Internet and Information Security Cases from Turkey Dr



















- Slides: 35

Internet and Information Security: Cases from Turkey Dr. İzzet Gökhan Özbilgin MSc, MBA, Ph. D

About me. . . • Head of IT Governance and Audit Group, Prime Ministry – Capital Markets Board of Turkey • Assoc. Prof, University of Turkish Aeronautical Association MIS Dept. • Part Time Instructor, University of Gazi Computer Engineering Dept. • Board Member • Turkish Informatics Association • Information Security Association • ISACA Turkey Chapter

The Internet = A World of Opportunities Look what’s at your fingertips A way to communicate with friends, family, colleagues Access to information and entertainment A means to learn, meet people, and explore



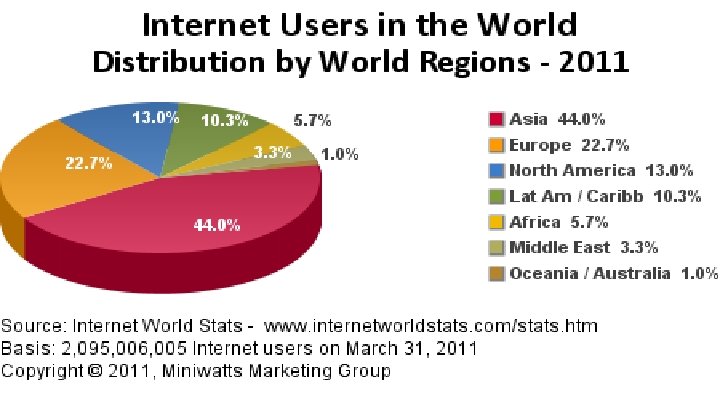
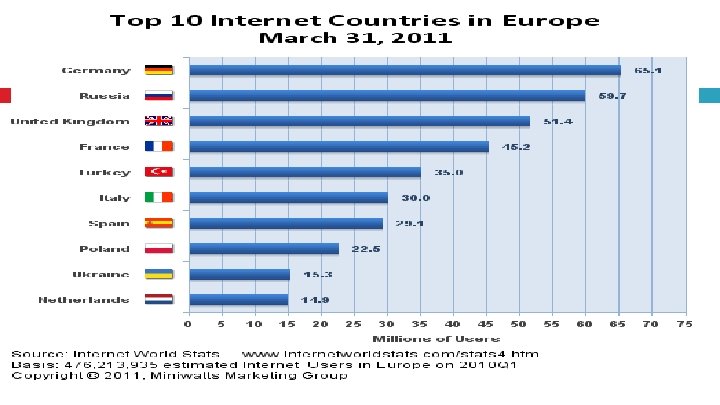
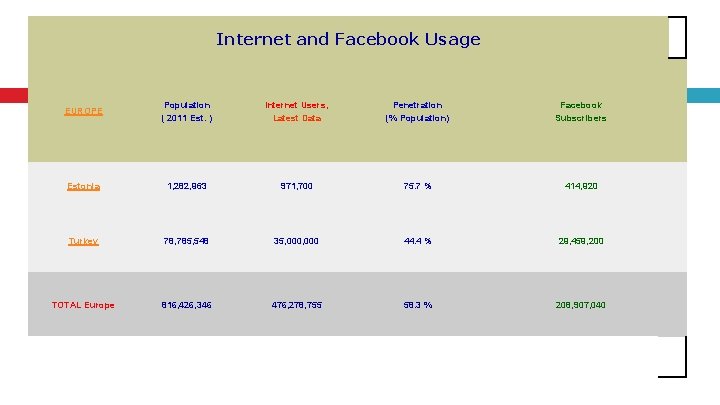
Internet and Facebook Usage EUROPE Population ( 2011 Est. ) Internet Users, Latest Data Penetration (% Population) Facebook Subscribers Estonia 1, 282, 963 971, 700 75. 7 % 414, 920 Turkey 78, 785, 548 35, 000 44. 4 % 29, 459, 200 TOTAL Europe 816, 426, 346 476, 278, 755 58. 3 % 208, 907, 040

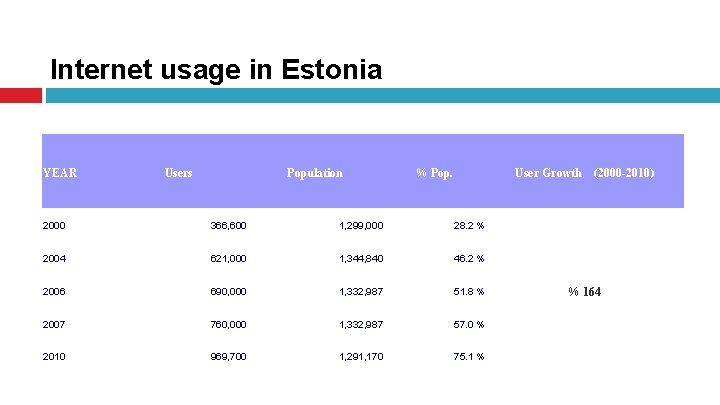
Internet usage in Estonia YEAR Users Population % Pop. User Growth 2000 366, 600 1, 299, 000 28. 2 % 2004 621, 000 1, 344, 840 46. 2 % 2006 690, 000 1, 332, 987 51. 8 % 2007 760, 000 1, 332, 987 57. 0 % 2010 969, 700 1, 291, 170 75. 1 % (2000 -2010) % 164

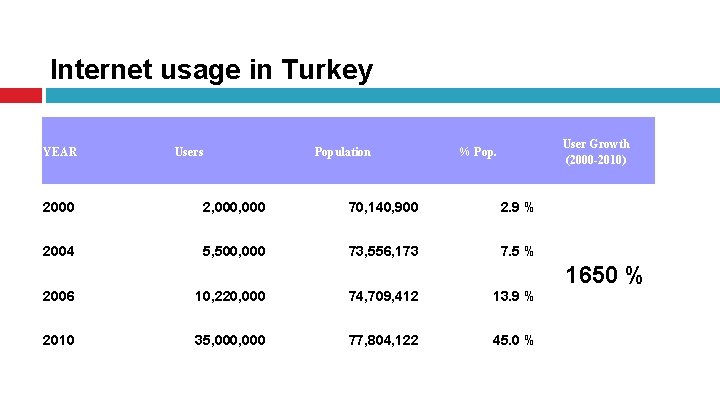
Internet usage in Turkey YEAR Users Population User Growth (2000 -2010) % Pop. 2000 2, 000 70, 140, 900 2. 9 % 2004 5, 500, 000 73, 556, 173 7. 5 % 1650 % 2006 10, 220, 000 74, 709, 412 13. 9 % 2010 35, 000 77, 804, 122 45. 0 %

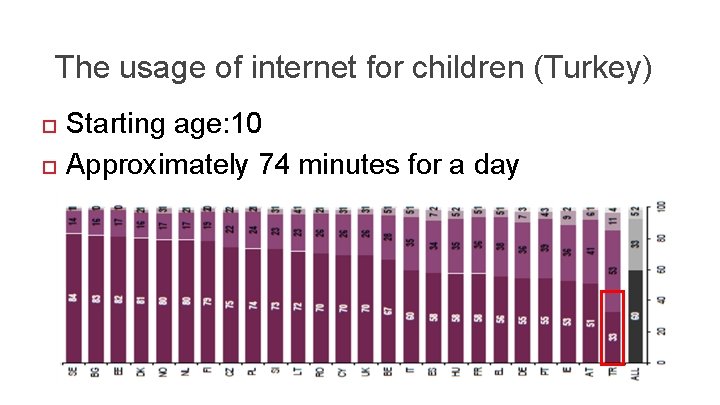
The usage of internet for children (Turkey) Starting age: 10 Approximately 74 minutes for a day

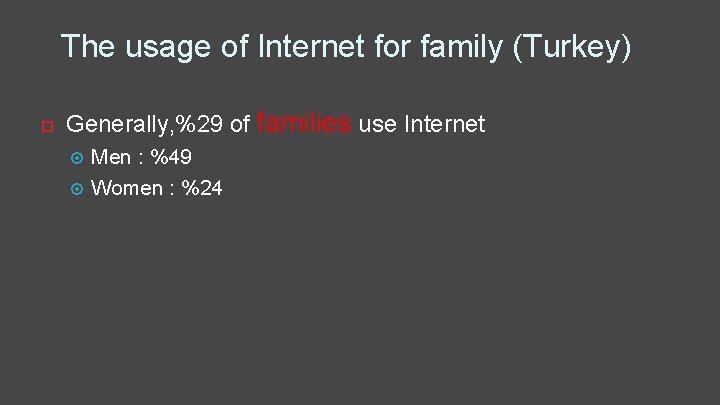
The usage of Internet for family (Turkey) Generally, %29 of families use Internet Men : %49 Women : %24

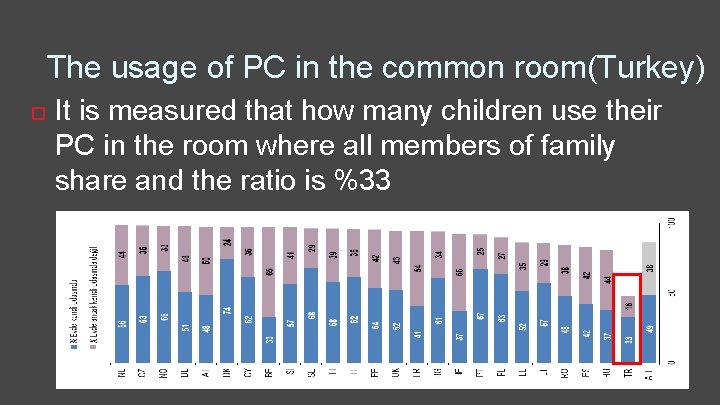
The usage of PC in the common room(Turkey) It is measured that how many children use their PC in the room where all members of family share and the ratio is %33

The activities on the Internet (Turkey) School activities: % 92 Entertainment watching video : % 59 Social network with his friends: %48 Game: % 49 Reading news: % 40 Download music or video: % 40

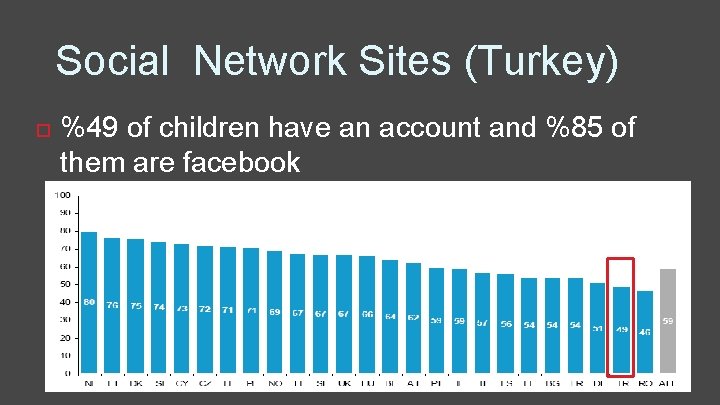
Social Network Sites (Turkey) %49 of children have an account and %85 of them are facebook

Social Network Sites % 46 use it with no level of confidentiality % 65 has a real photo of them % 59 do not know how to change the security settings %19 shares the address and %8 shares the phone numbers

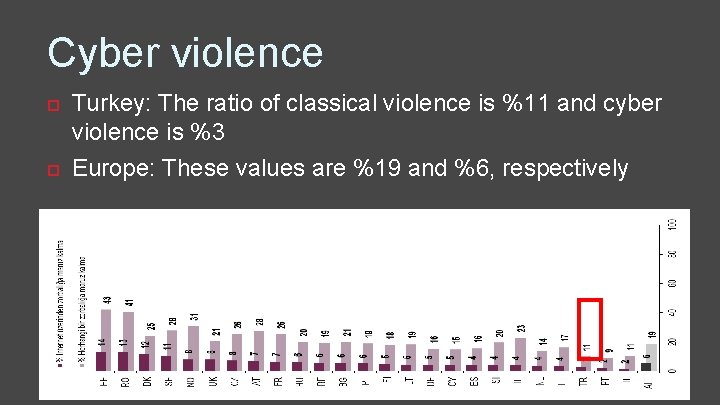
Cyber violence Turkey: The ratio of classical violence is %11 and cyber violence is %3 Europe: These values are %19 and %6, respectively

The world is changing… As you see, the users of Internet are increasing so fast Also risks are changing…In the past there was risk and still there is while socialization…only the media and the ways are changing Especially wireless, mobile applications and social networks You never disappear the risk, but you can manage it and develop the controls

From where… Tarzan has no clothes while we were watching him The Cindrella came the home after midnight The Pinokyo lies The Batman drives the car with the speed of 300 km/hour The Red Kit always smoke The Temel Reis pipes

To where…


Security is very important issue… • Security has become an integral part of daily life and all share holders need to ensure that they are adequately secured. • The general security objectives comprise the following: • Availability • Integrity, which may include authenticity and nonrepudiation • Confidentiality

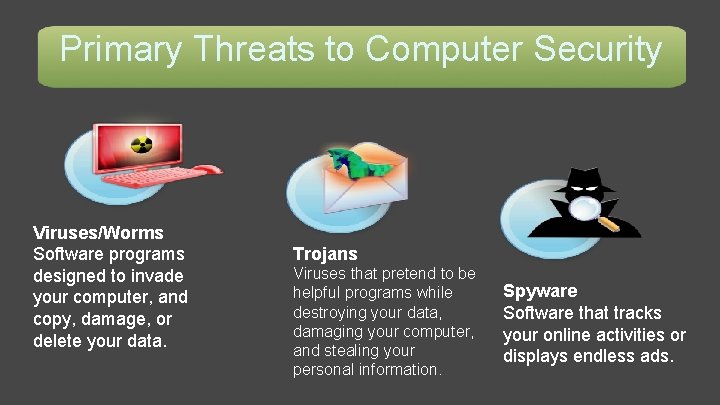
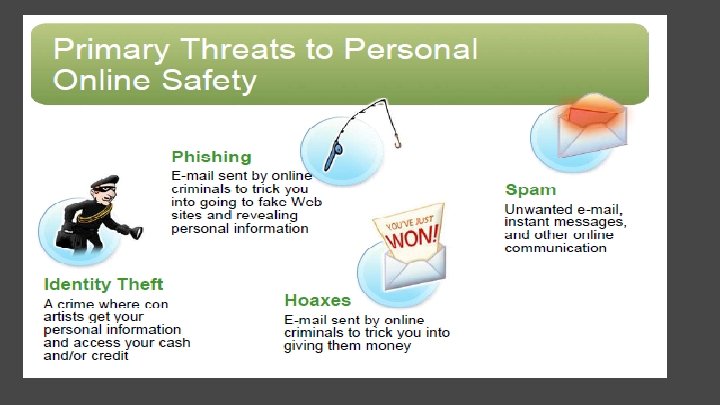
Primary Threats to Computer Security Viruses/Worms Software programs designed to invade your computer, and copy, damage, or delete your data. Trojans Viruses that pretend to be helpful programs while destroying your data, damaging your computer, and stealing your personal information. Spyware Software that tracks your online activities or displays endless ads.



SOCIAL ENGINEERING Basic principal “There is no patch for human stupidity…” Art of Deception, Kevin Mitnick

What is done in Turkey Trainings to increase the awareness of children and families

What is done NGOs: Going every city of Turkey to tell the Internet… how to use it and why needed ISPs: Giving online security trainings, take logs of their users

Some rules from these trainings • Do not share your personal information during email and insatant messaging (i. e Account information, Password, Age, Address, E-mail address, Phone number, Bank information) • Only visit secure sites, be sure where you are • Be carefull when using wireless networks

Real events A person who used modem without password has fallen the court • The student living in the dormitory was punished because of sharing his laptop while accessing the internet. •

What is done Web sites are prepared by government bodies http: //www. guvenlinet. org/ http: //www. cybersecurity. gov. tr/ http: //www. guvenliweb. org. tr/index_eng. php http: //www. ihbarweb. org. tr/eng/index. html

New regulation: “Safe Internet Service” • Safe Internet Service is the option of receipt of safe service from the Internet by the users who wish to use such service the infrastructure of which is created by Access Providers. • Published by Information and Communication Authority • After a 3 months test period, it started to use today (22. 11. 2011) • There are different packets and all packets are free of charge, easy to upload and fast • There assist questions for you while selecting suitable one.

New regulation: “Safe Internet Service” • The Safe Internet Service will consist of the child profile, family profile and domestic profile in addition to the current standard profile. • Child profile is the profile where access to the domain name, IP address and ports sent to the operators by the Authority is achieved. • Family Profile is the profile where access to the domain names, IP address port and web proxy sites sent to the operators by the Authority is not achieved. • Domestic Internet Profile is the profile where access to only the domain name, IP address and ports which are hosted within the country and sent to the operators by the Authority is achieved. • Standard profile refers to the profile where the current Internet is accessed and there is no limitation regarding the Internet sites and applications that can be accessed by the user.

Other regulations • Electronic Communications Act: Protecting information security and the privacy of communication , Taking precautions set forth by law in order to ensure national security, public order and the smooth operation of public services, Protecting personal data and privacy and ensuring network security against unauthorized access • Security of Electronic Communications Directive: Obligating the electronic communications operators to comply with the TS ISO/IEC 27001 standard • With the “Interoperability Reference Guide”, in the context of e. Transformation Turkey Project, all critical bodies should implement TS ISO/IEC 27001 system • Directive on Processing of Personal Data and Protection of Privacy in the Electronic Communications Sector: Protection of privacy, setting procedures for the processing of traffic and location data • Draft Procedures and Principles on the Secure Usage of Internet: Obligating the Internet service providers to provide Secure Internet Usage service to the subscribers

Cyber Security Activities • http: //www. cybersecurity. gov. tr • Cyber Security Exercise 2011 was executed successfully with the cooperation of Information and Communications Authority and TUBITAK Informatics and Information Security Advanced Technologies Research Center on 25 -28 January 2011. • The aim of the event was to increase the cyber security awareness throughout the country and to inform the participants about the precautions to be taken against cyber threats and to exercise the responses to be given to the cyber security incidents.

Cyber Security Activities • The National Cyber Security Exercise was performed with the participants from 41 public and private agencies, corporations and institutions including finance, electronic communication, education, defense sectors and the armed forces, juridical units, police force and several ministries. • 6 of the participants were observers. • 200 people consisting of IT experts, jurists and public relations experts participated in the exercise.

Thank you very much. . . gozbilgin@gmail. com