Advances in Hardware Security Prof K K Mahapatra















- Slides: 33

Advances in Hardware Security Prof. K. K. Mahapatra NIT Rourkela Workshop on Recent Trends in VLSI Design NIT Arunachal Pradesh

OUTLINE Ø Introduction Ø Widely discussed topics in Hardware Security Ø Secure Split Test Technique. Ø Future Directions and conclusion

Introduction • The effect of globalization has led to significant changes in semiconductor design process and manufacturing in last two decades. The major changes observed are: - • • Ø Dependence on the third party IP (Intellectual Property) core vendors for different functionalities, who are specialized in that application domain is increased. Ø Dependence on contract manufacturers (like TSMC, Global foundries etc) to manufacture the chips and Outsourced Assembly and Test (OSAT) centres for Assembly, Packaging and Test. Fabless So. C design houses completely depend upon contract manufacturers and OSAT centres for production operations. Ø Dependence on service providers and consultants involve in a design process like verification, post silicon validation etc is a common phenomenon. The above mentioned changes have led to a fragmentation of So. C design process and manufacturing across geographies. The third party IP core vendors, contract manufacturers and service providers locate in different countries. This fragmented business model in both design process and semiconductor supply chain raise the several hardware security issues.

Topics in Hardware Security • • • Counterfeiting and Overbuilding of chips in a untrusted fabrication facility. IP Violations Hardware Trojans Test and Debug Security Different Side Channel attacks on Cryptographic cores and Sensitive assets of the So. C.

Side Channel Attacks (SCA) The very well known Side channel attacks are: • Power Analysis based SCA. • DFT/Test Infrastructure based SCA. • Timing Analysis based SCA. • Fault Attack based SCA. • Electromagnetic/LASER based SCA and • Multi-level Attacks (mix of above attacks). Designing different variety of countermeasures against all types of SCA can be found in research literature.

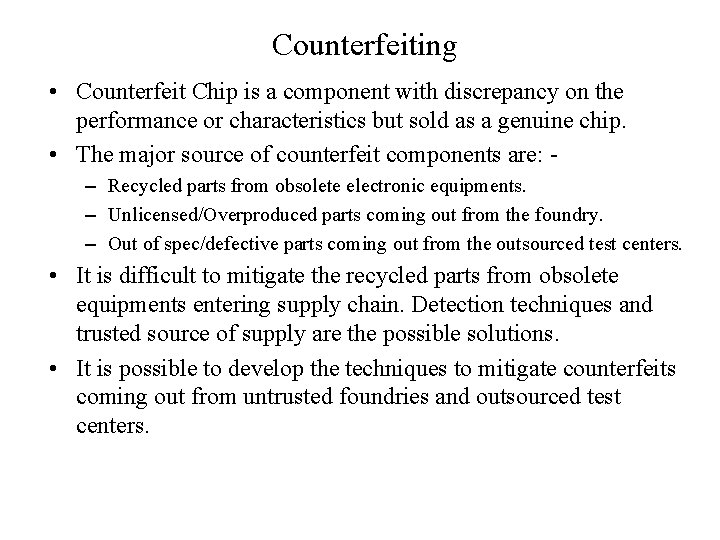
Counterfeiting • Counterfeit Chip is a component with discrepancy on the performance or characteristics but sold as a genuine chip. • The major source of counterfeit components are: – Recycled parts from obsolete electronic equipments. – Unlicensed/Overproduced parts coming out from the foundry. – Out of spec/defective parts coming out from the outsourced test centers. • It is difficult to mitigate the recycled parts from obsolete equipments entering supply chain. Detection techniques and trusted source of supply are the possible solutions. • It is possible to develop the techniques to mitigate counterfeits coming out from untrusted foundries and outsourced test centers.

Taxonomy and Detection Techniques to Identify Recycled Counterfeit Parts • Counterfeit Chip is a component with discrepancy on the performance or characteristics but sold as a genuine chip.

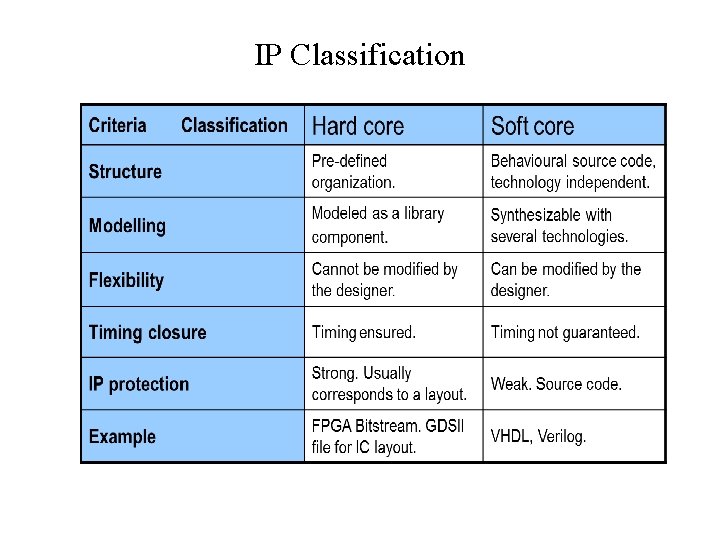
IP Cores • • Types of IP cores: Soft IP: - In HDL code Firm IP: - Synthesized Netlist for a target library (rarely used) Hard IP: - Physical Design IP (Layout)

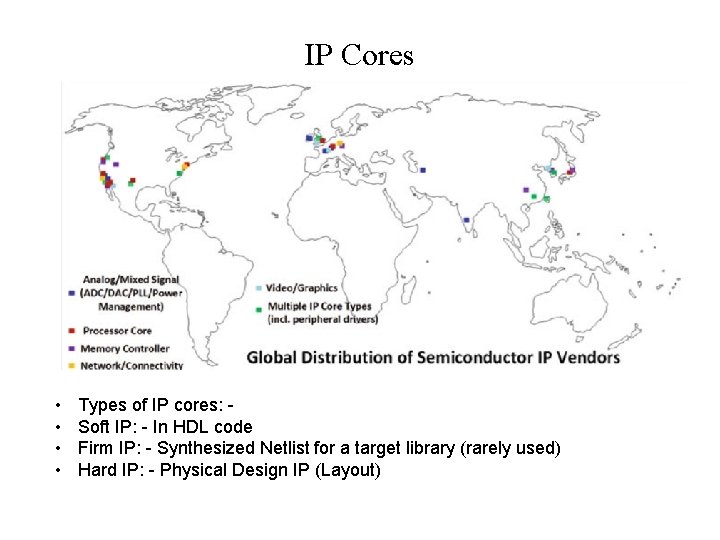
IP Classification

IP Protection Techniques • IP protection techniques are categorized as: Passive and Active techniques. • Passive Techniques: - Watermarking is widely discussed passive technique. Watermarking is based on timing or power signature. These techniques are useful to identify IP violations and litigations. • Active Techniques: - Functionality is unlocked when appropriate keys are applied. Only genuine customers will be provided with key. • IP protection during evaluation: - IP vendors allow potential customers to evaluate the functionality and specifications of IP products. The evaluation period is limited and specialized keys should be designed to lock the IP after evaluation period.

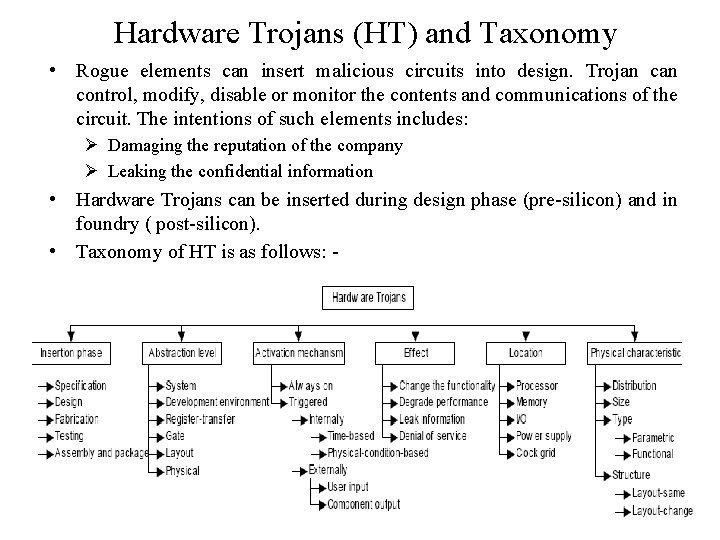
Hardware Trojans (HT) and Taxonomy • Rogue elements can insert malicious circuits into design. Trojan control, modify, disable or monitor the contents and communications of the circuit. The intentions of such elements includes: Ø Damaging the reputation of the company Ø Leaking the confidential information • Hardware Trojans can be inserted during design phase (pre-silicon) and in foundry ( post-silicon). • Taxonomy of HT is as follows: -

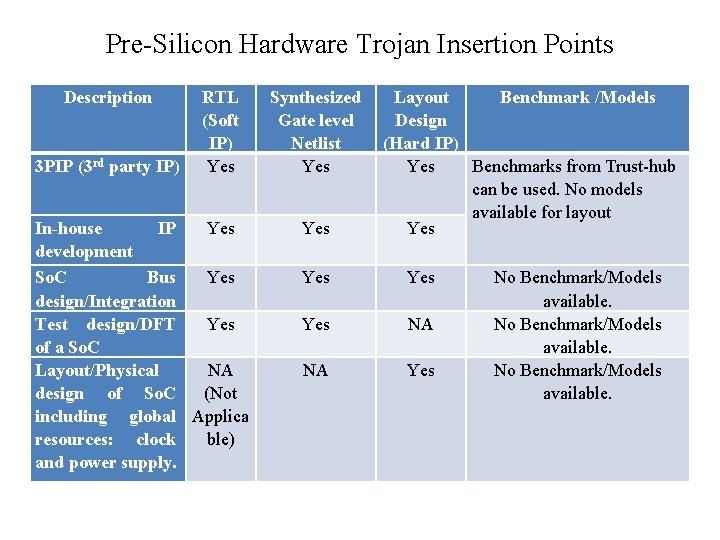
Pre-Silicon Hardware Trojan Insertion Points Description 3 PIP (3 rd party IP) RTL (Soft IP) Yes In-house IP Yes development So. C Bus Yes design/Integration Test design/DFT Yes of a So. C Layout/Physical NA design of So. C (Not including global Applica resources: clock ble) and power supply. Synthesized Gate level Netlist Yes Layout Benchmark /Models Design (Hard IP) Yes Benchmarks from Trust-hub can be used. No models available for layout Yes Yes NA NA Yes No Benchmark/Models available.

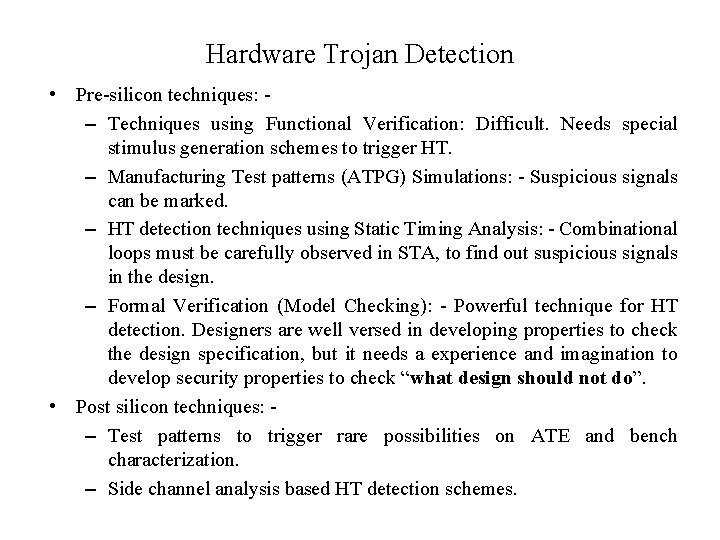
Hardware Trojan Detection • Pre-silicon techniques: – Techniques using Functional Verification: Difficult. Needs special stimulus generation schemes to trigger HT. – Manufacturing Test patterns (ATPG) Simulations: - Suspicious signals can be marked. – HT detection techniques using Static Timing Analysis: - Combinational loops must be carefully observed in STA, to find out suspicious signals in the design. – Formal Verification (Model Checking): - Powerful technique for HT detection. Designers are well versed in developing properties to check the design specification, but it needs a experience and imagination to develop security properties to check “what design should not do”. • Post silicon techniques: – Test patterns to trigger rare possibilities on ATE and bench characterization. – Side channel analysis based HT detection schemes.

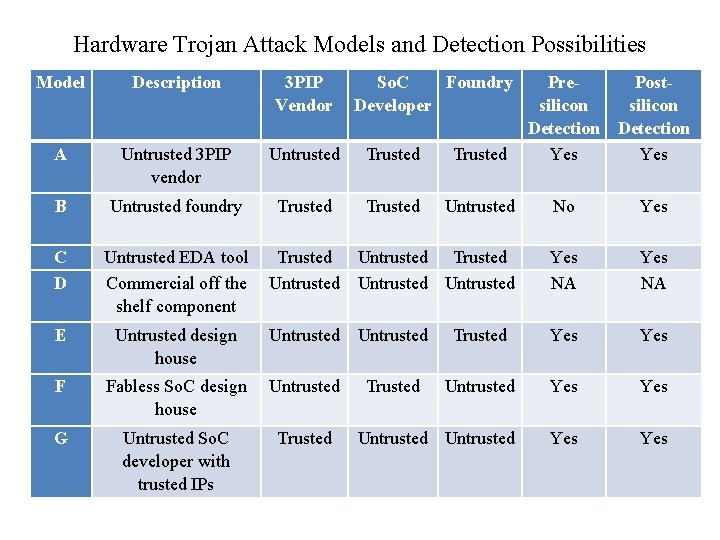
Hardware Trojan Attack Models and Detection Possibilities Model Description 3 PIP Vendor So. C Foundry Developer A Untrusted 3 PIP vendor Untrusted Trusted B Untrusted foundry Trusted Untrusted No Yes C D Untrusted EDA tool Commercial off the shelf component Trusted Untrusted Yes NA E Untrusted design house Untrusted Trusted Yes F Fabless So. C design house Untrusted Yes G Untrusted So. C developer with trusted IPs Trusted Untrusted Yes Trusted Pre. Postsilicon Detection Yes

Hardware Trojan Defense • There is a good possibility that HT will go undetected in both presilicon and post-silicon detection techniques. On-field defense against HT is important. • Currently Hardware Trojan defense is based on following: – Securing the crucial assets like program counter, Digital Rights Management (DRM) keys in the Microcontroller (So. C) etc. – Security during booting. – Access Control (confidential memory and crucial assets) – Information flow tracking

Test and Debug Security • • • In current So. C designs, corner case issues like clock domain crossing, cross talk, power droop and thermal stress identified during post-silicon validation are difficult to simulate using pre-silicon verification techniques. The recent advancements in post silicon debugging are able to find highly sophisticated errors and bugs in design by incorporating the on-chip instruments with better observability and controllability. Regular assertion checkers to monitor malfunction, silicon odometers to monitor aging and workload monitors are placed at appropriate locations to collect data. Access to these instruments in unsafe environments will compromise the security of So. C design house, application developer and end user. So test and debug security is important. Solution: - Cryptographic techniques are used secure the test and debug instruments access. Developing advanced techniques to secure the rights of all stake holders in the supply chain (Design house, IP vendor, end user) is an open research problem.

Physical Unclonable Functions (PUF) • PUF circuits are well known hardware security primitives, which are useful in solving hardware security problems like: - counterfeiting, IP protection, test and debug security. • PUF produces a unique response for an input challenge. • The input challenge and corresponding response obtained from PUF circuit is called challenge-response pair (CRP). • The uniqueness in CRP’s for every chip produced comes from process variation, which is hidden and distinct. • The PUFs can be classified as: Strong PUFs and Weak PUFs. Ø Strong PUF: The PUF design with more number of CRPs are known as Strong PUFs are used in device authentication. Ex: - Ring oscillator PUF. Ø Weak PUF: The PUF design with less number of CRPs are known as Weak PUFs. These are used in cryptographic applications for key generation. Ex: - SRAM PUF

Physical Unclonable Functions (PUF) • The quality of PUF is decided by security properties: - uniqueness, uniformity and reliability. • Uniqueness is an ability of PUF to generate a unique response in a specific chip among the group of chips of same type for same challenge. • Uniqueness is measured using hamming distance. Inter-chip variation of PUF response is measured using uniqueness. An ideal value of uniqueness is 50%. • Reliability of PUF is ability to generate the same response, when same stimulus is applied repeatedly. The ideal value of reliability is 100%. Reliability of PUF CRP’s is affected by temperature, supply voltages and aging. • Uniformity of the PUF is an estimation of the proportion of 1’s and 0’s in the response of PUF. The ideal value of uniformity is 50%. Uniformity is calculated using percentage of the hamming weight of the response.

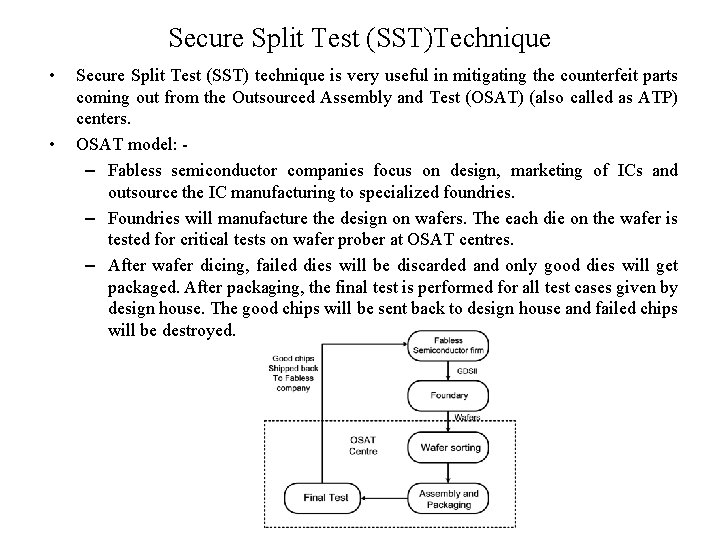
Secure Split Test (SST)Technique • • Secure Split Test (SST) technique is very useful in mitigating the counterfeit parts coming out from the Outsourced Assembly and Test (OSAT) (also called as ATP) centers. OSAT model: – Fabless semiconductor companies focus on design, marketing of ICs and outsource the IC manufacturing to specialized foundries. – Foundries will manufacture the design on wafers. The each die on the wafer is tested for critical tests on wafer prober at OSAT centres. – After wafer dicing, failed dies will be discarded and only good dies will get packaged. After packaging, the final test is performed for all test cases given by design house. The good chips will be sent back to design house and failed chips will be destroyed.

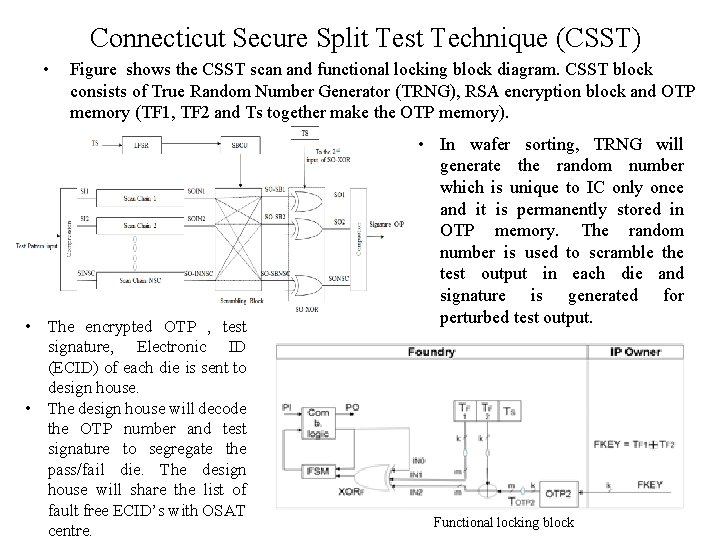
Connecticut Secure Split Test Technique (CSST) • Figure shows the CSST scan and functional locking block diagram. CSST block consists of True Random Number Generator (TRNG), RSA encryption block and OTP memory (TF 1, TF 2 and Ts together make the OTP memory). • The encrypted OTP , test signature, Electronic ID (ECID) of each die is sent to design house. • The design house will decode the OTP number and test signature to segregate the pass/fail die. The design house will share the list of fault free ECID’s with OSAT centre. • In wafer sorting, TRNG will generate the random number which is unique to IC only once and it is permanently stored in OTP memory. The random number is used to scramble the test output in each die and signature is generated for perturbed test output. Functional locking block

Connecticut Secure Split Test (CSST) • Wafers will be diced and only good dies will be packaged as chips. The output of final test, ECID of packaged parts is shared with design house. • Design house will determine the pass chips and release the functional key to OSAT centre will load the OTP with functional key. • Disadvantage of CSST: – Inclusion of few crucial functional tests in production test run is required to weed out faulty chips. – The CSST proposed can perform structural tests and does not support functional testing. During testing phase, no functional key is generated and key is required to unlock the XOR gates associated with functionality of chip. So functional testing is not possible in present CSST design.

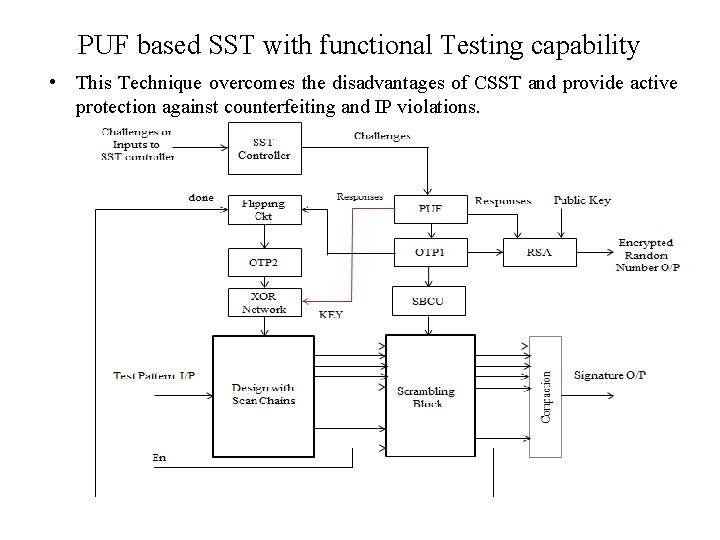
PUF based SST with functional Testing capability • This Technique overcomes the disadvantages of CSST and provide active protection against counterfeiting and IP violations.

PUF based SST with functional Testing capability • During wafer sorting, SST controller will drive the challenges to PUF circuit and responses are encrypted using RSA. Foundry/OSAT will send the challenges and corresponding encrypted responses and ECID’s of dies to design house. • Design house will decrypt the responses and store the challenge response pairs (CRP’s) in secure server. This PUF enrolment process is mandatory in this technique. • Design house will release the wafer sorting test program to OSAT centre with PUF CRP’s to functionally unlock the die for each ECID. And OSAT centre will run both structural and functional tests. Before executing the test cases, test program will pump in a given challenge to PUF through SST controller and response from the PUF will be written into OTP 1, which is used by scrambling logic. • Initial values stored in OTP 2 are all logic ‘ 0’. The input to XOR network from OTP 2 is logic ‘ 0’. XOR network will act like a buffer to PUF responses, which are used to unlock the functionality of design to perform functional testing. The encrypted number stored in OTP 1, test signatures and corresponding ECID’s will be sent to design house. Design house will determine the test result after decrypting the OTP 1 value and test signatures.

PUF based SST with functional Testing capability • The list of good dies is sent to OSAT centre for packaging. The same functional key (PUF CRP) can be used to unlock the chip and OSAT centre will perform both structural and functional tests. Test program will generate the ‘En’ signal after collecting all test case signatures. Scrambling block will generate ‘done’ signal and flipping circuit samples the OTP 1 value and write it into OTP 2. The XOR network will get different input from OTP 2 and KEY supplied with test program can’t be used to unlock the functionality of design. • OSAT centre will send the test signatures and corresponding device ECID’s to design house. The design house after decoding the test responses will send the list of good chips to OSAT centre and only good chips will enter open market. • A different PUF CRP is required to unlock the functionality of the chip, which design house will share with the customer with valid ECID.

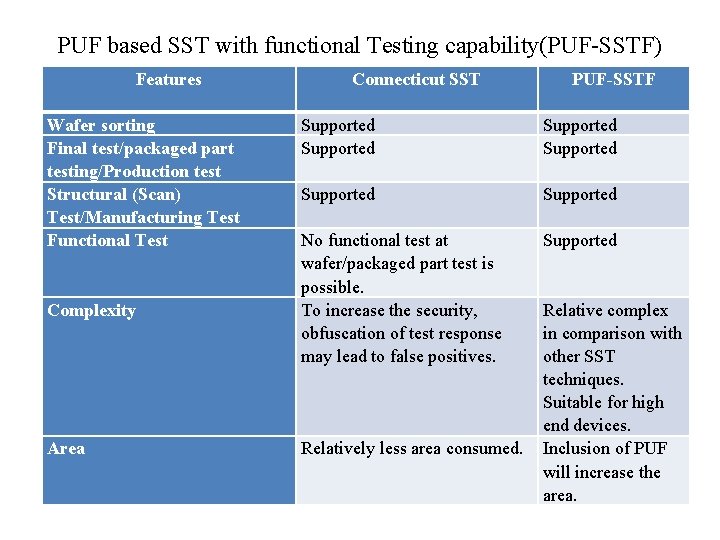
PUF based SST with functional Testing capability(PUF-SSTF) Features Wafer sorting Final test/packaged part testing/Production test Structural (Scan) Test/Manufacturing Test Functional Test Complexity Area Connecticut SST PUF-SSTF Supported Supported No functional test at wafer/packaged part test is possible. To increase the security, obfuscation of test response may lead to false positives. Supported Relatively less area consumed. Relative complex in comparison with other SST techniques. Suitable for high end devices. Inclusion of PUF will increase the area.

Internet of Things (Io. T) and its Challenges • The complete Io. T ecosystem consists of sensor and actuators, microcontrollers with modest processing and connectivity capabilities, network gateways and cloud computing. • The known challenges in an Io. T ecosystem are: - identification or authentication for addressing an Io. T node, choosing a right connectivity technique, maintaining data compliance across network and security. • The simple architecture of Io. T ecosystem contains edge nodes, gateways, network and cloud. • The edge nodes are generally powered by microcontrollers or System on Chip (So. C). • Edge nodes are connected to internet through gateways.

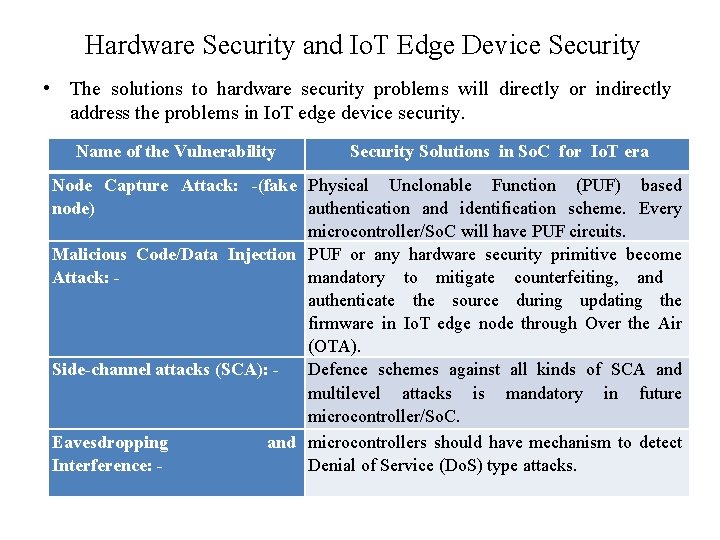
Io. T Edge Device Security The well known Io. T edge device security threats are: • Node Capture Attacks • Malicious Code Injection Attack • False Data Injection Attack • Side-channel attacks (SCA) • Sleep Deprivation Attacks • Denial of Service (Do. S) • Booting vulnerabilities • Hardware and Software Exploitation

Hardware Security and Io. T Edge Device Security • The solutions to hardware security problems will directly or indirectly address the problems in Io. T edge device security. Name of the Vulnerability Security Solutions in So. C for Io. T era Node Capture Attack: -(fake Physical Unclonable Function (PUF) based node) authentication and identification scheme. Every microcontroller/So. C will have PUF circuits. Malicious Code/Data Injection PUF or any hardware security primitive become Attack: mandatory to mitigate counterfeiting, and authenticate the source during updating the firmware in Io. T edge node through Over the Air (OTA). Side-channel attacks (SCA): Defence schemes against all kinds of SCA and multilevel attacks is mandatory in future microcontroller/So. C. Eavesdropping and microcontrollers should have mechanism to detect Interference: Denial of Service (Do. S) type attacks.

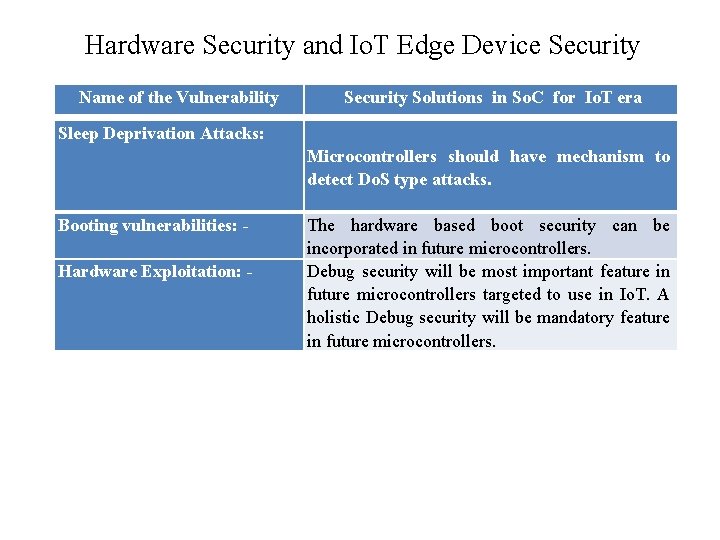
Hardware Security and Io. T Edge Device Security Name of the Vulnerability Security Solutions in So. C for Io. T era Sleep Deprivation Attacks: Microcontrollers should have mechanism to detect Do. S type attacks. Booting vulnerabilities: Hardware Exploitation: - The hardware based boot security can be incorporated in future microcontrollers. Debug security will be most important feature in future microcontrollers targeted to use in Io. T. A holistic Debug security will be mandatory feature in future microcontrollers.

Conclusions • Industry and Academia has recognized problems in hardware security are serious and working towards finding solutions to problems. • Security has became another tenet in chip design along with timing, power and area. • In next few years, security awareness in the every step of chip design flow will became mandatory. (especially in specs, design, verif, test and physical design). • The solutions to hardware security problems will directly or indirectly address the problems in Io. T edge device security.

References • • • [D. P. Sahoo, S. Saha, D. Mukhopadhyay, R. S. Charkraborty, H. Kapoor, “Composite PUF: A new design paradigm for Physically Unclonable Functions on FPGA”, IEEE International Symposium on Hardware-Oriented Security and Trust (HOST)-2014. Roel Maes, “Physical Unclonable Functions: Constructions, Properties and Applications”, Springer - Computer Science 2013. Y. Tamir and H. C. Chi, “Symmetric Crossbar Arbiters for VLSI Communication Switches”, IEEE Trans. On Parallel and Distributed Systems, Vol. 4, No. 1, 1993. “PCKS #1 v 2. 1: RSA Cryptography Standard”, ftp: //ftp. rsasecurity. com/pub/pkcs-1/pcks-1 v 2 -1. pdf, RSA Security-2002. Berk Sunar, “True Random Number Generators for Cryptography”, Cryptographic Engineering 2009. Mudit Bhargava, Carnegie Mellon University “Reliable, Secure, Efficient Physical Unclonable Functions” http: //repository. cmu. edu/dissertations/238/ Sauvagya Ranjan Sahoo et, al “A Modified Configurable RO PUF with Improved Security Metrics”, IEEE International Symposium on Nanoelectronic and Information Systems-INIS-2015. Urbi Chatterjee et, al “A PUF-based Secure Communication Protocol for Io. T” ACM Transactions on Embedded Computing Systems, https: //eprint. iacr. org/2016/674. pdf. Jiliang Zhang et, al, “Design and Implementation of a Delay-Based PUF for FPGA IP Protection, ” International Conference on Computer-Aided Design and Computer Graphics - 2013.

References • • • Mudit Bhargava et, al, “An efficient reliable PUF-based cryptographic key generator in 65 nm CMOS” IEEE Design, Automation & Test in Europe Conference & Exhibition (DATE)-2014. Farinaz Koushanfar, "Processor-Based Strong Physical Unclonable Functions with Aging. Based Response Tuning", IEEE Transactions on Emerging Topics in Computing, , no. 1, pp. 1, Pre. Prints, doi: 10. 1109/TETC. 2013. 2289385. Yu Zheng et, al “DScan. PUF: A Delay-Based Physical Unclonable Function Built Into Scan Chain” IEEE Transactions on Very Large Scale Integration (VLSI) Systems Volume: 24 , Issue: 3 , May 2015. Alessandro Cilardo et, al “Secure distribution infrastructure for hardware digital contents” IET Computers & Digital Techniques, Special Issue: Hardware Security-2014. Christopher Huth et al, “Secure Software Update and IP Protection for Untrusted Devices in the Internet of Things Via Physically Unclonable Functions” First IEEE International Workshop on Security, Privacy and Trust for Io. T, 2016. Sudeendra kumar K, K. K. Mahapatra, et, al, “Secure Split Test Techniques to prevent IC piracy in Io. T devices”, VLSI Integration, Elsevier, June-2017. Francisco da silva et al, “The core test wrapper handbook” Frontiers of Electronic Testing, Springer-2006. SPI Block User Guide, www. nxp. com/files/microcontrollers/doc/ref_manual/S 12 SPIV 4. pdf. Microchip PIC 16 F 84 Datasheet, ww 1. microchip. com/downloads/en/Device. Doc/35007 C. pdf.

Thank You