Analysis of privacy risks and measurement of privacy








![References [1] G. Yee, “Visual Analysis of Privacy Risks in Web Services”, Proceedings, 2007 References [1] G. Yee, “Visual Analysis of Privacy Risks in Web Services”, Proceedings, 2007](https://slidetodoc.com/presentation_image_h2/2ebc5f9024ec7c2e94df91f6e41adb36/image-33.jpg)

- Slides: 34

Analysis of privacy risks and measurement of privacy protection in Web Services complying with privacy policy Prepared by Ashif Adnan, Omair Alam, Aktar-uz-zaman School of Computer Science University of Windsor ON, Canada WS Privacy

Outline p p p p p Introduction Motivation Goal Related works Our observations Our modified method Strength and weakness Conclusion and future works Acknowledgment References 12/25/2021 WS Privacy 2

Introduction p Web Services According to “web services are self-contained, modular applications that can be described, published, located, and invoked over a network, generally, the World Wide Web. ” p Extended definition… n n n Web services can evolve or be adapted to other platforms Emerging WS can employ p XML (e. Xtensible Markup Language) p WSDL (Web Service Definition Language) p SOAP (Simple Object Access Protocol) p UDDI (Universal Description, Discovery, and Integration) Web browsers interacting with web servers 12/25/2021 WS Privacy 3

Motivation p WS targets n p WS applications n n n p Consumers Banking Shopping Learning Healthcare Government online Here concerns privacy WS requires consumer’s personal information 12/25/2021 WS Privacy 4

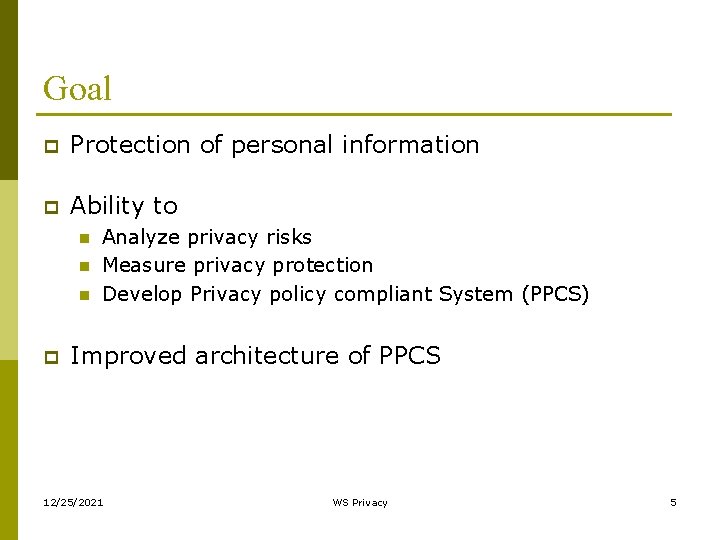
Goal p Protection of personal information p Ability to n n n p Analyze privacy risks Measure privacy protection Develop Privacy policy compliant System (PPCS) Improved architecture of PPCS 12/25/2021 WS Privacy 5

Related works 1. Privacy and web services 2. WS privacy risk analysis 3. WS privacy protection measurement 4. Privacy policy compliant WS 12/25/2021 WS Privacy 6

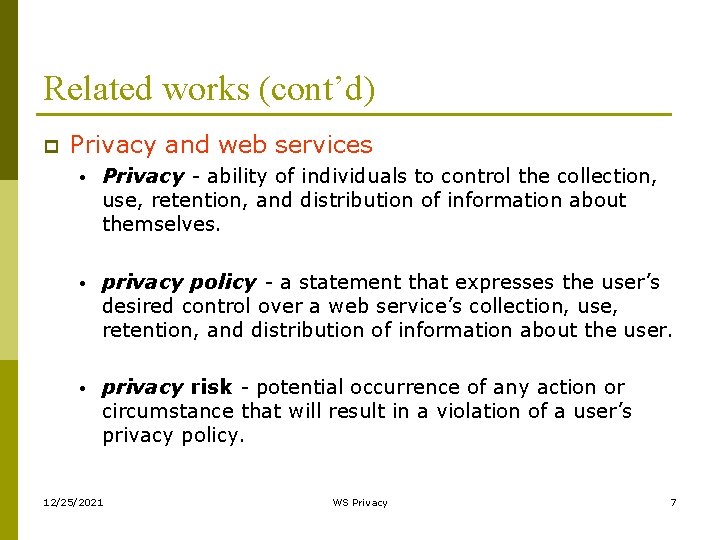
Related works (cont’d) p Privacy and web services • Privacy - ability of individuals to control the collection, use, retention, and distribution of information about themselves. • privacy policy - a statement that expresses the user’s desired control over a web service’s collection, use, retention, and distribution of information about the user. • privacy risk - potential occurrence of any action or circumstance that will result in a violation of a user’s privacy policy. 12/25/2021 WS Privacy 7

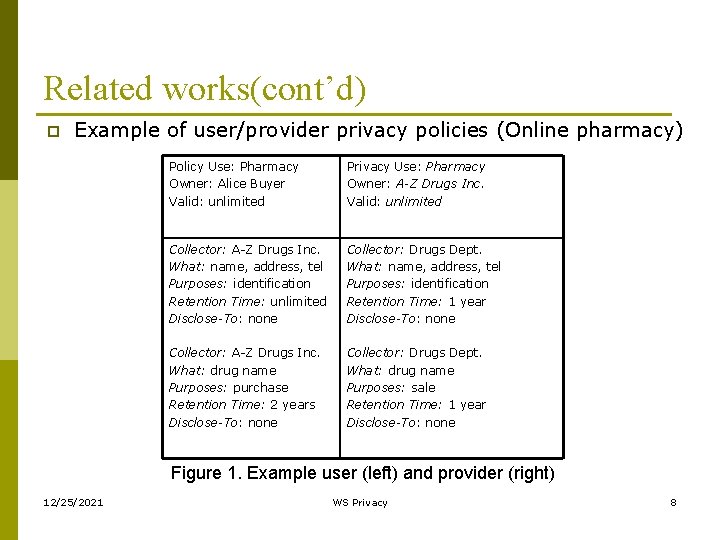
Related works(cont’d) p Example of user/provider privacy policies (Online pharmacy) Policy Use: Pharmacy Owner: Alice Buyer Valid: unlimited Privacy Use: Pharmacy Owner: A-Z Drugs Inc. Valid: unlimited Collector: A-Z Drugs Inc. What: name, address, tel Purposes: identification Retention Time: unlimited Disclose-To: none Collector: Drugs Dept. What: name, address, tel Purposes: identification Retention Time: 1 year Disclose-To: none Collector: A-Z Drugs Inc. What: drug name Purposes: purchase Retention Time: 2 years Disclose-To: none Collector: Drugs Dept. What: drug name Purposes: sale Retention Time: 1 year Disclose-To: none Figure 1. Example user (left) and provider (right) 12/25/2021 WS Privacy 8

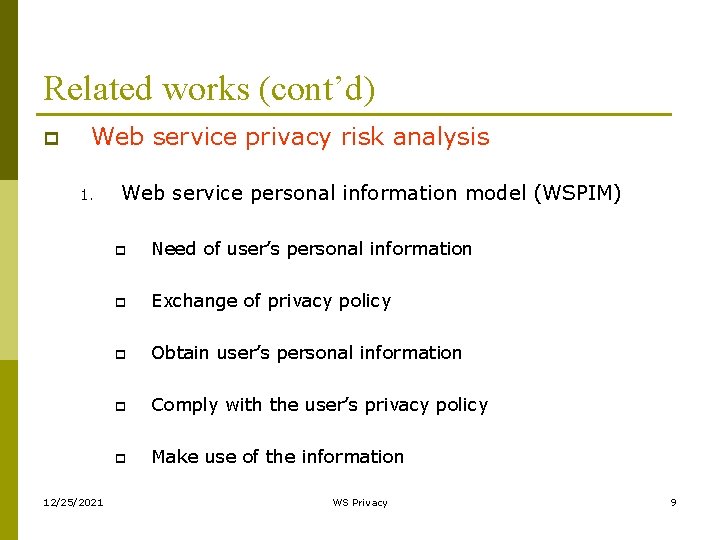
Related works (cont’d) p Web service privacy risk analysis 1. 12/25/2021 Web service personal information model (WSPIM) p Need of user’s personal information p Exchange of privacy policy p Obtain user’s personal information p Comply with the user’s privacy policy p Make use of the information WS Privacy 9

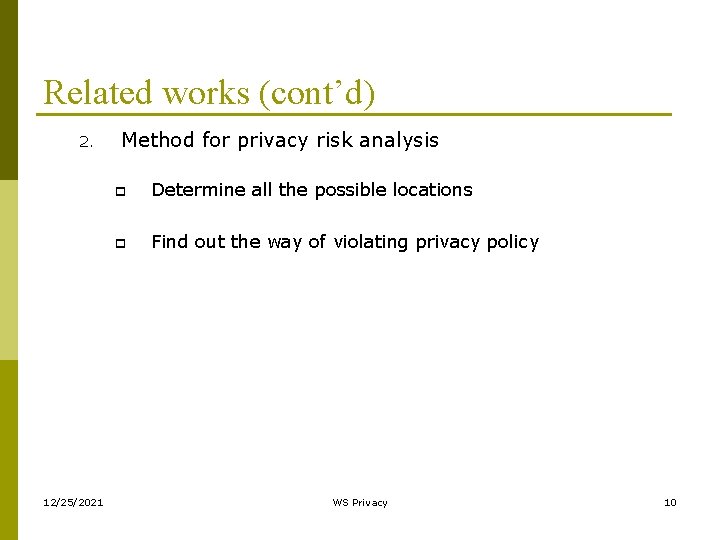
Related works (cont’d) 2. 12/25/2021 Method for privacy risk analysis p Determine all the possible locations p Find out the way of violating privacy policy WS Privacy 10

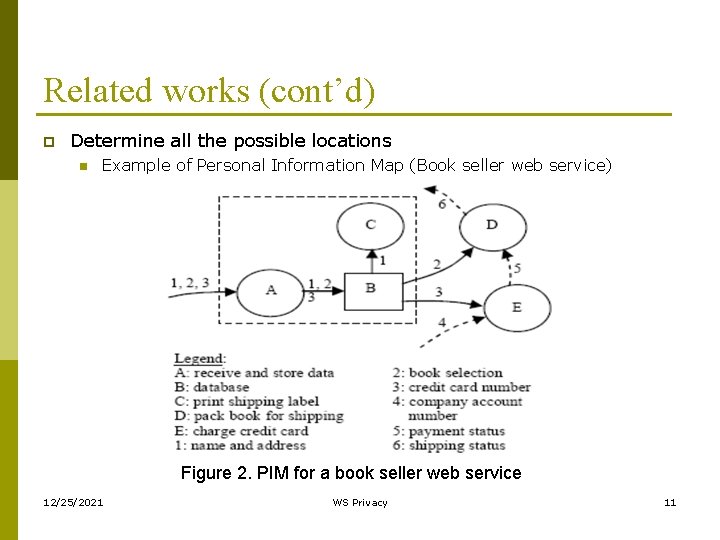
Related works (cont’d) p Determine all the possible locations n Example of Personal Information Map (Book seller web service) Figure 2. PIM for a book seller web service 12/25/2021 WS Privacy 11

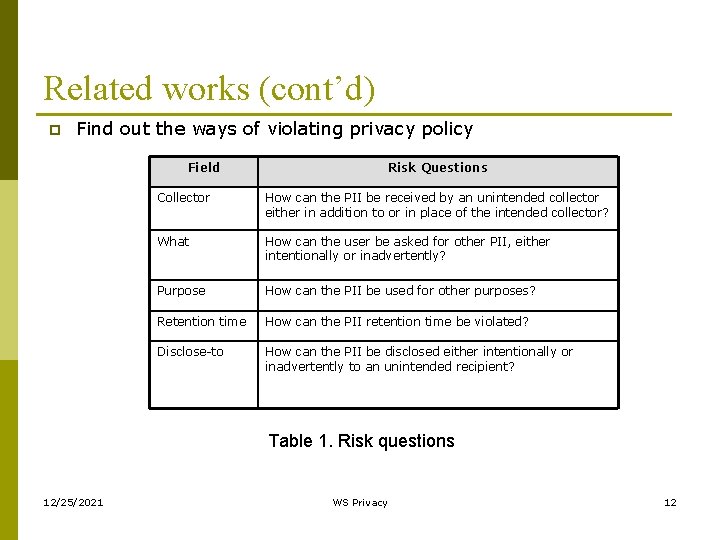
Related works (cont’d) p Find out the ways of violating privacy policy Field Risk Questions Collector How can the PII be received by an unintended collector either in addition to or in place of the intended collector? What How can the user be asked for other PII, either intentionally or inadvertently? Purpose How can the PII be used for other purposes? Retention time How can the PII retention time be violated? Disclose-to How can the PII be disclosed either intentionally or inadvertently to an unintended recipient? Table 1. Risk questions 12/25/2021 WS Privacy 12

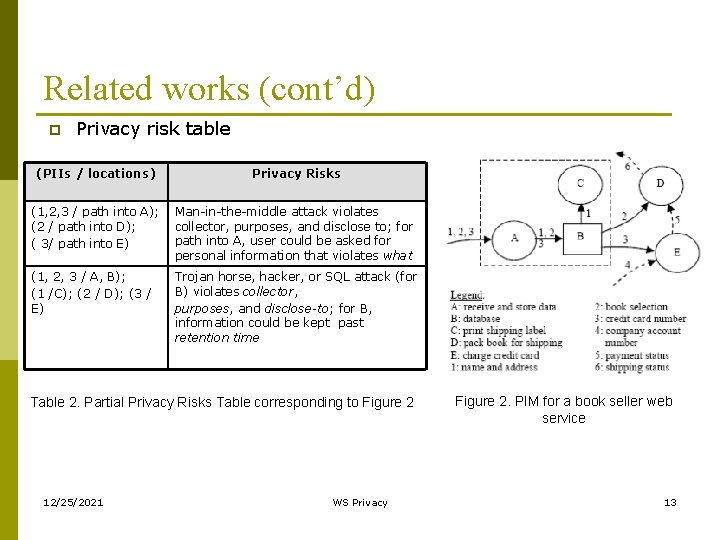
Related works (cont’d) p Privacy risk table (PIIs / locations) Privacy Risks (1, 2, 3 / path into A); (2 / path into D); ( 3/ path into E) Man-in-the-middle attack violates collector, purposes, and disclose to; for path into A, user could be asked for personal information that violates what (1, 2, 3 / A, B); (1 /C); (2 / D); (3 / E) Trojan horse, hacker, or SQL attack (for B) violates collector, purposes, and disclose-to; for B, information could be kept past retention time Table 2. Partial Privacy Risks Table corresponding to Figure 2 12/25/2021 WS Privacy Figure 2. PIM for a book seller web service 13

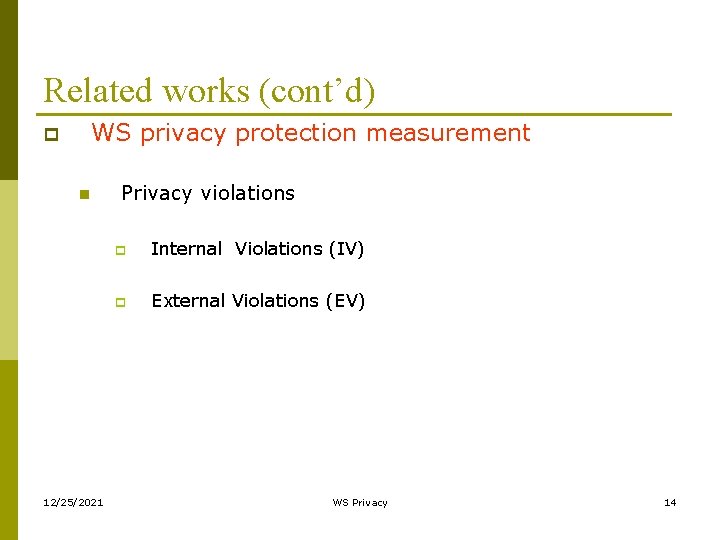
Related works (cont’d) WS privacy protection measurement p n 12/25/2021 Privacy violations p Internal Violations (IV) p External Violations (EV) WS Privacy 14

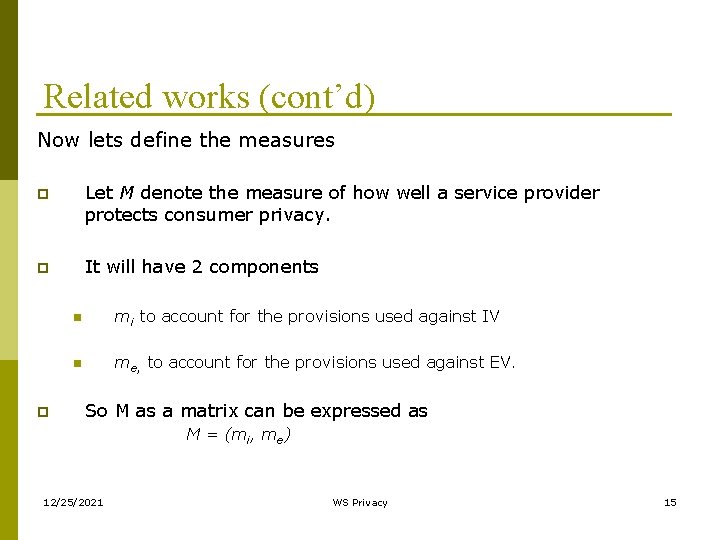
Related works (cont’d) Now lets define the measures p Let M denote the measure of how well a service provider protects consumer privacy. p It will have 2 components p n mi to account for the provisions used against IV n me, to account for the provisions used against EV. So M as a matrix can be expressed as M = (mi, me) 12/25/2021 WS Privacy 15

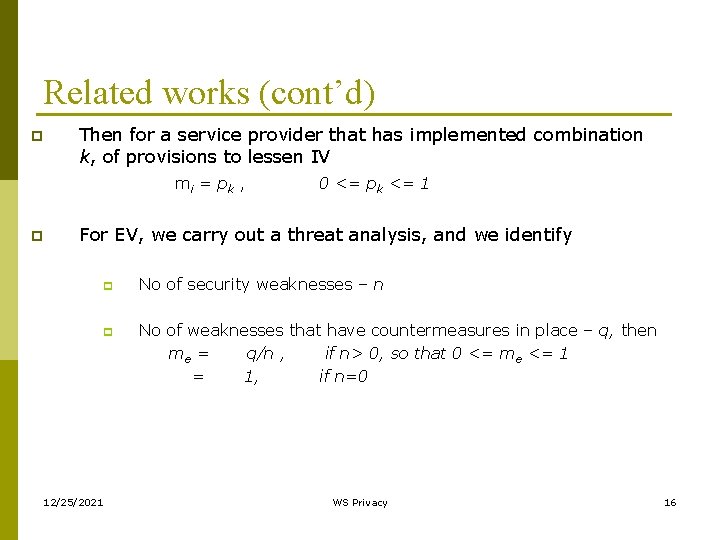
Related works (cont’d) p Then for a service provider that has implemented combination k, of provisions to lessen IV m i = pk , p 0 <= pk <= 1 For EV, we carry out a threat analysis, and we identify p p 12/25/2021 No of security weaknesses – n No of weaknesses that have countermeasures in place – q, then me = q/n , if n> 0, so that 0 <= me <= 1 = 1, if n=0 WS Privacy 16

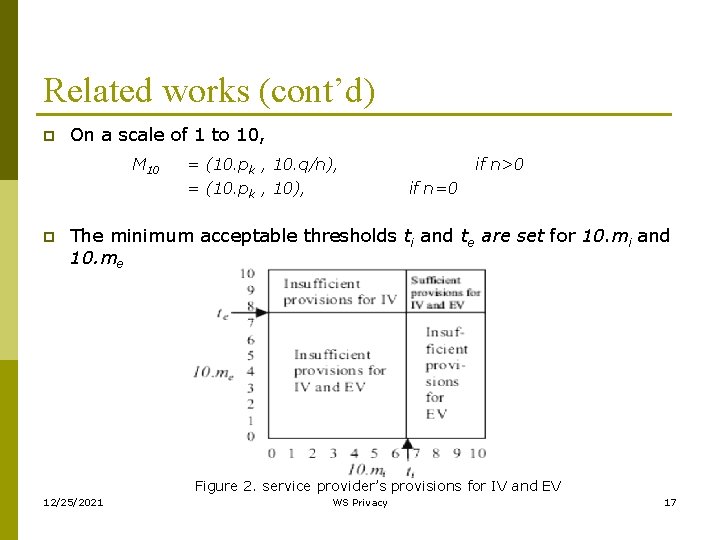
Related works (cont’d) p On a scale of 1 to 10, M 10 p = (10. pk , 10. q/n), = (10. pk , 10), if n>0 if n=0 The minimum acceptable thresholds ti and te are set for 10. mi and 10. me Figure 2. service provider’s provisions for IV and EV 12/25/2021 WS Privacy 17

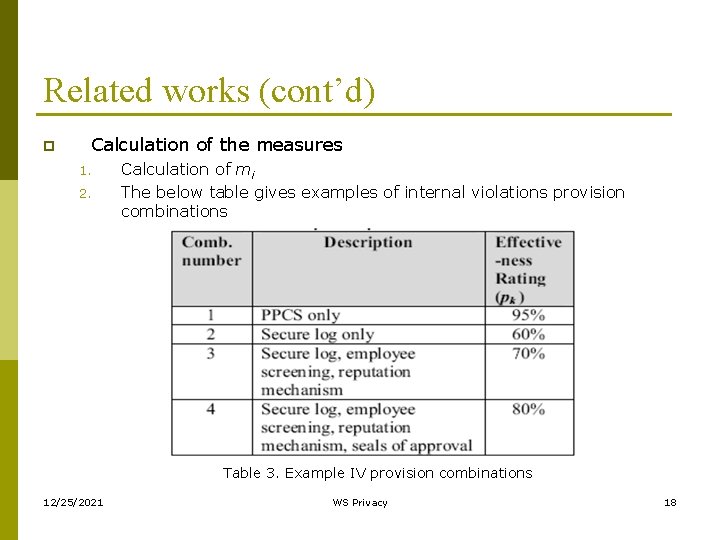
Related works (cont’d) p Calculation of the measures 1. 2. Calculation of mi The below table gives examples of internal violations provision combinations Table 3. Example IV provision combinations 12/25/2021 WS Privacy 18

Related works (cont’d) p Calculation of me 1. 2. 3. 4. 5. Identify threats on the user’s data. Create attack trees for the system. Apply weights to the leaves Prune the tree so that only exploitable leaves remain. Count the number of such leaves or vulnerabilities. Count the countermeasures are in place for the vulnerabilities. After performing the above steps, both q and n are available for calculating me 12/25/2021 WS Privacy 19

Related works (cont’d) Privacy policy compliant WS (PPCS) p n The Privacy Policy Compliance System for WS which will provide consumer with a promising approach to measure of control over his/her private information through the use of a PPCS (Private Policy Compliance system). n The policies of consumer and provider should match 12/25/2021 WS Privacy 20

Related works(cont’d) p Privacy Legislation 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. Accountability Identify purpose Consent Limiting collection Limiting use, disclosure and retention Accuracy Safeguard Openness Individual Access Challenging compliance Note: Those are also the requirements for PPCS 12/25/2021 WS Privacy 21

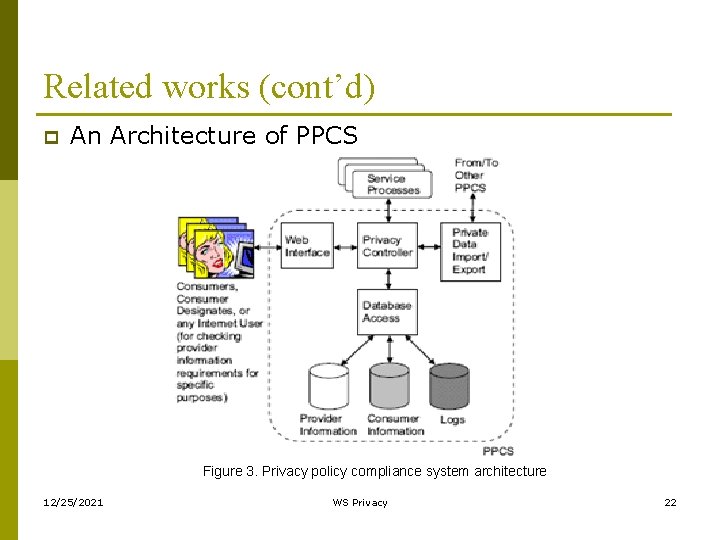
Related works (cont’d) p An Architecture of PPCS Figure 3. Privacy policy compliance system architecture 12/25/2021 WS Privacy 22

Our observations 1. Privacy policy proposed by the author is not complete which leads to incomplete set of risks questions giving the consumer less confidence to do the transaction. 2. There are no provisions for consumers to set up the measuring standards. 3. Following points need to be considered to build for more effective PPCS for WS: 1. 2. 3. 4. 5. 6. 7. 8. 12/25/2021 Damaged protection Children protection Right to transfer Right to opt in /opt out Lack of scalability Lack of knowledge Data tempering Cost WS Privacy 23

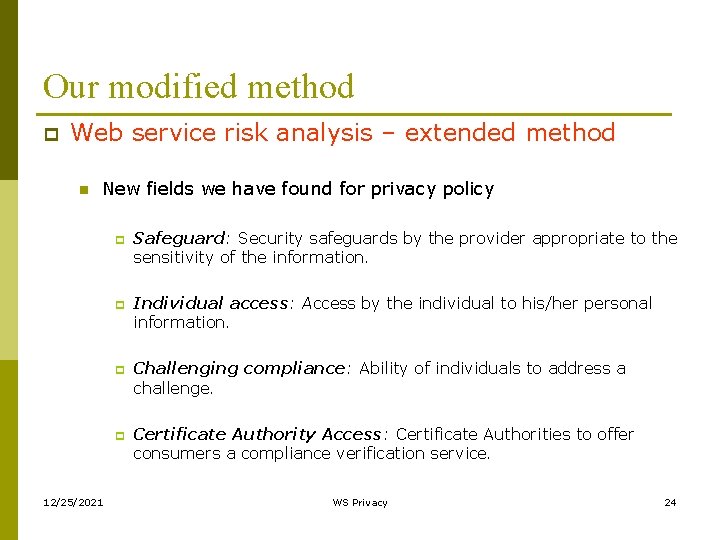
Our modified method p Web service risk analysis – extended method n New fields we have found for privacy policy p p 12/25/2021 Safeguard: Security safeguards by the provider appropriate to the sensitivity of the information. Individual access: Access by the individual to his/her personal information. Challenging compliance: Ability of individuals to address a challenge. Certificate Authority Access: Certificate Authorities to offer consumers a compliance verification service. WS Privacy 24

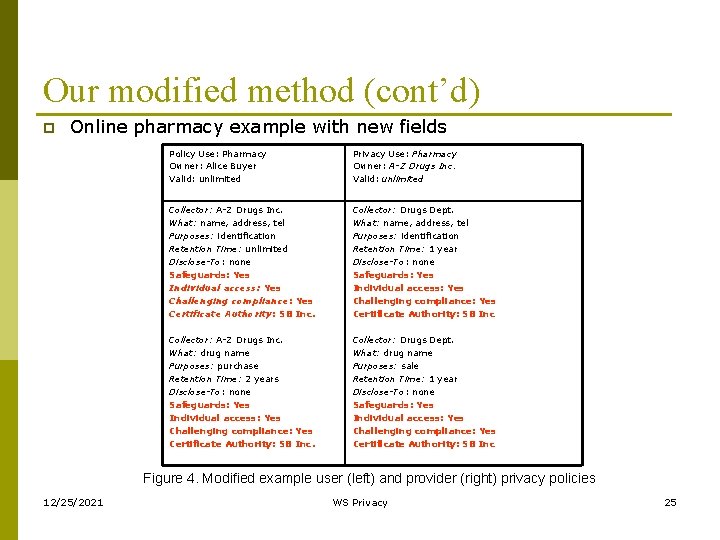
Our modified method (cont’d) p Online pharmacy example with new fields Policy Use: Pharmacy Owner: Alice Buyer Valid: unlimited Privacy Use: Pharmacy Owner: A-Z Drugs Inc. Valid: unlimited Collector: A-Z Drugs Inc. What: name, address, tel Purposes: identification Retention Time: unlimited Disclose-To: none Safeguards: Yes Individual access: Yes Challenging compliance: Yes Certificate Authority: SB Inc. Collector: Drugs Dept. What: name, address, tel Purposes: identification Retention Time: 1 year Disclose-To: none Safeguards: Yes Individual access: Yes Challenging compliance: Yes Certificate Authority: SB Inc Collector: A-Z Drugs Inc. What: drug name Purposes: purchase Retention Time: 2 years Disclose-To: none Safeguards: Yes Individual access: Yes Challenging compliance: Yes Certificate Authority: SB Inc. Collector: Drugs Dept. What: drug name Purposes: sale Retention Time: 1 year Disclose-To: none Safeguards: Yes Individual access: Yes Challenging compliance: Yes Certificate Authority: SB Inc Figure 4. Modified example user (left) and provider (right) privacy policies 12/25/2021 WS Privacy 25

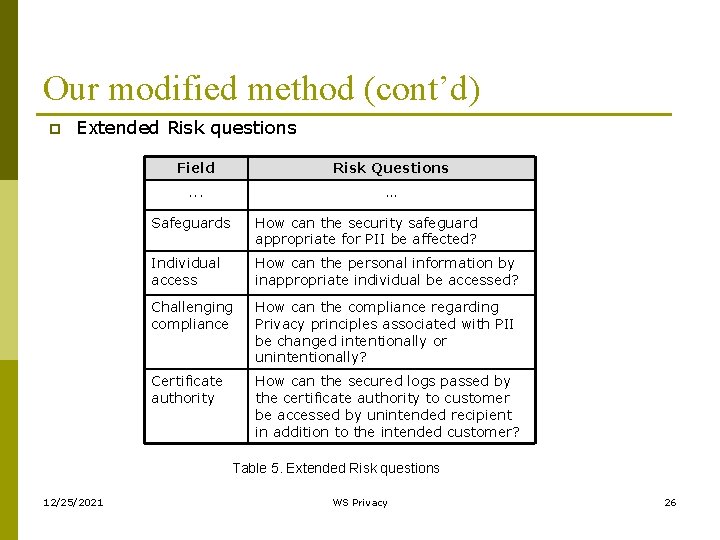
Our modified method (cont’d) p Extended Risk questions Field Risk Questions . . . … Safeguards How can the security safeguard appropriate for PII be affected? Individual access How can the personal information by inappropriate individual be accessed? Challenging compliance How can the compliance regarding Privacy principles associated with PII be changed intentionally or unintentionally? Certificate authority How can the secured logs passed by the certificate authority to customer be accessed by unintended recipient in addition to the intended customer? Table 5. Extended Risk questions 12/25/2021 WS Privacy 26

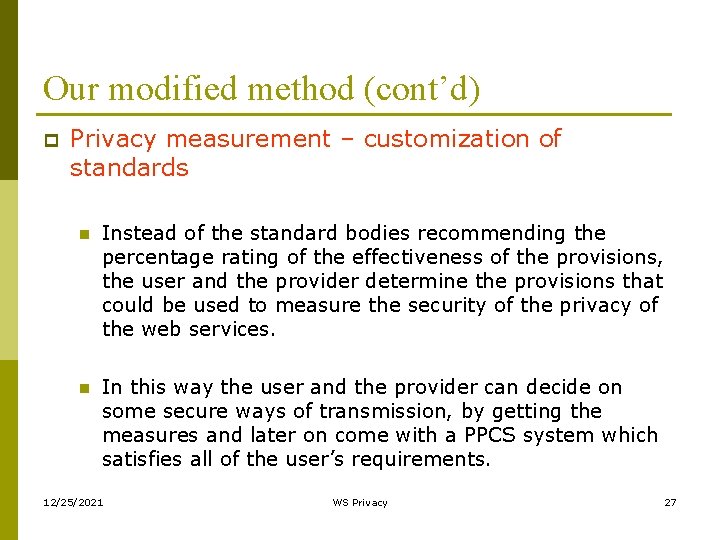
Our modified method (cont’d) p Privacy measurement – customization of standards n Instead of the standard bodies recommending the percentage rating of the effectiveness of the provisions, the user and the provider determine the provisions that could be used to measure the security of the privacy of the web services. n In this way the user and the provider can decide on some secure ways of transmission, by getting the measures and later on come with a PPCS system which satisfies all of the user’s requirements. 12/25/2021 WS Privacy 27

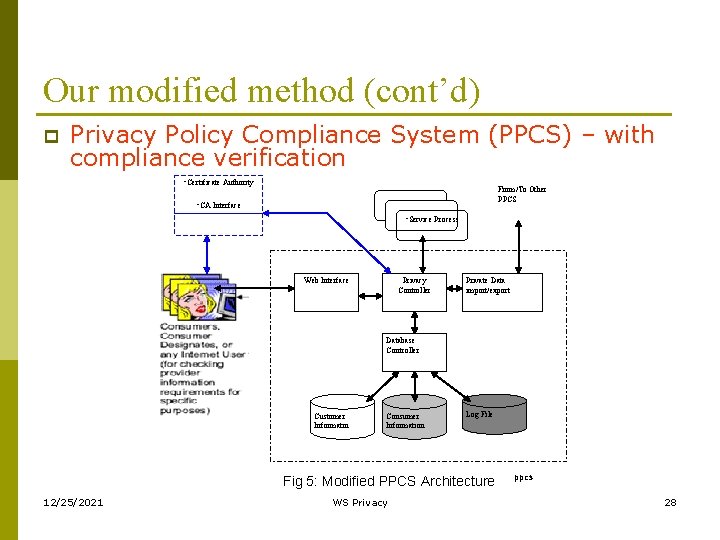
Our modified method (cont’d) p Privacy Policy Compliance System (PPCS) – with compliance verification • Certificate Authority From/To Other PPCS • CA Interface • Service Process Web Interface Privacy Controller Private Data import/export Database Controller Customer Informatin Consumer Information Log File Fig 5: Modified PPCS Architecture 12/25/2021 WS Privacy ppcs 28

Weakness and Strengths p Strength n n n p Consumer will now have the full confidence to do a transaction with the service provider. Privacy measurement standards can be customized to make transactions more secured. The consumer who does not bother or doesn’t know how to check log file to verify the compliancy, they can easily do so by Certified Authority Weakness n n 12/25/2021 PPCS for web service is semi automated, in some cases we need to notify respected officers for the non compliance matters, which are not automated. Cost of PPCS can not be controlled because it depends on the combination of hardware, software and storage. WS Privacy 29

Conclusion and Future Works p Observed steps n n n p Understanding how to analyze the risks to privacy Understanding how to measure privacy protection and Understanding a privacy policy compliant web service. Steps for our new PPCS system n n n WS risk analysis with extended privacy policy WS privacy protection measurement with customized standards PPCS with compliance verification 12/25/2021 WS Privacy 30

Conclusion and Future Works (cont’d) p Plans for future research include n n n Programming the graphical notation to be machine readable Protecting the system from occurring damage due to shared personal information Protecting children from getting affected by shared information by others Improving the procedure for threat analysis by automating it and making it more foolproof Investigating other possible methods of privacy protection effectiveness 12/25/2021 WS Privacy 31

Acknowledgement p We would like to thank our professor for his great support and giving us the opportunity to learn privacy and security in internet p We would like to thank our audience for listening our presentation 12/25/2021 WS Privacy 32
![References 1 G Yee Visual Analysis of Privacy Risks in Web Services Proceedings 2007 References [1] G. Yee, “Visual Analysis of Privacy Risks in Web Services”, Proceedings, 2007](https://slidetodoc.com/presentation_image_h2/2ebc5f9024ec7c2e94df91f6e41adb36/image-33.jpg)
References [1] G. Yee, “Visual Analysis of Privacy Risks in Web Services”, Proceedings, 2007 IEEE International Conference on Web Services (ICWS 2007), July 9 - 13, 2007, pp. 671 -678. [2] G. Yee, “Measuring Privacy Protection in Web Services”, Proceedings, 2006 IEEE International Conference on Web Services (ICWS 2006), Sept. , 2006, pp. 647 -654. [3] G. Yee, L. Korba, “Privacy policy compliance for Web services”, Proceedings, 2004 IEEE Intrnation-al Conference on Web Services (ICWS 2004), July, 2006, pp. 158 -165. [4] I. Goldberg, D. Wagner, and E. Brewer, “Privacy-Enhancing Technologies for the Internet”, IEEE COMPCON’ 97, 1997, pp. 103 -109. [5] Canadian Standards Association, “Model Code for the Protection of Personal Information”, retrieved Sept. 5, 2003 from: http: //www. csa. ca/standards/privacy/code/Default. asp? article. ID=5286&language=E nglish 12/25/2021 WS Privacy 33

The End Questions ? 12/25/2021 WS Privacy 34
 Owasp top 10 privacy risks
Owasp top 10 privacy risks Cvs privacy awareness and hipaa privacy training
Cvs privacy awareness and hipaa privacy training Opportunities of media and information in daily life
Opportunities of media and information in daily life Actions to address risks and opportunities
Actions to address risks and opportunities Costs and risks of database approach
Costs and risks of database approach Chapter 1 lesson 3 health risks and your behavior
Chapter 1 lesson 3 health risks and your behavior Cloud computing benefits and risks
Cloud computing benefits and risks Related risks that increase in effect with each added risk
Related risks that increase in effect with each added risk Chapter 1 lesson 3 health risks and your behavior
Chapter 1 lesson 3 health risks and your behavior Technology and operational risk
Technology and operational risk Workplace hazards and risks
Workplace hazards and risks Risks and mitigation slide
Risks and mitigation slide Understanding hazards and risks
Understanding hazards and risks Project finance risks and mitigants
Project finance risks and mitigants 7 domains of it infrastructure
7 domains of it infrastructure What factors affect region/community location decisions
What factors affect region/community location decisions Measurement and analysis of online social networks
Measurement and analysis of online social networks Tolerance ratio
Tolerance ratio Measurement and analysis of online social networks
Measurement and analysis of online social networks Dr kano's house of tqm
Dr kano's house of tqm Cmmi measurement and analysis
Cmmi measurement and analysis Resilience index measurement and analysis
Resilience index measurement and analysis The biggest risk is not taking any risk
The biggest risk is not taking any risk Special contingency risks
Special contingency risks David chaffey
David chaffey Risks of e procurement
Risks of e procurement Instant messaging security risks
Instant messaging security risks Civil engineering completed risks insurance
Civil engineering completed risks insurance Mātes vecuma risks t21
Mātes vecuma risks t21 Enterprise risk management for credit unions
Enterprise risk management for credit unions Criteria for bulimia nervosa
Criteria for bulimia nervosa Cips procurement process
Cips procurement process Tracing vs vouching
Tracing vs vouching Chapter 22 illegal drugs lesson 1 worksheet answers
Chapter 22 illegal drugs lesson 1 worksheet answers A thick, sticky, dark fluid produced when tobacco burns.
A thick, sticky, dark fluid produced when tobacco burns.