NETWORK ISSUES AND COMMUNICATION Security issues regarding data









































- Slides: 49

NETWORK ISSUES AND COMMUNICATION

Security issues regarding data transfer � � o o o Describe the security issues surrounding the use of computer networks Using a computer connected to a network means that… The computer is vulnerable to hackers If the network breaks, many tasks become very difficult Your computer can more easily be attacked by a virus

Security issues regarding data transfer � o o o In particular, if we use a computer connected to The Internet… We have to be careful about revealing personal information We have to be careful to avoid websites that might contain malware We have to be aware that information found on The Internet is not always accurate or reliable

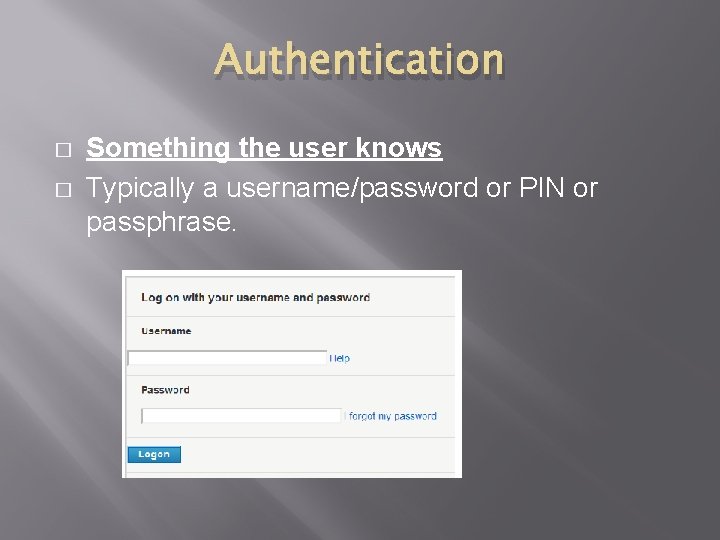
Authentication is how a user can prove who they are in order to access a system. It can be done in a number of ways the most common being username and password. � There are generally three factors that are considered for authentication: ○ Something the user knows ○ Something the user has ○ Something the user is �

Authentication � � Something the user knows Typically a username/password or PIN or passphrase.

Authentication � � � Something the user has This can be physical things such as a mobile phone, card with a chip, password authenticator. These are often used in addition to username/password authentication to give a more secure two factor authentication process. This is used by many services such as Google

Authentication � � � Something the user is. This includes such biometric data as fingerprints, iris patterns, face shapes, voice etc. Passwords In order to stay secure it is important to choose a password that is very hard to guess to keep you secure. This will help to prevent someone being able to either guess your password or to use a computer to brute force hack your password.

Authentication � o o � � How to make a strong password: Make it long (20 characters is a strong length). Include both uppercase and lowercase letters. Include symbols and other characters. Should not be a word in the dictionary ‘Weak’ passwords: password, 123456, david, 27 dec 1992 ‘Strong’ passwords: s 63 g. Rdd 1, G 66 ew$d. Q, gdr 298783 X

Authentication � o o o There is more to security than just choosing a good password you should also consider: Do not use the same password for sites that you care about. EG consider using programs such as Keepass or Last. Pass to manage your passwords. Beware that your “secret question” is not easy to guess. If a site offers “two step” verification then you should use it. EG Google’s two step authentication.

Authentication � � Other Authentication methods Magnetic strip cards allow the user to authenticate themselves by swiping through a reader. They are often used to unlock doors or provide access to certain areas of buildings. However the strip may be easily damaged and if stolen or lost this can cause a security issue.

Authentication � � ID Cards ID cards are used in most countries to identify a person officially, they often contain personal data such as date of birth and nationality and address. They also have signatures and pictures to confirm the person is who they say they are. They can be forged but this requires great skill to do effectively.

Authentication � � � Passports like ID cards are used to prove someone is who they say they are. They are recognised globally and allow people to travel into different countries. Mobile phone A mobile phone is often used to authenticate as part of a two step process. For example after you use a username and password to login to a website an SMS is also sent to the phone with a code that also need to be entered to gain access. Many email and social networking sites use this.

Authentication � � � Password tokens are often given to employees of businesses to generate one time login credentials for business systems. They are secure as the code can only be used once but if they are stolen it can be inconvenient and a security problem.

Malware and Antiviruses � � Antivirus An application software used by computer users to combat viruses and malware. What is malware? Malware is the name given to any software that could harm a computer system, interfere with a user's data, or make the computer perform actions without the owner's knowledge or permission.

Malware and Antiviruses � � � Adware: The least dangerous and most lucrative Malware. Adware displays ads on your computer. Spyware: Spyware is software that spies on you, tracking your internet activities in order to send advertising (Adware) back to your system. Virus: A virus is a contagious program or code that attaches itself to another piece of software, and then reproduces itself when that software is run. Most often this is spread by sharing software or files between computers.

Malware and Antiviruses � � Worm: A program that replicates itself and destroys data and files on the computer. Worms work to “eat” the system operating files and data files until the drive is empty. Trojan: The most dangerous Malware. Trojans are written with the purpose of discovering your financial information, taking over your computer’s system resources, and in larger systems creating a “denial-of-service attack ” Denial-of-service attack: an attempt to make a machine or network resource unavailable to those attempting to reach it. Example: AOL, Yahoo or your business network becoming unavailable.

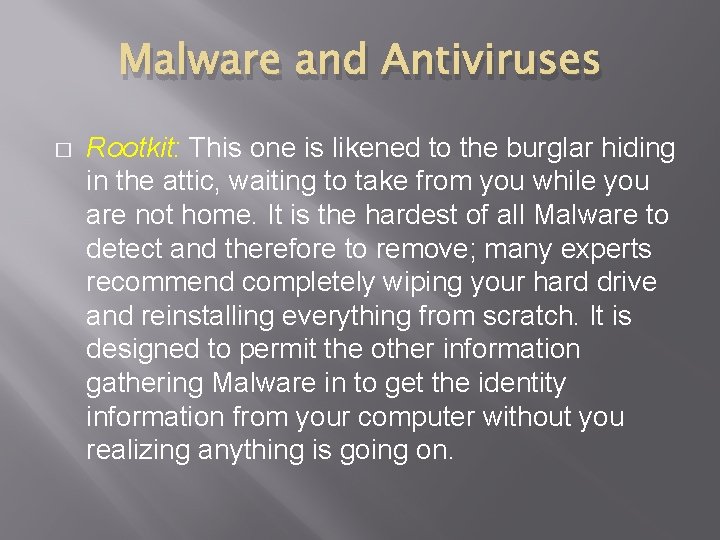
Malware and Antiviruses � Rootkit: This one is likened to the burglar hiding in the attic, waiting to take from you while you are not home. It is the hardest of all Malware to detect and therefore to remove; many experts recommend completely wiping your hard drive and reinstalling everything from scratch. It is designed to permit the other information gathering Malware in to get the identity information from your computer without you realizing anything is going on.

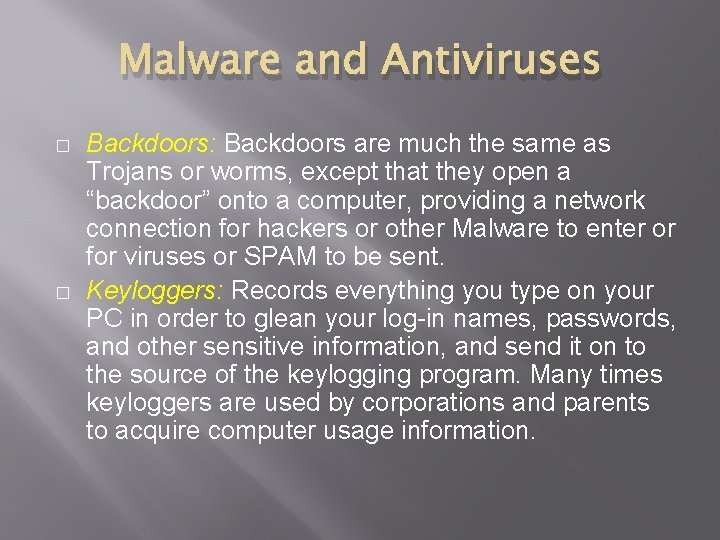
Malware and Antiviruses � � Backdoors: Backdoors are much the same as Trojans or worms, except that they open a “backdoor” onto a computer, providing a network connection for hackers or other Malware to enter or for viruses or SPAM to be sent. Keyloggers: Records everything you type on your PC in order to glean your log-in names, passwords, and other sensitive information, and send it on to the source of the keylogging program. Many times keyloggers are used by corporations and parents to acquire computer usage information.

Malware and Antiviruses � Rogue security software: This one deceives or misleads users. It pretends to be a good program to remove Malware infections, but all the while it is the Malware. Often it will turn off the real Anti-Virus software.

Malware and Antiviruses � � Ransom-ware: If you see this screen that warns you that you have been locked out of your computer until you pay for your cybercrimes. Your system is severely infected with a form of Malware called Ransom-ware. It is not a real notification from the FBI, but, rather an infection of the system itself. Even if you pay to unlock the system, the system is unlocked, but you are not free of it locking you out again. The request for money, usually in the hundreds of dollars is completely fake.

Malware and Antiviruses � Browser Hijacker: When your homepage changes to one that looks like those in the images inserted next, you may have been infected with one form or another of a Browser Hijacker. This dangerous Malware will redirect your normal search activity and give you the results the developers want you to see. Its intention is to make money off your web surfing. Using this homepage and not removing the Malware lets the source developers capture your surfing interests. This is especially dangerous when banking or shopping online. These homepages can look harmless, but in every case they allow other more infectious

Malware and Antiviruses � � o o o How do you get malware? There are many ways to get malware such as: Installing software from an untrustworthy source. You are not using an antivirus or antispyware solution. Sharing pen drives that are infected with a virus. Connecting to a network that is infected. Visiting disreputable websites. Additional software gets installed during the install of trustworthy software.

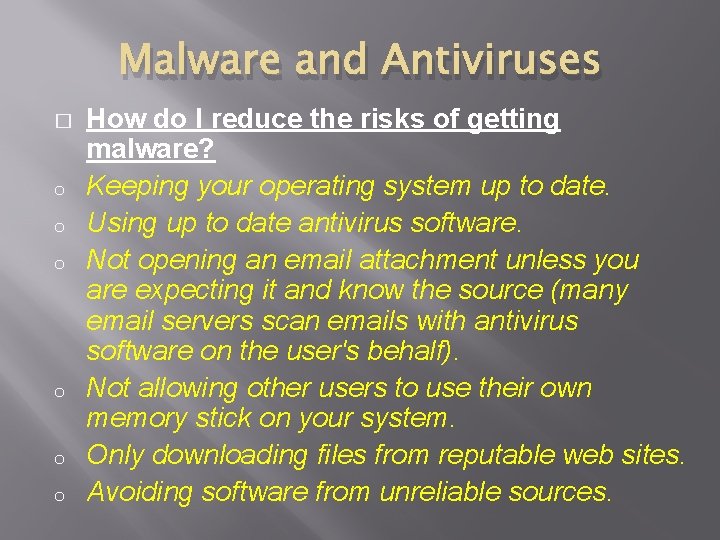
Malware and Antiviruses � o o o How do I reduce the risks of getting malware? Keeping your operating system up to date. Using up to date antivirus software. Not opening an email attachment unless you are expecting it and know the source (many email servers scan emails with antivirus software on the user's behalf). Not allowing other users to use their own memory stick on your system. Only downloading files from reputable web sites. Avoiding software from unreliable sources.

Malware and Antiviruses � � How does antivirus work? Real Time Scanning Antivirus software runs in the background on your computer, checking every file you open. This is generally known as on access scanning, background scanning, resident scanning realtime protection, or something else, depending on your antivirus program.

Malware and Antiviruses � � � Full system scanning A full system scan is helpful when you’ve just installed an antivirus program – it ensures there are no viruses lying dormant on your computer. Most antivirus programs set up scheduled full system scans, often once a week. This ensures that the latest virus definition files are used to scan your system for dormant viruses.

Malware and Antiviruses � � � Virus definitions Your antivirus software relies on virus definitions to detect malware. That’s why it automatically downloads new, updated definition files – once a day or even more often. Heuristics Antivirus programs also employ heuristics. Heuristics allow an antivirus program to identify new or modified types of malware, even without virus definition files. It looks for patterns or strange behaviour that is like a virus

Encryption � � � Encryption and its use The translation of data into a secret code. Process of encoding messages or information in such a way that only authorized parties can read it. It does not prevent interception, but denies the message content to the interceptor. Encryption is the most effective way to achieve data security. To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. Unencrypted data is called plain text ; encrypted data is referred to as cipher text

Encryption � o o � � � There are two main types of encryption: asymmetric encryption (also called public key encryption) symmetric encryption Symmetric encryption A secret key, which can be a number, a word, or just a string of random letters, is applied to the text of a message to change the content in a particular way. This might be as simple as shifting each letter by a number of places in the alphabet. As long as both sender and recipient know the secret key, they can encrypt and decrypt all messages that use this key. The problem with secret keys is exchanging them over the Internet or a large network while preventing them from falling into the wrong hands. Anyone who knows the secret key can decrypt the message.

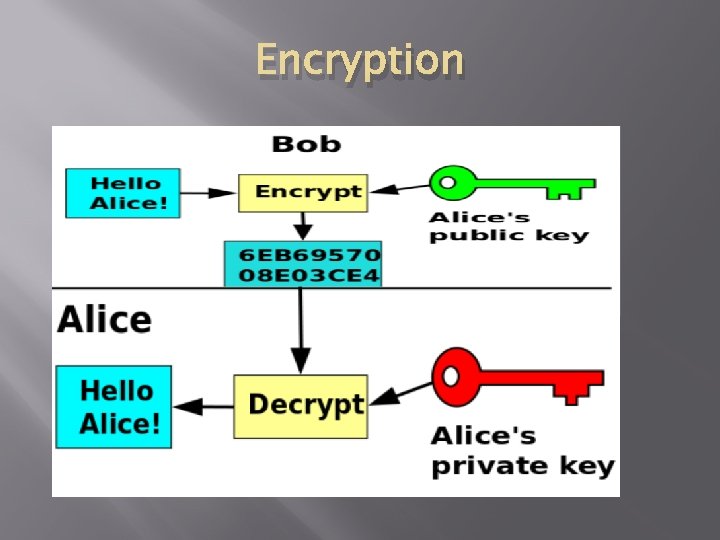
Encryption � � Asymmetric encryption A public key is made freely available to anyone who might want to send you a message. A second, private key is kept secret, so that only you know it. Any message (text, binary files, or documents) that are encrypted by using the public key can only be decrypted by applying the same algorithm, but by using the matching private key. Any message that is encrypted by using the private key can only be decrypted by using the matching public key. This means that you do not have to worry about passing public keys over the Internet (the keys are supposed to be public). A problem with asymmetric encryption, however, is that it is slower than symmetric encryption. It requires far more processing power to both encrypt and decrypt the content of the message.

Encryption

Encryption � � � Digital Certificates To use asymmetric encryption, there must be a way for people to discover other public keys. The typical technique is to use digital certificates (also known simply as certificates). A certificate is a package of information that identifies a user or a server, and contains information such as the organization name, the organization that issued the certificate, the user's email address and country, and the user's public key. When a server and client require a secure encrypted communication, they send a query over the network to the other party, which sends back a copy of the certificate. The other party's public key can be extracted from the certificate. A certificate can also be used to uniquely identify the holder.

Data protection act � � � The Data Protection Act controls how your personal information is used by organisations, businesses or the government. Everyone responsible for using data has to follow strict rules called 'data protection principles‘ First principle - Personal data shall be processed fairly and lawfully and, in particular, shall not be processed unless at least one of the conditions in Schedule 2 is met and in the case of sensitive personal data, at least one of the conditions set out in Schedule 3 or either of the two Statutory Instruments below is met.

Data protection act � � Second principle - Personal data shall be obtained only for one or more specified and lawful purposes, and shall not be further processed in any manner incompatible with that purpose or those purposes. Third principle - Personal data shall be adequate, relevant and not excessive in relation to the purpose or purposes for which they are processed. Fourth principle - Personal data shall be accurate and, where necessary, kept up to date. Fifth principle - Personal data processed for any purpose or purposes shall not be kept for longer than is necessary for that purpose or those purposes.

Data protection act � � � Sixth principle - Personal data shall be processed in accordance with the rights of data subjects under this Act. Seventh principle - Appropriate technical and organisational measures shall be taken against unauthorised or unlawful processing of personal data and against accidental loss or destruction of, or damage to, personal data. Eighth principle - Personal data shall not be transferred to a country or territory outside the European Economic Area, unless that country or territory ensures an adequate level of protection for the rights and freedoms of data subjects in relation to the processing of personal data.

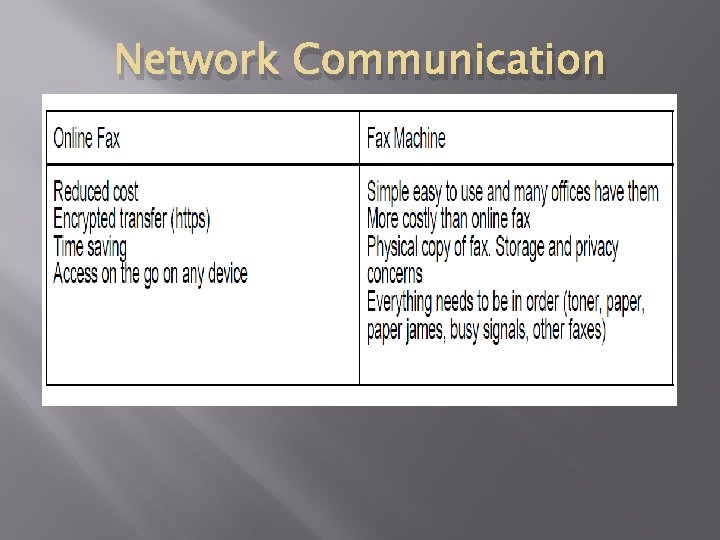
Network Communication Facsimile communication � There are two Two main methods to send faxes ● Online Fax ● Fax machine � Fax is short for ‘facsimile’ which means ‘copy’. � A fax machine is a device that can send a copy of a paper document over the telephone network. �

Network Communication ● The sending fax converts the light/dark areas of the printed document into noises. ● These noises travel through the phone system and are received by another fax machine. ● The receiving fax machine converts the noises into printed marks on a piece of paper making a copy of the original document � Online Fax � Online faxing is sending a fax using an internet connection. � Many online faxing services allow you to send these faxes through your web browser, email application, online account and more.

Network Communication

Network Communication

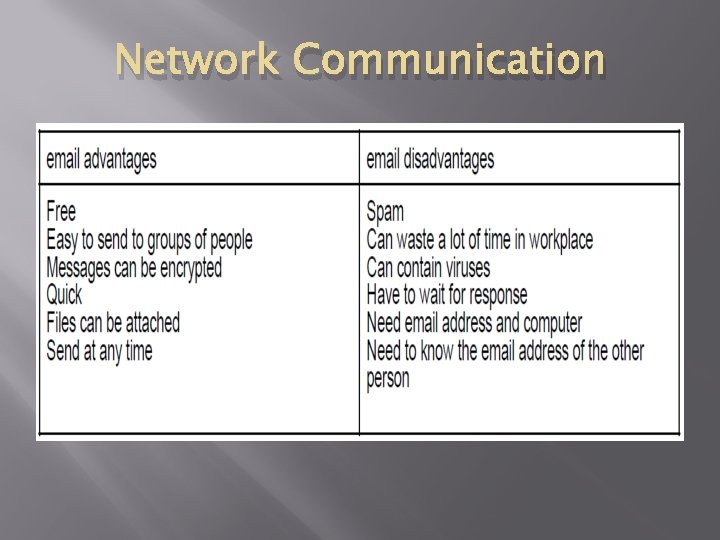
Network Communication email communication and attachments � What is email? ● email stand for electronic mail ● each email has its own mailbox ● emails can contain text, images, links etc. ● emails can have attachments �

Network Communication

Network Communication � v email compared with faxing Faxes are still seen by some as more secure as they are sent from machine to machine and as they travel in analogue signals through the phone line it requires specialist methods to hack. Whereas emails sent unencrypted may be easier to intercept. However these days most emails are encrypted by default and so harder to hack.

Network Communication v v v Emails can be printed from any machine but a fax will only come out in the fax machine so there is less likelihood that the fax can be seen by others. However fax machines are not always kept in secure areas. A fax machine will automatically send confirmation of the fax being received but this is not always the case with an email. You can check if it was delivered but not read. As the fax is printed it is in some cases more likely to be actually read rather than an email which may be deleted or ignored or worse sent to the spam folder.

Network Communication v Signatures can be made on faxes and sent and this provides a legal document. This cannot be done in email. However there are now many ways to make a “digital signature” on an email or other digital document that is equally binding.

Network Communication

Network Communication � � � Video-conferencing Videoconferencing is a system that allows people to have conversations and meetings with other people in different locations, but without leaving their office. A video-conference involves people sitting in front of a camera and a microphone, whilst watching other people on a screen and listening to them through loudspeakers.

Network Communication � ü ü ü � o o o The system uses the following hardware: Video camera Monitor Microphone Loudspeakers High-speed network / Internet connection Video conferencing advantages No travel costs No time wasted travelling to other cities/countries Can organise meetings at short notice Can organise meetings regularly You can see people as well as hear them. This means you can see their body language which you can't do with a telephone call.

Network Communication � ü ü ü Video conferencing disadvantages Can be expensive to buy the equipment May be delay in communication Reliability(technical problems can be a limiting factor) Problems across time zones. There is no substitute for a face-to-face meeting in getting to know someone.

Network Communication � � � ü ü ü Audio-conferencing Audio conference calls allow more than just two people to join the call. There are several common causes of poor quality conference calls: People simply not showing up. Lack of familiarity with behaviour and protocol. Lack of familiarity with equipment and technology. Background noise and disturbances. Poor coordination by call initiator. Lack of moderator.

Network Communication