Home Plug AV MAC c 2013 R Newman

































- Slides: 72

Home. Plug AV MAC (c) 2013 R. Newman University of Florida

What is Home. Plug AV? • Open industry standard – 4+ manufacturers (including Intellon/Atheros) – Compatible with HP 1. 0 • Developed 2003 -2007 by Homeplug Powerline Alliance (HPA) – Consortium of chip designers, OEMs, PLC users – Products shipped in Q 1 2006 • Most widely available ethernet class PLC – 150 Mbps coded PHY data rate – 0 ver 40 million units shipped • Comprises – PHY – modulation, coupling, FEC, etc. – MAC – medium access, ARQ, etc. – Bridging – to other PLC networks or to 803. 3/11/etc.

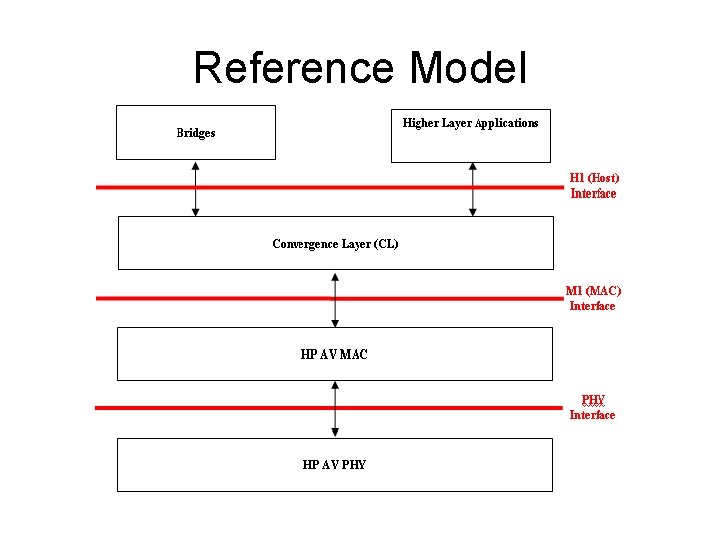
Reference Model

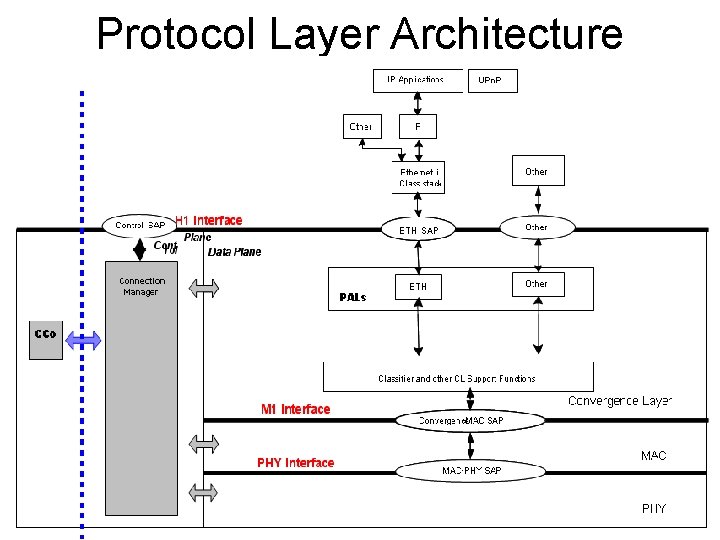
Protocol Layer Architecture

HPAV Challenges • Backward compatibility with HP 1. 0 • Delivered base of over 10 million chips • Return customers likely • Take advantage of high speed PHY • Fixed time overheads for delimiters/VCS • MSDUs typically less than 1500 octets • Provide Qo. S for video/audio/gaming/etc. • Latency and jitter control • Bandwidth “guarantees” • Deal with PHY challenges • Channels change – can degrade, cause loss • Impulse noise may destroy 1 -2 symbols per impulse • Hidden nodes, neighbor networks

HPAV Challenges (2) • Minimize overhead • Aim at 80% MAC efficiency for streams • Low efficiency expected with low data rate streams • User-friendly security • Must be understandable • Must be convenient • Must be secure • Stations may leave unexpectedly • Consumer electronic devices • Not dedicated to AVLN like AP is to WLAN

HPAV Solution Approaches • Backward compatibility with HP 1. 0 • Maintain common VCS • Take advantage of high speed PHY • Maximize PHY Body length for efficiency • Provide Qo. S for video/audio/gaming/etc. • • Timestamp MSDUs with Qo. S needs Move on if MSDU can’t be delivered on time Admission control for new Qo. S streams Scheduled access

HPAV Solution Approaches (2) • Deal with PHY challenges • • Allow tone maps to vary with line cycle Maintain view of channel rates Maintain view of stream backlogs Allow partial reception of MPDU RTS/CTS for hidden nodes Repeating for hidden nodes Redundancy for scheduling information Neighbor network coordination • User-friendly security • • Mental models Network password entry Device password entry Push-button authorization

HPAV Solution Approaches (3) • Minimize overhead • • • Aggregation of MSDUs, management messages Minimize use of delimiters Small addresses – 8 -bit Terminal Equipment IDs (TEIs) Allow for contention-free access Integrated encryption/IV derivation • Stations may leave unexpectedly • Employ soft state • Use negotiation for determining coordinator • Allow for handover/recovery of responsibilities

HPAV Solutions • Backward compatibility with HP 1. 0 • Hybrid delimiters – allow for common VCS • Central Coordinator • Allows admission control/scheduled access • Must be able to move CCo/recover from loss of CCo • Maintains authoritative network time base • Central Beacon • • • Provides common information Provides synchronization for access Advertises network time base (NTB) for Qo. S Includes persistence for redundancy Synchronized to line cycle • Proxy Coordinator • Repeats Central Beacon for hidden nodes

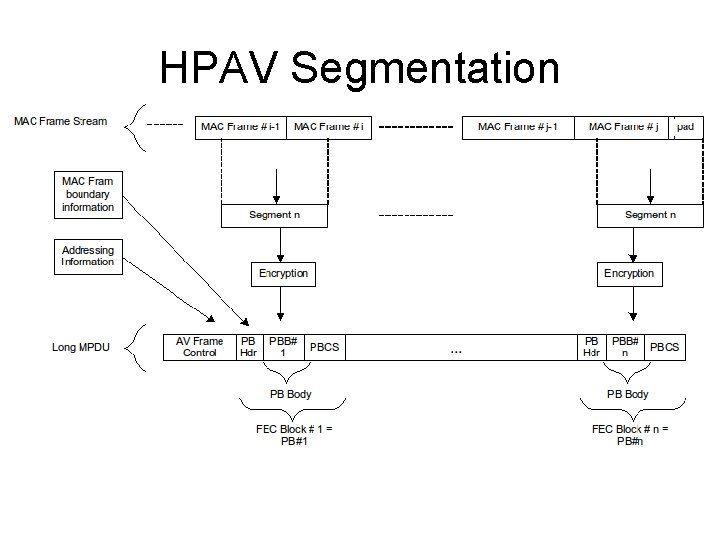
HPAV Solutions (2) • Contention-Free Periods • • • Managed by call admission through CCo Regions reserved for specific streams Reservations persist in same part of line cycle Qo. S stream creation negotiated by all parties Global link identifiers for efficient reference Expand/squeeze as needs/channels change • Two-level Segmentation/Reassembly • • • Aggregate MSDUs & MMs into MAC Frame stream Segment MF Stream for encryption/transmission Make segments unit of reliable delivery inside MAC CRC per segment Selective Acknowledgements for multiple segments

HPAV Solutions (3) • MPDU bursting to save on ACKs • Acknowledge all segments in multiple MPDUs in SACK • MPDU number to know when to send SACK • MPDU count to know burst duration • AV Logical Networks based on cryptography • • Key hierarchy NMK needed to join logical network NEK used for data encryption Integrated segmentation/encryption IV derived from MPDU and segment information Push-button inherently insecure at time of join Two security levels Password parameter definition

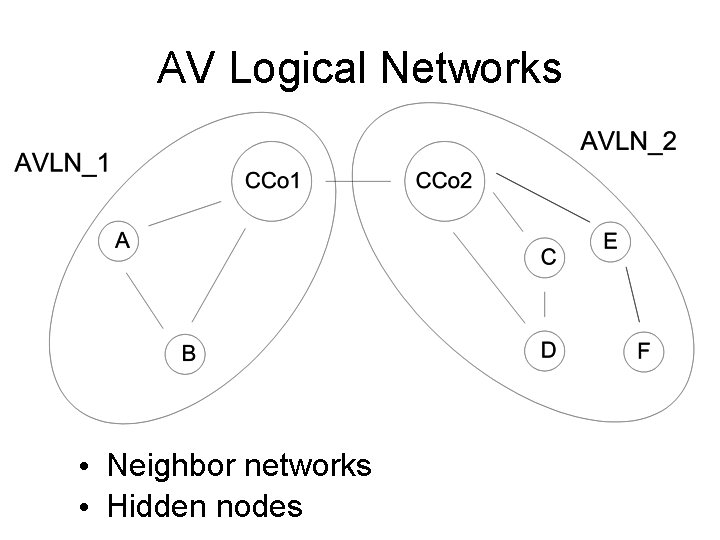
HPAV Networks • Physical Network (Phy. Net) • • Relative to a station (STA) All other STAs able to communicate with the reference STA • Logical Network (AVLN) • • Has a Central Coordinator (CCo) STA Set of STAs with same • • Network ID (NID) and Network Membership Key (NMK) (usually)

AV Logical Networks • Neighbor networks • Hidden nodes

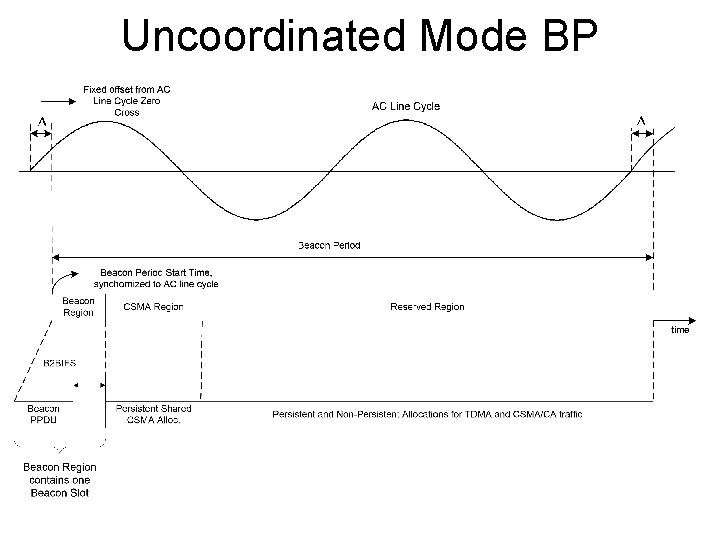
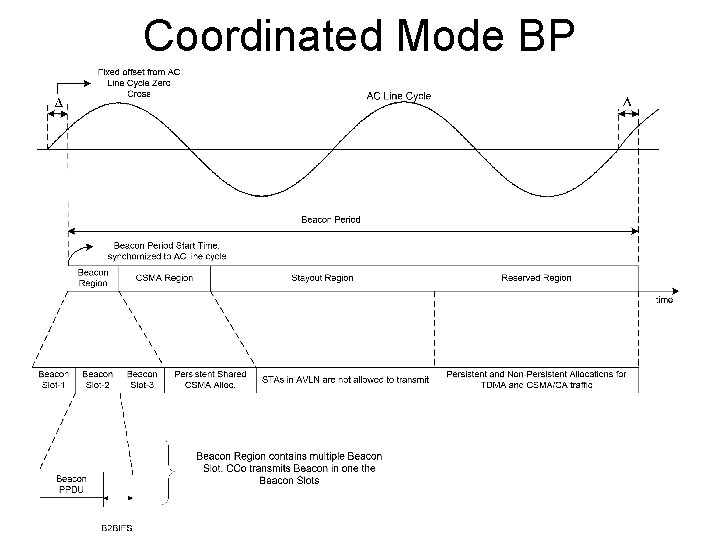
HPAV General Operation • Each AVLN has a CCo • • • CCo is determined dynamically CCo give general information in beacon CCo admits new STAs • STAs join AVLN by requesting NEK • • • STA must have Network Membership Key (NMK) to get Network Encryption Key (NEK) Unauthenticated STAs can do very little STA gets NEK from CCo • Time divided into Beacon Periods (BPs) • Access information based on BP

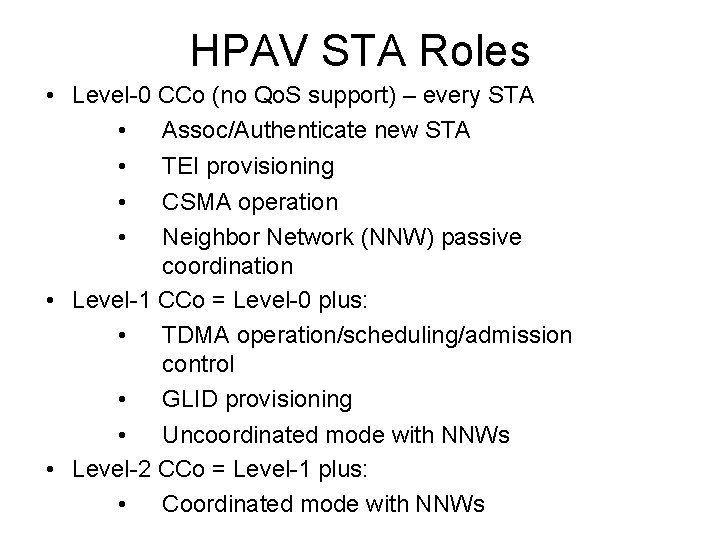
HPAV STA Roles • Level-0 CCo (no Qo. S support) – every STA • Assoc/Authenticate new STA • TEI provisioning • CSMA operation • Neighbor Network (NNW) passive coordination • Level-1 CCo = Level-0 plus: • TDMA operation/scheduling/admission control • GLID provisioning • Uncoordinated mode with NNWs • Level-2 CCo = Level-1 plus: • Coordinated mode with NNWs

HPAV Beacon Periods

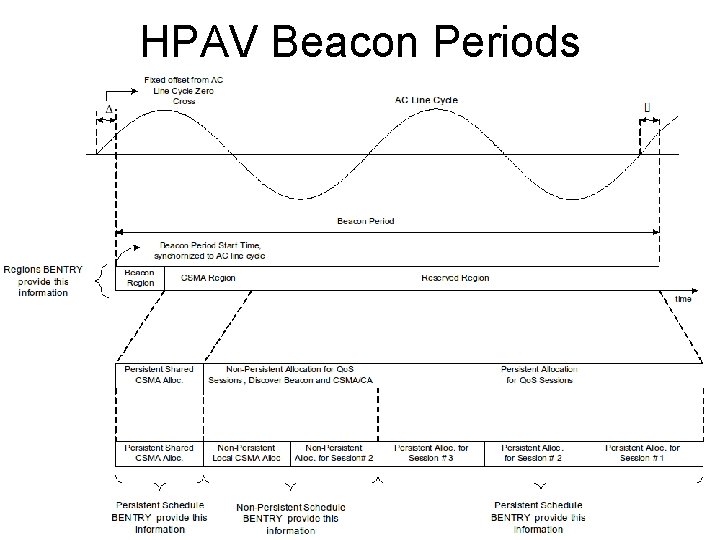
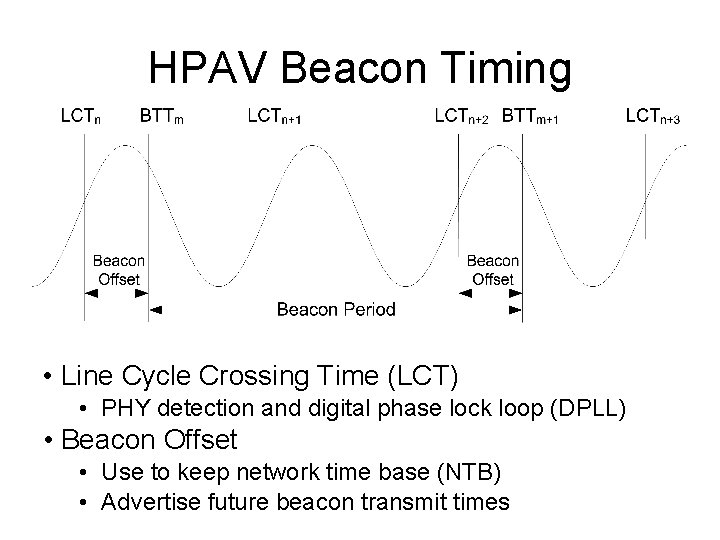
HPAV Beacon Timing • Line Cycle Crossing Time (LCT) • PHY detection and digital phase lock loop (DPLL) • Beacon Offset • Use to keep network time base (NTB) • Advertise future beacon transmit times

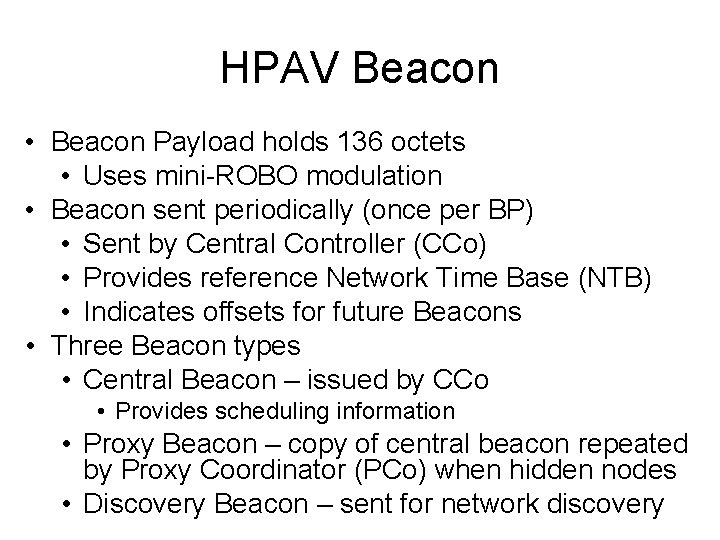
HPAV Beacon • Beacon Payload holds 136 octets • Uses mini-ROBO modulation • Beacon sent periodically (once per BP) • Sent by Central Controller (CCo) • Provides reference Network Time Base (NTB) • Indicates offsets for future Beacons • Three Beacon types • Central Beacon – issued by CCo • Provides scheduling information • Proxy Beacon – copy of central beacon repeated by Proxy Coordinator (PCo) when hidden nodes • Discovery Beacon – sent for network discovery

Beacon Scheduling Info • Non-Persistent Scheduling Information • • Can change from one Beacon Period to the next Extra allocations to backlogged Qo. S streams Extra CSMA region Discover beacons • Persistent Scheduling Information • • • Remains constant for advertised number of BPs Allows access even when Beacon is lost Persistence information included in Beacon Persistent CSMA allocations – for CSMA access Persistent TDMA allocations – contention-free May include preview schedule when changing

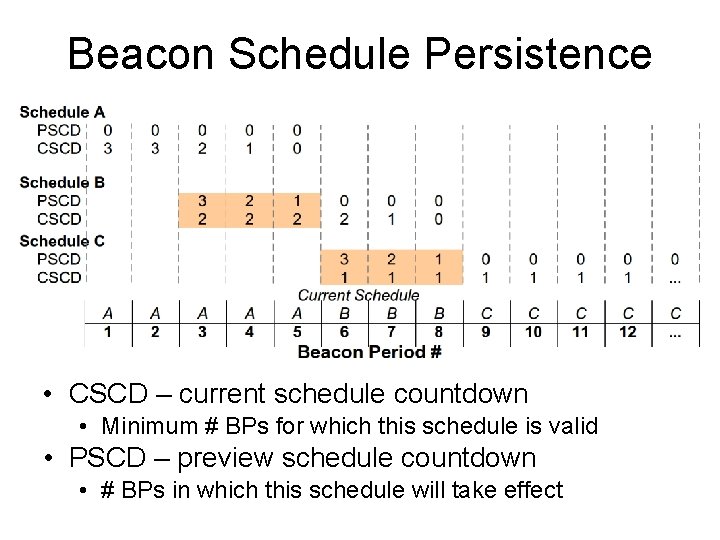
Beacon Schedule Persistence • CSCD – current schedule countdown • Minimum # BPs for which this schedule is valid • PSCD – preview schedule countdown • # BPs in which this schedule will take effect

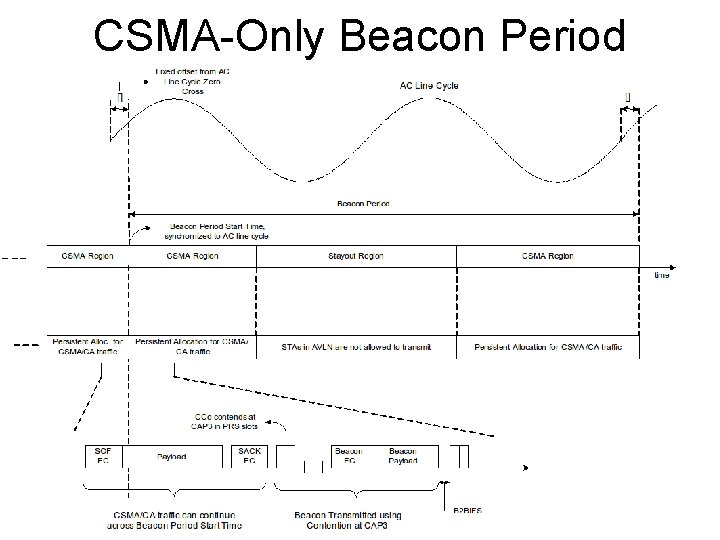
CSMA-Only Beacon Period

Uncoordinated Mode BP

Coordinated Mode BP

Channel Access • Beacons • In Beacon Slot (Coordinated and Uncoordinated) • CSMA (CSMA-Only mode, and Discovery Beacons) • CSMA (Contention-based Access) • • Like Home. Plug 1. 0. 1 Two priority reservation slots (PRS 0, PRS 1) Contention window depending on priority, history May use RTS/CTS for hidden nodes • TDMA (Contention-free Access) • • Must have global link identifier (GLID) CCo does admission control, scheduling Schedule advertised in central beacon Backlog advertised for non-persistent extra allocation

Links and Connections • Connections – higher layer abstraction • May be unidirectional unicast, bidirectional, or multicast • Do not reflect the asymmetry of PLC channels • Links - Used by Convergence Layer (CL) • Unidirectional (single source) • May be unicast or multicast/broadcast • Reflect underlying channel characteristics • Allow for scheduling based on channel • Local links for CSMA (source + link ID unique) • Global links for TDMA (assigned by CCo) • Connection Manager determines mapping to link • Connectionless traffic assigned a “priority link” • Priority Link IDs (PLIDs) only identify priority

Links and Scheduling • Priority Link IDs (PLIDs): 0 x 00 -0 x 03 • Only indicate priority of traffic • Compete in CP • Local Link IDs (LLIDs): 0 x 04 -0 x 7 F • Assigned by local STA’s CM • Compete in CP • Global Link IDs (GLIDs): 0 x 80 -0 x. FF • Used in Beacon Entries for scheduling • Special values: • 0 x. FF = local CSMA allocation • 0 x. FE = shared CSMA allocation • 0 x. FD = Discover Beacon by designated STA • 0 x. FC = Contention Free Period Initiation region • 0 x 80 -0 x. F 7 = CCo-assigned global link IDs • Rest are reserved

Connection IDs and CSPECs • Connection ID (CID) • Assigned by initiating STA’s CM • 16 -bit concatenation of TEI and initial LLID • Globally unique in AVLN • Connection Specification (CSPEC) • Associated with each connection • Contains Qo. S parameters for connection • Connection setup • • • HLE gives Connection Manager (CM) CSPEC If feasible, CM contacts destination CM If destination CM/HLE agree, connection formed If GLID needed (based on CSPEC), then CCo asked If CCo agrees, assigns GLID and schedules cnx Release messages needed on failure

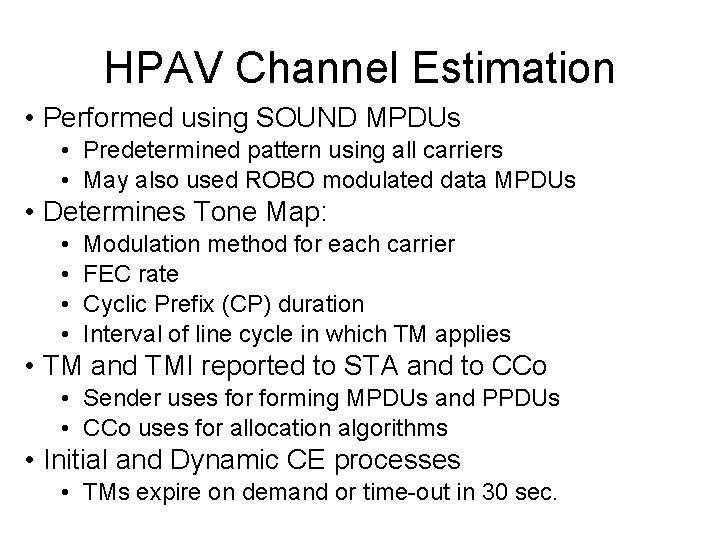
HPAV Channel Estimation • Performed using SOUND MPDUs • Predetermined pattern using all carriers • May also used ROBO modulated data MPDUs • Determines Tone Map: • • Modulation method for each carrier FEC rate Cyclic Prefix (CP) duration Interval of line cycle in which TM applies • TM and TMI reported to STA and to CCo • Sender uses forming MPDUs and PPDUs • CCo uses for allocation algorithms • Initial and Dynamic CE processes • TMs expire on demand or time-out in 30 sec.

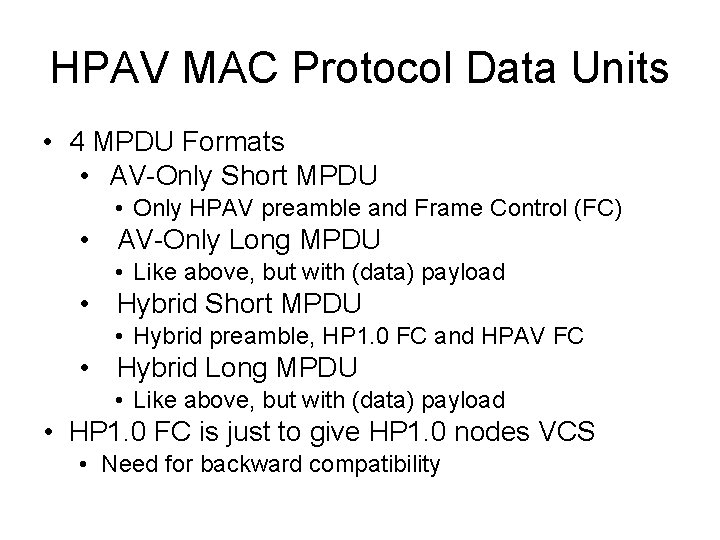
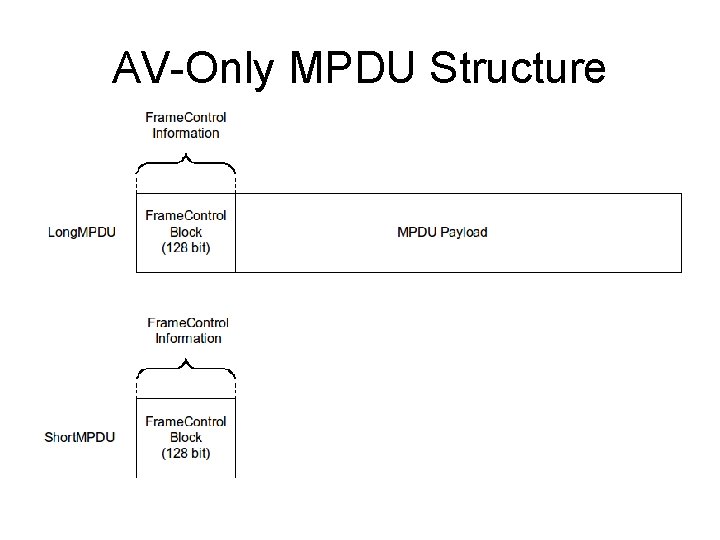
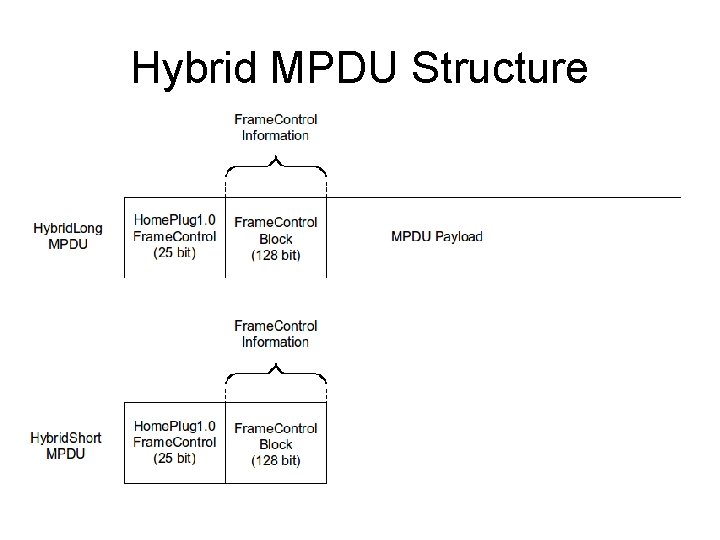
HPAV MAC Protocol Data Units • 4 MPDU Formats • AV-Only Short MPDU • Only HPAV preamble and Frame Control (FC) • AV-Only Long MPDU • Like above, but with (data) payload • Hybrid Short MPDU • Hybrid preamble, HP 1. 0 FC and HPAV FC • Hybrid Long MPDU • Like above, but with (data) payload • HP 1. 0 FC is just to give HP 1. 0 nodes VCS • Need for backward compatibility

AV-Only MPDU Structure

Hybrid MPDU Structure

HPAV MPDU Structure • Delimiter • Hybrid or AV-mode • HP 1. 0 FC is as in Home. Plug 1. 0. 1 (25 bits) • FC_AV holds 128 bits • Mapped by PHY to preamble and coded FC(s) • 7 Delimiter Types • Two sizes • Long MPDUs have payload • Short MPDUs have no payload (delimiter only) • Payload (if present) consists of PHY Blocks (PBs) • 520 octet or 136 octet length • Encoded by PHY as FEC blocks

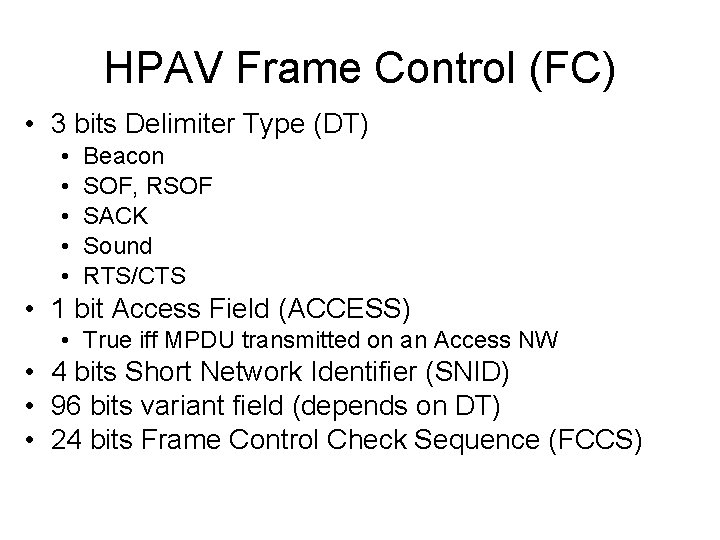
HPAV Frame Control (FC) • 3 bits Delimiter Type (DT) • • • Beacon SOF, RSOF SACK Sound RTS/CTS • 1 bit Access Field (ACCESS) • True iff MPDU transmitted on an Access NW • 4 bits Short Network Identifier (SNID) • 96 bits variant field (depends on DT) • 24 bits Frame Control Check Sequence (FCCS)

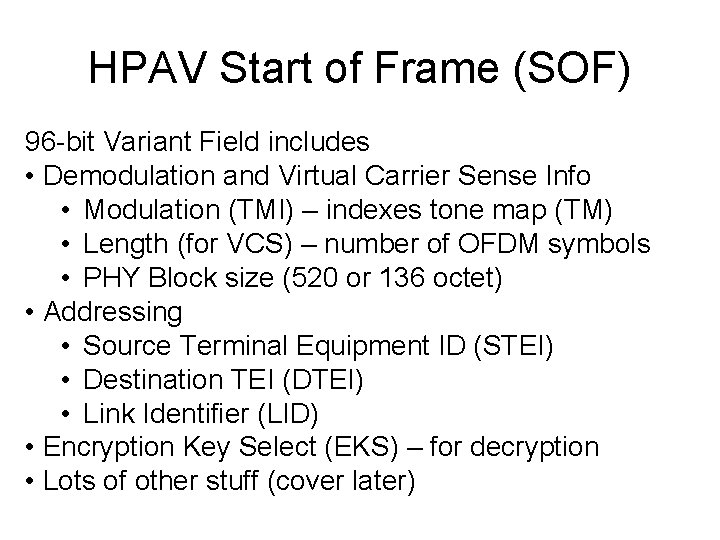
HPAV Start of Frame (SOF) 96 -bit Variant Field includes • Demodulation and Virtual Carrier Sense Info • Modulation (TMI) – indexes tone map (TM) • Length (for VCS) – number of OFDM symbols • PHY Block size (520 or 136 octet) • Addressing • Source Terminal Equipment ID (STEI) • Destination TEI (DTEI) • Link Identifier (LID) • Encryption Key Select (EKS) – for decryption • Lots of other stuff (cover later)

HPAV Selective ACK (SACK) 96 -bit Variant Field includes • Destination TEI (DTEI) • Coordination information • Encoded bitmap of correctly received PBs • Bits correspond to BP position in received transmission • Custom compression capability • A little other stuff (cover later)

HPAV Reverse SOF (RSOF) Carries SACK info plus a return payload 96 -bit RSOF Variant Field includes • SACK Information (like SACK) • Demodulation and Virtual Carrier Sense Info • Modulation (TMI) – indexes tone map (TM) • Length (for VCS) – number of OFDM symbols • PHY Block size (520 or 136 octet) • Addressing • DTEI only (why? Why not STEI/LID? ) • A little other stuff (cover later)

HPAV Request/Clear to Send (RTS/CTS) Needed when hidden nodes present 96 -bit Variant Field includes • Addressing • Source Terminal Equipment ID (STEI) • Destination TEI (DTEI) • Link Identifier (LID) • Coordination information • Duration • How long is medium busy • A little other stuff (cover later) BUT – only deals with one level of hidden nodes!

HPAV Sound/Sound. Ack Similar to SOF, but used for channel estimation Fixed modulation (ROBO) 96 -bit Variant Field includes • Channel Estimation and Virtual Carrier Sense Info • Maximum TMs requested • Length (for VCS) – time of payload • PHY Block size (520 or 136 octet) • Last SOUND flag • Sound ACK flag – indicates this is an ACK • Reason for SOUND • Addressing • STEI, DTEI, LID • Some other stuff (cover later)

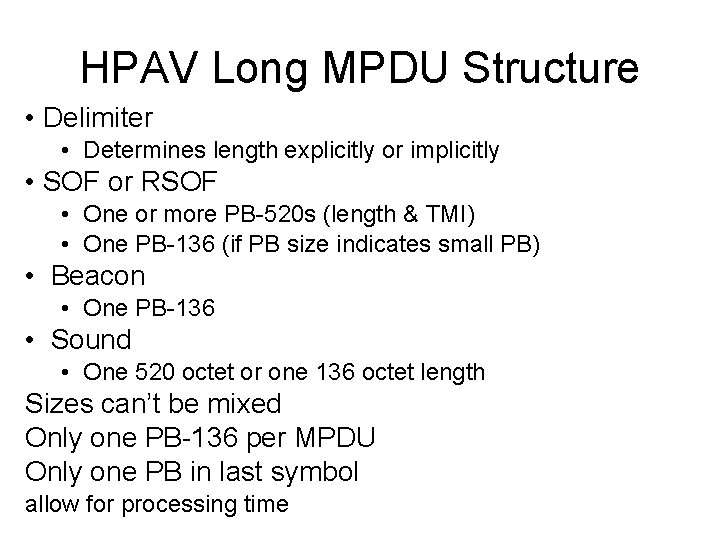
HPAV Long MPDU Structure • Delimiter • Determines length explicitly or implicitly • SOF or RSOF • One or more PB-520 s (length & TMI) • One PB-136 (if PB size indicates small PB) • Beacon • One PB-136 • Sound • One 520 octet or one 136 octet length Sizes can’t be mixed Only one PB-136 per MPDU Only one PB in last symbol allow for processing time

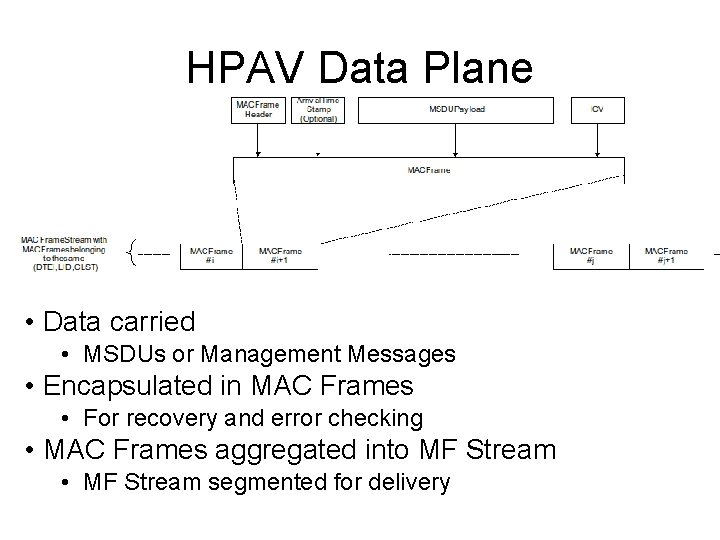
HPAV Data Plane • Data carried • MSDUs or Management Messages • Encapsulated in MAC Frames • For recovery and error checking • MAC Frames aggregated into MF Stream • MF Stream segmented for delivery

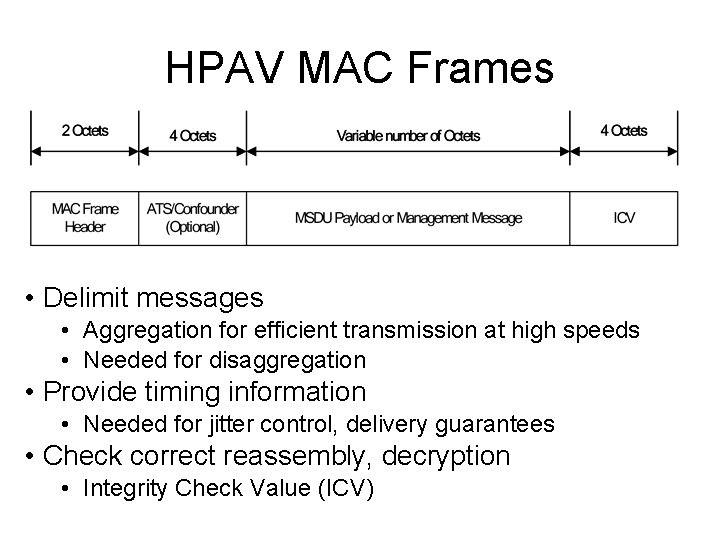
HPAV MAC Frames • Delimit messages • Aggregation for efficient transmission at high speeds • Needed for disaggregation • Provide timing information • Needed for jitter control, delivery guarantees • Check correct reassembly, decryption • Integrity Check Value (ICV)

MAC Frame Fields • MF Header • MF Type (2 bits) • • Bit pad to end of segment MSDU without ATS MSDU with ATS Management Message with confounder • MF Length (14 bits) • ATS/Confounder (0 or 32 bits) • Arrival timestamp for AV streams • Random confounder for Management Messages • Body • MSDU from higher layer or Management Message • Integrity Check Value (32 bit CRC) • Total overhead = 6 -10 octets

HPAV Segmentation

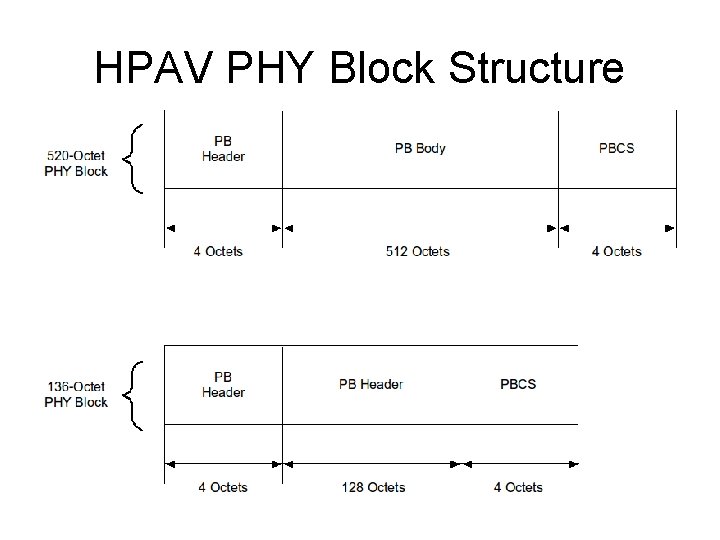
HPAV PHY Block Structure • PBs are mapped by PHY to FEC Blocks • FEC succeeds or fails • PBs are basic unit of delivery by MAC internally • PB is ACKed or retransmitted using SR-ARQ • SACK specifies ACK/NAK • PH Header (PBH) – 4 octets • Info for reassembly, disaggregation, recovery • PB Body (PBB) • 512 octets or 128 octets long – not interpreted here • PB Check Sequence (PBCS) • CRC-32 – not encrypted – for checking PB reception • PB discarded and NAKed if incorrect

HPAV PHY Block Structure

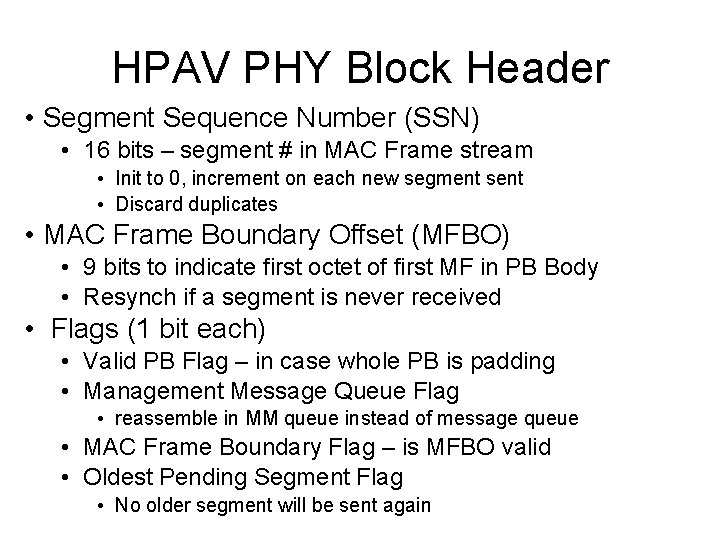
HPAV PHY Block Header • Segment Sequence Number (SSN) • 16 bits – segment # in MAC Frame stream • Init to 0, increment on each new segment sent • Discard duplicates • MAC Frame Boundary Offset (MFBO) • 9 bits to indicate first octet of first MF in PB Body • Resynch if a segment is never received • Flags (1 bit each) • Valid PB Flag – in case whole PB is padding • Management Message Queue Flag • reassemble in MM queue instead of message queue • MAC Frame Boundary Flag – is MFBO valid • Oldest Pending Segment Flag • No older segment will be sent again

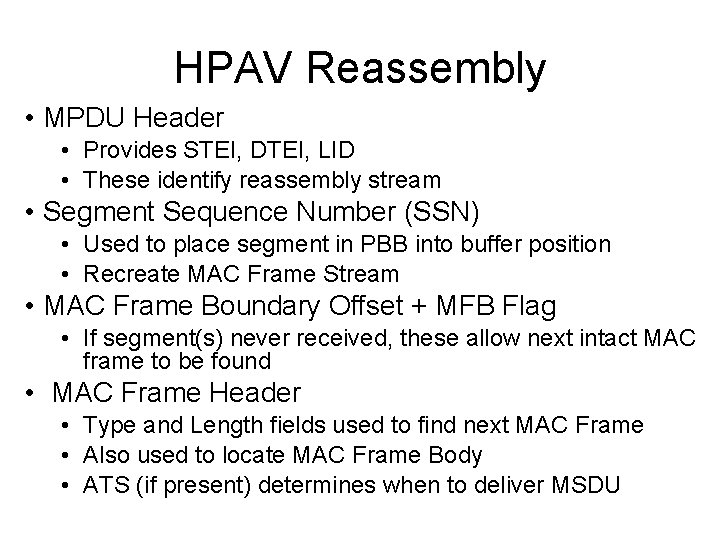
HPAV Reassembly • MPDU Header • Provides STEI, DTEI, LID • These identify reassembly stream • Segment Sequence Number (SSN) • Used to place segment in PBB into buffer position • Recreate MAC Frame Stream • MAC Frame Boundary Offset + MFB Flag • If segment(s) never received, these allow next intact MAC frame to be found • MAC Frame Header • Type and Length fields used to find next MAC Frame • Also used to locate MAC Frame Body • ATS (if present) determines when to deliver MSDU

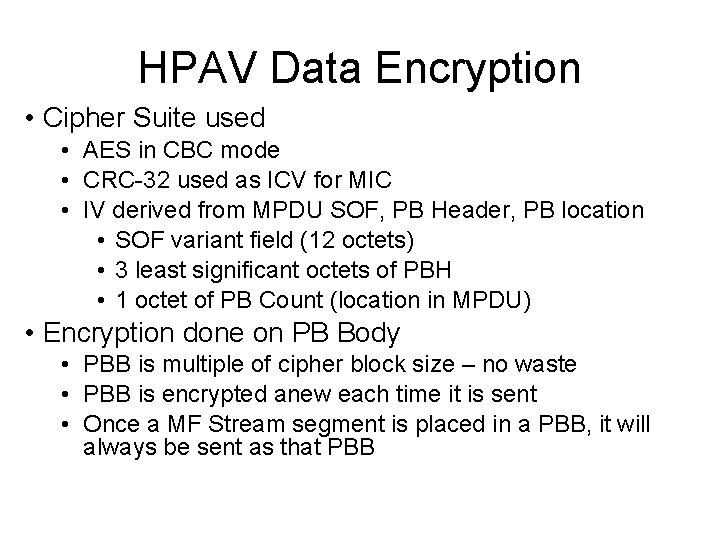
HPAV Data Encryption • Cipher Suite used • AES in CBC mode • CRC-32 used as ICV for MIC • IV derived from MPDU SOF, PB Header, PB location • SOF variant field (12 octets) • 3 least significant octets of PBH • 1 octet of PB Count (location in MPDU) • Encryption done on PB Body • PBB is multiple of cipher block size – no waste • PBB is encrypted anew each time it is sent • Once a MF Stream segment is placed in a PBB, it will always be sent as that PBB

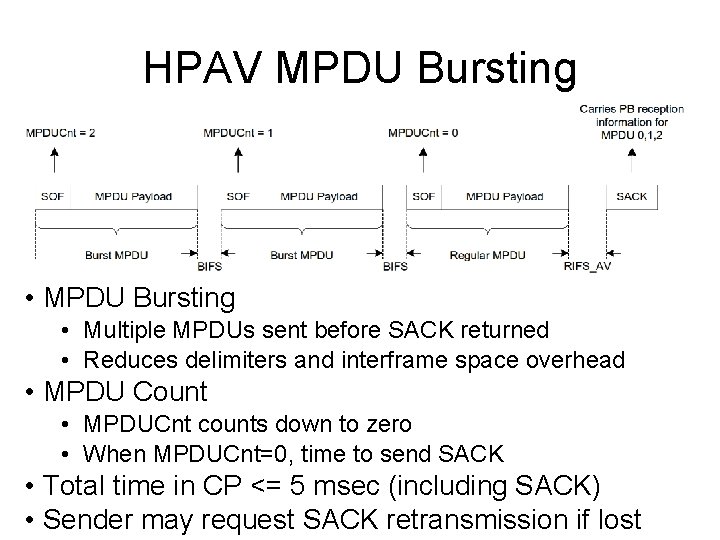
HPAV MPDU Bursting • MPDU Bursting • Multiple MPDUs sent before SACK returned • Reduces delimiters and interframe space overhead • MPDU Count • MPDUCnt counts down to zero • When MPDUCnt=0, time to send SACK • Total time in CP <= 5 msec (including SACK) • Sender may request SACK retransmission if lost

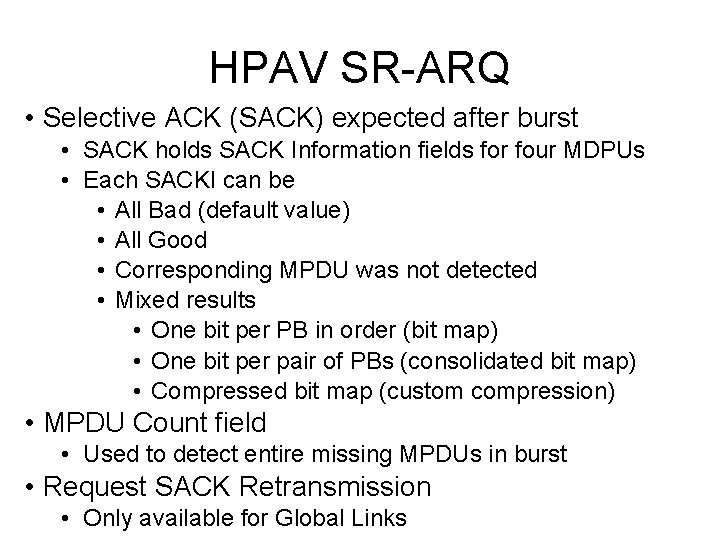
HPAV SR-ARQ • Selective ACK (SACK) expected after burst • SACK holds SACK Information fields for four MDPUs • Each SACKI can be • All Bad (default value) • All Good • Corresponding MPDU was not detected • Mixed results • One bit per PB in order (bit map) • One bit per pair of PBs (consolidated bit map) • Compressed bit map (custom compression) • MPDU Count field • Used to detect entire missing MPDUs in burst • Request SACK Retransmission • Only available for Global Links

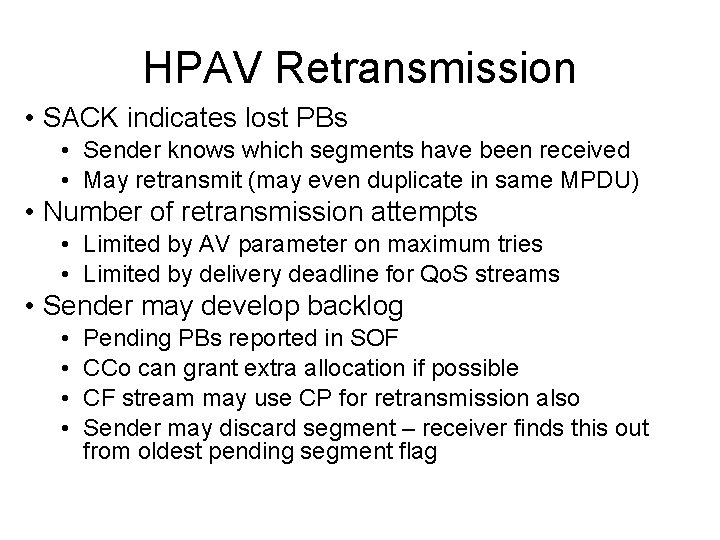
HPAV Retransmission • SACK indicates lost PBs • Sender knows which segments have been received • May retransmit (may even duplicate in same MPDU) • Number of retransmission attempts • Limited by AV parameter on maximum tries • Limited by delivery deadline for Qo. S streams • Sender may develop backlog • • Pending PBs reported in SOF CCo can grant extra allocation if possible CF stream may use CP for retransmission also Sender may discard segment – receiver finds this out from oldest pending segment flag

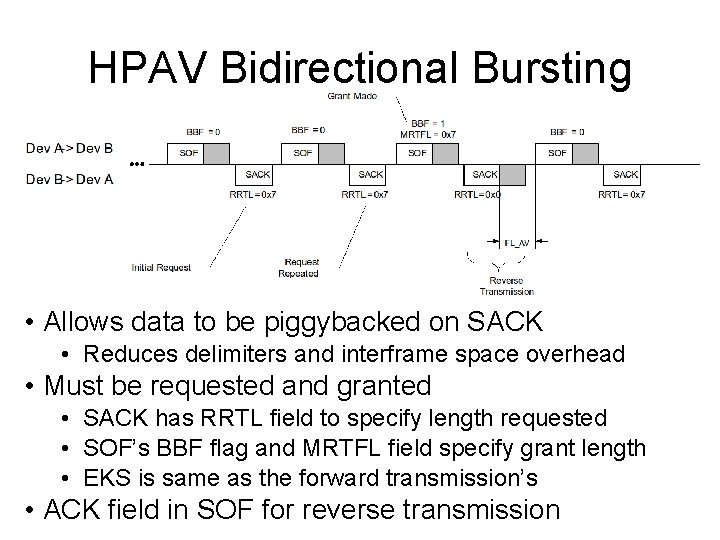
HPAV Bidirectional Bursting • Allows data to be piggybacked on SACK • Reduces delimiters and interframe space overhead • Must be requested and granted • SACK has RRTL field to specify length requested • SOF’s BBF flag and MRTFL field specify grant length • EKS is same as the forward transmission’s • ACK field in SOF for reverse transmission

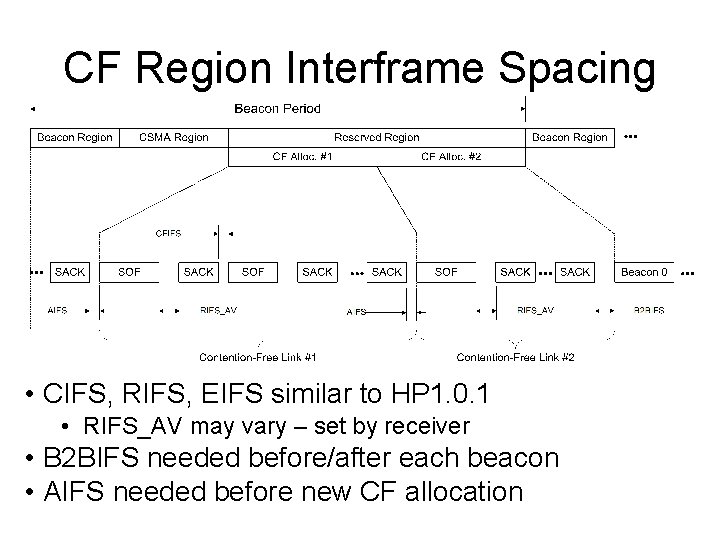
CF Region Interframe Spacing • CIFS, RIFS, EIFS similar to HP 1. 0. 1 • RIFS_AV may vary – set by receiver • B 2 BIFS needed before/after each beacon • AIFS needed before new CF allocation

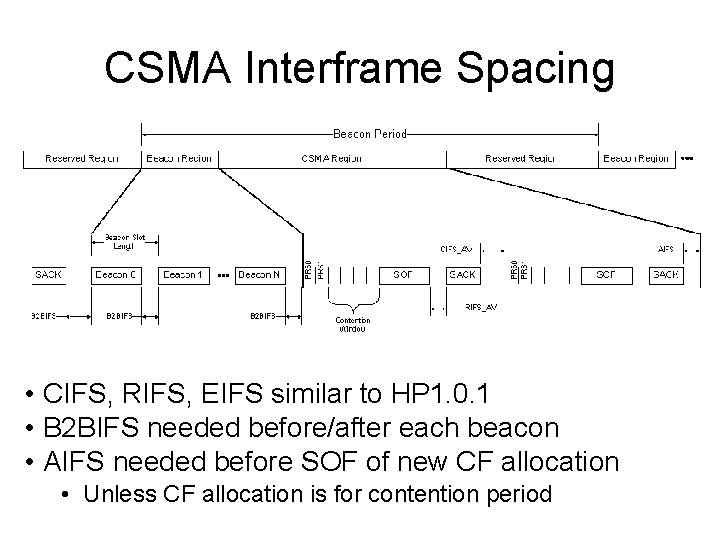
CSMA Interframe Spacing • CIFS, RIFS, EIFS similar to HP 1. 0. 1 • B 2 BIFS needed before/after each beacon • AIFS needed before SOF of new CF allocation • Unless CF allocation is for contention period

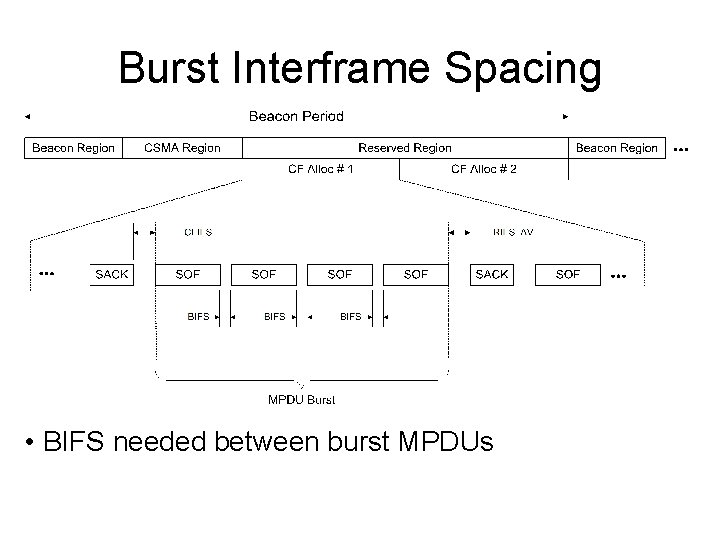
Burst Interframe Spacing • BIFS needed between burst MPDUs

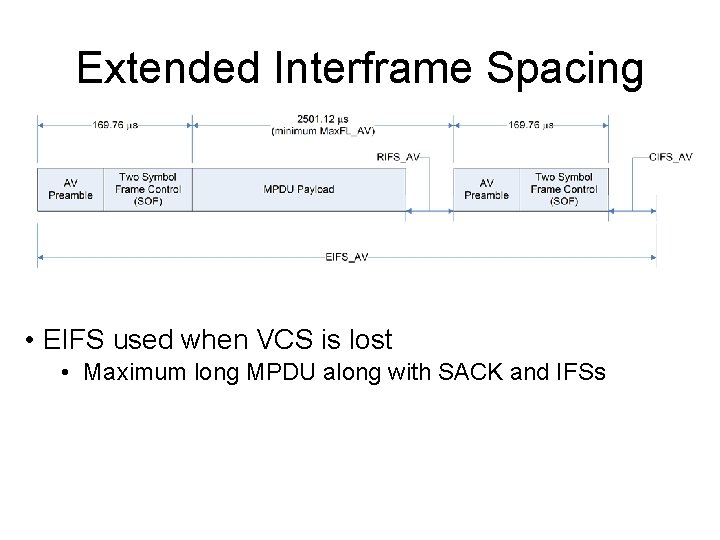
Extended Interframe Spacing • EIFS used when VCS is lost • Maximum long MPDU along with SACK and IFSs

Central Coordinator (CCo) • Issues central beacon • Associates new stations • Issues TEI with lease, announces to AVLN • Authenticates new stations • Verifies possession of NMK, issues NEK • Rotates NEK • Performs admission control • Determines resource needs and availability • Issues Global LID • Performs scheduling • May perform handover • Transfer CCo functions to another STA • Performs neighbor network coordination

Power-on Behavior • State of STA • Has it ever been a member of an AVLN? • Search for AVLNs • Listen for Central and Proxy Beacons • Listen for Discovery Beacons • Listen for Unassociated STA advertisements • If find matching Network ID (NID) • Associate • Attempt to authenticate (get NEK) • End if successful, else continue (mark NID) • If time runs out • If matching Unassociated STA NID, try to form AVLN • Else if AVLN present, advertise Unassociated STA • Else become Unassociated CCo (issue beacon)

Unassociated STA • Advertise infrequently • Issue Unassociated STA advertisements • Send once per Discovery Period, more or less • Synchronize to an existing AVLN • Adopt mode (Hybrid or AV-Only) from Beacon • Use NTB of AVLN • Use SNID of AVLN in multi-network broadcasts • If find matching Network ID (NID) • If beacon, try to join AVLN • If unassociated STA, try to form AVLN • If AVLN disappears • Become Unassociated CCo

Authenticated STA • Determine whether should become CCo • If STA is a User-appointed CCo, and current CCo is not a User-appointed CCo, request handover • May also execute CCo Selection process, become CCo if more capable or better positioned • May become CCo if current CCo fails and STA is backup • Adopt mode of operation from Beacon • Advertise detection of HP 1. 0/HP 1. 0. 1 delimiters • Piggybacked in SOF, SACK, etc. • If AVLN lost • No central/proxy beacon for timeout period • Start Power-on Procedure • If asked to leave • Become Unassociated STA

CCo Behavior • Perform CCo Duties • As long as there are other STAs in AVLN • If all other STAs leave AVLN • Remain CCo for at least Discovery period • If no STA joins and another AVLN is present, become Unassociated STA • Else become Unassociated CCo • If STA in AVLN should become CCo • • Other STA is User-appointed and this one is not Other STA is more capable or better positioned Execute handover procedure Become STA in AVLN

Mode of Operation • AV-Only Mode • Use AV-Only delimiters • Hybrid Mode • Use Hybrid delimiters • Deciding Mode • • • STA adopts mode of AVLN All STAs listen for HP 1. 0/HP 1. 0. 1 delimiters If seen often enough, advertise using flags CCo adopts mode based on detection Revert to AV-Only if HP 1. 0/HP 1. 0. 1 delimiters no longer detected

AVLNs • Have a CCo • CCo issues central beacon, acts as coordinator • May have Proxy Coordinator(s) also • Share same Network ID (NID) • NID normally derived from NMK • Should uniquely identify AVLN • Remains constant regardless of CCo • Share same Security Level • NMK associated with SL • SL must be the same throughout AVLN • Share same NEK • CCo provides NEK during authentication using NMK • NEK used to encrypt traffic in AVLN

Sub-AVLNs • One AVLN may have multiple sub-AVLNs • Share a single CCo • Share same Network ID (NID) • NID not derived from NMK • CCo must use MAC address to decide which NMK to use for a given STA

User-Friendly AVLN and STA IDs • User-friendly name is printable ASCII string • Use for humans to identify conveniently • Not guaranteed to be unique • STA and AVLNs may have these assigned • Assigning HFIDs • Use primitive over the H 1 interface for either • Use Management Message to CCo for AVLN • Getting HFIDs • Management Message to request from STA or CCo • Request not required to be encrypted • Response to non-encrypted request need not provide actual HFID

Association with an AVLN • Association provides a unique identifier • CCo assigns a valid TEI with lease on request • STA uses special TEI=0 x 00 before obtaining TEI • NID or SNID must be used to disambiguate TEIs • Obtaining a TEI • • STA makes request CCo responds (decline or provide valid TEI/lease) If accepted, CCo advertises all TEI/MAC addresses TEI must be renewed before lease expires • Leaving an AVLN • STA may leave voluntarily – send disassociate message • TEI lease may expire • CCo may ask STA to leave – send leave message

Authentication • Process Steps • Association is obtaining a valid TEI • Authorization is obtaining a valid NMK • Authentication is obtaining a valid NEK • Obtaining a valid NEK • STA must have NMK first • STA requests NEK from CCo using NMK, provide nonce • If CCo decrypts, NMK is valid; provide NEK and nonce using NMK, else CCo indicates failure • Updating NEK • NEK rotated at least once per hour • CCo requests nonce (NEK encrypted); STA responds with nonce (NEK encrypted) • CCo sends set key msg with nonce encrypted with NMK and old NEK; STA acknowledges using same keys

Forming a New AVLN • Circumstances for new AVLN formation • • Two Unassociated STAs with matching NID Two Unassociated STAs using DAK Two Unassociated STAs, one in Join, one in Add Two Unassociated STAs, both in Join • Matching NID • Determine from Unassociated STA advertisements • Decide who becomes CCo from CCo capabilities and MAC address in Unassociated STA advertisements • Winner becomes Unassociated CCo, sends beacons • Other STA(s) join it by associating, authenticating • Loser(s) continue to send Unassociated STA advertisements until beacon with NID detected • Multiple AVLNs with same NID/NMK can merge

Forming a New AVLN (2) • DAK-based Protocol • STA with Device Access Key (DAK) of another STA broadcasts a set-key message encrypted with DAK holding a TEK • Any STA receiving a message like this tries to decrypt it • If it succeeds, then it replies (unicast) encrypting with the Temporary Encryption Key (TEK) the message held • If the initiating STA decrypts a response encrypted with the TEK, it sends a set-key message with the new NMK and the nonce in the reply encrypted with the DAK • If the new STA decrypts this message with its DAK and the nonce matches, it sets its NMK and NID • STAs decide who becomes the CCo from capabilities in the exchanged messages • CCo issues beacons, other STA associates, authenticates

Forming a New AVLN (3) • Push-button Mechanism • Button press causes STA in AVLN to admin another one • STA never in AVLN (or reset) will join an AVLN • Two Unassociated STAs, one in Join, one in Add • • • STA that has been in an AVLN will enter silent Add state STA in Join state will broadcast its desire to join an AVLN STA in Add state will respond unicast and become CCo STA in Join will associate with new AVLN STAs should perform channel adaptation STAs then start UKE protocol • Exchange hash keys • Hash these to form temporary encryption key (TEK) • Use TEK to send NMK from CCo to new STA • STA then authenticates using NMK

Forming a New AVLN (4) • Two Unassociated STAs, both in Join • • STA in Join state will broadcast its desire to join an AVLN STAs will see each other’s advertisements STAs decide who should become CCo from capabilities Winner becomes CCo, generates new random NMK, switches to Add state, sends confirmation to other STA • STA in Join will associate with new AVLN • STAs should perform channel adaptation • STAs then start UKE protocol • Exchange hash keys • Hash these to form temporary encryption key (TEK) • Use TEK to send NMK from CCo to new STA • STA then authenticates using NMK