Accurate RealTime Identification of IP Prefix Hijacking Xin







- Slides: 36

Accurate Real-Time Identification of IP Prefix Hijacking Xin Hu Z. Morley Mao 2007 IEEE Symposium on Security and Privacy Oakland, California

Outline n Introduction n Taxonomy of IP prefix hijacking n Proposed approach of combining control and data plane information n Implementation and results n Conclusion IEEE Symposium on Security and Privacy May 2007 2

Outline n Introduction n Taxonomy of IP prefix hijacking n Proposed approach of combining control and data plane information n Implementation and results n Conclusion IEEE Symposium on Security and Privacy May 2007 3

IP prefix hijacking n Fraudulent origin attack n Steal IP prefixes belonging to other networks n Announce unauthorized prefixes through BGP n Can also result from network misconfiguration IEEE Symposium on Security and Privacy May 2007 4

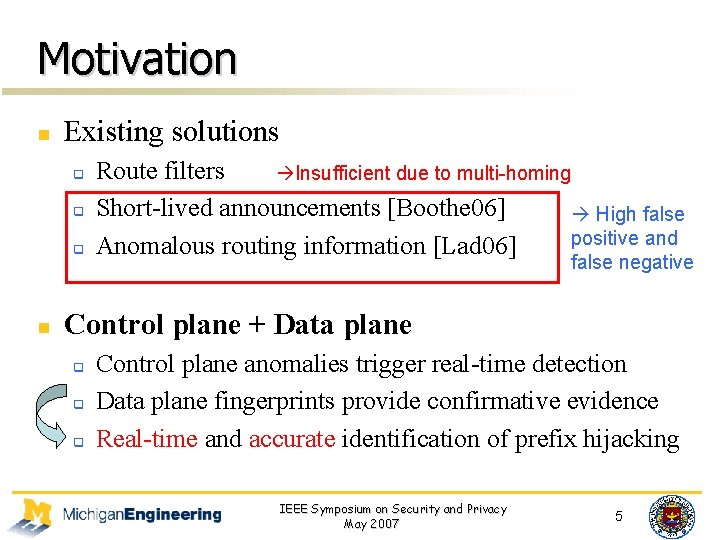
Motivation n Existing solutions q q q n Route filters Insufficient due to multi-homing Short-lived announcements [Boothe 06] High Solelyfalse rely on Control positive and Anomalous routing information [Lad 06] planenegative false Control plane + Data plane q q q Control plane anomalies trigger real-time detection Data plane fingerprints provide confirmative evidence Real-time and accurate identification of prefix hijacking IEEE Symposium on Security and Privacy May 2007 5

Outline n Introduction n Taxonomy of IP prefix hijacking n Proposed approach of combining control and data plane information n Implementation and results n Conclusion IEEE Symposium on Security and Privacy May 2007 6

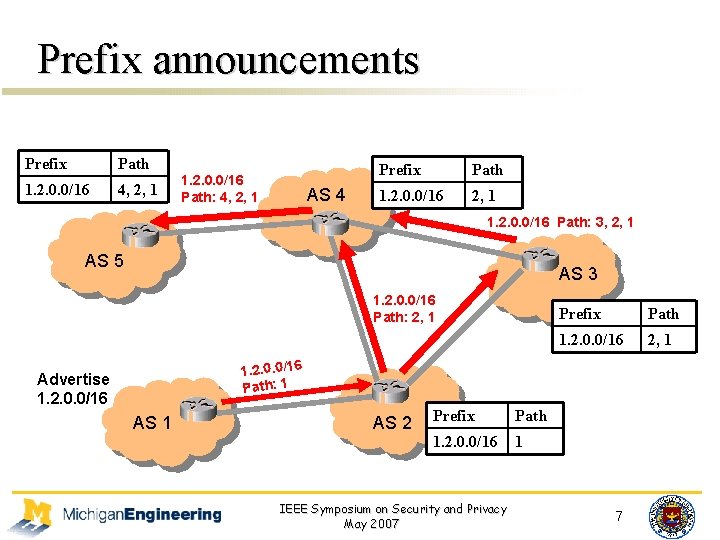
Prefix announcements Prefix Path 1. 2. 0. 0/16 4, 2, 1 1. 2. 0. 0/16 Path: 4, 2, 1 AS 4 Prefix Path 1. 2. 0. 0/16 2, 1 1. 2. 0. 0/16 Path: 3, 2, 1 AS 5 AS 3 1. 2. 0. 0/16 Path: 2, 1 Prefix Path 1. 2. 0. 0/16 2, 1 1. 2. 0. 0/16 Path: 1 Advertise 1. 2. 0. 0/16 AS 1 AS 2 Prefix Path 1. 2. 0. 0/16 1 IEEE Symposium on Security and Privacy May 2007 7

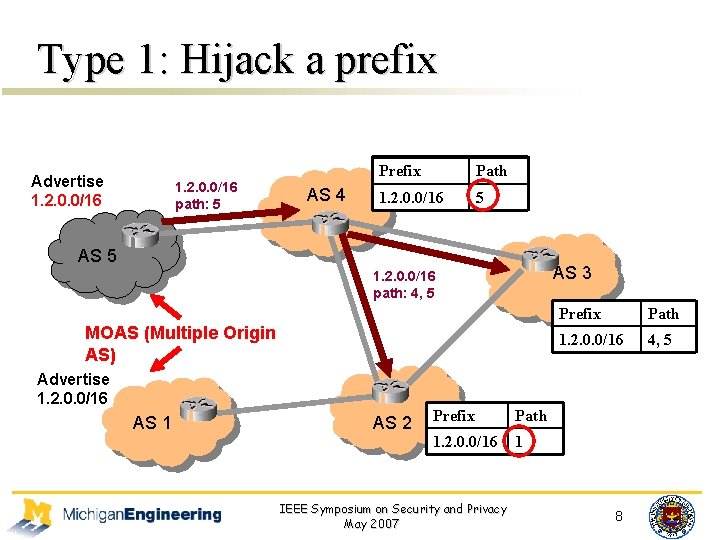
Type 1: Hijack a prefix Advertise 1. 2. 0. 0/16 path: 5 AS 4 Prefix Path 1. 2. 0. 0/16 2, 5 1 AS 5 AS 3 1. 2. 0. 0/16 path: 4, 5 MOAS (Multiple Origin AS) Advertise 1. 2. 0. 0/16 AS 1 AS 2 Prefix Path 1. 2. 0. 0/16 1 IEEE Symposium on Security and Privacy May 2007 Prefix Path 1. 2. 0. 0/16 2, 51 4, 8

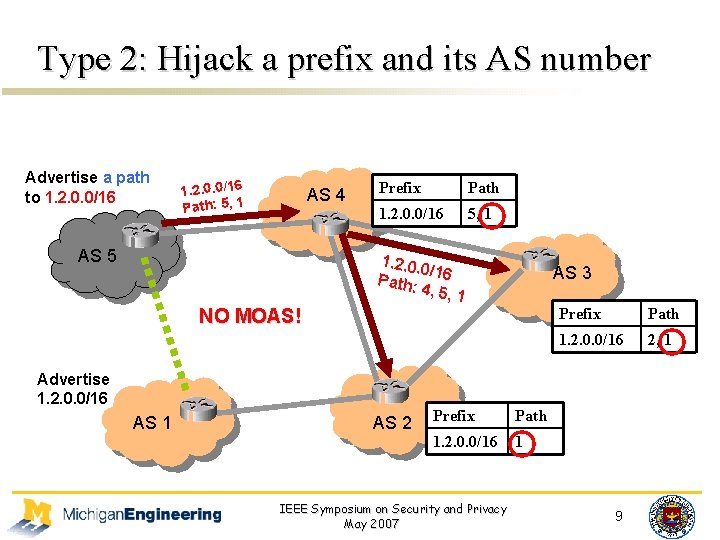
Type 2: Hijack a prefix and its AS number Advertise a path to 1. 2. 0. 0/16 Path: 5, 1 AS 4 AS 5 Prefix Path 1. 2. 0. 0/16 2, 1 5, 1. 2. 0. 0/ Path: 16 4, 5, 1 AS 3 NO MOAS! Advertise 1. 2. 0. 0/16 AS 1 AS 2 Prefix Path 1. 2. 0. 0/16 1 IEEE Symposium on Security and Privacy May 2007 Prefix Path 1. 2. 0. 0/16 2, 1 9

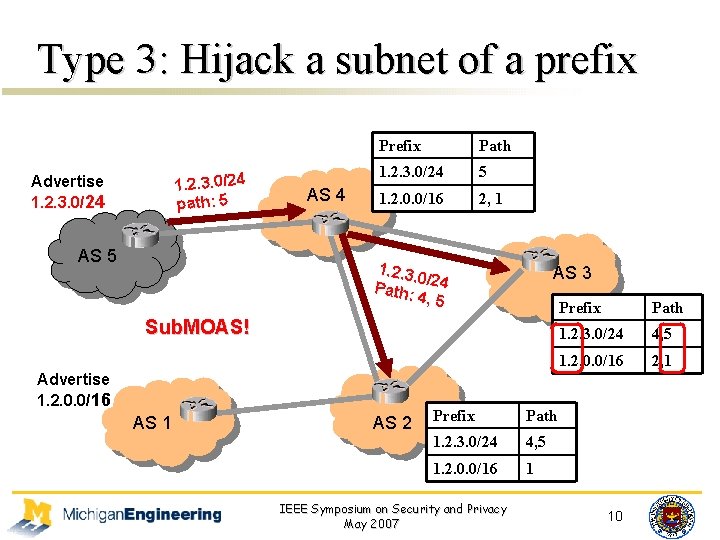
Type 3: Hijack a subnet of a prefix 1. 2. 3. 0/24 path: 5 Advertise 1. 2. 3. 0/24 AS 5 AS 4 Prefix 1. 2. 3. 0/24 1. 2. 0. 0/16 Path 5 2, 1 1. 2. 3. 0/ Path: 24 4, 5 AS 3 Sub. MOAS No MOAS!! Advertise 1. 2. 0. 0/16 AS 1 AS 2 Prefix Path 1. 2. 0. 0/16 1. 2. 3. 0/24 14, 5 1. 2. 0. 0/16 1 IEEE Symposium on Security and Privacy May 2007 Prefix 1. 2. 3. 0/24 1. 2. 0. 0/16 Path 4, 5 2, 1 1. 2. 0. 0/16 2, 1 10

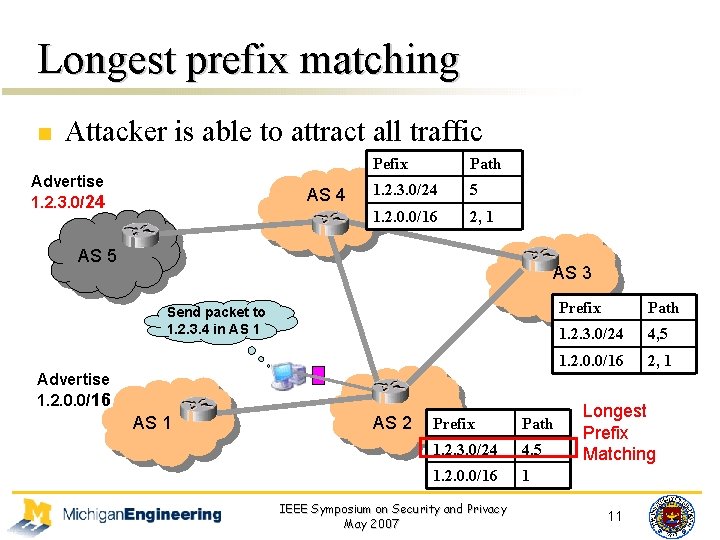
Longest prefix matching n Attacker is able to attract all traffic Advertise 1. 2. 3. 0/24 AS 4 Pefix Path 1. 2. 3. 0/24 5 1. 2. 0. 0/16 2, 1 AS 5 AS 3 Send packet to 1. 2. 3. 4 in AS 1 Prefix Path 1. 2. 0. 0/16 1. 2. 3. 0/24 2, 4, 5 1 1. 2. 0. 0/16 Advertise 1. 2. 0. 0/16 AS 1 AS 2 Prefix Path 1. 2. 3. 0/24 4, 5 1. 2. 0. 0/16 1 IEEE Symposium on Security and Privacy May 2007 2, 1 Longest Prefix Matching 11

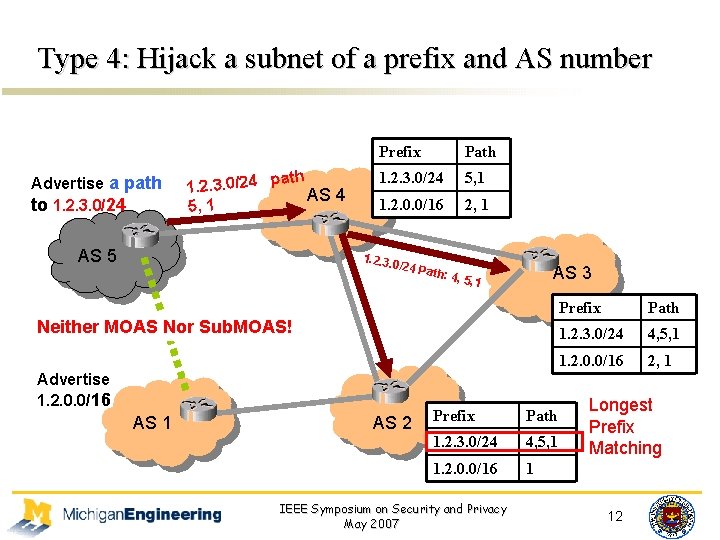
Type 4: Hijack a subnet of a prefix and AS number Advertise a path to 1. 2. 3. 0/24 path 1. 2. 3. 0/24 AS 4 5, 1 AS 5 Prefix 1. 2. 3. 0/24 Path 5, 1 1. 2. 0. 0/16 2, 1 1. 2. 3. 0/24 P AS 3 ath: 4 , 5, 1 Neither MOAS Nor Sub. MOAS! Advertise 1. 2. 0. 0/16 AS 1 AS 2 Prefix Path 1. 2. 0. 0/16 1. 2. 3. 0/24 14, 5, 1 1. 2. 0. 0/16 IEEE Symposium on Security and Privacy May 2007 Prefix 1. 2. 3. 0/24 1. 2. 0. 0/16 Path 4, 5, 1 2, 1 1. 2. 0. 0/16 2, 1 Longest Prefix Matching 1 12

Outline n Introduction n Taxonomy of IP prefix hijacking n Proposed approach of combining control and data plane information n Implementation and results n Conclusion IEEE Symposium on Security and Privacy May 2007 13

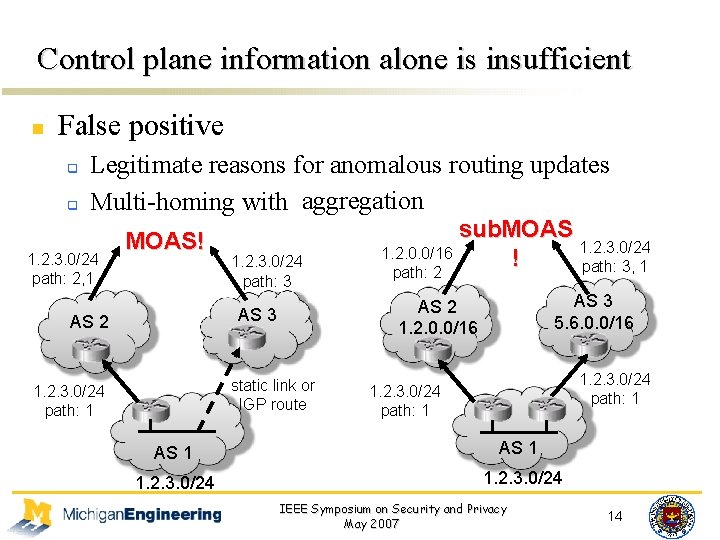
Control plane information alone is insufficient n False positive q q Legitimate reasons for anomalous routing updates aggregation Multi-homing with static link 1. 2. 3. 0/24 path: 2, 1 MOAS! 1. 2. 3. 0/24 path: 3 static link or IGP route 1. 2. 3. 0/24 path: 1 AS 3 5. 6. 0. 0/16 AS 2 1. 2. 0. 0/16 AS 3 AS 2 sub. MOAS 1. 2. 3. 0/24 1. 2. 0. 0/16 ! path: 3, 1 path: 2 1. 2. 3. 0/24 path: 1 AS 1 1. 2. 3. 0/24 IEEE Symposium on Security and Privacy May 2007 14

Control plane information alone is insufficient n False positive q q n Legitimate reasons for anomalous routing updates Multi-homing with static link and aggregation False negative q q AS-level path may not match the forwarding path Type 2 and type 4 attack do not lead to control plane anomalies IEEE Symposium on Security and Privacy May 2007 15

Proposed approach n Combine control plane and data plane information q q n A successful hijacking will result in conflicting data plane fingerprints A hijacking attempt cannot affect the entire network, especially the network topologically close to the victim Fingerprinting-based consistency check q q For valid MOAS and sub. MOAS, there is only one owner for the prefix Same data plane fingerprints For real hijacking, traffic from different locations may arrive at true owner or attackers conflicting fingerprints IEEE Symposium on Security and Privacy May 2007 16

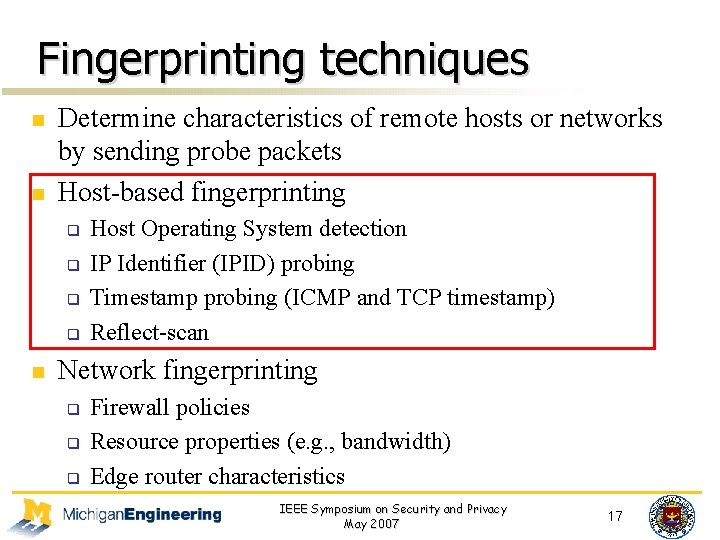
Fingerprinting techniques n n Determine characteristics of remote hosts or networks by sending probe packets Host-based fingerprinting q q n Host Operating System detection IP Identifier (IPID) probing Timestamp probing (ICMP and TCP timestamp) Reflect-scan Network fingerprinting q q q Firewall policies Resource properties (e. g. , bandwidth) Edge router characteristics IEEE Symposium on Security and Privacy May 2007 17

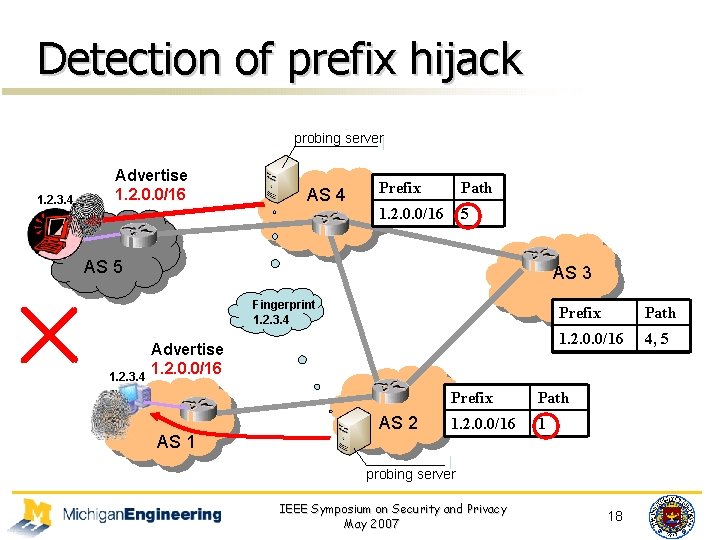
Detection of prefix hijack probing server 1. 2. 3. 4 Advertise 1. 2. 0. 0/16 AS 4 Prefix Path 1. 2. 0. 0/16 52, 1 AS 5 AS 3 Fingerprint 1. 2. 3. 4 Advertise 1. 2. 0. 0/16 AS 1 AS 2 Prefix Path 1. 2. 0. 0/16 4, 2, 51 Prefix Path 1. 2. 0. 0/16 1 probing server IEEE Symposium on Security and Privacy May 2007 18

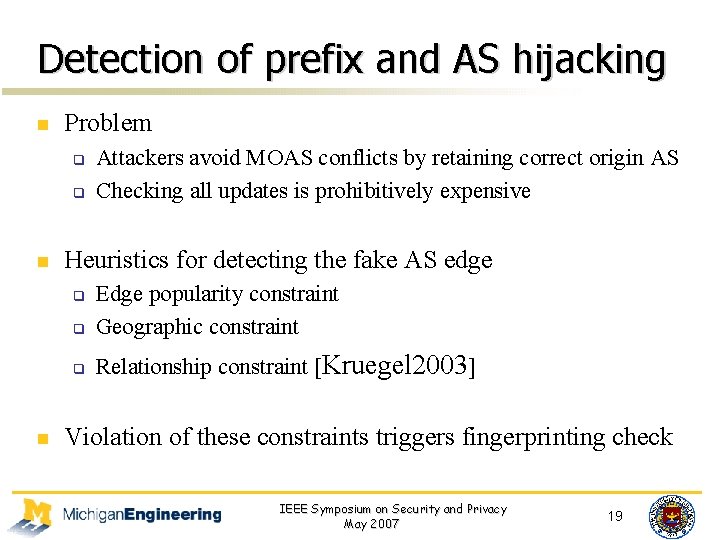
Detection of prefix and AS hijacking n Problem q q n Heuristics for detecting the fake AS edge q Edge popularity constraint Geographic constraint q Relationship constraint [Kruegel 2003] q n Attackers avoid MOAS conflicts by retaining correct origin AS Checking all updates is prohibitively expensive Violation of these constraints triggers fingerprinting check IEEE Symposium on Security and Privacy May 2007 19

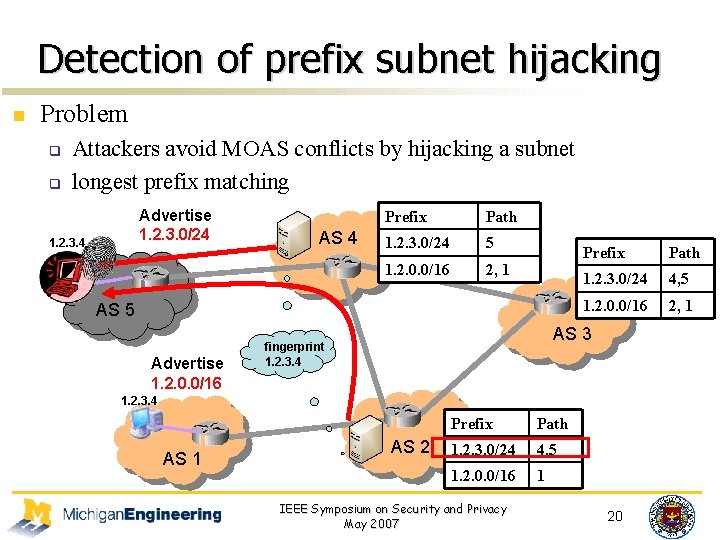
Detection of prefix subnet hijacking n Problem q q Attackers avoid MOAS conflicts by hijacking a subnet longest prefix matching Advertise 1. 2. 3. 0/24 1. 2. 3. 4 AS 4 Prefix Path 1. 2. 3. 0/24 5 1. 2. 0. 0/16 2, 1 AS 5 Advertise 1. 2. 0. 0/16 Prefix Path 1. 2. 3. 0/24 4, 5 1. 2. 0. 0/16 2, 1 AS 3 fingerprint 1. 2. 3. 4 AS 1 AS 2 Prefix Path 1. 2. 3. 0/24 4, 5 1. 2. 0. 0/16 1 IEEE Symposium on Security and Privacy May 2007 20

Detection of prefix subnet hijacking (Cont. ) n Identify sub. MOAS conflicts q n Customer-provider relationship check q n Newly announced prefixes which is part of existing prefix Assume provider and customer will not hijack one another Reflect-scan to detect subnet hijacking q q q IGP routing within victim AS is unaffected Use IP spoofing to solicit traffic inside victim AS Predictable IP ID increment in IP packet IEEE Symposium on Security and Privacy May 2007 21

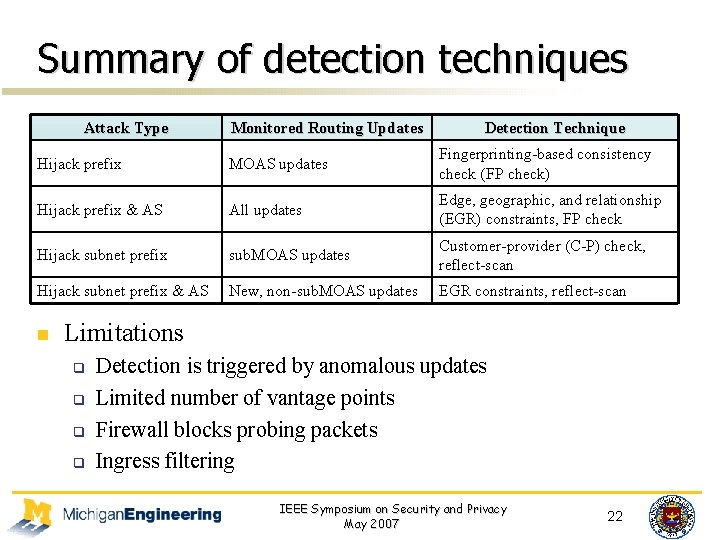
Summary of detection techniques Attack Type Monitored Routing Updates Detection Technique Hijack prefix MOAS updates Fingerprinting-based consistency check (FP check) Hijack prefix & AS All updates Edge, geographic, and relationship (EGR) constraints, FP check Hijack subnet prefix sub. MOAS updates Customer-provider (C-P) check, reflect-scan Hijack subnet prefix & AS New, non-sub. MOAS updates EGR constraints, reflect-scan n Limitations q q Detection is triggered by anomalous updates Limited number of vantage points Firewall blocks probing packets Ingress filtering IEEE Symposium on Security and Privacy May 2007 22

Outline n Introduction n Taxonomy of IP prefix hijacking n Proposed approach of combining control and data plane information n Implementation and results n Conclusion IEEE Symposium on Security and Privacy May 2007 23

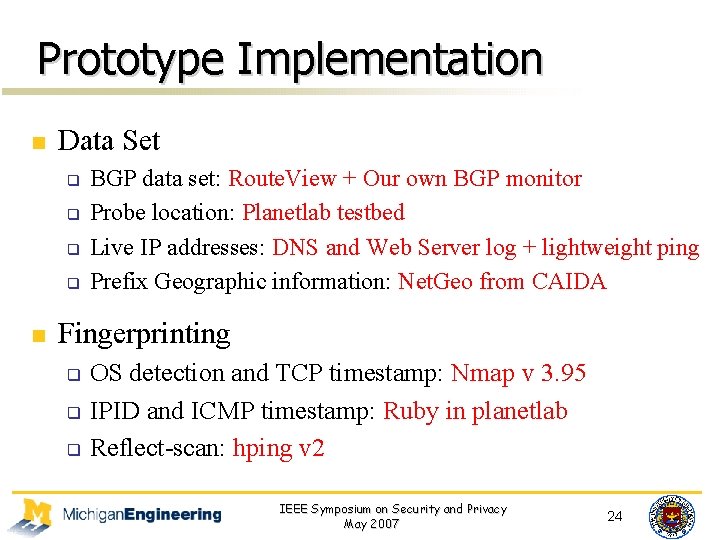
Prototype Implementation n Data Set q q n BGP data set: Route. View + Our own BGP monitor Probe location: Planetlab testbed Live IP addresses: DNS and Web Server log + lightweight ping Prefix Geographic information: Net. Geo from CAIDA Fingerprinting q q q OS detection and TCP timestamp: Nmap v 3. 95 IPID and ICMP timestamp: Ruby in planetlab Reflect-scan: hping v 2 IEEE Symposium on Security and Privacy May 2007 24

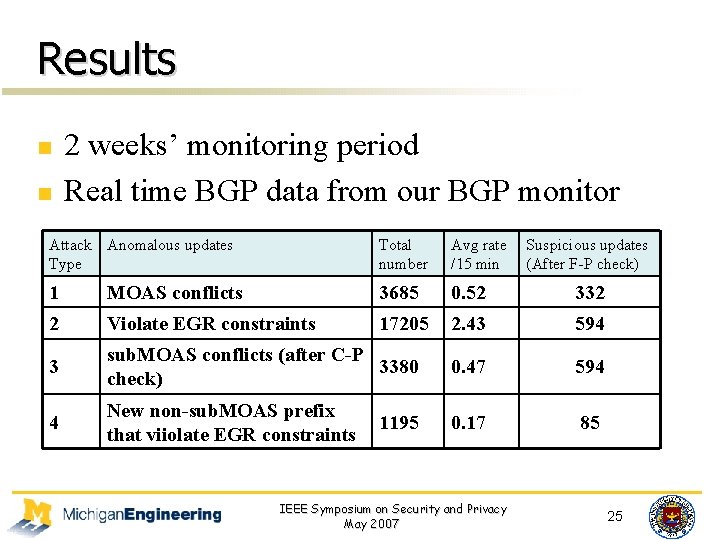
Results n n 2 weeks’ monitoring period Real time BGP data from our BGP monitor Attack Anomalous updates Type Total number Avg rate /15 min 1 MOAS conflicts 3685 0. 52 332 2 Violate EGR constraints 17205 2. 43 594 3 sub. MOAS conflicts (after C-P 3380 check) 0. 47 594 4 New non-sub. MOAS prefix that viiolate EGR constraints 0. 17 85 1195 IEEE Symposium on Security and Privacy May 2007 Suspicious updates (After F-P check) 25

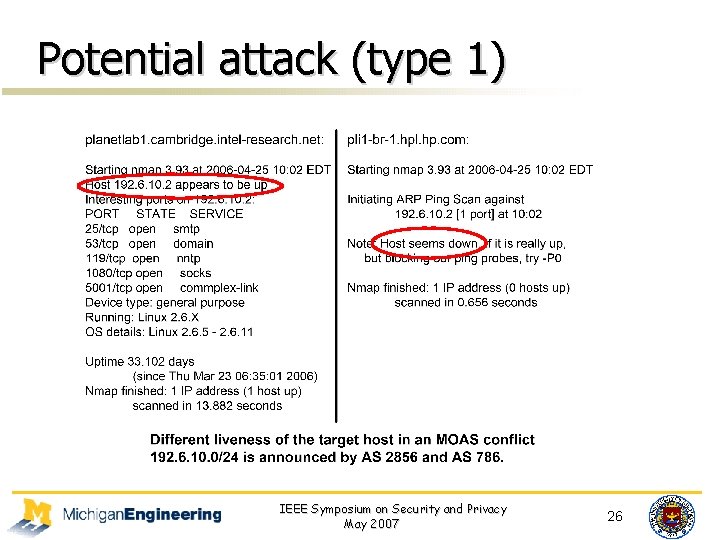
Potential attack (type 1) IEEE Symposium on Security and Privacy May 2007 26

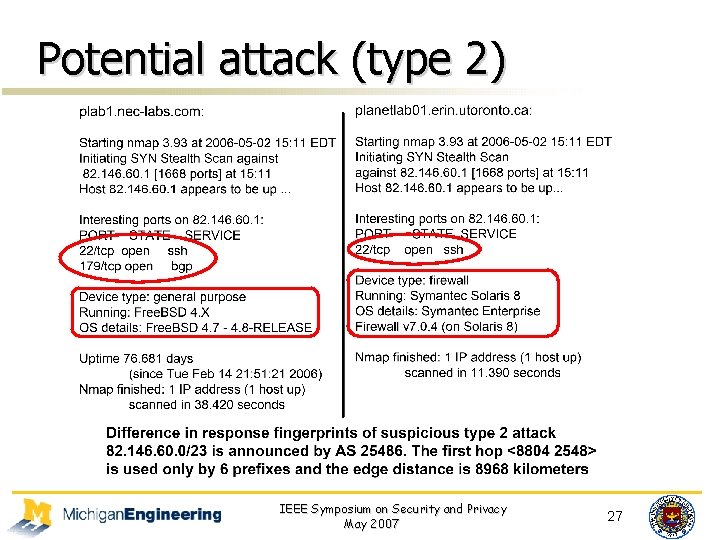
Potential attack (type 2) IEEE Symposium on Security and Privacy May 2007 27

DNS anycast validation n n IP anycast of root DNS server q Multiple server support same service under same IP address q 5 out of 13 DNS servers use anycast (C, F, I, J and K) Legitimate type 2 hijack attack q q q Hijack both prefix and AS number Our system successfully detect 4 of them C-root server doesn’t violate EGR check IEEE Symposium on Security and Privacy May 2007 28

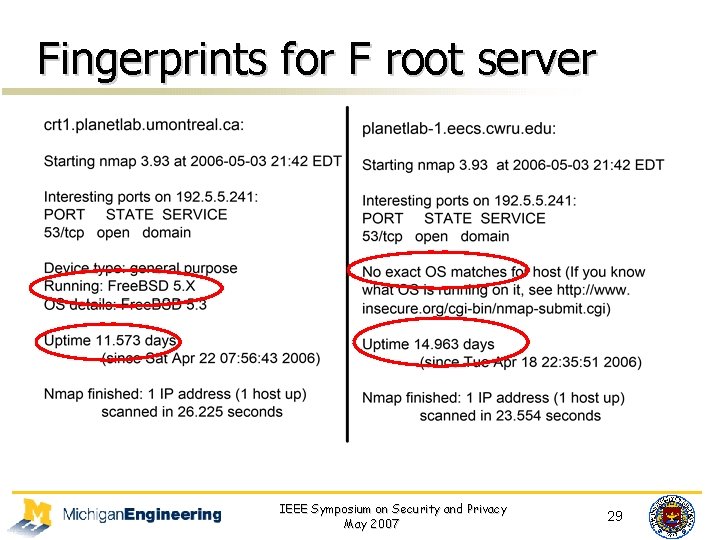
Fingerprints for F root server IEEE Symposium on Security and Privacy May 2007 29

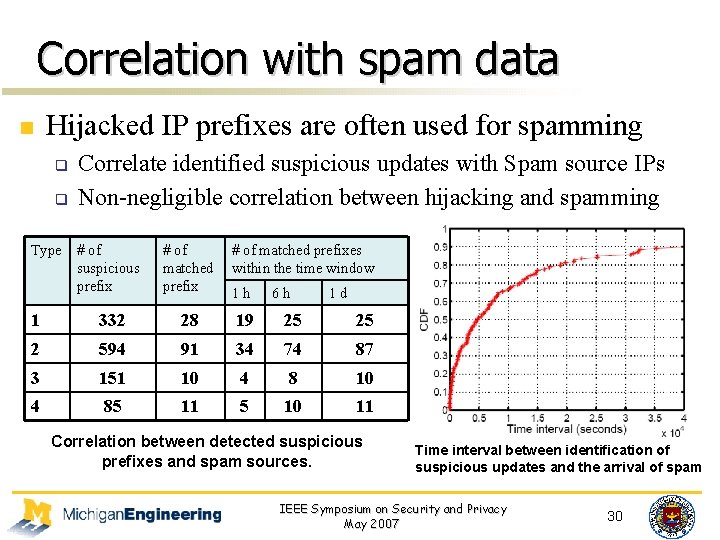
Correlation with spam data n Hijacked IP prefixes are often used for spamming q q Type Correlate identified suspicious updates with Spam source IPs Non-negligible correlation between hijacking and spamming # of suspicious prefix # of matched prefixes within the time window 1 h 6 h 1 d 1 332 28 19 25 25 2 594 91 34 74 87 3 151 10 4 85 11 5 10 11 Correlation between detected suspicious prefixes and spam sources. Time interval between identification of suspicious updates and the arrival of spam IEEE Symposium on Security and Privacy May 2007 30

Conclusion n Propose a framework for accurate real-time detection of IP prefix hijacking attacks n Exploit a novel insight that a real hijacking will result in conflicting data-plane fingerprints n Propose detailed classification of hijacking attacks and the detection algorithm for each type n Achieve significant reduction in both false positives and false negatives IEEE Symposium on Security and Privacy May 2007 31

Paper-2 n n A Light-Weight Distributed Scheme for Detecting IP Prefix Hijacks in Real-Time In SIGCOMM’ 07 IEEE Symposium on Security and Privacy May 2007 32

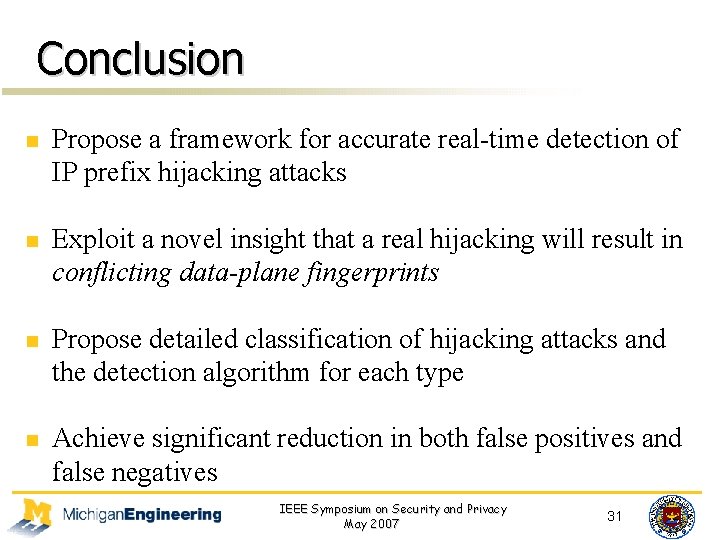
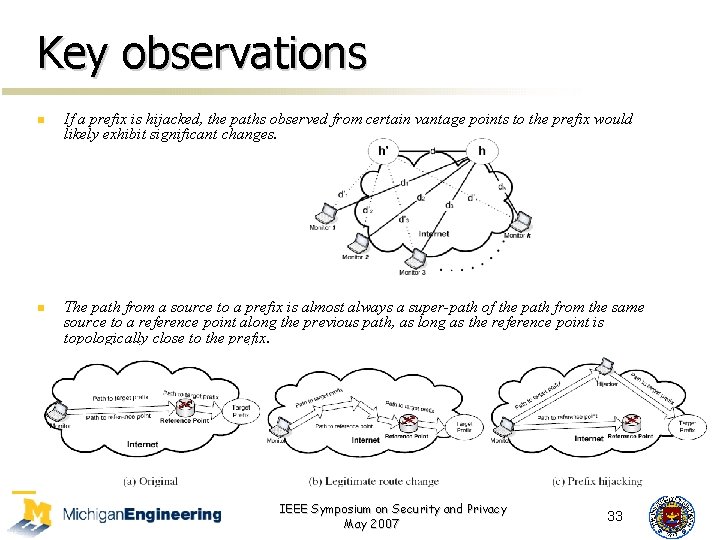
Key observations n n If a prefix is hijacked, the paths observed from certain vantage points to the prefix would likely exhibit significant changes. The path from a source to a prefix is almost always a super-path of the path from the same source to a reference point along the previous path, as long as the reference point is topologically close to the prefix. IEEE Symposium on Security and Privacy May 2007 33

High-level Methodology and Results n n n Detect the suspicious hijacking using the first observation Confirm the real hijacking using the second observation Result is surprising good, 0. 5% false positive and false negative. (which is really beyond my expectation, why? ) IEEE Symposium on Security and Privacy May 2007 34

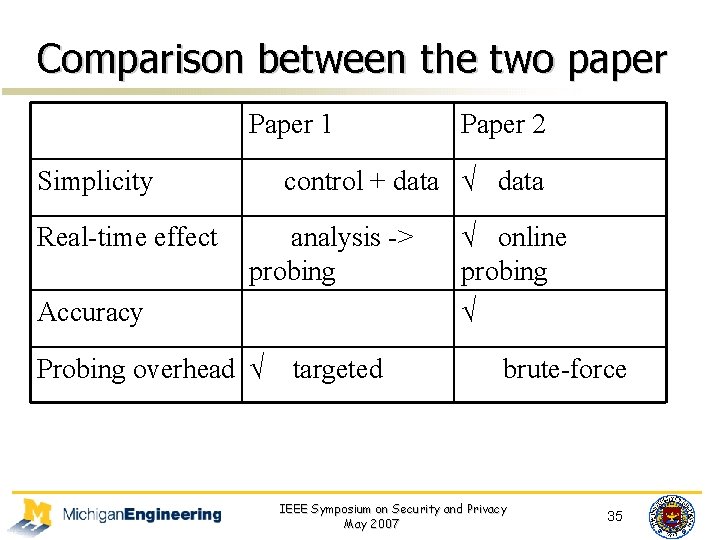
Comparison between the two paper Paper 1 Simplicity Real-time effect Paper 2 control + data √ data analysis -> probing Accuracy Probing overhead √ targeted √ online probing √ brute-force IEEE Symposium on Security and Privacy May 2007 35

My thinking (a 100% detection) Observation ? (my guess) - hijacked prefixes and victim prefixes are not identically used. Hijacked addresses may be little used ? n Proposed Method - Why not use a very simple and 100% accurate method, PING!!! Just ping the sampled addresses, to detect reachable or unreachable. n Merits - Very simple, easy to deploy, no false positive and false negative, comparable overhead with previous work, no other assistance is need! n Opportunity - I search online, nobody do so! n Want to discuss with all of you - Why cannot we just do so? n IEEE Symposium on Security and Privacy May 2007 36
 Prefix accurate
Prefix accurate Central pocket vs plain whorl
Central pocket vs plain whorl Hyster year by serial number
Hyster year by serial number Buffer overflow in control hijacking
Buffer overflow in control hijacking Dns spoofing
Dns spoofing Hijacking attacks
Hijacking attacks Hijacking attacks
Hijacking attacks Hijacking attacks
Hijacking attacks Example of control hijacking
Example of control hijacking What are the example of control hijacking attack
What are the example of control hijacking attack Type of control hijacking
Type of control hijacking Model stealing attacks
Model stealing attacks Hijacking attacks
Hijacking attacks Rational rose
Rational rose Realtime it
Realtime it Curis realtime
Curis realtime Realtime media
Realtime media Realtime
Realtime Cac realtime
Cac realtime Rendering realtime compositing
Rendering realtime compositing Rendering realtime compositing
Rendering realtime compositing Frankfurt realtime
Frankfurt realtime Realtime iep
Realtime iep Ams realtime weather maps central
Ams realtime weather maps central Realtime system
Realtime system Realtime it
Realtime it Market overview real-time interaction management
Market overview real-time interaction management Rto real time optimization
Rto real time optimization Realtime forex
Realtime forex Realtime big data
Realtime big data Real time characteristics of embedded operating systems
Real time characteristics of embedded operating systems Realtime database push
Realtime database push Real-time messaging protocol
Real-time messaging protocol Realtime interaction
Realtime interaction Gullistan carpet
Gullistan carpet Realtime etl
Realtime etl Realtime it
Realtime it