Phish Lurk A Mechanism for Classifying and Preventing












- Slides: 15

Phish. Lurk: A Mechanism for Classifying and Preventing Phishing Websites Master Project Proposal Mohammed Alqahtani

2/22/2021 Mohammed Alqahtani/Phish. Lurk Outline of the Talk § Introduction § Motivation § Phishing Defense § Goals § Phishlurk § How Phishlurk Works § Design Of Phish. Lurk § Tasks/Schedule § Deliverables § References 2

2/22/2021 Mohammed Alqahtani/Phish. Lurk Introduction § What is Phishing ? § How Bad ? § In the U. S. , companies lose more than $2 billion every year. § 7 of 10 users received phishing E-mail, are spoofed. § Why phishing works ? § Lack of Knowledge, carelessness, Visual Deception, and too many phishing attempts 3

2/22/2021 Motivation Mohammed Alqahtani/Phish. Lurk § Existed solutions : § Use black list to filter phishing sites § Integrate filtering/alerting functions into browsers through plugs-ins, extensions and toolbar. § Users have varieties ways to access the internet § Different platforms: notebooks, handhelds, smartphones, etc. § Different computation capabilities and features § Existed phishing protection mainly support desktop. § Expand the surface for phishing attackers and make it harder to provide protection 4

2/22/2021 5 Mohammed Alqahtani/Phish. Lurk Related Work § Phish. Tank § Short note on what it is. Highlight the research results § Title of paper 1, authors, conf/journal, year § Short note on what it is. Highlight the research results § Title of paper 2 , authors, conf/journal, year § Short note on what it is. Highlight the research results § Title of paper 3 , authors, conf/journal, year § Short note on what it is. Highlight the research results

2/22/2021 Mohammed Alqahtani/Phish. Lurk Locations for Implementing Phishing Defense § Browsers themselves § Browsers extensions or plug-ins [ref 1, ref 2] § Proxy server [Dansguardian] § Anti-phishing Server [author-year] § Anti-phishing Search Site. “my project falls in this category”. 6

2/22/2021 Mohammed Alqahtani/Phish. Lurk Goals § Provide user protection against phishing websites § Consume as little computation and screen resource as possible. § Categorize sites with different levels of risks. 7

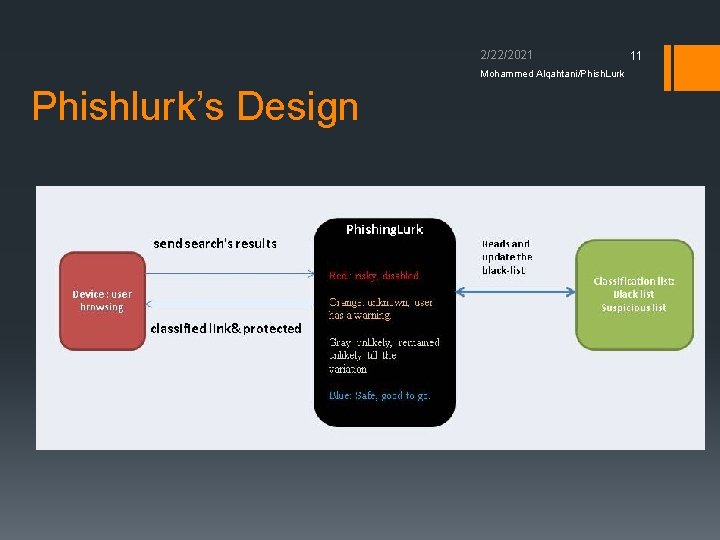
2/22/2021 8 Mohammed Alqahtani/Phish. Lurk Phishlurk § Uses PHP and CSS. § Classify and blocking phishing links. § Uses Phishtank’s blacklist. § Indicates the risk to users consume as less computation and screen recourses as possible. § Coloring scheme. § The process is done on the search server side. Users receive classified and protected links.

2/22/2021 Mohammed Alqahtani/Phish. Lurk How Phishlurks Works? § Valid Phishing link (Red): § For links from confiirmed phishining sites. § Treatment: Disabled. Users will be blocked to access the links. § Unknown link (Orange): § For links that are suspicious. Might be potentially phishing, but not verified yet. § Treatment: Users can decide whether access or not. Phishlurk warns about the impact or consequences. 9

2/22/2021 10 Mohammed Alqahtani/Phish. Lurk How Phishlurks Works? Con’t § Unlikely link (Gray): § For links from Unknown sites and Unlikely to be a phishing link. § i. e. Official websites (. edu or. gov). § Treatment: § Maintains to be unlikely until the verification. § User can choose whether to access the link or not § Phishlurk warn users to take the responsibility and that the link unlikely to be phishing. § Safe Link (Blue): § For links that are known to be safe. § user can access the link without triggering warning messages. . § Phish. Lurk reads and updates the blacklist periodically and automatically from the source “Phish. Tank. com”

2/22/2021 Mohammed Alqahtani/Phish. Lurk Phishlurk’s Design 11

2/22/2021 Mohammed Alqahtani/Phish. Lurk Tasks § Done already § In Progress 12

2/22/2021 Mohammed Alqahtani/Phish. Lurk Deliverables 13

References 1. 2. 3. 4. 5. 6. 2/22/2021 14 Mohammed Alqahtani/Phish. Lurk Rachna Dhamija, J. D. Tygar, and Marti Hearst. 2006. Why phishing works. In Proceedings of the SIGCHI conference on Human Factors in computing systems (CHI '06), Rebecca Grinter, Thomas Rodden, Paul Aoki, Ed Cutrell, Robin Jeffries, and Gary Olson (Eds. ). ACM, New York, NY, USA, 581 -590. DOI=10. 1145/1124772. 1124861 http: //doi. acm. org/10. 1145/1124772. 1124861. Aaron Blum, Brad Wardman, Thamar Solorio, and Gary Warner. 2010. Lexical feature based phishing URL detection using online learning. In <em>Proceedings of the 3 rd ACM workshop on Artificial intelligence and security</em> (AISec '10). ACM, New York, NY, USA, 54 -60. DOI=10. 1145/1866423. 1866434 http: //doi. acm. org/10. 1145/1866423. 1866434 Gross, Ben. "Smartphone Anti-Phishing Protection Leaves Much to Be Desired | Messaging News. " Messaging News | The Technology of Email and Instant Messaging. 26 Feb. 2010. Web. <http: //www. messagingnews. com/story/smartphone-anti-phishingprotection-leaves-much-be-desired>. Com. Score, Inc. "Smartphone Subscribers Now Comprise Majority of Mobile Browser and Application Users in U. S. " Com. Score, Inc. - Measuring the Digital World. Com. Score, Inc, 1 Oct. 2010. <http: //www. comscore. com/Press_Events/Press_Releases/2010/10/Smartphone_Subscri bers_Now_Comprise_Majority_of_Mobile_Browser_and_Application_Users_in_U. S>. Entner, Roger. "Smartphones to Overtake Feature Phones in U. S. by 2011. " Http: //www. nielsen. com. Nielsen Wire, 26 Mar. 2010. Web. <http: //blog. nielsen. com/nielsenwire/consumer/smartphones-to-overtake-feature-phonesin-u-s-by-2011/>. Kerstein, Paul L. "How Can We Stop Phishing and Pharming Scams? " CSO Online Security and Risk. CSO Magazine - Security and Risk, 19 July 2005. Web. <http: //www. csoonline. com/article/220491/how-can-we-stop-phishing-and-pharmingscams->.

References 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. 2/22/2021 15 Mohammed Alqahtani/Phish. Lurk Open. DNS, LLC. Phish. Tank: an Anti-phishing Site. [Online]. http: //www. phishtank. com. Joshi, Y. ; Saklikar, S. ; Das, D. ; Saha, S. ; , "Phish. Guard: A browser plug-in for protection from phishing, " Internet Multimedia Services Architecture and Applications, 2008. IMSAA 2008. 2 nd International Conference on , vol. , no. , pp. 1 -6, 10 -12 Dec. 2008 doi: 10. 1109/IMSAA. 2008. 4753929, URL: http: //ieeexplore. ieee. org/stamp. jsp? tp=&arnumber=4753929&isnumber=4753904 Phish. Tank - Statistics about phishing activity and Phish. Tank usage , http: //www. phishtank. com/stats. php Phish. Tank, Friends of Phish. Tank, http: //www. phishtank. com/friends. php Smart. Screen Filter: Frequently Asked Questions. " Windows Home - Microsoft Windows. <http: //windows. microsoft. com/en-US/windows 7/Smart. Screen-Filter-frequently-asked-questions-IE 9>. "Smart. Screen Filter - Microsoft Windows. " Windows Home - Microsoft Windows. Web. <http: //windows. microsoft. com/en-US/internet-explorer/products/ie-9/features/smartscreen-filter>. Apple - Safari - Learn about the Features Available in Safari. " Apple. <http: //www. apple. com/ca/safari/features. html>. TECH. BLORGE- Top Technology news, Paypal warns buyers to avoid Safari browser from Apple - < http: //tech. blorge. com/Structure: %20/2008/02/28/paypal-warns-buyers-to-avoid-safari-browser-fromapple/ > "Firefox 2 Phishing Protection Effectiveness Testing. " Home of the Mozilla Project. <http: //www. mozilla. org/security/phishing-test. html>. "AVIRA News - Anti-Virus Users Are Restless, Avira Survey Finds. " Antivirus Software Solutions for Home and for Business. <http: //www. avira. com/en/press-details/nid/482/>. Chuan Yue and Haining Wang. 2010. Bogus. Biter: A transparent protection against phishing attacks. ACM Trans. Internet Technol. 10, 2, Article 6 (June 2010), 31 pages. DOI=10. 1145/1754393. 1754395 http: //doi. acm. org/10. 1145/1754393. 1754395 Rachna Dhamija and J. D. Tygar. 2005. The battle against phishing: Dynamic Security Skins. In Proceedings of the 2005 symposium on Usable privacy and security (SOUPS '05). ACM, New York, NY, USA, 77 -88. DOI=10. 1145/1073001. 1073009 http: //doi. acm. org/10. 1145/1073001. 1073009