Medium Access Control in Sensor Networks Huaming Li




- Slides: 57

Medium Access Control in Sensor Networks Huaming Li Electrical and Computer Engineering Michigan Technological University 1

Outline n n Overview S-MAC: an energy-efficient MAC protocol for wireless sensor networks Other MAC Techniques References Computer Engineering Seminar Department of ECE

Medium Access Control in Sensor Networks n Sensor networks q q q n Consist of a set of sensor nodes; Each node is equipped with one or more sensors and is normally battery operated; Nodes communicate with each other via wireless connection. Medium Access Control (MAC) q Fundamental task is to avoid collisions so that two interfering nodes do not transmit at the same time Computer Engineering Seminar Department of ECE

Characteristics of Sensor Network n A special wireless ad hoc network q q q n Large number of nodes Battery powered Topology and density change Nodes for a common task In-network data processing Scalability & Self-configuration Energy efficiency Adaptivity Fairness not important Msg-level Latency Sensor-net applications q q Sensor-triggered bursty traffic Can often tolerate some delay n Adaptivity Trade for energy Speed of a moving object places a bound on network reaction time Computer Engineering Seminar Department of ECE

MAC Protocols Classification Scheduling-Based MAC Protocols n Contention-Based MAC n Collision Free Real Time MAC n Hybrid MAC n Computer Engineering Seminar Department of ECE

Scheduling Based MAC n n n Time is divided into slots Each node knows when to transmit Schedule is predetermined TDMA Synchronization problems Adaptability problems Computer Engineering Seminar Department of ECE

Contention Based MAC n n n Carrier sensing & collision avoidance In-band, out-band handshaking Busy-tone multiple access (BTMA) Multiple access with collision avoidance (MACA) High priority packets Computer Engineering Seminar Department of ECE

Common MAC Protocol Requirements n Quality of service (Qo. S) q q n Decentralized q n Tolerate message loss Support real time guarantees Global information may not be available Flexibility q Diversity of applications Computer Engineering Seminar Department of ECE

MAC Requirements in Sensor Networks n Important requirements of MAC protocols q q q q Collision avoidance Energy efficiency Scalability & Adaptivity Latency Fairness Throughput Bandwidth utilization Computer Engineering Seminar Primary Secondary Department of ECE

Energy Efficiency in MAC Design n n Energy is primary concern What causes energy waste on radio? q q Dominant in sensor networks Long idle time Control packet overhead Overhearing unnecessary traffic Collisions n n bursty traffic in sensor-net apps Idle listening consumes 50— 100% of the power for receiving (Stemm 97, Kasten) Computer Engineering Seminar Department of ECE

S-MAC Design Overview n Tradeoffs Latency Fairness Energy v. Major components in S-MAC • • Periodic listen and sleep Collision avoidance Overhearing avoidance Massage passing Computer Engineering Seminar Department of ECE

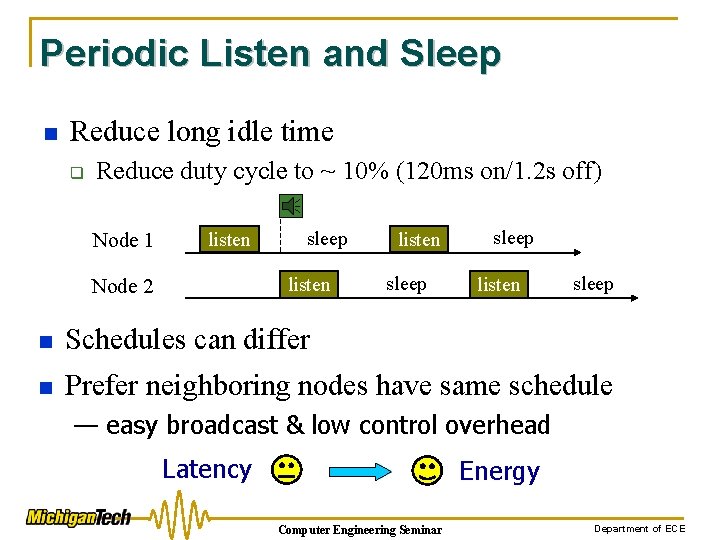
Periodic Listen and Sleep n Reduce long idle time q Reduce duty cycle to ~ 10% (120 ms on/1. 2 s off) Node 1 listen sleep listen Node 2 listen sleep n Schedules can differ n Prefer neighboring nodes have same schedule — easy broadcast & low control overhead Latency Energy Computer Engineering Seminar Department of ECE

Periodic Listen & Sleep n n Nodes are in idle for a long time if no sensing event happens Put nodes into periodic sleep mode q i. e. in each second, sleep for half second and listen for other half second Computer Engineering Seminar Department of ECE

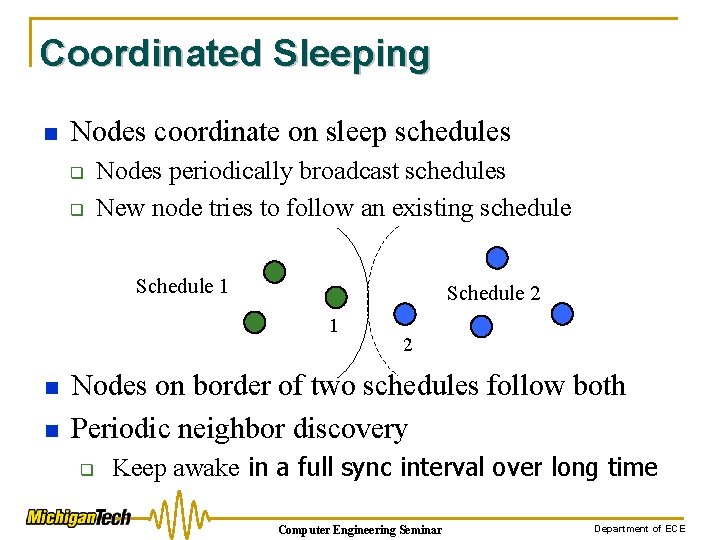
Coordinated Sleeping n Nodes coordinate on sleep schedules q q Nodes periodically broadcast schedules New node tries to follow an existing schedule Schedule 1 Schedule 2 1 n n 2 Nodes on border of two schedules follow both Periodic neighbor discovery q Keep awake in a full sync interval over long time Computer Engineering Seminar Department of ECE

Choose & Maintain Schedule n n Each node maintains a schedule table that stores schedules of all its neighbors Nodes exchange schedules by broadcasting them to its neighbors q Try to synchronize neighboring nodes together Computer Engineering Seminar Department of ECE

Choose Schedule n n n If not hear a schedule from others, the node randomly chooses a schedule and broadcast the schedule If receive a schedule, the node follows that schedule, wait for a random delay then rebroadcast this schedule If receive a different schedule, the node adopt both, broadcast its own schedule Computer Engineering Seminar Department of ECE

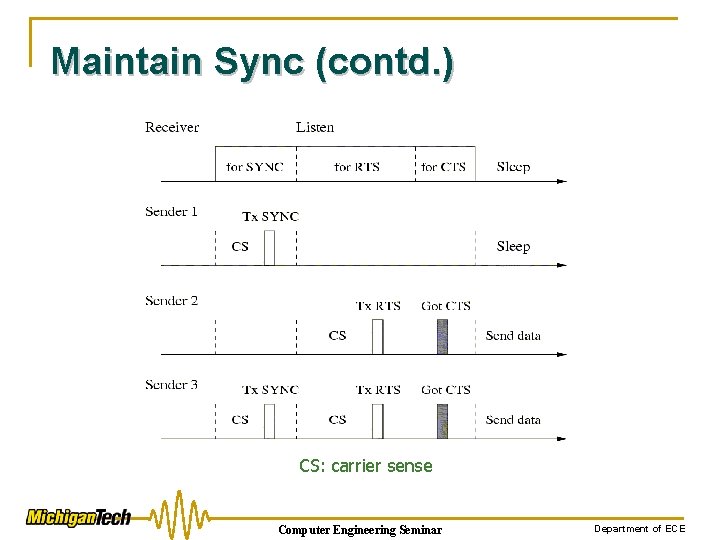
Maintain Synchronization n n Listen/sleep scheme requires synchronization among neighboring nodes Looser synchronization (compared to TDMA) q q q Listen period is significantly longer than clock error or drift Use relative time rather than absolute Update schedule by sending SYNC packets Computer Engineering Seminar Department of ECE

Maintain Sync (contd. ) n Divide listen time into two parts: q q n For receiving SYNC packets For receiving data packets Each part is further divided into many time slots for senders to perform carrier sense Computer Engineering Seminar Department of ECE

Maintain Sync (contd. ) CS: carrier sense Computer Engineering Seminar Department of ECE

Collision Avoidance n n Adopt IEEE 802. 11 collision avoidance Virtual carrier sense q q n n During field Network allocation vector (NAV) Physical carrier sense RTS/CTS exchange (for hidden terminal problem) q q Broadcast packets (SYNC) are sent without RTS/CTS Unicast packets (DATA) are sent with RTS/CTS Computer Engineering Seminar Department of ECE

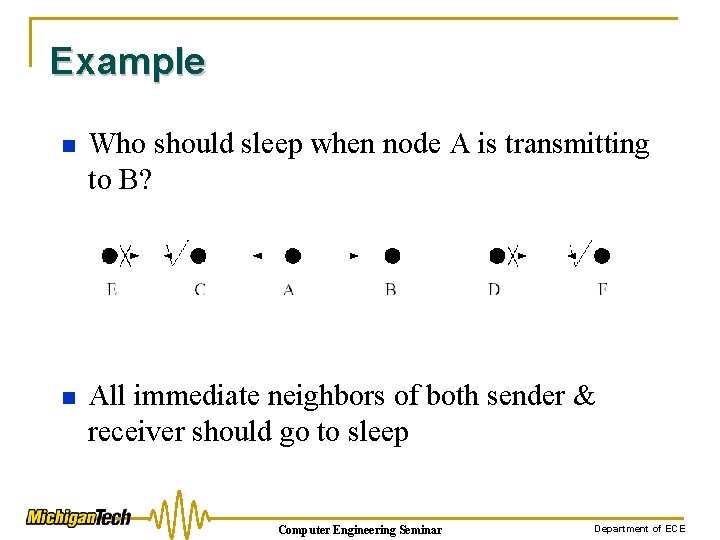
Overhearing Avoidance n n Problem: Receive packets destined to others Solution: Sleep when neighbors talk q q n Basic idea from PAMAS (Singh, Raghavendra 1998) But we only use in-channel signaling Who should sleep? • All immediate neighbors of sender and receiver v. How long to sleep? • The duration field in each packet informs other nodes the sleep interval Computer Engineering Seminar Department of ECE

Example n Who should sleep when node A is transmitting to B? n All immediate neighbors of both sender & receiver should go to sleep Computer Engineering Seminar Department of ECE

Message Passing n n How to efficiently transmit a long message? Single packet vs. fragmentations Single packet: high cost of retransmission if only a few bits have been corrupted q Fragmentations: large control overhead (RTS & CTS for each fragment), longer delay Problem: Sensor network in-network processing requires entire message q n Computer Engineering Seminar Department of ECE

Message Passing n Solution: Don’t interleave different messages q q q n Long message is fragmented & sent in burst RTS/CTS reserve medium for entire message Fragment-level error recovery — ACK — extend Tx time and re-transmit immediately Other nodes sleep for whole message time Fairness Energy Msg-level latency Computer Engineering Seminar Department of ECE

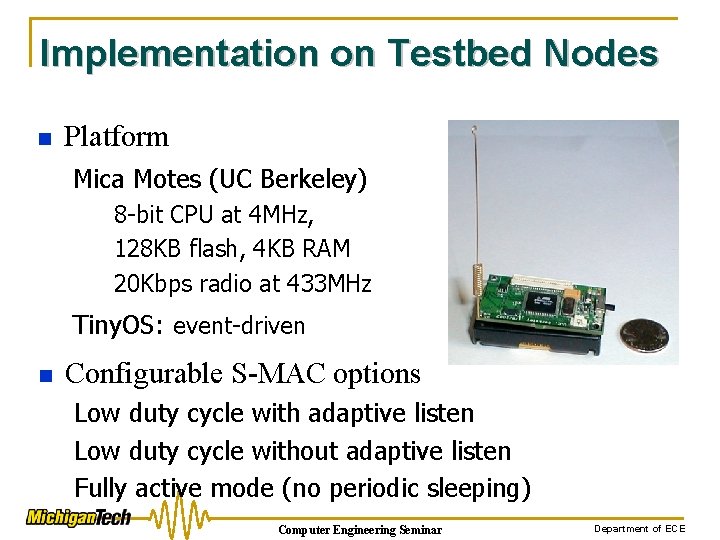
Implementation on Testbed Nodes n Platform Mica Motes (UC Berkeley) 8 -bit CPU at 4 MHz, 128 KB flash, 4 KB RAM 20 Kbps radio at 433 MHz Tiny. OS: event-driven n Configurable S-MAC options Low duty cycle with adaptive listen Low duty cycle without adaptive listen Fully active mode (no periodic sleeping) Computer Engineering Seminar Department of ECE

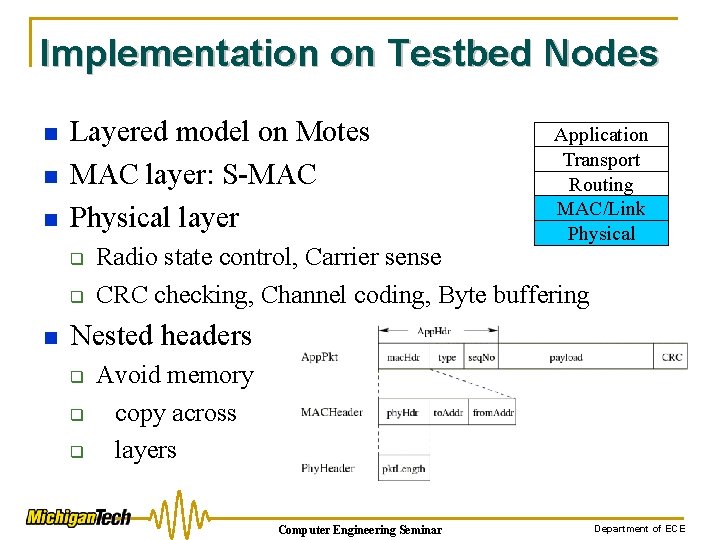
Implementation on Testbed Nodes n n n Layered model on Motes MAC layer: S-MAC Physical layer q q n Application Transport Routing MAC/Link Physical Radio state control, Carrier sense CRC checking, Channel coding, Byte buffering Nested headers q q q Avoid memory copy across layers Computer Engineering Seminar Department of ECE

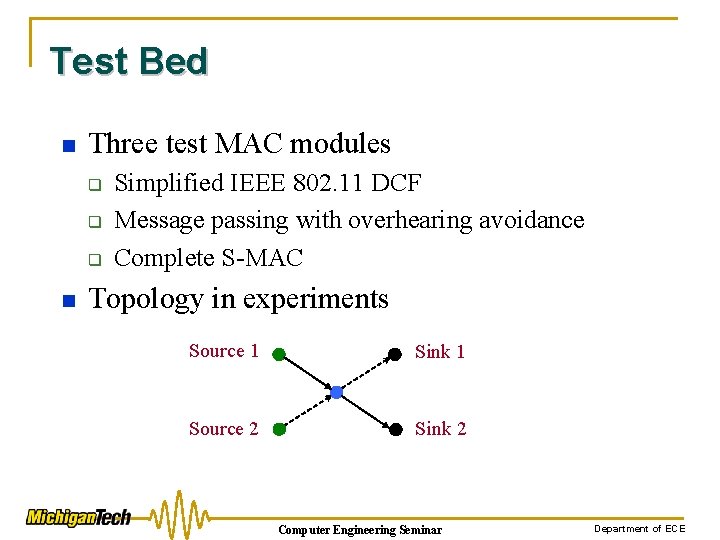
Test Bed n Three test MAC modules q q q n Simplified IEEE 802. 11 DCF Message passing with overhearing avoidance Complete S-MAC Topology in experiments Source 1 Sink 1 Source 2 Sink 2 Computer Engineering Seminar Department of ECE

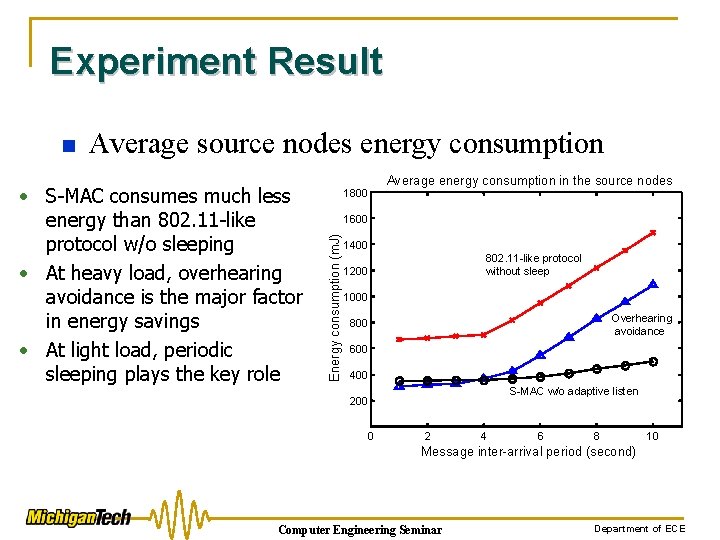
Experiment Result Average source nodes energy consumption • S-MAC consumes much less energy than 802. 11 -like protocol w/o sleeping • At heavy load, overhearing avoidance is the major factor in energy savings • At light load, periodic sleeping plays the key role Average energy consumption in the source nodes 1800 1600 Energy consumption (m. J) n 1400 802. 11 -like protocol without sleep 1200 1000 Overhearing avoidance 800 600 400 S-MAC w/o adaptive listen 200 0 2 4 6 8 10 Message inter-arrival period (second) Computer Engineering Seminar Department of ECE

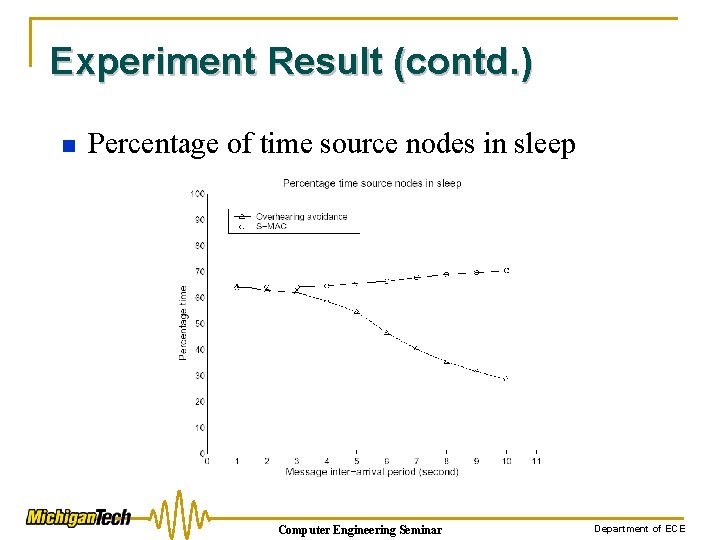
Experiment Result (contd. ) n Percentage of time source nodes in sleep Computer Engineering Seminar Department of ECE

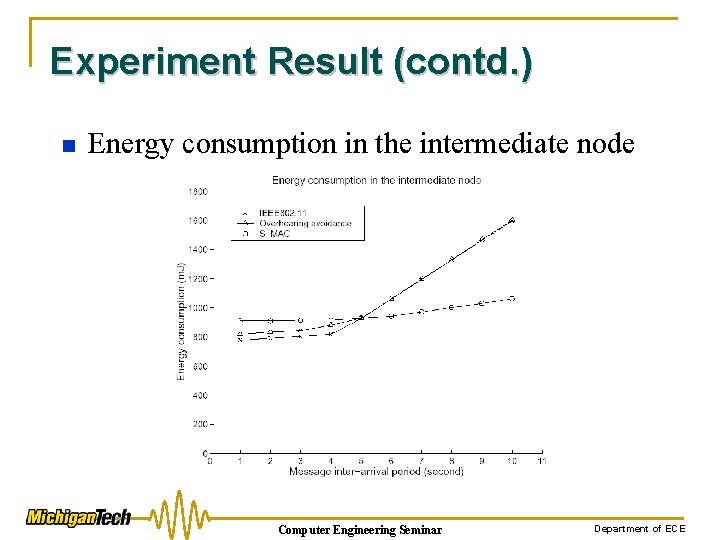
Experiment Result (contd. ) n Energy consumption in the intermediate node Computer Engineering Seminar Department of ECE

S-MAC Conclusions n Advantages: q q q n Periodically sleep reduces energy consumption in idle listening Sleep during transmissions of other nodes Message passing reduces contention latency and control packet overhead Disadvantages: q Reduction in both per-node fairness & latency Computer Engineering Seminar Department of ECE

Other MAC Techniques n Timeout-MAC (T-MAC) q q q S-MAC has fixed duty cycle and not optimal Reduce idle listening by transmitting data in bursts Sleep in between bursts to save power End the active time in an intuitive way Timeout on hearing nothing Computer Engineering Seminar Department of ECE

T-MAC n n n Every node periodically wakes up and communicates with its neighbors A node will keep listening and potentially transmitting, as long as it is in active period An active period ends when no activation event has occurred for time TA Computer Engineering Seminar Department of ECE

Activation event n n n The firing of periodic timer The reception of any data on radio The sensing of communication on the radio The end of transmission of a node’s own data packet The knowledge through prior RTS and CTS packets Computer Engineering Seminar Department of ECE

T-MAC n n A node will sleep if it is not in an active period TA determines the minimum amount of idle listening per frame All communication occurs as a burst in the beginning of the frame Buffer capacity determines the upper bound on the maximum frame time Computer Engineering Seminar Department of ECE

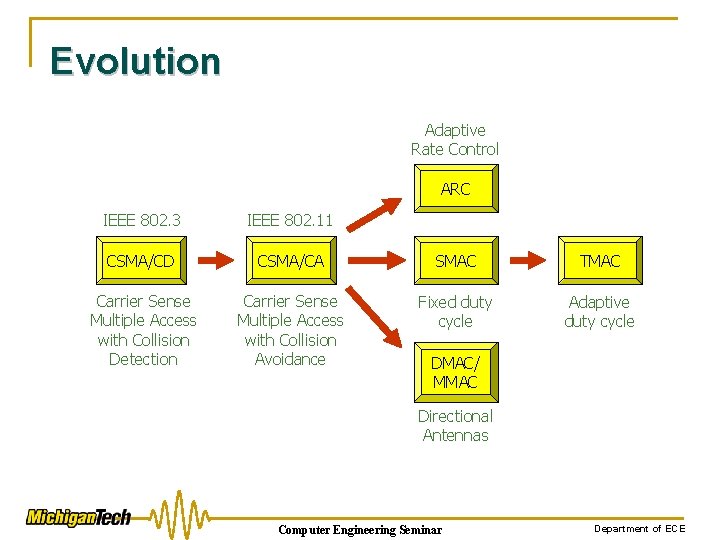
Evolution Adaptive Rate Control ARC IEEE 802. 3 IEEE 802. 11 CSMA/CD CSMA/CA SMAC TMAC Carrier Sense Multiple Access with Collision Detection Carrier Sense Multiple Access with Collision Avoidance Fixed duty cycle Adaptive duty cycle DMAC/ MMAC Directional Antennas Computer Engineering Seminar Department of ECE

Performance Analysis of 802. 15. 4 in WPAN One promising kind of sensor network: Wireless Personal Area Network (WPAN) Ø Medical sensing and control Ø Wearable computing Ø Location awareness and identification Ø Implanted medical sensors (Focus) ØCoronary care ØDiabetes ØOptical aids ØDrug delivery Computer Engineering Seminar Department of ECE

Critical Metric : Battery Life Implanted medical sensors (Main concern) ØObjective Make Batteries work 10 -15 years ØMethod Ensure that all sensors are powered down or in sleep mode when not in active use ØTradeoff Battery life VS. latency Computer Engineering Seminar Department of ECE

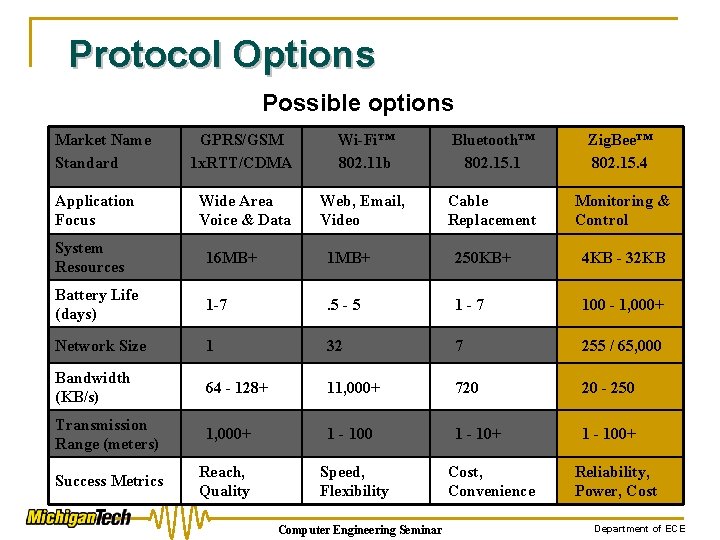
Protocol Options Possible options Market Name Standard Application Focus GPRS/GSM 1 x. RTT/CDMA Wi-Fi™ 802. 11 b Bluetooth™ 802. 15. 1 Zig. Bee™ 802. 15. 4 Wide Area Voice & Data Web, Email, Video Cable Replacement Monitoring & Control System Resources 16 MB+ 1 MB+ 250 KB+ 4 KB - 32 KB Battery Life (days) 1 -7 . 5 - 5 1 -7 100 - 1, 000+ Network Size 1 32 7 255 / 65, 000 Bandwidth (KB/s) 64 - 128+ 11, 000+ 720 20 - 250 Transmission Range (meters) 1, 000+ 1 - 100 1 - 10+ 1 - 100+ Success Metrics Reach, Quality Speed, Flexibility Computer Engineering Seminar Cost, Convenience Reliability, Power, Cost Department of ECE

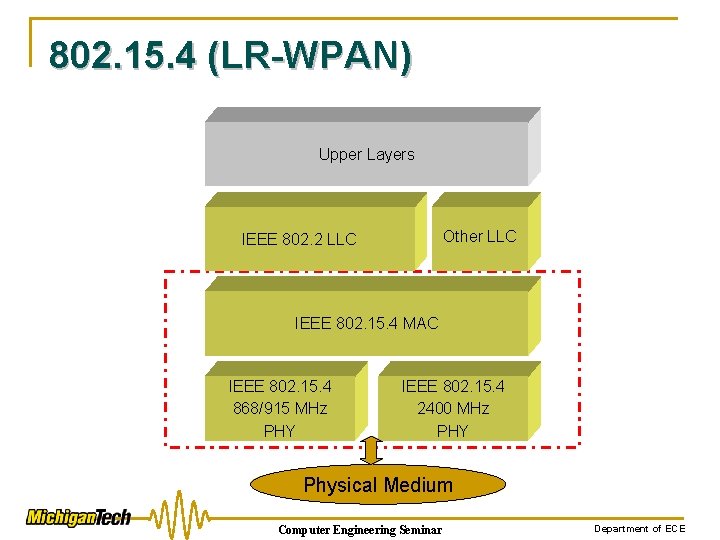
802. 15. 4 (LR-WPAN) Upper Layers Other LLC IEEE 802. 2 LLC IEEE 802. 15. 4 MAC IEEE 802. 15. 4 868/915 MHz PHY IEEE 802. 15. 4 2400 MHz PHY Physical Medium Computer Engineering Seminar Department of ECE

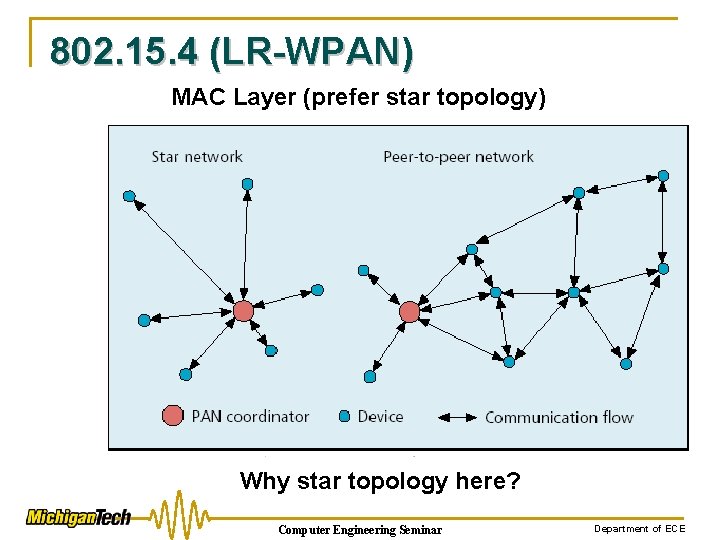
802. 15. 4 (LR-WPAN) MAC Layer (prefer star topology) Why star topology here? Computer Engineering Seminar Department of ECE

802. 15. 4 (LR-WPAN) Why star topology here? ØCoordinator is external to the body ØPDA, mobile phone or bedside monitor station ØEasy to replace of charge batteries ØEasy to communicate with other networks ØCoordinator defines the start and end of a superframe and is charge of the association and disassociation of the other nodes Computer Engineering Seminar Department of ECE

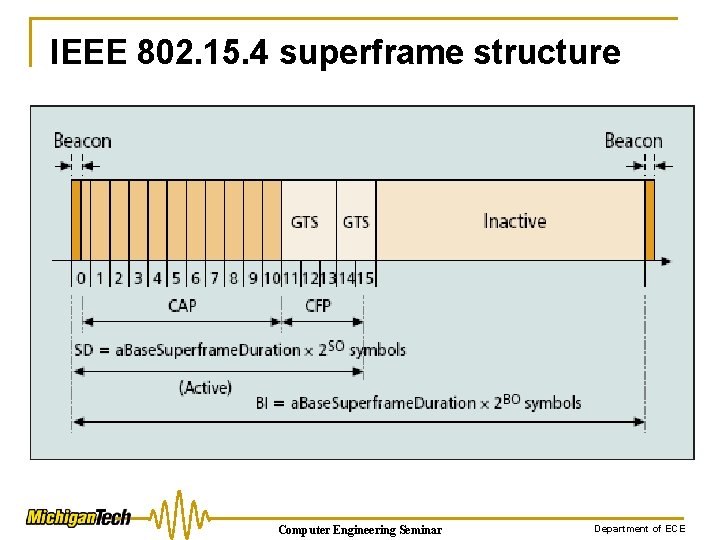
IEEE 802. 15. 4 superframe structure Computer Engineering Seminar Department of ECE

Two Communication methods ØBeacon mode ØPros: Coordinator can communicate at will ØCons: Listeners have to keep awake ØNon-beacon mode ØPros: Nodes can sleep more ØCons: Communication latency Computer Engineering Seminar Department of ECE

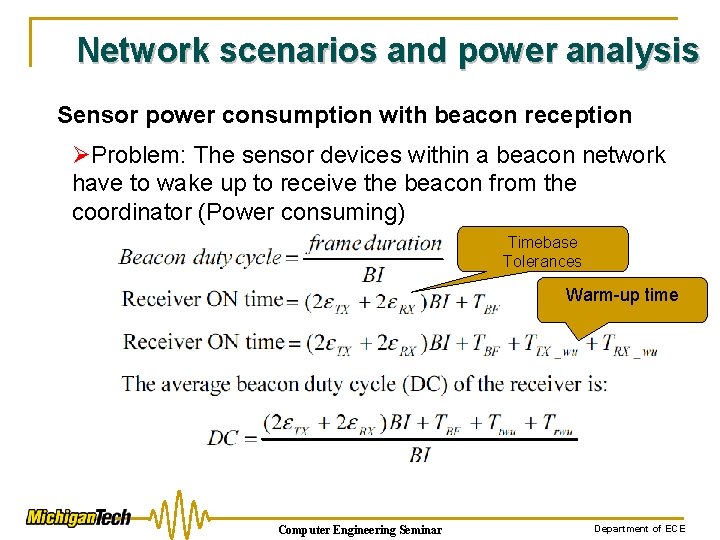
Network scenarios and power analysis Sensor power consumption with beacon reception ØProblem: The sensor devices within a beacon network have to wake up to receive the beacon from the coordinator (Power consuming) Timebase Tolerances Warm-up time Computer Engineering Seminar Department of ECE

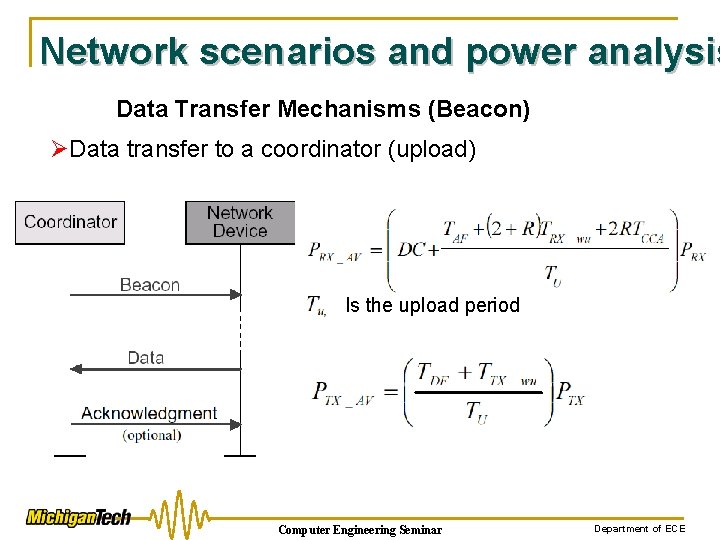
Network scenarios and power analysis Data Transfer Mechanisms (Beacon) ØData transfer to a coordinator (upload) Is the upload period Computer Engineering Seminar Department of ECE

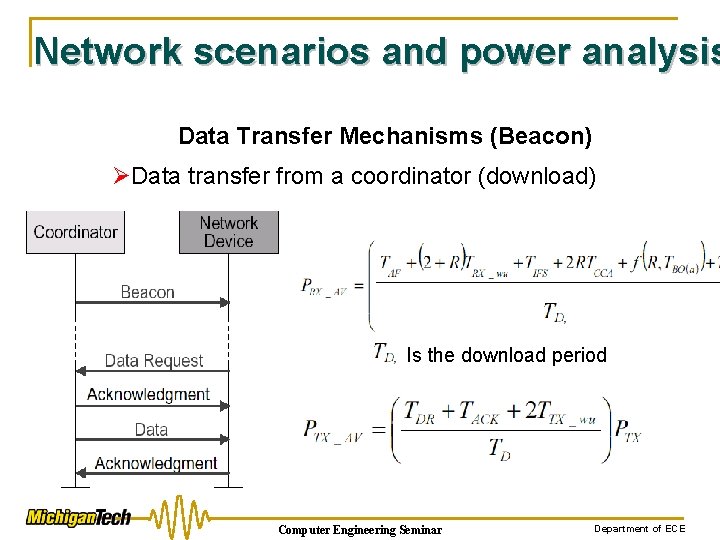
Network scenarios and power analysis Data Transfer Mechanisms (Beacon) ØData transfer from a coordinator (download) Is the download period Computer Engineering Seminar Department of ECE

Results Average Back-off With a small number of sensors that are effectively off most of the time, the probability of a channel being free is greater than 99 %. Therefore, for the relatively small number of sensors used in the WBAN networks explored here, it would be more economical to keep the CSMA/CA switched off. This is to ensure that the automatic initial back-off is avoided. Computer Engineering Seminar Department of ECE

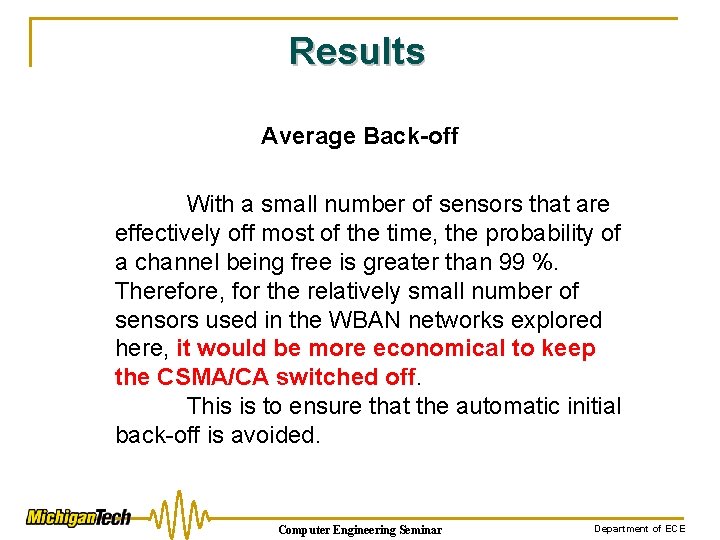
Node Lifetime in Beacon Networks Computer Engineering Seminar Department of ECE

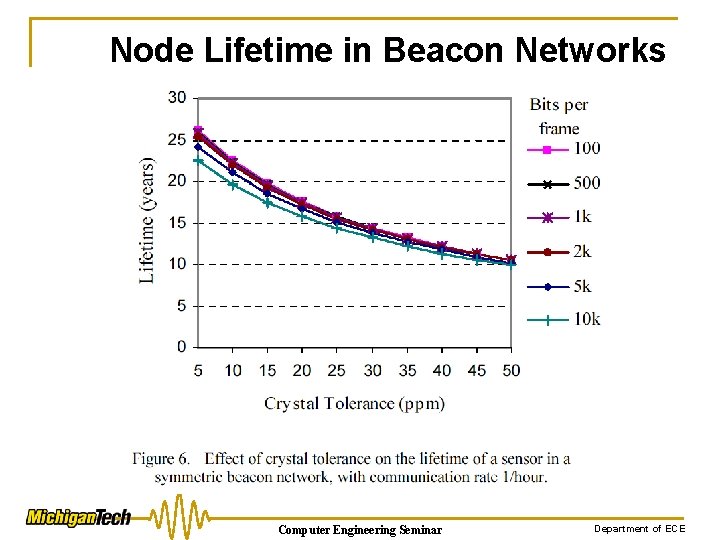
Node Lifetime in Beacon Networks Computer Engineering Seminar Department of ECE

Node Lifetime in Beacon Networks Ø 15 -year lifetime may only be obtained for very low upload rates. ØIt is under very limited data rate conditions and a tight tolerance crystal, which typically must be better than 25 ppm. Computer Engineering Seminar Department of ECE

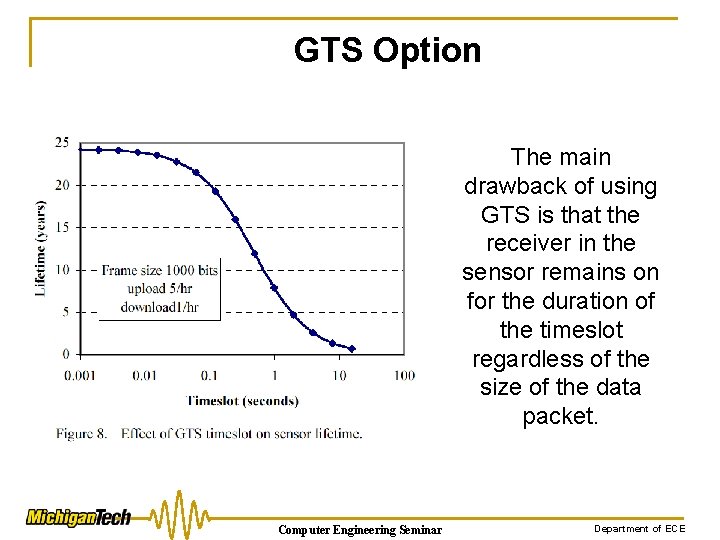
GTS Option The main drawback of using GTS is that the receiver in the sensor remains on for the duration of the timeslot regardless of the size of the data packet. Computer Engineering Seminar Department of ECE

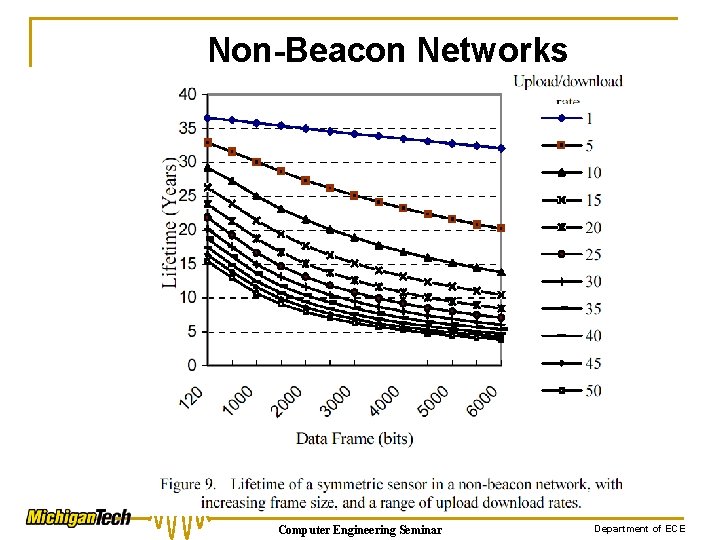
Non-Beacon Networks Computer Engineering Seminar Department of ECE

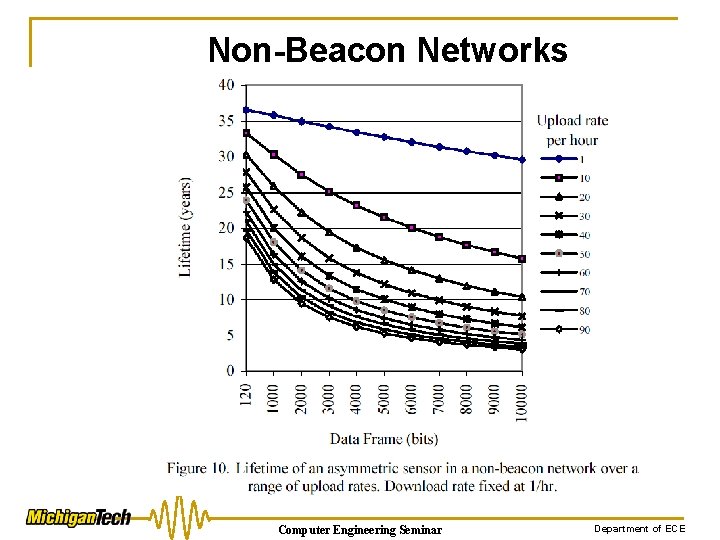
Non-Beacon Networks Computer Engineering Seminar Department of ECE

Conclusion ØAs a solution to the challenge of the personal area network, the IEEE 802. 15. 4 standard would provide a limited answer in its non-beacon form. ØSensors that do not have large amounts of data to transfer could be used, i. e. , small packets of data several times per hour. Computer Engineering Seminar Department of ECE

Questions and Comments Computer Engineering Seminar Department of ECE

Computer Engineering Seminar Department of ECE