Outline String String Processing Pattern Matching EncryptionDecryption Compression










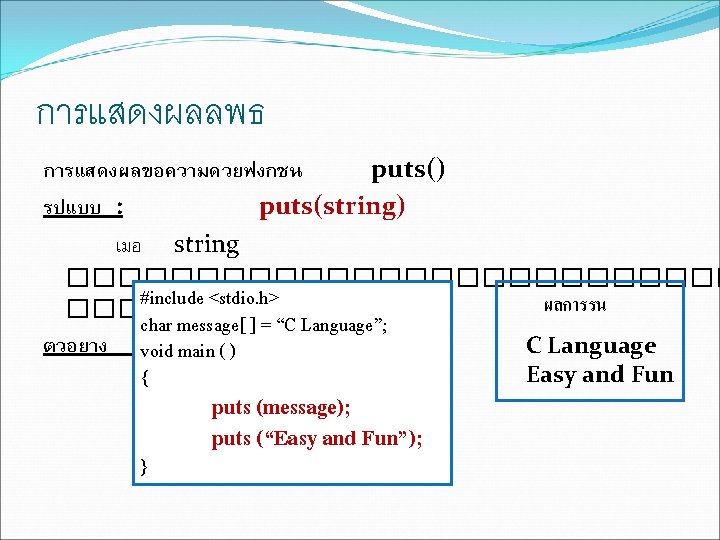
![ตวอยางโปรแกรม #include<stdio. h> char x [30]; void main ( ) { printf (“Enter your ตวอยางโปรแกรม #include<stdio. h> char x [30]; void main ( ) { printf (“Enter your](https://slidetodoc.com/presentation_image_h/23f560a7f83afede7e532c01ea19a201/image-12.jpg)
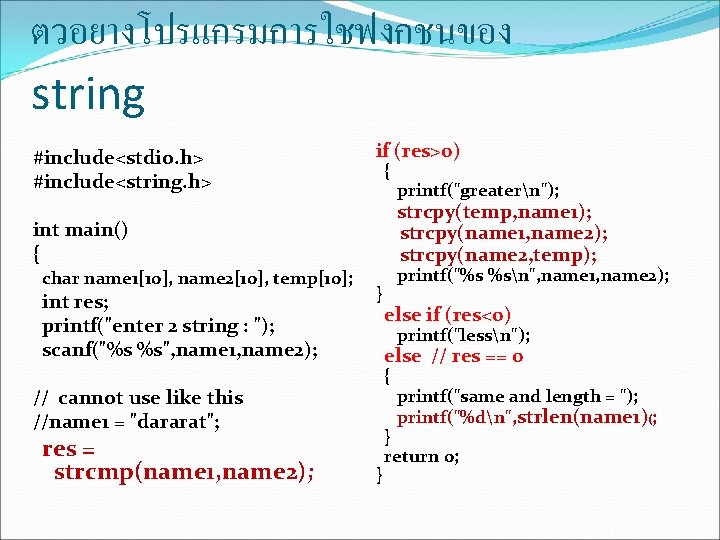
![การกำหนดคาใหกบตวแปรเกบขอ ความ Example #include<stdio. h> void main ( ) { char mass[11] = “C การกำหนดคาใหกบตวแปรเกบขอ ความ Example #include<stdio. h> void main ( ) { char mass[11] = “C](https://slidetodoc.com/presentation_image_h/23f560a7f83afede7e532c01ea19a201/image-13.jpg)




![Pattern Matching Algorithms Input: An array T[n] of n characters representing a text and Pattern Matching Algorithms Input: An array T[n] of n characters representing a text and](https://slidetodoc.com/presentation_image_h/23f560a7f83afede7e532c01ea19a201/image-21.jpg)




- Slides: 37


Outline �ทบทวน String ����������� (String Processing) �Pattern Matching �Encryption/Decryption �Compression









![ตวอยางโปรแกรม includestdio h char x 30 void main printf Enter your ตวอยางโปรแกรม #include<stdio. h> char x [30]; void main ( ) { printf (“Enter your](https://slidetodoc.com/presentation_image_h/23f560a7f83afede7e532c01ea19a201/image-12.jpg)
ตวอยางโปรแกรม #include<stdio. h> char x [30]; void main ( ) { printf (“Enter your name : ”); ผลลพธ Enter your name : manee dee Your name : manee dee gets(x); printf (“Your name : %sn”, x); }
![การกำหนดคาใหกบตวแปรเกบขอ ความ Example includestdio h void main char mass11 C การกำหนดคาใหกบตวแปรเกบขอ ความ Example #include<stdio. h> void main ( ) { char mass[11] = “C](https://slidetodoc.com/presentation_image_h/23f560a7f83afede7e532c01ea19a201/image-13.jpg)
การกำหนดคาใหกบตวแปรเกบขอ ความ Example #include<stdio. h> void main ( ) { char mass[11] = “C Language”; char book[4] = {‘A’, ‘B’, ‘C’, ‘�’}; } printf (“%sn”, mass); printf (“%sn”, book); printf (“%cn”, mass[3]); ผลการรน C Language ABC a



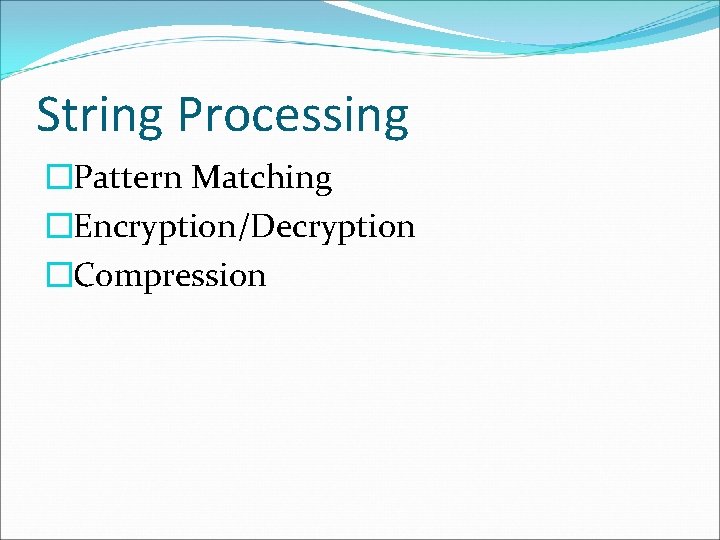
ตวอยางโปรแกรมการใชฟงกชนของ string #include<stdio. h> #include<string. h> if (res>0) { strcpy(temp, name 1); strcpy(name 1, name 2); strcpy(name 2, temp); int main() { char name 1[10], name 2[10], temp[10]; int res; printf("enter 2 string : "); scanf("%s %s", name 1, name 2); } printf("%s %sn", name 1, name 2); else if (res<0) printf("lessn"); else // res == 0 { // cannot use like this //name 1 = "dararat"; res = strcmp(name 1, name 2); printf("greatern"); } printf("same and length = "); printf("%dn", strlen(name 1)(; } return 0;

Don’t Sleep Yet…

String Processing �Pattern Matching �Encryption/Decryption �Compression

Pattern Matching �given a string of n characters called text (T) , and a string of m (m<=n) characters called pattern (P) �find a substring of the text that match the pattern

Pattern Matching Algorithms �Brute-Force �Boyer-Moore �Knuth-Morris-Pratt
![Pattern Matching Algorithms Input An array Tn of n characters representing a text and Pattern Matching Algorithms Input: An array T[n] of n characters representing a text and](https://slidetodoc.com/presentation_image_h/23f560a7f83afede7e532c01ea19a201/image-21.jpg)
Pattern Matching Algorithms Input: An array T[n] of n characters representing a text and an array P[m] of m character representing a patterm Output: The index of the first character in the text that starts a matching substring or 1 if the search is unsuccessful

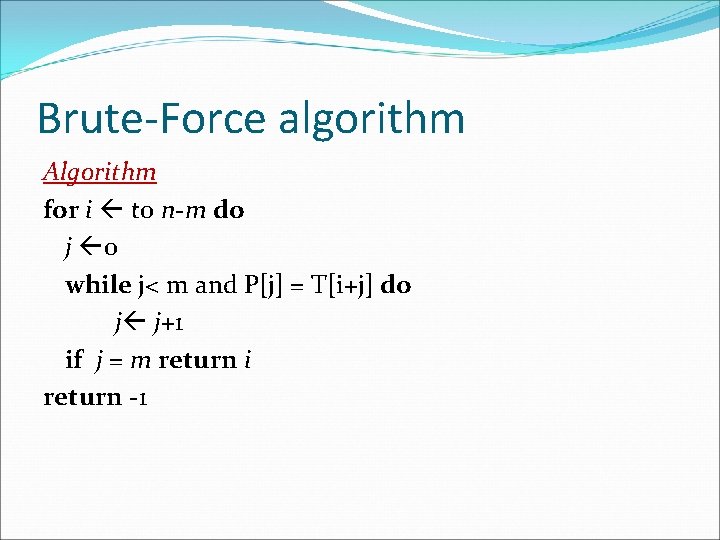
Brute-Force algorithm Algorithm for i to n-m do j 0 while j< m and P[j] = T[i+j] do j j+1 if j = m return i return -1

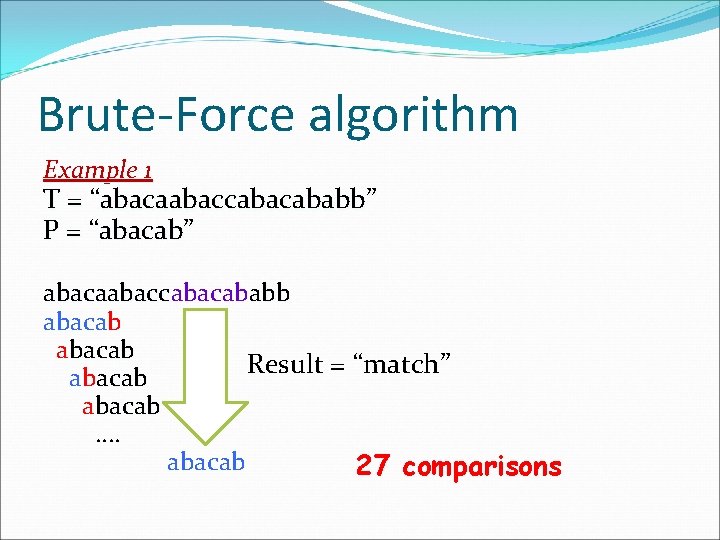
Brute-Force algorithm Example 1 T = “abacaabaccababb” P = “abacab” abacaabaccabacab abacaabacc abacab Result = “match” abacab …. abacab 27 comparisons

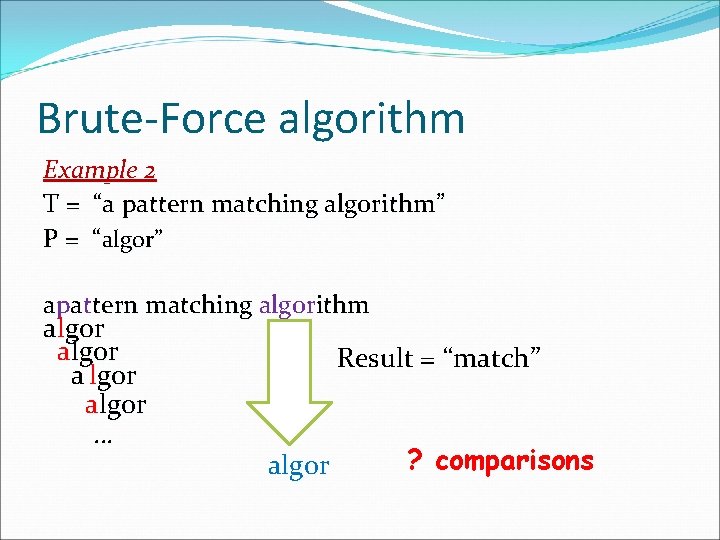
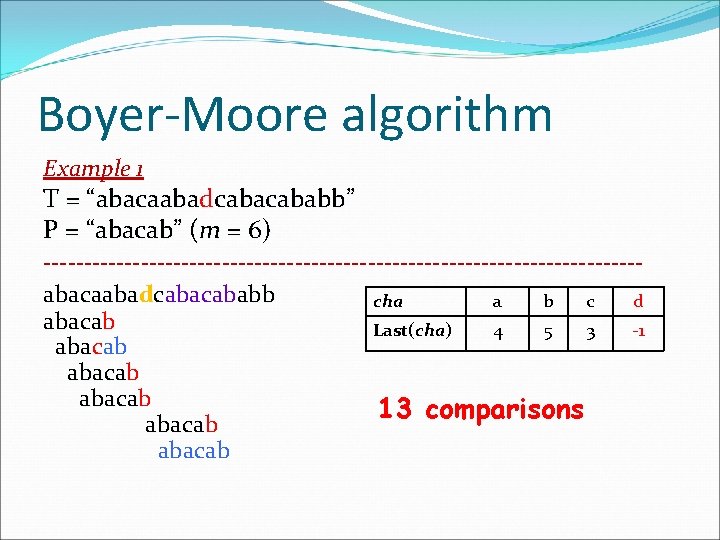
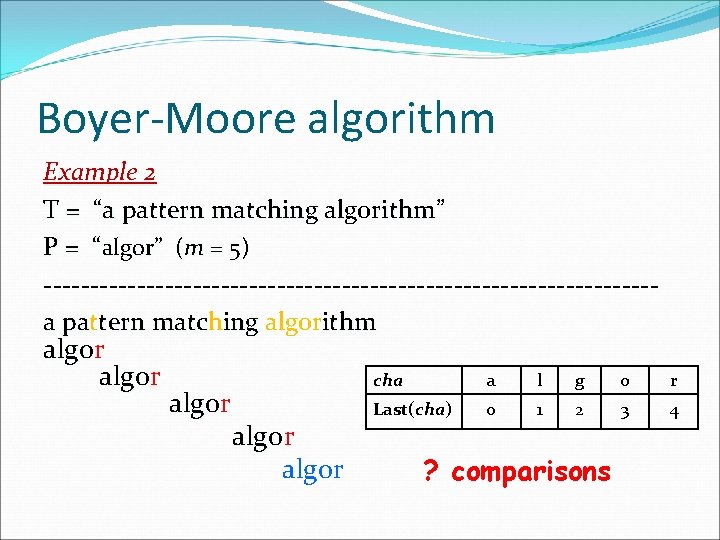
Brute-Force algorithm Example 2 T = “a pattern matching algorithm” P = “algor” apattern matching algorithm algor algor … Result = “match” algor ? comparisons

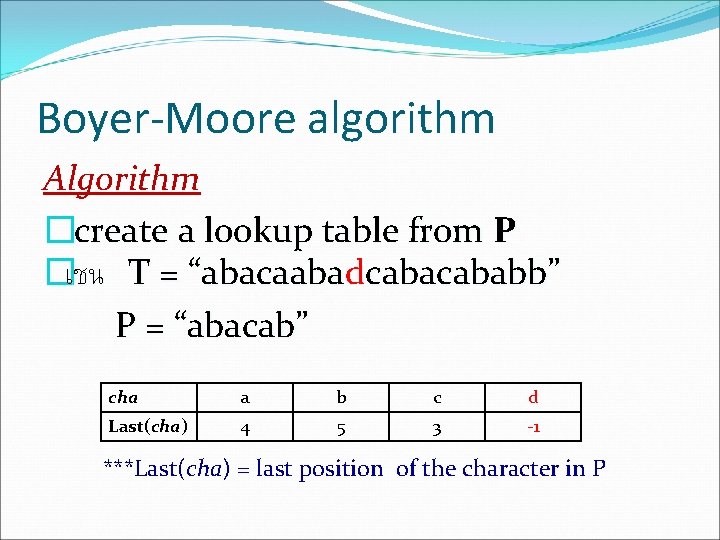
Boyer-Moore algorithm Algorithm �create a lookup table from P �เชน T = “abacaabad “abacaaba cababb” P = “abacab” cha a b c d Last(cha) 4 5 3 -1 ***Last(cha) = last position of the character in P

Boyer-Moore algorithm Algorithm (��� ) �compare from right to left 1 -by-1 �if not equal at position i in T, � if Ti is in lookup table �n = |last(Ti)-last(Pi)| �shift comparison to the next n location of T � if Ti is not in lookup table �shift comparison to the next m (ex. m=6) location of T

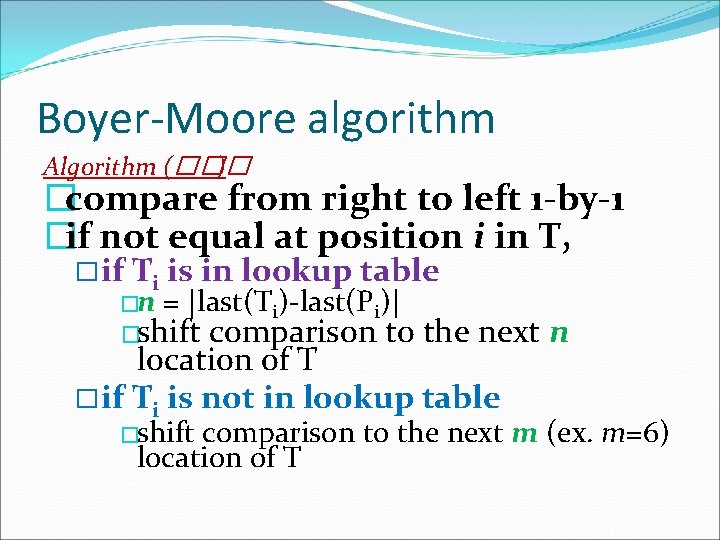
Boyer-Moore algorithm Example 1 T = “abacaabad “abacaaba cababb” P = “abacab” (m = 6) -------------------------------------abacaabad abacaaba cababb cha a b c d abacab abaca Last(cha) 4 5 3 -1 abacab abaca 13 comparisons abacab

Boyer-Moore algorithm Example 2 T = “a pattern matching algorithm” P = “algor” (m = 5) ---------------------------------a pat pa tern match matc ing algorithm algor algo algor cha a l g o r Last(cha) 0 1 2 3 4 ? comparisons

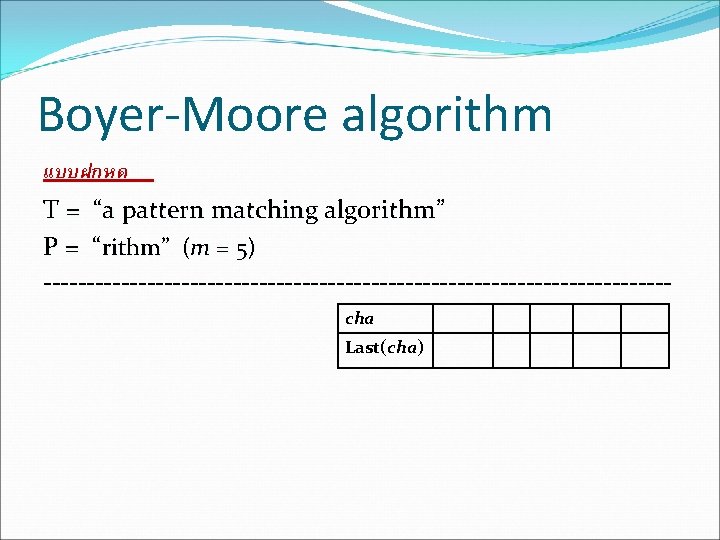
Boyer-Moore algorithm แบบฝกหด T = “a pattern matching algorithm” P = “rithm” (m = 5) ------------------------------------cha Last(cha)

Encryption/Decryption � Cryptographic computations encryption/decryption , digital signatures � To support secure communication over the Internet – using cryptographic computations for information security services

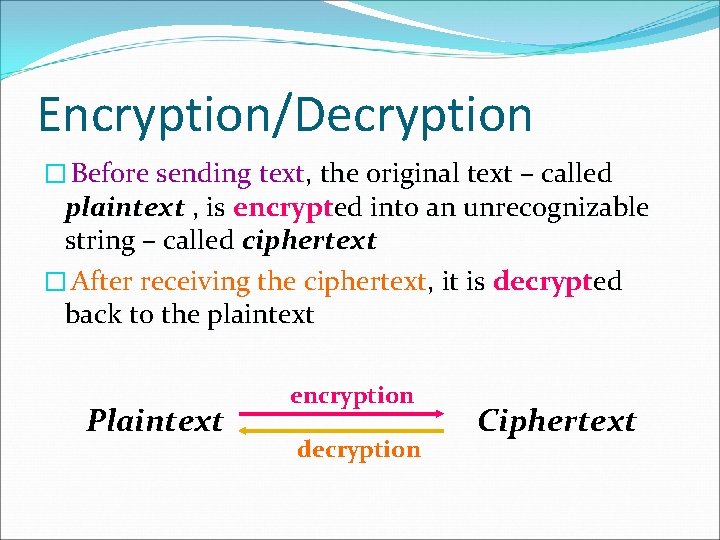
Encryption/Decryption � Before sending text, the original text – called plaintext , is encrypted into an unrecognizable string – called ciphertext � After receiving the ciphertext, it is decrypted back to the plaintext Plaintext encryption decryption Ciphertext

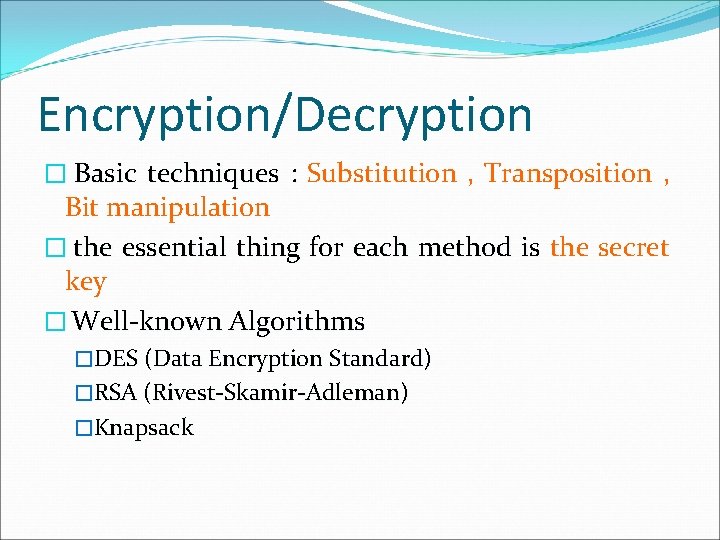
Encryption/Decryption � Basic techniques : Substitution , Transposition , Bit manipulation � the essential thing for each method is the secret key � Well-known Algorithms �DES (Data Encryption Standard) �RSA (Rivest-Skamir-Adleman) �Knapsack

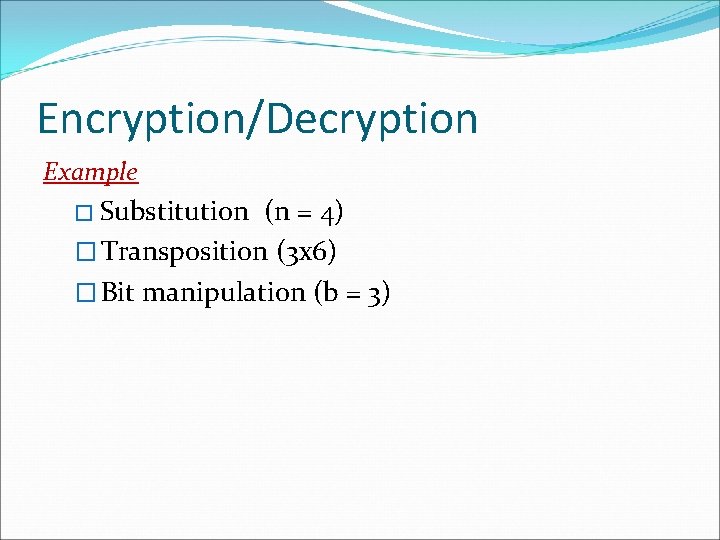
Encryption/Decryption Example � Substitution (n = 4) � Transposition (3 x 6) � Bit manipulation (b = 3)

Compression � given a string X (ascii, unicode), encode into a small binary string Y � Huffman coding algorithm – based on character frequency to construct a binary tree , uses greedy method

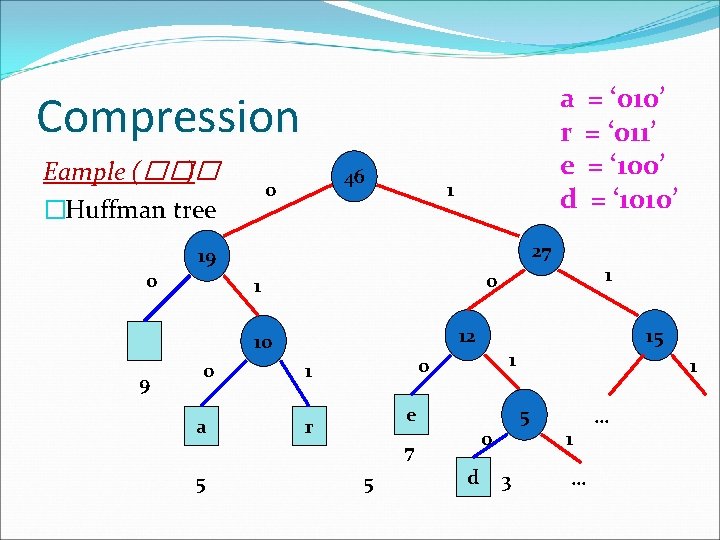
Compression Eample “a fast runner need never be afraid of the dark” �frequency of each character char. a b d e f h i k n o r s t u v freq. 9 5 1 3 7 3 1 1 1 4 1 5 1 2 1 1

a = ‘ 010’ r = ‘ 011’ e = ‘ 100’ d = ‘ 1010’ Compression Eample (��� ) �Huffman tree 0 46 0 1 27 19 12 10 9 0 a e r 5 1 5 0 d 15 1 0 1 7 5 1 0 1 3 1 … …

การบาน �Knuth-Morris-Pratt algorithm