Deployment Solution 7 1 Overview Neil Peckham Sr








- Slides: 44

Deployment Solution 7. 1 Overview Neil Peckham – Sr. Principle Systems Engineer Endpoint Management & Mobility / New England

Altiris Deployment Solution Deployment A solution specifically designed to solve today’s computer provisioning challenges Symantec Confidential – Do Not Distribute 2

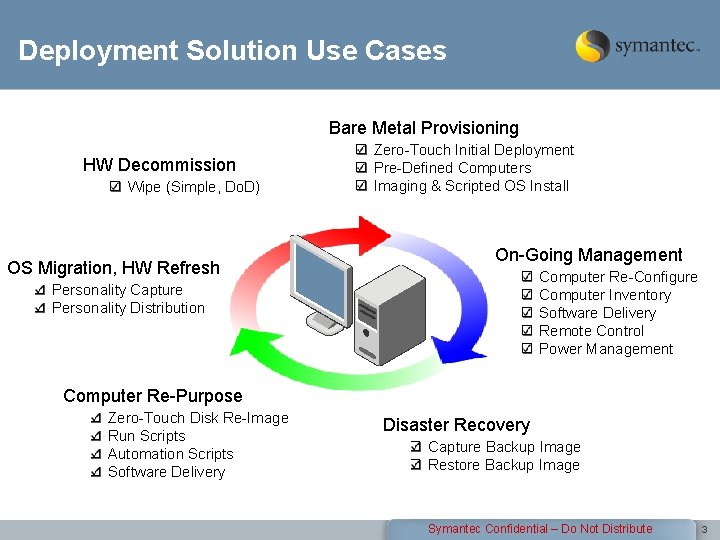
Deployment Solution Use Cases Bare Metal Provisioning HW Decommission Wipe (Simple, Do. D) OS Migration, HW Refresh Zero-Touch Initial Deployment Pre-Defined Computers Imaging & Scripted OS Install On-Going Management Computer Re-Configure Computer Inventory Software Delivery Remote Control Power Management Personality Capture Personality Distribution Computer Re-Purpose Zero-Touch Disk Re-Image Run Scripts Automation Scripts Software Delivery Disaster Recovery Capture Backup Image Restore Backup Image Symantec Confidential – Do Not Distribute 3

DS 7. 1 Answers Long-Standing Requests 1. DS Servers need to share data and keep it synchronized Computers, Jobs, Scripts, Security Settings, System Configurations, Drivers, Images, Software Packages, Pre-OSes, Personality Templates, Custom Tokens 2. Enhance management of multiple PXE server environments 3. Better security roles, more granular, global scoping 4. Provide job status and reports; what machines have pending jobs, how long have they been waiting, which jobs succeeded/failed, etc. 5. Smarter jobs with better branch logic, more reusability 6. Dynamic groups, filters 7. Make P 2 V and V 2 P transformations more fluid, provide advanced deployment capabilities of virtual environments 8. Better remote management, better inventory, real patch, better SW management, out-of-band management, best of breed back-up and restore Symantec Confidential – Do Not Distribute 4

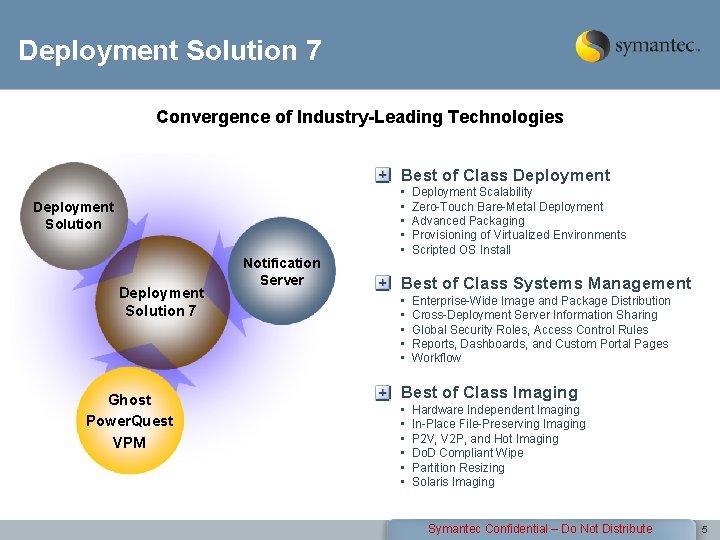
Deployment Solution 7 Convergence of Industry-Leading Technologies Best of Class Deployment Solution 7 Ghost Power. Quest VPM Notification Server • • • Deployment Scalability Zero-Touch Bare-Metal Deployment Advanced Packaging Provisioning of Virtualized Environments Scripted OS Install Best of Class Systems Management • • • Enterprise-Wide Image and Package Distribution Cross-Deployment Server Information Sharing Global Security Roles, Access Control Rules Reports, Dashboards, and Custom Portal Pages Workflow Best of Class Imaging • • • Hardware Independent Imaging In-Place File-Preserving Imaging P 2 V, V 2 P, and Hot Imaging Do. D Compliant Wipe Partition Resizing Solaris Imaging Symantec Confidential – Do Not Distribute 5

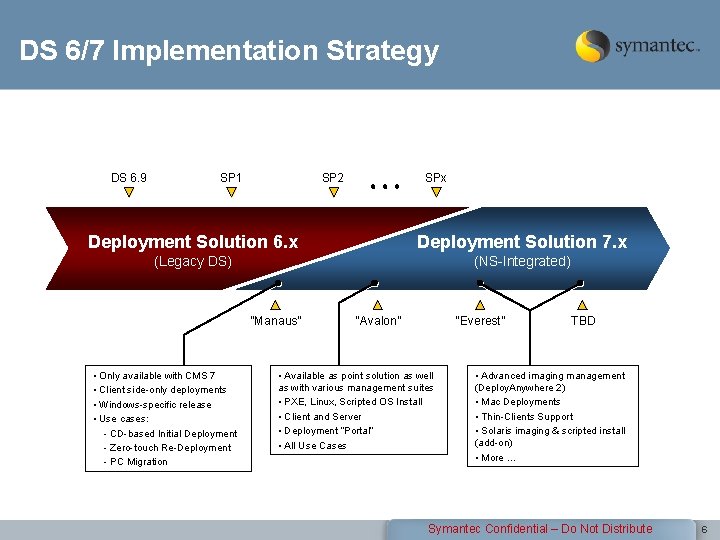
DS 6/7 Implementation Strategy DS 6. 9 SP 1 SP 2 SPx Deployment Solution 6. x Deployment Solution 7. x (Legacy DS) (NS-Integrated) “Manaus” • Only available with CMS 7 • Client side-only deployments • Windows-specific release • Use cases: - CD-based Initial Deployment - Zero-touch Re-Deployment - PC Migration “Avalon” “Everest” • Available as point solution as well as with various management suites • PXE, Linux, Scripted OS Install • Client and Server • Deployment “Portal” • All Use Cases TBD • Advanced imaging management (Deploy. Anywhere 2) • Mac Deployments • Thin-Clients Support • Solaris imaging & scripted install (add-on) • More … Symantec Confidential – Do Not Distribute 6

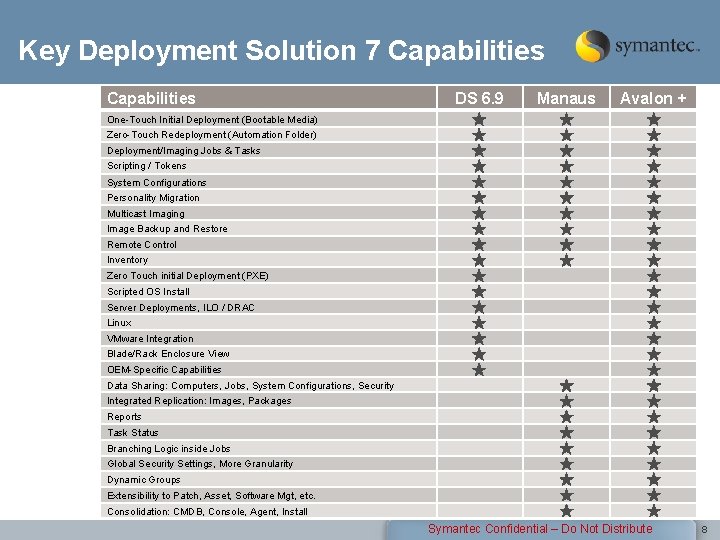
Key Deployment Solution 7 Capabilities DS 6. 9 Manaus Avalon + One-Touch Initial Deployment (Bootable Media) Zero-Touch Redeployment (Automation Folder) Deployment/Imaging Jobs & Tasks Scripting / Tokens System Configurations Personality Migration Multicast Imaging Image Backup and Restore Remote Control Inventory Zero Touch initial Deployment (PXE) Scripted OS Install Server Deployments, ILO / DRAC Linux VMware Integration Blade/Rack Enclosure View OEM-Specific Capabilities Data Sharing: Computers, Jobs, System Configurations, Security Integrated Replication: Images, Packages Reports Task Status Branching Logic inside Jobs Global Security Settings, More Granularity Dynamic Groups Extensibility to Patch, Asset, Software Mgt, etc. Consolidation: CMDB, Console, Agent, Install Symantec Confidential – Do Not Distribute 8

New Ghost Value Symantec Confidential – Do Not Distribute

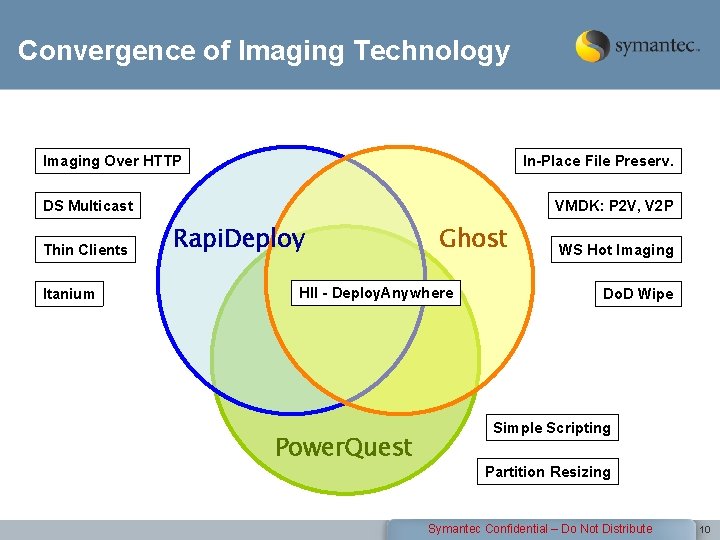
Convergence of Imaging Technology Imaging Over HTTP In-Place File Preserv. DS Multicast Thin Clients Itanium VMDK: P 2 V, V 2 P Rapi. Deploy Ghost HII - Deploy. Anywhere Power. Quest WS Hot Imaging Do. D Wipe Simple Scripting Partition Resizing Symantec Confidential – Do Not Distribute 10

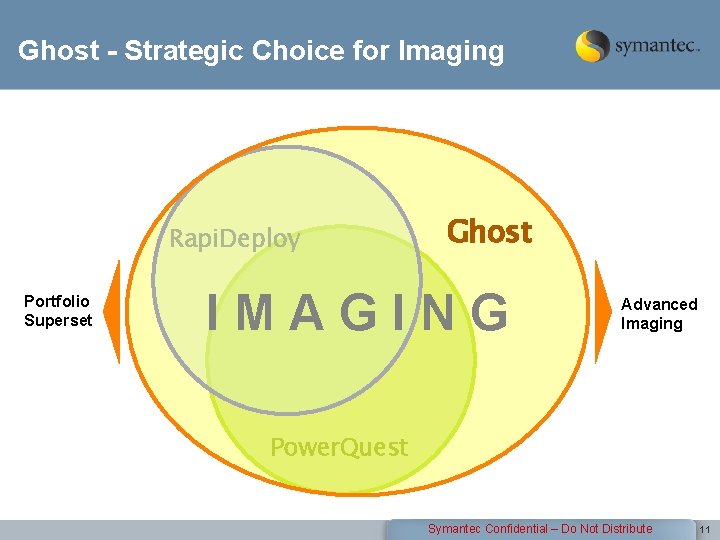
Ghost - Strategic Choice for Imaging Rapi. Deploy Portfolio Superset Ghost IMAGING Advanced Imaging Power. Quest Symantec Confidential – Do Not Distribute 11

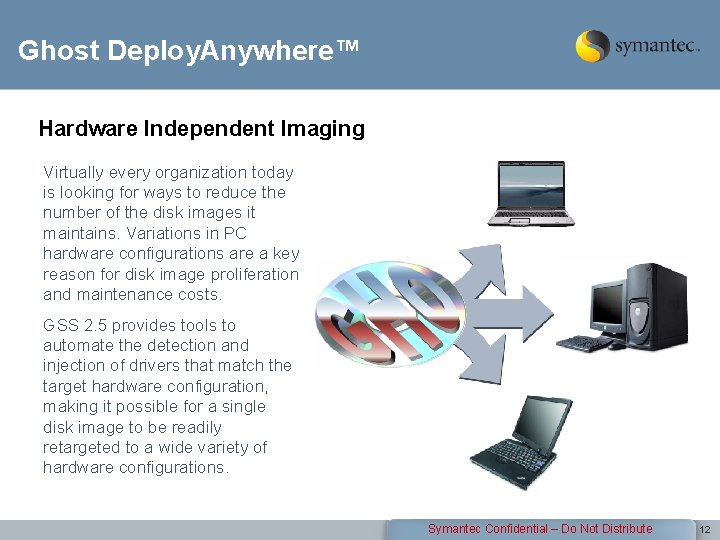
Ghost Deploy. Anywhere™ Hardware Independent Imaging Virtually every organization today is looking for ways to reduce the number of the disk images it maintains. Variations in PC hardware configurations are a key reason for disk image proliferation and maintenance costs. GSS 2. 5 provides tools to automate the detection and injection of drivers that match the target hardware configuration, making it possible for a single disk image to be readily retargeted to a wide variety of hardware configurations. Symantec Confidential – Do Not Distribute 12

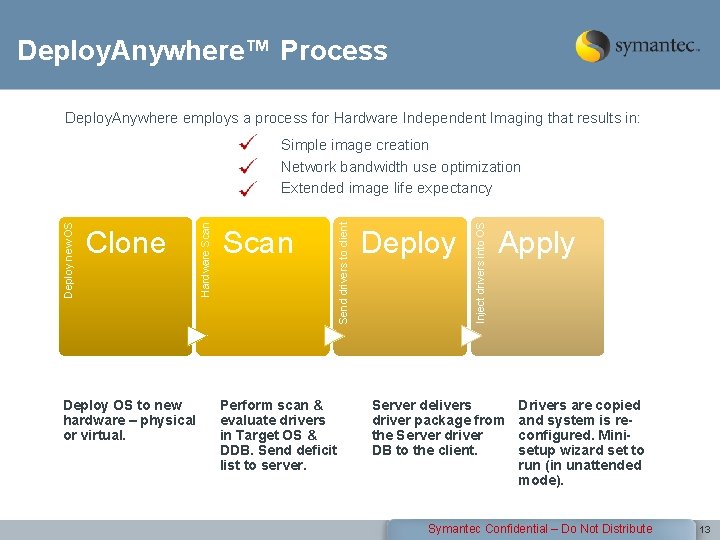
Deploy. Anywhere™ Process Deploy. Anywhere employs a process for Hardware Independent Imaging that results in: Deploy OS to new hardware – physical or virtual. Perform scan & evaluate drivers in Target OS & DDB. Send deficit list to server. Deploy Inject drivers into OS Scan Send drivers to client Clone Hardware Scan Deploy new OS Simple image creation Network bandwidth use optimization Extended image life expectancy Apply Server delivers driver package from the Server driver DB to the client. Drivers are copied and system is reconfigured. Minisetup wizard set to run (in unattended mode). Symantec Confidential – Do Not Distribute 13

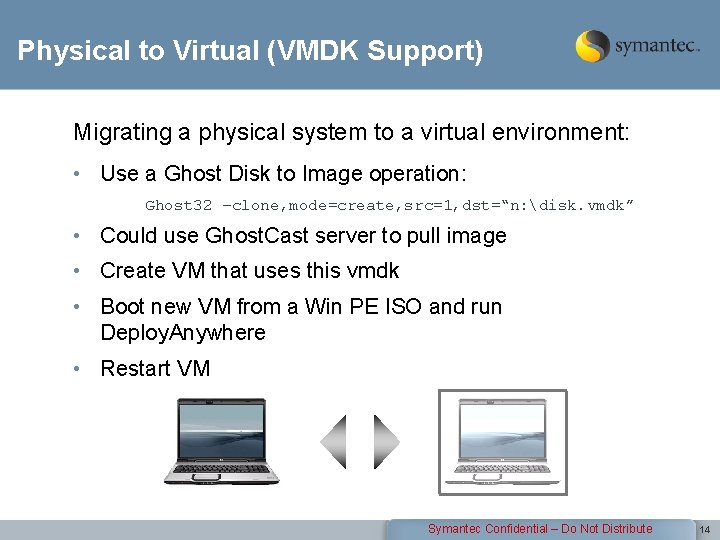
Physical to Virtual (VMDK Support) Migrating a physical system to a virtual environment: • Use a Ghost Disk to Image operation: Ghost 32 –clone, mode=create, src=1, dst=“n: disk. vmdk” • Could use Ghost. Cast server to pull image • Create VM that uses this vmdk • Boot new VM from a Win PE ISO and run Deploy. Anywhere • Restart VM Symantec Confidential – Do Not Distribute 14

In-Place File Preserving Imaging • Files or folders can be preserved when restoring an image – Use this for Client specific configuration or data files • Consider preserving data such as: – User Migration Packages – Software Install Sets – My Documents • Preserved files can be moved and renamed during the cloning operation • Major Advantages – – The image may be smaller Faster deployment Reduced network traffic Reduced central storage requirements Symantec Confidential – Do Not Distribute 15

Workstation Hot Image Creation • Uses Volume Snapshot capability of Windows • Uses Logical Volume Manager in Linux • Creates images while OS is up & running • Incompatible with Sysprep • Happens automatically if Ghost can’t get an exclusive lock on the volume being imaged. • Behavior can be changed with command line switches -forcevolumesnapshot -novolumesnapshot • Can be used on Windows or Linux Symantec Confidential – Do Not Distribute 16

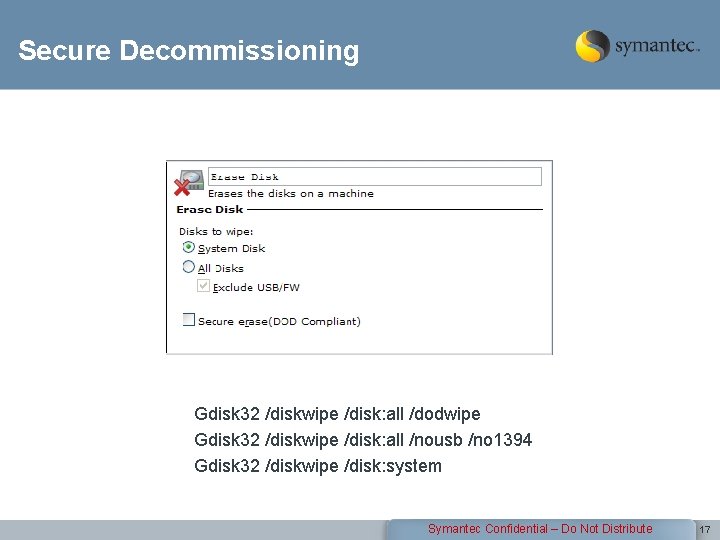
Secure Decommissioning Gdisk 32 /diskwipe /disk: all /dodwipe Gdisk 32 /diskwipe /disk: all /nousb /no 1394 Gdisk 32 /diskwipe /disk: system Symantec Confidential – Do Not Distribute 17

Deployment Solution 7. 1 Symantec Confidential – Do Not Distribute

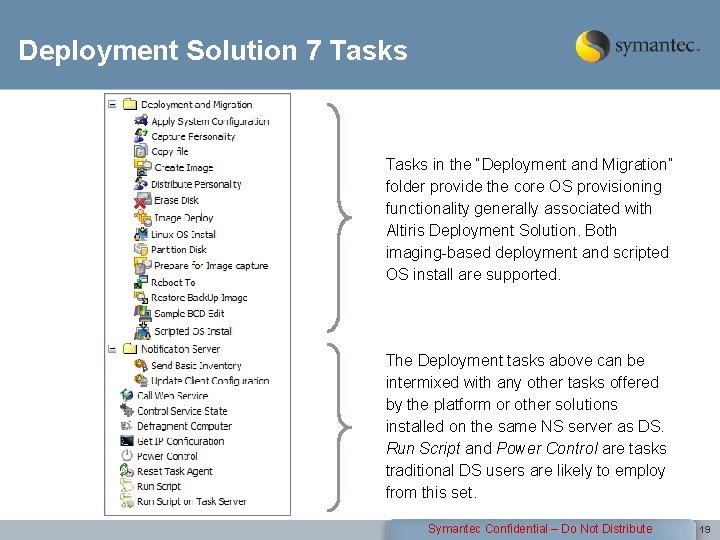
Deployment Solution 7 Tasks in the “Deployment and Migration” folder provide the core OS provisioning functionality generally associated with Altiris Deployment Solution. Both imaging-based deployment and scripted OS install are supported. The Deployment tasks above can be intermixed with any other tasks offered by the platform or other solutions installed on the same NS server as DS. Run Script and Power Control are tasks traditional DS users are likely to employ from this set. Symantec Confidential – Do Not Distribute 19

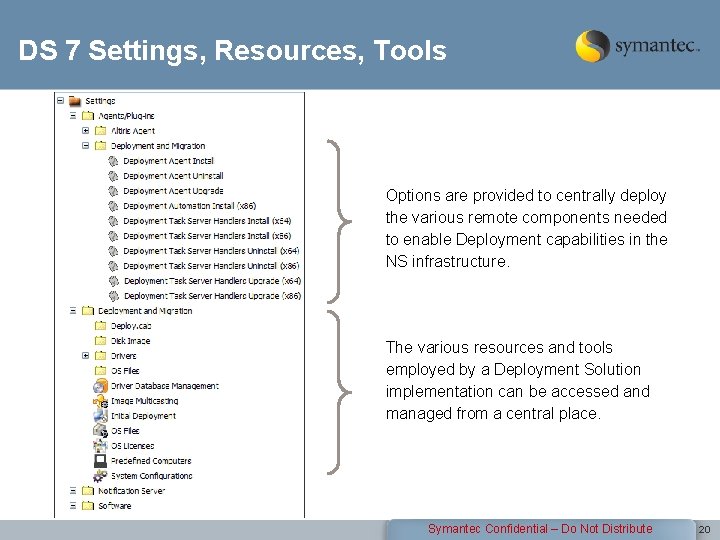
DS 7 Settings, Resources, Tools Options are provided to centrally deploy the various remote components needed to enable Deployment capabilities in the NS infrastructure. The various resources and tools employed by a Deployment Solution implementation can be accessed and managed from a central place. Symantec Confidential – Do Not Distribute 20

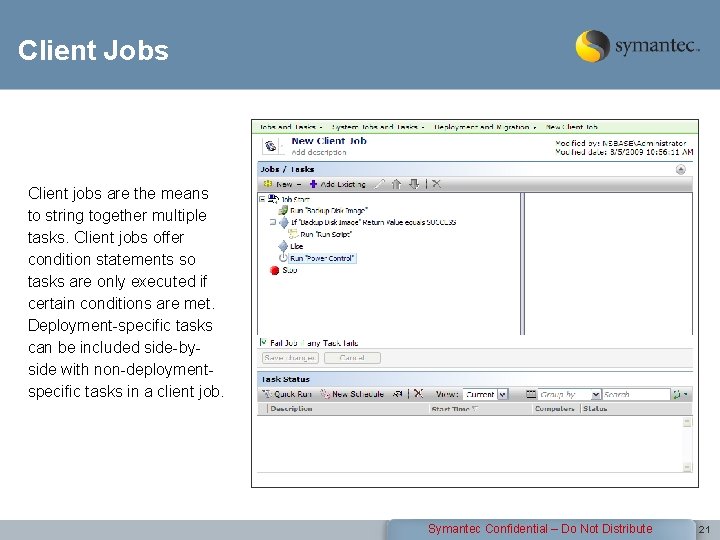
Client Jobs Client jobs are the means to string together multiple tasks. Client jobs offer condition statements so tasks are only executed if certain conditions are met. Deployment-specific tasks can be included side-byside with non-deploymentspecific tasks in a client job. Symantec Confidential – Do Not Distribute 21

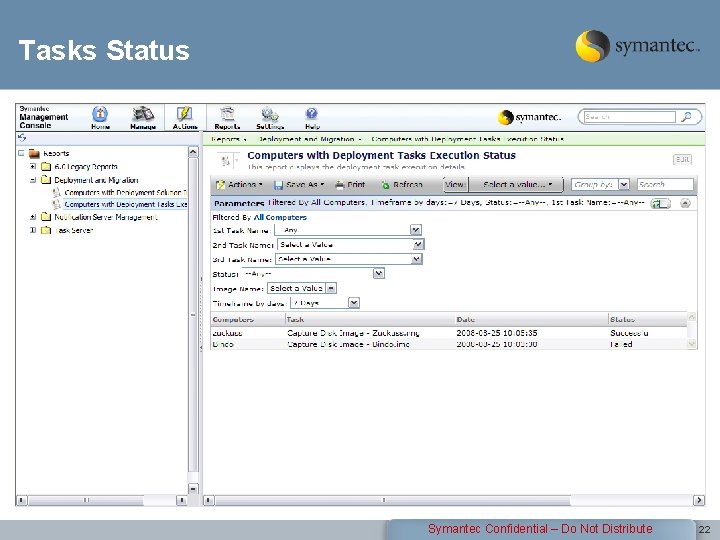
Tasks Status Symantec Confidential – Do Not Distribute 22

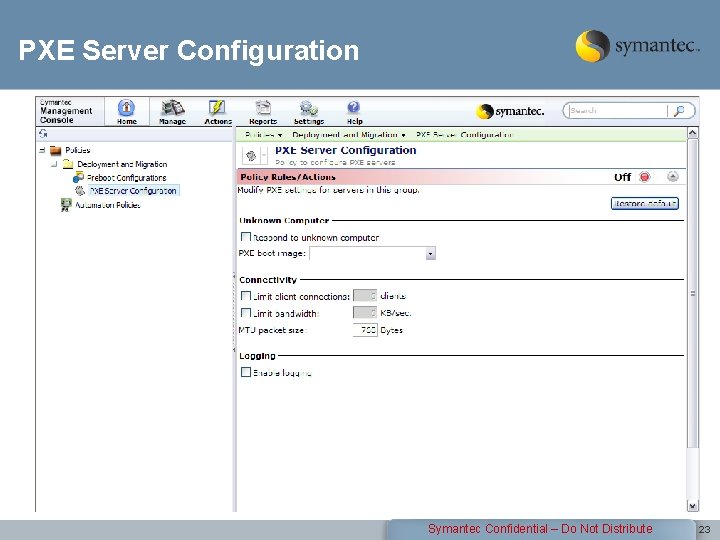
PXE Server Configuration Symantec Confidential – Do Not Distribute 23

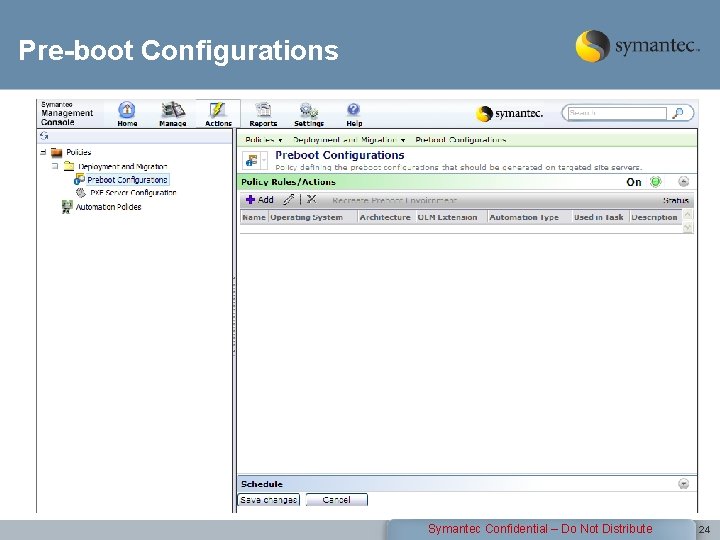
Pre-boot Configurations Symantec Confidential – Do Not Distribute 24

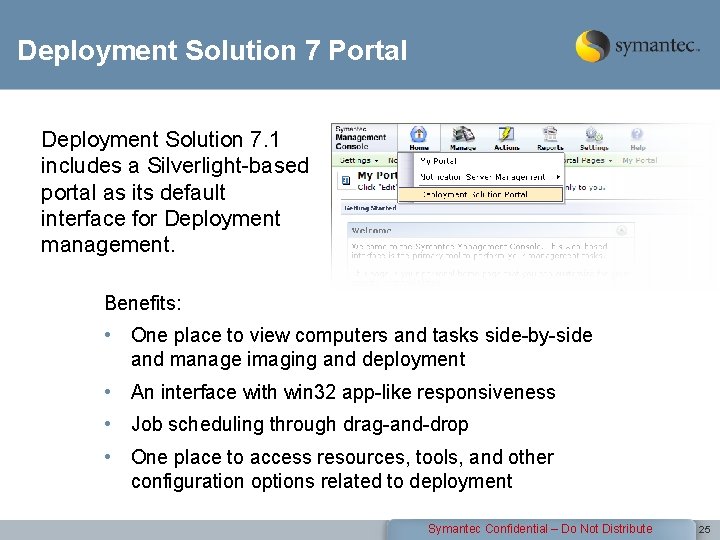
Deployment Solution 7 Portal Deployment Solution 7. 1 includes a Silverlight-based portal as its default interface for Deployment management. Benefits: • One place to view computers and tasks side-by-side and manage imaging and deployment • An interface with win 32 app-like responsiveness • Job scheduling through drag-and-drop • One place to access resources, tools, and other configuration options related to deployment Symantec Confidential – Do Not Distribute 25

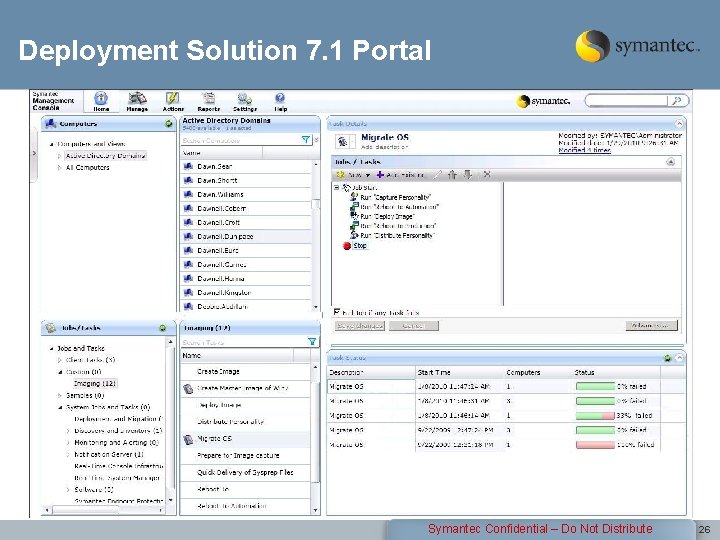
Deployment Solution 7. 1 Portal Symantec Confidential – Do Not Distribute 26

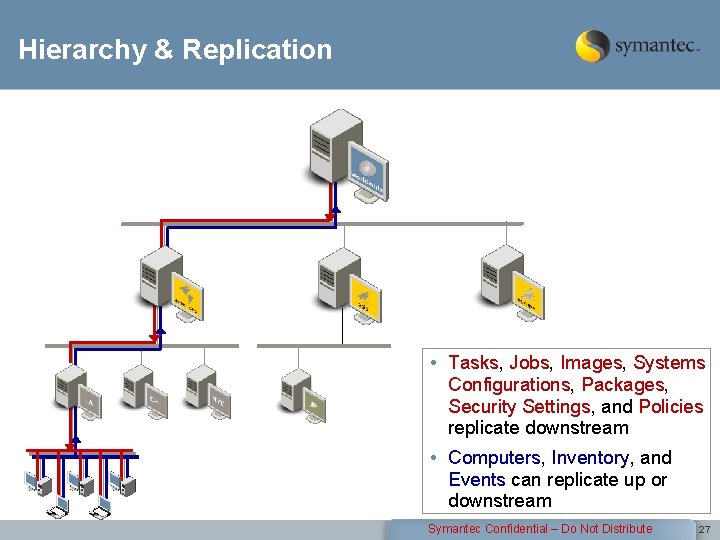
Hierarchy & Replication • Tasks, Jobs, Images, Systems Configurations, Packages, Security Settings, and Policies replicate downstream • Computers, Inventory, and Events can replicate up or downstream Symantec Confidential – Do Not Distribute 27

Appendix Symantec Confidential – Do Not Distribute

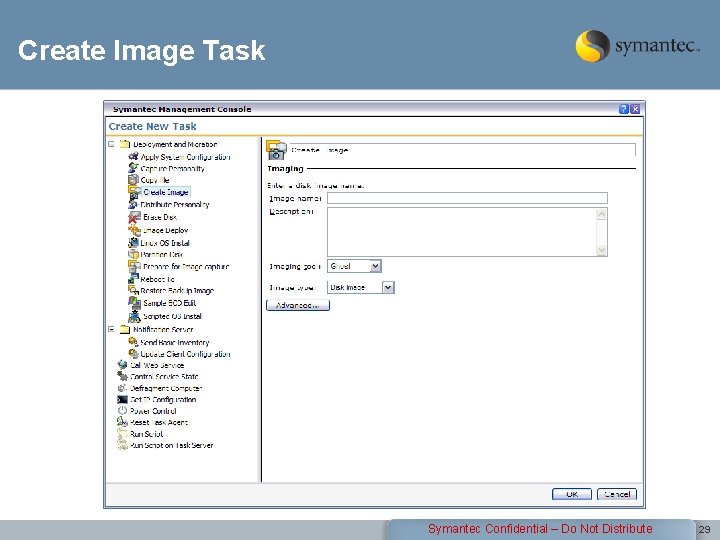
Create Image Task Symantec Confidential – Do Not Distribute 29

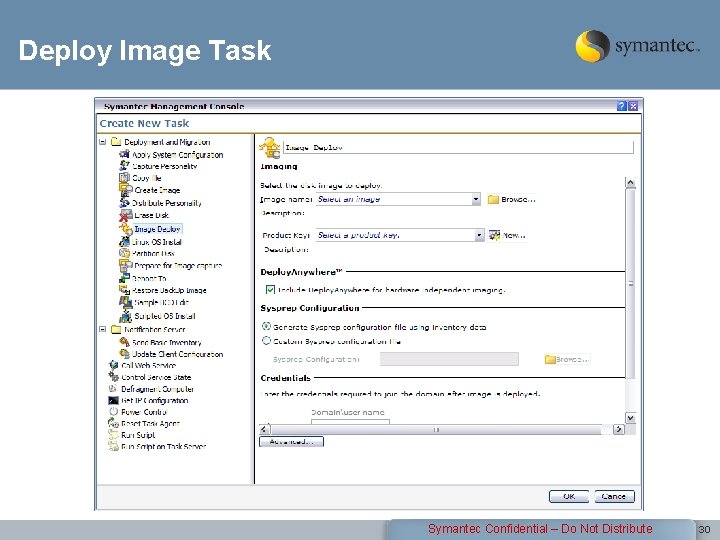
Deploy Image Task Symantec Confidential – Do Not Distribute 30

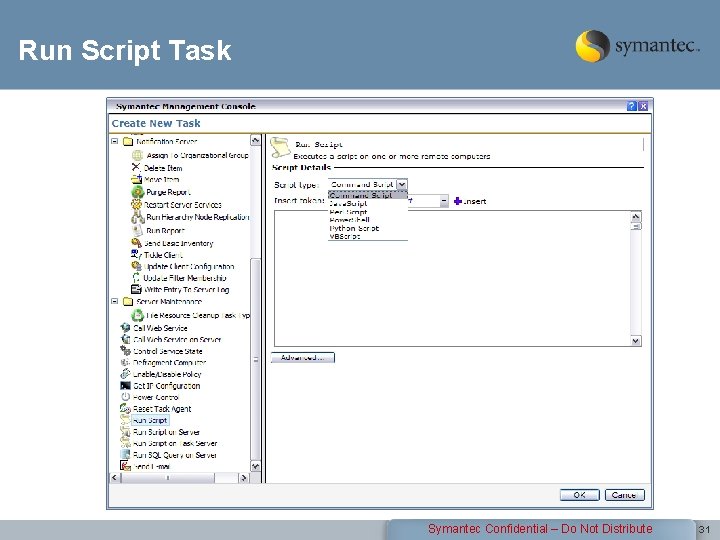
Run Script Task Symantec Confidential – Do Not Distribute 31

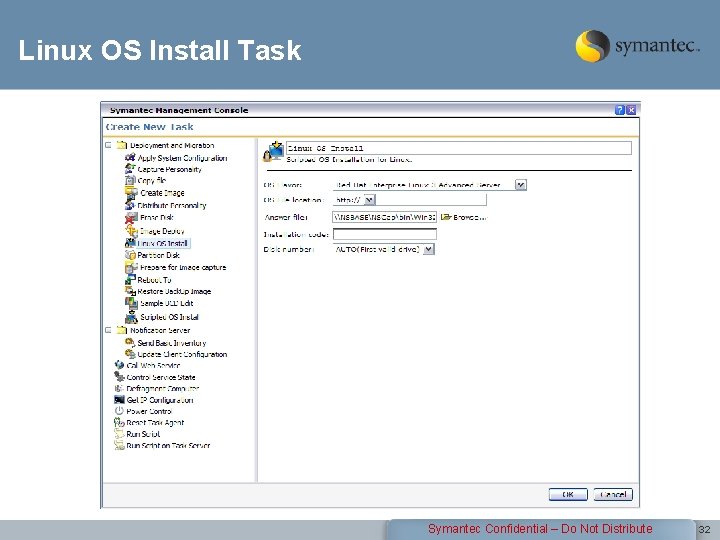
Linux OS Install Task Symantec Confidential – Do Not Distribute 32

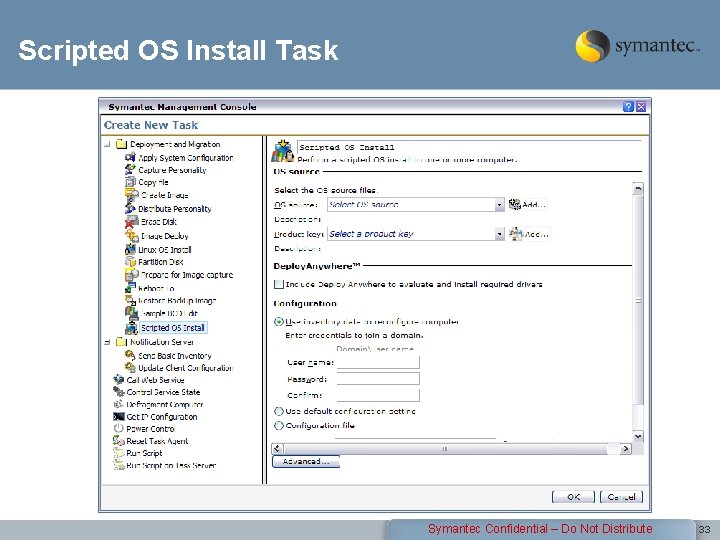
Scripted OS Install Task Symantec Confidential – Do Not Distribute 33

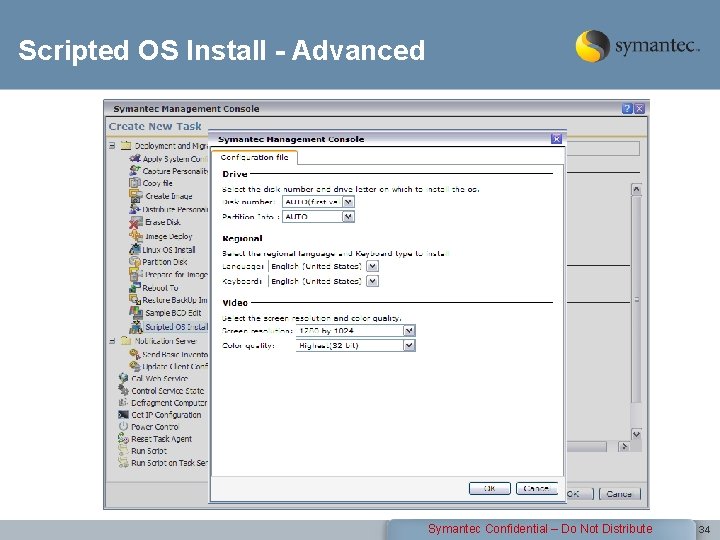
Scripted OS Install - Advanced Symantec Confidential – Do Not Distribute 34

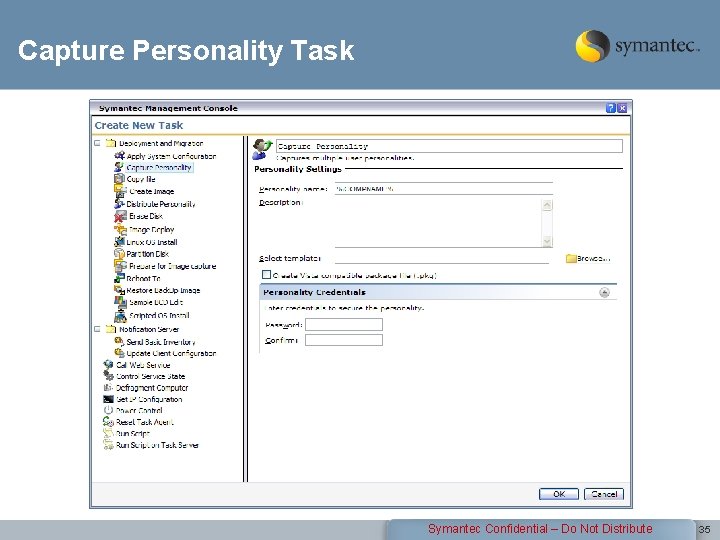
Capture Personality Task Symantec Confidential – Do Not Distribute 35

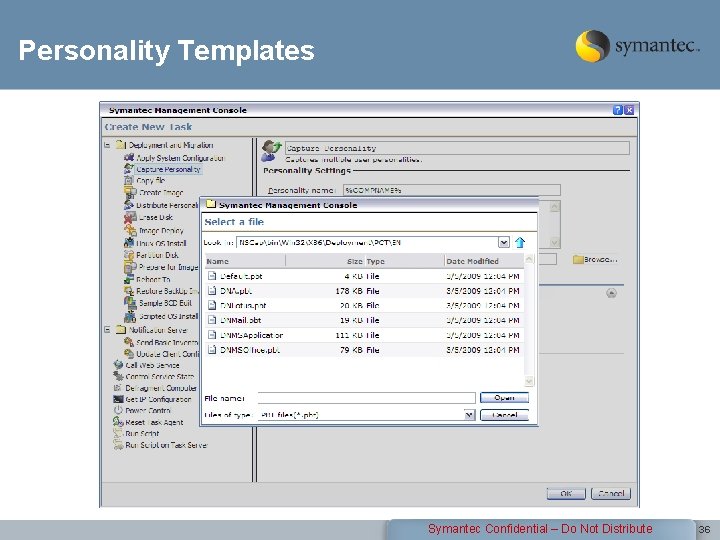
Personality Templates Symantec Confidential – Do Not Distribute 36

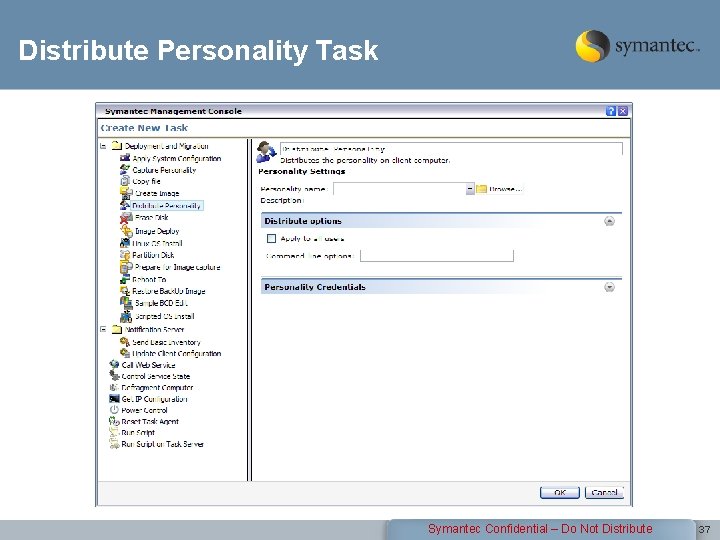
Distribute Personality Task Symantec Confidential – Do Not Distribute 37

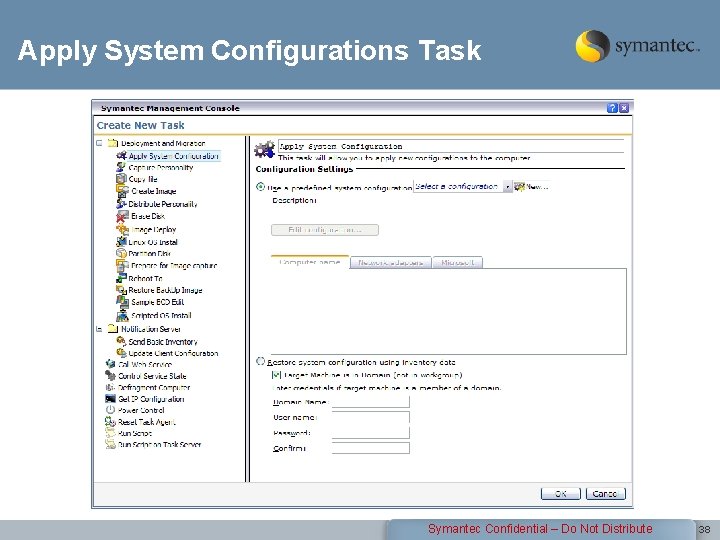
Apply System Configurations Task Symantec Confidential – Do Not Distribute 38

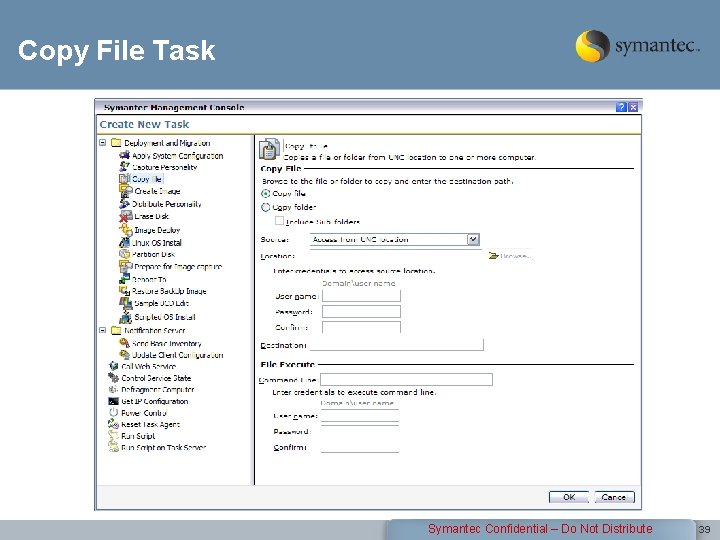
Copy File Task Symantec Confidential – Do Not Distribute 39

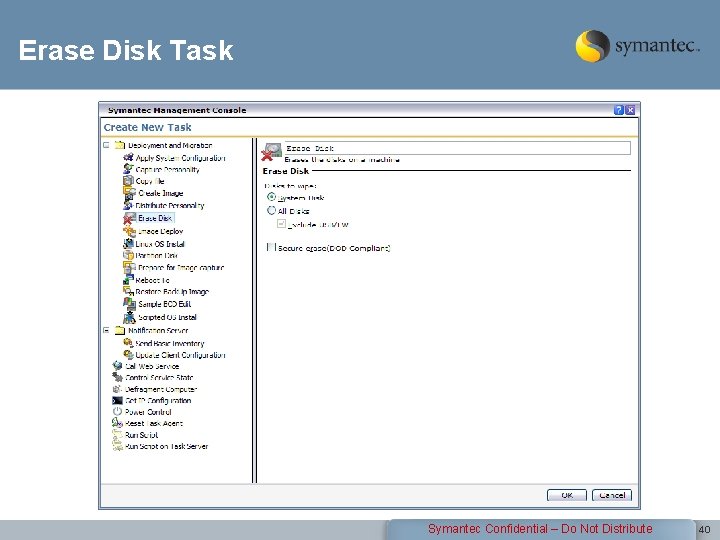
Erase Disk Task Symantec Confidential – Do Not Distribute 40

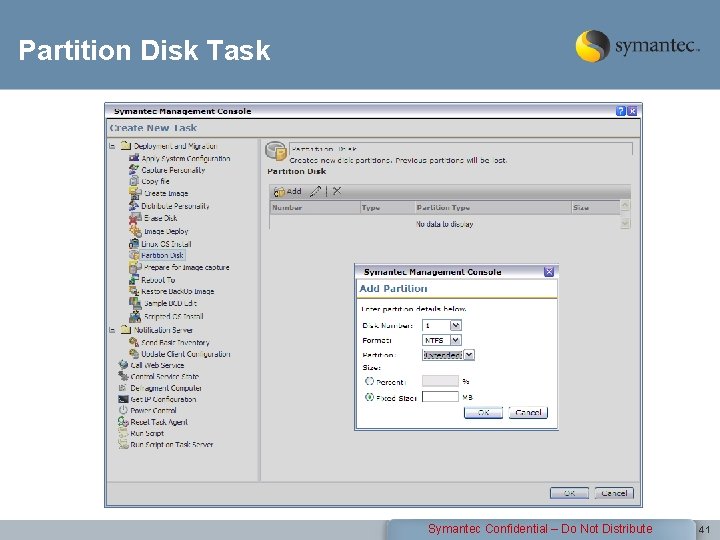
Partition Disk Task Symantec Confidential – Do Not Distribute 41

Power Control Task Symantec Confidential – Do Not Distribute 42

Prepare for Image Capture Task Symantec Confidential – Do Not Distribute 43

Reboot To. . . Task Symantec Confidential – Do Not Distribute 44

Restore Backup Image Task Symantec Confidential – Do Not Distribute 45