ACCOUNTING INFORMATION SYSTEMS The Crossroads of Accounting IT
















- Slides: 30

ACCOUNTING INFORMATION SYSTEMS The Crossroads of Accounting & IT Chapter 10 Fraud & Internal Control © Copyright 2012 Pearson Education. All Rights Reserved.

How does someone bilk his clients for $50 BILLION? Meet a Ponzi Scheme. . . & Bernard Madoff © Copyright 2012 Pearson Education. All Rights Reserved.

Why Does Fraud Occur? Top two reasons given for why executive fraud occurs: 1. Pressure to meet goals: 81% 2. Personal gain: 72% © Copyright 2012 Pearson Education. All Rights Reserved.

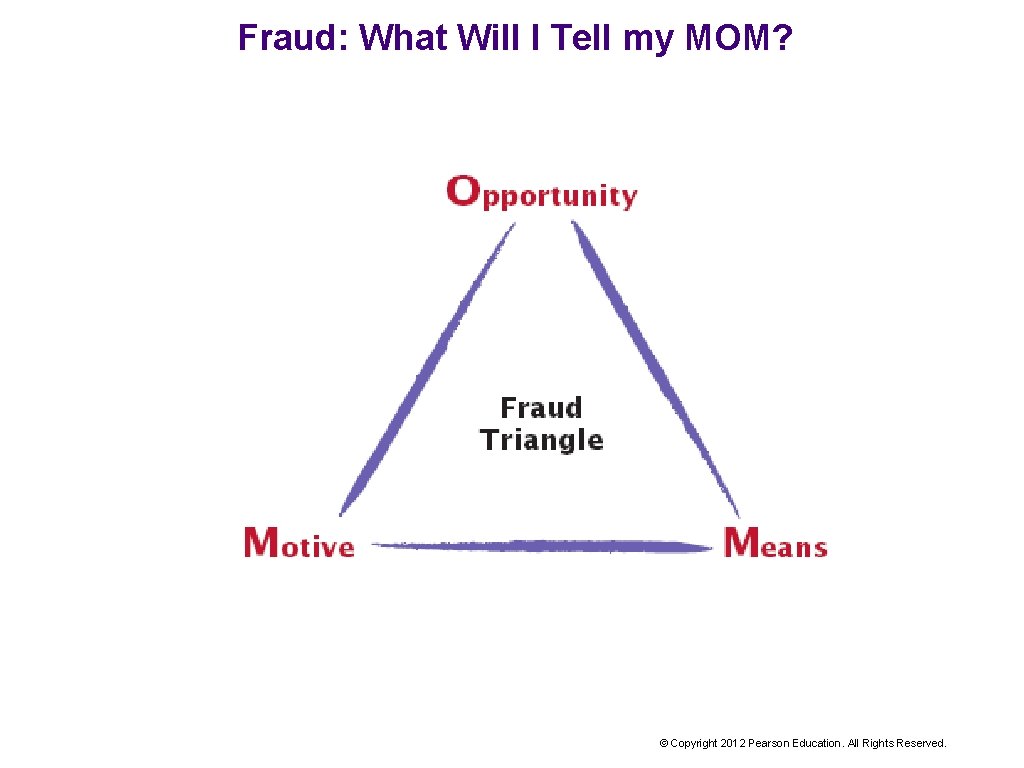
Fraud: What Will I Tell my MOM? © Copyright 2012 Pearson Education. All Rights Reserved.

Sarbanes-Oxley Act of 2002 Section 404. Management Assessment of Internal Controls. The public accounting firm that audits the financial statements of the company must issue an attestation report regarding the effectiveness of the company’s internal control. Section 302. Corporate Responsibility for Financial Reports. Section 302 requires the chief executive officer and chief financial officer to certify in each annual or quarterly report that the signing officer reviewed the report and that the report does not contain any untrue or omission of material fact that make the statements misleading. © Copyright 2012 Pearson Education. All Rights Reserved.

Sarbanes-Oxley Act of 2002 Section 806. Protection for Employees of Publicly Traded Companies Who Provide Evidence of Fraud. Known as Whistleblower Protection for Employees of Publicly Traded Companies. Section 806 provides for protection against retaliation for employees, such as company accountants, who provide information in fraud cases of publicly traded companies. Section 906. Corporate Responsibility for Financial Reports. Section 906 requires corporate management to certify reports filed with the SEC, such as the annual 10 -K and quarterly 10 -Q. Provides for criminal penalties of up to $5 million or 20 years imprisonment. © Copyright 2012 Pearson Education. All Rights Reserved.

Audit & Internal Control Types of Audits: Audit of internal control: tests of controls to obtain evidence that internal control over financial reporting has operated effectively. Audit of financial statements: tests of controls to assess control risk. Substantive procedures collect evidence regarding accuracy, completeness, and validity of data produced by the accounting system. IT audit: tests of IT to understand how IT affects internal control over financial reporting. PCAOB expects auditors to understand how IT affects the audit and integrate IT into the audit. Integrated audit: required by Auditing Standard No. 5, integrates the audit of internal control with the audit of financial statements. © Copyright 2012 Pearson Education. All Rights Reserved.

Controls Over Financial Reporting Preventive controls: The objective of preventive controls is to prevent errors or fraud that could result in a misstatement of the financial statements. Detective controls: The objective of detective controls is to detect errors or fraud that has occurred and that could result in a misstatement of the financial statements. © Copyright 2012 Pearson Education. All Rights Reserved.

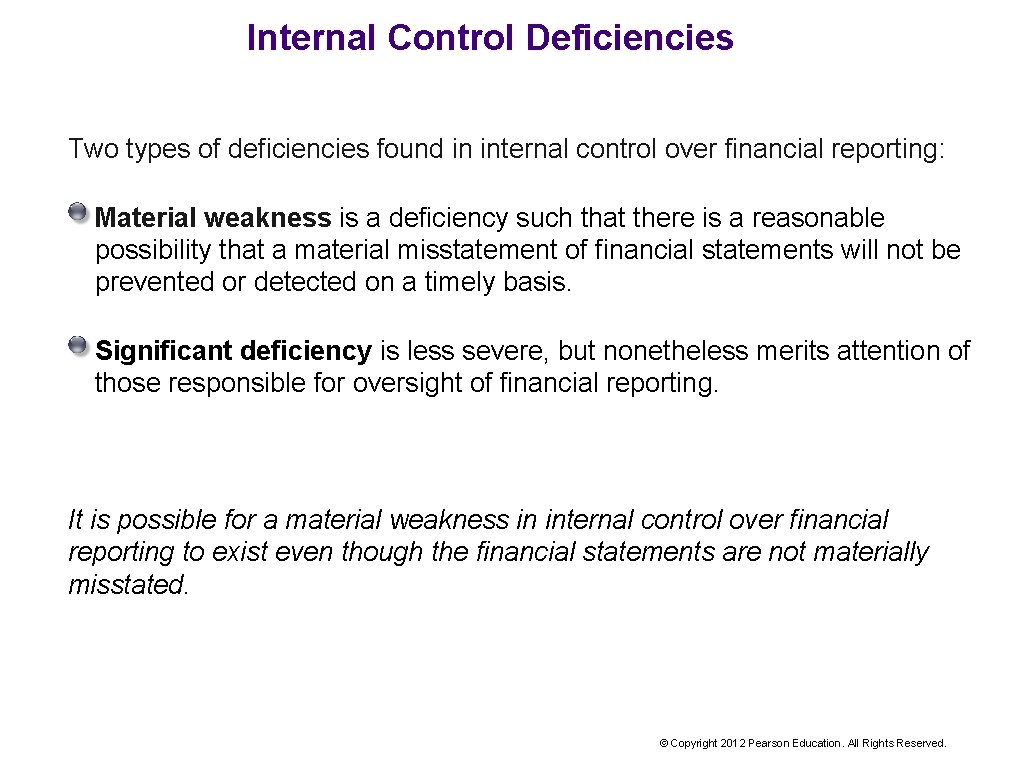
Internal Control Deficiencies Two types of deficiencies found in internal control over financial reporting: Material weakness is a deficiency such that there is a reasonable possibility that a material misstatement of financial statements will not be prevented or detected on a timely basis. Significant deficiency is less severe, but nonetheless merits attention of those responsible for oversight of financial reporting. It is possible for a material weakness in internal control over financial reporting to exist even though the financial statements are not materially misstated. © Copyright 2012 Pearson Education. All Rights Reserved.

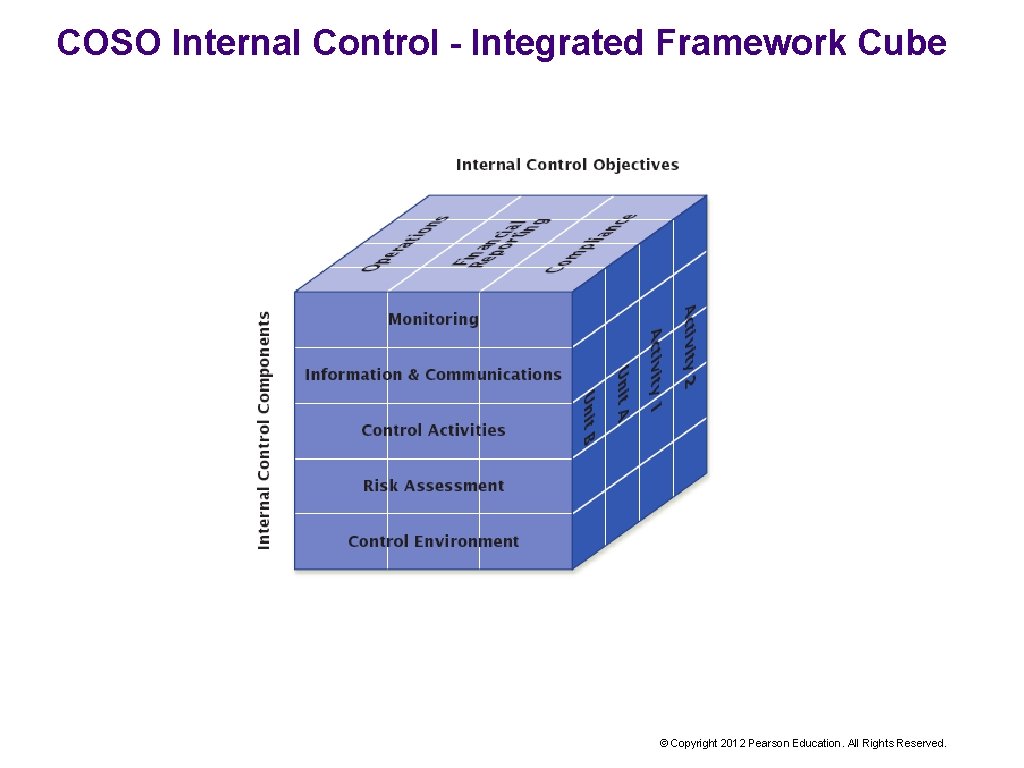
COSO Internal Control - Integrated Framework Cube © Copyright 2012 Pearson Education. All Rights Reserved.

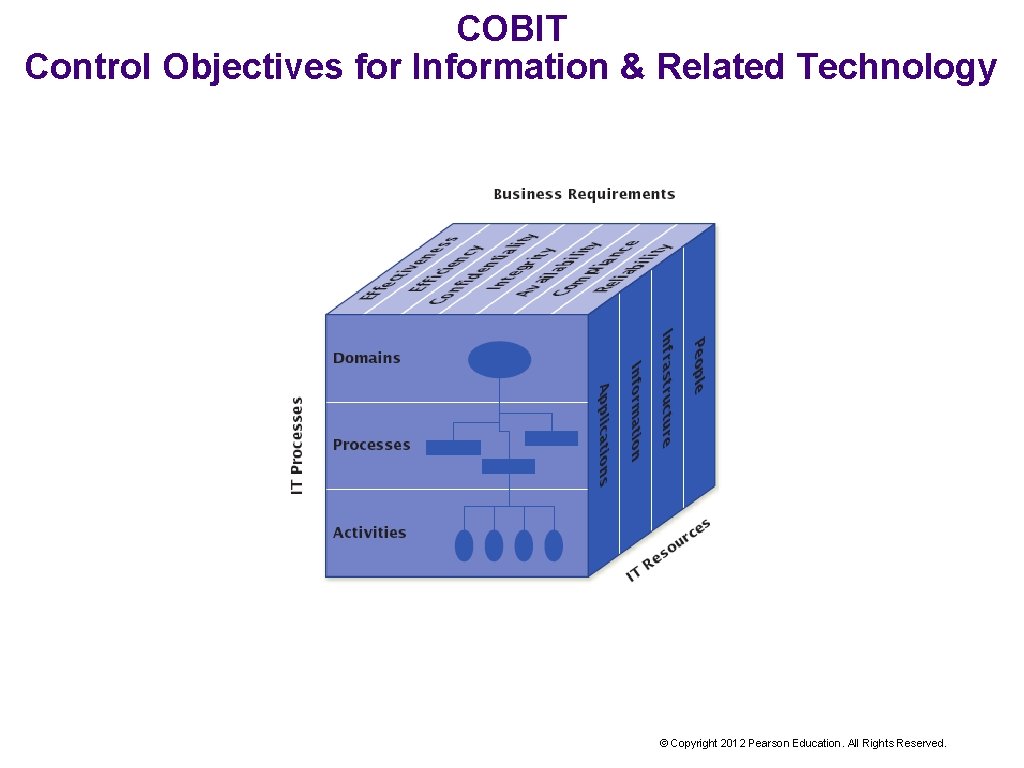
COBIT Control Objectives for Information & Related Technology © Copyright 2012 Pearson Education. All Rights Reserved.

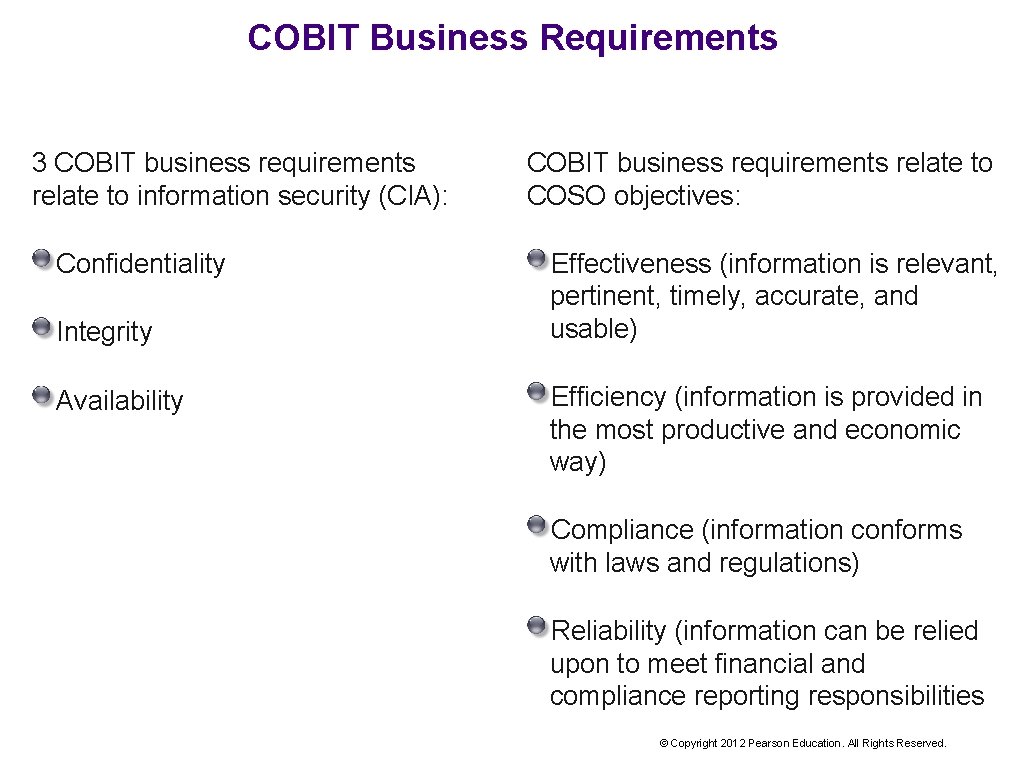
COBIT Business Requirements 3 COBIT business requirements relate to information security (CIA): Confidentiality Integrity Availability COBIT business requirements relate to COSO objectives: Effectiveness (information is relevant, pertinent, timely, accurate, and usable) Efficiency (information is provided in the most productive and economic way) Compliance (information conforms with laws and regulations) Reliability (information can be relied upon to meet financial and compliance reporting responsibilities © Copyright 2012 Pearson Education. All Rights Reserved.

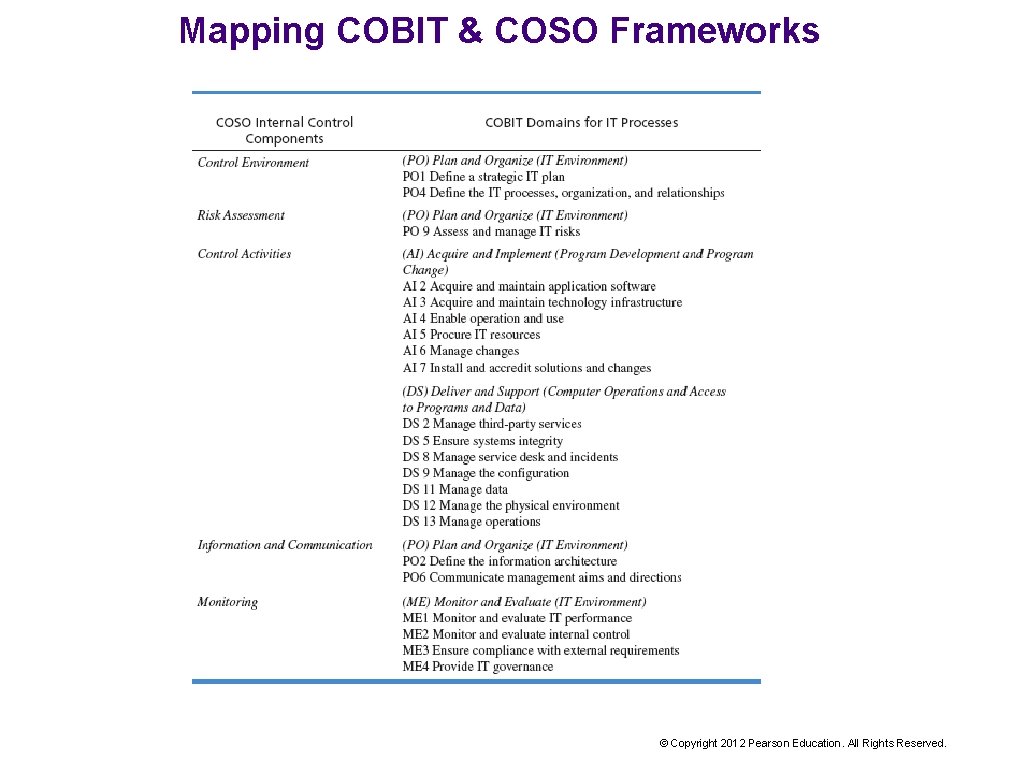
Mapping COBIT & COSO Frameworks © Copyright 2012 Pearson Education. All Rights Reserved.

© Copyright 2012 Pearson Education. All Rights Reserved.

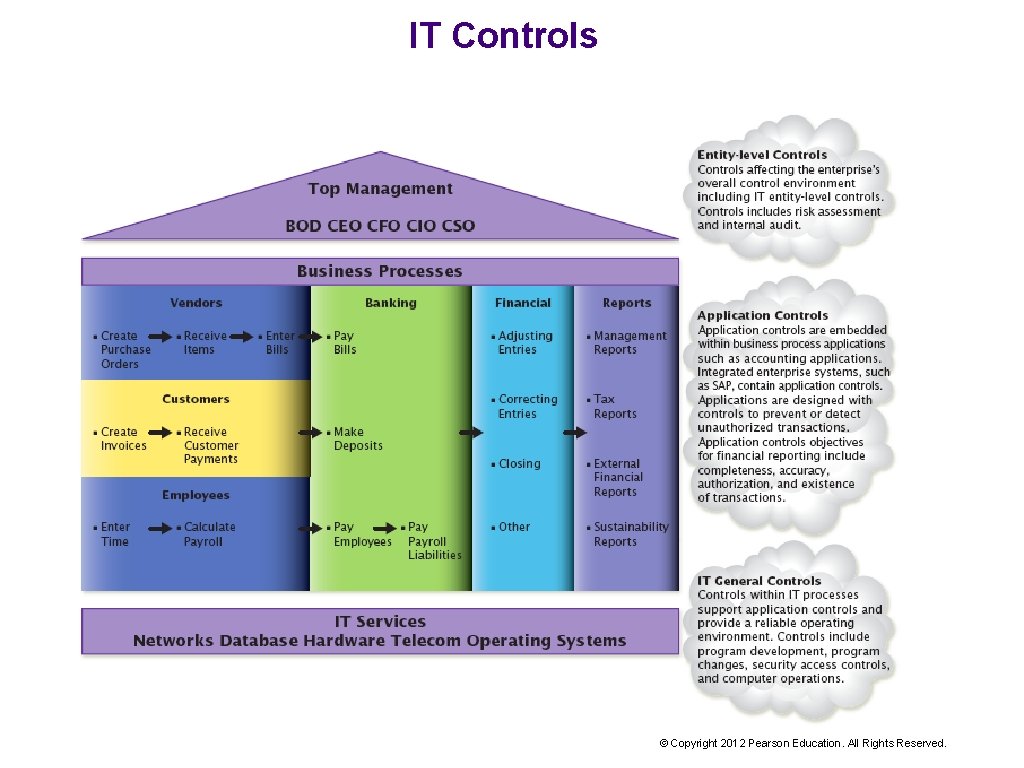
IT Controls © Copyright 2012 Pearson Education. All Rights Reserved.

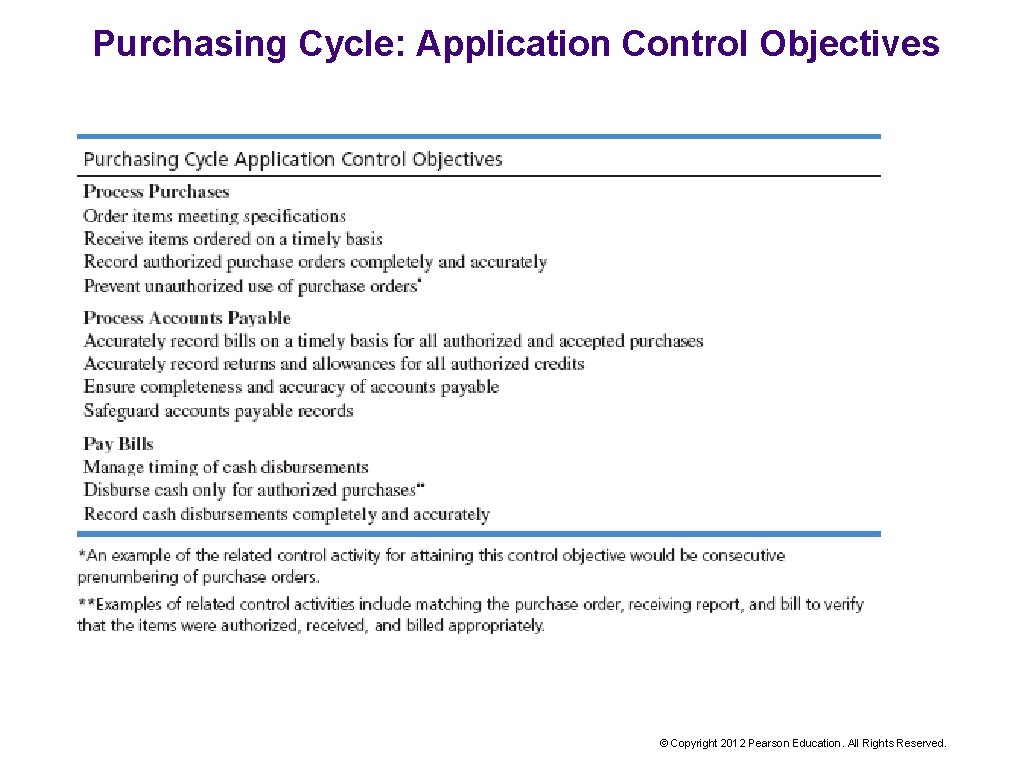
Purchasing Cycle: Application Control Objectives © Copyright 2012 Pearson Education. All Rights Reserved.

Sales Cycle: Application Control Objectives © Copyright 2012 Pearson Education. All Rights Reserved.

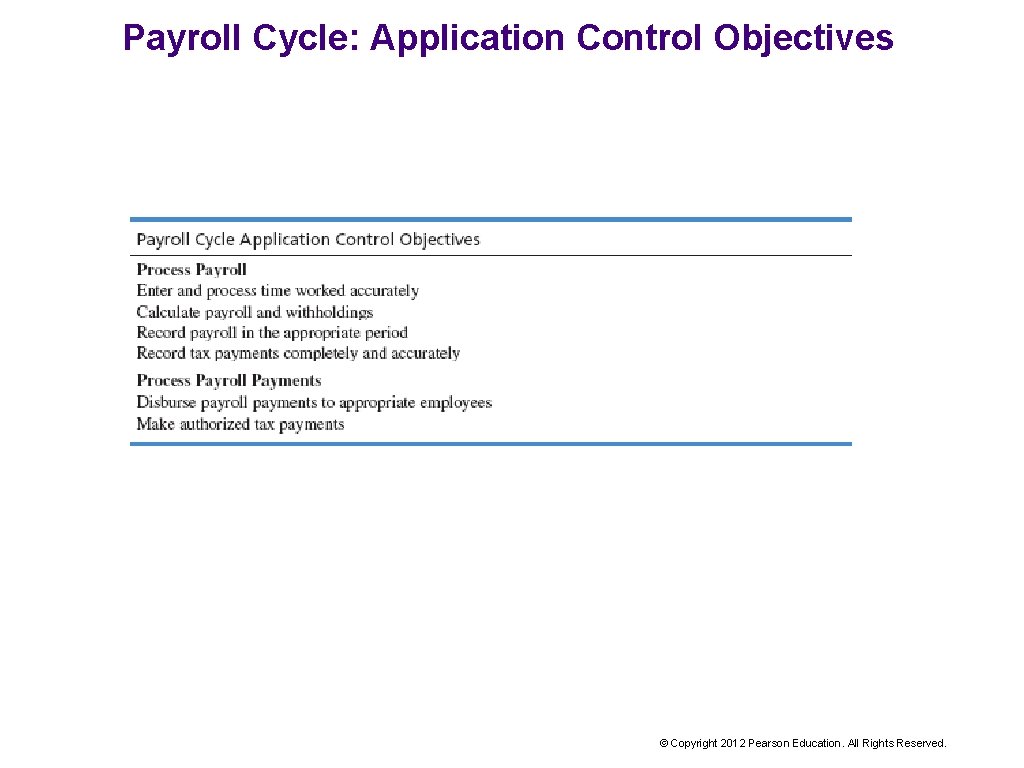
Payroll Cycle: Application Control Objectives © Copyright 2012 Pearson Education. All Rights Reserved.

Banking/Cash: Application Control Objectives © Copyright 2012 Pearson Education. All Rights Reserved.

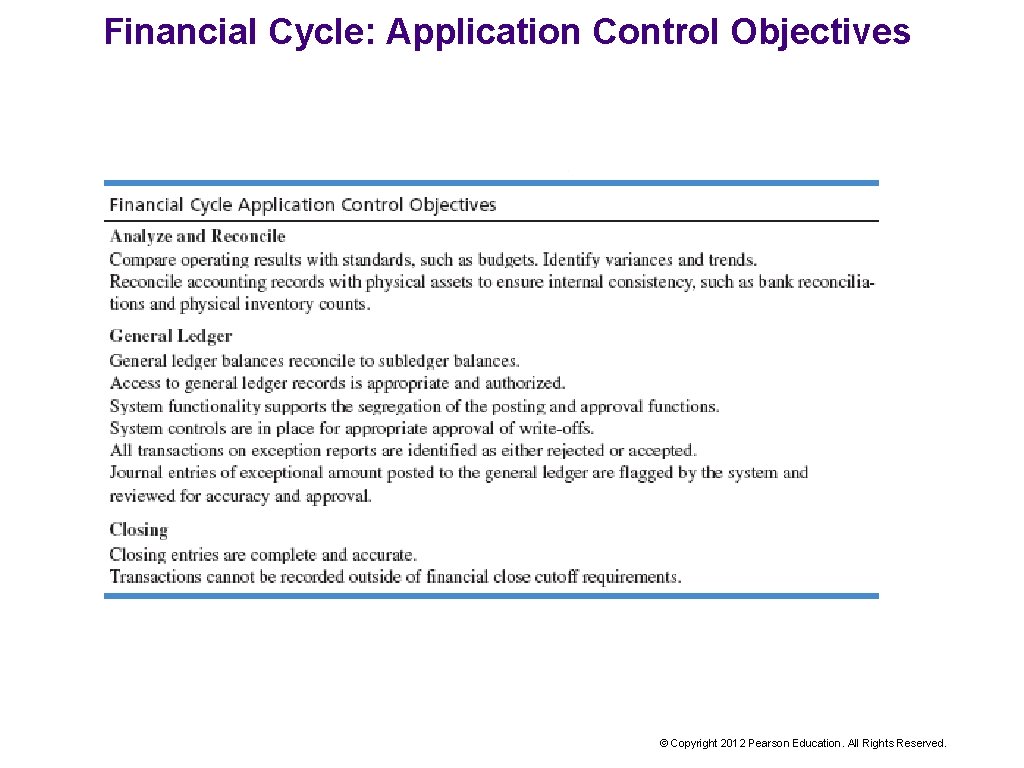
Financial Cycle: Application Control Objectives © Copyright 2012 Pearson Education. All Rights Reserved.

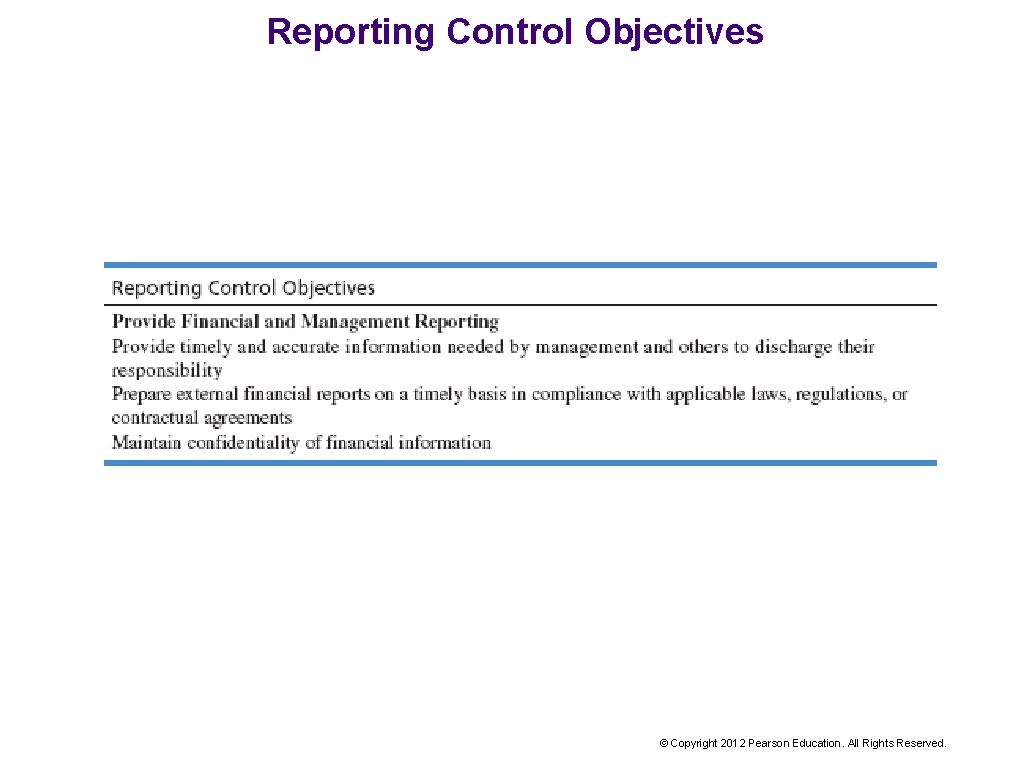
Reporting Control Objectives © Copyright 2012 Pearson Education. All Rights Reserved.

My Connection Study Less. Learn More. Make Connections. Exercise Identify the three levels of IT controls within an organization and give examples of each. © Copyright 2012 Pearson Education. All Rights Reserved.

AICPA’s Trust Services framework for evaluating information systems is based on five principles: Security. The system is protected against unauthorized access. Availability. The system is available for use as committed or agreed. Processing integrity. System processing is accurate, timely, complete, valid, and authorized. Confidentiality. Confidential information is protected as committed or agreed. Privacy. Personal information is collected, used, retained, disclosed, and destroyed in conformity with commitments in the entity’s privacy notice and with criteria set forth in Generally Accepted Privacy Principles (GAPP). © Copyright 2012 Pearson Education. All Rights Reserved.

Managing the Risk of Fraud Five principles for establishing an environment to effectively manage fraud risk: Principle 1: Fraud Risk Governance. There should be a written policy to convey the expectation of the board of directors and top management regarding managing fraud risk. Principle 2: Fraud Risk Assessment. Fraud risk exposure should be assessed periodically to identify potential events the organization should mitigate. Principle 3: Fraud Prevention techniques should be established to avoid fraud risk events and mitigate impact on the organization. Principle 4: Fraud Detection techniques should be established to uncover fraud events when preventive measures fail or unmitigated risks are realized. Principle 5: Fraud Investigation and Corrective Action. A reporting process should be in place to solicit input on potential fraud. Coordinated investigation is used to address potential fraud timely and appropriately. © Copyright 2012 Pearson Education. All Rights Reserved.

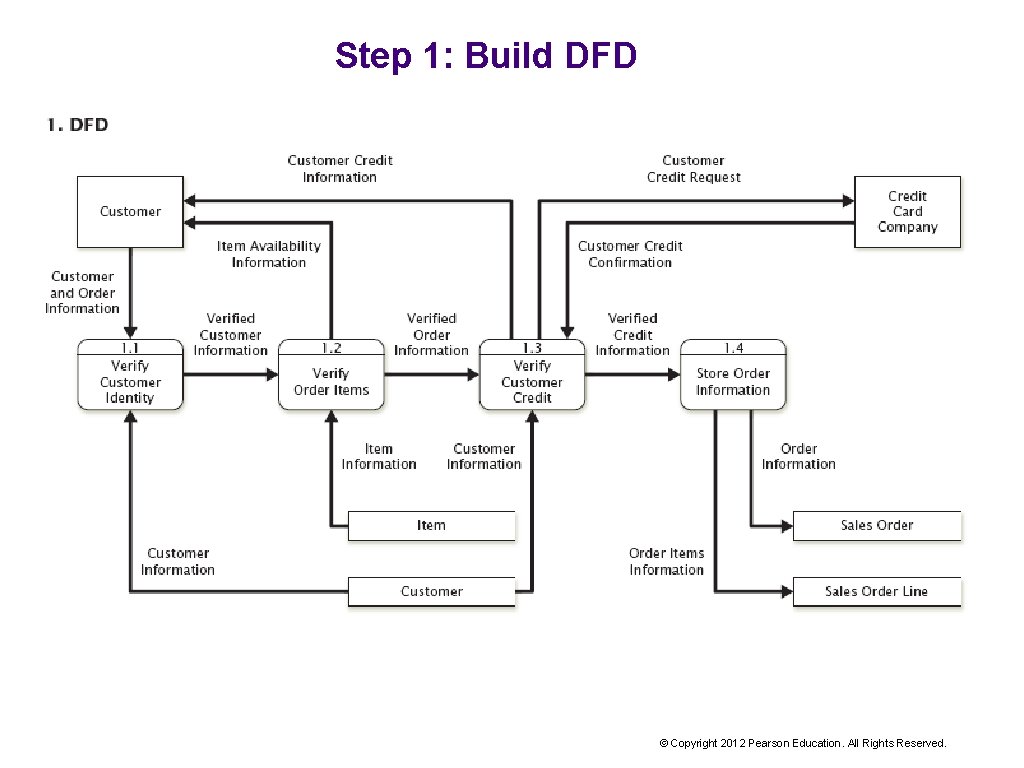
How Do I Document Control Hot. Spots? 1. Build a DFD. 2. Document controls. 3. Document control Hot. Spots. © Copyright 2012 Pearson Education. All Rights Reserved.

Step 1: Build DFD © Copyright 2012 Pearson Education. All Rights Reserved.

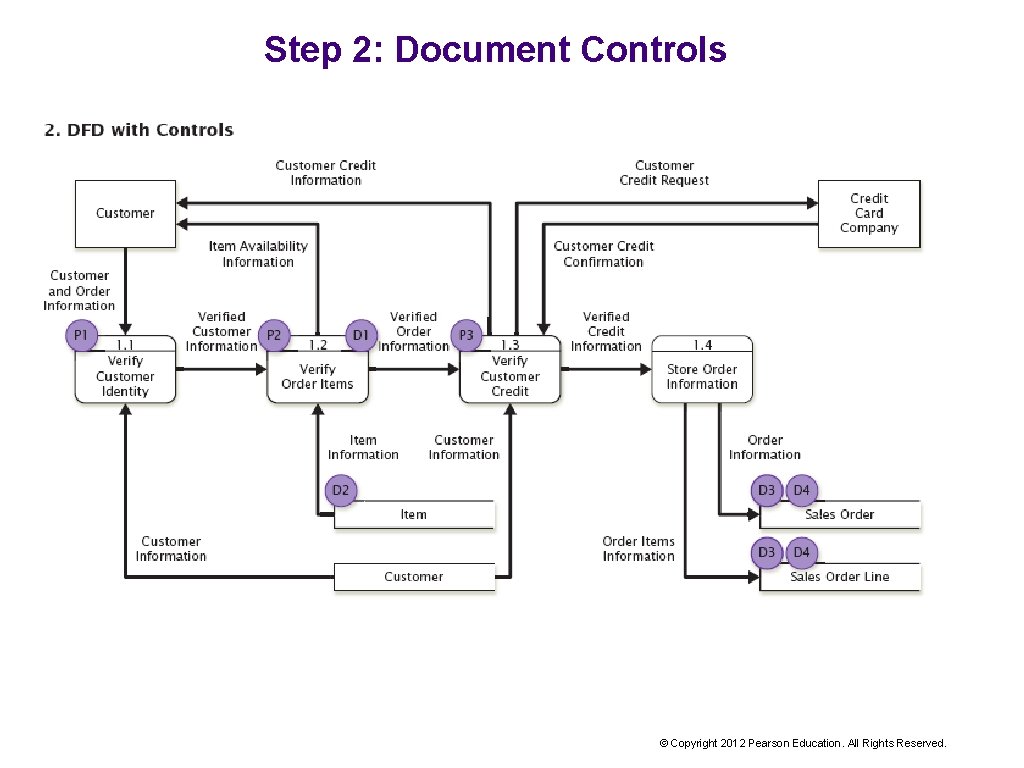
Step 2: Document Controls © Copyright 2012 Pearson Education. All Rights Reserved.

Step 2: Document Controls © Copyright 2012 Pearson Education. All Rights Reserved.

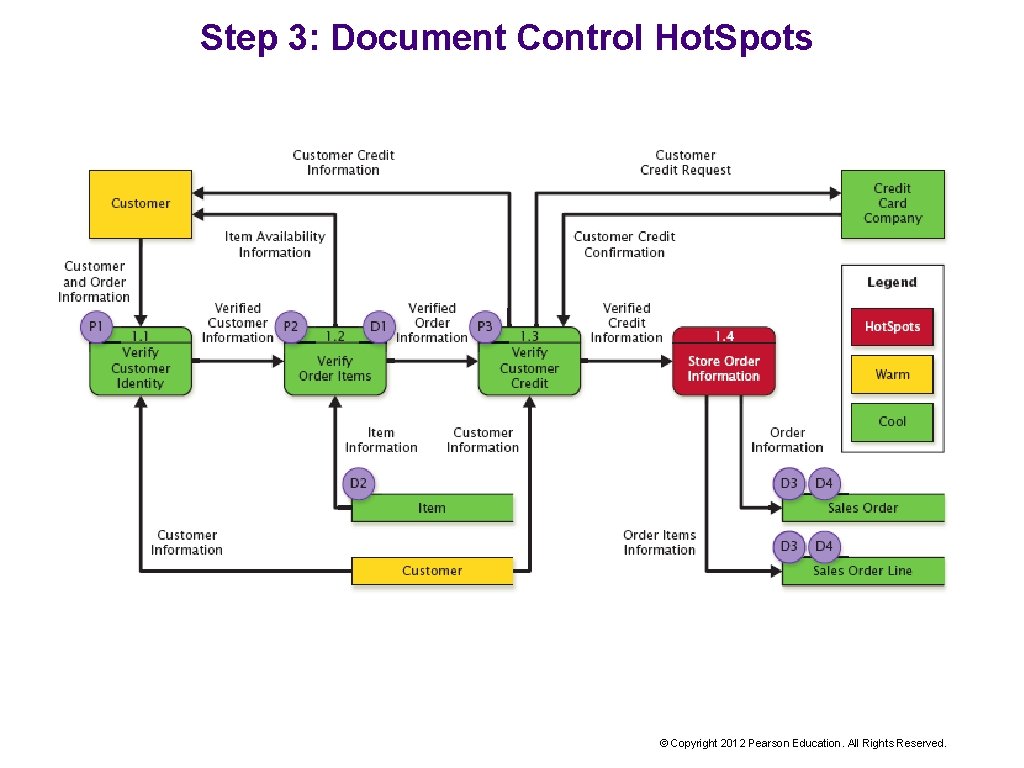
Step 3: Document Control Hot. Spots © Copyright 2012 Pearson Education. All Rights Reserved.

My Connection Study Less. Learn More. Make Connections. Exercise Use the DFD you prepared for chapter 5 and document control Hot. Spots. 1. Document controls. 2. Document control Hot. Spots. © Copyright 2012 Pearson Education. All Rights Reserved.
 Chapter 31 societies at crossroads outline
Chapter 31 societies at crossroads outline Bow tie quilt pattern meaning
Bow tie quilt pattern meaning The crossroads archetype examples
The crossroads archetype examples Threshold guardian examples
Threshold guardian examples The helpers archetype examples
The helpers archetype examples Archetype root word
Archetype root word What was the nomadic lifestyle
What was the nomadic lifestyle Middle east crossroads of the world
Middle east crossroads of the world On which side of the window are you
On which side of the window are you Crossroads bank for social security
Crossroads bank for social security Dr rick griffith
Dr rick griffith Child countable or uncountable
Child countable or uncountable Crossroads international church singapore
Crossroads international church singapore Crossroads hotel lilongwe
Crossroads hotel lilongwe Chapter 7 accounting information systems
Chapter 7 accounting information systems Chapter 7 accounting information systems
Chapter 7 accounting information systems Introduction to accounting information systems
Introduction to accounting information systems Core concepts of accounting information systems
Core concepts of accounting information systems Slidetodoc.com
Slidetodoc.com Tactical accounting
Tactical accounting Chapter 7 accounting information systems
Chapter 7 accounting information systems Accounting information systems marshall b romney
Accounting information systems marshall b romney Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Lp html
Lp html Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Voi kéo gỗ như thế nào
Voi kéo gỗ như thế nào Tư thế worms-breton
Tư thế worms-breton Chúa yêu trần thế
Chúa yêu trần thế Môn thể thao bắt đầu bằng chữ đua
Môn thể thao bắt đầu bằng chữ đua Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất





















































