C Rama Krishna Assistant Professor Dept of CSE



















- Slides: 80

C. Rama Krishna Assistant Professor Dept. of CSE NITTTR, Chandigarh Email: rkc_97 at yahoo. com National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Outline • History and Introduction • Brief overview to Physical Layer • Issues in Medium Access Control (MAC) • Issues in Routing and Transport Layers • Quality-of-Service Issues • Security Issues • Additional Resources National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

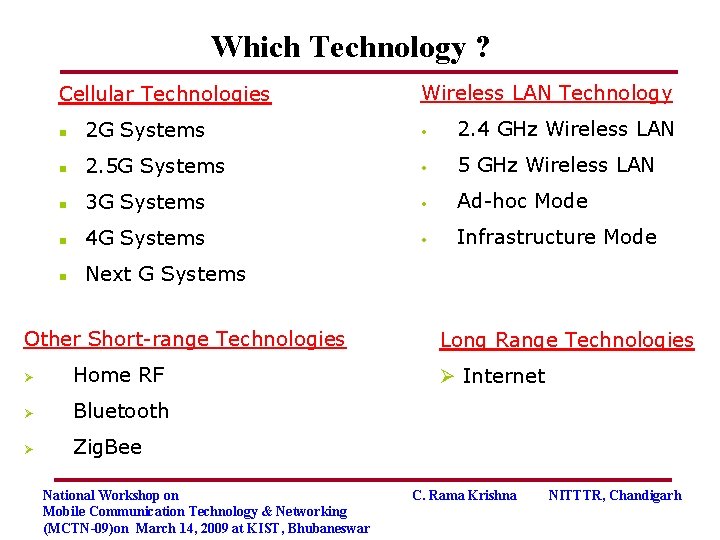
Which Technology ? Cellular Technologies Wireless LAN Technology n 2 G Systems • 2. 4 GHz Wireless LAN n 2. 5 G Systems • 5 GHz Wireless LAN n 3 G Systems • Ad-hoc Mode n 4 G Systems • Infrastructure Mode n Next G Systems Other Short-range Technologies Ø Home RF Ø Bluetooth Ø Zig. Bee National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar Long Range Technologies Ø Internet C. Rama Krishna NITTTR, Chandigarh

History and Introduction National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

History • Packet Radio NETwork (PRNET) by DARPA - late 1960 s • Military Communications • Disaster Management • Survivable Packet Radio Networks (SURAN) – 1980 s • MANET group formed under Internet Engineering Task Force (IETF) – 1990 s • IEEE released 802. 11 PHY and MAC standard – 1995 (later updated versions evolved) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

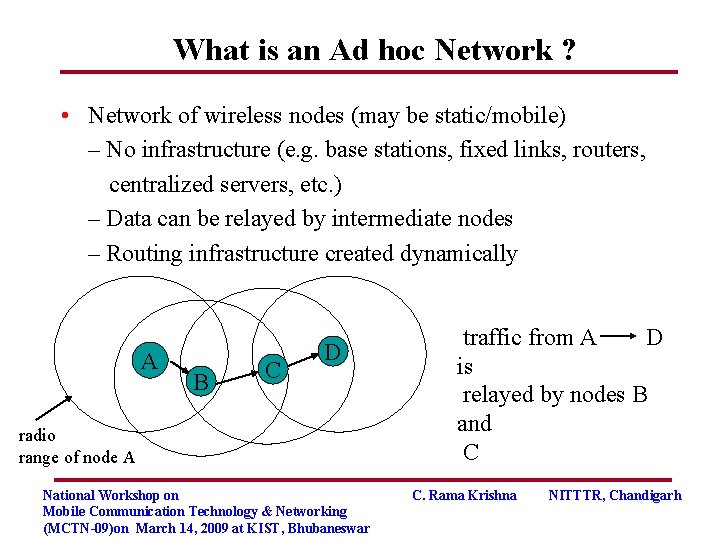
What is an Ad hoc Network ? • Network of wireless nodes (may be static/mobile) – No infrastructure (e. g. base stations, fixed links, routers, centralized servers, etc. ) – Data can be relayed by intermediate nodes – Routing infrastructure created dynamically A B C D radio range of node A National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar traffic from A D is relayed by nodes B and C C. Rama Krishna NITTTR, Chandigarh

Why an Ad hoc Network? • Does not depend on pre-existing infrastructure • Ease to deploy • Speed of deployment • Anytime-Anywhere-Any device-Anyone (A 4) network paradigm National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

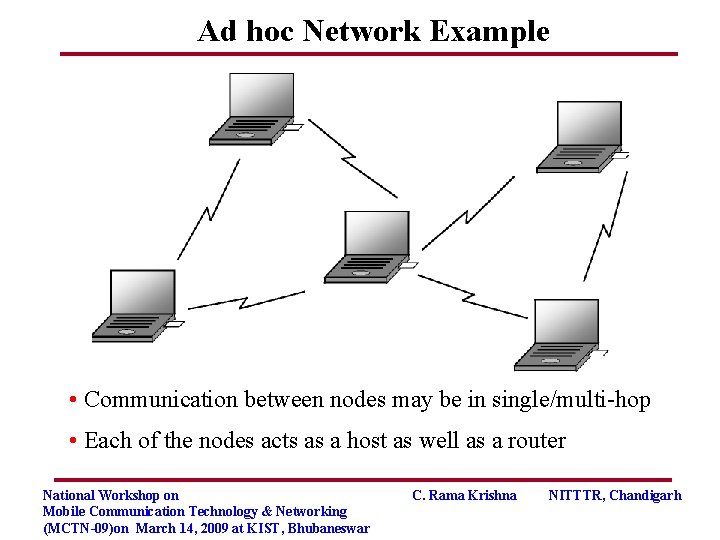
Ad hoc Network Example • Communication between nodes may be in single/multi-hop • Each of the nodes acts as a host as well as a router National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

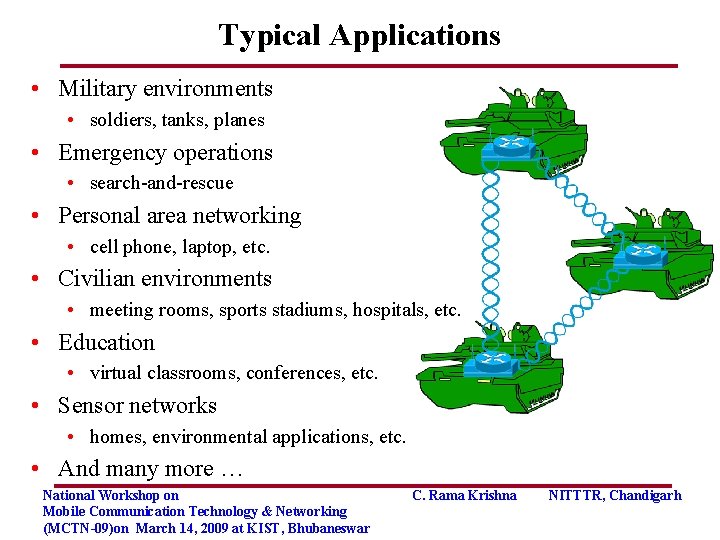
Typical Applications • Military environments • soldiers, tanks, planes • Emergency operations • search-and-rescue • Personal area networking • cell phone, laptop, etc. • Civilian environments • meeting rooms, sports stadiums, hospitals, etc. • Education • virtual classrooms, conferences, etc. • Sensor networks • homes, environmental applications, etc. • And many more … National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Some Challenges • Limited wireless transmission range • Broadcast nature of the wireless medium • hidden terminal and exposed terminal problems – MAC problem • Packet losses due to: transmission errors and mobility • Mobility-induced route changes – routing problem • Battery constraints • Ease of snooping - security problem National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Physical Layer National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

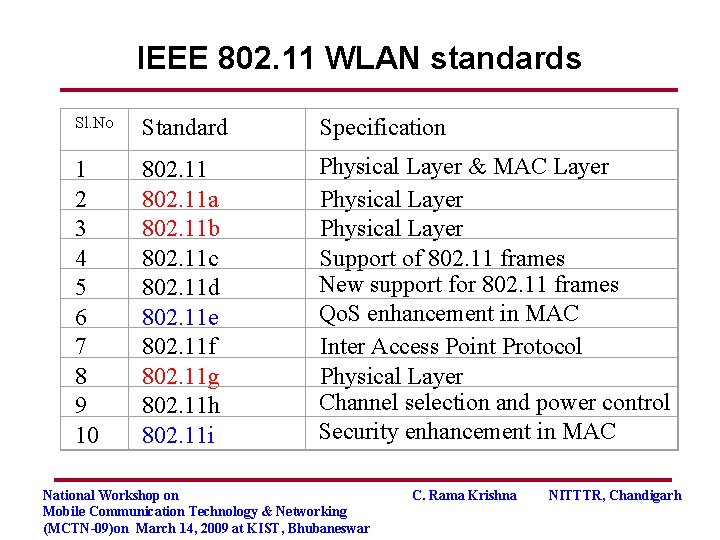
IEEE 802. 11 WLAN standards Sl. No Standard Specification 1 2 3 4 5 6 7 8 9 10 802. 11 a 802. 11 b 802. 11 c 802. 11 d 802. 11 e 802. 11 f 802. 11 g 802. 11 h 802. 11 i Physical Layer & MAC Layer Physical Layer Support of 802. 11 frames New support for 802. 11 frames Qo. S enhancement in MAC Inter Access Point Protocol Physical Layer Channel selection and power control Security enhancement in MAC National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

IEEE 802. 11 standard • Supports networking in two modes: • Infrastructure based WLAN using access points (APs) • Infrastructure-less ad hoc networks – widely used in simulation studies and testbeds of MANET National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

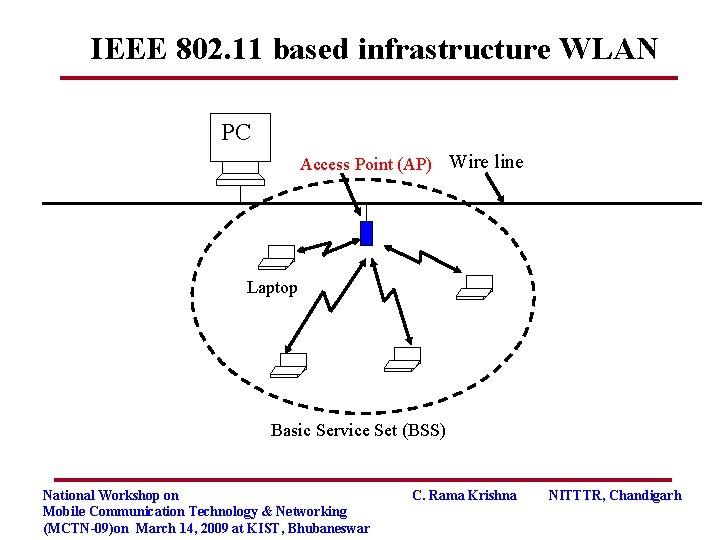
IEEE 802. 11 based infrastructure WLAN PC Access Point (AP) Wire line Laptop Basic Service Set (BSS) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

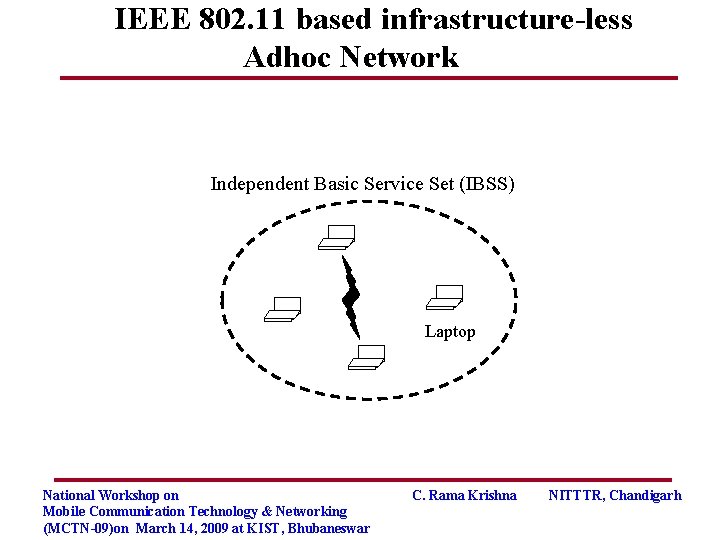
IEEE 802. 11 based infrastructure-less Adhoc Network Independent Basic Service Set (IBSS) Laptop National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

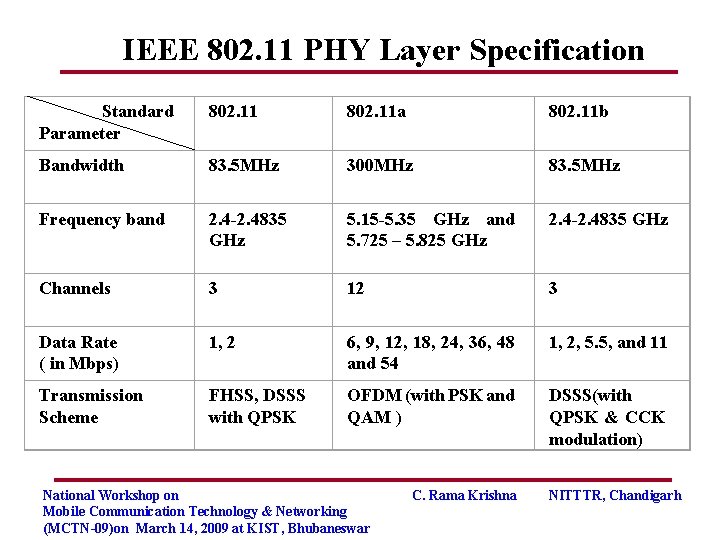
IEEE 802. 11 PHY Layer Specification Standard Parameter 802. 11 a 802. 11 b Bandwidth 83. 5 MHz 300 MHz 83. 5 MHz Frequency band 2. 4 -2. 4835 GHz 5. 15 -5. 35 GHz and 5. 725 – 5. 825 GHz 2. 4 -2. 4835 GHz Channels 3 12 3 Data Rate ( in Mbps) 1, 2 6, 9, 12, 18, 24, 36, 48 and 54 1, 2, 5. 5, and 11 Transmission Scheme FHSS, DSSS with QPSK OFDM (with PSK and QAM ) DSSS(with QPSK & CCK modulation) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Physical Layer for high speed MANET • Present PHY Layer • IEEE 802. 11, 11 a, 802. 11 b and 802. 11 g • Supports 1/ 2 /11/ 22/ 54 Mbps data rate in static indoor environment • DSSS is not suitable for data rate more than 10 Mbps • OFDM based PHY layer design for high data rate transmission up to 54 Mbps [ 802. 11 a & g] National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Medium Access Control (MAC) & Issues National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Need for a MAC Protocol • Wireless channel is a shared medium and bandwidth is a scarce resource • Need access control mechanism to avoid collision(s) • To maximize probability of successful transmissions by resolving contention among users • To avoid problems due to hidden and exposed nodes • To maintain fairness amongst all users • MAC protocol design has been an active area of research in recent years National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

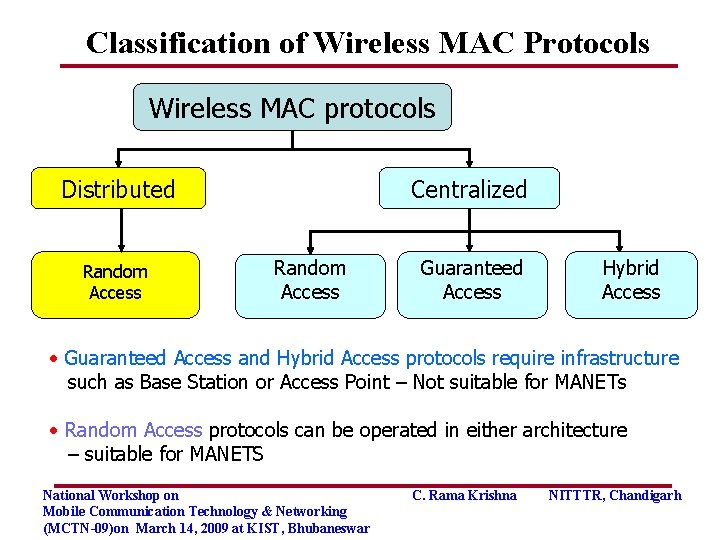
Classification of Wireless MAC Protocols Wireless MAC protocols Distributed Random Access Centralized Random Access Guaranteed Access Hybrid Access • Guaranteed Access and Hybrid Access protocols require infrastructure such as Base Station or Access Point – Not suitable for MANETs • Random Access protocols can be operated in either architecture – suitable for MANETS National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Distributed Random Access Protocols National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

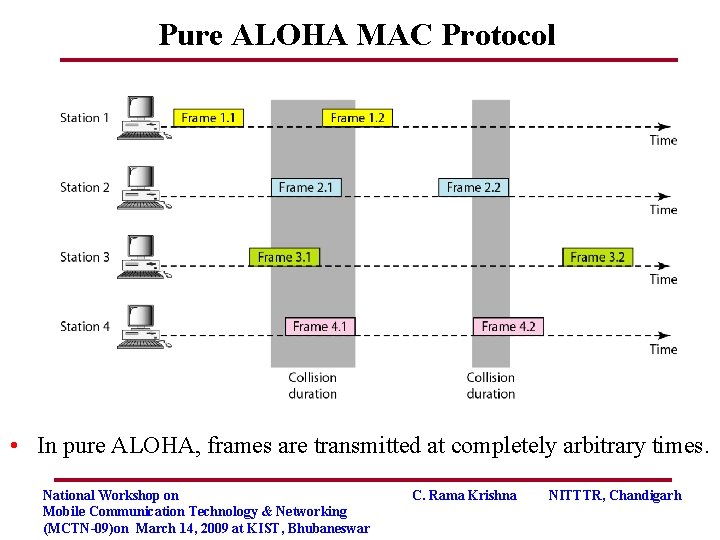
Pure ALOHA MAC Protocol • In pure ALOHA, frames are transmitted at completely arbitrary times. National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

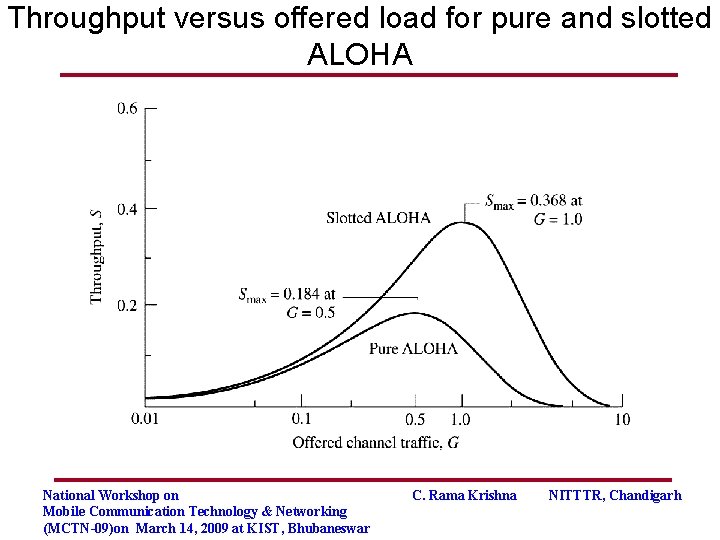
The throughput for pure ALOHA is S = G × e − 2 G The maximum throughput Smax = 0. 184 , when G = 0. 5 National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

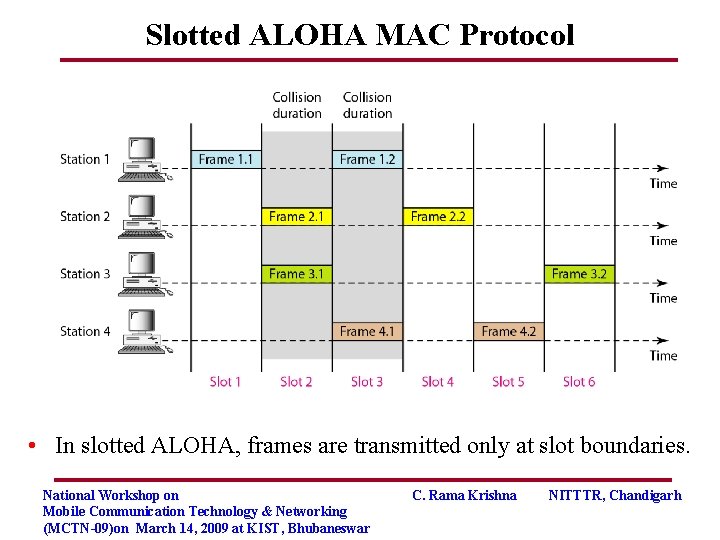
Slotted ALOHA MAC Protocol • In slotted ALOHA, frames are transmitted only at slot boundaries. National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

The throughput for slotted ALOHA is S = G × e−G The maximum throughput Smax = 0. 368, when G = 1 National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Throughput versus offered load for pure and slotted ALOHA National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Carrier Sense Multiple Access (CSMA) Protocol • Max. throughput achievable by pure ALOHA is 0. 184 and slotted ALOHA is 0. 368 • CSMA gives improved throughput compared to ALOHA protocols • Listens to the channel before transmitting a packet (reduces collisions) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

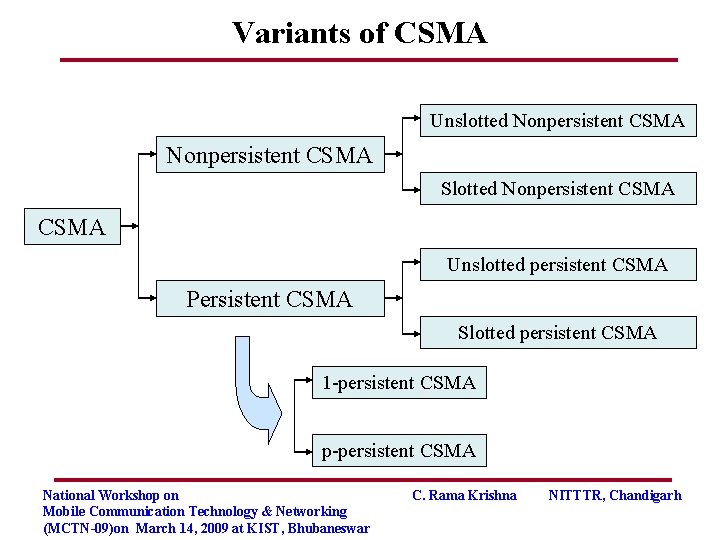
Variants of CSMA Unslotted Nonpersistent CSMA Slotted Nonpersistent CSMA Unslotted persistent CSMA Persistent CSMA Slotted persistent CSMA 1 -persistent CSMA p-persistent CSMA National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

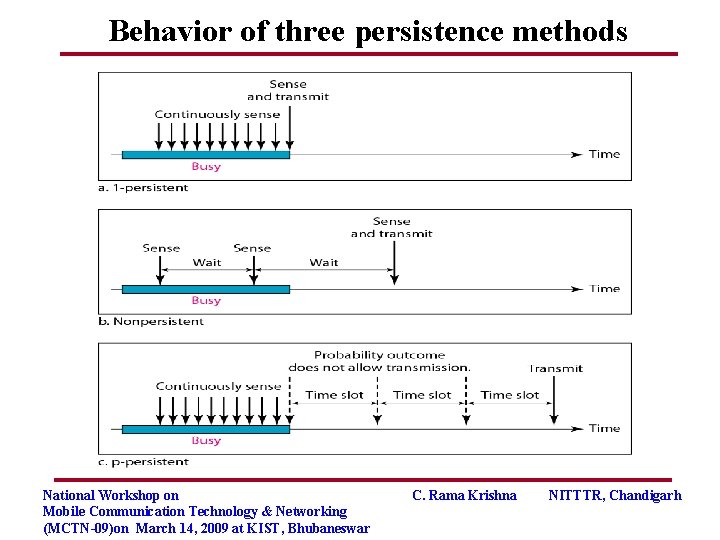
Behavior of three persistence methods National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

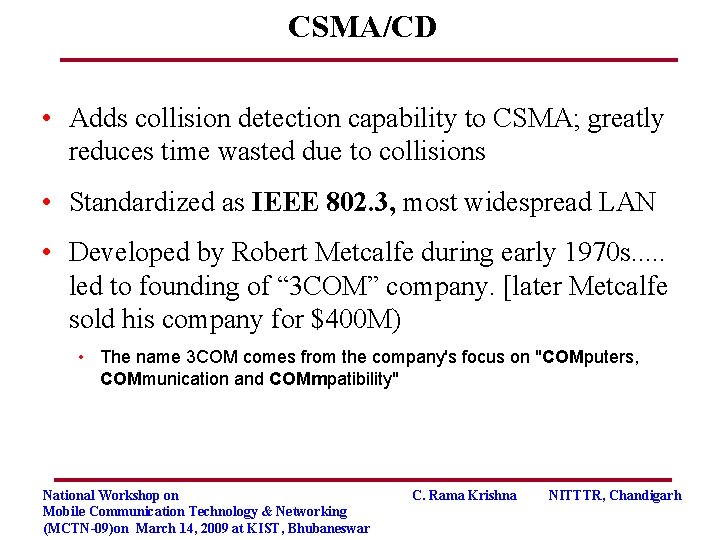
CSMA/CD • Adds collision detection capability to CSMA; greatly reduces time wasted due to collisions • Standardized as IEEE 802. 3, most widespread LAN • Developed by Robert Metcalfe during early 1970 s. . . led to founding of “ 3 COM” company. [later Metcalfe sold his company for $400 M) • The name 3 COM comes from the company's focus on "COMputers, COMmunication and COMmpatibility" National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Why can’t we use CSMA or CSMA/CD in a Wireless LAN or Adhoc Network? National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

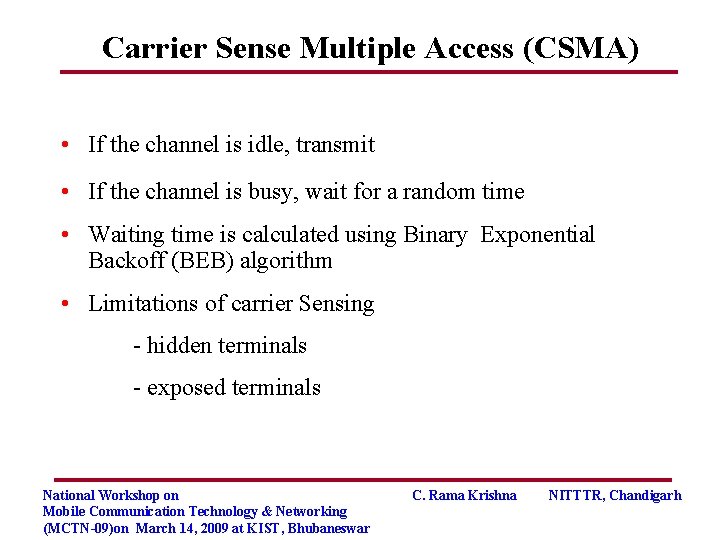
Carrier Sense Multiple Access (CSMA) • If the channel is idle, transmit • If the channel is busy, wait for a random time • Waiting time is calculated using Binary Exponential Backoff (BEB) algorithm • Limitations of carrier Sensing - hidden terminals - exposed terminals National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

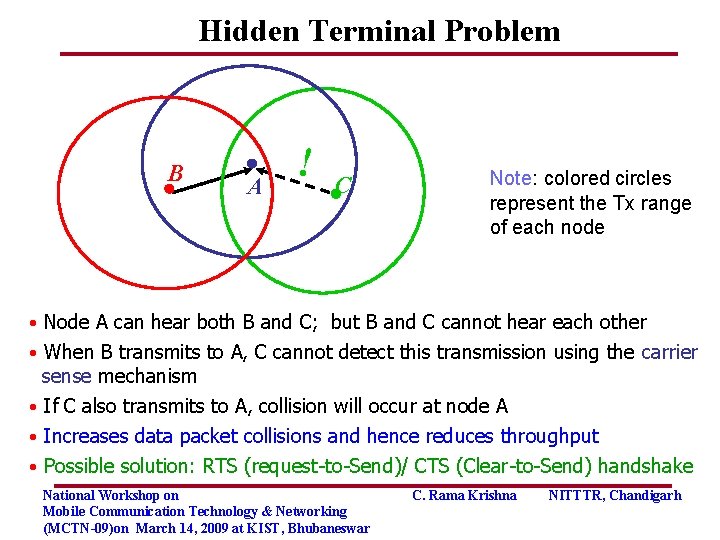
Hidden Terminal Problem B A ! C Note: colored circles represent the Tx range of each node • Node A can hear both B and C; but B and C cannot hear each other • When B transmits to A, C cannot detect this transmission using the carrier sense mechanism • If C also transmits to A, collision will occur at node A • Increases data packet collisions and hence reduces throughput • Possible solution: RTS (request-to-Send)/ CTS (Clear-to-Send) handshake National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

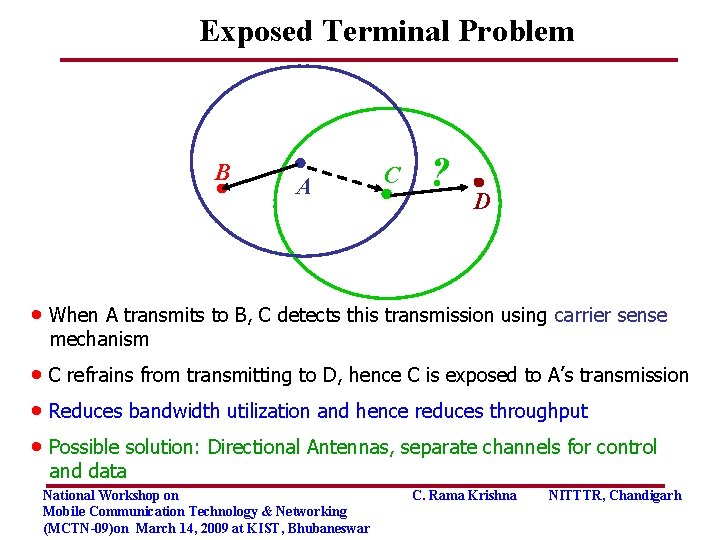
Exposed Terminal Problem B A C ? D • When A transmits to B, C detects this transmission using carrier sense mechanism • C refrains from transmitting to D, hence C is exposed to A’s transmission • Reduces bandwidth utilization and hence reduces throughput • Possible solution: Directional Antennas, separate channels for control and data National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

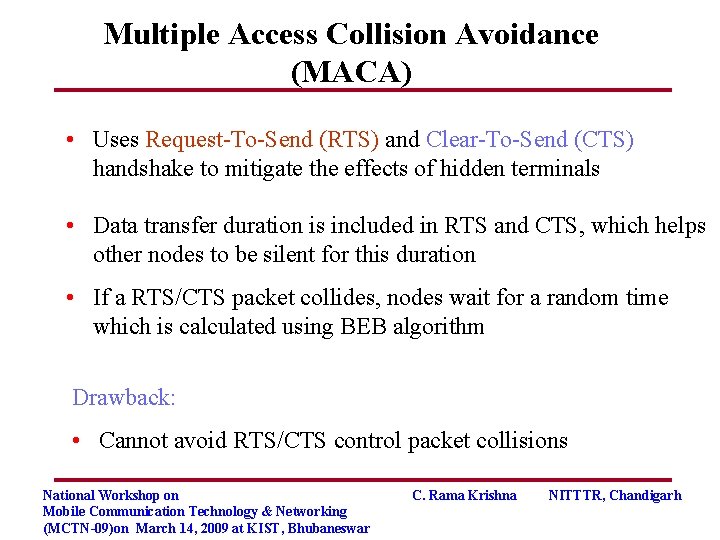
Multiple Access Collision Avoidance (MACA) • Uses Request-To-Send (RTS) and Clear-To-Send (CTS) handshake to mitigate the effects of hidden terminals • Data transfer duration is included in RTS and CTS, which helps other nodes to be silent for this duration • If a RTS/CTS packet collides, nodes wait for a random time which is calculated using BEB algorithm Drawback: • Cannot avoid RTS/CTS control packet collisions National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

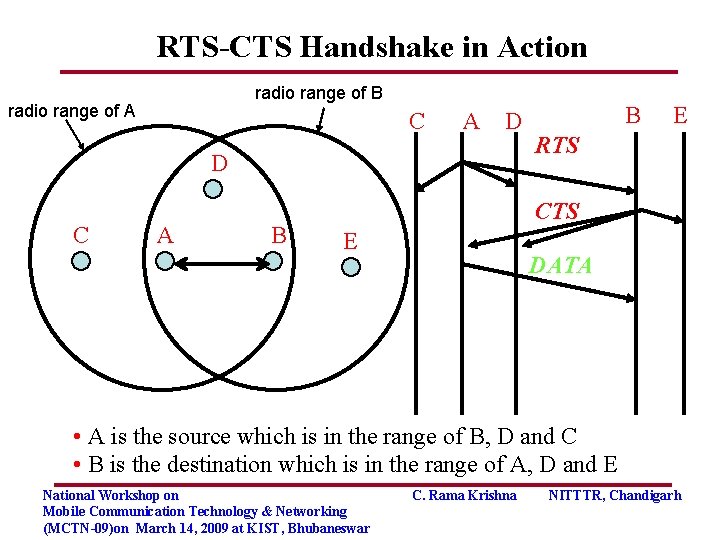
RTS-CTS Handshake in Action radio range of B radio range of A C A D D C A B B E RTS CTS E DATA • A is the source which is in the range of B, D and C • B is the destination which is in the range of A, D and E National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

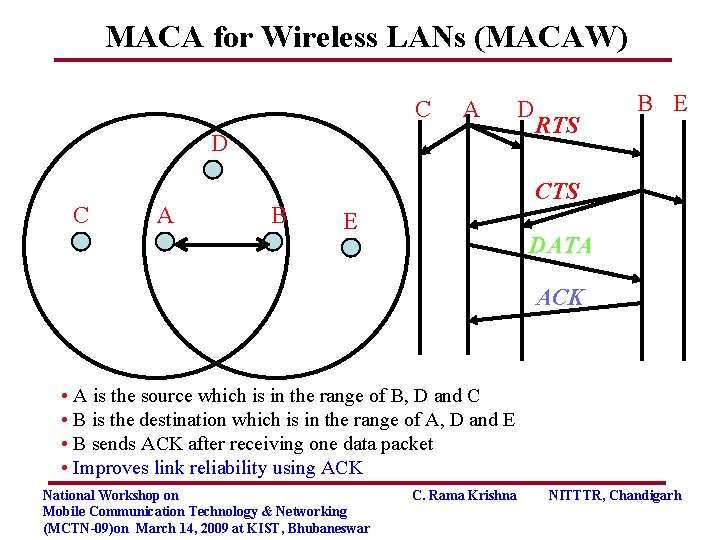
MACA for Wireless LANs (MACAW) C A D C A B D RTS B E CTS E DATA ACK • A is the source which is in the range of B, D and C • B is the destination which is in the range of A, D and E • B sends ACK after receiving one data packet • Improves link reliability using ACK National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

IEEE 802. 11 MAC Protocol • Has provision for two modes - Point Coordination Function (PCF) - Distributed Coordination Function (DCF) • Point Coordination Function - Provides contention-free access - Requires Access Point (AP) for coordination - Not suitable for a MANET National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

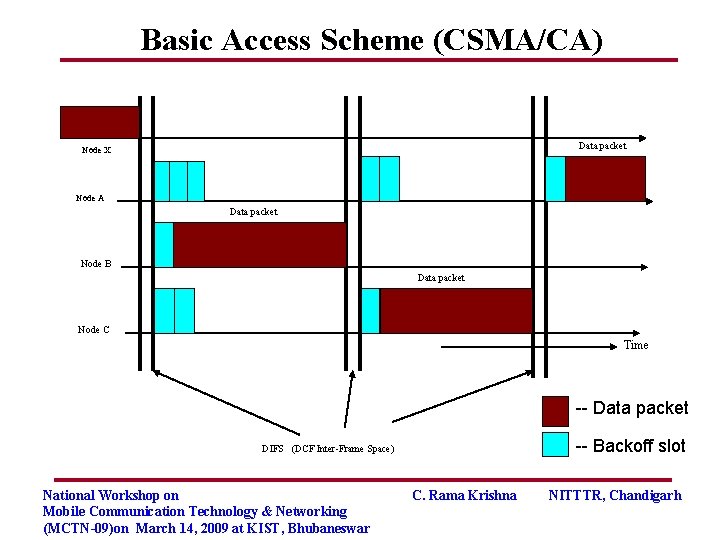
Distributed Coordination Function (DCF) Two schemes: • Basic access scheme (CSMA/CA) • CSMA/CA with RTS (Request-to-Send)/CTS (Clear-to. Send) handshake (optional) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Basic Access Scheme (CSMA/CA) Data packet Node X Node A Data packet Node B Data packet Node C Time -- Data packet -- Backoff slot DIFS (DCF Inter-Frame Space) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

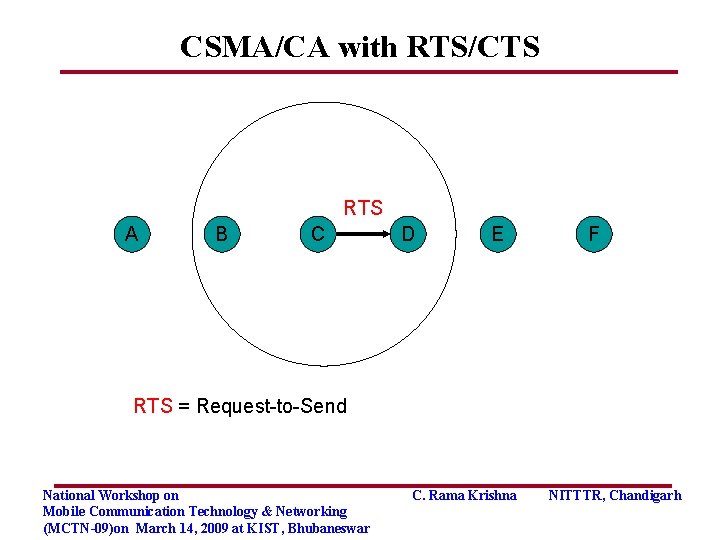
CSMA/CA with RTS/CTS RTS A B C D E F RTS = Request-to-Send National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

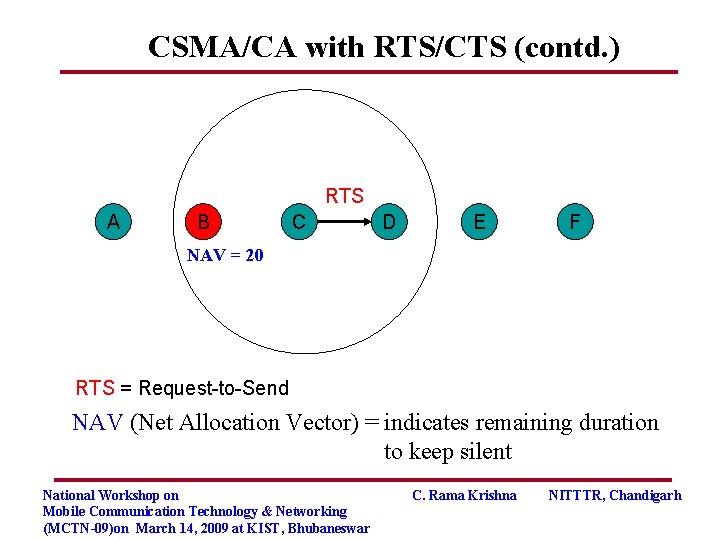
CSMA/CA with RTS/CTS (contd. ) RTS A B C D E F NAV = 20 RTS = Request-to-Send NAV (Net Allocation Vector) = indicates remaining duration to keep silent National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

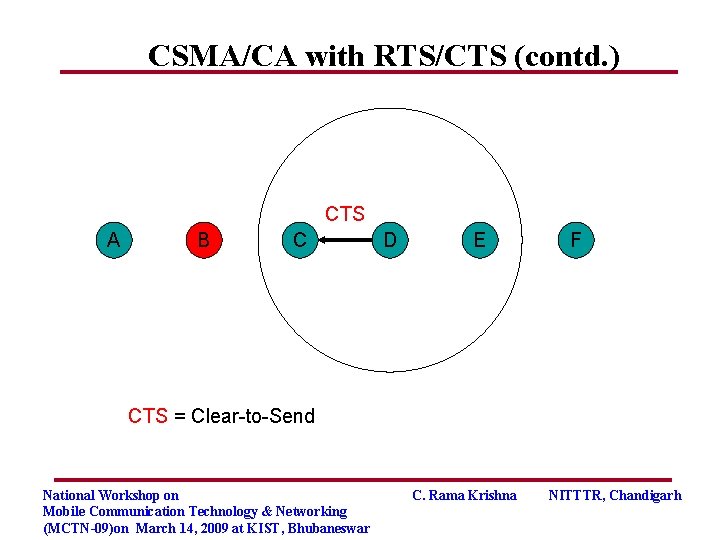
CSMA/CA with RTS/CTS (contd. ) CTS A B C D E F CTS = Clear-to-Send National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

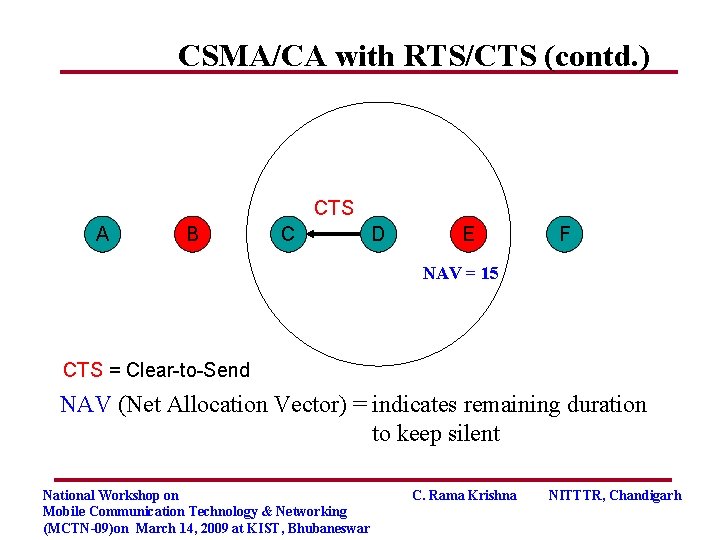
CSMA/CA with RTS/CTS (contd. ) CTS A B C D E F NAV = 15 CTS = Clear-to-Send NAV (Net Allocation Vector) = indicates remaining duration to keep silent National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

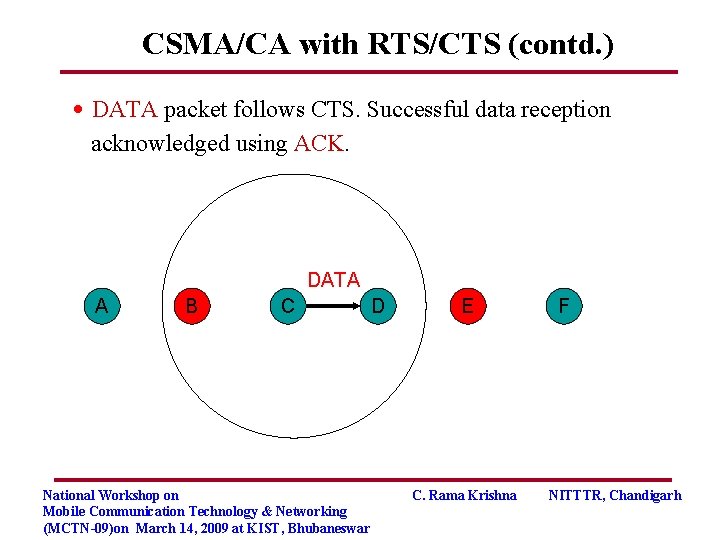
CSMA/CA with RTS/CTS (contd. ) • DATA packet follows CTS. Successful data reception acknowledged using ACK. DATA A B C National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar D E C. Rama Krishna F NITTTR, Chandigarh

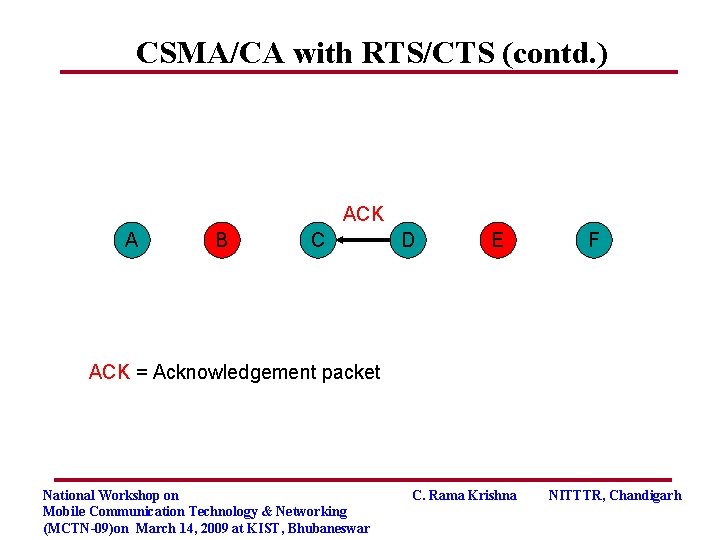
CSMA/CA with RTS/CTS (contd. ) ACK A B C D E F ACK = Acknowledgement packet National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

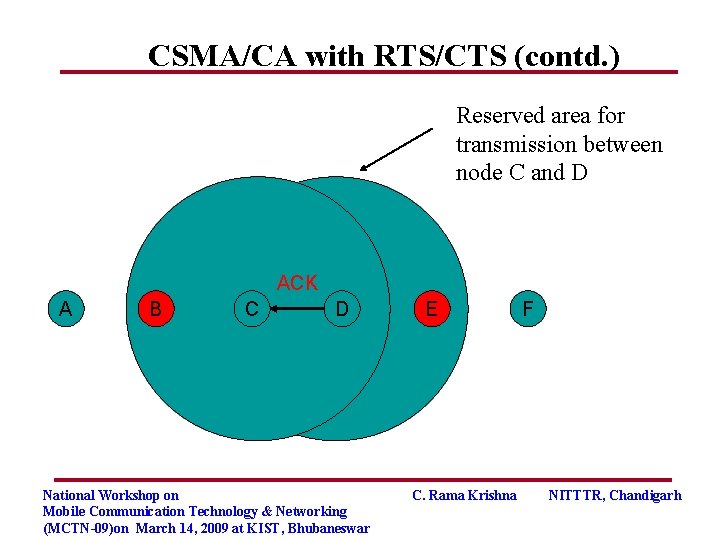
CSMA/CA with RTS/CTS (contd. ) Reserved area for transmission between node C and D ACK A B C D National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar E C. Rama Krishna F NITTTR, Chandigarh

Limitations of IEEE 802. 11 DCF MAC • Performance of Basic Access Method (CSMA/CA) degrades due to hidden and exposed node problems • CSMA/CA with RTS/CTS – consumes additional bandwidth for control packets transmission • may introduce significant delay in data packet transmission if RTS/CTS control packets experience frequent collisions and retransmissions (possible in case of high node concentration) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

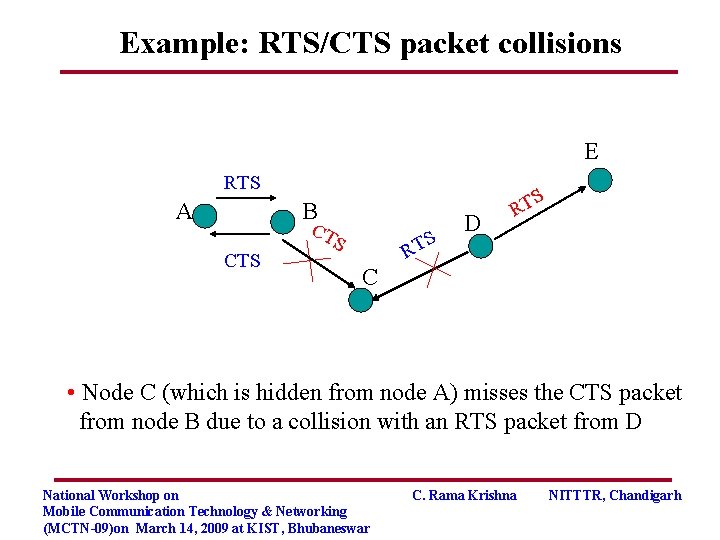
Example: RTS/CTS packet collisions E RTS A S B CT CTS S S RT D RT C • Node C (which is hidden from node A) misses the CTS packet from node B due to a collision with an RTS packet from D National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Multi-Channel MAC • Divides bandwidth into multiple channels using frequency division or by using orthogonal CDMA codes • Selects any one of the idle channels Advantages: • Improves throughput performance in the network by distributing traffic over time as well as over bandwidth Disadvantages: • Increases hardware complexity National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

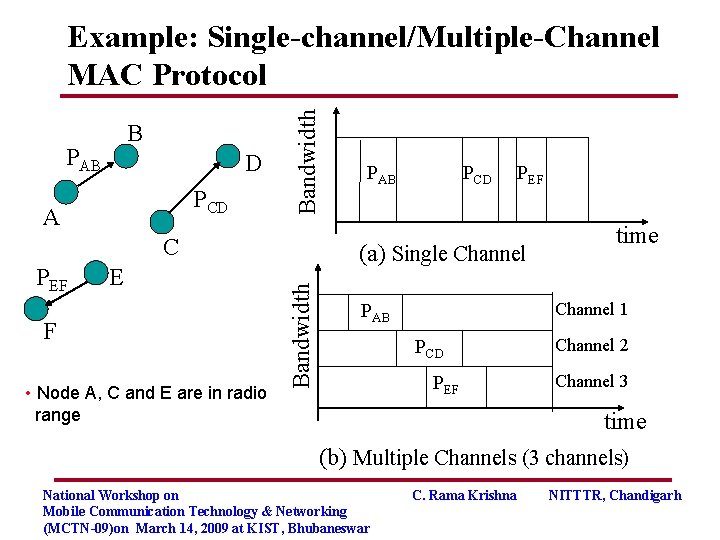
B PAB D PCD A Bandwidth Example: Single-channel/Multiple-Channel MAC Protocol C E F • Node A, C and E are in radio range PCD PEF (a) Single Channel Bandwidth PEF PAB time Channel 1 PAB PCD PEF Channel 2 Channel 3 time (b) Multiple Channels (3 channels) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

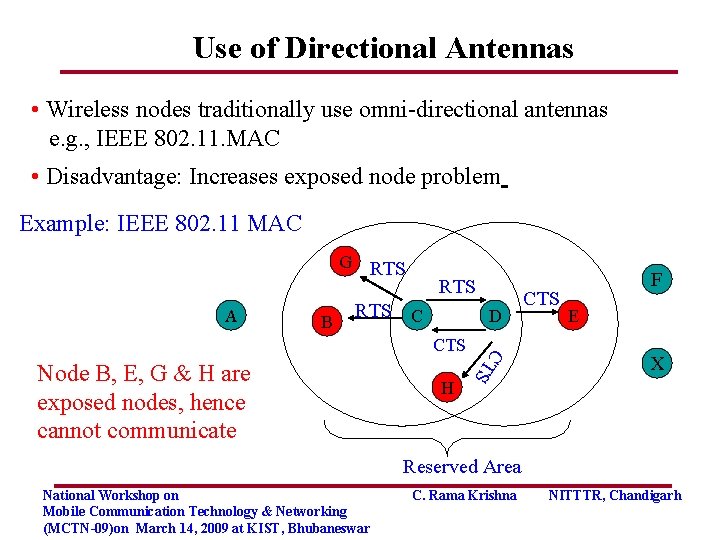
Use of Directional Antennas • Wireless nodes traditionally use omni-directional antennas e. g. , IEEE 802. 11. MAC • Disadvantage: Increases exposed node problem Example: IEEE 802. 11 MAC G A B RTS RTS C D Node B, E, G & H are exposed nodes, hence cannot communicate H C T S CTS F E X Reserved Area National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

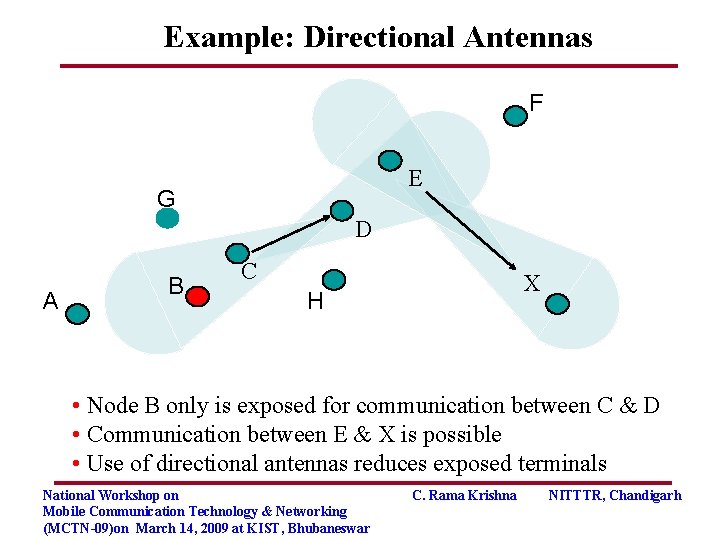
Example: Directional Antennas F E G D A B C X H • Node B only is exposed for communication between C & D • Communication between E & X is possible • Use of directional antennas reduces exposed terminals National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Directional Antennas: Advantages & Disadvantages • Reduces interference to neighboring nodes - helps in frequency reuse - increases packet success probability (or reduces number of collisions) • Higher gain due to their directivity - allows transmitters to operate at a smaller transmission power and still maintain adequate signal-to-interference-plus-noise ratio (SINR) - reduces average power consumption in the nodes • Requires a mechanism to determine direction for transmission and reception National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

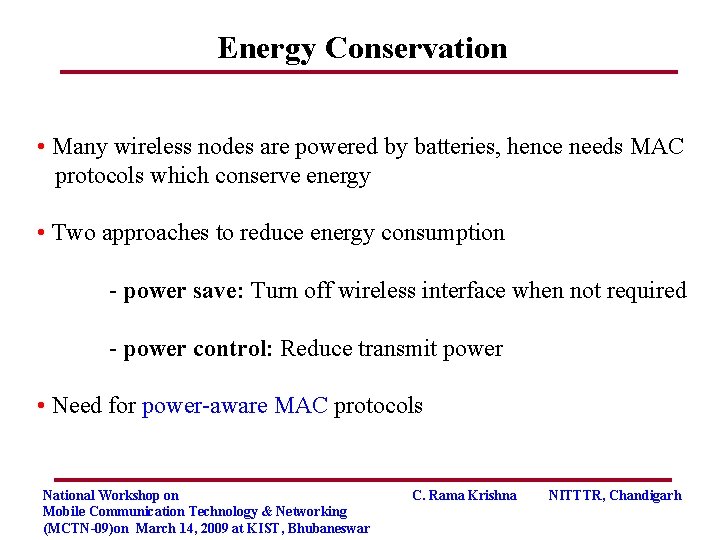
Energy Conservation • Many wireless nodes are powered by batteries, hence needs MAC protocols which conserve energy • Two approaches to reduce energy consumption - power save: Turn off wireless interface when not required - power control: Reduce transmit power • Need for power-aware MAC protocols National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

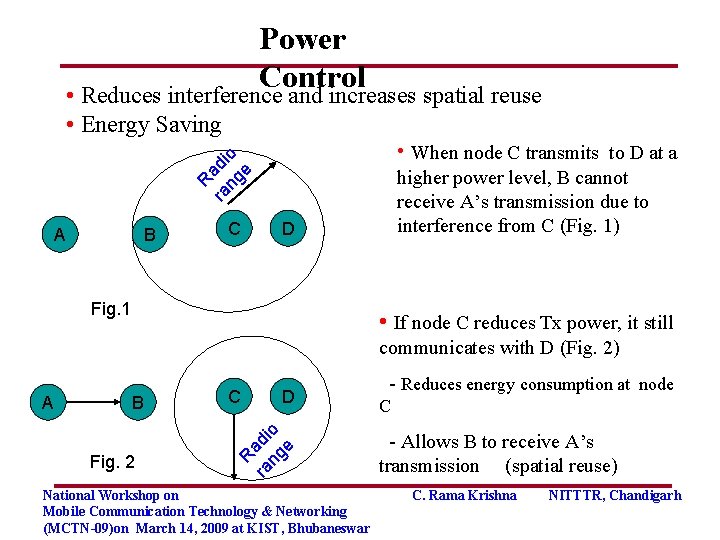
Power Control • Reduces interference and increases spatial reuse • Energy Saving R ra adi ng o e • When node C transmits to D at a A B C higher power level, B cannot receive A’s transmission due to interference from C (Fig. 1) D Fig. 1 • If node C reduces Tx power, it still communicates with D (Fig. 2) B Fig. 2 D R ra adi ng o e A C National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar - Reduces energy consumption at node C - Allows B to receive A’s transmission (spatial reuse) C. Rama Krishna NITTTR, Chandigarh

Routing Protocols National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Importance of Routing in MANET • Host mobility • link failure due to mobility of nodes • Rate of link failure may be high when nodes move fast • Some desirable features of routing protocols • • Minimum route discovery and maintenance time Minimum routing overhead Stable and optimum route despite mobility Shortest route, etc. National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

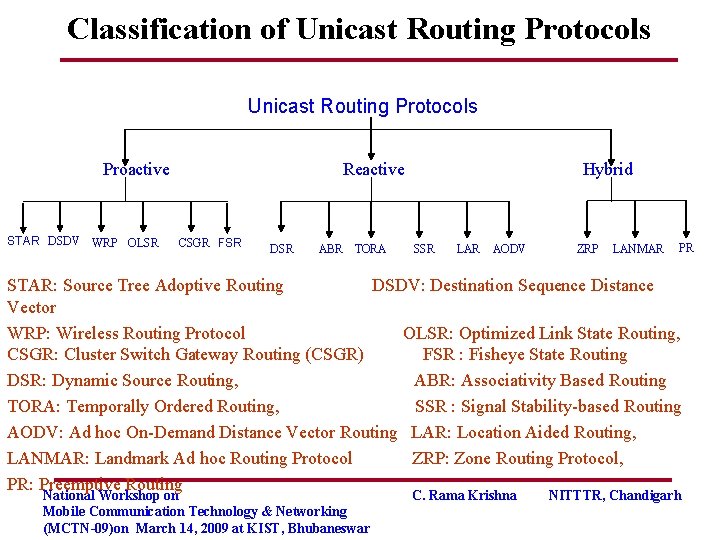
Classification of Unicast Routing Protocols Proactive STAR DSDV WRP OLSR Reactive CSGR FSR DSR ABR TORA Hybrid SSR LAR AODV ZRP LANMAR PR STAR: Source Tree Adoptive Routing DSDV: Destination Sequence Distance Vector WRP: Wireless Routing Protocol OLSR: Optimized Link State Routing, CSGR: Cluster Switch Gateway Routing (CSGR) FSR : Fisheye State Routing DSR: Dynamic Source Routing, ABR: Associativity Based Routing TORA: Temporally Ordered Routing, SSR : Signal Stability-based Routing AODV: Ad hoc On-Demand Distance Vector Routing LAR: Location Aided Routing, LANMAR: Landmark Ad hoc Routing Protocol ZRP: Zone Routing Protocol, PR: Preemptive Routing National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Proactive Routing Protocols National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Characteristics of Proactive Routing Protocols • Distributed, shortest-path protocols • Maintain routes between every host pair at all times • Based on Periodic updates of routing table • High routing overhead and consumes more bandwidth • Example: Destination Sequence Distance Vector (DSDV) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Reactive Routing Protocols National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Characteristics of Reactive Routing Protocols • Reactive protocols • Determine route if and when needed • Less control packet overhead • Source initiates route discovery process • More route discovery delay • Example: Ad hoc On-Demand Distance Vector Routing (AODV) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Proactive and Reactive Protocol Trade. Off • Latency of route discovery • Proactive protocols may have lower latency since routes are maintained at all times • Reactive protocols may have higher latency because a route from X to Y will be found only when X attempts to send a packet to Y • Overhead of route discovery and maintenance • Reactive protocols may have lower overhead since routes are determined only if needed • Proactive protocols may result in higher overhead due to continuous route updating • Which approach achieves a better trade-off depends on the traffic and mobility patterns National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Transmission Control Protocol (TCP) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Transmission Control Protocol (TCP) • Reliable ordered delivery • Implements congestion avoidance and control • Reliability achieved by means of retransmissions if necessary • End-to-end semantics • Acknowledgements (ACKs) sent to TCP sender confirm delivery of data received by TCP receiver • ACK for data sent only after data has reached the destination National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

TCP in MANET Several factors affect TCP performance in a MANET: • Wireless transmission errors – may cause fast retransmit, which results in • retransmission of a lost packet • reduction in congestion window size – reducing congestion window in response to errors is unnecessary • Route failures due to mobility National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Impact of Transmission Errors on TCP • TCP cannot distinguish between packet losses due to congestion and mobility induced transmission errors • Unnecessarily reduces congestion window size • Throughput suffers National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Qo. S Issues National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Quality-of-Service (QOS) • Guarantee by the network to satisfy a set of pre-determined service performance constraints for the user: - end-to-end delay - throughput - probability of packet loss - delay jitter (variance) • Enough network resources must be available during service invocation to honor the guarantee • Power consumption and service coverage area- other Qo. S attributes specific to MANET • Qo. S support in MANETs encompasses issues at physical layer, MAC layer, network, transport and application layers National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Qo. S support in MANETs: Issues • Unpredictable link properties • Node mobility • Limited battery life • Hidden and exposed node problem • Route maintenance • Security National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Security Issues National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Security Issues in Mobile Ad Hoc Networks • Wireless medium is easy to snoop • Due to ad hoc connectivity and mobility, it is hard to guarantee access to any particular node • Easier for trouble-makers to insert themselves into a mobile ad hoc network (as compared to a wired network) National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Open Issues in Mobile Ad Hoc Networking National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

Open Problems • Better PHY layer required to support high speed services • Efficient MAC protocols to support mobility, Qo. S, energy conservation, etc. • Efficient routing protocols with scalability, Qo. S and security, etc. • Security issues at other layers • Interoperation with Internet • Many more … National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

References • C. E. Perkins, Ad Hoc Networking, Addison-Wesley, 2002 • E. Royer and C. K. Toh, “A Review of Current Routing Protocols for Ad hoc Mobile Wireless Networks, ” IEEE Personal Communications Magazine, Vol. 6, Issue 2, pp. 46 -55, 1999. • C. E. Perkins, E. M. Royer, and Samir Das, “Ad hoc On-Demand Distance Vector Routing, ” http: //www. ietf. org/internet-drafts/draft-ietfmanet-aodv-13. txt, (work in progress), February 2003. • L. Bajaj et al. , “Glo. Mo. Sim: A Scalable Network Simulation Environment, ” CSD Technical Report, #990027, UCLA, 1997. • IEEE Standards Department, Wireless LAN Medium Access Control (MAC) and PHYsical layer (PHY) specifications, IEEE standard 802. 111997, 1997. National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

References (contd. ) • B. P. Crow et al. , “IEEE 802. 11 Wireless Local Area Networks, ” IEEE Communications Magazine, Vol. 35, Issue 9, pp. 116 -126, September 1997. • C-K. Toh, Ad Hoc Mobile Wireless Networks: Protocols and Systems, Prentice-Hall, 2002. • Yiyan Wu and Willium. Y. Zou, “Orthogonal Frequency Division Multiplexing, ” IEEE Trans. Consumer electronics, vol. 41, no. 3, pp. 392399, Aug. 1995. • R. V. Nee and Ramjee Prasad, OFDM for Wireless Multimedia Communications, Artech House, Boston, London, 2000. • A. Chandra, V. Gummalla, J. O. Limb, “Wireless Medium Access Control Protocols, ” IEEE Communications Survey, pp. 2 -15, Second Quarter 2000. National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

References (contd. ) • Y. B. Ko, V. Shankarkumar, and N. H. Vaidya, “Medium Access Control Protocols using Directional Antennas in Ad hoc Networks, ” In Proceedings of IEEE INFOCOM’ 2000, Mar. 2000. • G. Gaertner, V. Cahill, “Understanding Link Quality in 802. 11 Mobile Ad hoc Networks, ” IEEE Internet computing, pp. 55 -60, Jan. -Feb. 2004. • X. Shugong, T. Saadawi, “Does the IEEE MAC protocol work well in multi-hop wireless ad hoc networks? ” IEEE Comm. magazine, pp. 130 -137, June 2001. • M. Tubaishat, S. Madria, ”Sensor networks: an overview, ” IEEE potentials, pp. 20 -23, April-May-2003. National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

References (contd. ) • Prasant Mohapatra, J. Li, Chao Gui, ” Qo. S in Mobile Ad hoc Networks, ” IEEE Wireless Communication, pp. 44 -52, June-2003. • N, Choi, Y. Seok, Y. Choi, “Multi-channel MAC for Mobile Ad hoc Networks, ” Proc. VTC’ 03, pp. 1379 -1383, Oct. 2003. • C. Rama Krishna, S. Chakrabarti, and D. Datta, “A Modified Backoff Algorithm for IEEE 802. 11 DCF-based MAC Protocol in a Mobile Ad hoc Network, ” Proc. of the International Conference IEEE TENCON 2004, Chiang Mai, Thailand, 21 -24 November 2004. • V. Bhargavan et al. , “MACAW: A New Media Access Protocol for Wireless LANs, ” Proc. of ACM SIGCOMM, pp. 212 -225, 1994. • P. Karn, “MACA – A New Channel Access Method for Packet Radio, ” in ARRL/CRRL Amateur Radio 9 th Computer Networking Conference, pp. 134 -140, 1990 National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh

National Workshop on Mobile Communication Technology & Networking (MCTN-09)on March 14, 2009 at KIST, Bhubaneswar C. Rama Krishna NITTTR, Chandigarh
 Crishnal
Crishnal Proses tumbesaran rama-rama
Proses tumbesaran rama-rama Sri rama sri rama sri manoharama
Sri rama sri rama sri manoharama Promotion from assistant to associate professor
Promotion from assistant to associate professor Cuhk assistant professor salary
Cuhk assistant professor salary Krishna avanti lunch menu
Krishna avanti lunch menu Krishna sigdel
Krishna sigdel Krishna education centre
Krishna education centre Krisna hallada
Krisna hallada Sri krsna caitanya prabhu nityananda
Sri krsna caitanya prabhu nityananda Hare krishna sekta
Hare krishna sekta Shree krishna chaitanya prabhu nityananda
Shree krishna chaitanya prabhu nityananda Jaya jaya radha krishna yugala milana lyrics
Jaya jaya radha krishna yugala milana lyrics Sai krishna kamepalli
Sai krishna kamepalli Sri krishna caitanya prabhu nityananda
Sri krishna caitanya prabhu nityananda Suresh sundaresan
Suresh sundaresan Krishna sigdel
Krishna sigdel Cs 131 stanford
Cs 131 stanford Sri wahyu c esther
Sri wahyu c esther Motivational interviewing wiki
Motivational interviewing wiki Kapil krishna thakur
Kapil krishna thakur Lotus feet of krishna
Lotus feet of krishna Sold goods to krishna
Sold goods to krishna Lori and george schappell separated
Lori and george schappell separated Krishna godavari dispute
Krishna godavari dispute Sf6cb
Sf6cb Dr murali krishna voona
Dr murali krishna voona Krishna education centre
Krishna education centre Sri krishna caitanya prabhu nityananda
Sri krishna caitanya prabhu nityananda Srnvatam sva katha krishna
Srnvatam sva katha krishna Bhidyate hrdaya-granthis
Bhidyate hrdaya-granthis Sree krishna college of engineering vellore
Sree krishna college of engineering vellore Dept nmr spectroscopy
Dept nmr spectroscopy Nebraska dept of agriculture
Nebraska dept of agriculture Dept a
Dept a Gome dept
Gome dept Gome dept
Gome dept Dept. name of organization
Dept. name of organization La dept of revenue
La dept of revenue Bromocicloesano
Bromocicloesano Dept of education
Dept of education Employment first ohio
Employment first ohio Florida department of agriculture and consumer services
Florida department of agriculture and consumer services Ee dept iitb
Ee dept iitb Central islip fire dept
Central islip fire dept Hoe dept
Hoe dept Gome dept
Gome dept Mn dept of education
Mn dept of education La geaux biz
La geaux biz Pt dept logistik
Pt dept logistik Florida dept of agriculture and consumer services
Florida dept of agriculture and consumer services Hjdkdkd
Hjdkdkd Finance departments
Finance departments Dept ind onegov
Dept ind onegov Micah ennis
Micah ennis Firefighter oral interview questions
Firefighter oral interview questions Liz welch mississippi
Liz welch mississippi Nys department of homeland security
Nys department of homeland security Oxford dept of continuing education
Oxford dept of continuing education Florida dept of agriculture and consumer services
Florida dept of agriculture and consumer services Nyttofunktion
Nyttofunktion Vaginal dept
Vaginal dept Worcester building department
Worcester building department Albany county dss
Albany county dss Dept of education
Dept of education Oviposition
Oviposition Dept. name of organization
Dept. name of organization Y v rao
Y v rao Rama media neuquen
Rama media neuquen Junta de clasificacion rama media
Junta de clasificacion rama media Rama oktavian
Rama oktavian üstün zekalı ram raporu nasıl alınır
üstün zekalı ram raporu nasıl alınır Rama raghava jaya seetha nayaka lyrics
Rama raghava jaya seetha nayaka lyrics Izmitram
Izmitram Rama hoetzlein
Rama hoetzlein Tmpi de rama secundaria
Tmpi de rama secundaria Polska rama kwalifikacji
Polska rama kwalifikacji Ecuacion de nernst
Ecuacion de nernst Kademe değişikliğinde rama yönlendirme
Kademe değişikliğinde rama yönlendirme Rama hoetzlein
Rama hoetzlein Rama griega e italica
Rama griega e italica