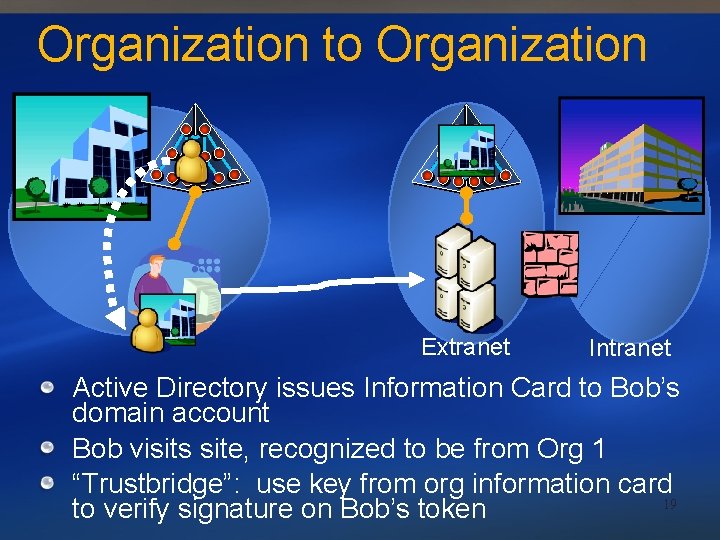
Organization to Organization Extranet Intranet Active Directory issues Information Card to Bob’s domain account Bob visits site, recognized to be from Org 1 “Trustbridge”: use key from org information card 19 to verify signature on Bob’s token

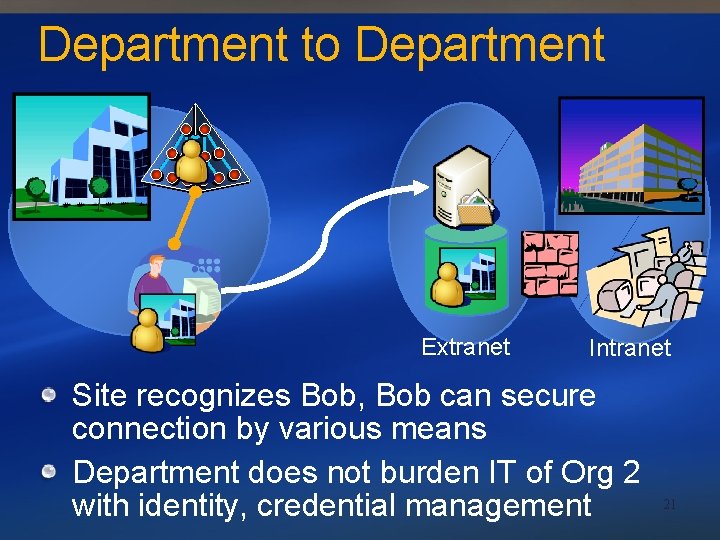
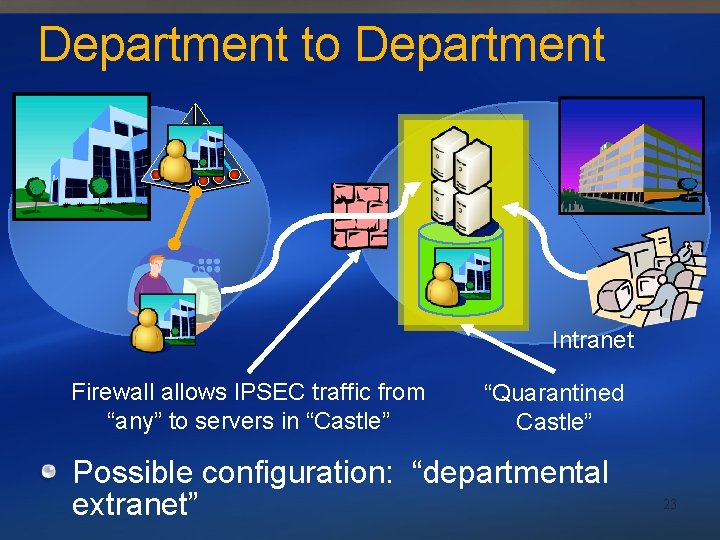
Department to Department Extranet Intranet Bob submits Information Card to extranet site owned by department in Org 2 Similar to person to organization 20

Department to Department Extranet Intranet Site recognizes Bob, Bob can secure connection by various means Department does not burden IT of Org 2 with identity, credential management 21

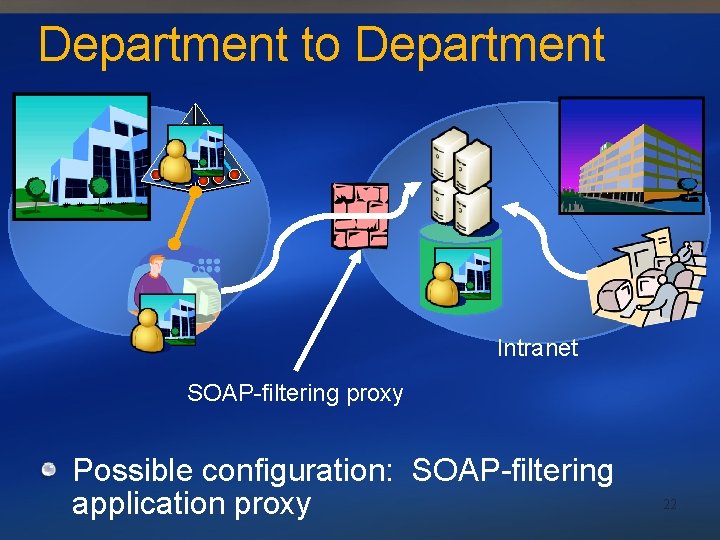
Department to Department Intranet SOAP-filtering proxy Possible configuration: SOAP-filtering application proxy 22

Department to Department Intranet Firewall allows IPSEC traffic from “any” to servers in “Castle” “Quarantined Castle” Possible configuration: “departmental extranet” 23

Tracking Disclosed Information Identity system tracks Information Card disclosure To whom Information Cards were sent What information was sent If information changes, can selectively or automatically send updates Updates signed thus known to be from you, can process automatically at destination For example: your mailing address changes – automatically update magazine subscriptions 24

Roaming Within home: “Castle” replicates data Within organization Credentials, data stored in Active Directory Download to Identity System on clients To arbitrary other computers Identity system data can be backed up, encrypted, and stored in vault in “cloud” Can also use combination smartcard storage “dongle” for any of the above 25

Identity Loss and Recovery What happens if your computer dies? If a “Castle”, data is on other computer(s) Or, restore from system backup Mechanisms used for roaming can also apply to recovery Upload from smart dongle Download from vault in cloud or from Active Directory 26

Identity Theft What if computer, smart dongle is stolen? Send signed revocation message to people you have sent an Information Card If backup in cloud vault, service could send revocation for you, like canceling credit card Bootstrap replacement identity using disclosure information from backup How know if identity has been stolen? How discover this today? For example, by checking credit card statement May need similar mechanisms online 27

Programming Model Contacts and principals integral part of Win. FS API, allowing reuse of skills Fully integrated with system controls Identity is first class concept in “Longhorn” Check out CLI 310 “People and Group Controls” (repeats Wednesday morning) Supports secure communication in “Indigo” Check out ARC 241 on federated web services and “Trustbridge” 28

Call to Action Think about how new digital interaction scenarios will impact your applications Simulate/experiment using Active Directory Build applications that use Windows integrated authentication (SSPI, NEGO) Check out walkthroughs and code samples with “Longhorn” PDC build 29

Summary Consolidated store and platform for applications that consume identity Exchange identity with Information Card, control disclosure, create secure relationships Concepts span continuum from person-to-person to organization-to-organization Longhorn provides solutions to all three common challenges of digital interaction Name resolution Connectivity barriers Recognizing identities from outside your system 30

Community Resources See Identity System team at the Pavilion Ask The Experts tonight 7 -9 pm Hall G, H Attend the Collaboration panel (PNL 11) PDC Weblogs: http: //pdcbloggers. net Newsgroup: microsoft. private. identitysystem username=identity, password=identity 31

© 2003 -2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary. 32

33