RSAC SESSION ID TECHR 11 Phish Your Employees































- Slides: 63

#RSAC SESSION ID: TECH-R 11 Phish Your Employees Now or Be Phished! Todd Fitzgerald, CISSP, CISM, CISA, CRISC, CGEIT, CIPP/US/E/C, CIPM, PMP, ISO 27001, ITILv 3 f todd_fitzgerald@yahoo. com @securityfitz

Today's Agenda 1. What Is The Phishing Threat Today? 2. The Phishing Hidden Costs Are Blindsiding! 3. The Changing Nature of Security Awareness Programs 4. CASE STUDY: Phishing Awareness #RSAC

#RSAC 1. What Is The Phishing Threat Today? What is the Phishing Threat Today?

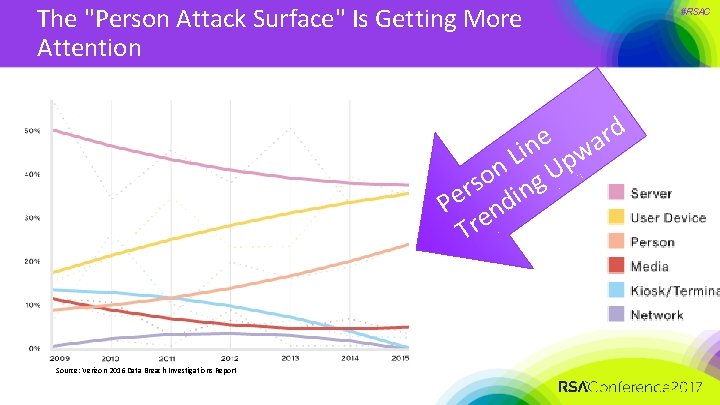
The "Person Attack Surface" Is Getting More Attention d r e a in pw L n U o g s r e P ndin Tre Source: Verizon 2016 Data Breach Investigations Report #RSAC

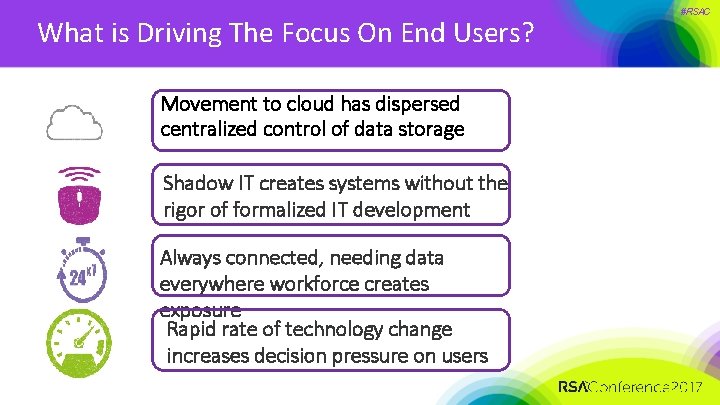
What is Driving The Focus On End Users? Movement to cloud has dispersed centralized control of data storage Shadow IT creates systems without the rigor of formalized IT development Always connected, needing data everywhere workforce creates exposure Rapid rate of technology change increases decision pressure on users #RSAC

#RSAC LET'S GO PHISHING!!!

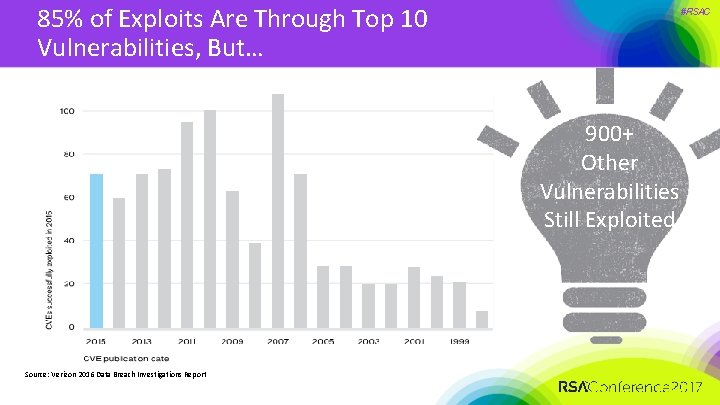
85% of Exploits Are Through Top 10 Vulnerabilities, But… #RSAC 900+ Other Vulnerabilities Still Exploited Source: Verizon 2016 Data Breach Investigations Report

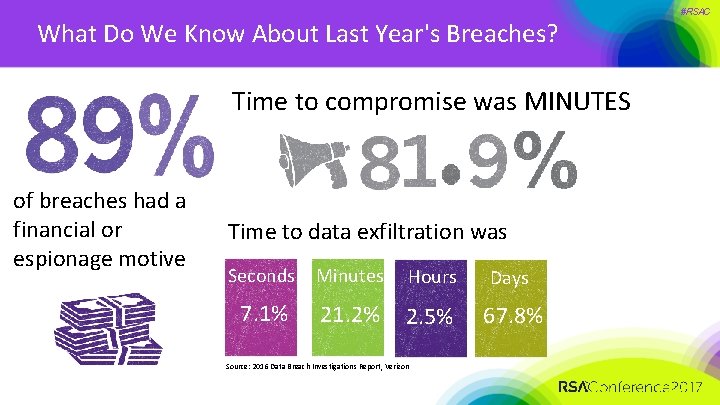
What Do We Know About Last Year's Breaches? Time to compromise was MINUTES of breaches had a financial or espionage motive Time to data exfiltration was Seconds Minutes Hours Days 7. 1% 21. 2% 2. 5% 67. 8% Source: 2016 Data Breach Investigations Report, Verizon #RSAC

Phishing Attempts Are Taking Little Time Phishing Emails Opened by Target Clicked on link or attachment First User Took Only 1 Minute 40 Seconds Source: 2016 Data Breach Investigations Report, Verizon #RSAC

#RSAC ALARMS?

#RSAC 2. The Phishing Hidden Costs Are Blindsiding!

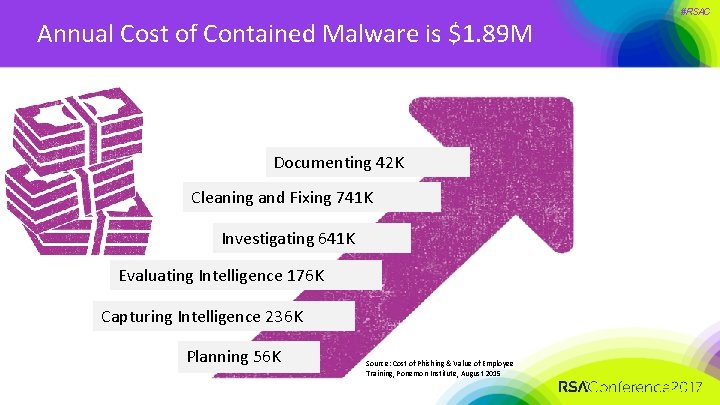
Annual Cost of Contained Malware is $1. 89 M Documenting 42 K Cleaning and Fixing 741 K Investigating 641 K Evaluating Intelligence 176 K Capturing Intelligence 236 K Planning 56 K Source: Cost of Phishing & Value of Employee Training, Ponemon Institute, August 2015 #RSAC

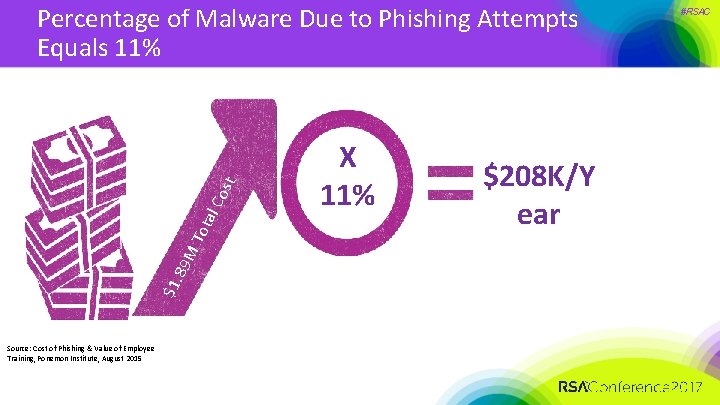
$1. 89 M Tot al C ost Percentage of Malware Due to Phishing Attempts Equals 11% Source: Cost of Phishing & Value of Employee Training, Ponemon Institute, August 2015 X 11% $208 K/Y ear #RSAC

Total Costs Exceed $3. 77 M/Year for Average Sized Organization Contain Malware $208 K Not Contained $338 K Credential Compromises Not Contained $1 M Source: Cost of Phishing & Value of Employee Training, Ponemon Institute, August 2015 Contain Credential Compromises $382 K Productivity Loss $1. 8 M #RSAC

Improvement By Using Phishing Awareness… Translates Into Cost Savings of $1. 8 M/year or $188. 40/user Source: Cost of Phishing & Value of Employee Training, Ponemon Institute, August 2015 #RSAC

$3. 1 Billion , 1300% Increase since January, 2015, Transfers to 79 Countries, 22 K victims FBI Warning on Email Scams Source: Federal Bureau of Investigation, June 2016 #RSAC

#RSAC Security Awareness Programs Are Changing! 3. The Changing Nature of Security Awareness Programs

The Old Way… #RSAC Slide 1 Password Controls Don’t write passwords down Don’t make pet name, spouses name, SSN, sports team Don’t share them with others Don’t make them less than 8 charachters Don’t keep the same one past 60 days

Slide 47 of 109 Slide 2 Security Myths We have anti-virus software, so we are secure We have a firewall, so we are secure The most serious threats come from the outside Responsbily for security rests with the IT staff Security doesn’t matter, because I backup my data daily #RSAC

#RSAC NO!! Don't Do It!

#RSAC Use Security Themes • • • • Appropriate internet usage • Viruses, malware , spyware • Privacy regulations • Phishing Attacks • Email security • Identity theft Confidentiality, information sensitivity • • Mobile security • Social engineering • Incident response • Out of the office security • Government regulations Cloud file shares PII, PHI Wireless security Laptop security Copyright protections Software licenses Need-to-know access Individual security responsibility Password management Identification badges Physical access Clean desk policy Home network usage

Target Audience Is Shifting, So Must Training Traditionalist Boomer Gen Y Gen X • • • Rote Memorization Extensive Study Classroom Course-based Course‐based learning/Books Power. Point Workshops/Lectures Hands-on Hands‐on Learn thru play/fun Media centric (CDs, video) Mobile/Ipod Web 2. 0, Blogs E-learning/Interactive E‐learning/Interactive Source: securingthehuman. sans. org Security awareness blog 4/21/14 (data by T. Fitzgerald) #RSAC

All Security Frameworks Require Awareness NIST PR. AT Security Awareness Cybersecurity Framework Definition Source: Framework for Improving Critical Infrastructure Cybersecurity, NIST, 2014 #RSAC

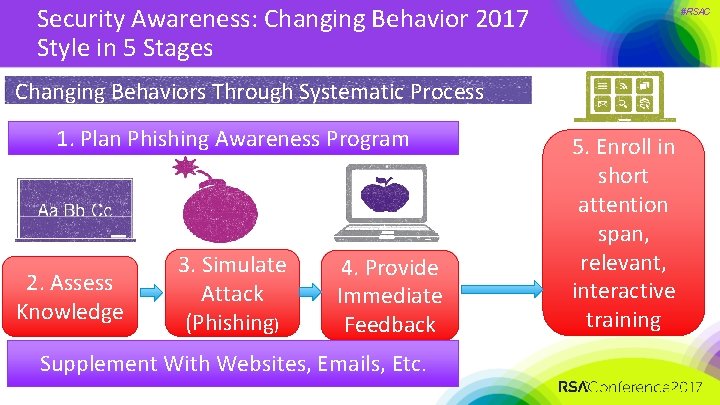
Security Awareness: Changing Behavior 2017 Style in 5 Stages #RSAC Changing Behaviors Through Systematic Process 1. Plan Phishing Awareness Program 2. Assess Knowledge 3. Simulate Attack (Phishing) 4. Provide Immediate Feedback Supplement With Websites, Emails, Etc. 5. Enroll in short attention span, relevant, interactive training

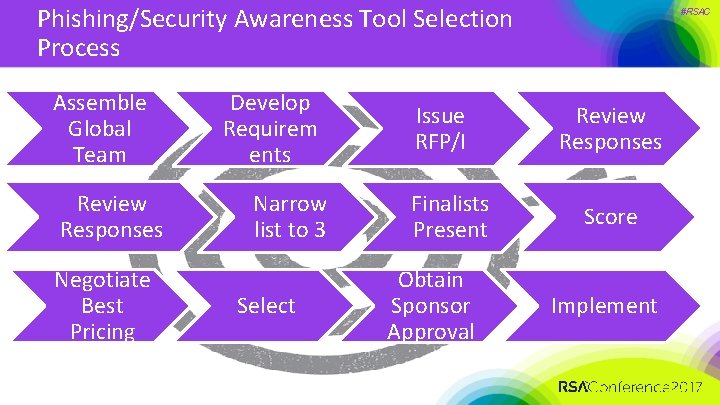
Phishing/Security Awareness Tool Selection Process Assemble Global Team Review Responses Negotiate Best Pricing Develop Requirem ents Narrow list to 3 Select Issue RFP/I Finalists Present Obtain Sponsor Approval #RSAC Review Responses Score Implement

RFP Sample Questions What languages do you support? For training? Administration? How are imports handled? Csv files? AD Synchronization? How are different user groups reported on? What metrics are provided? Are users asked to provide logon/password through clear text? What format options are available for phishing emails? #RSAC

RFP Sample Questions (Cont'd) Can the emails be staggered? What facilities are available for phish‐reporting? Any integration with email client? What training modules are available? Are splash pages available after clicking on link? Are clickers enrolled automatically in training? Can emails be automatically sent to non‐clickers for training? How are mobile devices supported? #RSAC

RFP Sample Questions (There's More) What is the style (fun/professional) of the training? Does the training have to be completed at once? How do domains for phish interact with e‐mail scanning software? Are repeat offenders identified? What reports are available for phishing statistics? Is the device identified? Can the data be exported? Global availability? Where are support centers? #RSAC

#RSAC CASE STUDY: Phishing Simulation & Security Awareness 4. CASE STUDY: Phishing Awareness

Let's Start With The Real Challenge: "Most people operate under the illusion of invulnerability, imagining that they are too smart to be manipulated, conned, deceived or influenced. They believe that stupid things happen only to "stupid" people. " - Kevin Mitnick, The Art of Intrusion #RSAC

Phishing and Human Nature- Shouldn't Surprise Us #RSAC

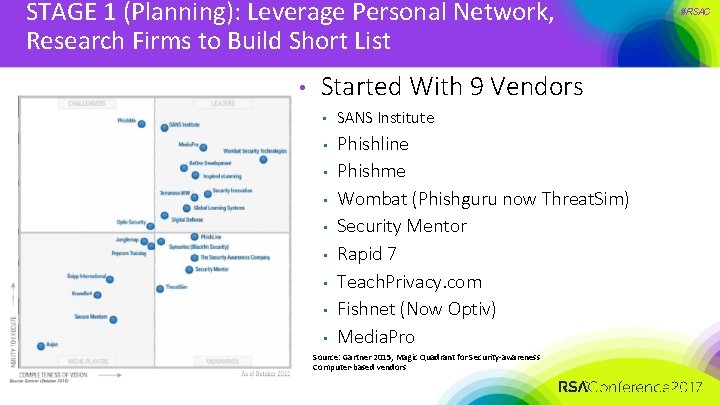
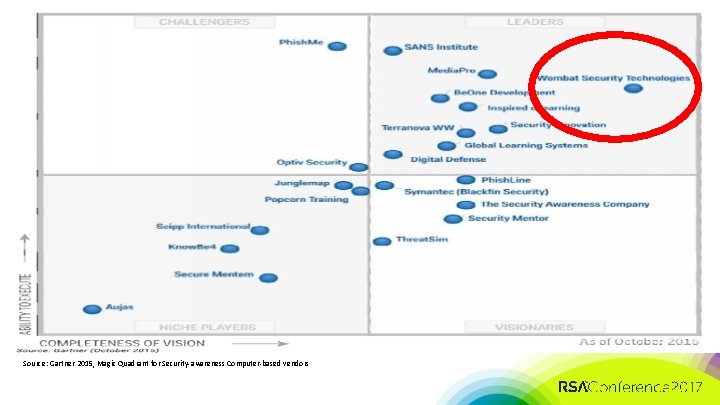
STAGE 1 (Planning): Leverage Personal Network, Research Firms to Build Short List • Started With 9 Vendors • • • SANS Institute Phishline Phishme Wombat (Phishguru now Threat. Sim) Security Mentor Rapid 7 Teach. Privacy. com Fishnet (Now Optiv) Media. Pro Source: Gartner 2015, Magic Quadrant for Security-awareness Computer-based vendors #RSAC

#RSAC Source: Gartner 2015, Magic Quadrant for Security-awareness Computer-based vendors

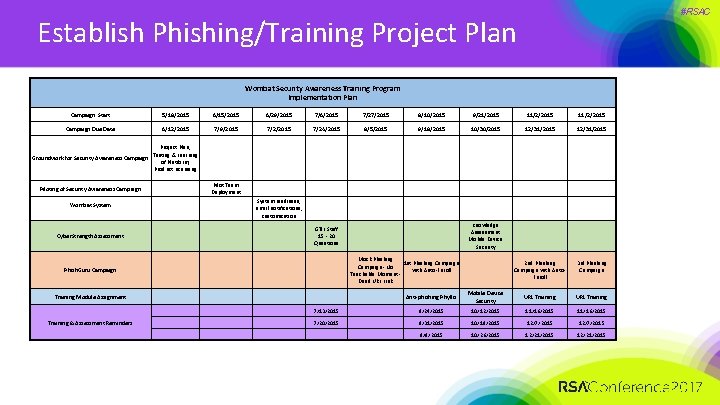
#RSAC Establish Phishing/Training Project Plan Wombat Security Awareness Training Program Implementation Plan Campaign Start 5/18/2015 6/15/2015 6/29/2015 7/6/2015 7/27/2015 8/10/2015 9/21/2015 11/2/2015 Campaign Due Date 6/12/2015 7/9/2015 7/24/2015 8/5/2015 9/18/2015 10/30/2015 12/31/2015 Groundwork for Security Awareness Campaign Project Plan, Testing & Learning of Platform, Product Licensing 2 nd Phishing Campaign with Auto. Enroll 3 rd Phishing Campaign Piloting of Security Awareness Campaign Wombat System Cyber. Strength Assessment Pilot Team Deployment System readiness, email notifications, customization Mock Phishing 1 st Phishing Campaign - No with Auto-Enroll Teachable Moment Dead URL Link Phish. Guru Campaign Anti-phishing Phyllis Mobile Device Security URL Training 7/13/2015 8/24/2015 10/12/2015 11/16/2015 7/20/2015 8/31/2015 10/19/2015 12/7/2015 9/9/2015 10/26/2015 12/21/2015 Training Module Assignment Training & Assessment Reminders Knowledge Assessment Mobile Device Security GTIL Staff 15 - 20 Questions

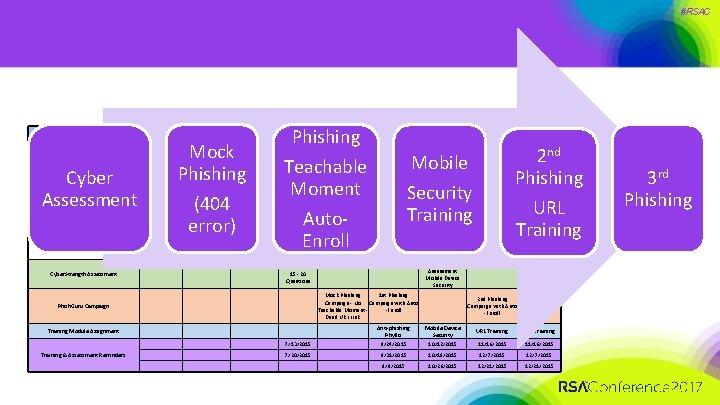
#RSAC Phishing Wombat Security Awareness Training Program Implementation Plan Campaign Start Cyber Assessment 5/18/2015 Mock Phishing Campaign Due Date 6/12/2015 Groundwork for Security Awareness Campaign Project Plan, Testing & Learning of Platform, Product Licensing Piloting of Security Awareness Campaign Wombat System Cyber. Strength Assessment 6/15/2015 6/29/2015 7/2/2015 (404 error) Pilot Team Deployment System readiness, email notifications, customization Teachable Moment Auto. Enroll 7/27/2015 8/10/2015 9/21/2015 11/2/2015 7/24/2015 8/5/2015 9/18/2015 10/30/2015 12/31/2015 2 nd Phishing 11/2/2015 12/31/2015 URL Training Knowledge Assessment Mobile Device Security GTIL Staff 15 - 20 Questions Mock Phishing 1 st Phishing Campaign - No Campaign with Auto Teachable Moment -Enroll Dead URL Link Phish. Guru Campaign 2 nd Phishing Campaign with Auto -Enroll 3 rd Phishing Campaign Anti-phishing Phyllis Mobile Device Security URL Training 7/13/2015 8/24/2015 10/12/2015 11/16/2015 7/20/2015 8/31/2015 10/19/2015 12/7/2015 9/9/2015 10/26/2015 12/21/2015 Training Module Assignment Training & Assessment Reminders Mobile Security Training 7/6/2015 3 rd Phishing

#RSAC Announce The Program INSERT LOGO 30 days in advance Why, What, When, How URL that training is coming from Tie it to home value INSERT LOGO Refer to other materials Also inform executive leadership in advance

#RSAC 30 days in advance WHY Why, What, When, How LOGO URL that INSERT training is coming from Tie it to home value Refer to other. WHEN materials Also inform executive leadership in advance WHAT HOW WHERE

Stage 2 (Assess Knowledge): Send Out Link INSERT LOGO Refer to Program Announcement Take away "failing fear" Ask not to share Provide reasons for training Provide reporting avenue for suspicious emails #RSAC

INSERT LOGO #RSAC

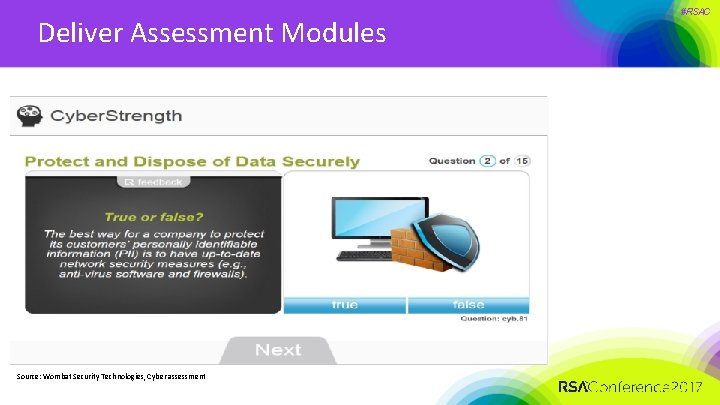
Deliver Assessment Modules Source: Wombat Security Technologies, Cyber assessment #RSAC

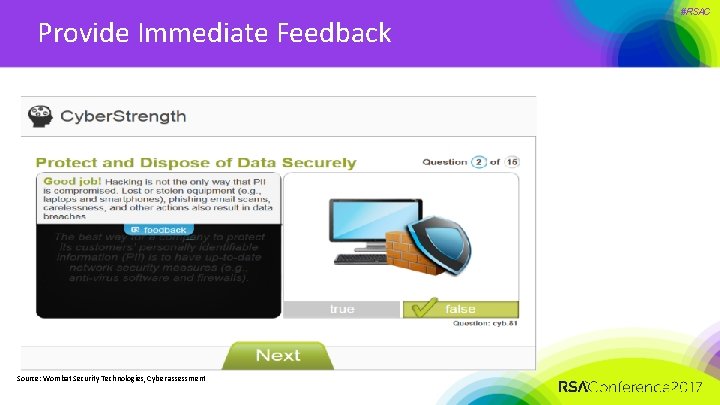
Provide Immediate Feedback Source: Wombat Security Technologies, Cyber assessment #RSAC

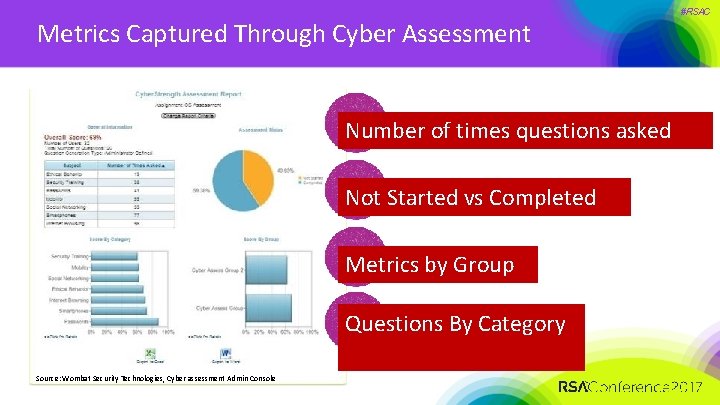
Metrics Captured Through Cyber Assessment Number of times questions asked Not Started vs Completed Metrics by Group Questions By Category Source: Wombat Security Technologies, Cyber assessment Admin Console #RSAC

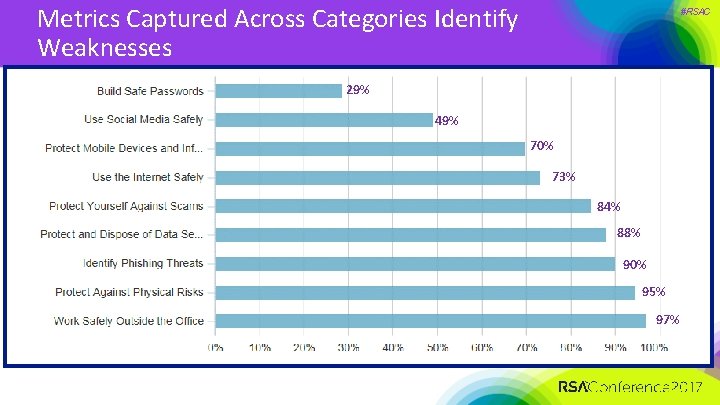
Metrics Captured Across Categories Identify Weaknesses #RSAC 29% 49% 70% 73% 84% 88% 90% 95% 97%

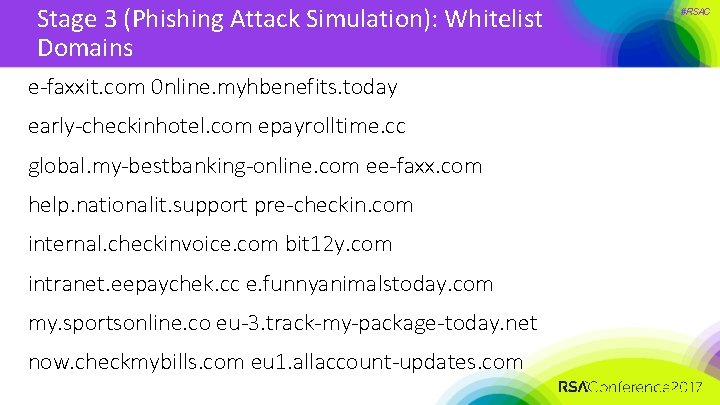
Stage 3 (Phishing Attack Simulation): Whitelist Domains e‐faxxit. com 0 nline. myhbenefits. today early‐checkinhotel. com epayrolltime. cc global. my‐bestbanking‐online. com ee‐faxx. com help. nationalit. support pre‐checkin. com internal. checkinvoice. com bit 12 y. com intranet. eepaychek. cc e. funnyanimalstoday. com my. sportsonline. co eu‐ 3. track‐my‐package‐today. net now. checkmybills. com eu 1. allaccount‐updates. com #RSAC

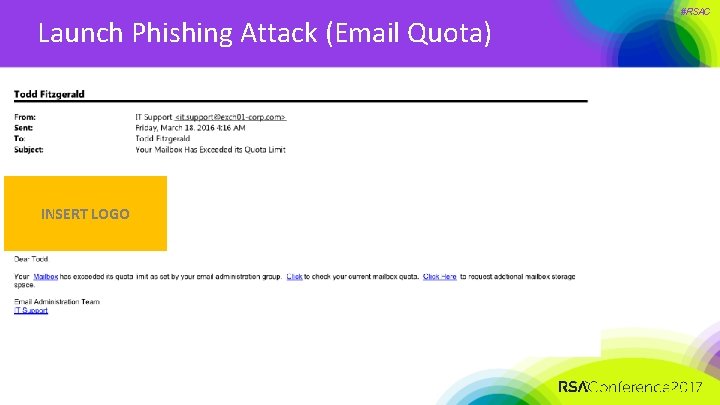
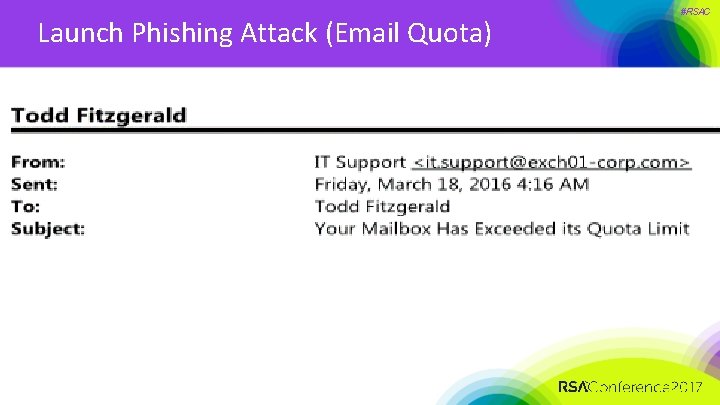
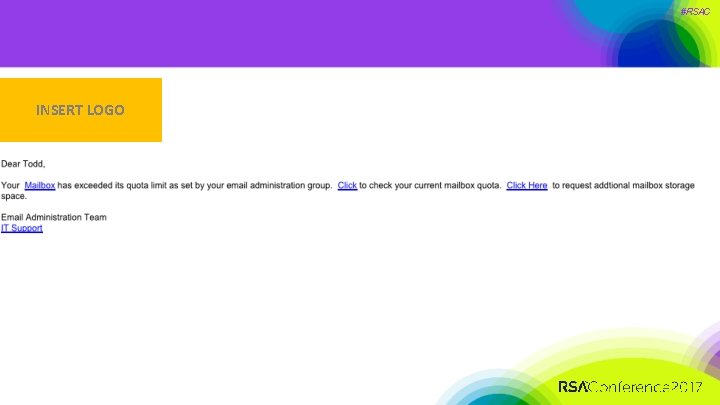
Launch Phishing Attack (Email Quota) INSERT LOGO #RSAC

Launch Phishing Attack (Email Quota) #RSAC

#RSAC INSERT LOGO

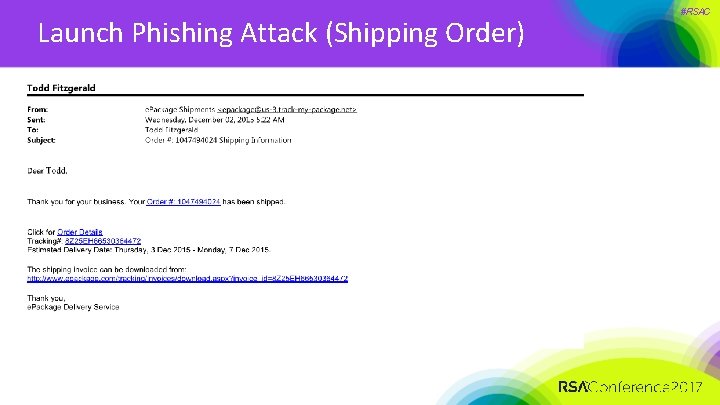
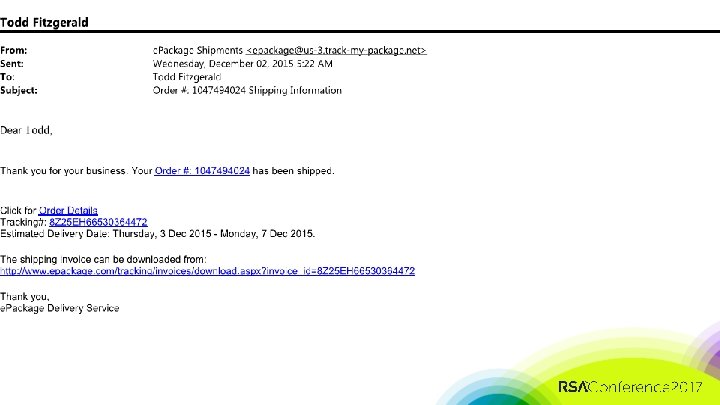
Launch Phishing Attack (Shipping Order) #RSAC

#RSAC Launch Phishing Attack (Shipping Order)

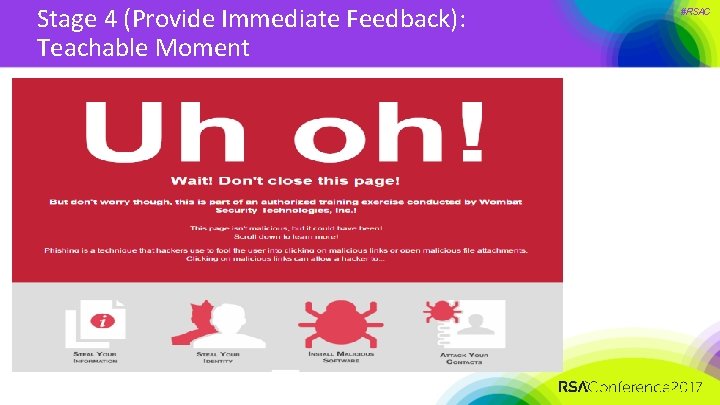
Stage 4 (Provide Immediate Feedback): Teachable Moment #RSAC

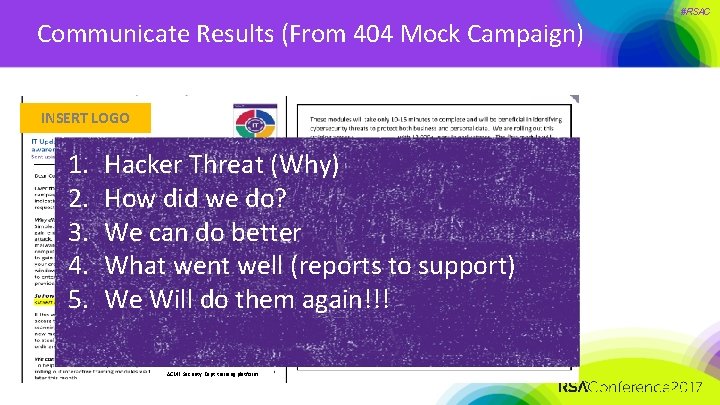
Communicate Results (From 404 Mock Campaign) INSERT LOGO 1. 2. 3. 4. 5. Hacker Threat (Why) How did we do? We can do better What went well (reports to support) We Will do them again!!! ACME Security Dept training platform #RSAC

Stage 5 (Enroll): Interactive 10 -15 minute Training Modules INSERT LOGO ACME Security Dept #RSAC

Thank and Enroll Non-Clickers Also INSERT LOGO ACME Security Training #RSAC

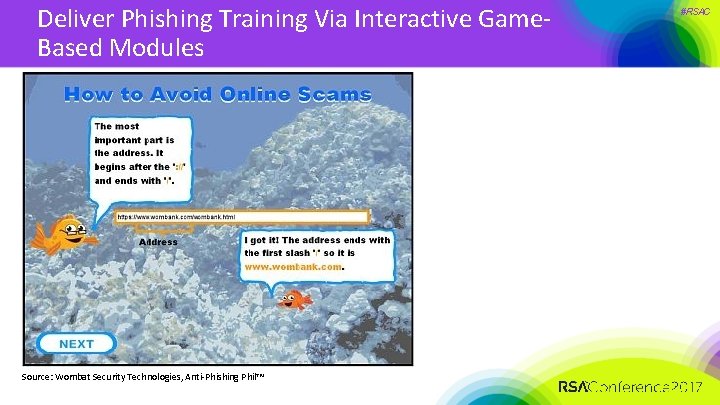
Deliver Phishing Training Via Interactive Game. Based Modules Source: Wombat Security Technologies, Anti-Phishing Phil™ #RSAC

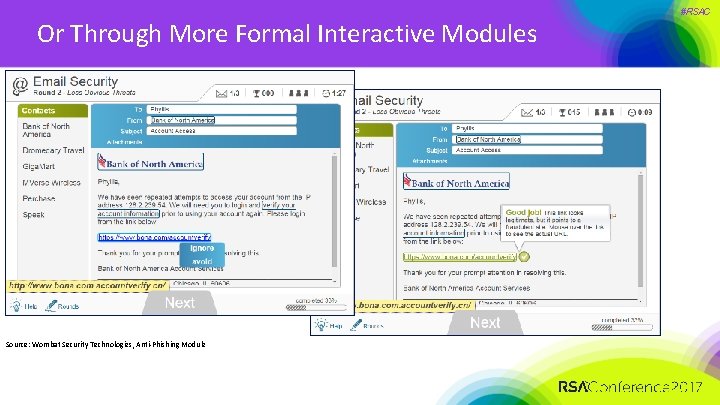
Or Through More Formal Interactive Modules Source: Wombat Security Technologies, Anti-Phishing Module #RSAC

Thank for Completion of Training INSERT LOGO #RSAC

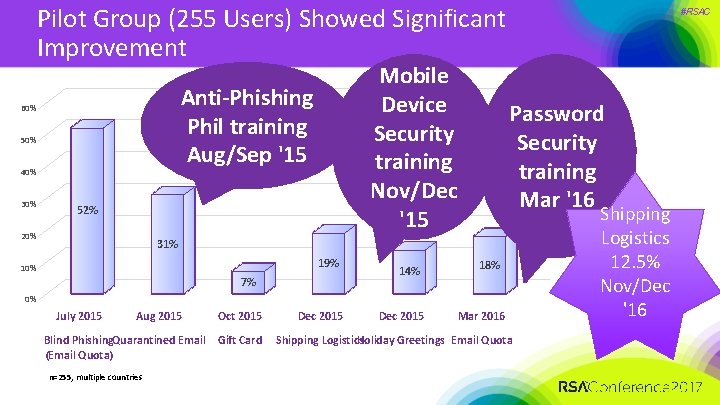
Pilot Group (255 Users) Showed Significant Improvement Anti-Phishing Phil training Aug/Sep '15 60% 50% 40% 30% Mobile Device Security training Nov/Dec '15 52% 20% #RSAC Password Security training Mar '16 31% 19% 10% 7% 14% 18% 0% July 2015 Aug 2015 Blind Phishing. Quarantined Email (Email Quota) n=255, multiple countries Oct 2015 Gift Card Dec 2015 Mar 2016 Shipping Logistics Holiday Greetings Email Quota Shipping Logistics 12. 5% Nov/Dec '16

Let's Not Forget Technical Phishing Controls Email Filtering – before human contact Task‐bar Buttons For Reporting Phish Governing data on endpoints Make pivoting difficult Restrict local admin rights Network segmentation Strong authentication vs static passwords for key assets Monitor outbound traffic Suspicious connections Outbound traffic #RSAC

Today We Explored 1. What Is The Phishing Threat Today? 2. The Phishing Hidden Costs Are Blindsiding! 3. The Changing Nature of Security Awareness Programs 4. CASE STUDY: Phishing Awareness #RSAC

Resources Contributed To By Presenter (Available thru Amazon, Barnes & Noble, ISACA, ISC 2, E-C Council, RSA Bookstore) Since 2004 New Book Coming in 2017 -18 #RSAC

Final Thoughts • Planning and advance communication of Phishing/awareness campaigns is essential • Learning must be behavioral to stick • Employees at every organization level will click • Significant reductions and follow-on willingness to learn will be achieved • Bury the once a year 1 hour training sessions… #RSAC

Final, Final Thought: May Your Future Not Look Like This! #RSAC

Thank You Very Much For Your Participation! Todd Fitzgerald CISSP, CISM, CISA, CRISC, CGEIT, CIPP/US/E/C, CIPM, PMP, ISO 27001, ITILv 3 f Deerfield, IL Todd_fitzgerald@yahoo. com linkedin. com/in/toddfitzgerald #RSAC