Separate Domains of IT Infrastructure CS 5493 7












- Slides: 15

Separate Domains of IT Infrastructure CS 5493

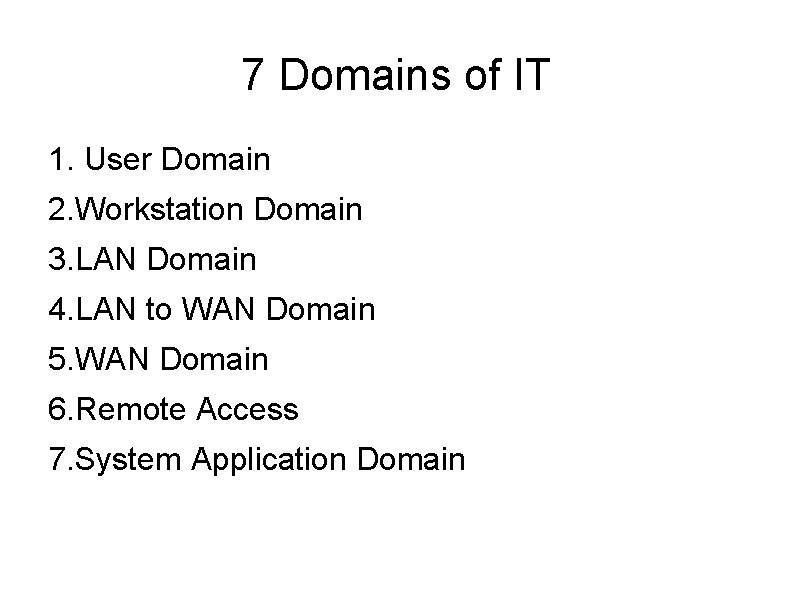
7 Domains of IT 1. User Domain 2. Workstation Domain 3. LAN Domain 4. LAN to WAN Domain 5. WAN Domain 6. Remote Access 7. System Application Domain

User Domain ● Defines the people who access an organization's information system. – This is the domain of the AUP

User Domain ● Risks/Threats/Vulnerabilities – Lack of user awareness – User apathy toward policies – Security policy violations – Disgruntled employee attacks – etc

Workstation Domain ● The computer on your desk. – This can extend to other devices that provide access to computing resources. – The staff that supports the workstations

Workstation Domain ● Risks/threats/vulnerabilities – Unauthorized access – Malware – etc

Network Service Domain ● For the purpose of this course, we will combine the domains for LAN, LAN-to-WAN, and WAN into the Network Service Domain

Network Service Domain ● Includes the equipment, cables, the wireless access, etc.

Network Service Domain ● Risks/Threats/Vulnerabilities/ – Unauthorized access, physical or otherwise – Malware attacks – etc

Remote Access Domain ● Accessing the computing services from outside the boundary of the computing system. – Smart phones – Laptop computers – PDAs – E-mail usage – Wireless access – Access to cloud resources

Remote Access Domain ● Risk/threat/vulnerability – Theft – Unauthorized access – etc

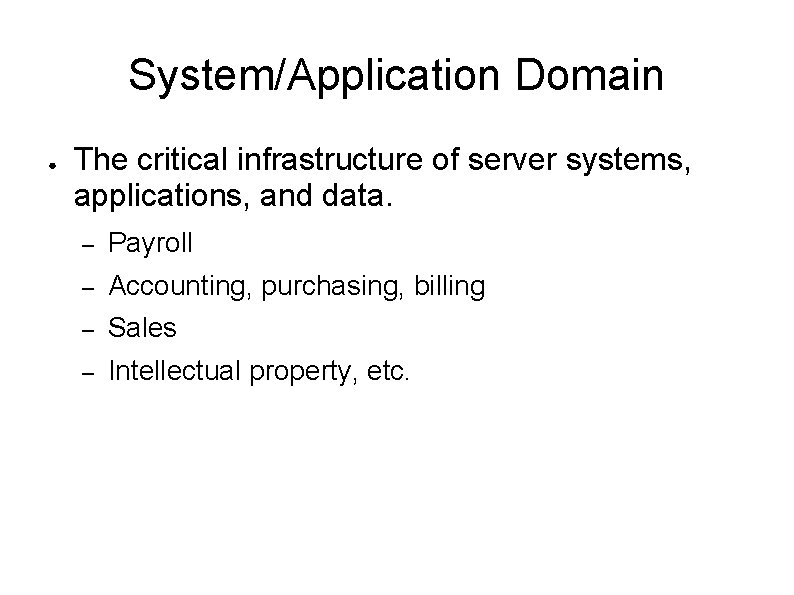
System/Application Domain ● The critical infrastructure of server systems, applications, and data. – Payroll – Accounting, purchasing, billing – Sales – Intellectual property, etc.

System/Application Domain ● Risk/threat/vulnerability – Unauthorized access – Hardware failure – Data loss – etc

5 Domains ● User ● Workstation ● Network ● Remote ● System/Application

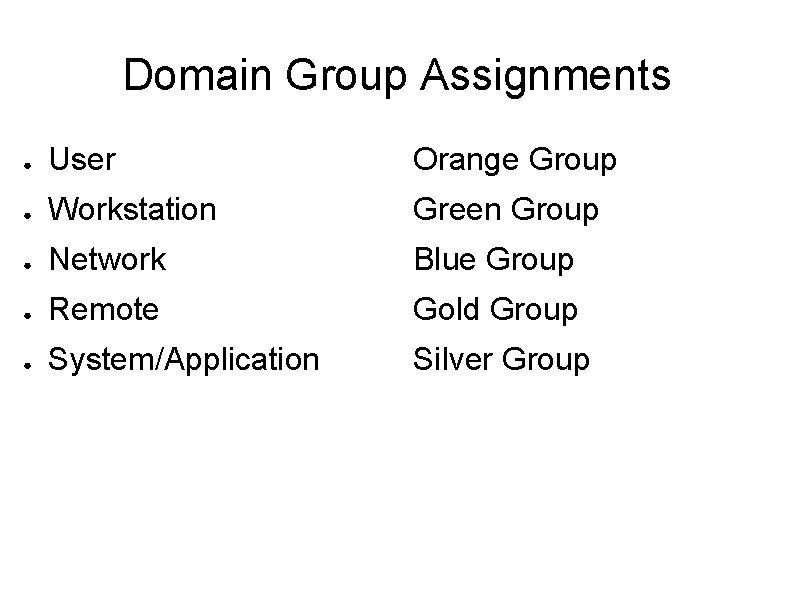
Domain Group Assignments ● User Orange Group ● Workstation Green Group ● Network Blue Group ● Remote Gold Group ● System/Application Silver Group
 7 it domains
7 it domains Who is gregor mendel
Who is gregor mendel A sign separates items in a list
A sign separates items in a list Separate earthing system
Separate earthing system A separate peace test
A separate peace test Chapter 1 a separate peace
Chapter 1 a separate peace Horizontal imaginary line
Horizontal imaginary line Sieving separation examples
Sieving separation examples How does finny react to brinker’s question?
How does finny react to brinker’s question? How to seperate salt and sand
How to seperate salt and sand Affinity chromatography animation
Affinity chromatography animation Separate result unknown
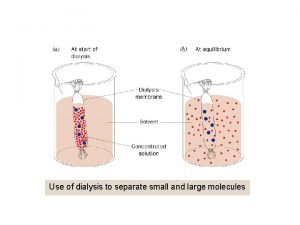
Separate result unknown Dialysis can separate
Dialysis can separate Hash separate chaining
Hash separate chaining Separate picture
Separate picture Are english language and literature separate gcses
Are english language and literature separate gcses