Cryptographic Hash Functions Ch 11 u Applications of




















- Slides: 46

Cryptographic Hash Functions (Ch. 11) u Applications of cryptographic hash functions u Simple hash functions u Requirements and security u Hash functions based on cipher block chaining u Secure hash algorithm (SHA) u SHA-3 u Summary Cryptograpgy and Network Security 11 - 1 Anthony J. T. Lee Dept. of Information Management, NTU

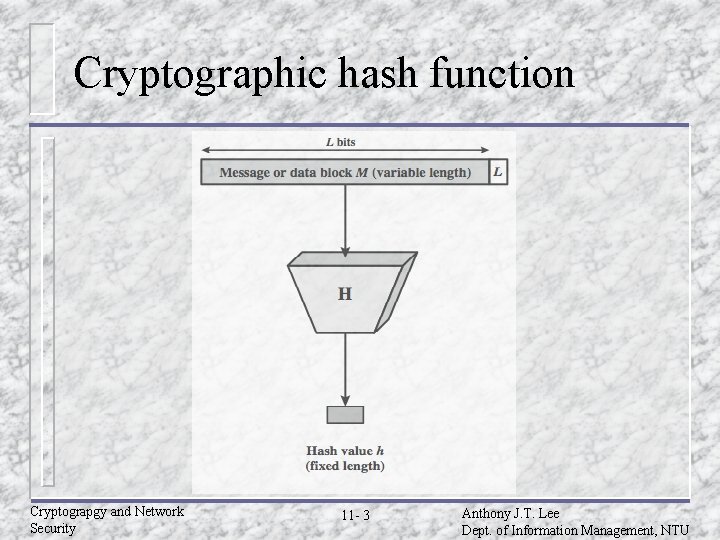
Hash functions u Condenses arbitrary message to fixed size h = H(M) u Usually assume hash function is public u Hash used to detect changes to message u Properties of cryptographic hash function – – computationally infeasible to find data mapping to specific hash (one-way property) computationally infeasible to find two data to same hash (collision-free property) Cryptograpgy and Network Security 11 - 2 Anthony J. T. Lee Dept. of Information Management, NTU

Cryptographic hash function Cryptograpgy and Network Security 11 - 3 Anthony J. T. Lee Dept. of Information Management, NTU

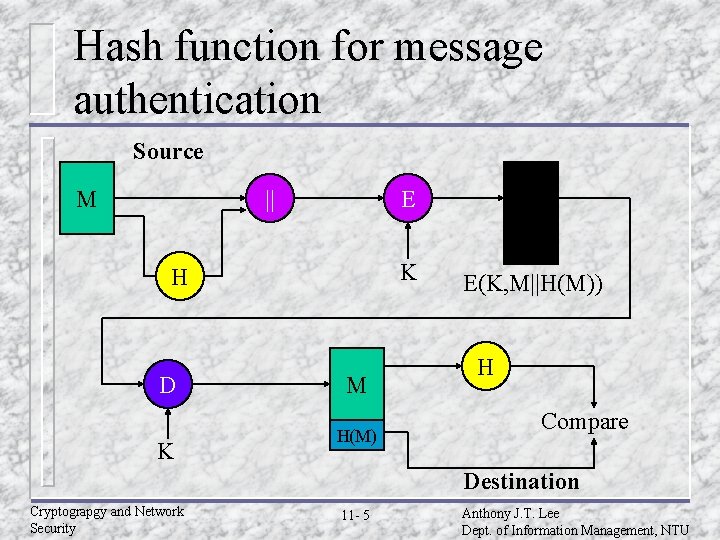
Message authentication u. A mechanism or service used to verify the integrity of a message. u Message authentication assures that data received are exactly as sent. Cryptograpgy and Network Security 11 - 4 Anthony J. T. Lee Dept. of Information Management, NTU

Hash function for message authentication Source || M E K H D K M H(M) E(K, M||H(M)) H Compare Destination Cryptograpgy and Network Security 11 - 5 Anthony J. T. Lee Dept. of Information Management, NTU

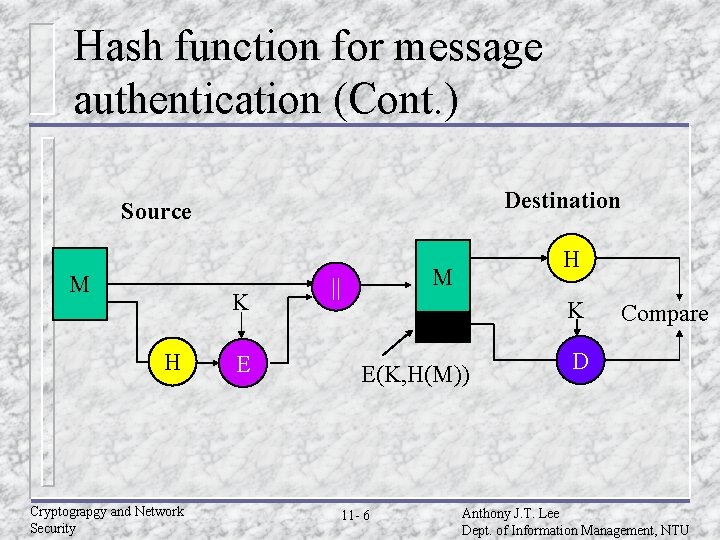
Hash function for message authentication (Cont. ) Destination Source M K H Cryptograpgy and Network Security E H M || K E(K, H(M)) 11 - 6 Compare D Anthony J. T. Lee Dept. of Information Management, NTU

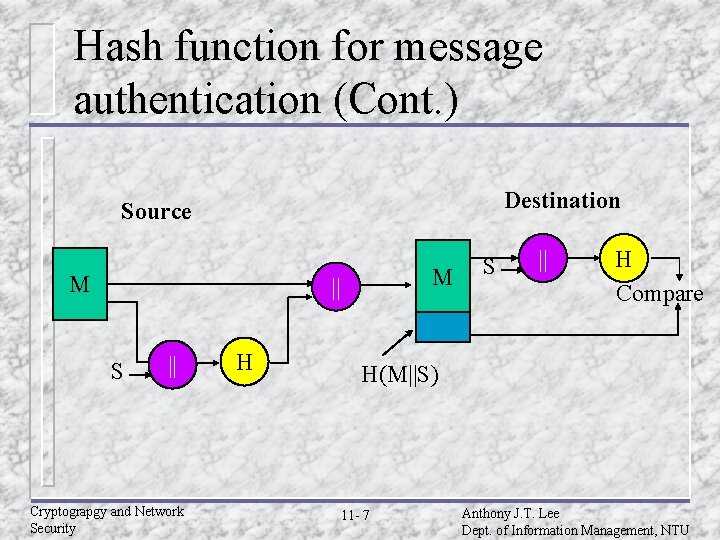
Hash function for message authentication (Cont. ) Destination Source M M || S || Cryptograpgy and Network Security H S || H Compare H(M||S) 11 - 7 Anthony J. T. Lee Dept. of Information Management, NTU

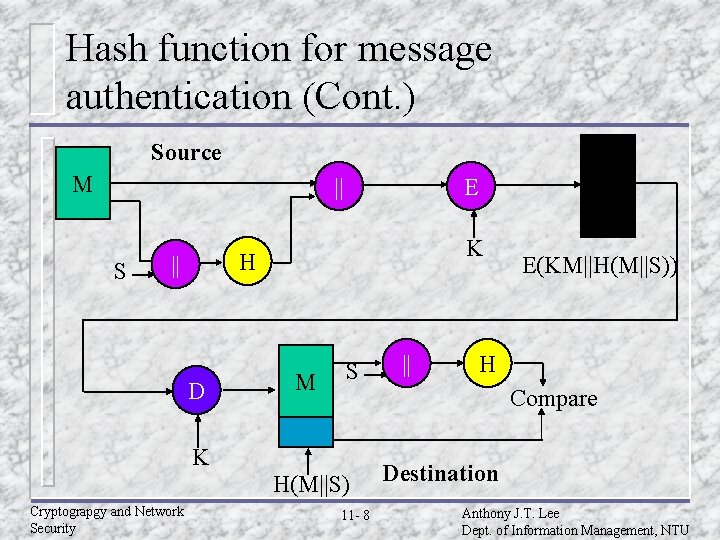
Hash function for message authentication (Cont. ) Source M || S E K H || D M S K H(M||S) Cryptograpgy and Network Security 11 - 8 || E(KM||H(M||S)) H Compare Destination Anthony J. T. Lee Dept. of Information Management, NTU

Hash function for message authentication u A B: E(K, M||H(M)) – Provides confidentiality: only A and B share K – Provides authentication: H(M) is cryptograpically protected u A B: M||E(K, H(M)) – Provides authentication: H(M) is cryptograpically protected u A B: M||H(M||S) – Provides authentication: only A and B share S u A B: – – E(K, [M||H(M||S)) Provides authentication : only A and B share S Provides confidentiality: only A and B share K Cryptograpgy and Network Security 11 - 9 Anthony J. T. Lee Dept. of Information Management, NTU

Digital signature u The hash value of a message is encrypted with a user’s private key. u Anyone who knows the user’s public key can verify the integrity of the message that is associated with the digital signature. Cryptograpgy and Network Security 11 - 10 Anthony J. T. Lee Dept. of Information Management, NTU

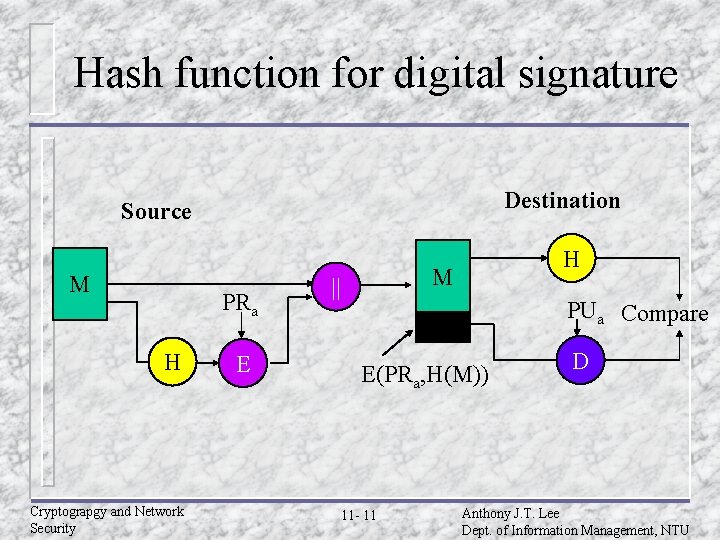
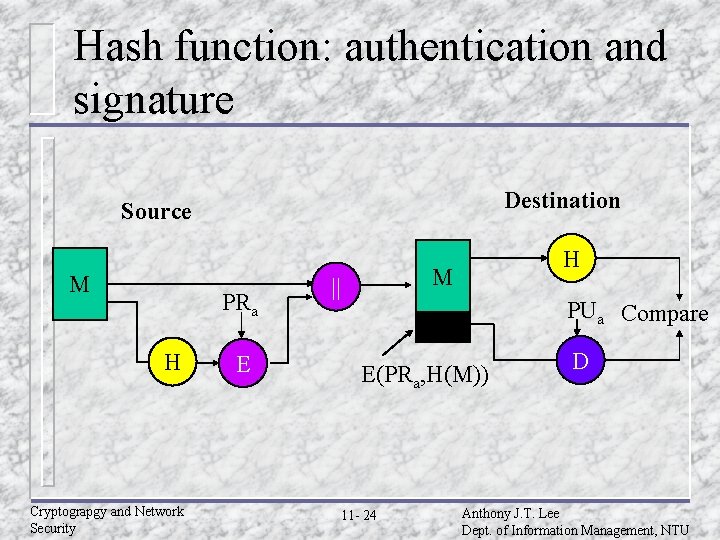
Hash function for digital signature Destination Source M PRa H Cryptograpgy and Network Security E H M || PUa Compare E(PRa, H(M)) 11 - 11 D Anthony J. T. Lee Dept. of Information Management, NTU

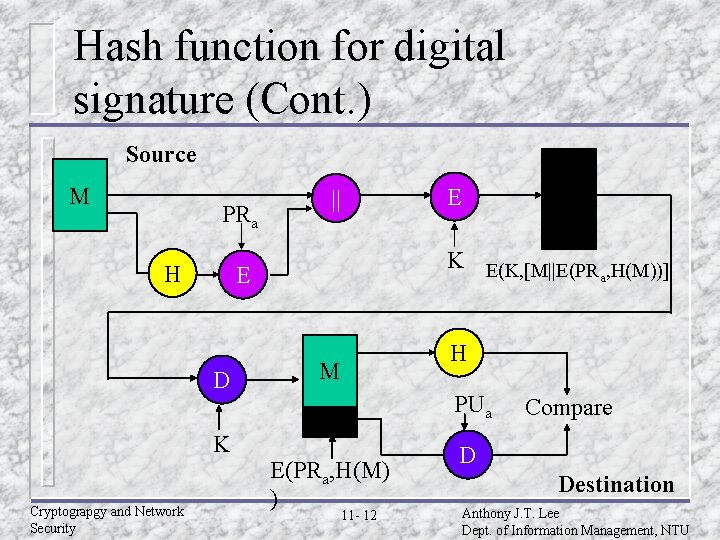
Hash function for digital signature (Cont. ) Source M PRa H K E(K, [M||E(PR , H(M))] a E D K Cryptograpgy and Network Security E || H M PUa E(PRa, H(M) ) 11 - 12 Compare D Destination Anthony J. T. Lee Dept. of Information Management, NTU

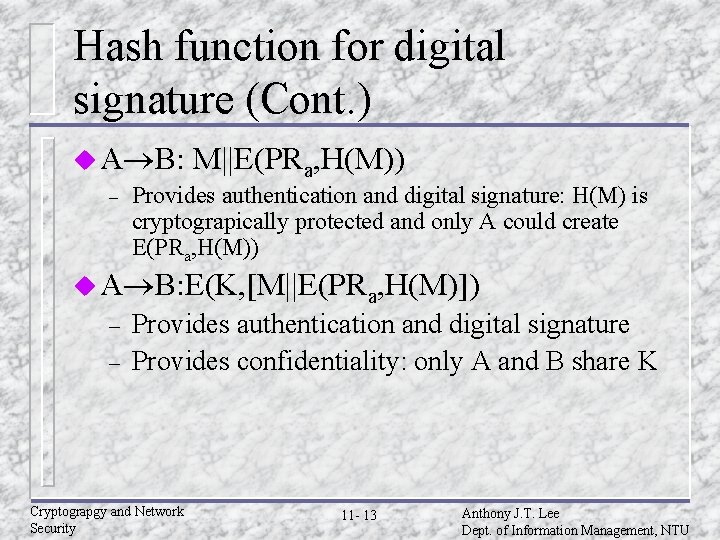
Hash function for digital signature (Cont. ) u A B: M||E(PRa, H(M)) – Provides authentication and digital signature: H(M) is cryptograpically protected and only A could create E(PRa, H(M)) u A B: E(K, [M||E(PRa, H(M)]) – – Provides authentication and digital signature Provides confidentiality: only A and B share K Cryptograpgy and Network Security 11 - 13 Anthony J. T. Lee Dept. of Information Management, NTU

Other hash functions u To – create a one-way password file store hash of password not actual password u For – intrusion detection and virus detection keep & check hash of files on system u Pseudorandom function (PRF) or pseudorandom number generator (PRNG) Cryptograpgy and Network Security 11 - 14 Anthony J. T. Lee Dept. of Information Management, NTU

Simple hash functions Cryptograpgy and Network Security 11 - 15 Anthony J. T. Lee Dept. of Information Management, NTU

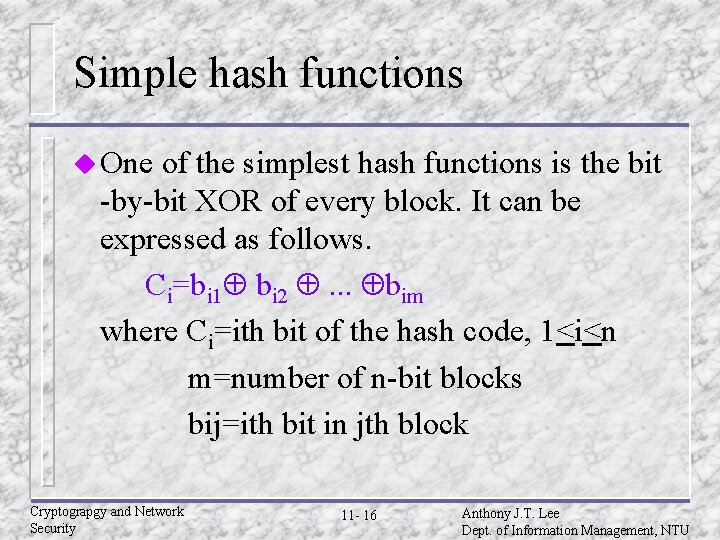
Simple hash functions u One of the simplest hash functions is the bit -by-bit XOR of every block. It can be expressed as follows. Ci=bi 1 bi 2 . . . bim where Ci=ith bit of the hash code, 1<i<n m=number of n-bit blocks bij=ith bit in jth block Cryptograpgy and Network Security 11 - 16 Anthony J. T. Lee Dept. of Information Management, NTU

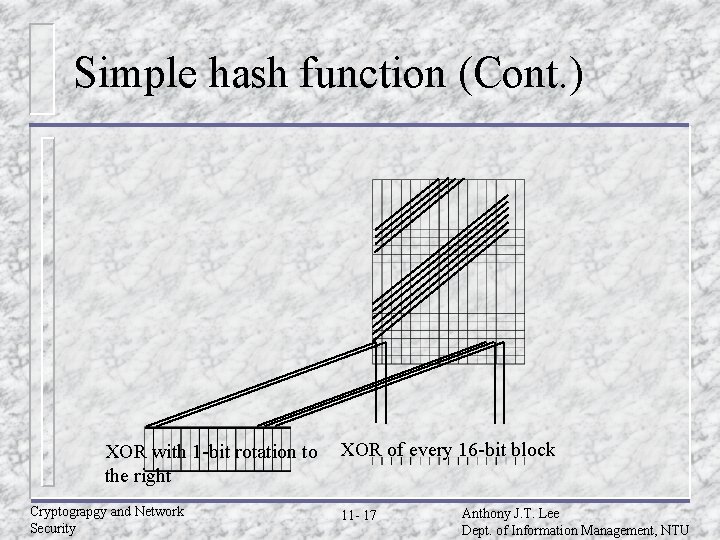
Simple hash function (Cont. ) XOR with 1 -bit rotation to the right Cryptograpgy and Network Security XOR of every 16 -bit block 11 - 17 Anthony J. T. Lee Dept. of Information Management, NTU

Simple XOR or rotated XOR u u u Although a simple XOR or rotated XOR (RXOR) is insufficient if only the hash code is encrypted, you may still feel that such a simple function could be useful when the message as well as the hash code are encrypted. However, you must be really careful. Consider the cipher block chaining (CBC). Given a message consisting of a sequence of 64 -bit blocks of X 1, X 2, …, XN, define the hash code C as the block-by-block XOR or all blocks and append the hash code as the final block. C=XN+1=X 1 X 2 … XN Cryptograpgy and Network Security 11 - 18 Anthony J. T. Lee Dept. of Information Management, NTU

CBC u u Next, encrypt the entire message plus hash code, using CBC mode to produce the encrypted message Y 1, Y 2, …, YN+1. Then we have X 1=IV D(K, Y 1) Xi=Yi-1 D(K, Yi) XN+1=YN D(K, YN+1) But XN+1 is the hash code: XN+1=X 1 X 2 … XN =[IV D(K, Y 1)] [Y 1 D(K, Y 2)] . . . [YN-1 D(K, YN)] The hash code would not change if the ciphertext blocks were permuted. Cryptograpgy and Network Security 11 - 19 Anthony J. T. Lee Dept. of Information Management, NTU

Requirement for a hash function A hash function H can be applied to a block size of any size. u H produces a fixed-length output. u H(x) is relatively easy to compute for any given x. u For any given code h, it is computationally infeasible to find x such that H(x)=h. (preimage resistant; oneway) u For any given block x, it is computationally infeasible to find y x with H(y)=H(x). (second preimage resistant) u It is computationally infeasible to find any pair (x, y) such that H(x)=H(y). (collision resistant) u Cryptograpgy and Network Security 11 - 20 Anthony J. T. Lee Dept. of Information Management, NTU

Attacks on hash functions u have brute-force attacks and cryptanalysis u a preimage or second preimage attack – find y s. t. H(y)equals a given hash value (2 m-1 attempts) u collision – resistance find two messages x & y with the same hash so that H(x)=H(y) (2 m/2 attempts) u hence value 2 m/2 determines strength of hash code against brute-force attacks – 128 -bits inadequate, 160 -bits suspect Cryptograpgy and Network Security 11 - 21 Anthony J. T. Lee Dept. of Information Management, NTU

Birthday attacks u Suppose that a 64 -bit hash code is used. One might think this is quite secure. u For example, if an encrypted hash code C is transmitted with the corresponding unencrypted message M, then an opponent would need to find an M’ such that H(M’)=H(M) to substitute another message and fool the receiver. u On average, the opponent would have to try 263 messages to find one. Cryptograpgy and Network Security 11 - 22 Anthony J. T. Lee Dept. of Information Management, NTU

Birthday attacks (Cont. ) u Yuval – – proposed the following attack strategy: The source A is prepared to “sign” a message by appending the appropriate m-bit MAC and encrypting that MAC with A’s private key. The opponent generates 2 m/2 variations on the message, all of which convey essentially the same meaning. The opponent prepares for an equal number of messages, all of which are variations on the fraudulent message to be substituted for the real one. Cryptograpgy and Network Security 11 - 23 Anthony J. T. Lee Dept. of Information Management, NTU

Hash function: authentication and signature Destination Source M PRa H Cryptograpgy and Network Security E H M || PUa Compare E(PRa, H(M)) 11 - 24 D Anthony J. T. Lee Dept. of Information Management, NTU

Birthday attacks (Cont. ) – – The two sets of messages are compared to find a pair of messages that produces the same hash code. If no match is found, additional valid and fraudulent messages are generated until a match is made. The opponent offers the valid variation to A for signature. This signature can then be attached to the fraudulent variation for transmission to the intended recipient. Cryptograpgy and Network Security 11 - 25 Anthony J. T. Lee Dept. of Information Management, NTU

Birthday attacks (Cont. ) u Thus, if a 64 -bit hash code is used, the level of effort required is only on the order of 232. u The conclusion to be drawn from this is that the length of the hash code should be substantial. Cryptograpgy and Network Security 11 - 26 Anthony J. T. Lee Dept. of Information Management, NTU

A letter in 237 variations

Security of hash functions We can group attacks on hash functions into two categories: brute-force attacks and cryptanalysis. u The strength of a hash functions against brute-force attacks depends solely on the length of the hash code. u For a code of length m, the level of effort required is proportional to the following. u Cryptograpgy and Network Security 11 - 28 Anthony J. T. Lee Dept. of Information Management, NTU

Another version of birthday attack u Assume that the opponent intercepts a message with a signature in the form of an encrypted hash code and that the unencrypted hash code is m bits long. u Use the algorithm defined at the beginning of this subsection to calculate the unencrypted has code G. u Construct any desired message in the form Q 1, Q 2, …, QN-2. u Compute Hi= E(Qi, Hi-1), for 1<i<(N-2). Cryptograpgy and Network Security 11 - 29 Anthony J. T. Lee Dept. of Information Management, NTU

Another version of birthday attack (Cont. ) u Generate 2 m/2 random blocks, for each block X, compute D(Y, G), where D is the decryption function corresponding to E. u Based on the birthday paradox, with high probability there will be an X and Y such that E(X, HN-2)=D(Y, G). u Form the message Q 1, Q 2, …, QN-2, X, Y. This message has the hash code G and therefore can be used with the intercepted encrypted signature. Cryptograpgy and Network Security 11 - 30 Anthony J. T. Lee Dept. of Information Management, NTU

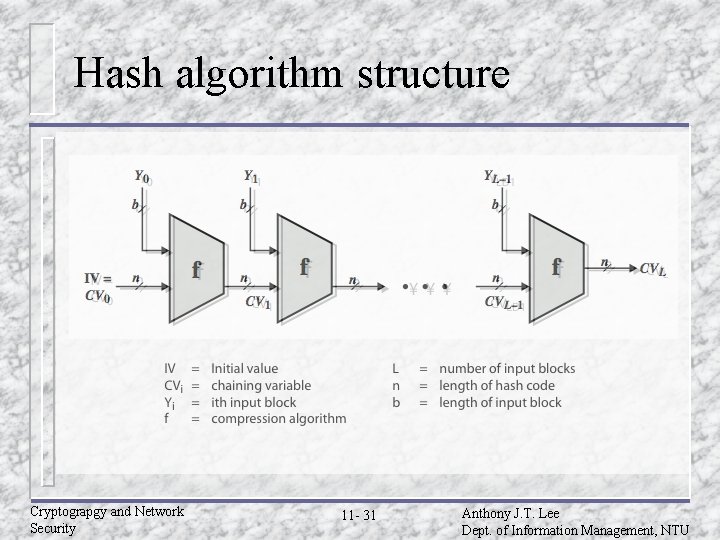
Hash algorithm structure Cryptograpgy and Network Security 11 - 31 Anthony J. T. Lee Dept. of Information Management, NTU

Secure hash algorithm u SHA was originally designed by NIST & NSA in 1993 and revised in 1995 as SHA-1. u US standard for use with DSA signature scheme. u Based on design of MD 4 with key differences. u SHA-1 produces 160 -bit hash values. u Two messages deliver the same SHA-1 hash using 269 operations, far fewer than 280 operations. (王小 雲) u Recent 2005 results on security of SHA-1 have raised concerns on its use in future applications. Cryptograpgy and Network Security 11 - 32 Anthony J. T. Lee Dept. of Information Management, NTU

Revised secure hash standard u NIST issued revision FIPS 180 -2 in 2002. u Adds 3 additional versions (SHA-2) – SHA-256, SHA-384, SHA-512 u Designed for compatibility with increased security provided by the AES cipher. u Structure & detail is similar to SHA-1, hence analysis should be similar, but security levels are rather higher. Cryptograpgy and Network Security 11 - 33 Anthony J. T. Lee Dept. of Information Management, NTU

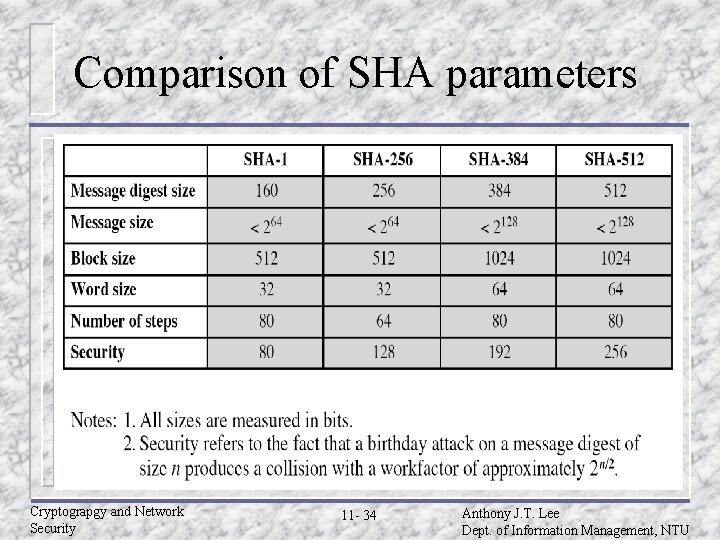
Comparison of SHA parameters Cryptograpgy and Network Security 11 - 34 Anthony J. T. Lee Dept. of Information Management, NTU

SHA-512 logic u Append padding bits: the length in bits is congruent to 896 mod 1024. The padding consists of a single 1 -bit followed by 0 -bits. u Append length: a 128 -bit representation of the length in bits of the original message is appended. Cryptograpgy and Network Security 11 - 35 Anthony J. T. Lee Dept. of Information Management, NTU

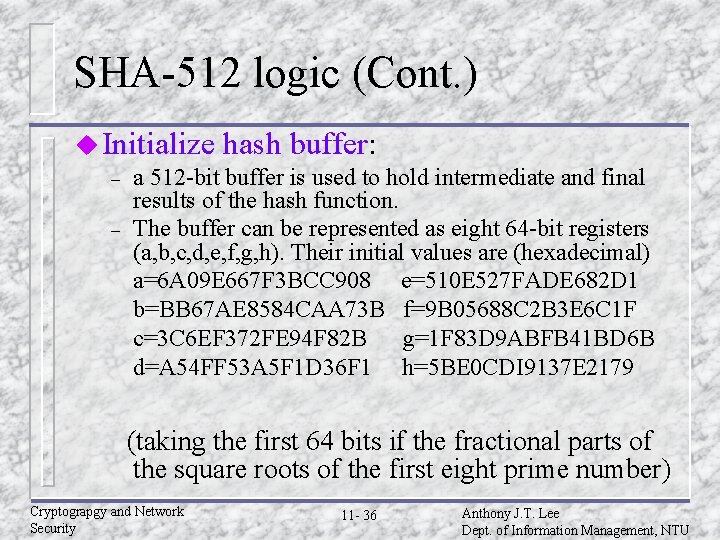
SHA-512 logic (Cont. ) u Initialize hash buffer: – a 512 -bit buffer is used to hold intermediate and final results of the hash function. – The buffer can be represented as eight 64 -bit registers (a, b, c, d, e, f, g, h). Their initial values are (hexadecimal) a=6 A 09 E 667 F 3 BCC 908 e=510 E 527 FADE 682 D 1 b=BB 67 AE 8584 CAA 73 B f=9 B 05688 C 2 B 3 E 6 C 1 F c=3 C 6 EF 372 FE 94 F 82 B g=1 F 83 D 9 ABFB 41 BD 6 B d=A 54 FF 53 A 5 F 1 D 36 F 1 h=5 BE 0 CDI 9137 E 2179 (taking the first 64 bits if the fractional parts of the square roots of the first eight prime number) Cryptograpgy and Network Security 11 - 36 Anthony J. T. Lee Dept. of Information Management, NTU

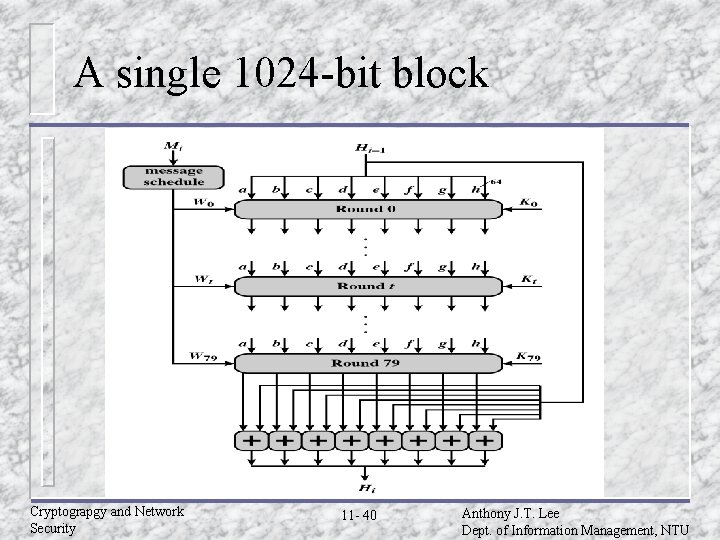
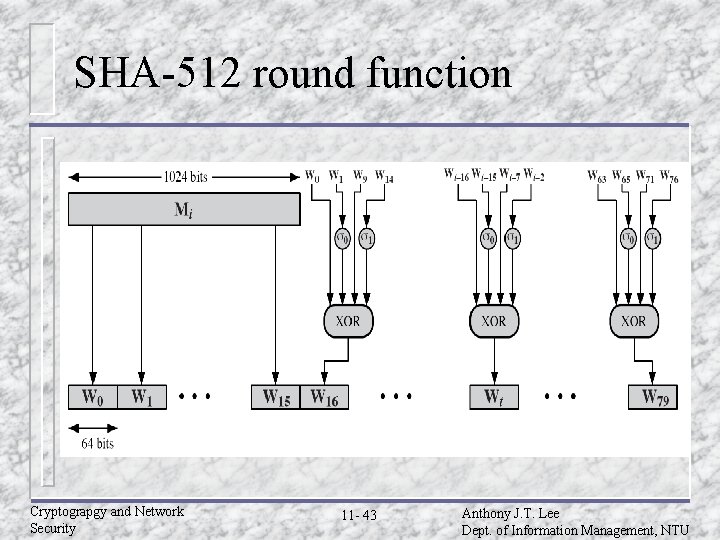
SHA-512 logic (Cont. ) u Process – message in 1024 -bit (128 -word) blocks. The compression function contains 80 rounds. u Output. After all N 1024 -bit blocks have been processed, the output from the Nth stage is the 512 -bit message digest. u The behavior of MD 5 can be summarized H 0=IV Hi=SUM 64(Hi-1, abcdefghi) MD=HN Cryptograpgy and Network Security 11 - 37 Anthony J. T. Lee Dept. of Information Management, NTU

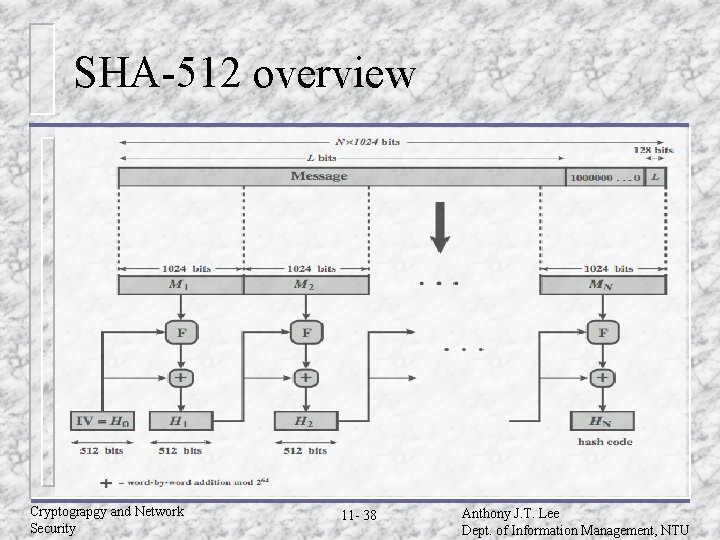
SHA-512 overview Cryptograpgy and Network Security 11 - 38 Anthony J. T. Lee Dept. of Information Management, NTU

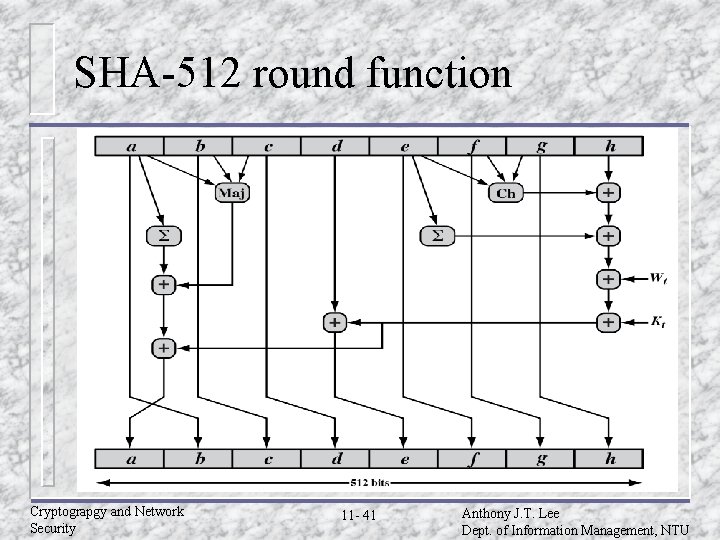
SHA-512 compression function u Process message in 1024 -bit blocks. u Contains 80 rounds. – – – Updating a 512 -bit buffer. Using a 64 -bit value derived from the current message block. A round constant based on cube root of first 80 prime numbers. Cryptograpgy and Network Security 11 - 39 Anthony J. T. Lee Dept. of Information Management, NTU

A single 1024 -bit block Cryptograpgy and Network Security 11 - 40 Anthony J. T. Lee Dept. of Information Management, NTU

SHA-512 round function Cryptograpgy and Network Security 11 - 41 Anthony J. T. Lee Dept. of Information Management, NTU

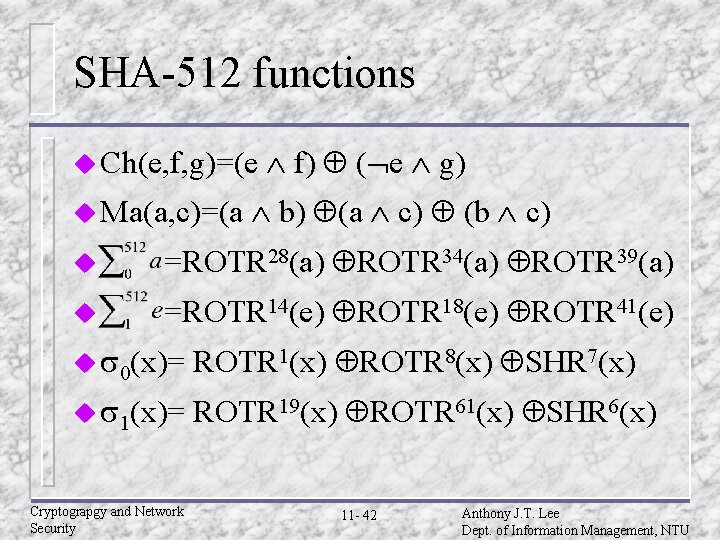
SHA-512 functions u Ch(e, f, g)=(e u Ma(a, c)=(a f) ( e g) b) (a c) (b c) u =ROTR 28(a) ROTR 34(a) ROTR 39(a) u =ROTR 14(e) ROTR 18(e) ROTR 41(e) u s 0(x)= ROTR 1(x) ROTR 8(x) SHR 7(x) u s 1(x)= ROTR 19(x) ROTR 61(x) SHR 6(x) Cryptograpgy and Network Security 11 - 42 Anthony J. T. Lee Dept. of Information Management, NTU

SHA-512 round function Cryptograpgy and Network Security 11 - 43 Anthony J. T. Lee Dept. of Information Management, NTU

SHA-3 u SHA-1 – – But similar to broken MD 5 & SHA-0. So considered insecure. u SHA-2 – not yet "broken”. (esp. SHA-512) seems secure. Shares the same structure and mathematical operations as predecessors. u NIST announced in 2007 a competition for the SHA-3 next genenation NIST hash function. – To have in place by 2012 but not fixed. Cryptograpgy and Network Security 11 - 44 Anthony J. T. Lee Dept. of Information Management, NTU

SHA-3 requirements u Replace – so use the same hash sizes u Preserve – SHA-2 with SHA-3 in any use the online nature of SHA-2 Must process small blocks (512 / 1024 bits). u Evaluation – – – criteria Security close to theoretical max for hash sizes Cost in time & memory Characteristics: such as flexibility & simplicity Cryptograpgy and Network Security 11 - 45 Anthony J. T. Lee Dept. of Information Management, NTU

Homework u P 378 (Chapter 11) 11. 3 11. 8 11. 12 Cryptograpgy and Network Security 11 - 46 Anthony J. T. Lee Dept. of Information Management, NTU