Agenda The Linux File System chapter 4 in














![umask Command Used to automatically establish file permission upon creation Format: n umask [mask] umask Command Used to automatically establish file permission upon creation Format: n umask [mask]](https://slidetodoc.com/presentation_image/006325d5854bfd75dbf407b220d0a2fb/image-26.jpg)






![Linking Files There are two major types of links: Hard Link: ln [existing_file] [linked_file] Linking Files There are two major types of links: Hard Link: ln [existing_file] [linked_file]](https://slidetodoc.com/presentation_image/006325d5854bfd75dbf407b220d0a2fb/image-34.jpg)

- Slides: 37

Agenda The Linux File System (chapter 4 in text) n Directory Structures / Navigation Terminology / File Naming Rules Relative vs Absolute pathnames mkdir, mkdir -p, rmdir, rm -r ls, ls -a, ls -F, ls -ld n Setting Access Permissions chmod / umask n Linking Files Hard Links / Symbolic Links

File System n n n A File System is a structure used to organize programs and data on a computer’s storage device Linux (Unix) OS has a special file called a directory file used to store ordinary files as well as other “directories” Directories allow a computer’s file system to be better organized.

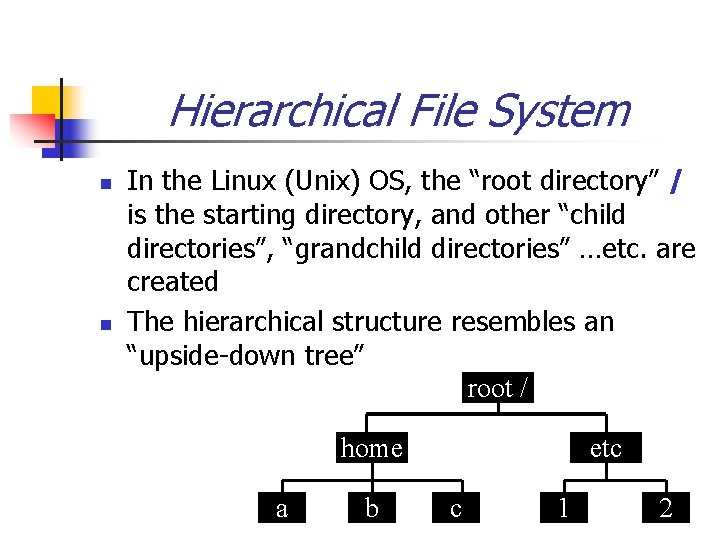
Hierarchical File System n n In the Linux (Unix) OS, the “root directory” / is the starting directory, and other “child directories”, “grandchild directories” …etc. are created The hierarchical structure resembles an “upside-down tree” root / home a b etc c 1 2

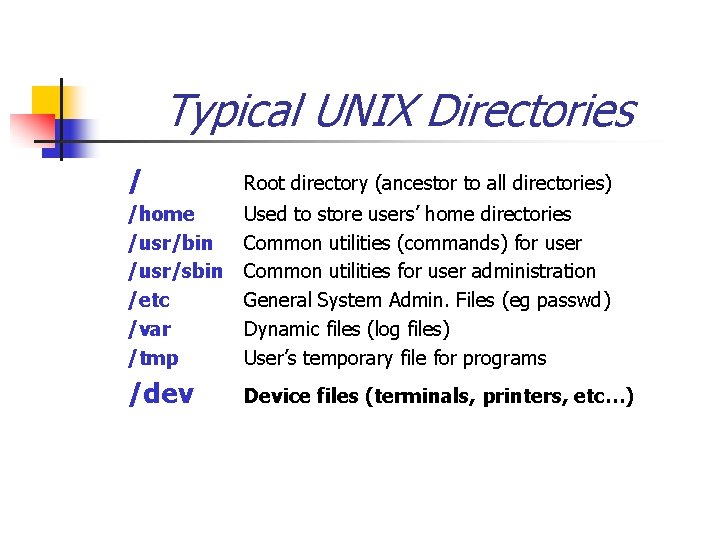
Typical UNIX Directories / Root directory (ancestor to all directories) /home /usr/bin /usr/sbin /etc /var /tmp Used to store users’ home directories Common utilities (commands) for user Common utilities for user administration General System Admin. Files (eg passwd) Dynamic files (log files) User’s temporary file for programs /dev Device files (terminals, printers, etc…)

File Naming Rules The following rules apply to naming ordinary files or “directory files”: n n Some file systems restrict filename size to 14 characters, other file systems allow for 255 characters (best to select filename size of 14) Can use letters (upper & lower case), numbers, period , comma or underscore _ characters Upper case different than lower case Period at beginning of filename hides file

Pathnames n n A pathname is a listing of directories that will lead to a directory or a file. Examples: n Directory pathname: /home/username/ics 124/assignments n File pathname: /home/username/ops 224/assignments/assn 1. txt

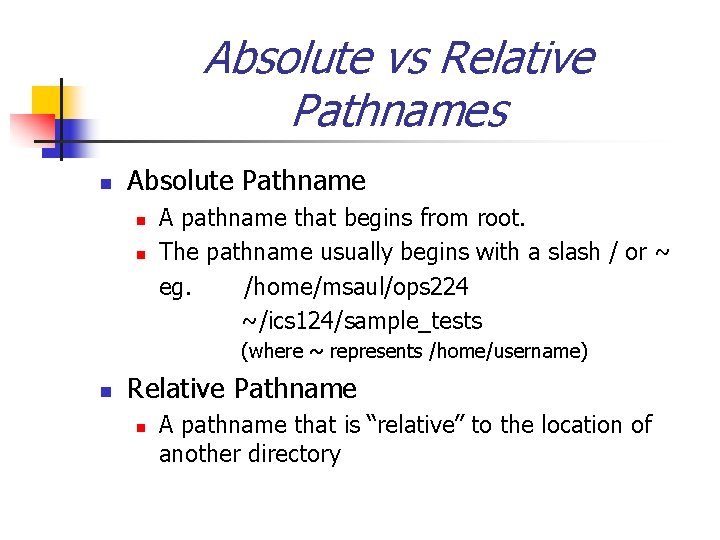
Absolute vs Relative Pathnames n Absolute Pathname n n A pathname that begins from root. The pathname usually begins with a slash / or ~ eg. /home/msaul/ops 224 ~/ics 124/sample_tests (where ~ represents /home/username) n Relative Pathname n A pathname that is “relative” to the location of another directory

Relative Pathnames Rules: n n Relative pathname does NOT begin with a slash. Following symbols can be used: . . parent directory. current directory

Relative Pathnames Examples: n n Change to another directory branch from parent directory: cd. . /ops 224 copy sample. c file from your professor’s directory to your current directory: cp /home/profid/oop 244/sample. c.

Making Directories Building directories is similar in approach to building a house n n n Begins from a foundation (eg home directory) Need to build in proper order (add on addition to house in right location) when building directories from different locations, must provide proper absolute or relative pathname!!

Where do we want to build directory? n n Want to build a directory called tmp that branches-off of your home directory Verify which directory you are located (either look at directory from command prompt or issue the command pwd Type mkdir tmp at the Unix prompt, followed by ENTER Always verify that directory has been created (e. g. use ls or ls -ld command)

Creating Parent Directories To create directory paths with parent directories that do not exist you can use the command mkdir -p pathname eg. Mkdir -p mur/dir 1 (This would create the parent directory mur and then the child directory dir 1)

Removing Directories Removing directories is reverse order of building directories n n n Issue command rmdir Cannot remove directories containing files or other subdirectories (unless using rm -r) Need to “step-back” to at least parent directory to remove empty directory or related child, grandchild, etc… directories

Listing Directory Contents ls ls -a ls -l ls -F ls -ld ls -i Compact listing on non-hidden files Compact listing of ALL files Detailed listing of non-hidden files Displays symbols to mark directories and executable files Detailed listing of specified directory Displays i-node number (I. d. number of files)

Access Permissions n n Limiting unauthorized access to your directories and files is a very important concern for ALL Linux (Unix) users. Consequences of Unauthorized Access: n n Copying your assignments (cheating) Using your account for illegal activity Using your account to send obscene messages Tampering with files

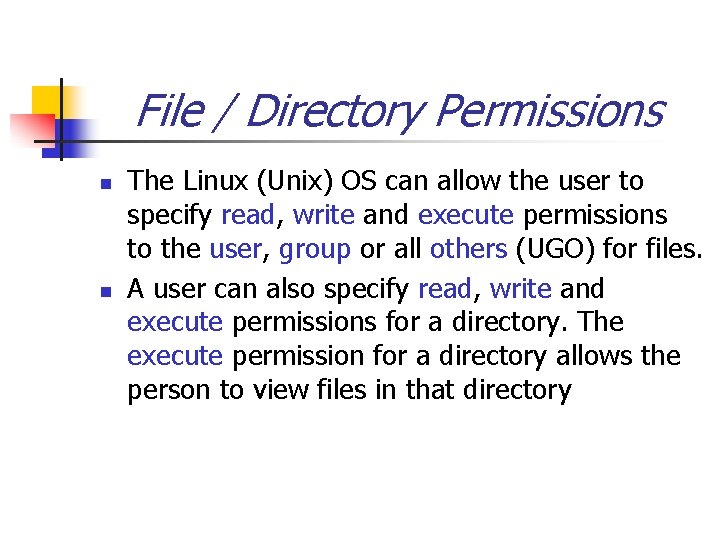
File / Directory Permissions n n The Linux (Unix) OS can allow the user to specify read, write and execute permissions to the user, group or all others (UGO) for files. A user can also specify read, write and execute permissions for a directory. The execute permission for a directory allows the person to view files in that directory

chmod Command (Relative Method) Used to change the access permissions of a file or directory Format: chmod [option] [who] [operation] [permission] file chmod [option] [permission] file-list n n n who relates to user (u) , group (g) or all others (o) operation relates to adding (+), removing (-) or setting (=) permissions are read (r), write (w) and execute (x)

chmod Command (Relative Method) Examples: n Add Permission chmod g+rw file. name chmod o+x file. name n Remove Permission Note: you can use wildcard symbols (eg *) to match particular files chmod g-w file. name chmod a-w file. name (removes write for ugo) n Set Permission chmod o=rx file. name chmod go=rx filename

chmod Command (Absolute Method) 1. 2. You can use the chmod command with octal number to represent (in binary) a permission (1) or removal of a permission (0) for the file or directory This is referred to as an Absolute command, and many prefer this “short-cut” method to changing file / directory permissions

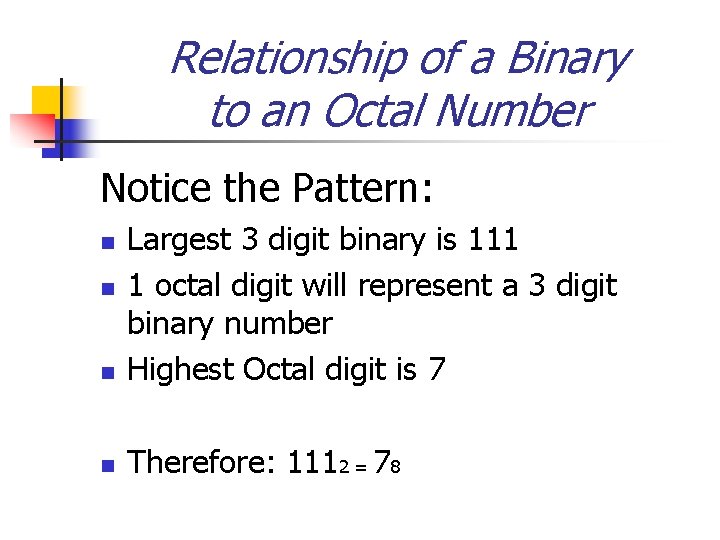
Relationship of a Binary to an Octal Number Notice the Pattern: n Largest 3 digit binary is 111 1 octal digit will represent a 3 digit binary number Highest Octal digit is 7 n Therefore: 1112 = 78 n n

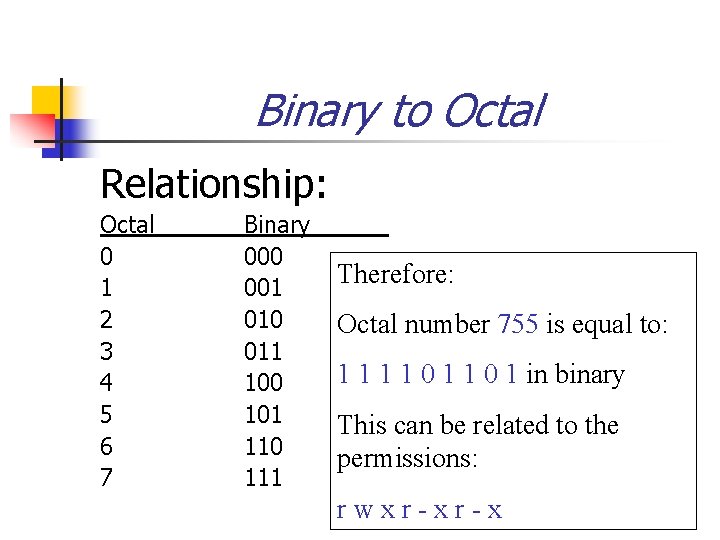
Binary to Octal Relationship: Octal 0 1 2 3 4 5 6 7 Binary 000 001 010 011 100 101 110 111 Therefore: Octal number 755 is equal to: 1 1 0 1 in binary This can be related to the permissions: rwxr-xr-x

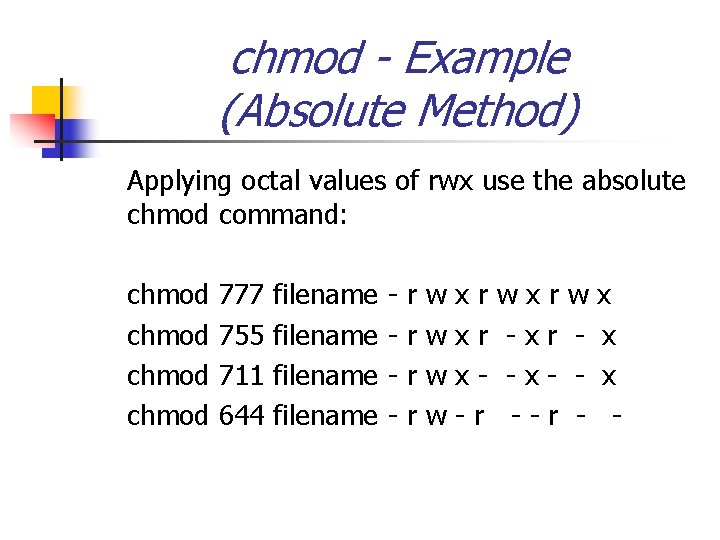
chmod - Example (Absolute Method) Applying octal values of rwx use the absolute chmod command: chmod 777 755 711 644 filename - r r w w xr xr x-r wxr -x--r w - x x x -

Practical Applications of chmod Command n Pass-Through Permissions n n Pass-Through Permissions allow users to passthrough the home directories and other subdirectories until they reach a directory that provides read and execute permissions to read files. (pass-through permissions drwx--x--x) To deny access other than yourself, you can remove pass-through permissions of your home directory (drwx------)

Practical Applications of chmod Command n Linking & Sharing Files n n Set up directory and file permissions to allow users to modify a file or set up permissions of file to allow user to view, but not modify a file. Webpages n Allow or deny other access to files. For example, use chmod command to allow group & others read and execute permissions to “pass-through” your directories.

Creating a Mask n n n Are you tired of continually changing access permissions for newly-created files or directories? The umask command automatically sets the file permissions upon creation of the file. This process is useful, since user may sometimes forget to change the permissions of newly-created files or when they transfer files via the FTP application
![umask Command Used to automatically establish file permission upon creation Format n umask mask umask Command Used to automatically establish file permission upon creation Format: n umask [mask]](https://slidetodoc.com/presentation_image/006325d5854bfd75dbf407b220d0a2fb/image-26.jpg)
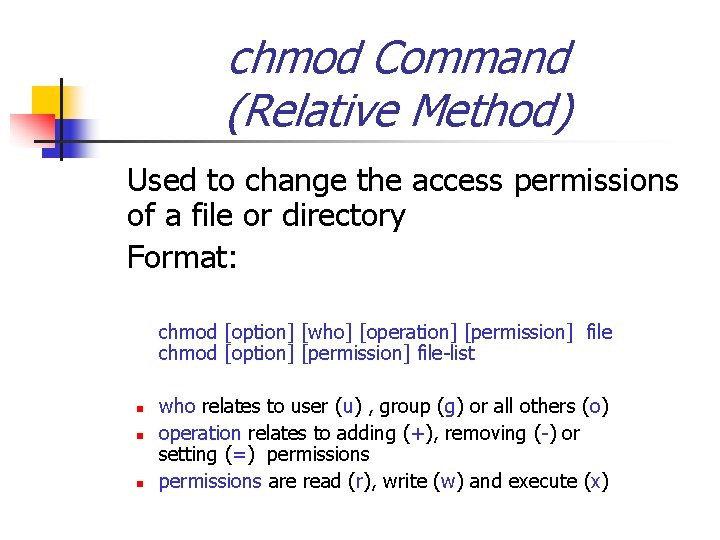
umask Command Used to automatically establish file permission upon creation Format: n umask [mask] where mask represents a 3 -digit octal number regarding UGO and permissions to be assigned. Note: The rules vary between setting file masks and directory masks

Setting Directory Mask To change directory mask: n n n Determine octal number that would set directory permission Subtract octal number 777 from octal number determined above to get result issue the command : umask [octal number] Note: should also be able to use “relative method” with umask command - may be easier

Setting Directory Mask Example: n n n To set mask for newly-created directories to: rwxr--r-Determine octal number 1 1 0 0 = 744 Subtract 777 from 744 = 033 Issue command umask to verify change

Setting File Mask To change directory mask: n n n Determine binary number that would set directory permission Subtract above binary number from 110110110 and convert result to octal number to determine umask value issue the command : umask [octal number]

Setting File Mask - Example 1 Example: n n To set mask for newly-created files to: rw-r--r-Convert to binary 110100100 Subtract above from 110110110 - 110100100 = 000010010 (which is 022) issue umask 022 (enter umask to verify)

Setting File Mask - Example 2 Example: n n To set mask for newly-created files to: rwxr--r-Convert to binary 111100100 Subtract above from 110110110 Cannot subtract 1 from 0 - 111100100 = 000010010 (which is 022 octal) issue umask 022 (enter umask to verify)

File Identification n n Files in UNIX and Linux contain contents (e. g. source code) but each file also contains information regarding the file itself. Each file is assigned a i-node number. To view i-node information, you can issue the UNIX command ls -i 705900 testfor 706640 chevy 703817 thefile Note that each file is unique since they have been assigned a different i-node number for identification.

Linking Files n n Since UNIX is a multi-user operating system, it makes sense to allow users to share files to collaborate on projects (such as programming projects, reports, etc. ) In order to avoid duplication and inefficiency, it is better to provide links between files to give user illusion that what is edited on their file affects contents on other groups’ files.
![Linking Files There are two major types of links Hard Link ln existingfile linkedfile Linking Files There are two major types of links: Hard Link: ln [existing_file] [linked_file]](https://slidetodoc.com/presentation_image/006325d5854bfd75dbf407b220d0a2fb/image-34.jpg)
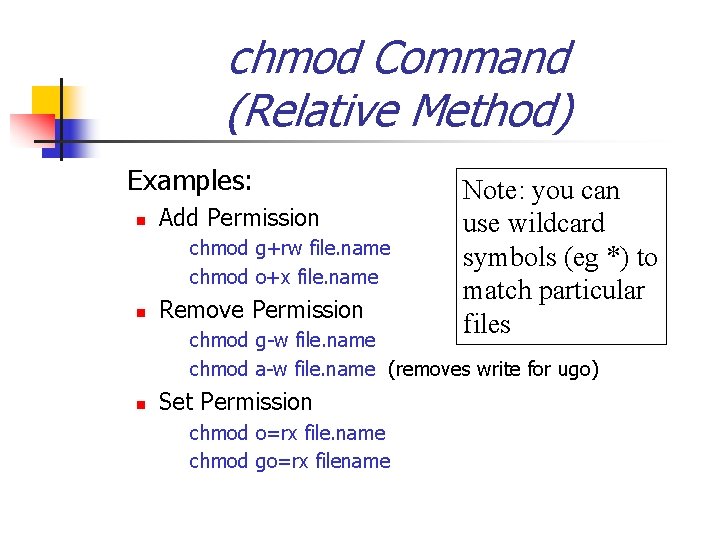
Linking Files There are two major types of links: Hard Link: ln [existing_file] [linked_file] A directory entry containing the same “i-node number” of a file. All files have at least one hardlink - when removed, the link is removed Symbolic Link: ln -s [existing_file] [linked_file] n A directory entry containing pathname to file (i. e. a pointer). Unlike hard links, i-node numbers can be different, but possess other useful features. n

Linking Files n Remember to set appropriate permissions for: n n your directories (such as pass-through permissions and permissions for appropriate directory) the file to link (which groups can modify the link file, which groups can view, but not modify file, and which groups are not permitted to modify or view linked file)

Hard Link Features n n Cannot make hard links to directories Cannot cross different file systems (since other file system may use i-node number for a already existing file…) User can allow access to file to link via directory access permissions and will still allow access if user later block group & other access. When “original file” that other user’s linked to is removed “linked file(s)’ will still exist.

Soft Link Features n n n Can be used by users to link directories Can link across different file systems since they are considered to be “pointers” “Broken Links” can occur if original file is removed and link “points” to a file that does not exist.