IT Deployment Risks Revised 2015 Risks associated with




























- Slides: 40

IT Deployment Risks Revised 2015

Risks associated with IT deployment in an organization: 1. IT Strategic Planning 2. IT Project Management 3. Software Applications a) Acquisition b) Development c) Change Management d) Implementation CISB 424, Sulfeeza Content

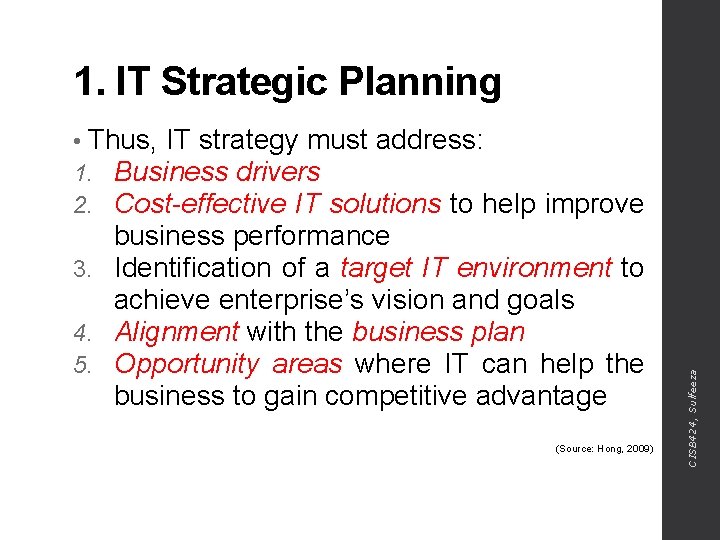
1. IT Strategic Planning of strategic business management • It results in long-term planning for and future direction of an enterprise at a strategic level • Since the business strategy is different from IT strategy, the concept of strategic alignment refers to the need for alignment between business strategy and IT goals and processes (Source: Shahid Ali, 2014) CISB 424, Sulfeeza • Strategic planning is an important component

1. IT Strategic Planning • An effective strategic alignment will help to understand the enterprise’s IT requirements and providing innovative IT solutions to keep business successful • IT strategy must ensure that business needs are the driving force for technology solutions. CISB 424, Sulfeeza (Source: Hong, 2009)

1. IT Strategic Planning improve business performance 3. Identification of a target IT environment to achieve enterprise’s vision and goals 4. Alignment with the business plan 5. Opportunity areas where IT can help the business to gain competitive advantage (Source: Hong, 2009) CISB 424, Sulfeeza • Thus, IT strategy must address: 1. Business drivers 2. Cost-effective IT solutions to help

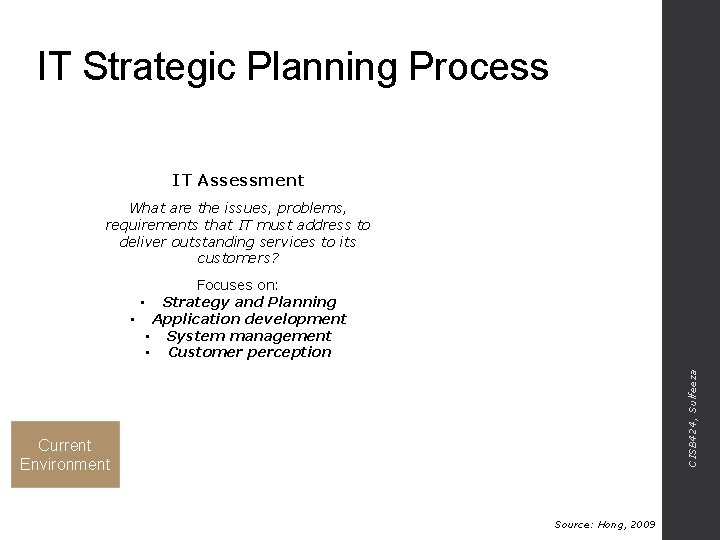
IT Strategic Planning Process IT Assessment What are the issues, problems, requirements that IT must address to deliver outstanding services to its customers? CISB 424, Sulfeeza Focuses on: • Strategy and Planning • Application development • System management • Customer perception Current Environment Source: Hong, 2009

CISB 424, Sulfeeza IT Strategic Planning Process Source: Hong, 2009

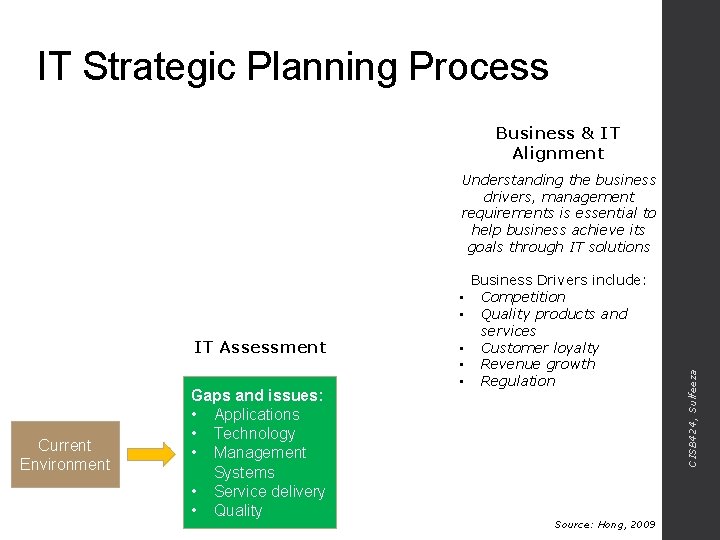
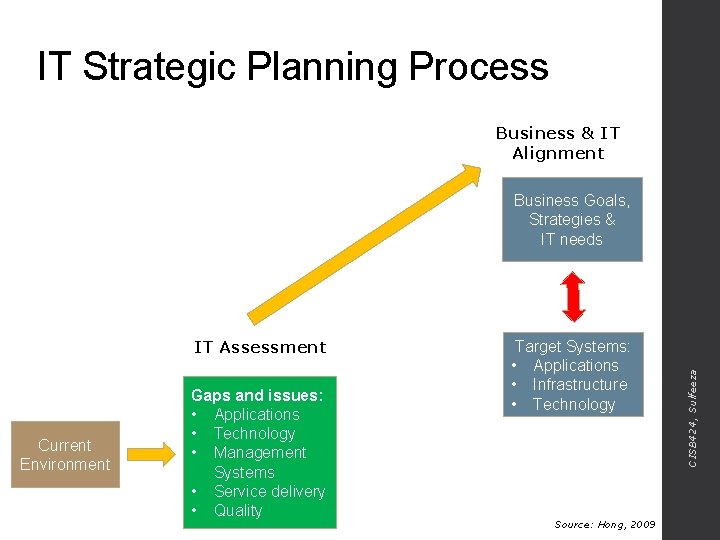
IT Strategic Planning Process Business & IT Alignment • • IT Assessment Current Environment Gaps and issues: • Applications • Technology • Management Systems • Service delivery • Quality • • • Business Drivers include: Competition Quality products and services Customer loyalty Revenue growth Regulation Source: Hong, 2009 CISB 424, Sulfeeza Understanding the business drivers, management requirements is essential to help business achieve its goals through IT solutions

IT Strategic Planning Process Business & IT Alignment IT Assessment Current Environment Gaps and issues: • Applications • Technology • Management Systems • Service delivery • Quality Target Systems: • Applications • Infrastructure • Technology Source: Hong, 2009 CISB 424, Sulfeeza Business Goals, Strategies & IT needs

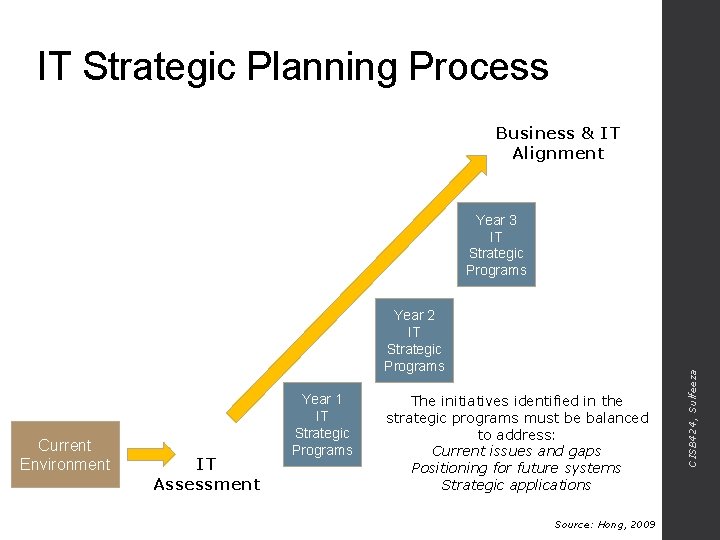
IT Strategic Planning Process Business & IT Alignment Year 2 IT Strategic Programs Current Environment IT Assessment Year 1 IT Strategic Programs The initiatives identified in the strategic programs must be balanced to address: Current issues and gaps Positioning for future systems Strategic applications Source: Hong, 2009 CISB 424, Sulfeeza Year 3 IT Strategic Programs

IT Strategic Planning Risks requirements are not understood or addressed by IT management • No regular and formal consultation between IT management and senior management • IT plans are not aligned with business needs • Unnecessary IT initiatives and investments • IT plans are inconsistent with the organization’s expectations or requirements • IT is not focused on the right priorities (Source: COBIT 4. 1 by ISACA) CISB 424, Sulfeeza • Business

IT Strategic Plan Control Practices As such, to ensure that the identified risks can be minimized, effective controls practices must be established. • Failure to design and manage effective IT strategic management control practices could result in: 1. Adopting IT strategy that does not support business strategy 2. Misuse or underutilization of enterprise assets 3. Miscommunication of IT processes and disconnects with business management 4. Acquisition and/or implementation of applications that do not fulfill minimum security and architecture standards 5. Additional costs to maintain and administer nonconforming applications (Source: ISACA) CISB 424, Sulfeeza •

ISACA has established a number of control practices that can be adopted by organization in their IT strategy management, namely: 1. Establish a process to translate business strategy, business expectations, and current and future IT capabilities into an IT strategic plan 2. Ensure that IT has established a process to identify, document and adequately address organisational changes, technology evolution, regulatory requirements, business process re-engineering, staffing, in- and outsourcing opportunities, etc. , in the planning process 3. Define roles and responsibilities of the stakeholders involved in the strategic planning process 4. Develop IT capabilities to support the business requirements and contribute to expected benefits as included in the enterprise’s strategic plan 5. Identify and document the implications on the business strategy in terms of risk and cost of the required IT capabilities. (Source: COBIT 4. 1 by ISACA) CISB 424, Sulfeeza IT Strategic Plan Control Practices

The minimum audit skills required When involve in IT strategic management audit, IT auditors are recommended to have an in-depth knowledge in the following areas: IT governance IT strategy best practices Risk management Business strategy Industry practices IT architecture and its alignment with business process CISB 424, Sulfeeza •

IT Strategic Management Audit Scope • When performing IT strategic management audit, IT auditors are recommended to review the following areas: • The IT auditor should look for evidence of a prescribed, documented IT strategic planning process. • The existence of an ongoing process of this nature indicates that the organization is constantly and diligently seeking an optimal “fit” between the IT infrastructure and the organization’s overall goals. CISB 424, Sulfeeza IT strategy – assess for integration with business strategy; IT strategic plan defines how IT will contribute and support enterprise strategic objectives IT-enabled investments – assess whether it is being supported by a Formal Evaluation Process IT assessment – assess if assessment of IT current capabilities and performance are being performed

2. IT Project Management What is a project? • A project is a temporary endeavor undertaken to create a unique product or service • Temporary indicates a definite beginning i. The project’s objectives are met ii. The need for the project no longer exists; or iii. Terminated because the project’s objectives will not or cannot be met (Source: Project Management Institute) CISB 424, Sulfeeza and end • End is reached when:

2. IT Project Management What is IT project management? IT project management is the process of planning, organizing and delineating (defining) responsibility for the completion of organizations' specific information technology goals (Source: http: //searchcio. techtarget. com/definition/IT-project-management) CISB 424, Sulfeeza •

2. IT Project Management IT project can be any type of project that deals with IT infrastructure, information systems or computer technology. This can include software development activities (such as programming a simple mobile app or a programming large scale software system) b) web development (including updating a web page, creating an online shopping site, or developing an entire Web infrastructure) c) other common examples of IT projects include designing an organization’s IT infrastructure, deploying systems and software, and employing IT security measures. (Source: http: //www. attask. com/resources/blogpost/beginners-guide-it-project-management/) CISB 424, Sulfeeza a)

2. IT Project Management CISB 424, Sulfeeza Categories of IT-related project: a) Research b) Service c) Software development d) System deployment e) Change management f) Infrastructure g) Needs assessment (Source: http: //www. attask. com/resources/blogpost/beginners-guide-it-project-management/)

2. IT Project Management Project management process: b) c) d) e) Initiating A formal process to launch a project, including the description of the project’s objectives, estimated budget, appropriate approval required and obtained Planning In terms of time and resources estimates as well as for the linkages between components and other projects that require coordination Executing Defines the actual project activities, in terms of what needs to be done to accomplish project goals Controlling An on-going set of processes should be in place to monitor the appropriate completion of project elements, determining that budgets and objectives are met Closing The wrapping-up the project effort, delivering the project outcomes as well as summarizing and reporting project results (Source: Project Management Institute; Moeller, 2009) CISB 424, Sulfeeza a)

2. IT Project Management • Improper management of IT project could lead to project failure. • Among the main causes of IT project failure: Lack of user input Incomplete requirements Changing requirements Lack of executive support Technology incompetence Unrealistic expectations This could lead to projects that are: a) Late delivery b) Cost overrun c) Lack of functions d) Poor quality CISB 424, Sulfeeza a) b) c) d) e) f)

IT Project Risks Red Flags 1. Management does not use a formal project management methodology. 2. Project leaders: a) are not adequately experienced at project management b) have insufficient domain expertise. 3. Project teams: a) are unqualified to handle the project size/ complexity. b) are dissatisfied and frustrated. a) do not have management support. b) do not include input from all affected parties. c) taking longer to develop than planned. d) are costing more than budgeted. 5. Project recipients are dissatisfied with project outcomes. CISB 424, Sulfeeza 4. Projects:

IT Project Management Audit Objective: provide management with an independent assessment of the progress, quality and attainment of project objectives at defined milestones within the project CISB 424, Sulfeeza • To

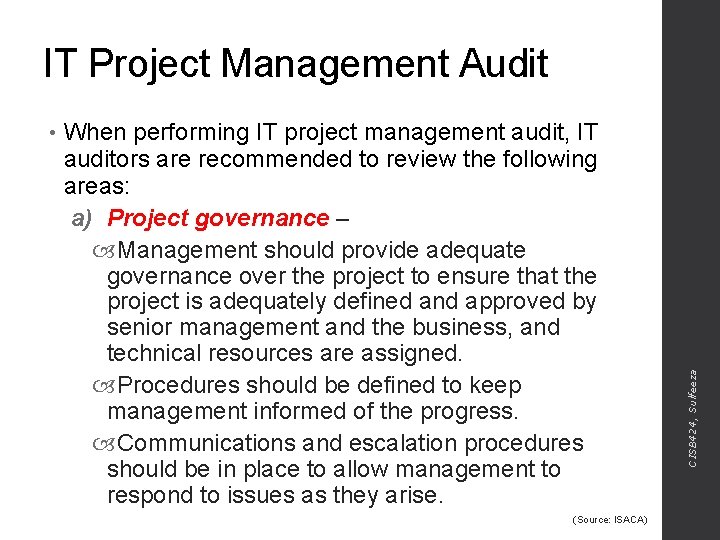
• When performing IT project management audit, IT auditors are recommended to review the following areas: a) Project governance – Management should provide adequate governance over the project to ensure that the project is adequately defined and approved by senior management and the business, and technical resources are assigned. Procedures should be defined to keep management informed of the progress. Communications and escalation procedures should be in place to allow management to respond to issues as they arise. (Source: ISACA) CISB 424, Sulfeeza IT Project Management Audit

As such, in reviewing the project governance aspect, IT auditors are recommended to ascertain that: • A business case has been prepared and reviewed by management. The business case is the rationale for initiating the project, expected benefits, estimated costs, and key attributes to evaluate the success of the project. • The initial scope of the project has been established through a feasibility study, alignment with the IT architecture and the development of an initial high-level project plan • The roles and responsibility for the project are clearly defined (i. e. assigned to senior stakeholders from the affected business units and IT. ) • The project is approved by senior management, depending on the investment and criticality of the project, and the approvals are documented. • Metrics to objectively evaluate the success of a project are established (KPIs, CSFs, ROI) (Source: ISACA) CISB 424, Sulfeeza IT Project Management Audit

• When performing IT project management audit, IT auditors are recommended to review the following areas: b) Project management – The project management approach should be commensurate with the size, complexity and regulatory requirements of the project. The project management controls should ensure adequate oversight of the project (financial, meeting deadlines, etc. ), appropriate involvement by the stakeholders, iterative evaluation of risks, monitoring of issues, and escalation of issues where required (Source: ISACA) CISB 424, Sulfeeza IT Project Management Audit

As such, in reviewing the project management aspect, IT auditors are recommended to ascertain that: • The business and information management teams are integrated, information requirements are clearly documented, project objectives are aligned with the business and information strategies • The project team consists of a team leader with appropriate project management experience and the team consists of the skill sets and authority levels from their respective business units. • Risk analysis has been applied to the project during the initial phase; risks have been identified. Where risks can be mitigated, appropriate processes have been implemented; where risks are inherent to the process, appropriate monitoring processes are in place. • A communications plan is established to provide stakeholders and project leadership with appropriate information to ensure that the project meets functionality, budgetary and timeline goals. (Source: ISACA) CISB 424, Sulfeeza IT Project Management Audit

3. Application Software An application is a program, or group of programs, that is designed for the end user. • Application software can be divided into two general classes: a) Systems software - programs that are dedicated to managing • the computer itself, such as the operating system, file management utilities, and disk operating system (or DOS) software (end-user programs or applications) - enable the user to complete tasks such as creating documents, spreadsheets, databases, and publications, doing online research, sending email, designing graphics, running businesses, and even playing games. Example of applications software database programs, word processors, Web browsers, spreadsheets, Uniten Student Information Portal, maybank 2 u. com (Source: www. webopedia. com; Education Portal) CISB 424, Sulfeeza b) Applications

3. Application Software Why we need to audit applications used by organization? Hidden within numerous software applications in use every day by countless companies and organizations is one of the greatest security risks and challenges. • As security threats shift away from attacks on the network perimeter protected by firewalls and intrusion detection devices, security attacks have become more focused on software applications and their links to data repositories. • The Gartner Group reports that more than 70% of current business security vulnerabilities are found within software applications rather than the network boundaries. • The financial risk to companies resulting from these attacks is not benign; it has been documented that businesses spend billions of US dollars each year recovering from these security breaches. (Source: Computer. World; Newswire) CISB 424, Sulfeeza •

a) Application Development What is application / systems development? CISB 424, Sulfeeza The activity of computer programming, which includes all activities involved between the conception of the desired application through to the final demonstration of that application

a) Application Development systems development process can be broken down into eight phases: 1. Systems Planning 2. Systems Analysis 3. Conceptual Design 4. Systems Evaluation and Selection 5. Detailed Design 6. Programming and Testing Systems 7. Systems Implementation 8. Systems Maintenance CISB 424, Sulfeeza • The

a) Application Development risks in the application development: 1. Inadequate controls in the development process 2. Schedule and budget overruns 3. User requirements not being met by the application system 4. Inadequate stakeholder involvement (Source: Henderson, 2008) CISB 424, Sulfeeza • Potential

a) Application Development What is the role of IS auditing in the application development process? • IT auditors typically execute three (3) types of reviews of the system development process, which are: 1. Pre-implementation review 3. Parallel review Reviews the pertinent stages of the methodology as they proceed and identify potential or possible risks and provides suitable risk mitigation approaches Post-implementation review Reviews the relevant stages of the methodology after the system development project has completed; emphasizes on the issues faced during the systems development and provides recommendations for improvements (Source: Henderson, 2008) CISB 424, Sulfeeza 2. • Investigates the proposed methodology and considers its applicability and potential risks associated with the systems development project

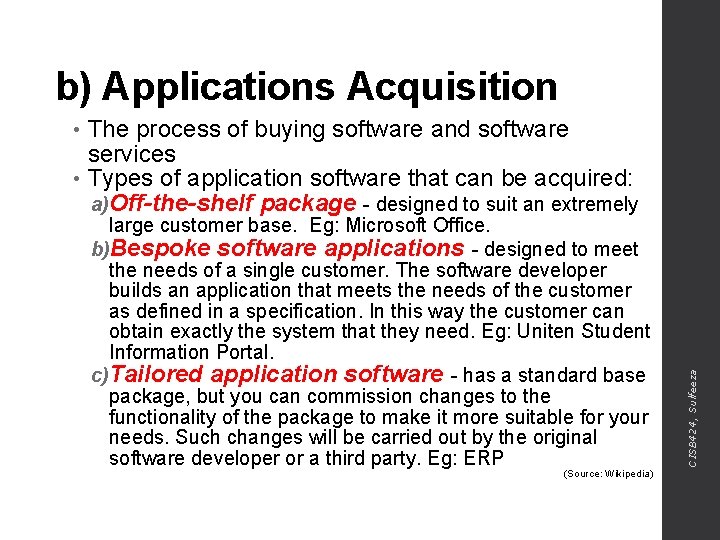
b) Applications Acquisition The process of buying software and software services • Types of application software that can be acquired: a)Off-the-shelf package - designed to suit an extremely large customer base. Eg: Microsoft Office. b)Bespoke software applications - designed to meet the needs of a single customer. The software developer builds an application that meets the needs of the customer as defined in a specification. In this way the customer can obtain exactly the system that they need. Eg: Uniten Student Information Portal. c)Tailored application software - has a standard base package, but you can commission changes to the functionality of the package to make it more suitable for your needs. Such changes will be carried out by the original software developer or a third party. Eg: ERP (Source: Wikipedia) CISB 424, Sulfeeza •

b) Applications Acquisition The applications acquisition process can be broken down into three phases: 1. Planning • 2. Implementation a) Define implementation plan b) Obtain approval c) Complete purchase d) Implement 3. Post-implementation a) User acceptance b) Maintenance and support CISB 424, Sulfeeza a) Identify the needs b) Assess suitability c) Secure funding

c) Application Change Management • ISO 20000 defines Change Management Program as: A formal process used to ensure that changes to a product or system are introduced in a controlled and coordinated manner Also known as Change Control Process or Change Control Management Process • The purpose of the CMP is to ensure that the negative impact of changes to a company’s IT and IS are minimized by using a standardized process of governance. CISB 424, Sulfeeza •

c) Application Change Management to COBIT 4. 1 by ISACA, change management process is described as: All changes, including emergency maintenance and patches, relating to infrastructure and applications within the production environment are formally managed in a controlled manner. Changes are logged, assessed and authorized prior to implementation and reviewed against planned outcomes following the implementation. This process assures mitigation of the risks of negatively impacting the stability or integrity of the production environment (Source: Singleton, 2011) CISB 424, Sulfeeza • According

c) Application Change Management Process 1. Develop a Request for Change (RFC) a) Specifies the change b) Justifies the need 2. Obtain Business Change Acceptance a) Approvals/ rejected results by the business stakeholders 3. Initiate the Development Project 4. Pass the Change Management Gate 5. 6. 7. Implement the Change Report the Results Link Problem Management to Changes CISB 424, Sulfeeza a) Approvals/ rejected results by Change Advisory Board

Control over the change management process is measured by metrics such as: 1. Number of disruptions or data errors caused by inaccurate specifications or incomplete impact assessment 2. Amount of application of infrastructure rework caused by inadequate change specifications 3. Percentage of changes that follow formal change control processes (Source: Singleton, 20111) CISB 424, Sulfeeza c) Application Change Management Process

c) Application Change Management Process What is the role of IS auditing in the change management process? Review a sample of application development projects and see if evidence exists that the entity has mitigated risks of application development by establishing effective control of the enterprise’s change management process 2. Examine enterprise documentation for evidence of the employment of best practices of systems development life cycle (SDLC) 3. Assess the maturity of an enterprise’s change management process using maturity matrix (Source: Singleton, 20111) CISB 424, Sulfeeza 1.