HIPAA Security Complying with the HIPAA Security Rule



















- Slides: 25

HIPAA Security: Complying with the HIPAA Security Rule Implementation Specifications – Are you Correctly Addressing Them? Thursday, June 5 10: 45 - 11: 45 AM Session 1. 01 Tom Walsh, CISSP 1 Copyright © 2003, Tom Walsh

Tom Walsh • Certified Information Systems Security Professional (CISSP) • Invited speaker at national conferences • Former information security manager for large healthcare system in Kansas City, MO • DOE-certified safeguards and security instructor • A little nerdy, but overall, a nice guy 2 Copyright © 2003, Tom Walsh

HIPAA Security Standards • Administrative Safeguards (55%) – 12 Required, 11 Addressable • Physical Safeguards (24%) – 4 Required, 6 Addressable • Technical Safeguards (21%) – 4 Requirements, 5 Addressable Flexibility, Scalability, and Technology Neutral Covered entities must assess if an implementation specification is reasonable and appropriate 3 Copyright © 2003, Tom Walsh

Addressable Implementation Specifications “In meeting standards that contain addressable implementation specifications, a covered entity will ultimately do one of the following: a. Implement one or more of the addressable implementation specifications; b. Implement one or more alternative security measures; c. Implement a combination of both; or d. Not implement either an addressable implementation specification or an alternative security measure. ” 4 Copyright © 2003, Tom Walsh

Administrative Safeguards • Security Management Process § § Risk Analysis (R) Risk Management (R) Sanction Policy (R) Information System Activity Review (R) “Risk Analysis” is listed before “Assigned Security Responsibility” 5 Copyright © 2003, Tom Walsh

Risk Assessment / Analysis Each covered entity: • Assesses its own security risks • Determines its risk tolerance or risk aversion • Devises, implements, and maintains appropriate security to address its business requirements • Does not imply that organizations are given complete discretion to make their own rules • Documents its security decisions Copyright © 2003, Tom Walsh 6

Risk Analysis Two types: • Qualitative – (Easiest and most common) Rating risks on a scale such as: • Quantitative – (Most difficult to determine) Placing a dollar value on the risk based upon some formulas or calculations 7 Copyright © 2003, Tom Walsh

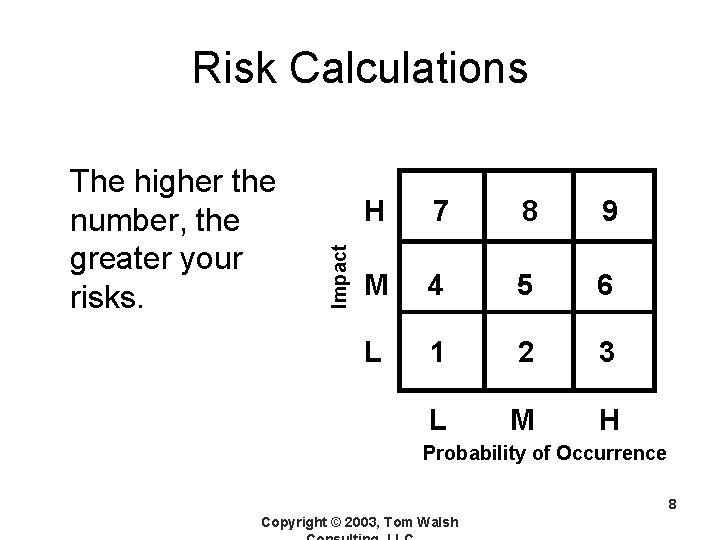
The higher the number, the greater your risks. Impact Risk Calculations H 7 8 9 M 4 5 6 L 1 2 3 L M H Probability of Occurrence 8 Copyright © 2003, Tom Walsh

Administrative Safeguards • Assigned Security Responsibility – Responsibility must rest with one individual to ensure accountability – Information Security Officer (ISO) – Large organizations may have site-security coordinators working with the ISO – Security standards extends to the members of a covered entity’s workforce even if they work at home such as transcriptionists 9 Copyright © 2003, Tom Walsh

Administrative Safeguards • Workforce Security § Authorization and/or Supervision (A) § Workforce Clearance Procedure (A) § Termination Procedures (A) – Authorization controls to verify the identity of the workforce member – Types of background checks that will be conducted for workforce members (Does not imply background checks on everyone. ) – Termination – Collecting access control devices or changing door locks, etc. 10 Copyright © 2003, Tom Walsh

Administrative Safeguards • Information Access Management § Isolating Healthcare Clearinghouse Function (R) § Access authorization (A) § Access Establishment and Modification (A) – Isolating Healthcare Clearinghouse Function – New requirement – Requirement for “User-based, role-based, or context-based” was removed – However – Compliance with the Privacy Rule’s “Minimum necessary” and JCAHO IM standards may drive role-based access controls 11 Copyright © 2003, Tom Walsh

Administrative Safeguards • Security Awareness and Training § § Security Reminders (A) Protection from Malicious Software (A) Log-in Monitoring (A) Password Management (A) – What is the difference between: Training, Education and Awareness? – What other information security content should be covered in workforce training? – “Security awareness training is a critical activity, regardless of an organization’s size. ” 12 Copyright © 2003, Tom Walsh

Administrative Safeguards • Security Incident Procedures § Response and Reporting (R) – Provides a way for users to report unusual occurrences in security or breaches to patient confidentiality – Goals: Identify Contain Correct Prevent 13 Copyright © 2003, Tom Walsh

Administrative Safeguards • Contingency Plan § § § Data Backup Plan (R) Disaster Recovery Plan (R) Emergency Mode Operation Plan (R) Testing and Revision Procedure (A) Applications and Data Criticality Analysis (A) – Documented procedure for the secure, off-site storage and rotation of backups – Work in conjunction with Data Owners to determine the organization’s Recovery Point Objective (RPO) and Recovery Time Objective (RTO) for all other applications as part of a Business Impact Analysis (BIA). 14 Copyright © 2003, Tom Walsh

Administrative Safeguards • Evaluation • Periodic review of technical controls and procedural review of the entity’s security program • Non-Technical review – • • Self assessment, readiness assessment, or gap analysis Certification of systems Compliance documentation Audit logs and incident reports • Technical review – • Vulnerability scan • Testing of security controls 15 Copyright © 2003, Tom Walsh

Administrative Safeguards • Business Associate Contracts and Other Arrangement § Written Contract or Other Arrangement (R) – Identify all business associates who receive or have access to electronic PHI – Tie efforts with the Privacy initiative. – Leverage the opportunity to establish rules for remote access for vendors to limit downstream liability. 16 Copyright © 2003, Tom Walsh

Physical Safeguards • Facility Access Controls § § Contingency Operations (A) Facility Security Plan (A) Access Control and Validation Procedures (A) Maintenance Records (A) 1. To protect buildings, equipment, and media from natural and environmental hazards and unauthorized intrusions 2. Track maintenance records for door lock repairs or changes 17 Copyright © 2003, Tom Walsh

Physical Safeguards • Workstation Use • Workstation Security – Could address both standards in a single policy – Verify workstations are located to prevent unauthorized, casual viewing by others – Conduct a random audit of computer workstations to verify they have been updated with the latest version of virus definitions (Process for standalone PCs and laptops) Copyright © 2003, Tom Walsh 18

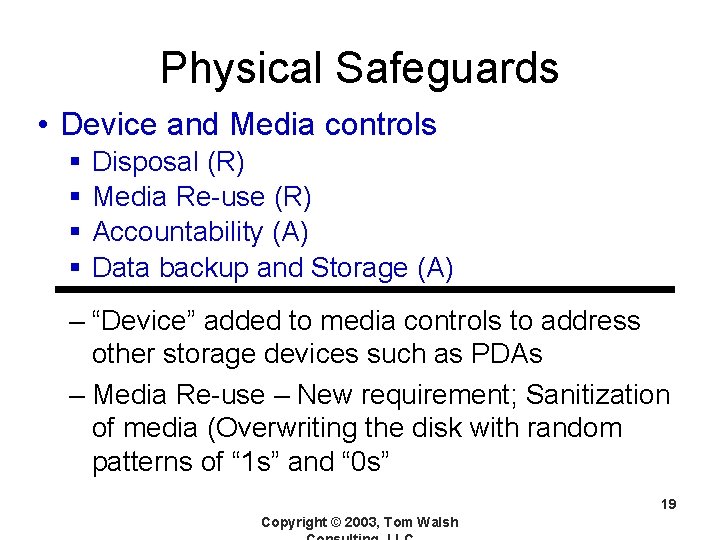
Physical Safeguards • Device and Media controls § § Disposal (R) Media Re-use (R) Accountability (A) Data backup and Storage (A) – “Device” added to media controls to address other storage devices such as PDAs – Media Re-use – New requirement; Sanitization of media (Overwriting the disk with random patterns of “ 1 s” and “ 0 s” 19 Copyright © 2003, Tom Walsh

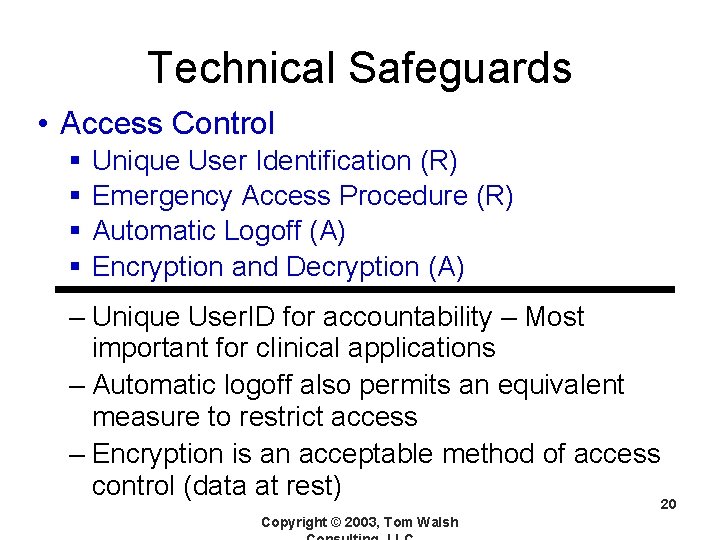
Technical Safeguards • Access Control § § Unique User Identification (R) Emergency Access Procedure (R) Automatic Logoff (A) Encryption and Decryption (A) – Unique User. ID for accountability – Most important for clinical applications – Automatic logoff also permits an equivalent measure to restrict access – Encryption is an acceptable method of access control (data at rest) 20 Copyright © 2003, Tom Walsh

Technical Safeguards • Audit Controls – Use risk assessment and analysis to determine how intensive audit trails need to be – Events that trigger an audit trail need to be jointly determined by the Data Owners, the Privacy and Security Officers – Check with vendors on audit capability – Store audit logs on a separate server – System administrators should not have access to the audit logs 21 Copyright © 2003, Tom Walsh

Technical Safeguards • Integrity § Mechanism to Authenticate Electronic PHI (A) – Document any integrity controls that will be employed especially for transmissions outside of the internal network to ensure the validity of the data being sent or the sender of the data – Examples: Check sum, encryption, PKI, digital signature, etc. 22 Copyright © 2003, Tom Walsh

Technical Safeguards • Person or Entity Authentication – Person or entity authentication is primarily accomplished through User. ID and passwords – Consider two-factor authentication for remote access to systems 23 Copyright © 2003, Tom Walsh

Technical Safeguards • Transmission Security § Integrity Controls (A) § Encryption (A) – “…When electronic protected health information is transmitted from one point to another, it must be protected in a manner commensurate with the associated risk. ” – Recognition that there is not a simple and interoperable solution to encrypting e-mail containing PHI 24 Copyright © 2003, Tom Walsh

Tom Walsh, CISSP twalshconsulting@aol. com 913 -696 -1573 25 Copyright © 2003, Tom Walsh