Introduction to Wireless Sensor Networks Medium Access Control


- Slides: 16

Introduction to Wireless Sensor Networks Medium Access Control (MAC) 17 February 2005 The University of Iowa. Copyright© 2005 1 A. Kruger

Organizational Class Website www. engineering. uiowa. edu/~ece 195/2005/ Class Time Monday 4: 30 -5: 20 Room 4511 SC Thursday 12: 30 -1: 20 Room 3220 SC Please note that the room numbers are different for Mondays and Thursdays. Office Hours Monday 5: 20 -6: 20 Room 1126 SC Thursday 1: 30 -2: 30 Room 1126 SC Other By appointment Room 523 C SHL The University of Iowa. Copyright© 2005 2 A. Kruger

Medium Access Control (MAC) Introduction • One Approach (Be nice – share) – Avoid interference by scheduling nodes on subchannels • TDMA (Time-Division Multiple Access) • FDMA (Frequency-Division Multiple Access) • CDMA (Code-Division Multiple Access) • Another Approach (Compete/contend) – Don’t pre-allocate transmission, compete => probabilistic coordination – ALOHA (Transmit. Collision? Yes, discard packet, retransmit later) – Carrier Sense (IEEE 802. 11) The University of Iowa. Copyright© 2005 3 A. Kruger

MAC Attributes • Basic task of MAC protocol – Collision avoidance/minimization • Energy efficiency – MAC layer controls radio. Radio often consume most energy • Scalability and adaptivity – Nodes join, exit, rejoin, die, move to different location – Good MAC should accommodate such changes • Channel utilization – Very important in cellular or wireless LAN – Often secondary in WSNs (Why? ) • Latency • Throughput • Fairness – Important in traditional cellular/wireless LAN, less important in WSNs (Why? ) The University of Iowa. Copyright© 2005 4 A. Kruger

MAC Attributes • For WSNs, most important attributes of a good MAC are – Effective collision avoidance – Energy Efficiency – Scalability and adaptivity • Other attributes are normally secondary – Fairness – Latency – Channel utilization The University of Iowa. Copyright© 2005 5 A. Kruger

Energy Efficiency in MAC Protocols • Motivation – Energy efficiency is very important in WSNs. • Question – what causes energy waste from a MAC perspective? – Collision • Collided packets are discarded, retransmission require energy • Not a big issue in scheduled (TDMA, CDMA, FDMA) MAC protocols, but an issue in contention MAC protocols. – Idle listening • Long distance (500 m or more) Tx energy consumption dominates, but in short-range communication Rx energy consumption can be close to Tx energy consumption • MICA 2 idle: receiving: transmission ratio at 1 m. W is 1: 1: 1. 41 @ 433 MHz and 1 m. W • Can be a dominant factor in WSN energy consumption The University of Iowa. Copyright© 2005 6 A. Kruger

Energy Efficiency in Mac Protocols – Overhearing • When a node receives packets that are destined for another node – Control packet overhead • Sending, receiving, listening, all consumes energy – Adaptation • Reconfiguring when nodes join leave The University of Iowa. Copyright© 2005 7 A. Kruger

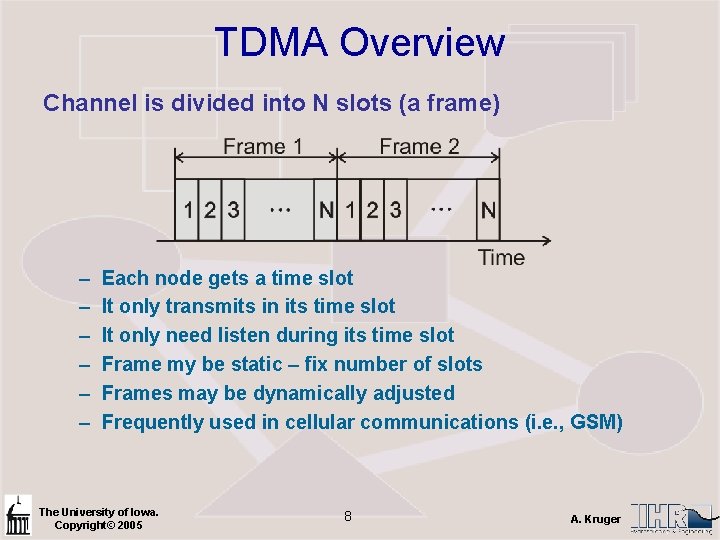
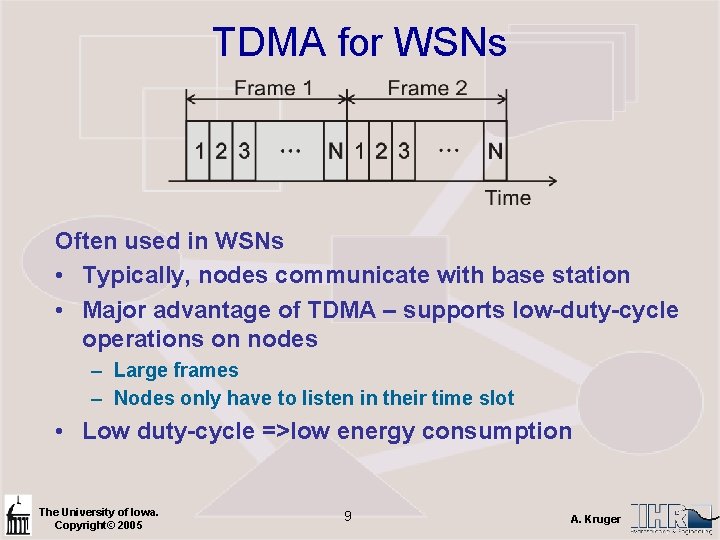
TDMA Overview Channel is divided into N slots (a frame) – – – Each node gets a time slot It only transmits in its time slot It only need listen during its time slot Frame my be static – fix number of slots Frames may be dynamically adjusted Frequently used in cellular communications (i. e. , GSM) The University of Iowa. Copyright© 2005 8 A. Kruger

TDMA for WSNs Often used in WSNs • Typically, nodes communicate with base station • Major advantage of TDMA – supports low-duty-cycle operations on nodes – Large frames – Nodes only have to listen in their time slot • Low duty-cycle =>low energy consumption The University of Iowa. Copyright© 2005 9 A. Kruger

TDMA Disadvantages for WSNs • Cluster paradigm (analogous to cell phones) • One node is selected as the cluster head and acts as base station • Nodes communicate only with head • Direct peer-to-peer communication not energy efficient – Nodes must listen on all time slots, reducing energy • Inter-cluster communication requires other MAC protocols • Most important issue is limited scaling – When a new nodes joins the base station must reallocate slots and adjusting the frame size – This can take time and energy to propagate The University of Iowa. Copyright© 2005 10 A. Kruger

Examples of Scheduled Protocols • Sohrabi & Pottie – Homework/Exam (page 79 in book) • Low-Energy Adaptive Clustering Hierarchy (LEACH) – – Organize nodes into cluster hierarchies TDMA within each cluster Nodes only talk to node head Position of head is rotated among nodes depending on remaining energy – Node then uses long-range/high-power communication to base – Nodes don’t need to know global topology – Nodes don’t need control information from base station The University of Iowa. Copyright© 2005 11 A. Kruger

Scheduled Protocols • Bluetooth – Designed for PAN, but attractive for WSNs – Bluetooth organizes itself into clusters, piconets – Frequency-hopping CDMA is used to handle intercluster interference – Within cluster, TDMA MAC protocol – Master-slave approach. Cluster head (master), other nodes are slaves. – Master uses polling to decide which salve can transmit – Only communication between master and one or more slaves are possible – Maximum number of nodes in a cluster is 8 The University of Iowa. Copyright© 2005 12 A. Kruger

Bluetooth The University of Iowa. Copyright© 2005 13 A. Kruger

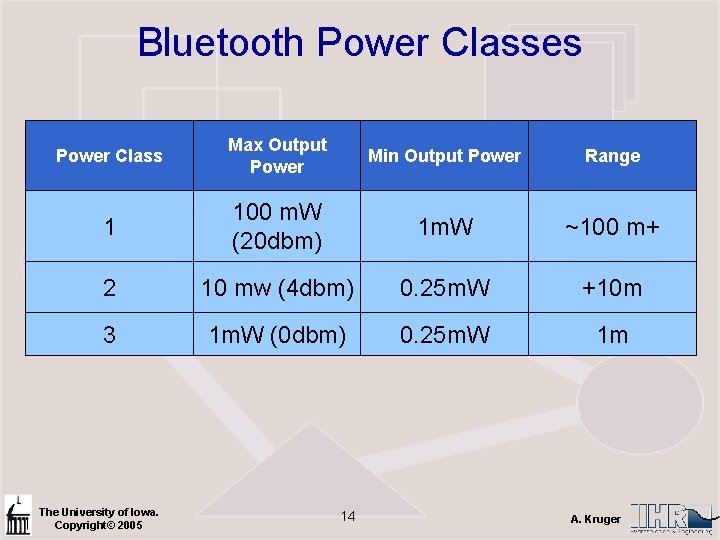
Bluetooth Power Classes Power Class Max Output Power Min Output Power Range 1 100 m. W (20 dbm) 1 m. W ~100 m+ 2 10 mw (4 dbm) 0. 25 m. W +10 m 3 1 m. W (0 dbm) 0. 25 m. W 1 m The University of Iowa. Copyright© 2005 14 A. Kruger

Energy Conservation in Scheduled MAC Protocols • Collision free • No need for idle listening • TDMA naturally support low-duty cycle operation The University of Iowa. Copyright© 2005 15 A. Kruger

Review Question • True or false – With respect to WSN MACs, effective collision avoidance is less important than fairness. • Describe and elaborate briefly (three sentences) what we mean by the term “latency” as an attribute of a WSN MAC. • True or false – channel utilization is a crucial attribute of as WSN MAC • True or false – energy waste from collisions are less in contention MAC protocols than in scheduled MAC protocols. • List three scheduled MAC protocols. • True or false – in WSN where low-power, short range radio transmission is used, idle listing contributes very little to the energy consumption budget of a node • Briefly explain the term idle listening in WSNs • One major issue in TDMA MAC protocols that of limited scaling. Explain in a 5 -6 sentence paragraph. • Describe the LEACH MAC protocol. • Describe the Sohrabi & Pottie MAC protocol. • What is the fundamental purpose of a MAC protocol? The University of Iowa. Copyright© 2005 16 A. Kruger