Game Theory Primer Prisoners dilemma Dominated strategies Payoff

































- Slides: 60

Game Theory Primer Prisoner’s dilemma • Dominated strategies • Payoff Matrix • Nash equilibrium Coordination game

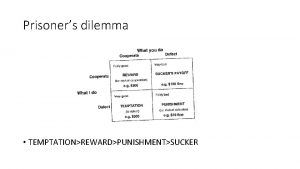
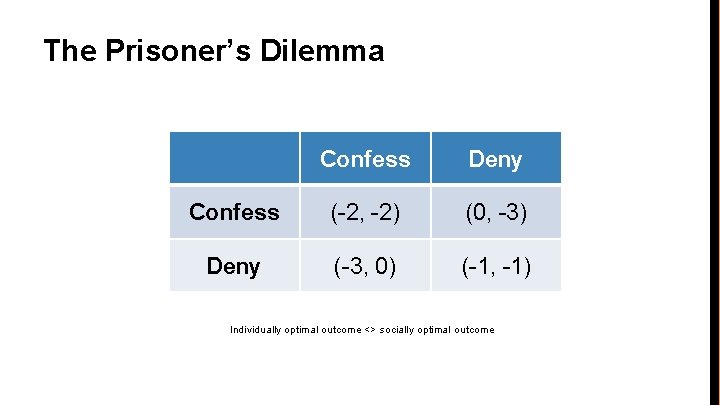
The Prisoner’s Dilemma • • Two accomplices interrogated separately The prosecutors – – • • • have enough evidence to sentence each one 1 year do not have enough evidence to sentence 2 years unless at least one suspect confesses If both confess, each sentenced 2 years If neither confesses, each sentenced 1 year If only one confesses, the confessor is immediately released, and the denier sentenced 3 years No further interaction between the two accomplices after verdict How should each criminal do?

The Prisoner’s Dilemma Confess Deny Confess (-2, -2) (0, -3) Deny (-3, 0) (-1, -1) Individually optimal outcome <> socially optimal outcome

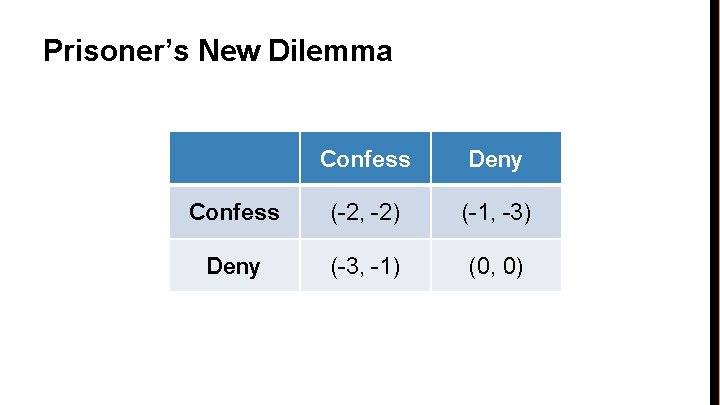
Prisoner’s New Dilemma Confess Deny Confess (-2, -2) (-1, -3) Deny (-3, -1) (0, 0)

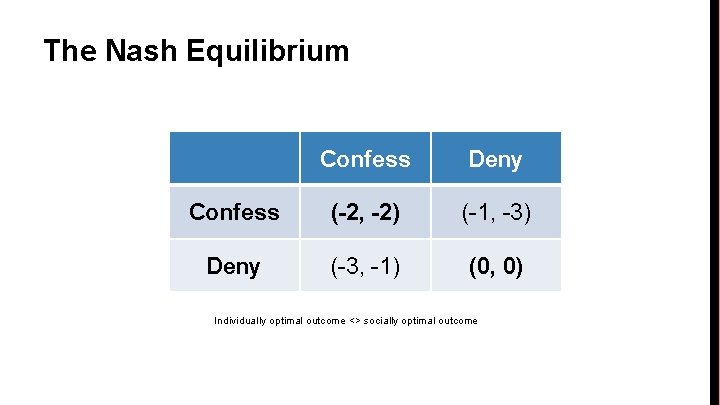
The Nash Equilibrium Confess Deny Confess (-2, -2) (-1, -3) Deny (-3, -1) (0, 0) Individually optimal outcome <> socially optimal outcome

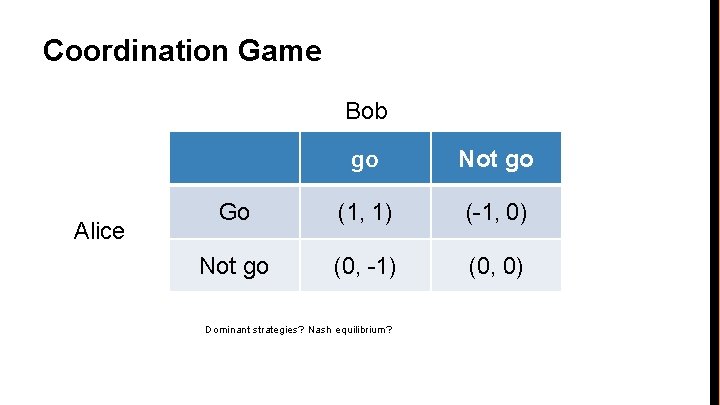
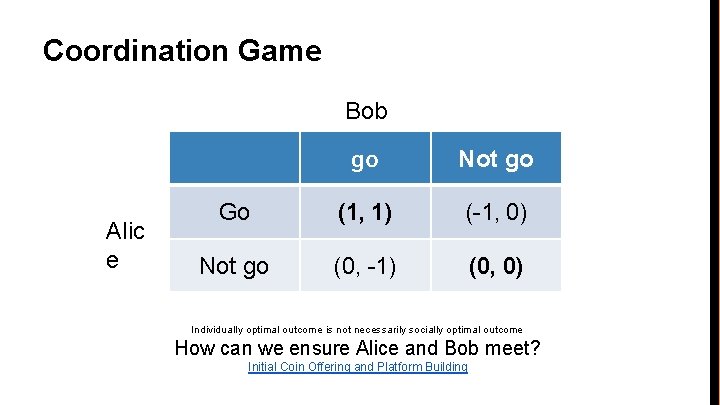
Coordination Game • • Alice and Bob wish to see each other at a party – If Bob goes, Alice would like to go too – If Bob does not go, Alice would not go either Same for Bob – If Alice goes, Bob would like to go too – If Alice does not go, Bob would not go either They don’t have each other’s contact info Should Alice and Bob go to the party or not?

Coordination Game Bob Alice go Not go Go (1, 1) (-1, 0) Not go (0, -1) (0, 0) Dominant strategies? Nash equilibrium?

Coordination Game Bob Alic e go Not go Go (1, 1) (-1, 0) Not go (0, -1) (0, 0) Individually optimal outcome is not necessarily socially optimal outcome How can we ensure Alice and Bob meet? Initial Coin Offering and Platform Building

Game tree

A Nash equilibrium? https: //www. youtube. com/watch? v=LJS 7 Igvk 6 ZM

Part 2 How Bitcoin Achieves Decentralization

Lecture 2. 1: Centralization vs. decentralization

Centralization vs. decentralization Competing paradigms that underlie many digital technologies

Decentralization is not all-or-nothing E-mail: decentralized protocol, but dominated by centralized webmail services Equifax?

Aspects of decentralization in Bitcoin 1. 2. 3. 4. 5. Who Who How maintains the ledger? has authority over which transactions are valid? creates new bitcoins? determines how the rules of the system change? do bitcoins acquire exchange value? Beyond the protocol: exchanges, wallet software, service providers. . .

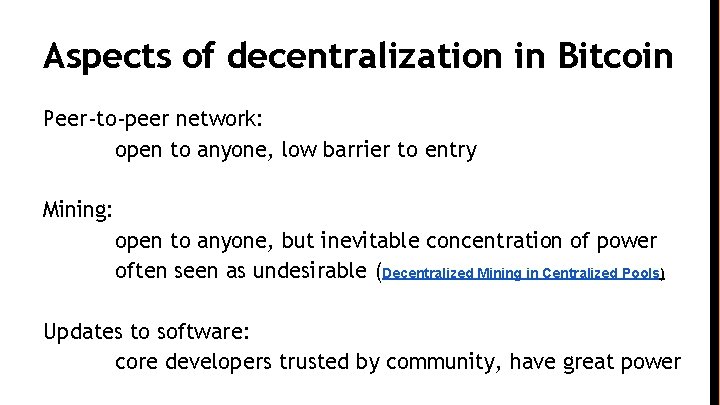
Aspects of decentralization in Bitcoin Peer-to-peer network: open to anyone, low barrier to entry Mining: open to anyone, but inevitable concentration of power often seen as undesirable (Decentralized Mining in Centralized Pools) Updates to software: core developers trusted by community, have great power

Lecture 2. 2: Distributed consensus

Bitcoin’s key challenge Key technical challenge of decentralized e-cash: distributed consensus or: how to decentralize Scrooge. Coin (remove trust of Scrooge’s reputation)

Why consensus protocols? Traditional motivation: reliability in distributed systems Distributed key-value store enables various applications: DNS, public key directory, stock trades … Good targets for Altcoins!

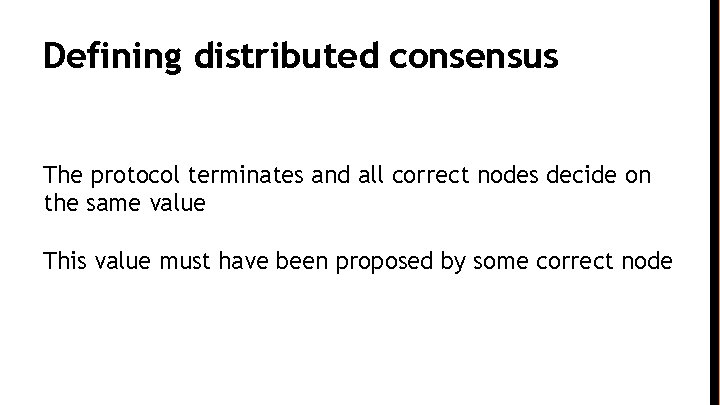
Defining distributed consensus The protocol terminates and all correct nodes decide on the same value This value must have been proposed by some correct node

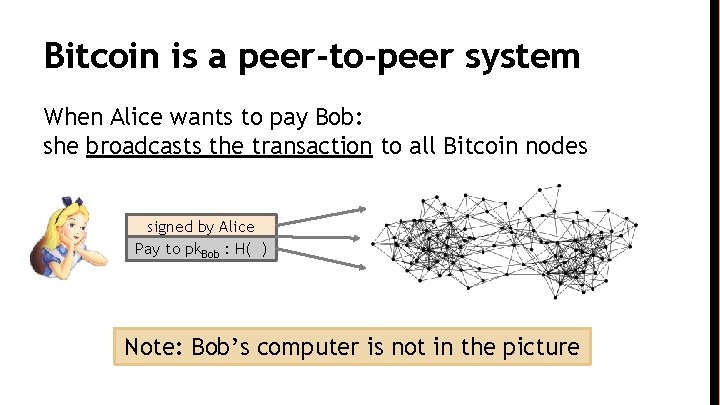
Bitcoin is a peer-to-peer system When Alice wants to pay Bob: she broadcasts the transaction to all Bitcoin nodes signed by Alice Pay to pk. Bob : H( ) Note: Bob’s computer is not in the picture

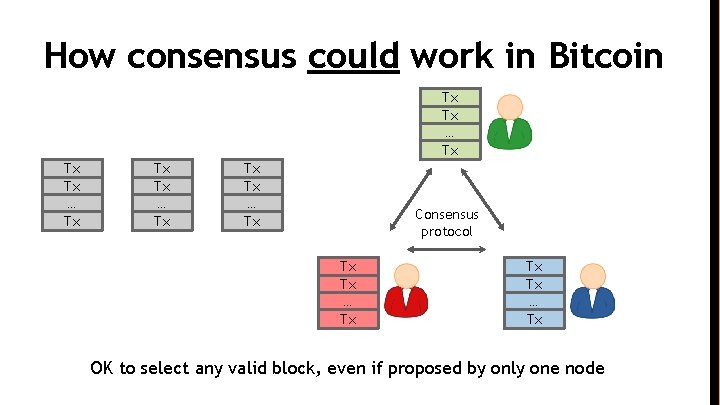
How consensus could work in Bitcoin At any given time: ● All nodes have a sequence of blocks of transactions they’ve reached consensus on ● Each node has a set of outstanding transactions it’s heard about

How consensus could work in Bitcoin Tx Tx … Tx Consensus protocol Tx Tx … Tx OK to select any valid block, even if proposed by only one node

Why consensus is hard Nodes may crash Nodes may be malicious Network is imperfect • Not all pairs of nodes connected • Faults in network • Latency No notion of global time

Many impossibility results • Byzantine generals problem • Fischer-Lynch-Paterson (deterministic nodes): consensus impossible with a single faulty node

Some well-known protocols Example: Paxos Never produces inconsistent result, but can (rarely) get stuck

Understanding impossibility results These results say more about the model than about the problem The models were developed to study systems like distributed databases

Bitcoin consensus: theory & practice Bitcoin consensus works better in practice than in theory Theory is still catching up (e. g. The blockchain folk theorem) BUT theory is important, can help predict unforeseen attacks

Some things Bitcoin does differently Introduces incentives • Possible only because it’s a currency! Embraces randomness • Does away with the notion of a specific end-point • Consensus happens over long time scales — about 1 hour

Lecture 2. 3: Consensus without identity: the block chain

Why identity? Pragmatic: some protocols need node IDs Security: assume less than 50% malicious

Why don’t Bitcoin nodes have identities? Identity is hard in a P 2 P system — Sybil attack Pseudonymity is a goal of Bitcoin

Weaker assumption: select random node Analogy: lottery or raffle When tracking & verifying identities is hard, we give people tokens, tickets, etc. Now we can pick a random ID & select that node

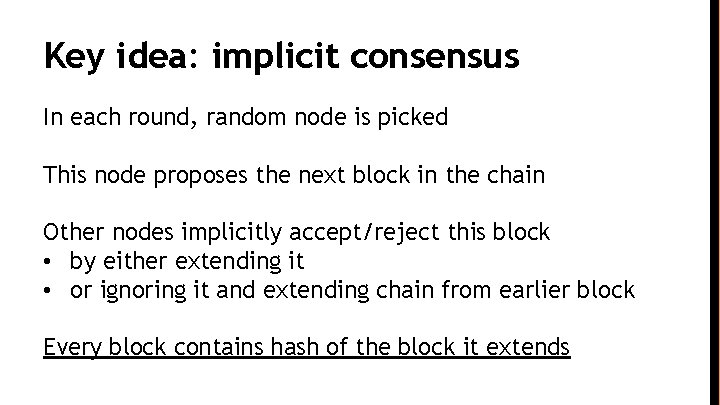
Key idea: implicit consensus In each round, random node is picked This node proposes the next block in the chain Other nodes implicitly accept/reject this block • by either extending it • or ignoring it and extending chain from earlier block Every block contains hash of the block it extends

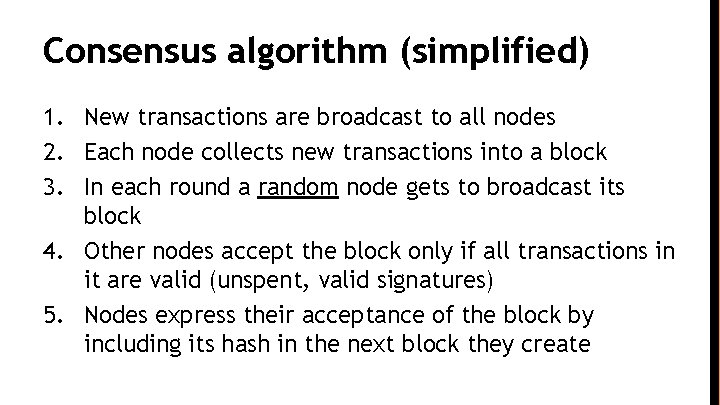
Consensus algorithm (simplified) 1. New transactions are broadcast to all nodes 2. Each node collects new transactions into a block 3. In each round a random node gets to broadcast its block 4. Other nodes accept the block only if all transactions in it are valid (unspent, valid signatures) 5. Nodes express their acceptance of the block by including its hash in the next block they create

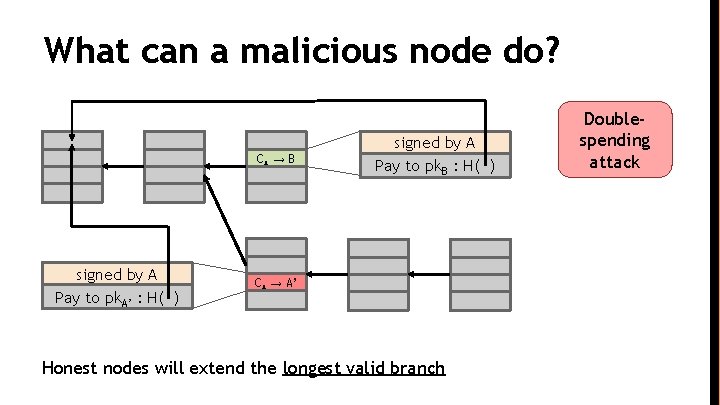
What can a malicious node do? CA → B signed by A Pay to pk. A’ : H( ) signed by A Pay to pk. B : H( ) CA → A’ Honest nodes will extend the longest valid branch Doublespending attack

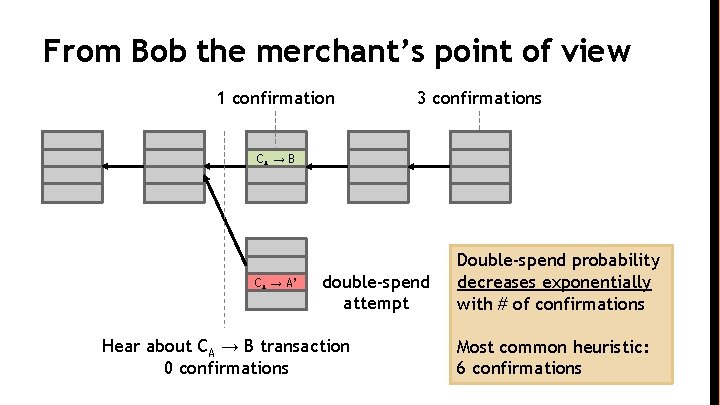
From Bob the merchant’s point of view 1 confirmation 3 confirmations CA → B CA → A’ double-spend attempt Hear about CA → B transaction 0 confirmations Double-spend probability decreases exponentially with # of confirmations Most common heuristic: 6 confirmations

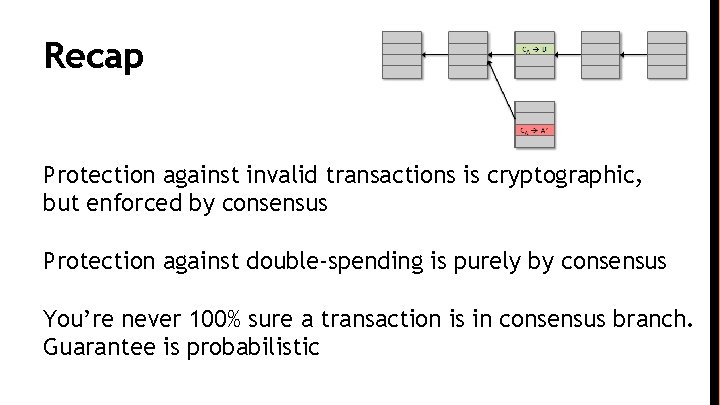
Recap Protection against invalid transactions is cryptographic, but enforced by consensus Protection against double-spending is purely by consensus You’re never 100% sure a transaction is in consensus branch. Guarantee is probabilistic

Lecture 2. 4: Incentives and proof of work

Assumption of honesty is problematic Can we give nodes incentives for behaving honestly? Can we reward nodes that created these blocks? Can we penalize the node that created this block? Everything so far is just a distributed consensus protocol But now we utilize the fact that the currency has value

Incentive 1: block reward Creator of block gets to • include special coin-creation transaction in the block • choose recipient address of this transaction Value is fixed: currently 12. 5 BTC, halves every 4 years Block creator gets to “collect” the reward only if the block ends up on long-term consensus branch!

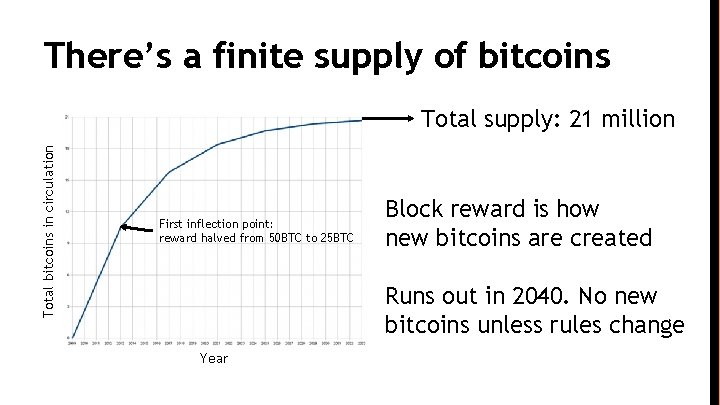
There’s a finite supply of bitcoins Total bitcoins in circulation Total supply: 21 million First inflection point: reward halved from 50 BTC to 25 BTC Block reward is how new bitcoins are created Runs out in 2040. No new bitcoins unless rules change Year

Incentive 2: transaction fees Creator of transaction can choose to make output value less than input value Remainder is a transaction fee and goes to block creator Purely voluntary, like a tip

Remaining problems 1. How to pick a random node? 1. How to avoid a free-for-all due to rewards? 1. How to prevent Sybil attacks?

Proof of work To approximate selecting a random node: select nodes in proportion to a resource that no one can monopolize (we hope) • In proportion to computing power: proof-of-work • In proportion to ownership: proof-of-stake

Equivalent views of proof of work 1. Select nodes in proportion to computing power 1. Let nodes compete for right to create block 1. Make it moderately hard to create new identities

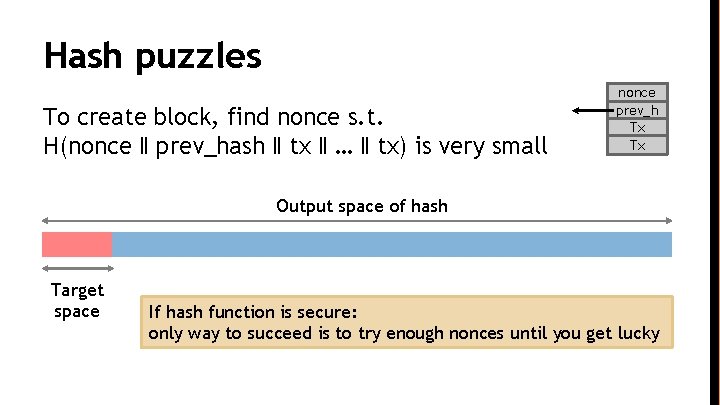
Hash puzzles To create block, find nonce s. t. H(nonce ‖ prev_hash ‖ tx ‖ … ‖ tx) is very small nonce prev_h Tx Tx Output space of hash Target space If hash function is secure: only way to succeed is to try enough nonces until you get lucky

Po. W property 1: difficult to compute As of Aug 2014: about 1020 hashes/block Only some nodes bother to compete — miners

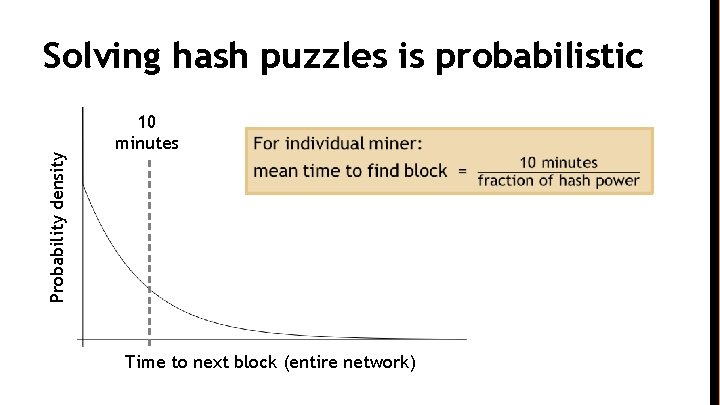
Po. W property 2: parameterizable cost Nodes automatically re-calculate the target every two weeks Goal: average time between blocks = 10 minutes Prob (Alice wins next block) = fraction of global hash power she controls

Key security assumption Attacks infeasible if majority of miners weighted by hash power follow the protocol

Probability density Solving hash puzzles is probabilistic 10 minutes Time to next block (entire network)

Po. W property 3: trivial to verify Nonce must be published as part of block Other miners simply verify that H(nonce ‖ prev_hash ‖ tx ‖ … ‖ tx) < target

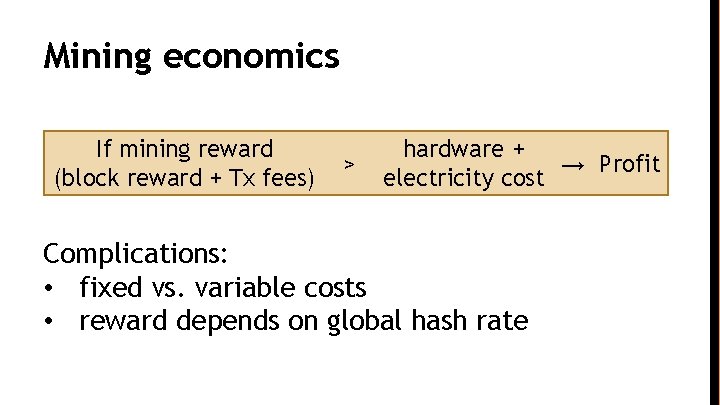
Mining economics If mining reward (block reward + Tx fees) > hardware + → Profit electricity cost Complications: • fixed vs. variable costs • reward depends on global hash rate

Lecture 2. 5: Putting it all together

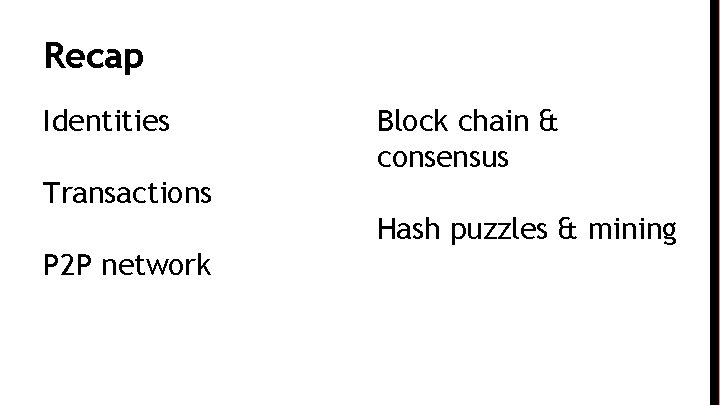
Recap Identities Block chain & consensus Transactions Hash puzzles & mining P 2 P network

Bitcoin has three types of consensus • Value • State • Rules

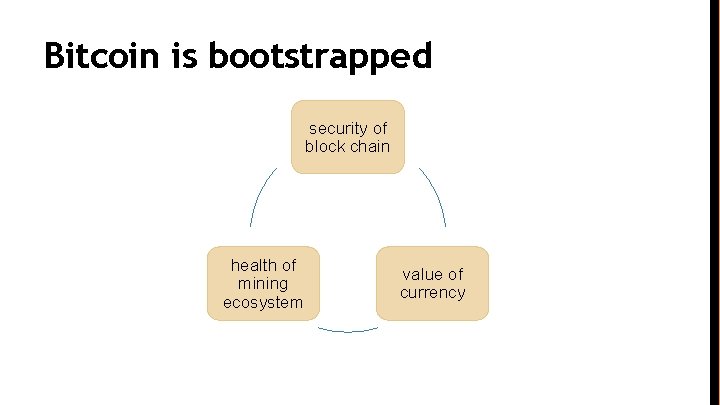
Bitcoin is bootstrapped security of block chain health of mining ecosystem value of currency

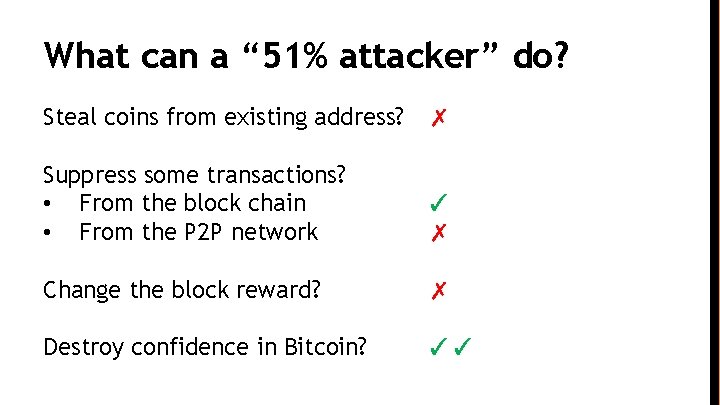
What can a “ 51% attacker” do? Steal coins from existing address? ✗ Suppress some transactions? • From the block chain • From the P 2 P network ✓ ✗ Change the block reward? ✗ Destroy confidence in Bitcoin? ✓✓

Remaining questions How do we get from consensus to currency? What else can we do with consensus?

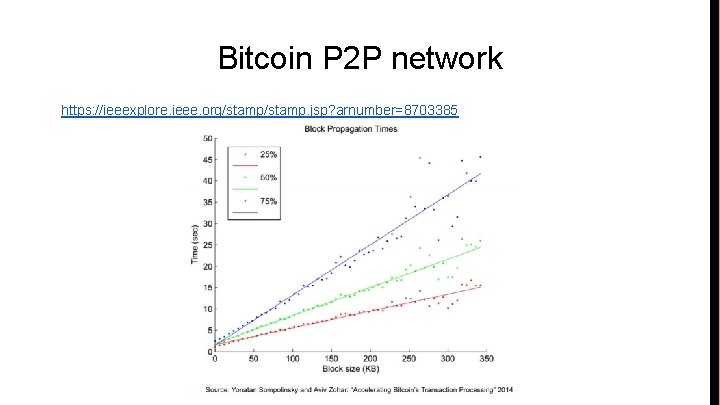
Bitcoin P 2 P network https: //ieeexplore. ieee. org/stamp. jsp? arnumber=8703385
 Prisoners dilemma
Prisoners dilemma Prisoners dilemma
Prisoners dilemma Prisoner's dilemma
Prisoner's dilemma Payoff tables
Payoff tables Prisoners dillemma
Prisoners dillemma When prisoners come home
When prisoners come home After they arrived the prisoners are supposed to shower
After they arrived the prisoners are supposed to shower Action for prisoners families
Action for prisoners families Adx florence cell
Adx florence cell The pirate game
The pirate game Game lab game theory
Game lab game theory Liar game game theory
Liar game game theory Liar game game theory
Liar game game theory Euthyphro dilemma summary
Euthyphro dilemma summary Napoleon's relatives ruled
Napoleon's relatives ruled Game theory in strategic management
Game theory in strategic management Different approaches and methods
Different approaches and methods Game theory pure strategy
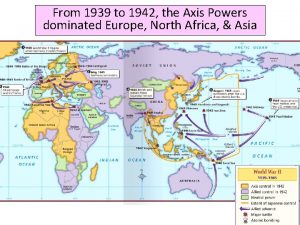
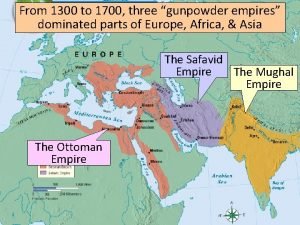
Game theory pure strategy Who dominated europe, north africa and asia from 1939-1942?
Who dominated europe, north africa and asia from 1939-1942? Biome sb
Biome sb 3 gunpowder empires
3 gunpowder empires Marine ecosystem dominated by marsh grasses
Marine ecosystem dominated by marsh grasses River dominated delta
River dominated delta A market dominated by a single seller
A market dominated by a single seller Divestment in consumer decision process
Divestment in consumer decision process Chapter 7 market structures
Chapter 7 market structures Greek civilization map
Greek civilization map Napoleon bonaparte dominated
Napoleon bonaparte dominated Revenue dominated cash flow
Revenue dominated cash flow Game theory and graph theory
Game theory and graph theory Contribution payoff table
Contribution payoff table Purpose process payoff
Purpose process payoff Laplace criterion example
Laplace criterion example Payoff matrix oligopoly
Payoff matrix oligopoly Bear spread using puts
Bear spread using puts Payoff matrix economics
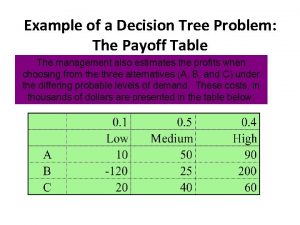
Payoff matrix economics Payoff table example
Payoff table example Asian option payoff
Asian option payoff Line sensitivity
Line sensitivity Payoff function
Payoff function Swaption payoff diagram
Swaption payoff diagram Fra product
Fra product Payoff table excel
Payoff table excel Payoff diagram
Payoff diagram Farming game rules
Farming game rules A formal approach to game design and game research
A formal approach to game design and game research Strategies for theory construction in nursing
Strategies for theory construction in nursing Carol gilligan's theory of moral development
Carol gilligan's theory of moral development Vangin dilemma
Vangin dilemma Stag hunt vs prisoner's dilemma
Stag hunt vs prisoner's dilemma Sociological imagination abortion
Sociological imagination abortion Outcome of prisoner's dilemma
Outcome of prisoner's dilemma Dilemma spill
Dilemma spill Pinpointing the enemy propaganda
Pinpointing the enemy propaganda Organisation
Organisation Global-local dilemma examples
Global-local dilemma examples Spt regel
Spt regel Dilemma del prigioniero spiegazione
Dilemma del prigioniero spiegazione Dialectici
Dialectici Game theory cartoon
Game theory cartoon False dilemma in the crucible
False dilemma in the crucible