Network Layer a Forwarding Goals r understand principles






- Slides: 54

Network Layer: a. Forwarding Goals: r understand principles behind network layer services: m m m forwarding routing (path selection) dealing with scale r instantiation and implementation in the Internet and in other types of networks Overview: r network layer services r VC network operation r ATM r IP addresses & their usage r NAT r IP header r IP fragmentation r ICMP r IPv 6 Ch. 4: Network Layer - Forwarding #1

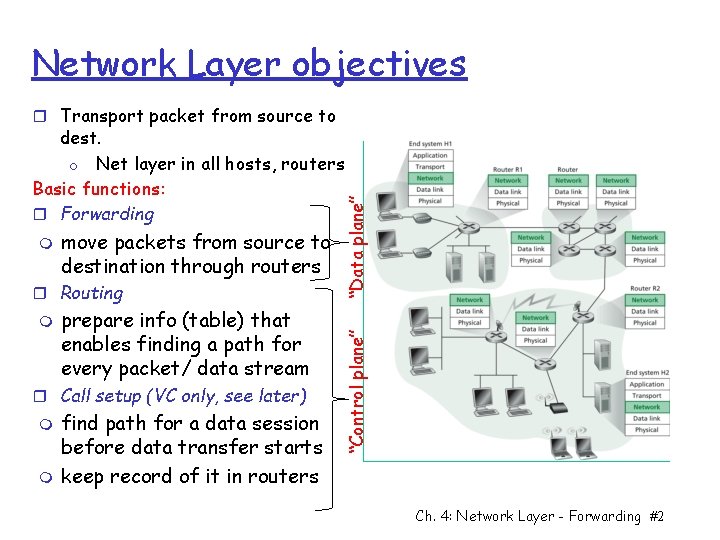
Network Layer objectives r Transport packet from source to move packets from source to destination through routers r Routing m prepare info (table) that enables finding a path for every packet/ data stream r Call setup (VC only, see later) m m find path for a data session before data transfer starts keep record of it in routers “Control plane” m “Data plane” dest. o Net layer in all hosts, routers Basic functions: r Forwarding Ch. 4: Network Layer - Forwarding #2

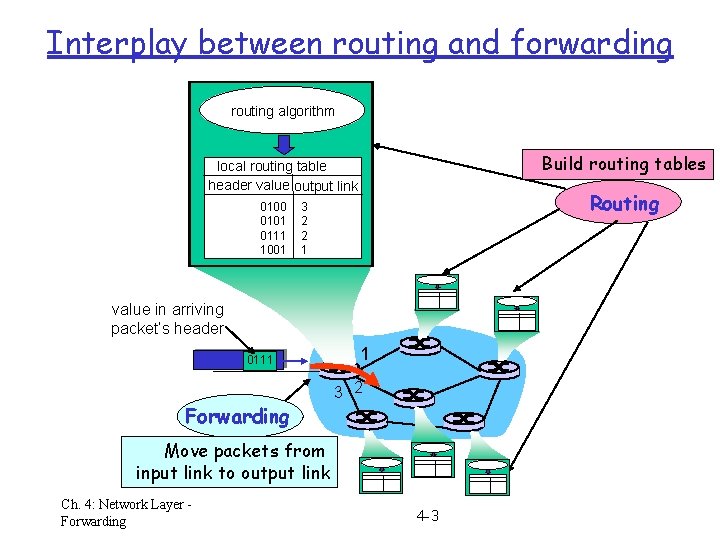
Interplay between routing and forwarding routing algorithm Build routing tables local routing table header value output link 0100 0101 0111 1001 Routing 3 2 2 1 value in arriving packet’s header 0111 Forwarding 1 3 2 Move packets from input link to output link Ch. 4: Network Layer Forwarding 4 -3

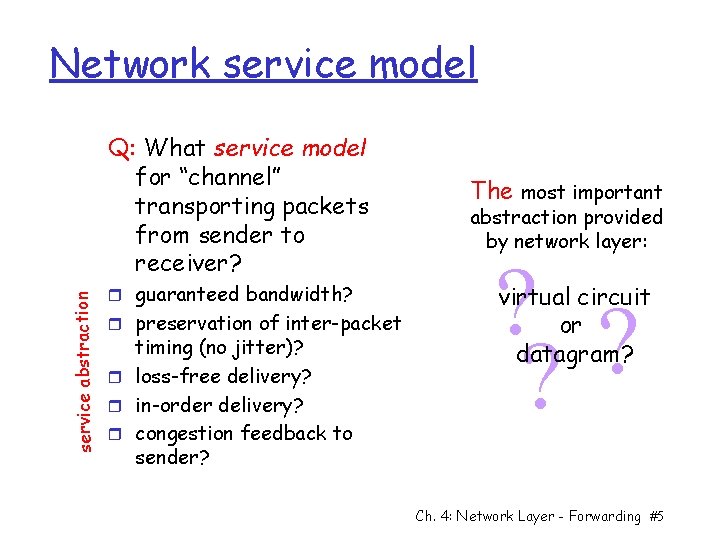
Network service model service abstraction Q: What service model for “channel” transporting packets from sender to receiver? r guaranteed bandwidth? r preservation of inter-packet timing (no jitter)? r loss-free delivery? r in-order delivery? r congestion feedback to sender? The most important abstraction provided by network layer: ? ? ? virtual circuit or datagram? Ch. 4: Network Layer - Forwarding #5

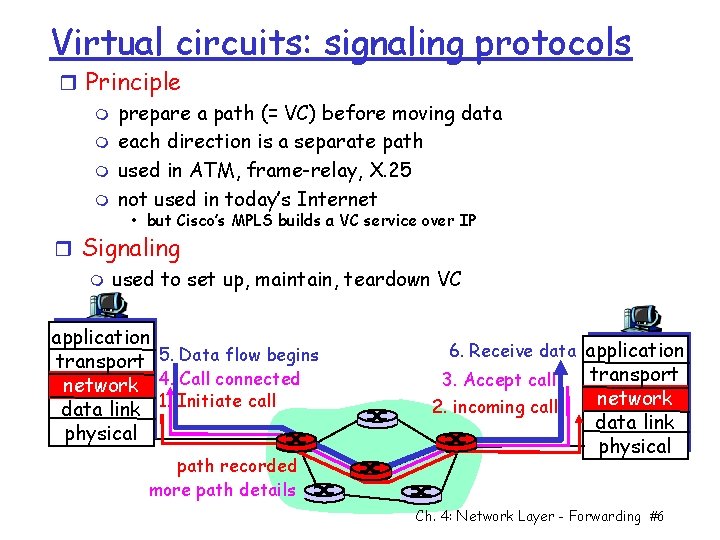
Virtual circuits: signaling protocols r Principle m prepare a path (= VC) before moving data m each direction is a separate path m used in ATM, frame-relay, X. 25 m not used in today’s Internet • but Cisco’s MPLS builds a VC service over IP r Signaling m used to set up, maintain, teardown VC application transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical path recorded more path details 6. Receive data application 3. Accept call 2. incoming call transport network data link physical Ch. 4: Network Layer - Forwarding #6

Virtual Circuit: call setup r Path preparation + resource allocation: m Call setup message flows from source to destination. • path recorded at this time m Path determination (routing): • Source based or network based. m Msg may indicate required resources: • BW, latency, buffer, etc. m. A router can either: • accept (and commit required resources) or reject m Path accepted if all routers accept. Ch. 4: Network Layer - Forwarding #7

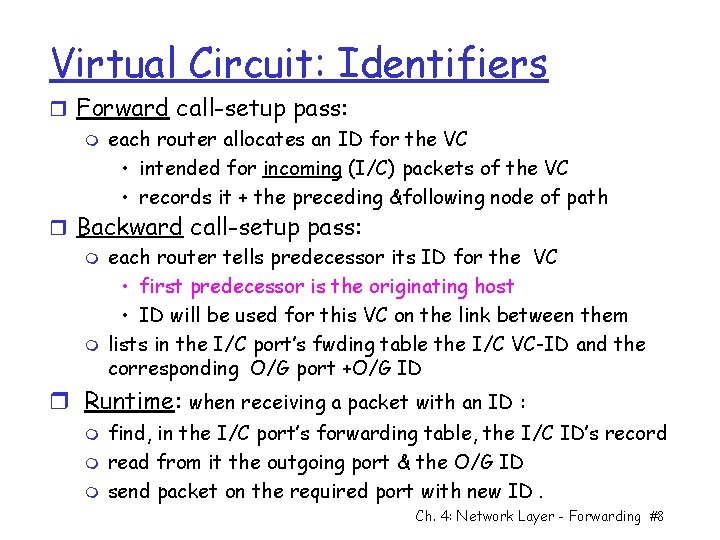
Virtual Circuit: Identifiers r Forward call-setup pass: m each router allocates an ID for the VC • intended for incoming (I/C) packets of the VC • records it + the preceding &following node of path r Backward call-setup pass: m each router tells predecessor its ID for the VC • first predecessor is the originating host • ID will be used for this VC on the link between them m lists in the I/C port’s fwding table the I/C VC-ID and the corresponding O/G port +O/G ID r Runtime: when receiving a packet with an ID : m m m find, in the I/C port’s forwarding table, the I/C ID’s record read from it the outgoing port & the O/G ID send packet on the required port with new ID. Ch. 4: Network Layer - Forwarding #8

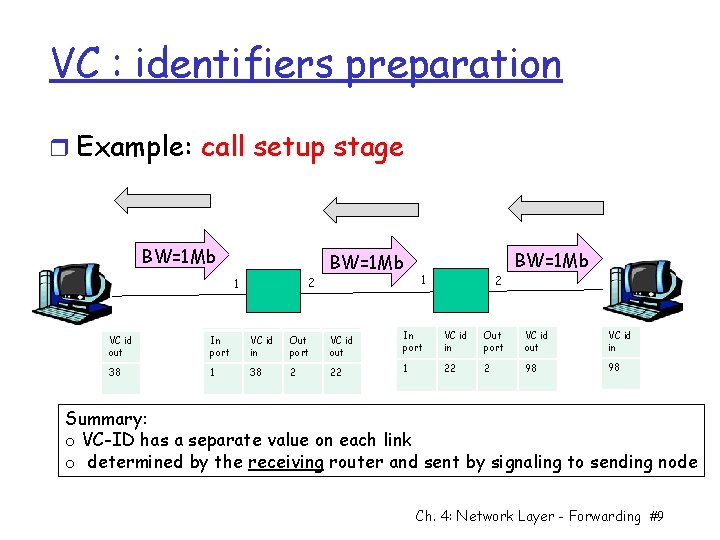
VC : identifiers preparation r Example: call setup stage BW=1 Mb 2 1 BW=1 Mb 1 2 BW=1 Mb VC id out In In port VC VC id id in in Out port VC VC id id out In In port VC id in Out port VC id out VC id in 38 11 38 2 22 11 22 2 98 98 Summary: o VC-ID has a separate value on each link o determined by the receiving router and sent by signaling to sending node Ch. 4: Network Layer - Forwarding #9

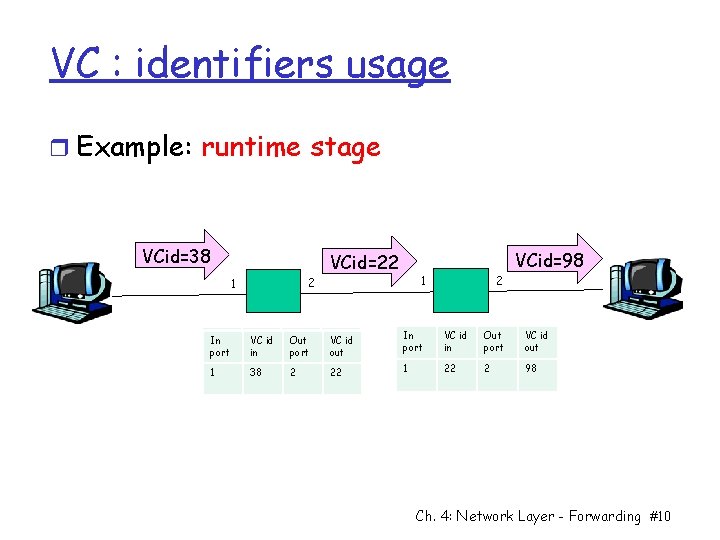
VC : identifiers usage r Example: runtime stage VCid=38 2 1 VCid=22 2 1 VCid=98 In In port VC VC id id in in Out port VC VC id id out In In port VC id in Out port VC id out 11 38 2 22 11 22 2 98 Ch. 4: Network Layer - Forwarding #10

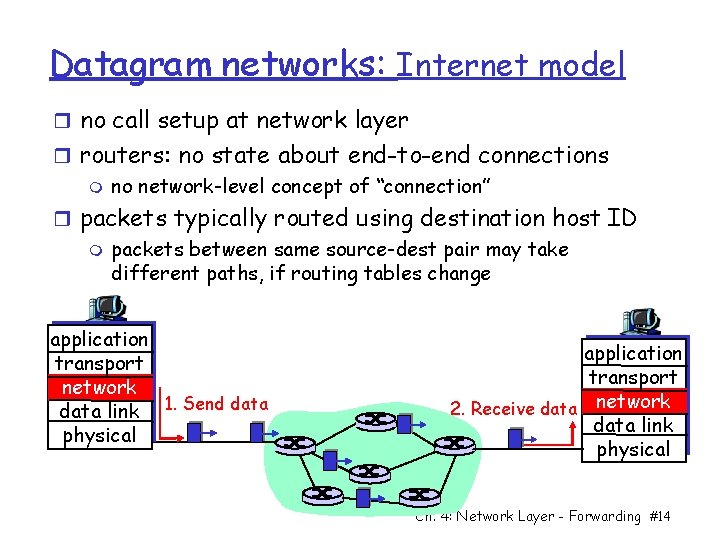
Datagram networks: Internet model r no call setup at network layer r routers: no state about end-to-end connections m no network-level concept of “connection” r packets typically routed using destination host ID m packets between same source-dest pair may take different paths, if routing tables change application transport network data link 1. Send data physical application transport 2. Receive data network data link physical Ch. 4: Network Layer - Forwarding #14

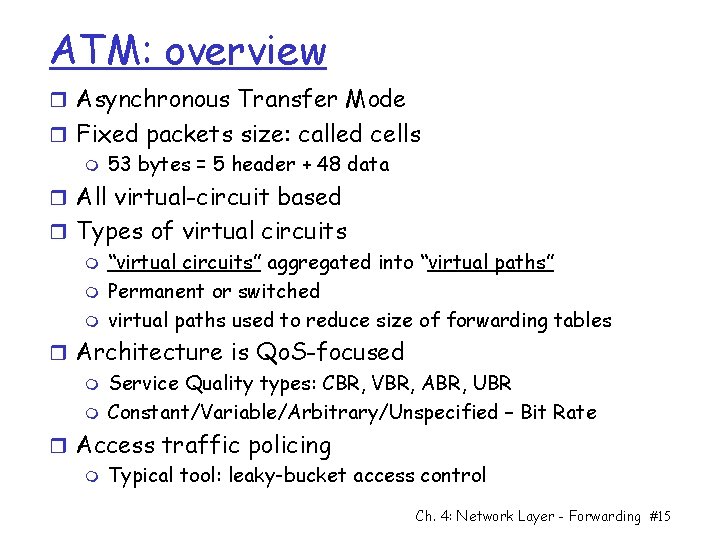
ATM: overview r Asynchronous Transfer Mode r Fixed packets size: called cells m 53 bytes = 5 header + 48 data r All virtual-circuit based r Types of virtual circuits m “virtual circuits” aggregated into “virtual paths” m Permanent or switched m virtual paths used to reduce size of forwarding tables r Architecture is Qo. S-focused m Service Quality types: CBR, VBR, ABR, UBR m Constant/Variable/Arbitrary/Unspecified – Bit Rate r Access traffic policing m Typical tool: leaky-bucket access control Ch. 4: Network Layer - Forwarding #15

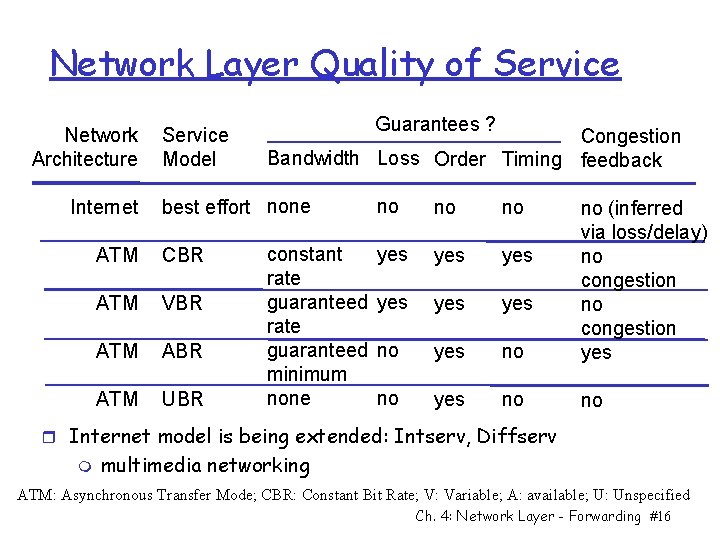
Network Layer Quality of Service Network Architecture Internet Service Model Guarantees ? Congestion Bandwidth Loss Order Timing feedback best effort none ATM CBR ATM VBR ATM ABR ATM UBR constant rate guaranteed minimum none no no no yes yes yes no no (inferred via loss/delay) no congestion yes no no r Internet model is being extended: Intserv, Diffserv m multimedia networking ATM: Asynchronous Transfer Mode; CBR: Constant Bit Rate; V: Variable; A: available; U: Unspecified Ch. 4: Network Layer - Forwarding #16

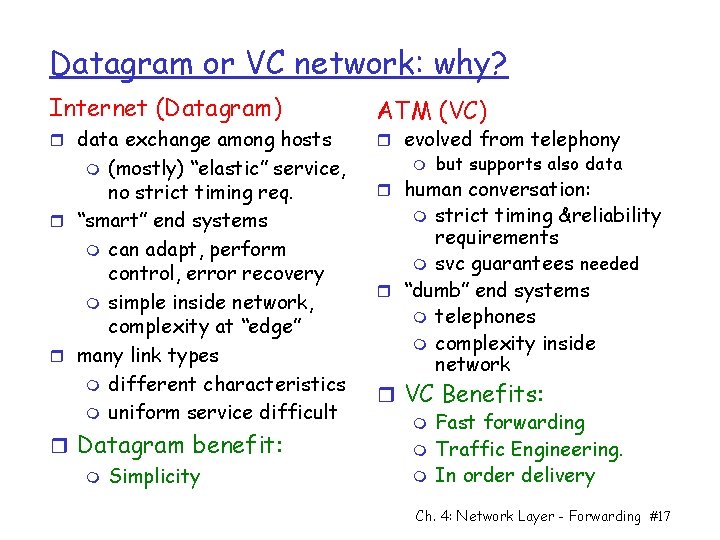
Datagram or VC network: why? Internet (Datagram) r data exchange among hosts (mostly) “elastic” service, no strict timing req. r “smart” end systems m can adapt, perform control, error recovery m simple inside network, complexity at “edge” r many link types m different characteristics m uniform service difficult m r Datagram benefit: m Simplicity ATM (VC) r evolved from telephony m but supports also data r human conversation: strict timing &reliability requirements m svc guarantees needed r “dumb” end systems m telephones m complexity inside network m r VC Benefits: m Fast forwarding m Traffic Engineering. m In order delivery Ch. 4: Network Layer - Forwarding #17

IP Addressing Scheme r We need an address to uniquely identify each destination r Routing scalability requires flexibility in aggregation of destination addresses m we should be able to aggregate a set of destinations as a single routing unit m necessary for routing table scalability r Preview: the unit of routing in the Internet is a network - the destinations in the routing protocols and tables are networks Ch. 4: Network Layer - Forwarding #19

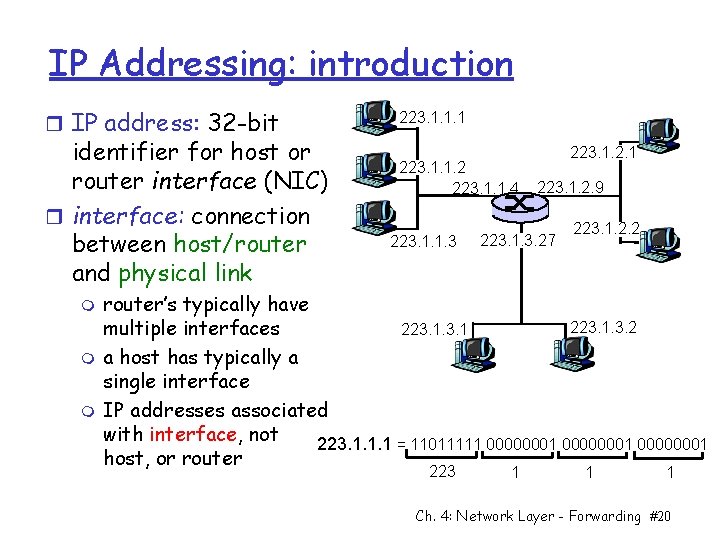
IP Addressing: introduction r IP address: 32 -bit identifier for host or router interface (NIC) r interface: connection between host/router and physical link m m m 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 router’s typically have 223. 1. 3. 2 multiple interfaces 223. 1 a host has typically a single interface IP addresses associated with interface, not 223. 1. 1. 1 = 11011111 00000001 host, or router 223 1 1 1 Ch. 4: Network Layer - Forwarding #20

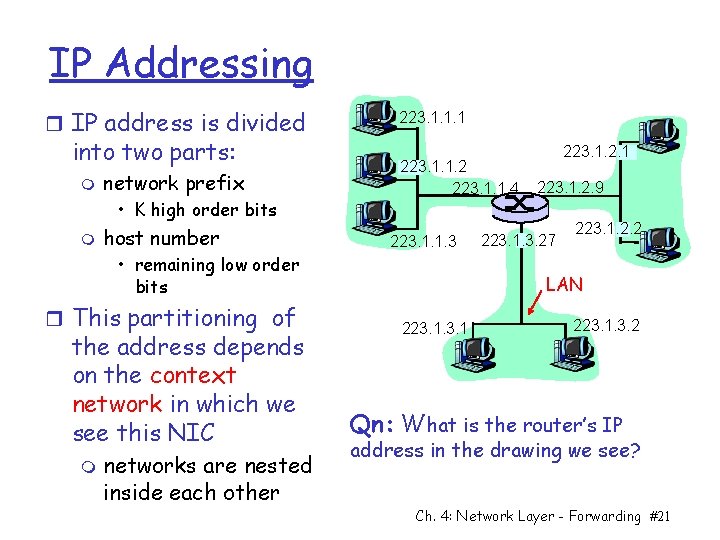
IP Addressing r IP address is divided into two parts: m network prefix • K high order bits m host number 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 • remaining low order bits r This partitioning of the address depends on the context network in which we see this NIC m networks are nested inside each other 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 LAN 223. 1. 3. 2 Qn: What is the router’s IP address in the drawing we see? Ch. 4: Network Layer - Forwarding #21

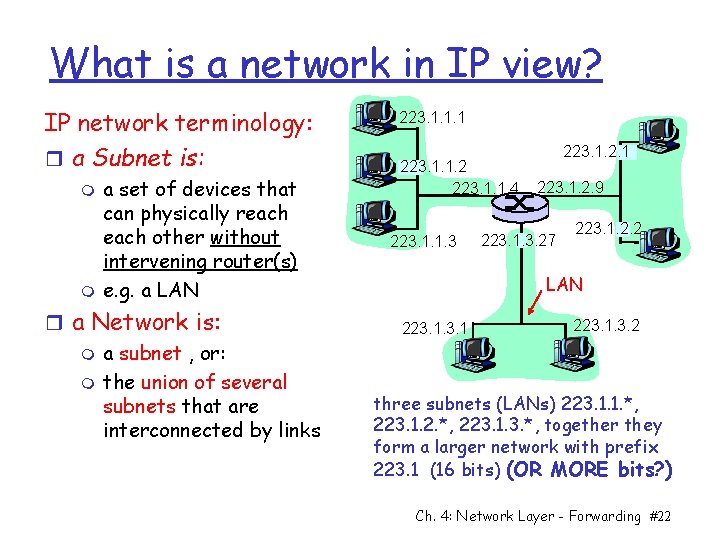
What is a network in IP view? IP network terminology: r a Subnet is: m m a set of devices that can physically reach other without intervening router(s) e. g. a LAN r a Network is: m a subnet , or: m the union of several subnets that are interconnected by links 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 LAN 223. 1. 3. 2 three subnets (LANs) 223. 1. 1. *, 223. 1. 2. *, 223. 1. 3. *, together they form a larger network with prefix 223. 1 (16 bits) (OR MORE bits? ) Ch. 4: Network Layer - Forwarding #22

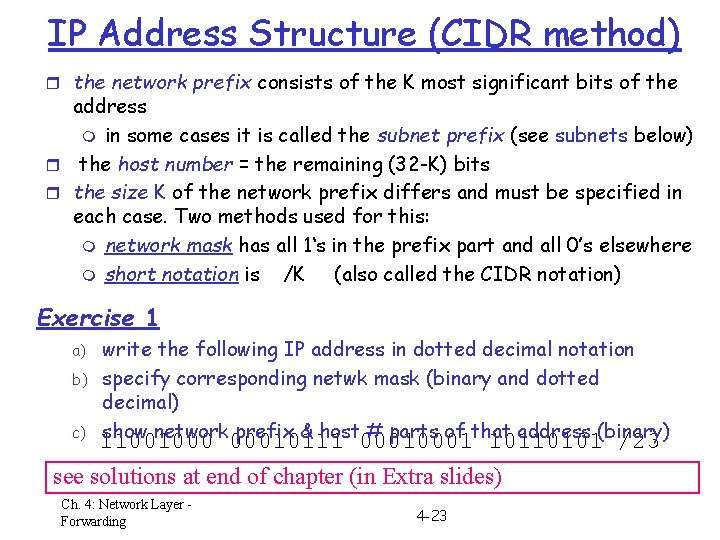
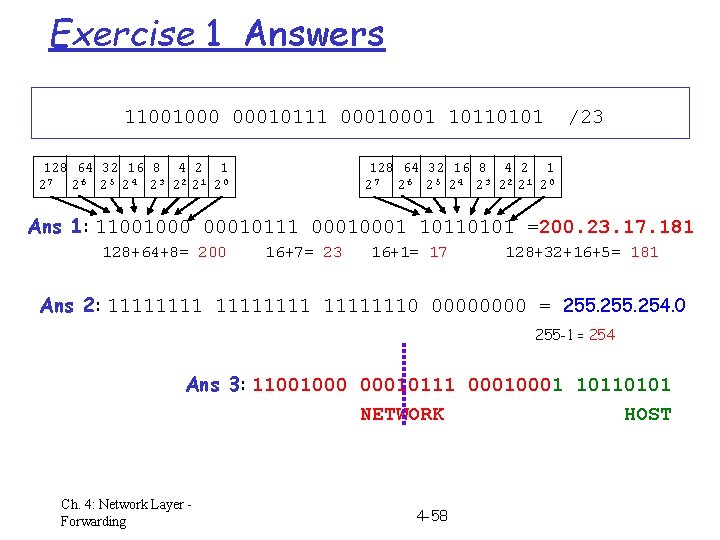
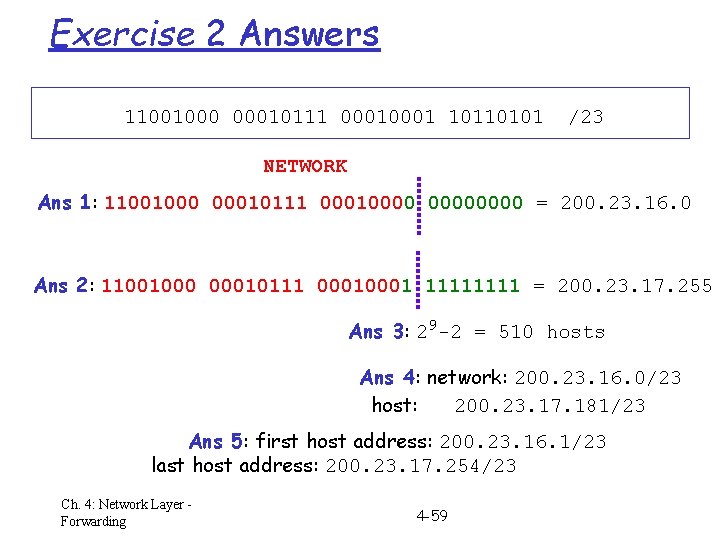
IP Address Structure (CIDR method) r the network prefix consists of the K most significant bits of the address m in some cases it is called the subnet prefix (see subnets below) r the host number = the remaining (32 -K) bits r the size K of the network prefix differs and must be specified in each case. Two methods used for this: m network mask has all 1‘s in the prefix part and all 0’s elsewhere m short notation is /K (also called the CIDR notation) Exercise 1 a) b) c) write the following IP address in dotted decimal notation specify corresponding netwk mask (binary and dotted decimal) show network prefix & host # parts of that address (binary) 11001000 00010111 0001 10110101 /23 see solutions at end of chapter (in Extra slides) Ch. 4: Network Layer Forwarding 4 -23

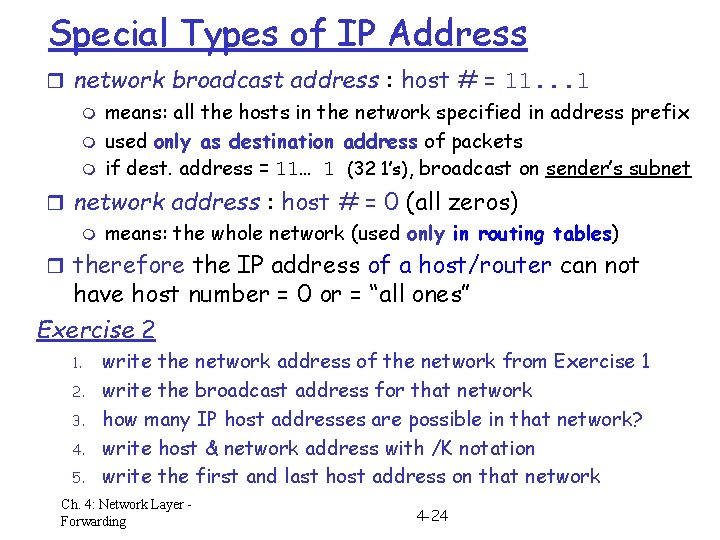
Special Types of IP Address r network broadcast address : host # = 11. . . 1 m means: all the hosts in the network specified in address prefix used only as destination address of packets if dest. address = 11… 1 (32 1’s), broadcast on sender’s subnet r network address : host # = 0 (all zeros) m means: the whole network (used only in routing tables) r therefore the IP address of a host/router can not have host number = 0 or = “all ones” Exercise 2 1. 2. 3. 4. 5. write the network address of the network from Exercise 1 write the broadcast address for that network how many IP host addresses are possible in that network? write host & network address with /K notation write the first and last host address on that network Ch. 4: Network Layer Forwarding 4 -24

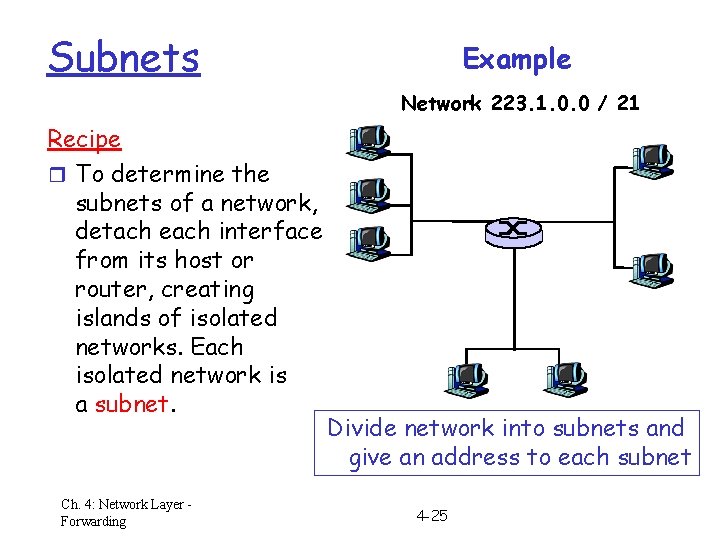
Subnets Example Network 223. 1. 0. 0 / 21 Recipe r To determine the subnets of a network, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is a subnet. Ch. 4: Network Layer Forwarding Divide network into subnets and give an address to each subnet 4 -25

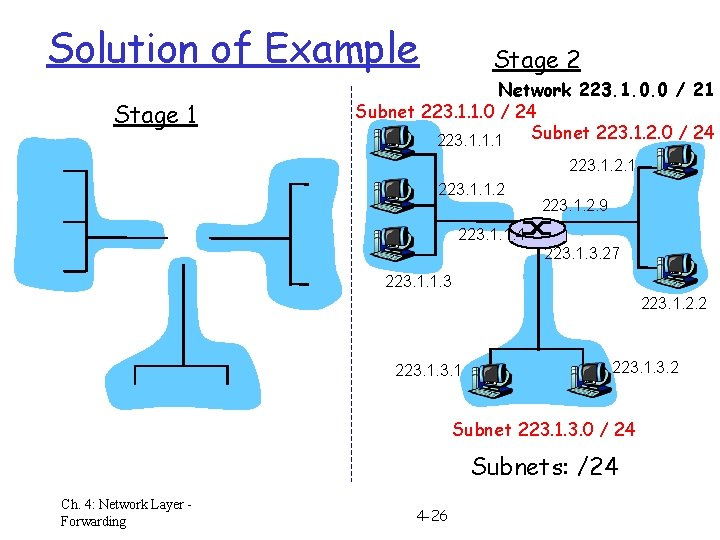
Solution of Example Stage 1 Stage 2 Network 223. 1. 0. 0 / 21 Subnet 223. 1. 1. 0 / 24 Subnet 223. 1. 2. 0 / 24 223. 1. 1. 1 223. 1. 2. 1 223. 1. 1. 2 223. 1. 2. 9 223. 1. 1. 4 223. 1. 3. 27 223. 1. 1. 3 223. 1. 2. 2 223. 1. 3. 2 Subnet 223. 1. 3. 0 / 24 Subnets: /24 Ch. 4: Network Layer Forwarding 4 -26

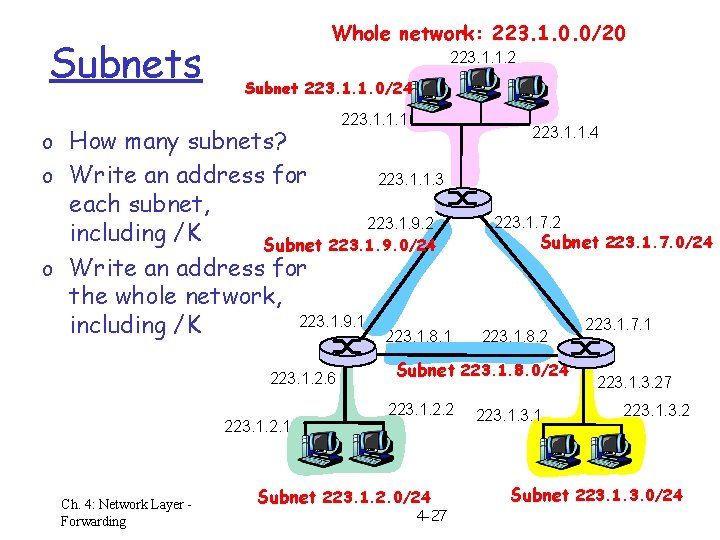
Subnets Whole network: 223. 1. 0. 0/20 223. 1. 1. 2 Subnet 223. 1. 1. 0/24 o How many subnets? o Write an address for 223. 1. 1. 1 223. 1. 1. 4 223. 1. 1. 3 each subnet, 223. 1. 9. 2 including /K Subnet 223. 1. 9. 0/24 o Write an address for the whole network, 223. 1. 9. 1 including /K 223. 1. 8. 1 223. 1. 2. 6 223. 1. 2. 1 Ch. 4: Network Layer Forwarding 223. 1. 7. 2 Subnet 223. 1. 7. 0/24 223. 1. 8. 2 Subnet 223. 1. 8. 0/24 223. 1. 2. 2 Subnet 223. 1. 2. 0/24 4 -27 223. 1. 7. 1 223. 1. 3. 27 223. 1. 3. 2 Subnet 223. 1. 3. 0/24

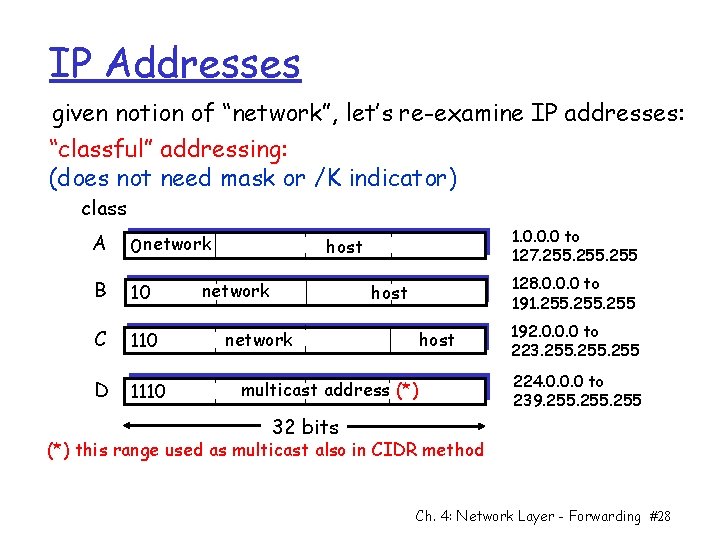
IP Addresses given notion of “network”, let’s re-examine IP addresses: “classful” addressing: (does not need mask or /K indicator) class A 0 network B 10 C 110 D 1110 1. 0. 0. 0 to 127. 255 host network 128. 0. 0. 0 to 191. 255 host network host multicast address (*) 192. 0. 0. 0 to 223. 255 224. 0. 0. 0 to 239. 255 32 bits (*) this range used as multicast also in CIDR method Ch. 4: Network Layer - Forwarding #28

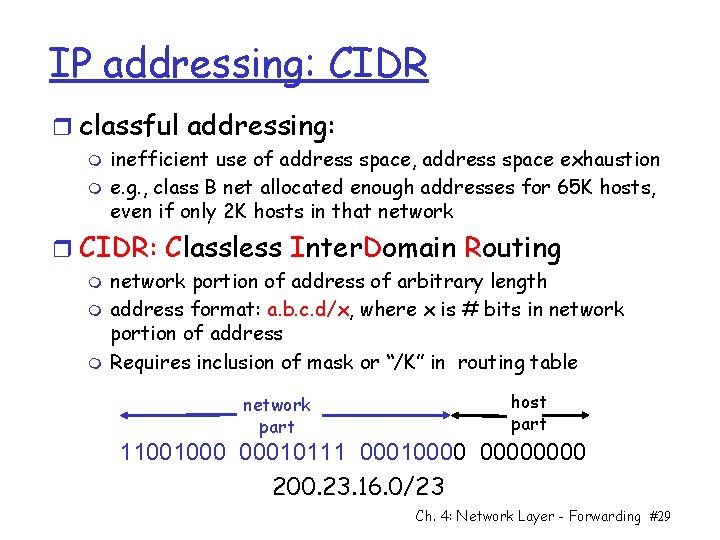
IP addressing: CIDR r classful addressing: m m inefficient use of address space, address space exhaustion e. g. , class B net allocated enough addresses for 65 K hosts, even if only 2 K hosts in that network r CIDR: Classless Inter. Domain Routing m m m network portion of address of arbitrary length address format: a. b. c. d/x, where x is # bits in network portion of address Requires inclusion of mask or “/K” in routing table network part host part 11001000 00010111 00010000 200. 23. 16. 0/23 Ch. 4: Network Layer - Forwarding #29

IP addresses: how to get one? Hosts (host number): r hard-coded by system admin in a file m Can see in IPConfig r DHCP: Dynamic Host Configuration Protocol: dynamically get address: “plug-and-play” m host broadcasts “DHCP discover” msg m DHCP server responds with “DHCP offer” msg m host requests IP address: “DHCP request” msg m DHCP server sends address: “DHCP ack” msg m this is the common practice in LAN (why? ) m in home access: same procedure using PPP protocol Ch. 4: Network Layer - Forwarding #30

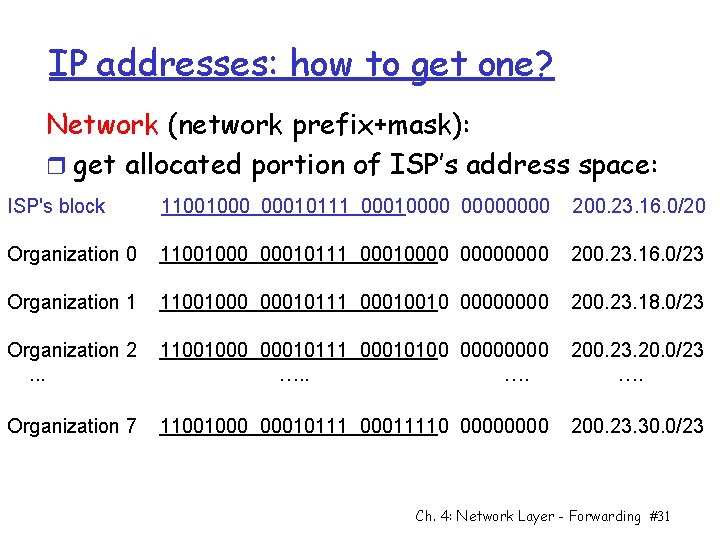
IP addresses: how to get one? Network (network prefix+mask): r get allocated portion of ISP’s address space: ISP's block 11001000 00010111 00010000 200. 23. 16. 0/20 Organization 0 11001000 00010111 00010000 200. 23. 16. 0/23 Organization 1 11001000 00010111 00010010 0000 200. 23. 18. 0/23 Organization 2. . . 11001000 00010111 00010100 0000 …. 200. 23. 20. 0/23 …. Organization 7 11001000 00010111 00011110 0000 200. 23. 30. 0/23 Ch. 4: Network Layer - Forwarding #31

IP addresses: how to get one? ISP r Gets a block of addresses from ICANN: A: ICANN: Internet Corporation for Assigned Names and Numbers m allocates addresses m manages DNS m assigns domain names, resolves disputes m allocates codes for the various protocols Ch. 4: Network Layer - Forwarding #32

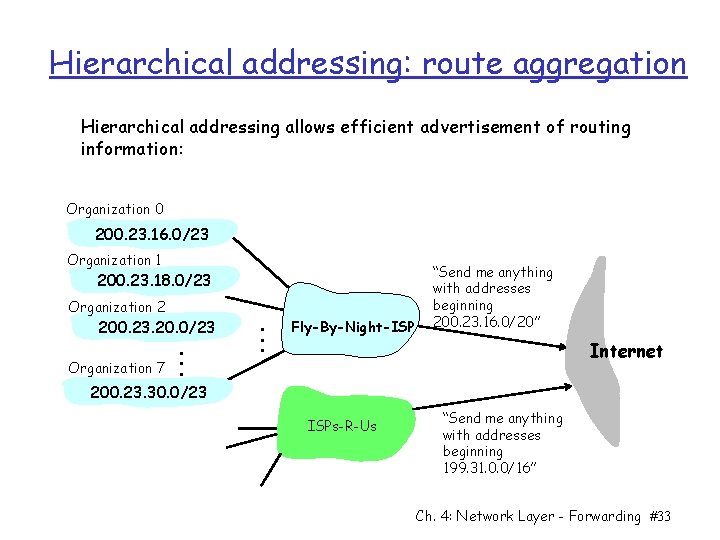
Hierarchical addressing: route aggregation Hierarchical addressing allows efficient advertisement of routing information: Organization 0 200. 23. 16. 0/23 Organization 1 200. 23. 18. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us “Send me anything with addresses beginning 199. 31. 0. 0/16” Ch. 4: Network Layer - Forwarding #33

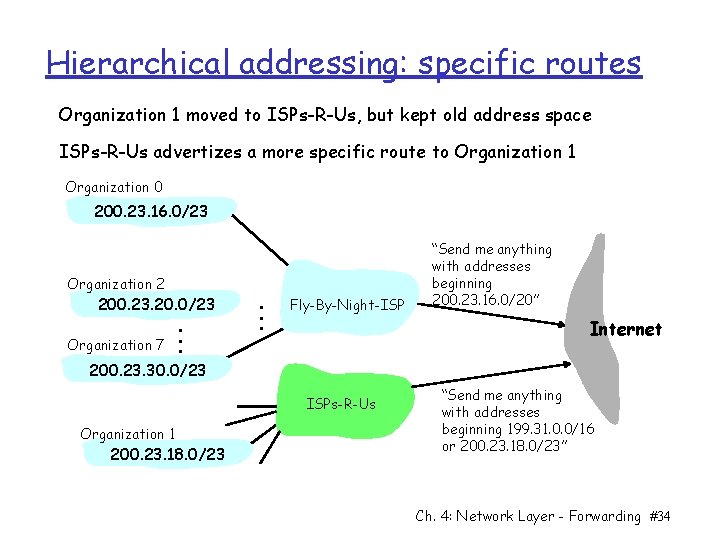
Hierarchical addressing: specific routes Organization 1 moved to ISPs-R-Us, but kept old address space ISPs-R-Us advertizes a more specific route to Organization 1 Organization 0 200. 23. 16. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us Organization 1 200. 23. 18. 0/23 “Send me anything with addresses beginning 199. 31. 0. 0/16 or 200. 23. 18. 0/23” Ch. 4: Network Layer - Forwarding #34

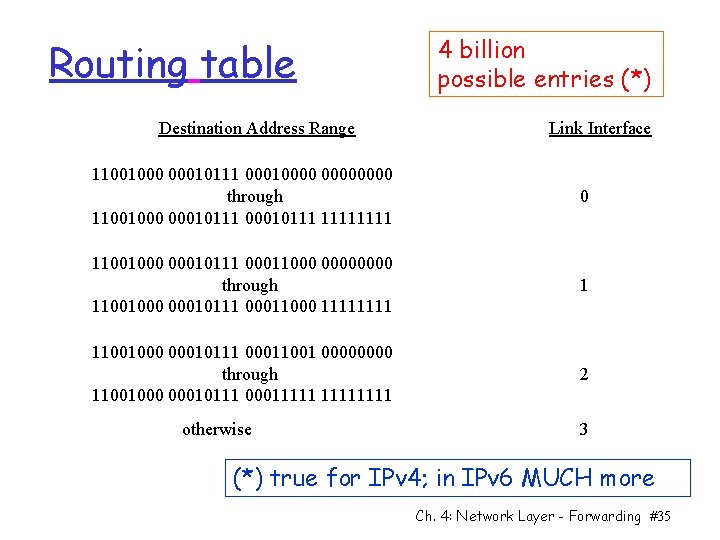
Routing table Destination Address Range 4 billion possible entries (*) Link Interface 11001000 00010111 00010000 through 11001000 00010111 1111 0 11001000 00010111 00011000 0000 through 11001000 00010111 00011000 1111 1 11001000 00010111 00011001 0000 through 11001000 00010111 00011111 2 otherwise 3 (*) true for IPv 4; in IPv 6 MUCH more Ch. 4: Network Layer - Forwarding #35

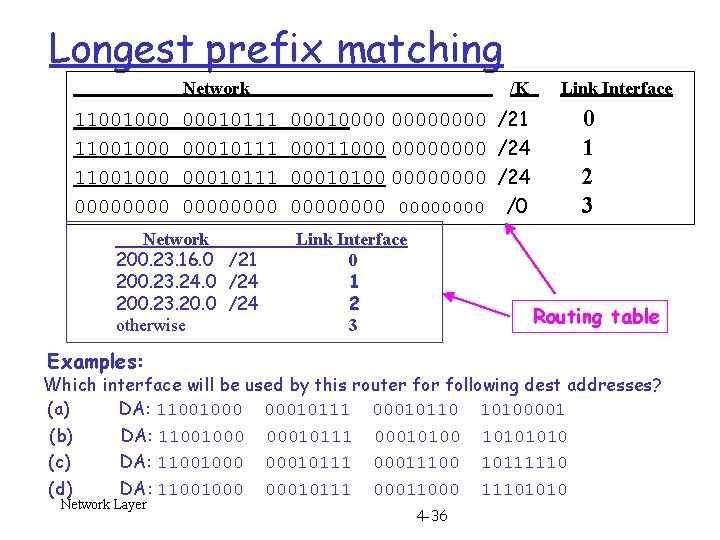
Longest prefix matching Network 11001000 0000 /K 00010111 0000 Network 200. 23. 16. 0 /21 200. 23. 24. 0 /24 200. 23. 20. 0 /24 otherwise 00010000 00011000 0000 00010100 00000000 Link Interface 0 1 2 3 Link Interface /21 /24 /0 0 1 2 3 Routing table Examples: Which interface will be used by this router following dest addresses? (a) DA: 11001000 00010111 00010110 10100001 (b) DA: 11001000 00010111 00010100 1010 (c) DA: 11001000 00010111 00011100 10111110 (d) DA: 11001000 Network Layer 00010111 00011000 4 -36 11101010

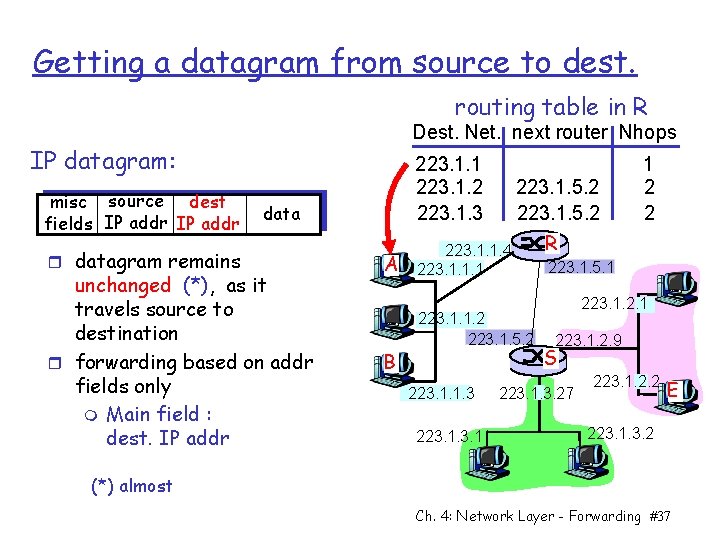
Getting a datagram from source to dest. routing table in R Dest. Net. next router Nhops IP datagram: misc source dest fields IP addr r datagram remains 223. 1. 1 223. 1. 2 223. 1. 3 data unchanged (*), as it travels source to destination r forwarding based on addr fields only m Main field : dest. IP addr A B 223. 1. 5. 2 R 223. 1. 1. 4 223. 1. 5. 1 223. 1. 1. 2 223. 1. 5. 2 223. 1. 1. 3 223. 1 1 2 2 223. 1. 2. 1 223. 1. 2. 9 S 223. 1. 3. 27 223. 1. 2. 2 E 223. 1. 3. 2 (*) almost Ch. 4: Network Layer - Forwarding #37

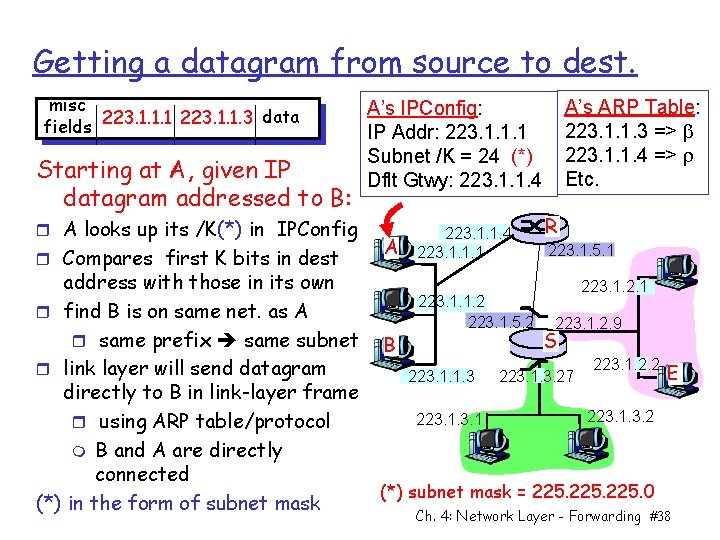
Getting a datagram from source to dest. misc data fields 223. 1. 1. 1 223. 1. 1. 3 Starting at A, given IP datagram addressed to B: r A looks up its /K(*) in IPConfig r Compares first K bits in dest address with those in its own r find B is on same net. as A r same prefix same subnet r link layer will send datagram directly to B in link-layer frame r using ARP table/protocol m B and A are directly connected (*) in the form of subnet mask A’s ARP Table: 223. 1. 1. 3 => 223. 1. 1. 4 => Etc. A’s IPConfig: IP Addr: 223. 1. 1. 1 Subnet /K = 24 (*) Dflt Gtwy: 223. 1. 1. 4 A B 223. 1. 1. 4 223. 1. 1. 1 223. 1. 1. 2 223. 1. 5. 2 223. 1. 1. 3 223. 1 R 223. 1. 5. 1 223. 1. 2. 9 S 223. 1. 3. 27 223. 1. 2. 2 E 223. 1. 3. 2 (*) subnet mask = 225. 0 Ch. 4: Network Layer - Forwarding #38

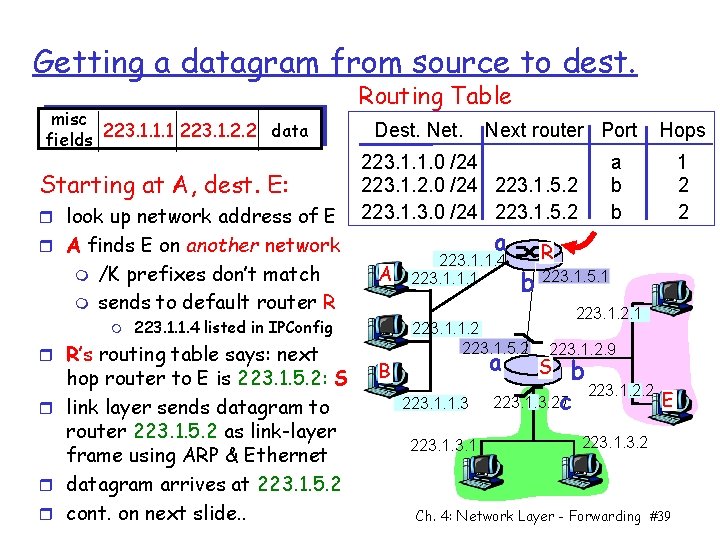
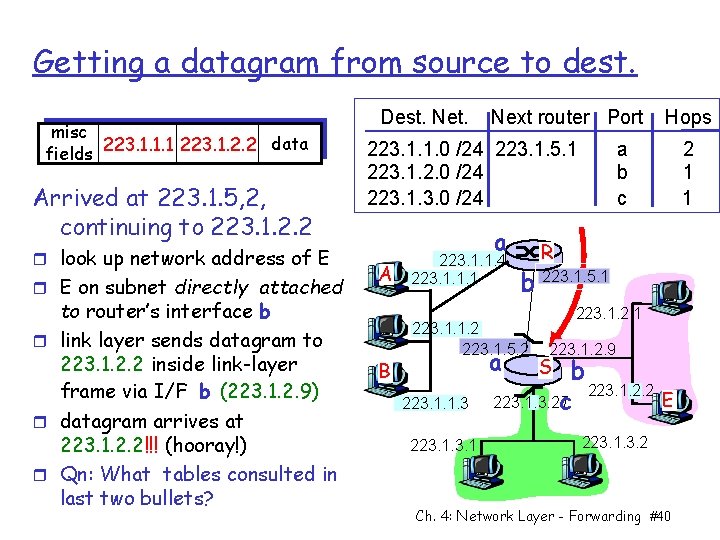
Getting a datagram from source to dest. misc data fields 223. 1. 1. 1 223. 1. 2. 2 Starting at A, dest. E: r look up network address of E Routing Table Dest. Net. 223. 1. 1. 0 /24 223. 1. 2. 0 /24 223. 1. 5. 2 223. 1. 3. 0 /24 223. 1. 5. 2 a r A finds E on another network m m /K prefixes don’t match sends to default router R m A 223. 1. 1. 4 listed in IPConfig r R’s routing table says: next hop router to E is 223. 1. 5. 2: S r link layer sends datagram to router 223. 1. 5. 2 as link-layer frame using ARP & Ethernet r datagram arrives at 223. 1. 5. 2 r cont. on next slide. . Next router Port B 223. 1. 1. 4 223. 1. 1. 1 223. 1. 1. 3 223. 1 a b b R b 223. 1. 5. 1 223. 1. 1. 2 223. 1. 5. 2 a Hops 223. 1. 2. 1 223. 1. 2. 9 b 223. 1. 2. 2 E 223. 1. 3. 27 c S 223. 1. 3. 2 Ch. 4: Network Layer - Forwarding #39 1 2 2

Getting a datagram from source to dest. misc data fields 223. 1. 1. 1 223. 1. 2. 2 Arrived at 223. 1. 5, 2, continuing to 223. 1. 2. 2 r look up network address of E r E on subnet directly attached to router’s interface b r link layer sends datagram to 223. 1. 2. 2 inside link-layer frame via I/F b (223. 1. 2. 9) r datagram arrives at 223. 1. 2. 2!!! (hooray!) r Qn: What tables consulted in last two bullets? Dest. Net. Next router Port 223. 1. 1. 0 /24 223. 1. 5. 1 223. 1. 2. 0 /24 223. 1. 3. 0 /24 a A B 223. 1. 1. 4 223. 1. 1. 1 223. 1. 1. 3 223. 1 a b c R b 223. 1. 5. 1 223. 1. 1. 2 223. 1. 5. 2 a Hops 223. 1. 2. 1 223. 1. 2. 9 b 223. 1. 2. 2 E 223. 1. 3. 27 c S 223. 1. 3. 2 Ch. 4: Network Layer - Forwarding #40 2 1 1

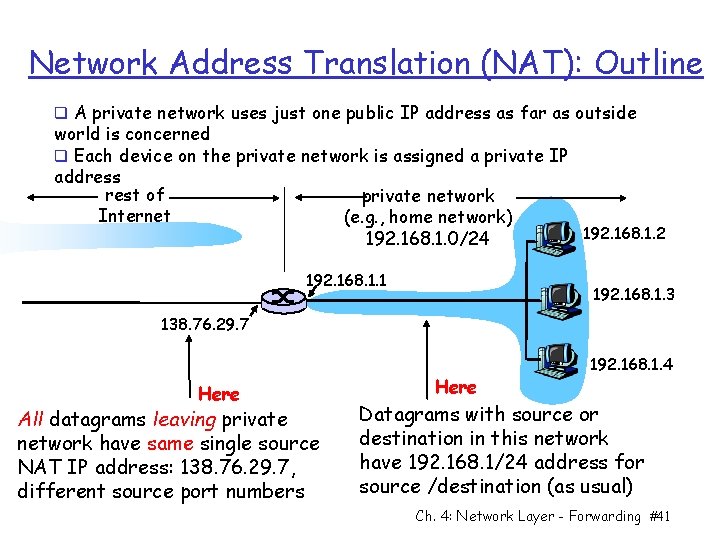
Network Address Translation (NAT): Outline q A private network uses just one public IP address as far as outside world is concerned q Each device on the private network is assigned a private IP address rest of private network Internet (e. g. , home network) 192. 168. 1. 2 192. 168. 1. 0/24 192. 168. 1. 1 192. 168. 1. 3 138. 76. 29. 7 Here All datagrams leaving private network have same single source NAT IP address: 138. 76. 29. 7, different source port numbers Here 192. 168. 1. 4 Datagrams with source or destination in this network have 192. 168. 1/24 address for source /destination (as usual) Ch. 4: Network Layer - Forwarding #41

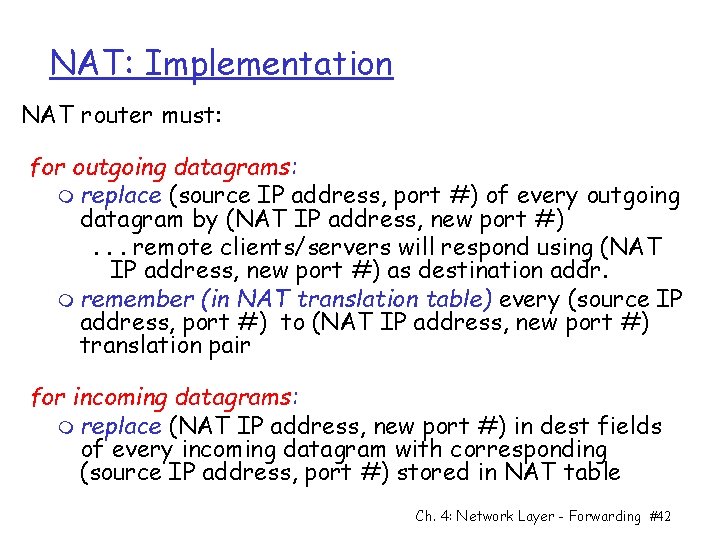
NAT: Implementation NAT router must: for outgoing datagrams: m replace (source IP address, port #) of every outgoing datagram by (NAT IP address, new port #). . . remote clients/servers will respond using (NAT IP address, new port #) as destination addr. m remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair for incoming datagrams: m replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table Ch. 4: Network Layer - Forwarding #42

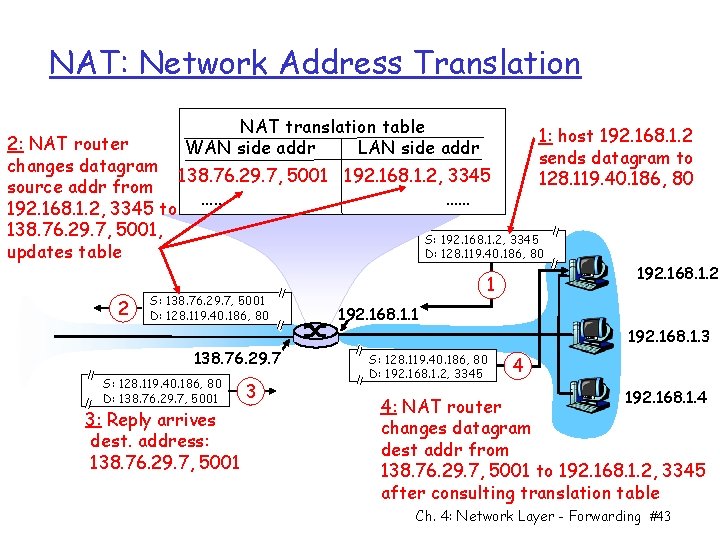
NAT: Network Address Translation NAT translation table WAN side addr LAN side addr 1: host 192. 168. 1. 2 2: NAT router sends datagram to changes datagram 138. 76. 29. 7, 5001 192. 168. 1. 2, 3345 128. 119. 40. 186, 80 source addr from …… …… 192. 168. 1. 2, 3345 to 138. 76. 29. 7, 5001, S: 192. 168. 1. 2, 3345 D: 128. 119. 40. 186, 80 updates table 2 S: 138. 76. 29. 7, 5001 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5001 3: Reply arrives dest. address: 138. 76. 29. 7, 5001 3 192. 168. 1. 2 1 192. 168. 1. 1 S: 128. 119. 40. 186, 80 D: 192. 168. 1. 2, 3345 192. 168. 1. 3 4 192. 168. 1. 4 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 192. 168. 1. 2, 3345 after consulting translation table Ch. 4: Network Layer - Forwarding #43

NAT: Advantages r No need to be allocated range of addresses from ISP: - just one public IP address is used for all devices m 16 -bit port-number field allows 60, 000 simultaneous connections with a single LAN-side address ! m can change ISP without changing addresses of devices in private network m can change addresses of devices in private network without notifying outside world r Devices inside private net not explicitly addressable, visible by outside world (a security plus) Ch. 4: Network Layer - Forwarding #44

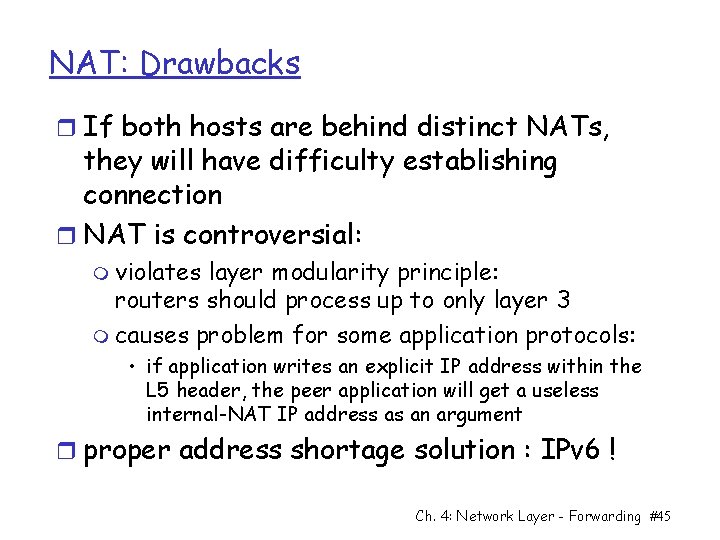
NAT: Drawbacks r If both hosts are behind distinct NATs, they will have difficulty establishing connection r NAT is controversial: m violates layer modularity principle: routers should process up to only layer 3 m causes problem for some application protocols: • if application writes an explicit IP address within the L 5 header, the peer application will get a useless internal-NAT IP address as an argument r proper address shortage solution : IPv 6 ! Ch. 4: Network Layer - Forwarding #45

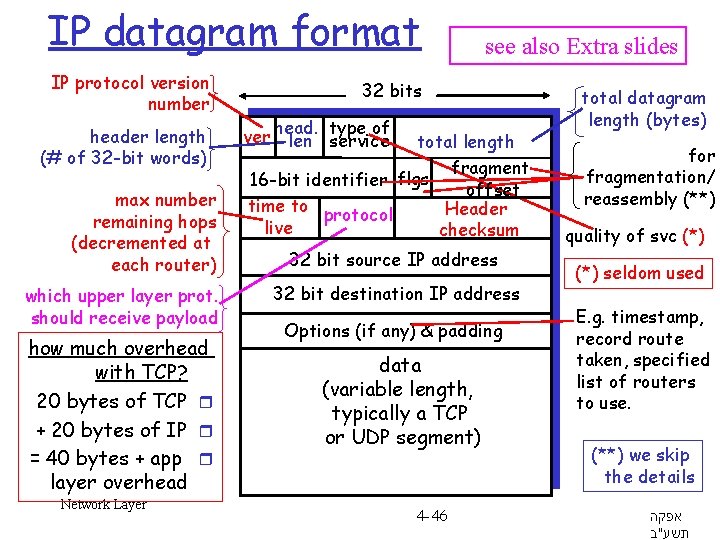
IP datagram format IP protocol version number header length (# of 32 -bit words) max number remaining hops (decremented at each router) which upper layer prot. should receive payload how much overhead with TCP? 20 bytes of TCP r + 20 bytes of IP r = 40 bytes + app r layer overhead Network Layer see also Extra slides 32 bits type of ver head. len service total length fragment 16 -bit identifier flgs offset time to protocol Header live checksum 32 bit source IP address 32 bit destination IP address Options (if any) & padding data (variable length, typically a TCP or UDP segment) 4 -46 total datagram length (bytes) for fragmentation/ reassembly (**) quality of svc (*) seldom used E. g. timestamp, record route taken, specified list of routers to use. (**) we skip the details אפקה תשע"ב

IPv 6 r Initial motivation: 32 -bit address space soon to be completely allocated. r Additional motivation: m IPv 6 header format helps speed processing r IPv 6 datagram format: m 16 -byte (128 bit) IP address m fixed-length 40 byte header • no options allowed inside the header • each option gets its own header after the main IP header m fragmentation discouraged • allowed only using an options header Network Layer 4 -47

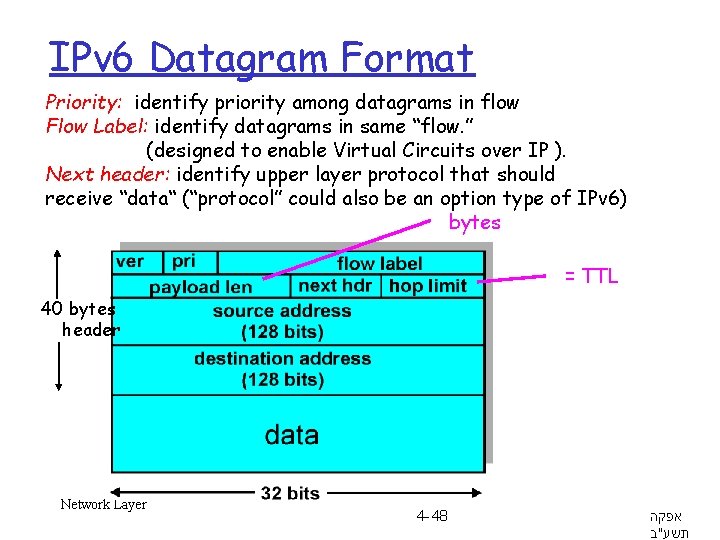
IPv 6 Datagram Format Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow. ” (designed to enable Virtual Circuits over IP ). Next header: identify upper layer protocol that should receive “data“ (“protocol” could also be an option type of IPv 6) bytes = TTL 40 bytes header Network Layer 4 -48 אפקה תשע"ב

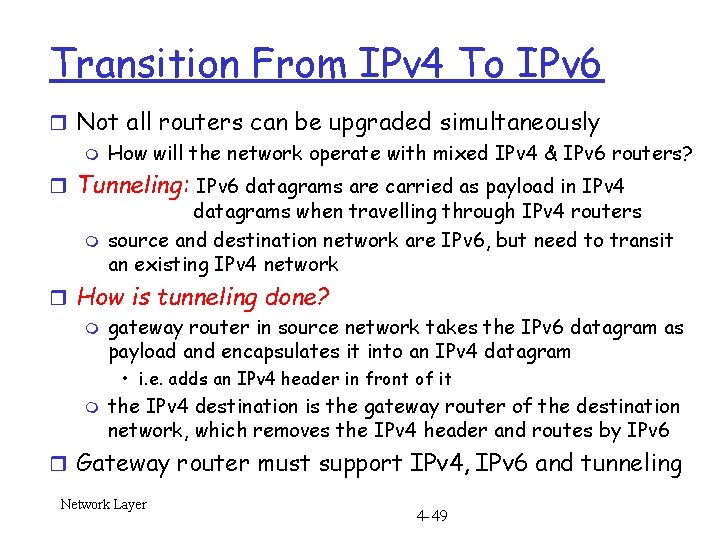
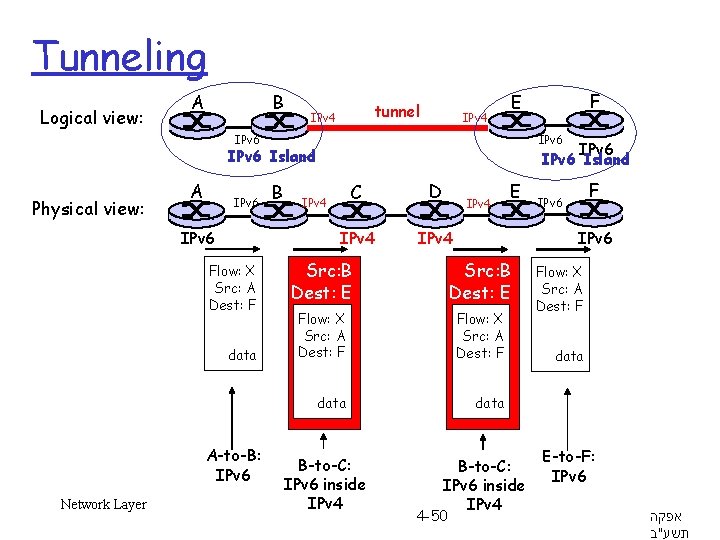
Transition From IPv 4 To IPv 6 r Not all routers can be upgraded simultaneously m How will the network operate with mixed IPv 4 & IPv 6 routers? r Tunneling: IPv 6 datagrams are carried as payload in IPv 4 datagrams when travelling through IPv 4 routers m source and destination network are IPv 6, but need to transit an existing IPv 4 network r How is tunneling done? m gateway router in source network takes the IPv 6 datagram as payload and encapsulates it into an IPv 4 datagram • i. e. adds an IPv 4 header in front of it m the IPv 4 destination is the gateway router of the destination network, which removes the IPv 4 header and routes by IPv 6 r Gateway router must support IPv 4, IPv 6 and tunneling Network Layer 4 -49

Tunneling Logical view: A B tunnel IPv 4 IPv 6 Island IPv 6 Island Physical view: A IPv 6 Flow: X Src: A Dest: F data A-to-B: IPv 6 Network Layer B F E C D IPv 4 E IPv 6 Src: B Dest: E Flow: X Src: A Dest: F data B-to-C: IPv 6 inside IPv 4 4 -50 F IPv 6 Flow: X Src: A Dest: F data E-to-F: IPv 6 אפקה תשע"ב

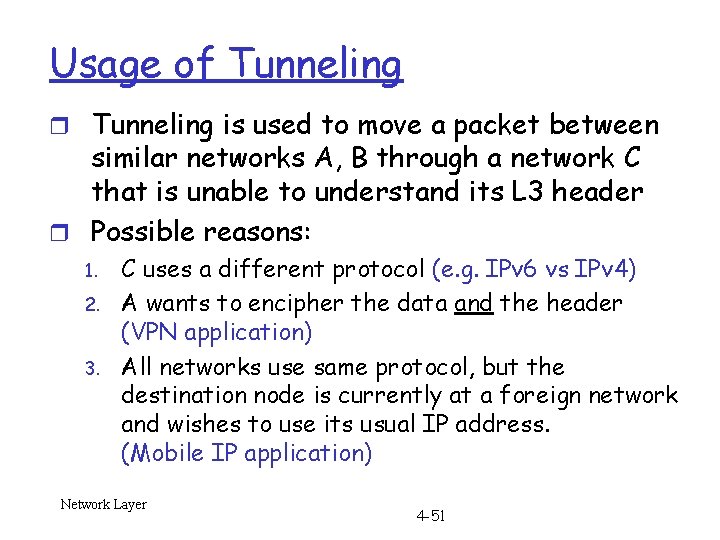
Usage of Tunneling r Tunneling is used to move a packet between similar networks A, B through a network C that is unable to understand its L 3 header r Possible reasons: 1. 2. 3. C uses a different protocol (e. g. IPv 6 vs IPv 4) A wants to encipher the data and the header (VPN application) All networks use same protocol, but the destination node is currently at a foreign network and wishes to use its usual IP address. (Mobile IP application) Network Layer 4 -51

IPv 6 status report r Operating systems – m wide support – early 2000 m Windows (2000, XP, Vista), BSD, Linux, Apple r Networking infrastructure m Cisco r Deployment m Slow r Penetration m Host - minor (less than 1%) m Used in 2008 in China Olympic games r Motivation: CIDR & NAT Ch. 4: Network Layer - Forwarding #52

Extra Ch. 4: Network Layer - Forwarding #53

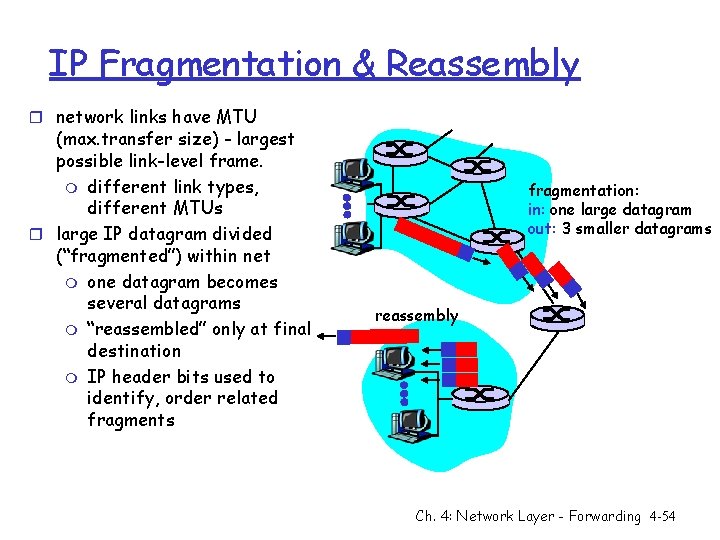
IP Fragmentation & Reassembly r network links have MTU (max. transfer size) - largest possible link-level frame. m different link types, different MTUs r large IP datagram divided (“fragmented”) within net m one datagram becomes several datagrams m “reassembled” only at final destination m IP header bits used to identify, order related fragments fragmentation: in: one large datagram out: 3 smaller datagrams reassembly Ch. 4: Network Layer - Forwarding 4 -54

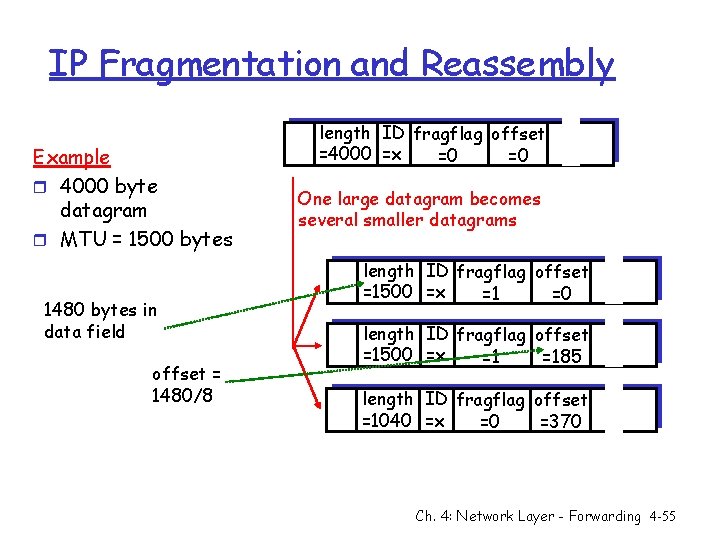
IP Fragmentation and Reassembly Example r 4000 byte datagram r MTU = 1500 bytes 1480 bytes in data field offset = 1480/8 length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =185 length ID fragflag offset =1040 =x =0 =370 Ch. 4: Network Layer - Forwarding 4 -55

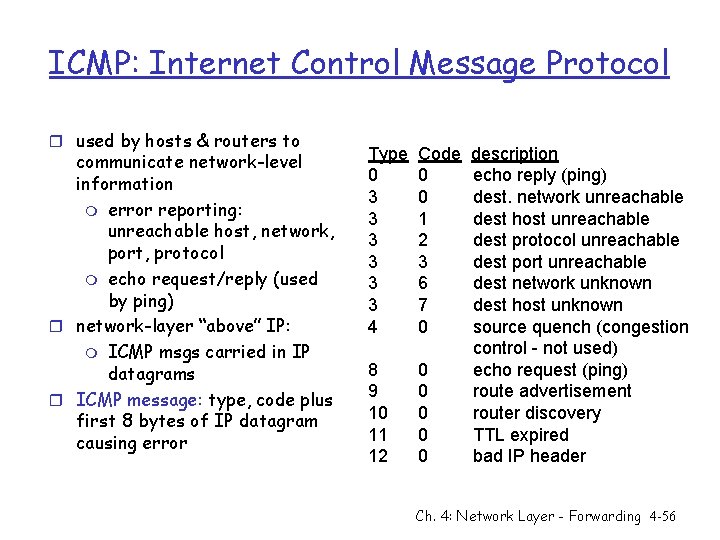
ICMP: Internet Control Message Protocol r used by hosts & routers to communicate network-level information m error reporting: unreachable host, network, port, protocol m echo request/reply (used by ping) r network-layer “above” IP: m ICMP msgs carried in IP datagrams r ICMP message: type, code plus first 8 bytes of IP datagram causing error Type 0 3 3 3 4 Code 0 0 1 2 3 6 7 0 8 9 10 11 12 0 0 0 description echo reply (ping) dest. network unreachable dest host unreachable dest protocol unreachable dest port unreachable dest network unknown dest host unknown source quench (congestion control - not used) echo request (ping) route advertisement router discovery TTL expired bad IP header Ch. 4: Network Layer - Forwarding 4 -56

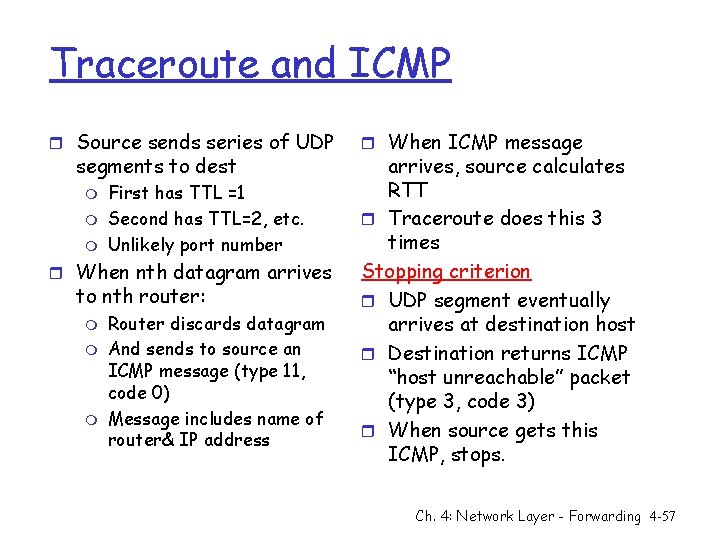
Traceroute and ICMP r Source sends series of UDP segments to dest m m m First has TTL =1 Second has TTL=2, etc. Unlikely port number r When nth datagram arrives to nth router: m m m Router discards datagram And sends to source an ICMP message (type 11, code 0) Message includes name of router& IP address r When ICMP message arrives, source calculates RTT r Traceroute does this 3 times Stopping criterion r UDP segment eventually arrives at destination host r Destination returns ICMP “host unreachable” packet (type 3, code 3) r When source gets this ICMP, stops. Ch. 4: Network Layer - Forwarding 4 -57

Exercise 1 Answers 11001000 00010111 0001 10110101 128 64 32 16 8 4 2 1 27 2 6 2 5 2 4 2 3 2 2 21 2 0 /23 128 64 32 16 8 4 2 1 27 2 6 2 5 2 4 2 3 2 2 21 2 0 Ans 1: 11001000 00010111 0001 10110101 =200. 23. 17. 181 128+64+8= 200 16+7= 23 16+1= 17 128+32+16+5= 181 Ans 2: 111111110 0000 = 255. 254. 0 255 -1 = 254 Ans 3: 11001000 00010111 0001 10110101 NETWORK HOST Ch. 4: Network Layer Forwarding 4 -58

Exercise 2 Answers 11001000 00010111 0001 10110101 /23 NETWORK Ans 1: 11001000 00010111 00010000 = 200. 23. 16. 0 Ans 2: 11001000 00010111 0001 1111 = 200. 23. 17. 255 Ans 3: 29 -2 = 510 hosts Ans 4: network: 200. 23. 16. 0/23 host: 200. 23. 17. 181/23 Ans 5: first host address: 200. 23. 16. 1/23 last host address: 200. 23. 17. 254/23 Ch. 4: Network Layer Forwarding 4 -59