Security Overview Trends Rafal Lukawiecki Strategic Consultant Project

































- Slides: 42

Security Overview: Trends Rafal Lukawiecki Strategic Consultant Project Botticelli Ltd rafal@projectbotticelli. co. uk

2 Objectives Overview a process-oriented approach to security Discuss the recent trends in approaching security issues

3 Session Agenda Frameworks, Processes and Concepts Issues Trends

4 The Problem We have (more than enough) security technologies, but we do not know how (and if) we are secure

5 Security Frameworks

6 Security Definition (Cambridge Dictionary of English) Ability to avoid being harmed by any risk, danger or threat …therefore, in practice, an impossible goal What can we do then? Be as secure as needed Ability to avoid being harmed too much by reasonably predictable risks, dangers or threats (Rafal’s Definition)

7 Adequate Security CERT usefully suggests: “A desired enterprise security state is the condition where the protection strategies for an organization's critical assets and business processes are commensurate with the organization's risk appetite and risk tolerances. ” – www. cert. org/governance/adequate. html Risk Appetite – defined through executive decision, influences amount of risk worth taking to achieve enterprise goals and missions Relates to risks that must be mitigated and managed Risk Tolerance – residual risk accepted Relates to risk for which no mitigation would be in place

8 Approaches for Achieving Security Two approaches are needed: Active, dynamic, transient Implemented through behaviour and pattern analysis Passive, static, pervasive Implemented through cryptography

9 Holistic View of Security should be: Static + Active Across All Your Assets Based On Ongoing Threat Risk Assessment

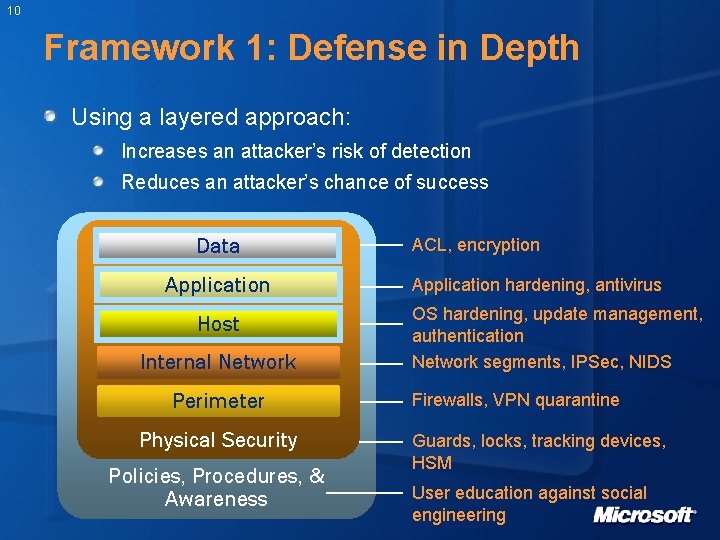
10 Framework 1: Defense in Depth Using a layered approach: Increases an attacker’s risk of detection Reduces an attacker’s chance of success Data Application Host Internal Network Perimeter Physical Security Policies, Procedures, & Awareness ACL, encryption Application hardening, antivirus OS hardening, update management, authentication Network segments, IPSec, NIDS Firewalls, VPN quarantine Guards, locks, tracking devices, HSM User education against social engineering

11 Secure Environment A secure environment is a combination of: Hardened hosts (nodes) Intrusion Detection System (IDS) Operating Processes Standard and Emergency Threat Modelling and Analysis Dedicated Responsible Staff Chief Security Officer (CSO) responsible for all Continuous Training Users and security staff – against “social engineering”

12 Framework 2: OCTAVE Operationally Critical Threat, Asset and Vulnerability Evaluation Carnegie-Mellon University guidance Origin in 2001 Used by US military and a growing number of larger organisations www. cert. org/octave

13 Concept of OCTAVE Workshop-based analysis Collaborative approach Guided by an 18 -volume publication Very specific, with suggested timings, personnel selection etc. www. cert. org/octave/omig. html Smaller version, OCTAVE-S, for small and medium organisations www. cert. org/octave/osig. html

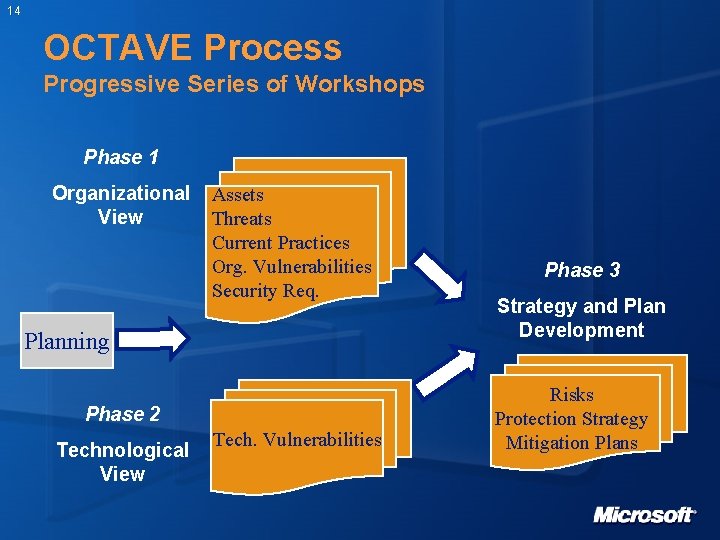
14 OCTAVE Process Progressive Series of Workshops Phase 1 Organizational View Assets Threats Current Practices Org. Vulnerabilities Security Req. Planning Phase 2 Technological View Tech. Vulnerabilities Phase 3 Strategy and Plan Development Risks Protection Strategy Mitigation Plans

15 Framework 3: Security Risk Analysis A simplified approach, taking into account your assets exposure to security risks Requires: 1. Identifying your assets 2. Assesing risks and their impact, probability and exposure 3. Formulating plans to reduce overall risk exposure

16 Risk Impact Assessment For each asset and risk attach a measure of impact Monetary scale if possible (difficult) or relative numbers with agreed meaning E. g. : Trivial (1), Low (2), Medium (3), High (4), Catastrophic (5) Ex: Asset: Internal MD mailbox Risk: Access to content by press Impact: Catastrophic (5)

17 Risk Probability Assessment Now for each entry measure probability the loss may happen Real probabilities (difficult) or a relative scale (easier) such as: Low (0. 3), Medium, (0. 6), and High (0. 9) Ex: Asset: Internal MD mailbox Risk: Access to content by press Probability: Low (0. 3)

18 Risk Exposure and Risk List Multiply probability by impact for each entry Exposure = Probability x Impact Sort by exposure High-exposure risks need very strong security measures Lowest-exposure risks can be covered by default mechanisms or ignored Example: Press may access MD mailbox: Exposure = P(Low=0. 3) x I(Catastrophic=5) = 1. 5 By the way, minimum exposure is 0. 3 and maximum is 4. 5 is our examples

19 Mitigation and Contingency For high-exposure risks plan: Mitigation: Reduce its probability or impact (so exposure) Transfer: Make someone else responsible for the risk Avoidance: avoid the risk by not having the asset Contingency: what to do if the risk becomes reality

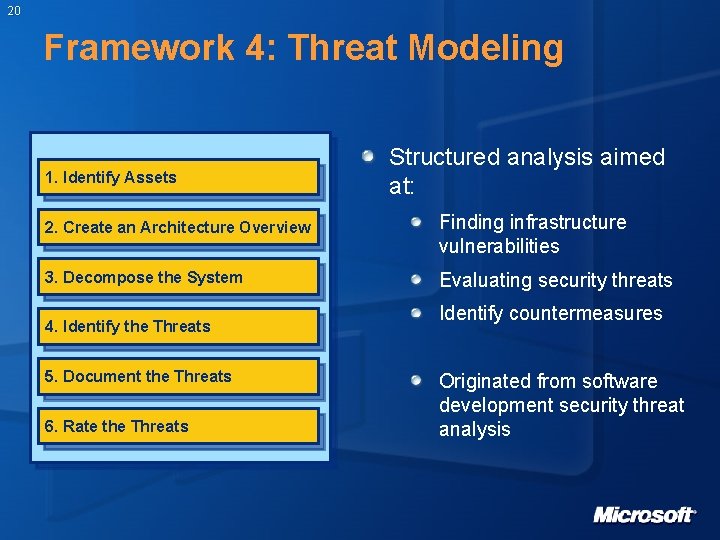
20 Framework 4: Threat Modeling 1. Identify Assets Structured analysis aimed at: 2. Create an Architecture Overview Finding infrastructure vulnerabilities 3. Decompose the System Evaluating security threats 4. Identify the Threats 5. Document the Threats 6. Rate the Threats Identify countermeasures Originated from software development security threat analysis

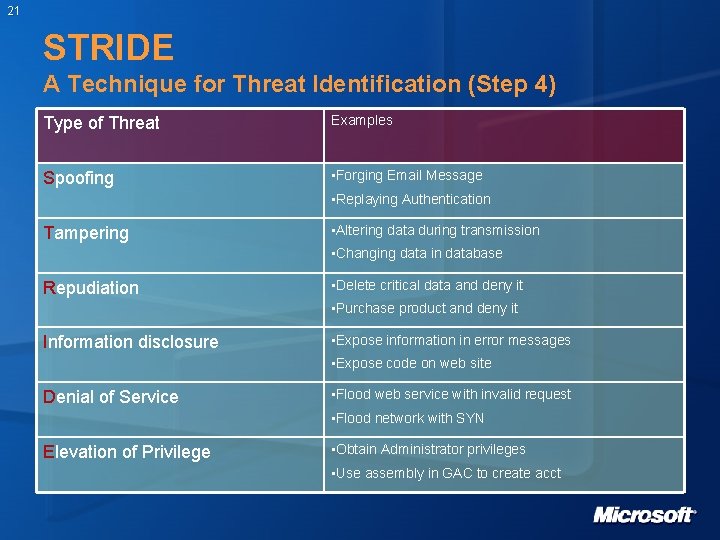
21 STRIDE A Technique for Threat Identification (Step 4) Type of Threat Examples Spoofing • Forging Email Message • Replaying Authentication Tampering • Altering data during transmission • Changing data in database Repudiation • Delete critical data and deny it • Purchase product and deny it Information disclosure • Expose information in error messages • Expose code on web site Denial of Service • Flood web service with invalid request • Flood network with SYN Elevation of Privilege • Obtain Administrator privileges • Use assembly in GAC to create acct

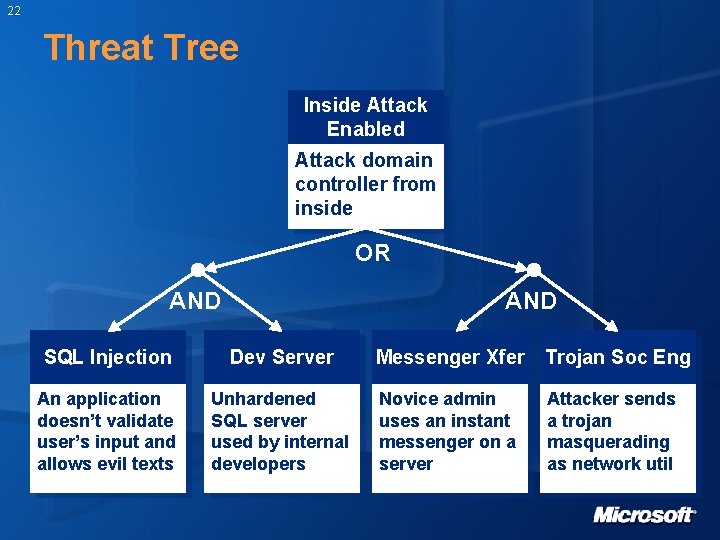
22 Threat Tree Inside Attack Enabled Attack domain controller from inside OR AND SQL Injection Dev Server Messenger Xfer Trojan Soc Eng An application doesn’t validate user’s input and allows evil texts Unhardened SQL server used by internal developers Novice admin uses an instant messenger on a server Attacker sends a trojan masquerading as network util

23 Current Security Issues

24 Industry Issues for 2005 -2006 Without undue generalisation: Mobile security at data layer Malware/spyware Compliance auditing Identity management Patch/update management Application defence Intrusion detection

25 Mobile Security at Data Layer Laptops and PDAs are rarely protected against physical data extraction Encryption with removable keys is very effective, though deployment requires planning and is sometimes cumbersome Smartcards plus EFS or an alternative system, such as PGP etc. can be applied Data recovery needs (legal and practical) complicate the matter greatly

26 Spyware (Malware) Protection 90% machines have malicious software, on average 28 separate spyware programs (report by Earthlink & Webroot) Zombies Network bandwidth and CPU degradation Commercial secrets leaked Privacy destroyed 3 rd party liability arises Best practice: Spy. Bot Search and Destroy (www. spybot. info) Microsoft Anti. Spyware (in beta) Ad. Aware Limit use of administrative privileges for end-users

27 Compliance Auditing An area of rapid growth, primarily due to Sarbannes/Oxley (“Sarbox”, or “Sox”) and EU Data Privacy regulation In hands of specialised providers, mainly consulting business Microsoft Operations Manager (MOM) can be applied for this purpose

28 Identity Management Heterogeneity of authentication and security measures is a common fact Don’t fight it, integrate it Synchronisation between directories, no matter how different, is becoming a reality with solutions build on systems such as MIIS (Identity Integration Server) Alternatively, converge onto a client-solution, such as smartcards or OTP/tokens

29 Patch and Update Management As of Sept 2005, Microsoft Update is fully functioning, and integrates, at present: Windows OS updates Office SQL Server Exchange More Microsoft products being added over the next months Enterprise solutions, however, will still benefit from a fully -managed software distribution system, such as SMS (Systems Management Server)

30 Application Defence As networks and hosts become well protected, application-level attacks are on the increase Other than for very new in-house applications, development security has rarely been a concern This is a major area of worry from both perspectives of an insider and outside attacks Approaches: Prove it’s safe (threat modelling) Isolate-and-monitor Replace

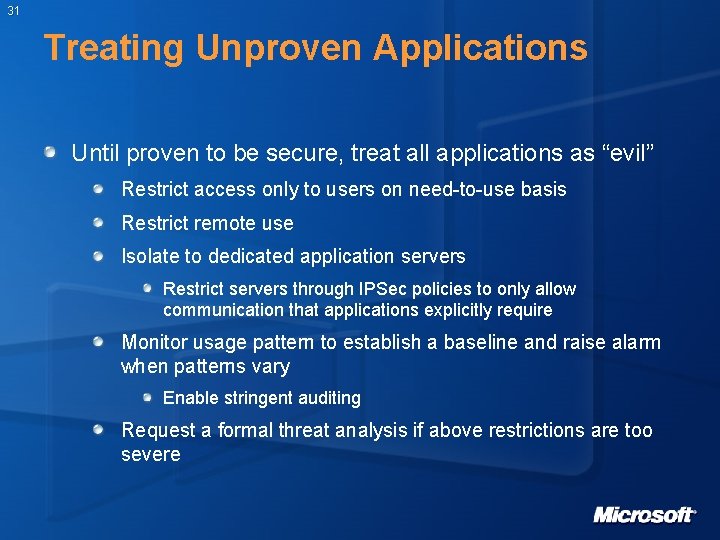
31 Treating Unproven Applications Until proven to be secure, treat all applications as “evil” Restrict access only to users on need-to-use basis Restrict remote use Isolate to dedicated application servers Restrict servers through IPSec policies to only allow communication that applications explicitly require Monitor usage pattern to establish a baseline and raise alarm when patterns vary Enable stringent auditing Request a formal threat analysis if above restrictions are too severe

32 Intrusion Detection Systems (IDS) are still fairly basic, though sophistication grew at networklevel detection Honeypots, i. e. monitored vulnerable servers exposed as “bait” are still very effective, though may pose legal problems

33 Trends for 2006

34 Network Security – IPv 6 A major development for 2006+ will be gradual replacement of IPv 4 with IPv 6 Amongst many benefits of this move, a crucial introduction of compulsory IPSec 6 will provide much needed authentication and confidentiality of data at wirelevel Interesting issues still remain to be solved, but now is a very good time to seriously evaluate the technology Windows Vista comes with a new IPv 6 stack, as part of the entirely rewritten TCP/IP substrate, called “Next Generation TCP/IP”

35 Network Device Port Protection Though long awaited, “ 802. 1 x for wired networks” is off to a confused start, as many basic devices, such as switches, are unlikely to support the technology as expected With new infrastructure this technology might be useful in high-risk areas, especially exposed networks

36 Smartcards While not a new technology, Microsoft’s support in Windows Vista promises a serious approach to solving deployment, manageability and developer issues Infocard specification for developers Alacris acquisition (20 Sept) for smartcard lifecycle management Axalto deal for smartcard infrastructure Windows Vista re-write of smartcard functionality

37 Biometrics Overhyped: be careful and sceptical Useful as a secondary protection of a private encryption key on a smartcard in a controlled environment Advantage: Simple and works in some environments, e. g. immigration control or secondary authentication of staff Weakness: Not useful for at-home, remote etc. applications as no way to ensure it is your real fingerprint, iris, retina etc. being scanned Biometric data can be stolen and can be used to fake identity – no way to change it later Too many positive and negative false matches

38 Application-level Protection With. NET Framework 2. 0 and SQL Server 2005 developers can use a plethora of security technologies – easily Developers are increasingly seen as responsible for security This extends even to database developers, previously unlikely to engage in cryptography or ACL management It is very important that all in-house and vertical solutionprovider application developers undergo security training Refresher courses or workshops are a good idea Community participation helps

39 Summary

40 Summary Viewing security holistically combines perspectives of people, processes, technologies and requires ongoing research and education Security goals oppose those of usability Frameworks enable achieving security goals without facing unexpected costs Network and host protections are fairly mature Developer-oriented solutions to prevent application-level attacks must be employed

41 © 2005 Project Botticelli Ltd & Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. PROJECT BOTTICELLI AND MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY. You must verify all the information presented before relying on it. E&OE.

Welcome Clare Dillon Developer and Platform Group Microsoft Ireland Clare. Dillon@microsoft. com
 Rafal lukawiecki
Rafal lukawiecki Rafal lukawiecki
Rafal lukawiecki Rafal lukawiecki
Rafal lukawiecki Rafal lukawiecki
Rafal lukawiecki Court security consultant
Court security consultant Palo alto networks certified network security consultant
Palo alto networks certified network security consultant Provate security
Provate security Rafal wietsma
Rafal wietsma Rafal otto
Rafal otto Przemiany metaboliczne
Przemiany metaboliczne Sms 2003
Sms 2003 Current trends in strategic management
Current trends in strategic management Owasp asvs level 2
Owasp asvs level 2 Android security overview
Android security overview Project overview example
Project overview example Sap ps
Sap ps Management topics for project
Management topics for project Strategic fit vs strategic intent
Strategic fit vs strategic intent Strategic substitute
Strategic substitute Strategic management and strategic competitiveness
Strategic management and strategic competitiveness Tows matrix
Tows matrix Current trends in project management
Current trends in project management Modern data architecture consultant
Modern data architecture consultant Consultant mediu
Consultant mediu Claudia norman a marketing consultant
Claudia norman a marketing consultant Judith james educational consultant
Judith james educational consultant Behavioral genetics consultant
Behavioral genetics consultant Rcem consultant sign off
Rcem consultant sign off Open source consultant
Open source consultant Knowledge management consultants
Knowledge management consultants Verizon ip centrex
Verizon ip centrex United states lactation consultant association
United states lactation consultant association Consultant radiographer
Consultant radiographer Call script for recruiter
Call script for recruiter Stuart minty camden planning consultant
Stuart minty camden planning consultant Philips talent acquisition
Philips talent acquisition Nous hospital consultant
Nous hospital consultant Test consultant capgemini
Test consultant capgemini Doing business with fdot
Doing business with fdot Epicor configurator consulting
Epicor configurator consulting Advanced nutraceuticals
Advanced nutraceuticals Temple family history consultant
Temple family history consultant Scan based trading data
Scan based trading data






























































