ADM 310 Microsofts Identity Management Strategy Addressing the





























- Slides: 51

ADM 310: Microsoft’s Identity Management Strategy Addressing the Myths of Single Sign On and the Enterprise Directory Paul Reiner Program Manager Directory Services

Agenda Origin of the species Microsoft’s solution for the intranet and extranet Futures

Origins of Digital Identity…

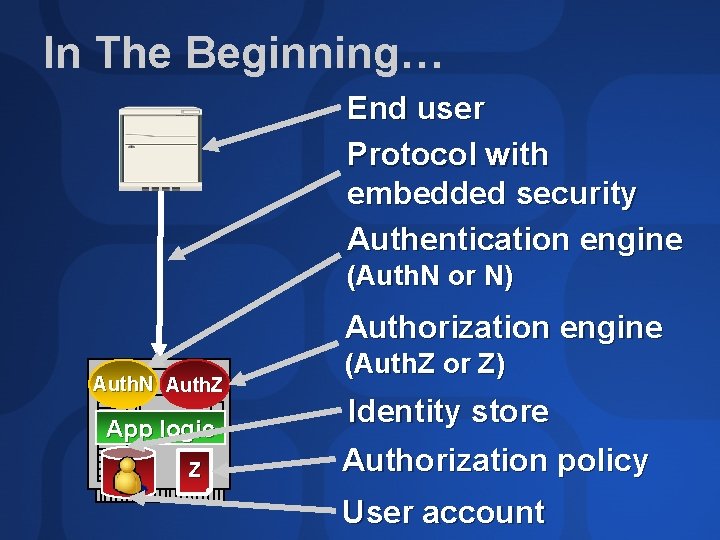
In The Beginning… End user Protocol with embedded security Authentication engine (Auth. N or N) Authorization engine Auth. N Auth. Z App logic Z (Auth. Z or Z) Identity store Authorization policy User account

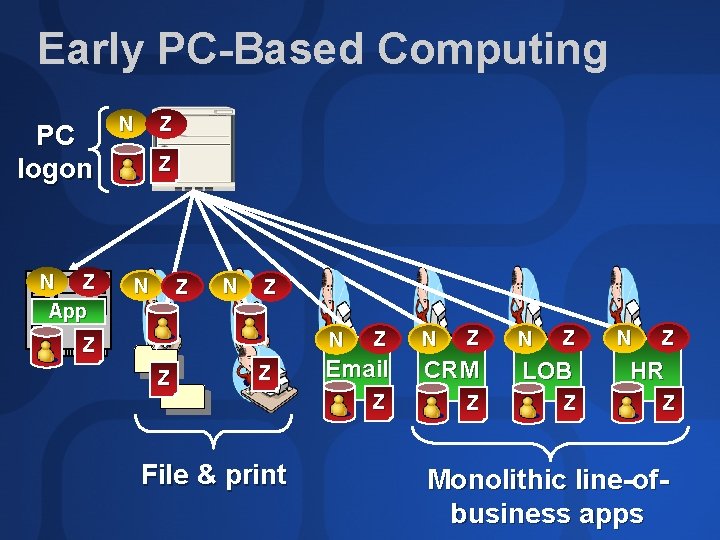
Early PC-Based Computing PC logon N Z App N Z Z N Z N Z Z Z File & print Z N Z Email CRM LOB Z Z Z N Z HR Z Monolithic line-ofbusiness apps

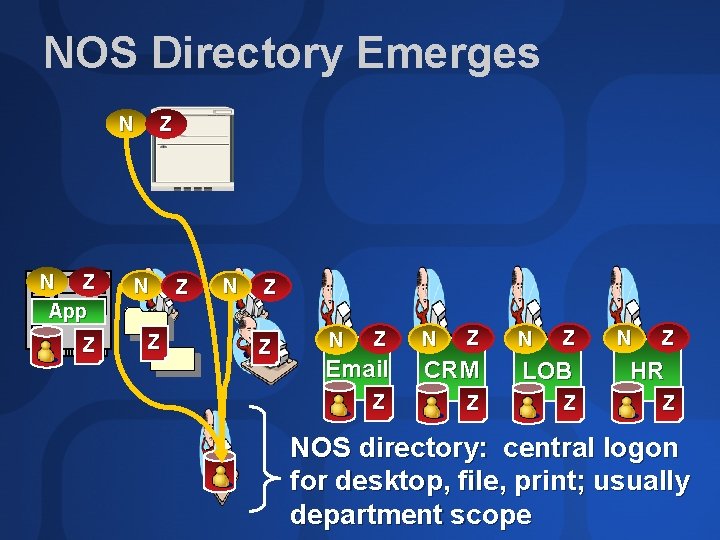
NOS Directory Emerges N N Z App Z Z N Z N Z Email CRM LOB Z Z Z N Z HR Z NOS directory: central logon for desktop, file, print; usually department scope

Assessment Multiple IDs and passwords per user Difficult to remember Inconsistent password/lockout policies Helpdesk password reset burden Identical user data in multiple stores Manually keyed, multiple times Data becomes inconsistent between stores over time Bottom line: managing environment is time and people intensive, expensive

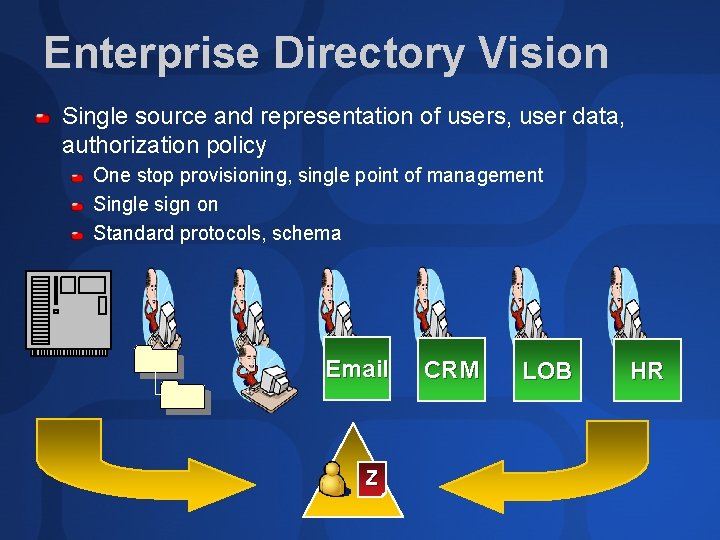
Enterprise Directory Vision Single source and representation of users, user data, authorization policy One stop provisioning, single point of management Single sign on Standard protocols, schema Email Z CRM LOB HR

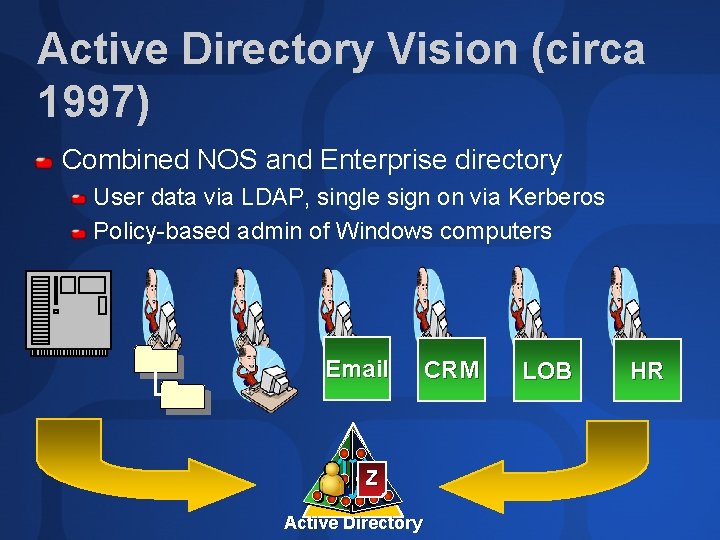
Active Directory Vision (circa 1997) Combined NOS and Enterprise directory User data via LDAP, single sign on via Kerberos Policy-based admin of Windows computers Email Z Active Directory CRM LOB HR

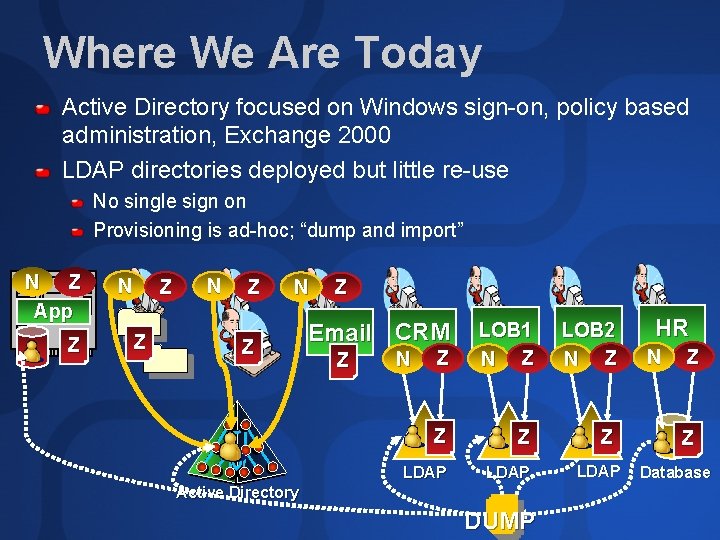
Where We Are Today Active Directory focused on Windows sign-on, policy based administration, Exchange 2000 LDAP directories deployed but little re-use No single sign on Provisioning is ad-hoc; “dump and import” N Z App Z N Z N Z Z Email CRM Z Z LOB 1 N Z LOB 2 N Z Z LDAP N Active Directory DUMP LDAP HR N Z Z Database

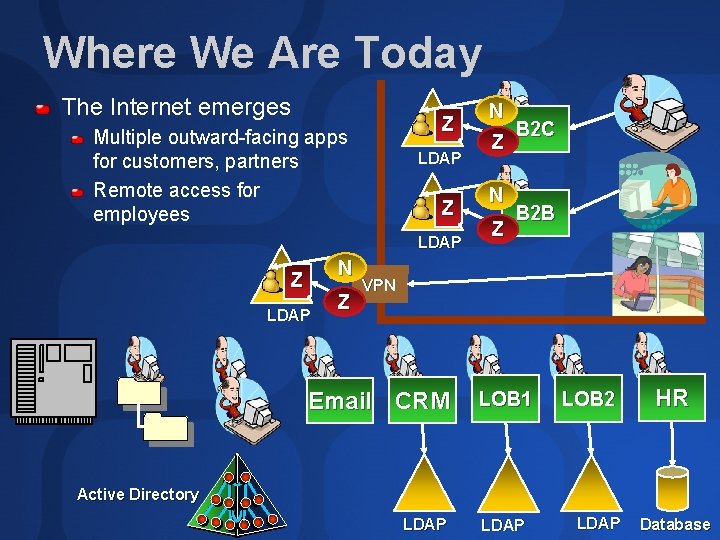
Where We Are Today The Internet emerges Z Multiple outward-facing apps for customers, partners Remote access for employees LDAP Z LDAP N Z LDAP Z N B 2 C Z N Z B 2 B VPN Email CRM LOB 1 LOB 2 HR Active Directory LDAP Database

How Did We Get Here? Business factors Push for rapid adoption of web technology put identity into portal apps Business drivers for speed outweighed drivers for enterprise directory Political factors Pushback on updating enterprise schema App owners want full accountability “I don’t want to unleash my corporate developers on my domain controllers”

How Did We Get Here? Technical factors No standard authentication protocol LDAP apps not easily retargeted Restrictions on data in central directory (size, volatility) Active Directory factors Not easy to install and experiment Uncertainty about version 1. 0 product

Assessment No improvement from initial situation Multiple IDs/passwords, error prone ad-hoc provisioning, delays to productivity, data inconsistencies, manpower intensive Situation is getting worse More line of business applications coming online every day Multiple directory implementations requiring different skill sets Customer, partner identities to manage

Assessment Demands on IT changing significantly Regulatory compliance and accountability Pressure to reduce costs across board Plus… Pressure to move at greater speed Establish service level agreements Improve security Enable new scenarios such as B 2 C, B 2 B Handle mergers, acquisitions, divestitures

Microsoft’s Identity Management Strategy and Solution

Framework Authentication Authorization & auditing Profile Lifecycle management & provisioning Federation Privacy

Authentication Minimize # of authentication systems Fewer accounts to disable on revoke Fewer pwd/lockout policies to manage Fewer passwords per user Fewer authenticating stores = increased security + lower costs Leverage workstation sign-on Present clear text password to as few systems as possible

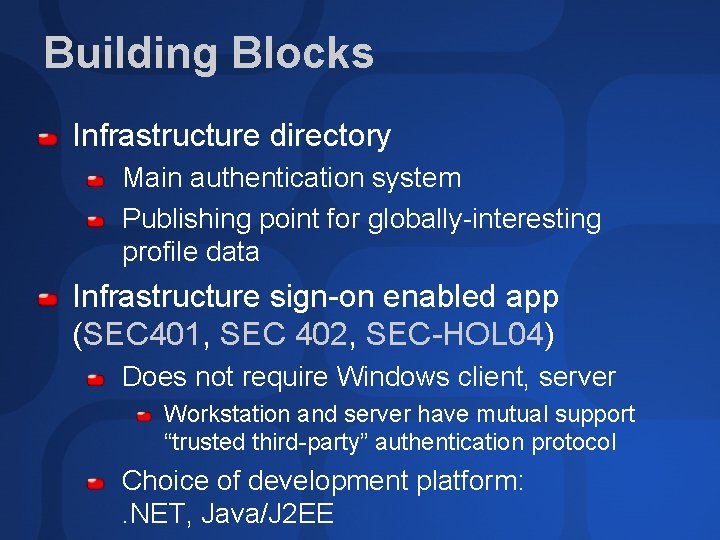
Building Blocks Infrastructure directory Main authentication system Publishing point for globally-interesting profile data Infrastructure sign-on enabled app (SEC 401, SEC 402, SEC-HOL 04) Does not require Windows client, server Workstation and server have mutual support “trusted third-party” authentication protocol Choice of development platform: . NET, Java/J 2 EE

Authentication 1. BE Workstation sign-on B 2 C B 2 B N VPN Web app Infrastructure Directory (AD) 2. Access infrastructure sign-on enabled app no additional sign-on to application HR LOB 4 3 rd party LDAP LOB 5 3 rd party LDAP LOB 1 LOB 2 LOB 3

Active Directory as Infrastructure Directory Scales out to thousands of remote locations across slow WAN links (WIN 310) Multiple standard authentication protocols: Kerberos, SSL Multiple credential types: passwords, smartcards, biometrics Federation between business units using trusts between forests Additional role of policy-based administration of Windows computers

Active Directory in Windows Server 2003 Increased flexibility during, after deployment Domain rename Schema redefine Cross-forest transitive trust Scaling, replication, performance improvements Per-value replication of group membership No more 5000 direct member limit for groups Topology generator supports 5000 sites No-GC logon for branch offices Fast replica creation (from media) GCs do not full sync when adding attributes to GC partial attribute set Simple upgrade from Windows 2000; improved ADMT v 2. 0 migration tool for Windows NT 4. 0

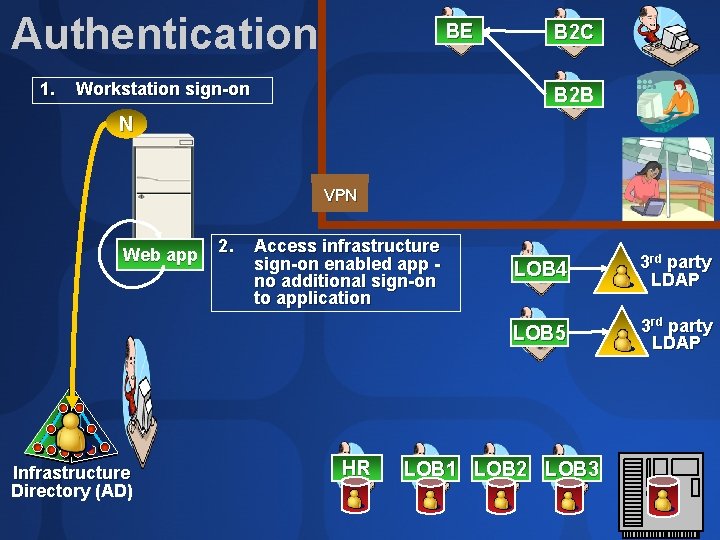
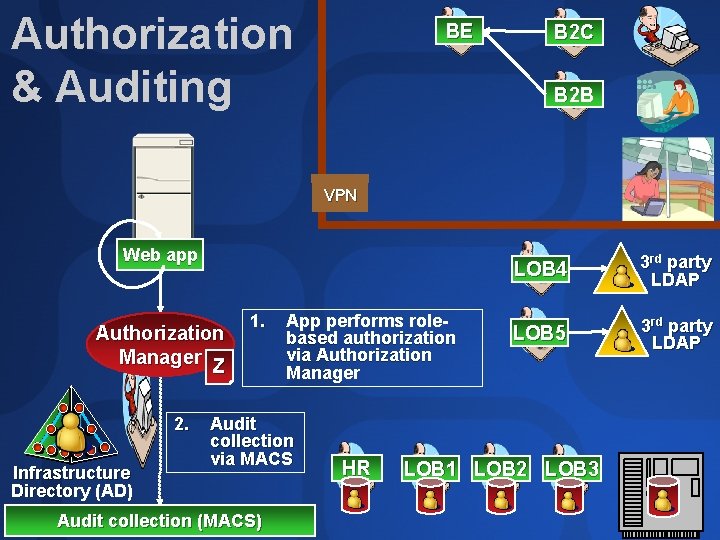
Authorization & Auditing BE B 2 C B 2 B VPN Web app Authorization Manager Z 2. Infrastructure Directory (AD) 1. App performs rolebased authorization via Authorization Manager Audit collection via MACS Audit collection (MACS) HR LOB 4 3 rd party LDAP LOB 5 3 rd party LDAP LOB 1 LOB 2 LOB 3

Authorization Manager (SEC 401) Manage roles, not object ACLs Simplify entitlement reporting & auditing Query-based groups capture business dynamics – users do not need to be specifically provisioned at application API supplied in Windows Server 2003

Auditing Microsoft Audit Collection System (MACS) Fast & secure collection of security events to central SQL database Events normalized & schematized for flexible query Real-time intrusion detection from collector or at-need reporting from database Beta 2 release during Tech. Ed, ship final at same time as Windows Server 2003 SP 1 Free download, licensed as part of Windows

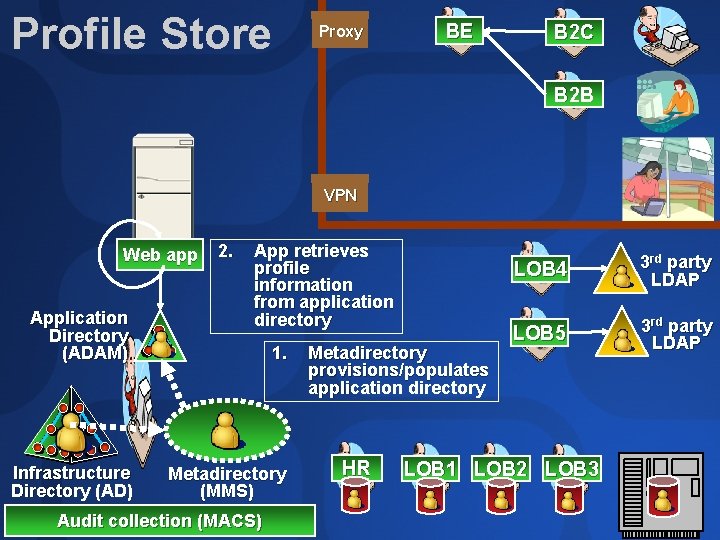
Profile Factor profile data into global and applicationspecific parts Global part: small, centrally-controlled schema shared by multiple applications Application part: app-specific schema Avoid schema bottleneck of enterprise directory Store profile data in app-specific directory App owner has full accountability for availability Reduce concerns over applications disrupting infrastructure

Profile Store Proxy BE B 2 C B 2 B VPN Web app Application Directory (ADAM) Infrastructure Directory (AD) 2. App retrieves profile information from application directory 1. Metadirectory (MMS) Audit collection (MACS) Metadirectory provisions/populates application directory HR LOB 4 3 rd party LDAP LOB 5 3 rd party LDAP LOB 1 LOB 2 LOB 3

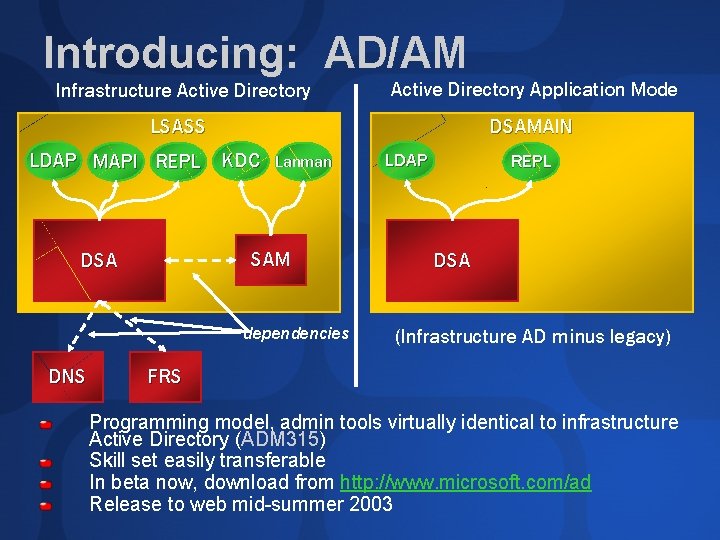
Introducing: AD/AM Infrastructure Active Directory Application Mode LSASS DSAMAIN LDAP MAPI REPL KDC Lanman SAM DSA dependencies DNS LDAP REPL DSA (Infrastructure AD minus legacy) FRS Programming model, admin tools virtually identical to infrastructure Active Directory (ADM 315) Skill set easily transferable In beta now, download from http: //www. microsoft. com/ad Release to web mid-summer 2003

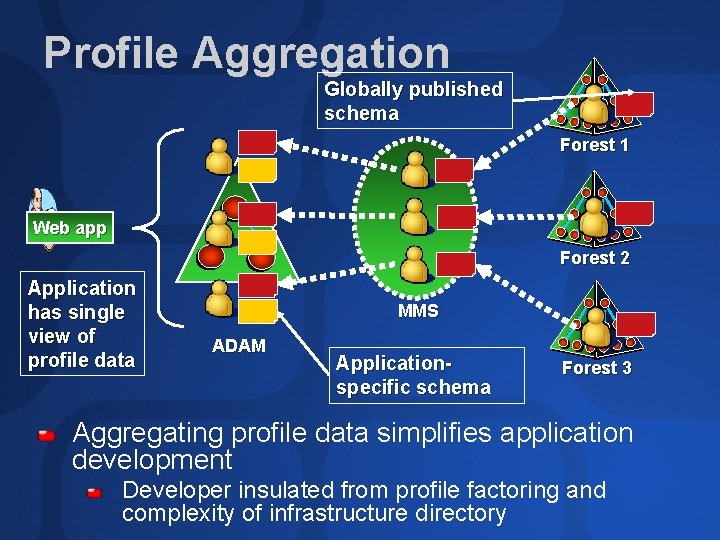
Profile Aggregation Globally published schema Forest 1 Web app Forest 2 Application has single view of profile data MMS ADAM Applicationspecific schema Forest 3 Aggregating profile data simplifies application development Developer insulated from profile factoring and complexity of infrastructure directory

Authentication Extend infrastructure-based sign-on to existing applications Enterprise Application Integration (EAI): front end app calls into multiple back end apps “Proxy-based authentication”: infrastructure sign-on mapped to credentials in back end app Leverage workstation sign-on Building blocks Share. Point Portal Server v 2 (OFC 333) Biz. Talk 2004 (EBZ 305) Host Integration Server 2004 (EBZ 305)

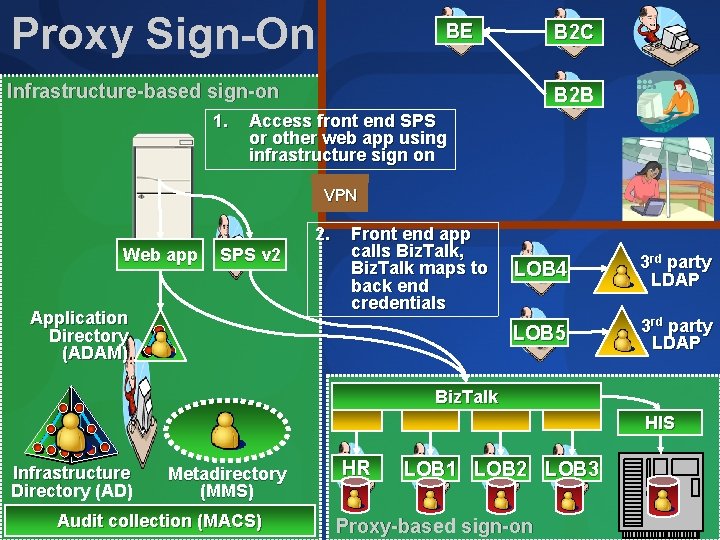
Proxy Sign-On BE B 2 C Infrastructure-based sign-on 1. B 2 B Access front end SPS or other web app using infrastructure sign on VPN 2. Web app SPS v 2 Application Directory (ADAM) Front end app calls Biz. Talk, Biz. Talk maps to back end credentials LOB 4 3 rd party LDAP LOB 5 3 rd party LDAP Biz. Talk HIS Infrastructure Directory (AD) Metadirectory (MMS) Audit collection (MACS) HR LOB 1 LOB 2 LOB 3 Proxy-based sign-on

Authentication If EAI-type methods not appropriate, fall back to application sign-on Requires user to do multiple sign-ons Clear text password exposed to app “Single password” approach to reduce # of passwords user has to remember ADAM with bind-redirect Metadirectory for password management (programmatically extensible)

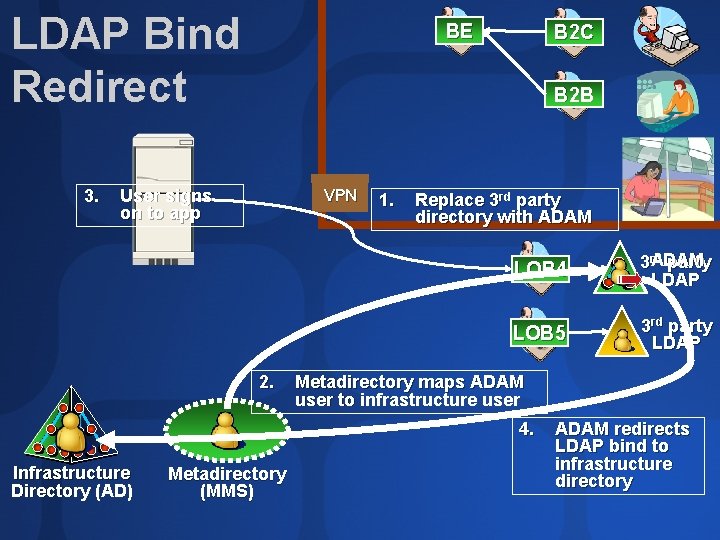
LDAP Bind Redirect 3. BE B 2 C B 2 B User signs on to app VPN 2. 1. Replace 3 rd party directory with ADAM LOB 4 ADAM 3 rd party LDAP LOB 5 3 rd party LDAP Metadirectory maps ADAM user to infrastructure user 4. Infrastructure Directory (AD) Metadirectory (MMS) ADAM redirects LDAP bind to infrastructure directory

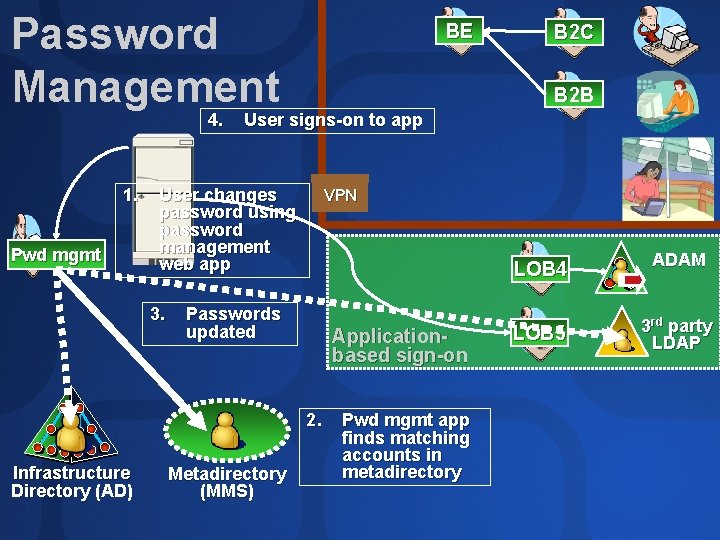
Password Management 4. 1. Pwd mgmt BE B 2 B User signs-on to app User changes password using password management web app 3. VPN Passwords updated Applicationbased sign-on 2. Infrastructure Directory (AD) B 2 C Metadirectory (MMS) Pwd mgmt app finds matching accounts in metadirectory LOB 4 ADAM LOB 5 3 rd party LDAP

Lifecycle Management Automate with metadirectory (ADM 311, SEC-HOL 03) Join identities from multiple stores to create single consistent view If same data appears in multiple stores, get data from authoritative source, sync where needed Rule-based provisioning/de-provisioning Automate processes in “hire/fire” scenario Group management Rule-based group membership Sync groups across identity stores

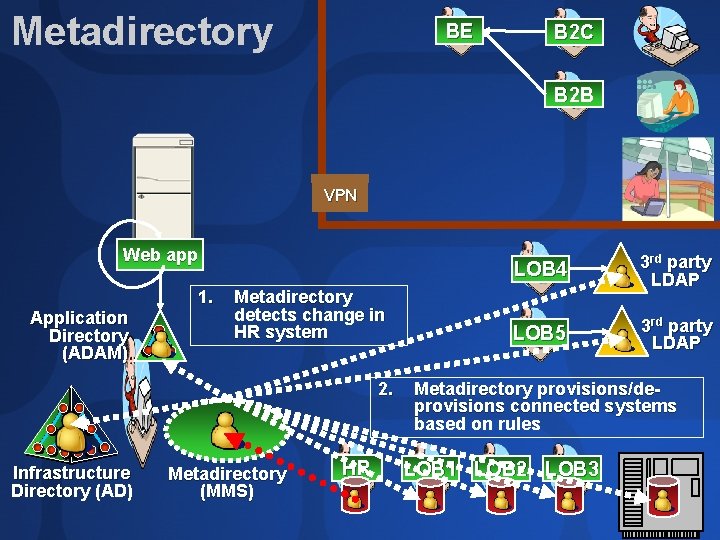
Metadirectory BE B 2 C B 2 B VPN Web app 1. Application Directory (ADAM) Metadirectory detects change in HR system 2. Infrastructure Directory (AD) Metadirectory (MMS) HR LOB 4 3 rd party LDAP LOB 5 3 rd party LDAP Metadirectory provisions/deprovisions connected systems based on rules LOB 1 LOB 2 LOB 3

Lifecycle Management Cost savings Reduce lost productivity while new employee waits for access Reduce # of hands and time spent touching process Improved security Immediate revocation of access when user status changes Disable account on termination Remove from rule-based group on job change

Microsoft Metadirectory Services 2003 Emphasis on transparency: data lineage, preview, statistics/logging Leverage familiar technology Visual Studio. NET for development SQL Server 2000 store Easily extend to enable simple workflow Integrate with Biz. Talk 2004 for complex workflow Password management capability Release mid-summer 2003

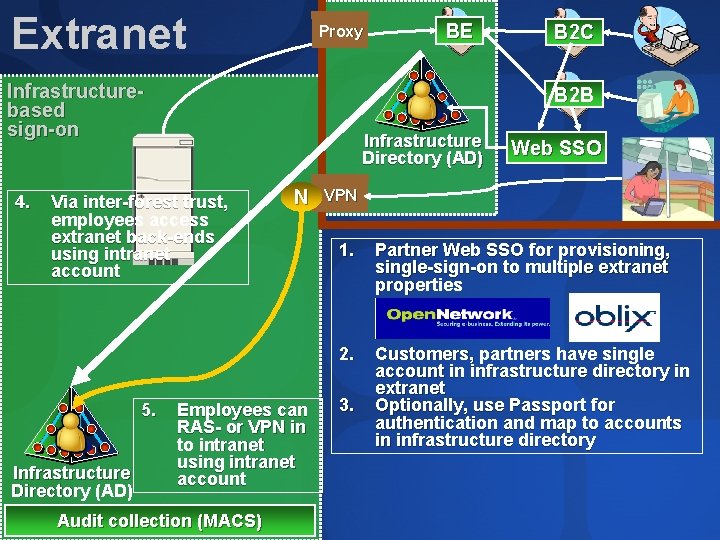
Extranet Proxy Infrastructurebased sign-on 4. Infrastructure Directory (AD) B 2 C B 2 B Infrastructure Directory (AD) Via inter-forest trust, employees access extranet back-ends using intranet account 5. BE N Employees can RAS- or VPN in to intranet using intranet account Audit collection (MACS) Web SSO VPN 1. Partner Web SSO for provisioning, single-sign-on to multiple extranet properties 2. Customers, partners have single account in infrastructure directory in extranet Optionally, use Passport for authentication and map to accounts in infrastructure directory 3.

Getting From Here to There… a Suggested Approach

Suggested Approach 1. Assign identity management owner Create identity management project Establish lines of communication Investigate cost and security impacts, create business case Start small, get wins up front 2. 3. Establish policy: new applications must leverage infrastructure sign-on Investigate if existing applications can be converted to infrastructure sign-on

Suggested Approach 3. Deploy metadirectory Join users, establish attribute flow Clean up environment 4. 5. 6. Deploy password management Deploy automated provisioning and deprovisioning Revisit existing applications 1. 2. Deploy ADAM with bind-redirect Use EAI to extend infrastructure sign-on

The Future




The Future Web Services Security (WEB 311) Enhanced identity programming model Reduce need to understand esoteric DS protocols and APIs Leverage knowledge of existing programming model and tools Improved manageability Role-based access control Seamless user move between forests

Summary Identity management essential part of business strategy Highly leveraged – simultaneously increase security and productivity while reducing costs Competitive advantage - quickly enable new scenarios, business opportunities Microsoft and partners deliver complete solution Flexibility beyond the enterprise directory Cross-platform capable

Community Resources http: //www. microsoft. com/communities/default. mspx Most Valuable Professional (MVP) http: //www. mvp. support. microsoft. com/ Newsgroups Converse online with Microsoft Newsgroups, including Worldwide http: //www. microsoft. com/communities/newsgroups/default. mspx User Groups Meet and learn with your peers http: //www. microsoft. com/communities/usergroups/default. mspx

evaluations

© 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.