Computer Networks 2021 Networking Computer network A collection
























































- Slides: 93

Computer Networks 2021

Networking • Computer network A collection of computing devices that are connected in various ways in order to communicate and share resources Usually, the connections between computers in a network are made using physical wires or cables However, some connections are wireless, using radio waves or infrared signals

Networking • The generic term node or host refers to any device on a network • Data transfer rate. The speed with which data is moved from one place on a network to another • Data transfer rate is a key issue in computer networks


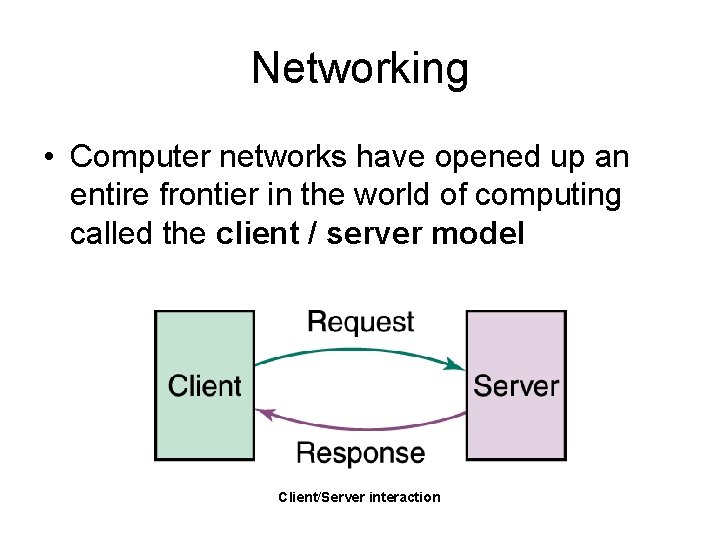
Networking • Computer networks have opened up an entire frontier in the world of computing called the client / server model Client/Server interaction

Networking • File server A computer that stores and manages files for multiple users on a network • Web server A computer dedicated to responding to requests (from the browser client) for web pages

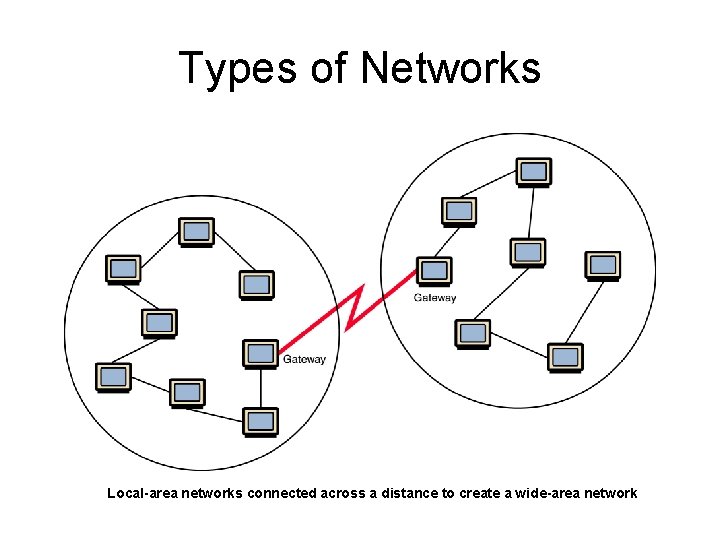
Types of Networks • Local-area network (LAN) A network that connects a relatively small number of machines in a relatively close geographical area.

Types of Networks • Various configurations, called topologies, have been used to administer LANs – Bus topology – Star topology – Passive star topology – Ring topology – Mixed topology

Схема Bus topology server РС РС line Bus topology All nodes are connected to a single communication line that carries messages in both directions.




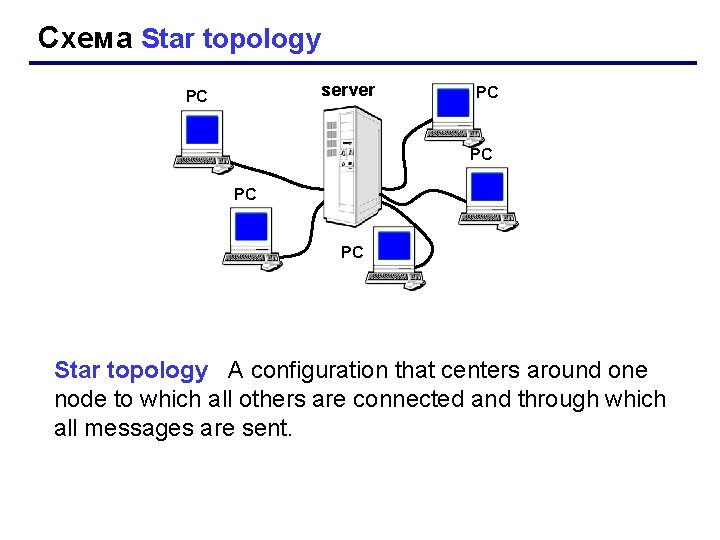
Схема Star topology server РС РС РС Star topology A configuration that centers around one node to which all others are connected and through which all messages are sent.


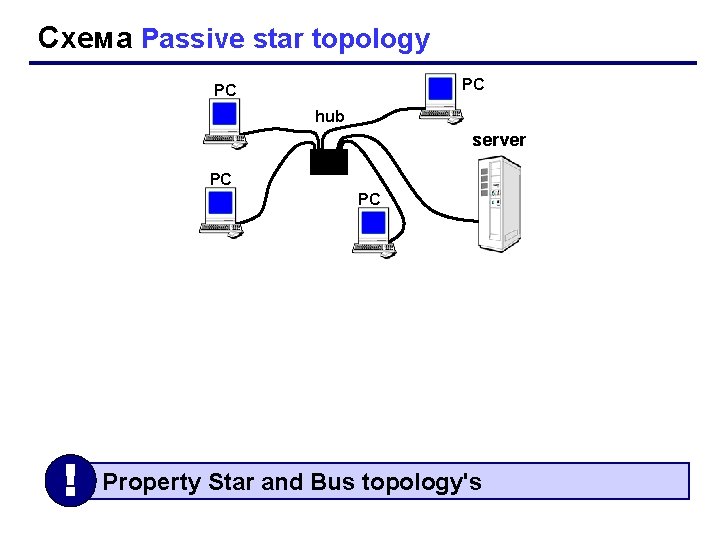
Схема Passive star topology РС РС hub server РС РС ! Property Star and Bus topology's

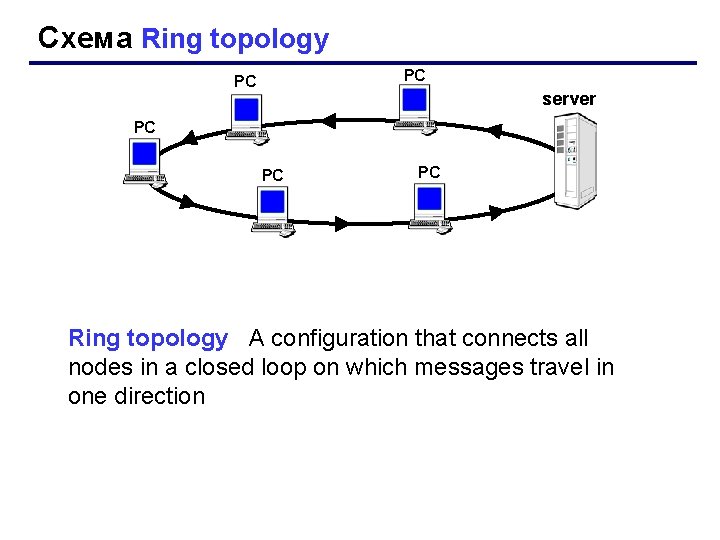
Схема Ring topology РС РС server РС РС РС Ring topology A configuration that connects all nodes in a closed loop on which messages travel in one direction

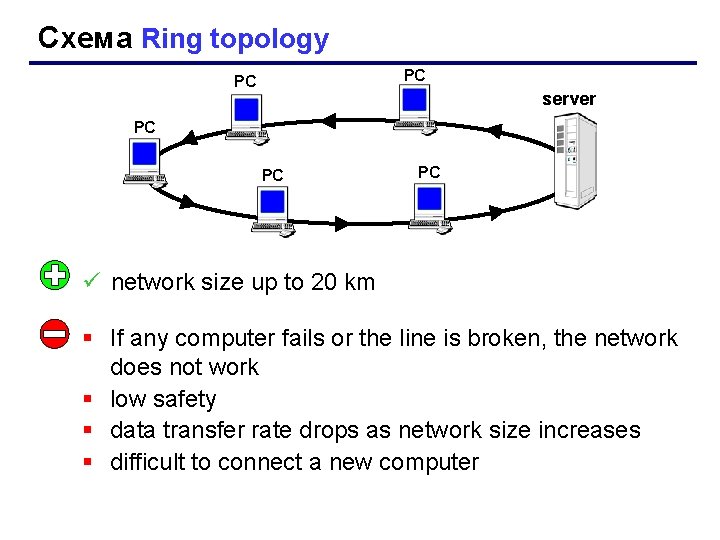
Схема Ring topology РС РС server РС РС РС ü network size up to 20 km § If any computer fails or the line is broken, the network does not work § low safety § data transfer rate drops as network size increases § difficult to connect a new computer

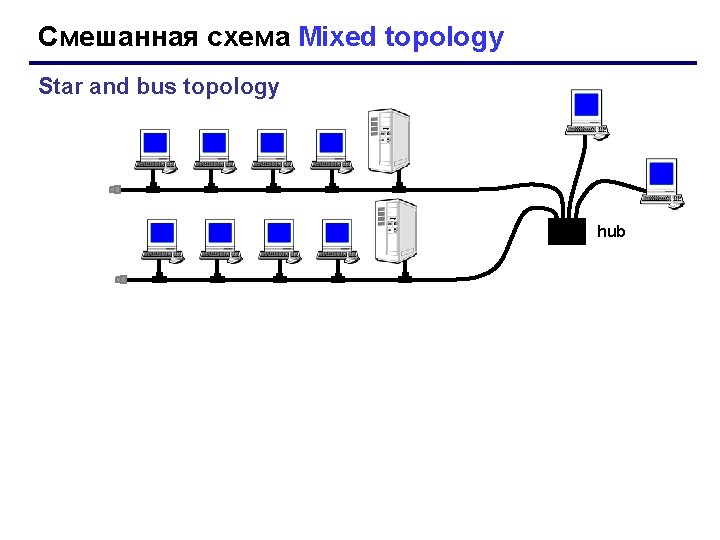
Смешанная схема Mixed topology Star and bus topology hub


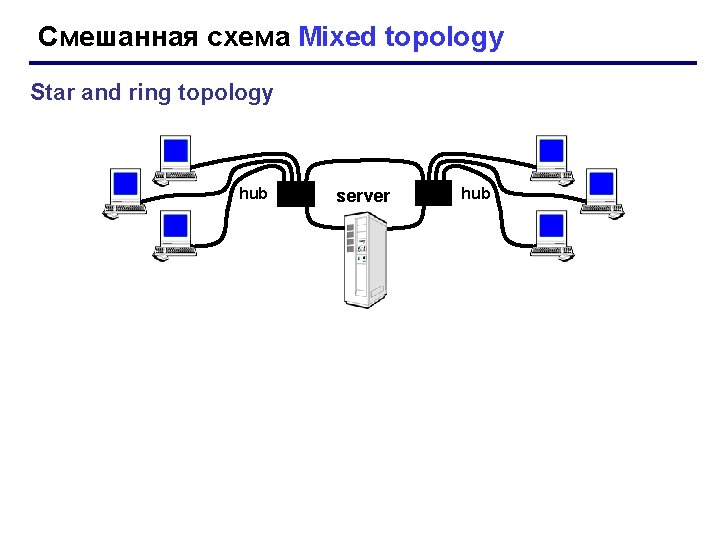
Смешанная схема Mixed topology Star and ring topology hub server hub


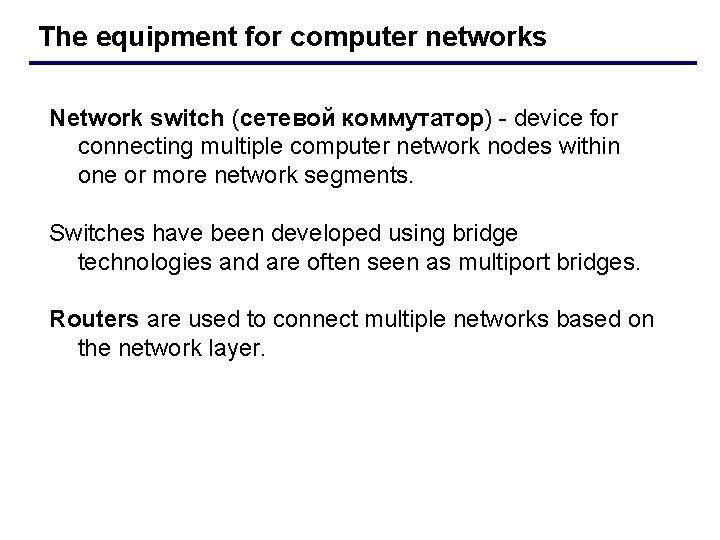
The equipment for computer networks Network switch (сетевой коммутатор) - device for connecting multiple computer network nodes within one or more network segments. Switches have been developed using bridge technologies and are often seen as multiport bridges. Routers are used to connect multiple networks based on the network layer.

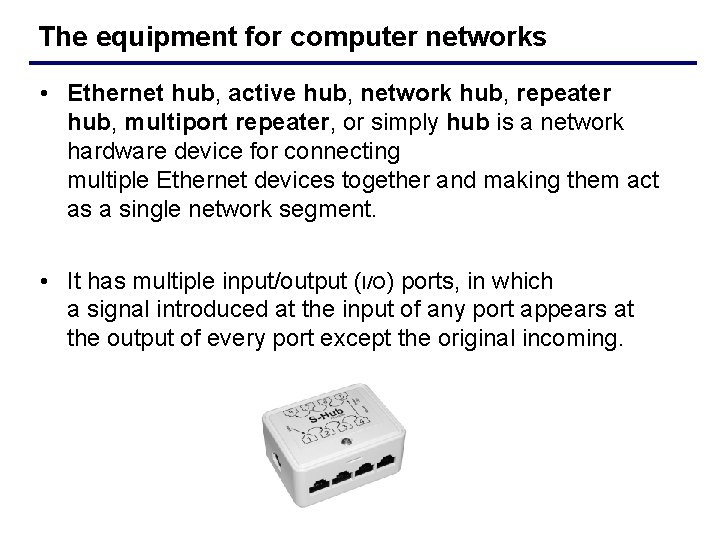
The equipment for computer networks • Ethernet hub, active hub, network hub, repeater hub, multiport repeater, or simply hub is a network hardware device for connecting multiple Ethernet devices together and making them act as a single network segment. • It has multiple input/output (I/O) ports, in which a signal introduced at the input of any port appears at the output of every port except the original incoming.

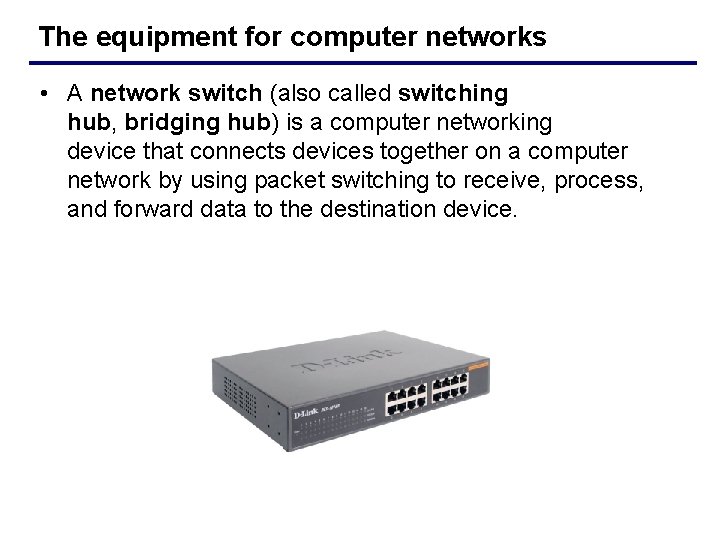
The equipment for computer networks • A network switch (also called switching hub, bridging hub) is a computer networking device that connects devices together on a computer network by using packet switching to receive, process, and forward data to the destination device.

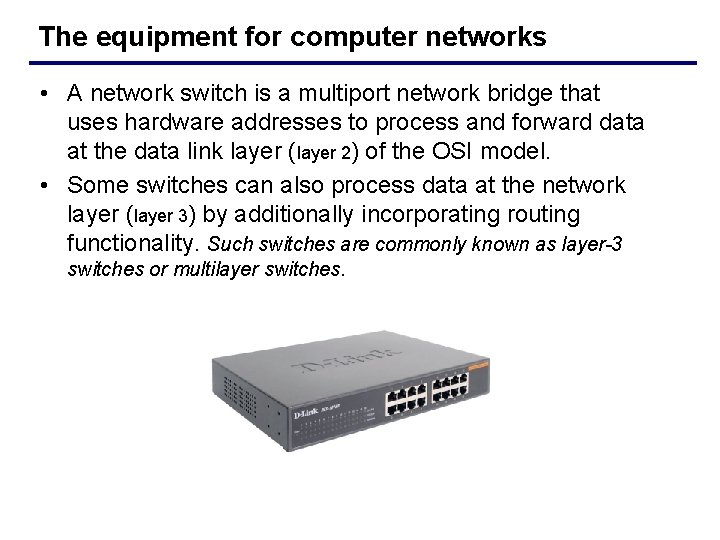
The equipment for computer networks • A network switch is a multiport network bridge that uses hardware addresses to process and forward data at the data link layer (layer 2) of the OSI model. • Some switches can also process data at the network layer (layer 3) by additionally incorporating routing functionality. Such switches are commonly known as layer-3 switches or multilayer switches.


OSI model • The Open Systems Interconnection model (OSI model) is a conceptual model that characterizes and standardizes the communication functions of a telecommunication or computing system without regard to its underlying internal structure and technology. Its goal is the interoperability of diverse communication systems with standard protocols. • The model partitions a communication system into abstraction layers. • The original version of the model defined seven layers. • A layer serves the layer above it and is served by the layer below it.

OSI model • Open Systems Interconnection model • For example, a layer that provides error-free communications across a network provides the path needed by applications above it, while it calls the next lower layer to send and receive packets that comprise the contents of that path. Two instances at the same layer are visualized as connected by a horizontal connection in that layer.

Communication between networks

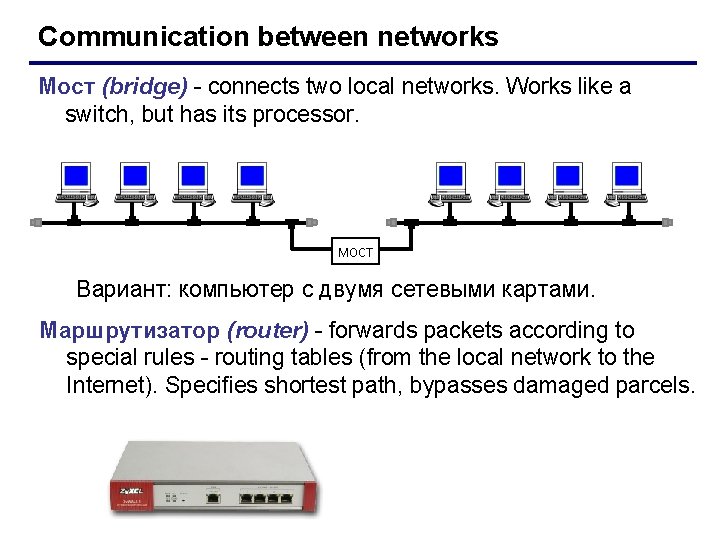
Communication between networks Мост (bridge) - connects two local networks. Works like a switch, but has its processor. мост Вариант: компьютер с двумя сетевыми картами. Маршрутизатор (router) - forwards packets according to special rules - routing tables (from the local network to the Internet). Specifies shortest path, bypasses damaged parcels.

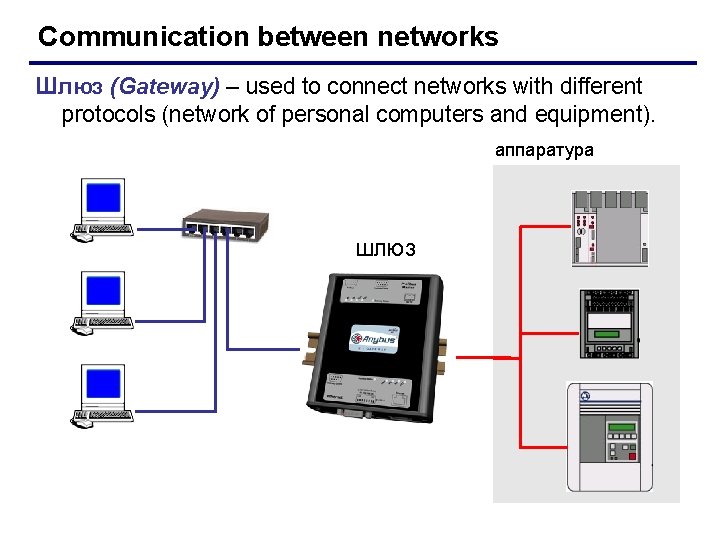
Communication between networks Шлюз (Gateway) – used to connect networks with different protocols (network of personal computers and equipment). аппаратура шлюз


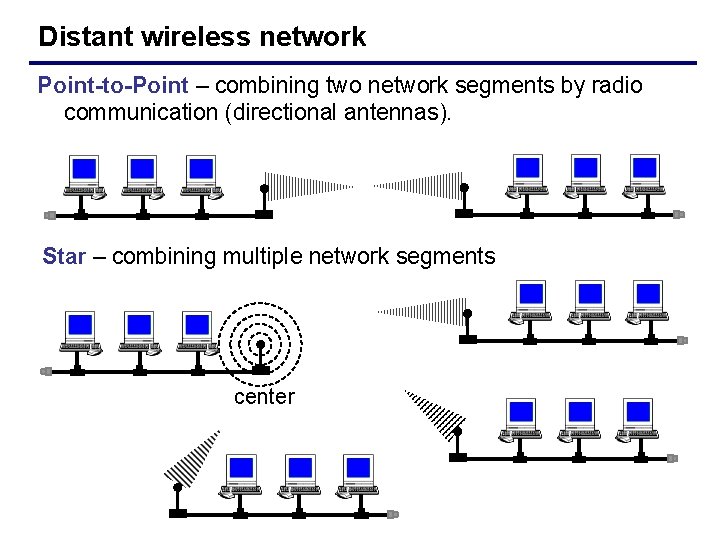
Distant wireless network Point-to-Point – combining two network segments by radio communication (directional antennas). Star – combining multiple network segments center


Types of Networks • Wide-area network (WAN) A network that connects two or more local-area networks over a potentially large geographic distance Often one particular node on a LAN is set up to serve as a gateway to handle all communication going between that LAN and other networks Communication between networks is called internetworking The Internet, as we know it today, is essentially the ultimate wide-area network, spanning the entire globe

Types of Networks • Metropolitan-area network (MAN) The communication infrastructures that have been developed in and around large cities

So, who owns the Internet? Well, nobody does. No single person or company owns the Internet or even controls it entirely. As a wide-area network, it is made up of many smaller networks. These smaller networks are often owned and managed by a person or organization. The Internet, then, is really defined by how connections can be made between these networks.

Types of Networks Local-area networks connected across a distance to create a wide-area network

Internet Connections • Internet backbone A set of high-speed networks that carry Internet traffic These networks are provided by companies such as AT&T, GTE, and IBM • Internet service provider (ISP) A company that provides other companies or individuals with access to the Internet

Internet Connections • There are various technologies available that you can use to connect a home computer to the Internet – A phone modem converts computer data into an analog audio signal for transfer over a telephone line, and then a modem at the destination converts it back again into data – A digital subscriber line (DSL) uses regular copper phone lines to transfer digital data to and from the phone company’s central office – A cable modem uses the same line that your cable TV signals come in on to transfer the data back and forth

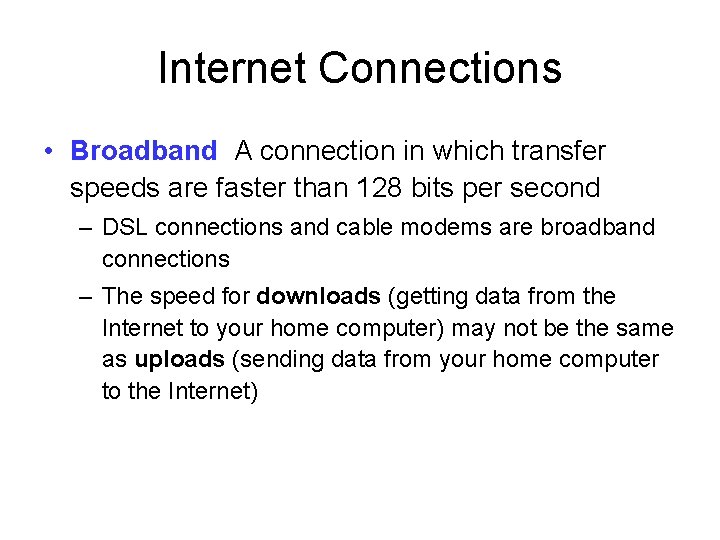
Internet Connections • Broadband A connection in which transfer speeds are faster than 128 bits per second – DSL connections and cable modems are broadband connections – The speed for downloads (getting data from the Internet to your home computer) may not be the same as uploads (sending data from your home computer to the Internet)

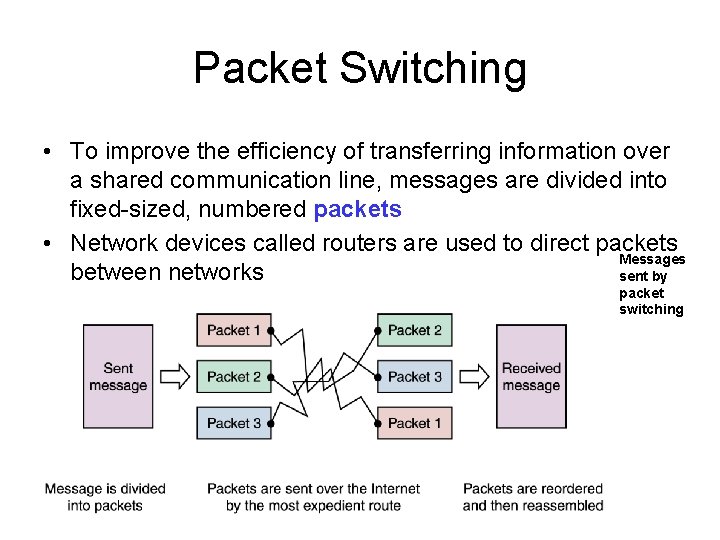
Packet Switching • To improve the efficiency of transferring information over a shared communication line, messages are divided into fixed-sized, numbered packets • Network devices called routers are used to direct packets Messages between networks sent by packet switching

Open Systems • Proprietary system A system that uses technologies kept private by a particular commercial vendor One system couldn’t communicate with another, leading to the need for • Interoperability The ability of software and hardware on multiple machines and from multiple commercial vendors to communicate Leading to • Open systems Systems based on a common model of network architecture and a suite of protocols used in its implementation

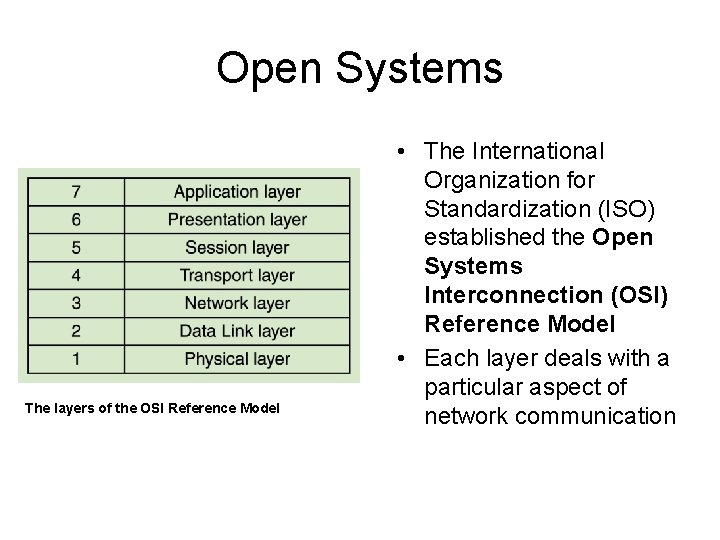
Open Systems The layers of the OSI Reference Model • The International Organization for Standardization (ISO) established the Open Systems Interconnection (OSI) Reference Model • Each layer deals with a particular aspect of network communication

VIRUS & ANTIVIRUS

What is a computer virus? • began in the late 1980 s as personal computers and electronic bulletin boards became more common. Back then, operating systems, word processing programs and other programs were stored on floppy disks. Hidden viruses were programmed onto these disks; as the disks were transferred from person to person, the virus spread.

What is a computer virus? • A computer virus is a malicious program that spreads from computer to computer. • Computer virus refers to a program which damages computer systems and/or destroys or erases data files.

What is a computer virus? • Computer viruses are small software programs that are designed to spread from one computer to another and to interfere with computer operation. • A virus might corrupt or delete data on your computer, use your e-mail program to spread itself to other computers, or even erase everything on your hard disk. • Viruses can be disguised as attachments of funny images, greeting cards, or audio and video files.

What is a computer virus? • Viruses are most easily spread by attachments in e-mail messages or instant messaging messages. That is why it is essential that you never open e-mail attachments unless you know who it's from and you are expecting it. • Viruses also spread through downloads on the Internet. They can be hidden in illicit software or other files or programs you might download.

Types of Viruses • • 1. Boot sector viruses 2. Program viruses 3. Macro- viruses 4. Other types

Types of Viruses • 1. Boot sector viruses are most predominant viruses until the mid-90 s. They infects boot sectors on diskettes and hard disks. On diskettes, the boot sector normally contains code to load the operating system files.

Types of Viruses • 2. Program viruses, the second type of computer viruses, infect executable programs; usually *. COM and *. EXE files, but they sometimes also infect overlay files, device drivers or even object files.

Types of Viruses • 3. The third type of viruses is Macro-viruses, which do not infect normal programs, but instead spread as "macros" in various types of files. This type of viruses can easily spread through E-mail, when users unknowingly exchange infected documents.

Other types of Viruses • Worms: A program or algorithm that replicates itself over a computer network and usually performs malicious actions. – – Replicates itself automatically. Can infect computers by Spyware, Malware, and Email. • Spam: Spam is flooding the Internet with many copies of the same message, in an attempt to force the message on people who would not otherwise choose to receive it.

Other types of Viruses • Virus Hoaxes – Do not carry a harmful payload, but do waste an incredible amount of time. • Trojan Horses: a malicious program that pretends to be a normal program. – Does not replicate itself like a worm. – Also comes in as an attachment with various file extensions. (*. exe, *. zip, *. htm, etc…) – Installs backdoors.

Other types of Viruses • Time bomb • A time bomb is a virus program that performs an activity on a particular date. • Logical bomb • A logical bomb is a destructive program that performs an activity when a certain action has occurred.

Other types of Viruses • Script Virus – • Commonly found script viruses are written using the Visual Basic Scripting edition (VBS) and the Java. Script programming languages.

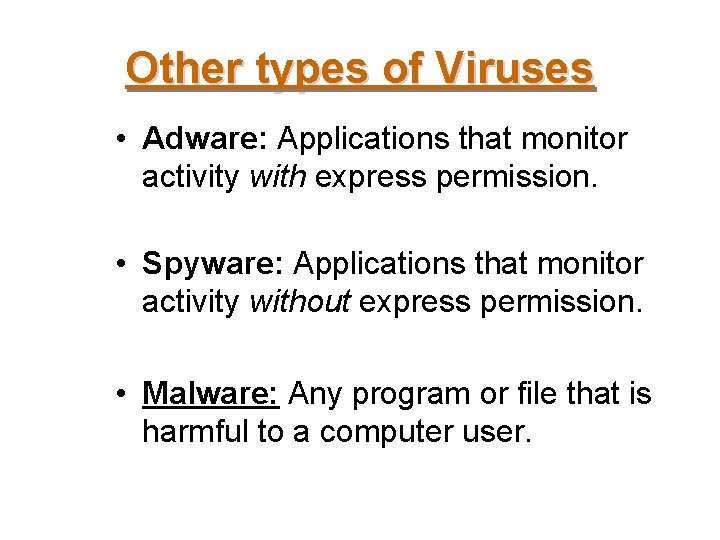
Other types of Viruses • Adware: Applications that monitor activity with express permission. • Spyware: Applications that monitor activity without express permission. • Malware: Any program or file that is harmful to a computer user.


Who Creates Viruses? • Where do viruses come from? • Every virus is created by an author with a different motive - but all virus builders feel their actions are justified. For some, a killer virus is the ultimate technical challenge, like climbing a mountain. For others, creating viruses is a form of self-expression. Some disgruntled employees, consumers or citizens turn to virus building as revenge for perceived injustices.

What Do Viruses Do? • Today’s viruses are far more potent than the beginner versions we saw several decades ago. Viruses may be sent by opening email attachments, clicking on spam, visiting corrupt websites and links online, opening spreadsheets or even the original method—infected disks. But the Internet is now the superhighway for virus transmission.

What Do Viruses Do? • A frightening prospect - opening an email from someone you trust to be greeted by a virus, and that’s exactly what the author is counting on, your trust. • The damage caused by these viruses varies from minor delays in computer function to complete destruction of your hard drive. For companies, the price is far higher. A downed website can cost a company millions of dollars a day.

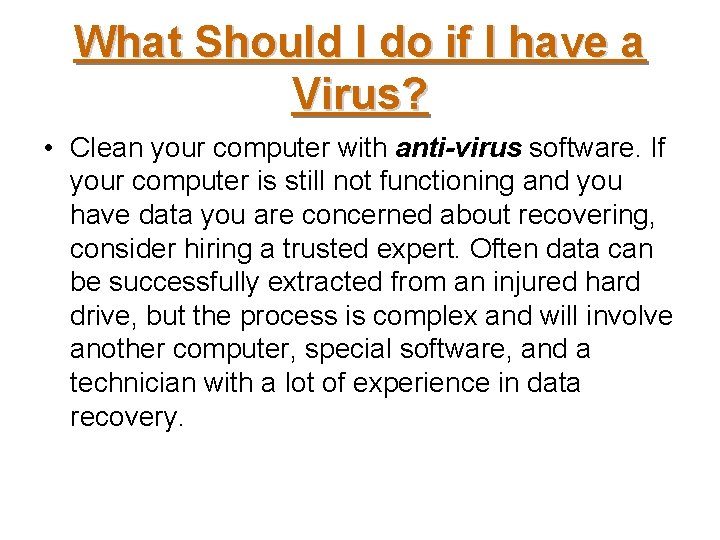
What Should I do if I have a Virus? • Clean your computer with anti-virus software. If your computer is still not functioning and you have data you are concerned about recovering, consider hiring a trusted expert. Often data can be successfully extracted from an injured hard drive, but the process is complex and will involve another computer, special software, and a technician with a lot of experience in data recovery.

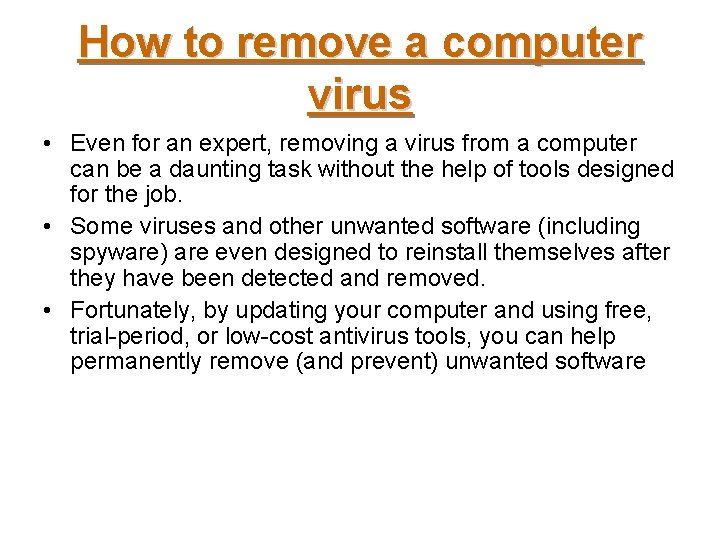
How to remove a computer virus • Even for an expert, removing a virus from a computer can be a daunting task without the help of tools designed for the job. • Some viruses and other unwanted software (including spyware) are even designed to reinstall themselves after they have been detected and removed. • Fortunately, by updating your computer and using free, trial-period, or low-cost antivirus tools, you can help permanently remove (and prevent) unwanted software

How to help prevent computer viruses • Nothing can guarantee the security of your computer 100 percent. • You can continue to improve your computer's security and decrease the possibility of infection by using a firewall, keeping your system up-todate, maintaining a current antivirus software subscription, and following a few best practices

How to help prevent computer viruses • Don’t automatically open email and email attachments. – Immediately delete emails from unknown sources. • Avoiding downloading files that you can’t be sure are safe. – Free games, screen savers, desktops, etc… • When in doubt, Err on the side of caution.

How to help prevent computer viruses – Anti Virus Software – – If you don’t have it, get it! ~Norton Anti. Virus ~Mc. Afee Virus Sheild ~Kaspersky Anti. Virus ~Avast ~Dr. Web – Keep your virus software updated! – Verify that it your virus software is working. http: //www. eicar. org/anti_virus_test_file. htm

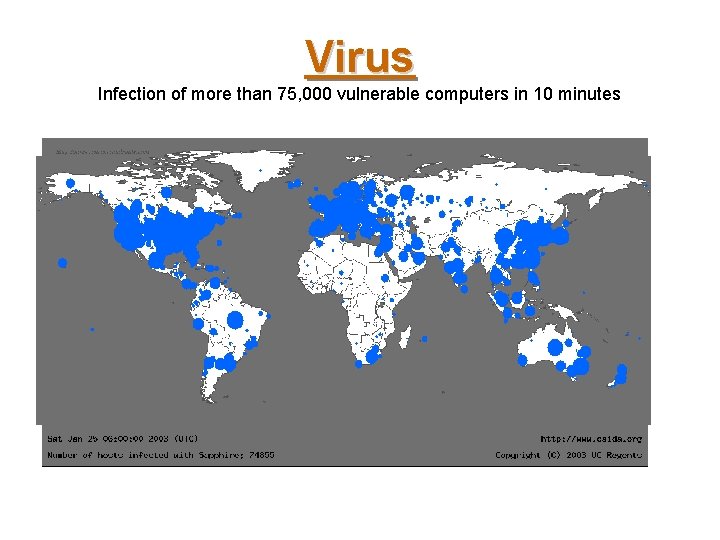
Virus Infection of more than 75, 000 vulnerable computers in 10 minutes

What is an Anti-Virus? • Anti-virus is a software (computer program) that scans files or your computer's memory for certain patterns that may indicate an infection. The patterns it looks for are based on the signatures, or fingerprints, of known viruses. Once a virus is detected in the wild, the Anti-Virus companies then release these new patterns for your Antivirus software to use. These updates come out daily by some vendors. Virus authors are continually releasing new and updated viruses, so it is important that you have the latest definitions installed on your computer.

What is an Anti-Virus? • Once you have installed an anti-virus package, you should scan your entire computer periodically. Always leave your Anti-virus software running so it can provide constant protection. • Automatic scans- Depending what software you choose, you may be able to configure it to automatically scan specific files or directories and prompt you at set intervals to perform complete scans. •

What is an Anti-Virus? • Manual scans- It is also a good idea to manually scan files you receive from an outside source before opening them. • This includes: • Saving and scanning email attachments or web downloads rather than selecting the option to open them directly from the source • Scanning floppy disks, CDs, or DVDs for viruses before opening any of the files

Types of Anti-virus product: • Depending on the installation method of the Anti-Virus these can be in the following forms: • On-Access scanners, • On-Demand scanners, • Hardware scanners.

Types of Anti-virus product: • On-access scanners check for viruses when files or floppy disks are "accessed". They are designed to run transparently in the background. When well implemented they should be invisible to the user - they shouldn’t even realize they are running an anti-virus product until it intercepts a virus. It has been our experience that on-access scanners are the most popular type of anti-virus product.

Types of Anti-virus product: • On-demand scanners only execute when the user tells them to execute. In other words they only scan for viruses when the user tells them, for example, to scan the floppy disk they have just inserted. The drawback with this method is that users have to remember to scan files and disks for viruses.

Types of Anti-virus product: • Hardware anti-virus products tend to be unpopular. The reason for this is that it is considerably harder to install a hardware card into many hundreds of PCs than it is to install computer software. Furthermore, difficulties may arise if the hardware antivirus needs to be updated to deal with new threats (macro viruses for example).

Global computer network

Creation of ARPANET • 1957 – USSR launched Sputnik I United States were shocked. . . They wanted to do something special.

Creation of ARPANET • 1957 – USSR launched Sputnik I United States were shocked • Advanced Research Projects Agency – Thechnological think-tank – Space, ballistic missiles and nuclear test monitoring – Communication between operational base and subcontracters

Creation of ARPANET • 1962 – computer research program – Leaded by John Licklider (MIT) – Leonard Kleinrock published his first paper on packet-switching theory • 1965 – first “wide area network” created


From ARPANET to Internet • 1972 – ARPANET went ‘public’ – First program for person-to-person communication (e-mail) • 1973 – 75% of all ARPANET traffic is e-mail – First international connection (University College of London)

From ARPANET to Internet • 1974 – TCP/IP – Each network should work on its own – Within each network there would be a ‘gateway’ – Packages would be routed through the fastest available route – Large mainframe computers – Several years of modification and redesign

From ARPANET to Internet • 1974/1982 – Networks launched – – – – – Telenet – first commercial version of ARPANET MFENet – researchers into Magnetic Fusion Energy HEPNet – researchers into High Energy Physics SPAN – space physicists Usenet – open system focusing on e-mail and newsgroups Bitnet – university scientists using IBM computers CSNet – Computer Scientists in universities, industry and government Eunet – European version of the Unix network EARN – European version of Bitnet

From ARPANET to Internet • 1974/1982 – Very chaotic – Different competing techniques and protocols – ARPANET is still the backbone • 1982 – The internet is born using the TCP/IP standard

From Internet to WWW • System expands – Advances in computer capacities and speeds – Introduction of glass-fibre cables • Problems created by its own success – More computers are linked (1984 – 1000 hosts) – Large volume of traffic (success of e-mail) • 1984 – Introduction DNS

From Internet to WWW • Use of internet throughout the higher educational system – British government – Joint Academic Network – US National Science Foundation – NSFNet • NSFNet – – – Use of TCP/IP Federal Agencies share cost of infrastructures NSFNet shared infrastructure Support behind the ‘Internet Activities Board’ NSFNet provided the ‘backbone’

From Internet to WWW • NSFNet – broke the capacity bottleneck – encouraged a surge in Internet use • • • 1984 – 1, 000 hosts 1986 – 5, 000 hosts 1987 – 28, 000 hosts 1989 – 100, 000 hosts 1990 – 300, 000 hosts – encouraged the development of private Internet providers • Commercial users

From Internet to WWW • 1990 – ARPANET was wound up • 1990 – first search-engine (Archie) • 1991 – NSF removed restrictions on private access • “Information superhighway” project

The World Wide Web • 1989 – WWW concept by Tim Berners-Lee • 1990 – first browser/editor program

The World Wide Web • National Center for Super. Computing Applications launched Mosaic X • Commercial websites began their proliferation • Followed by local shool/club/family sites • The web exploded – – 1994 – 3, 2 million hosts and 3, 000 websites 1995 – 6, 4 million hosts and 25, 000 websites 1997 – 19, 5 million hosts and 1, 2 million websites January 2001 – 110 million hosts and 30 million websites

The World Wide Web

The World Wide Web • Some facts – 1991 – Russia connected to the Internet – 1994 – Hotmail starts web based email – 1994 – World Wide Web Consortium (W 3 C) was founded – 1995 – JAVA source code was released – 1996 – Mirabilis (Israel) starts ICQ – 1998 – Google is founded

Information in the Internet • Electronic library service is used to search for scientific information and scientific publications, for example: • http: //elibrary. ru