ACCOUNTING INFORMATION SYSTEMS The Crossroads of Accounting IT
























- Slides: 51

ACCOUNTING INFORMATION SYSTEMS The Crossroads of Accounting & IT Chapter 11 Cybersecurity © Copyright 2012 Pearson Education. All Rights Reserved.

How Secure is Your Credit Card? Meet Heartland. © Copyright 2012 Pearson Education. All Rights Reserved.

What is Cybersecurity? Cybersecurity combines people, processes, and technology to continually monitor vulnerabilities and respond proactively to secure the system. Cybersecurity is a highly technical, specialized field. The confidential nature of data stored in accounting systems puts increasing pressure on accounting professionals to understand IT security. © Copyright 2012 Pearson Education. All Rights Reserved.

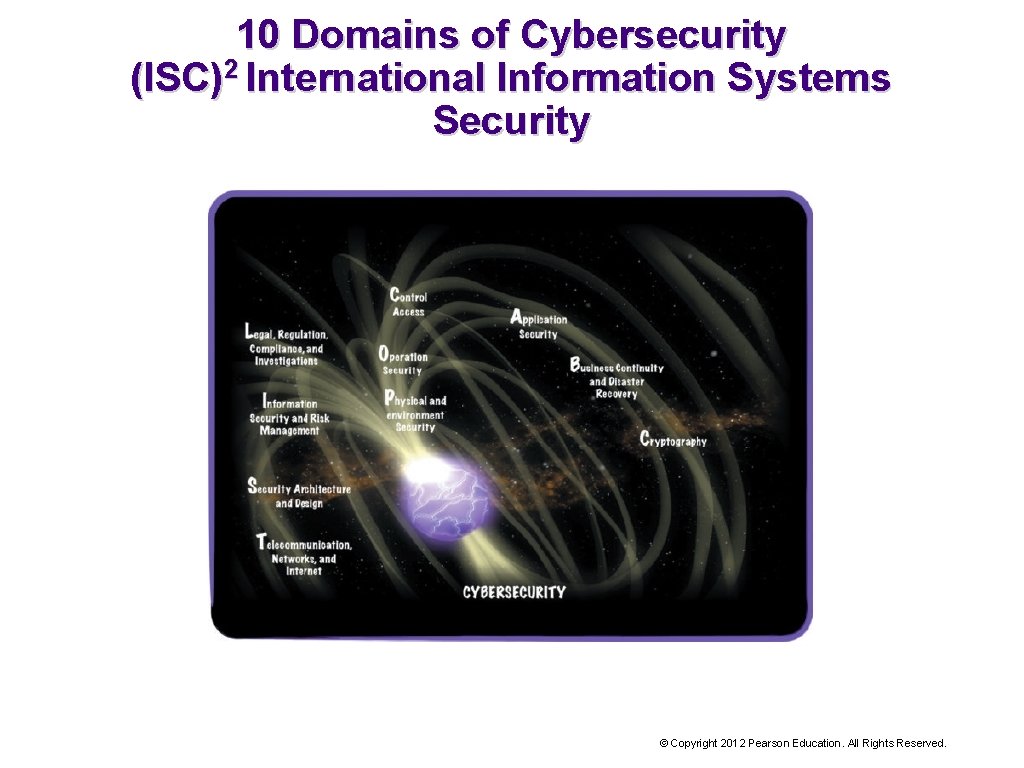
10 Domains of Cybersecurity (ISC)2 International Information Systems Security © Copyright 2012 Pearson Education. All Rights Reserved.

10 Domains of Cybersecurity (ISC)2 International Information Systems Security © Copyright 2012 Pearson Education. All Rights Reserved.

What is the Legal, Regulations, Compliance and Investigations Domain? Cybercrimes: crimes connected to information assets and IT. Cyberlaws: laws and regulations to prevent, investigate, and prosecute cybercrimes. Cyber forensics: involves collecting, examining, and preserving evidence of cybercrimes. © Copyright 2012 Pearson Education. All Rights Reserved.

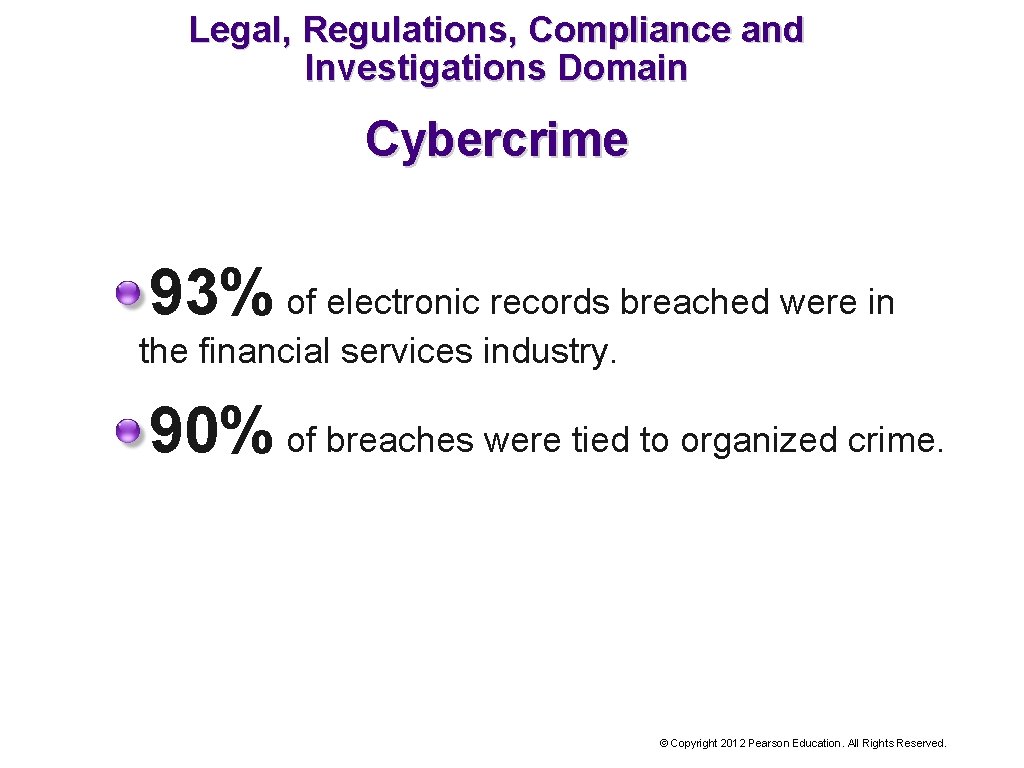
Legal, Regulations, Compliance and Investigations Domain Cybercrime 93% of electronic records breached were in the financial services industry. 90% of breaches were tied to organized crime. © Copyright 2012 Pearson Education. All Rights Reserved.

Legal, Regulations, Compliance and Investigations Domain Cybercrime Successful breaches typically involve an attacker exploiting a mistake made by the victim organization © Copyright 2012 Pearson Education. All Rights Reserved.

Legal, Regulations, Compliance and Investigations Domain Cybercrime Well-known cyberattacks include: Salami attacks Typically for very small amounts over numerous accounts that accumulate into significant sums Example: rounding interest calculations into an attacker’s account. Social engineering Manipulating an individual into divulging confidential information to be used for fraudulent purposes. Example: Phishing: faked IT email request to email back information regarding your account © Copyright 2012 Pearson Education. All Rights Reserved.

Legal, Regulations, Compliance and Investigations Domain Cybercrime Well-known cyberattacks include: Dumpster diving Rummaging through garbage for discarded documents or digital media. Example: buying discarded computer hardware and extracting data left on the hard drive. Password sniffing Attempting to obtain passwords by sniffing messages sent between computers on the network. Example: Sniffing messages sent over a free wi-fi network at the local coffee shop to obtain others’ passwords. © Copyright 2012 Pearson Education. All Rights Reserved.

Legal, Regulations, Compliance and Investigations Domain Cyberlaws are constantly evolving to meet more sophisticated cyberattacks. Laws related to cybersecurity originate from: Legislation Regulations Case law © Copyright 2012 Pearson Education. All Rights Reserved.

Legal, Regulations, Compliance and Investigations Domain Cyberlaw Legislation affecting cyberlaw include: Sarbanes-Oxley Addresses requirements for proper internal control, including information security and controls. Gramm-Leach-Bliley Act Requires institutions to have adequate cybersecurity to prevent unauthorized sharing of customer data. Payment Card Industry Data Security Standards PCI-DSS legislation require organizations to meet cybersecurity requirements to safeguard credit and debit card data, including security for storage and transmission of payment card data. Federal Information Security Management Act Requires federal agencies and their contractors to have information security programs. © Copyright 2012 Pearson Education. All Rights Reserved.

Legal, Regulations, Compliance and Investigations Domain Cyber Forensics Collecting, examining, and preserving evidence of cybercrimes. Organizations often use law enforcement, regulatory agencies, and outside consultants to conduct cyber forensic investigations. © Copyright 2012 Pearson Education. All Rights Reserved.

What is the Information Security and Risk Management Domain? Information security and risk management consists of the preventive and proactive measures taken to prevent cybercrimes. Information security: policies and procedures required to secure information assets, including IT hardware, software, and stored data. Information risk management: manages the risk related to information assets and IT and is part of the larger enterprise risk management (ERM). © Copyright 2012 Pearson Education. All Rights Reserved.

Information Security and Risk Management Domain Security Management Principles Fundamental principles of information security include CIA: Confidentiality: Sensitive data at each point in information processing is secure and protected from unauthorized access Integrity: Data is accurate and reliable. Availability: Required data is available as needed by an organization’s users, such as accountants. If data is destroyed, data can be restored so it is available. © Copyright 2012 Pearson Education. All Rights Reserved.

Information Security and Risk Management Domain Information Security Management Information security management involves developing and enforcing security policies, standards, guidelines and procedures for information. Three types of information security controls are: Administrative controls: security policies, standards, guidelines and procedures to screen employees and provide security training. Technical or logical controls: security policies, standards, guidelines and procedures for access control and configuration of IT infrastructure. Physical controls: includes facility access control, environmental controls, and intrusion detection. © Copyright 2012 Pearson Education. All Rights Reserved.

Information Security and Risk Management Domain Security Frameworks A security framework provides a conceptual structure to address security and control. Security frameworks include: Control Objectives for Information and Related Technology (COBIT) for managing IT security. Committee on Sponsoring Organizations of the Treadway Commission (COSO) provides a framework for corporate governance. International Standardization Organization ISO 27000 contains specifications for an information security management system. © Copyright 2012 Pearson Education. All Rights Reserved.

What is the Security Architecture and Design Domain? Security architecture and design domain relates to security for IT architecture and design. IT architecture consists of architecture for computers, networks, and databases. © Copyright 2012 Pearson Education. All Rights Reserved.

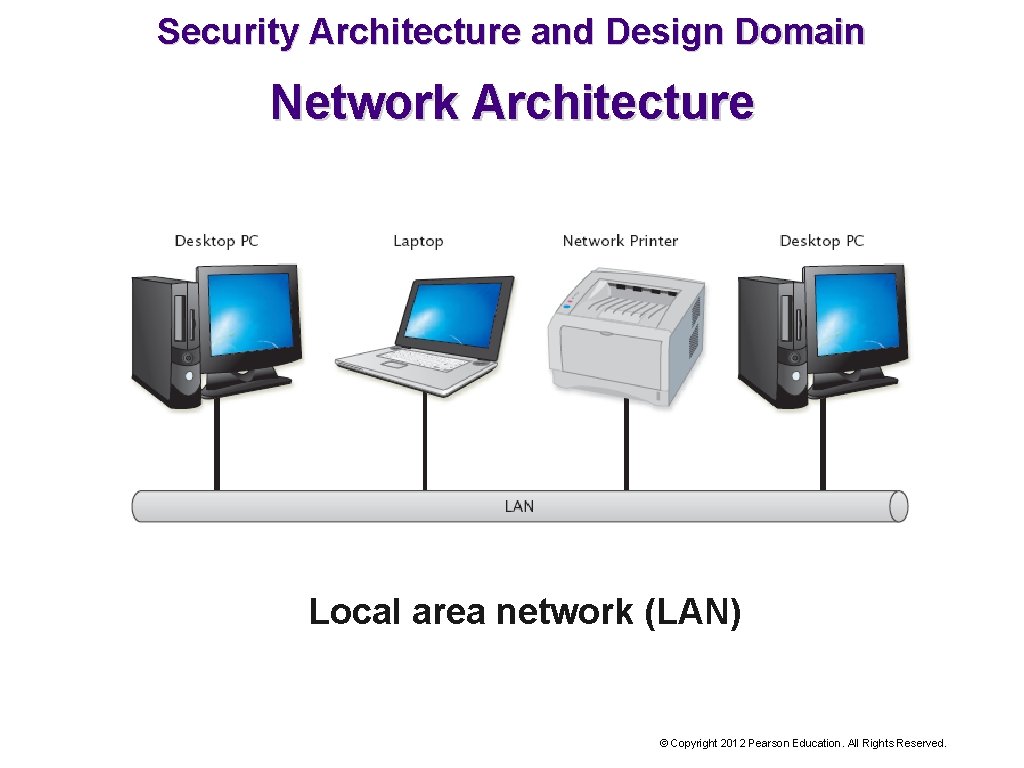
Security Architecture and Design Domain Network Architecture Networks are interconnected computers and devices. Network architecture consists of network hardware and software. Three categories of networks: Local area networks (LANs) Metropolitan area networks (MANs) Wide area networks (WANs) © Copyright 2012 Pearson Education. All Rights Reserved.

Security Architecture and Design Domain Network Architecture Local area network (LAN) © Copyright 2012 Pearson Education. All Rights Reserved.

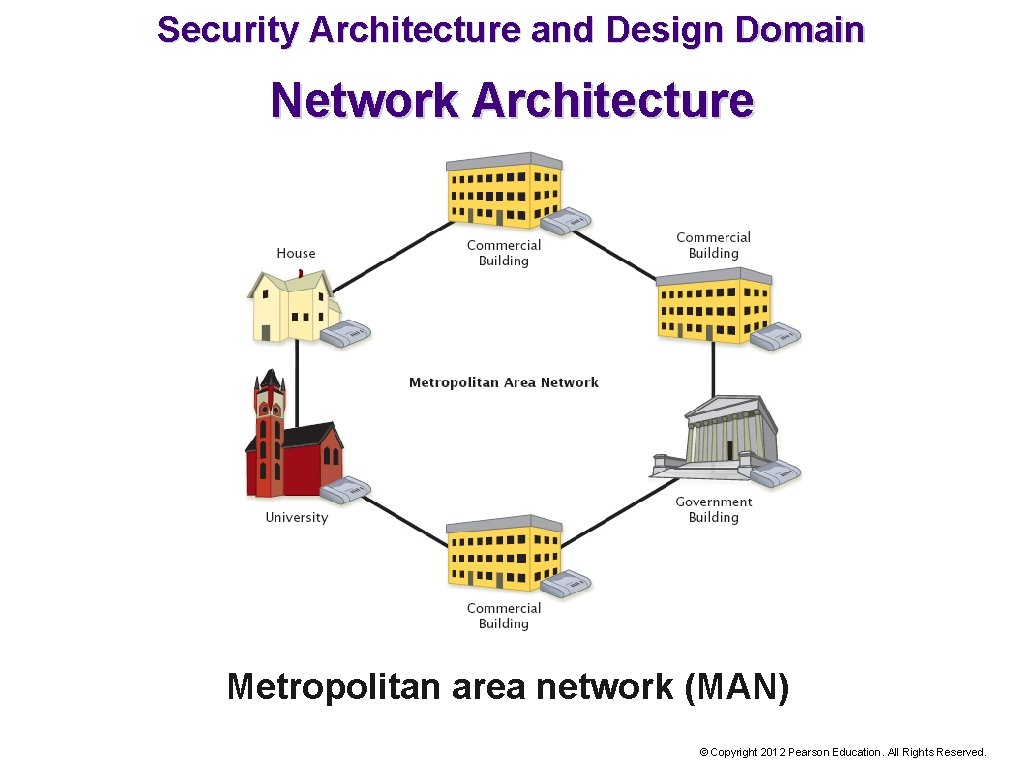
Security Architecture and Design Domain Network Architecture Metropolitan area network (MAN) © Copyright 2012 Pearson Education. All Rights Reserved.

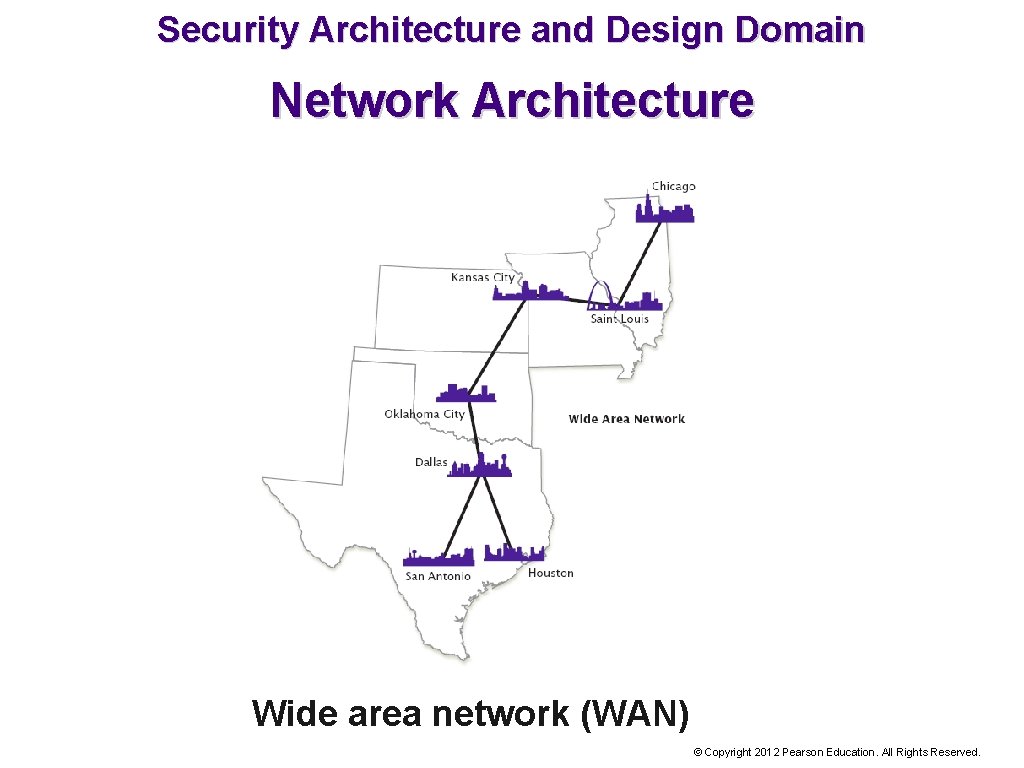
Security Architecture and Design Domain Network Architecture Wide area network (WAN) © Copyright 2012 Pearson Education. All Rights Reserved.

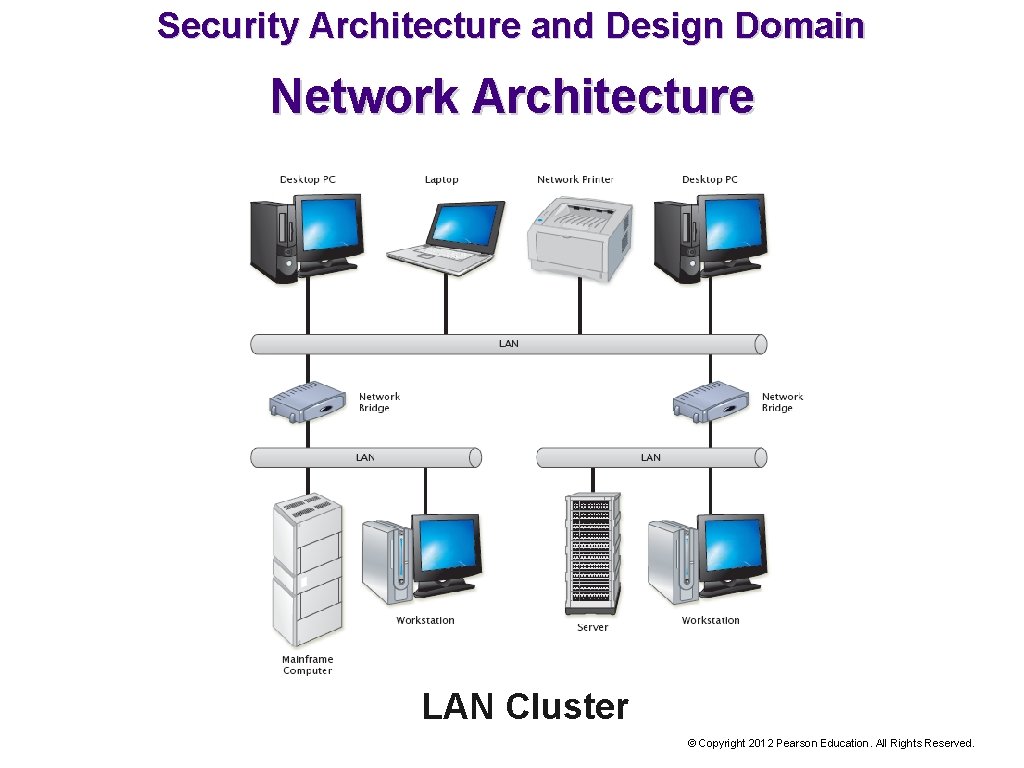
Security Architecture and Design Domain Network Architecture LAN Cluster © Copyright 2012 Pearson Education. All Rights Reserved.

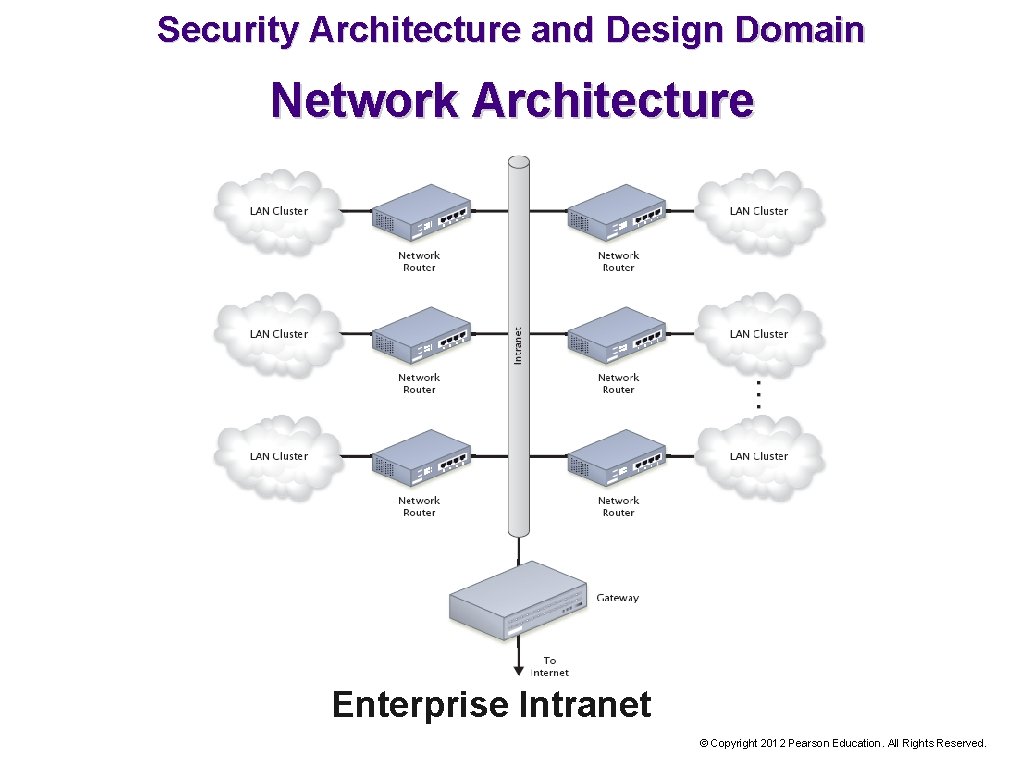
Security Architecture and Design Domain Network Architecture Enterprise Intranet © Copyright 2012 Pearson Education. All Rights Reserved.

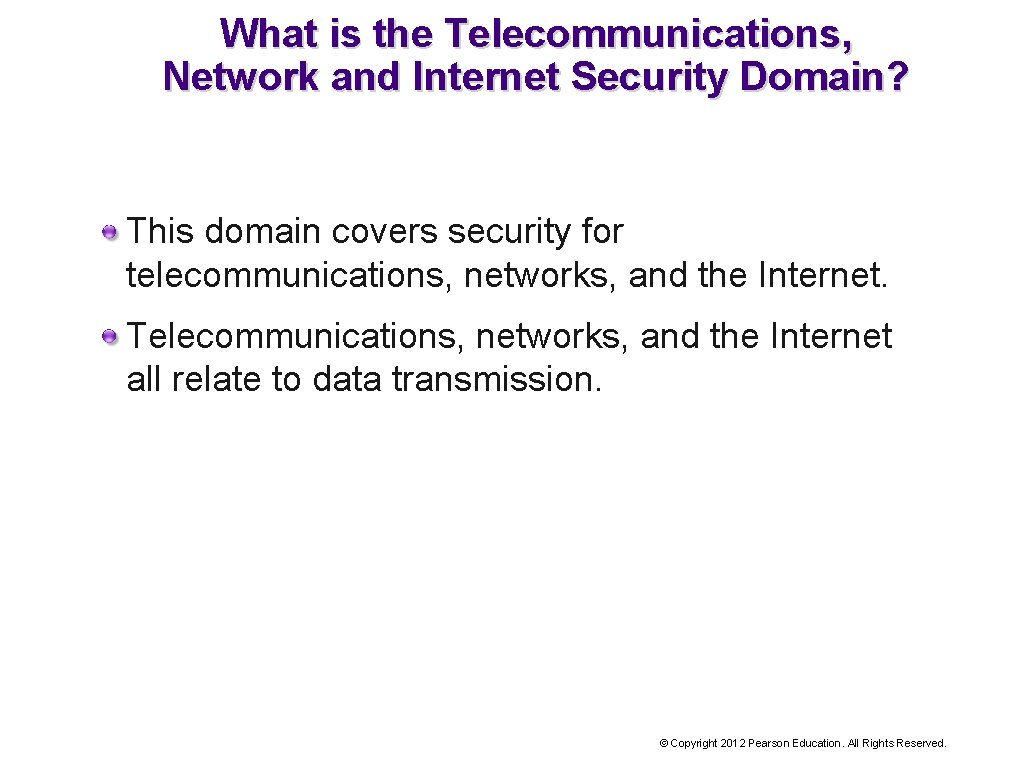
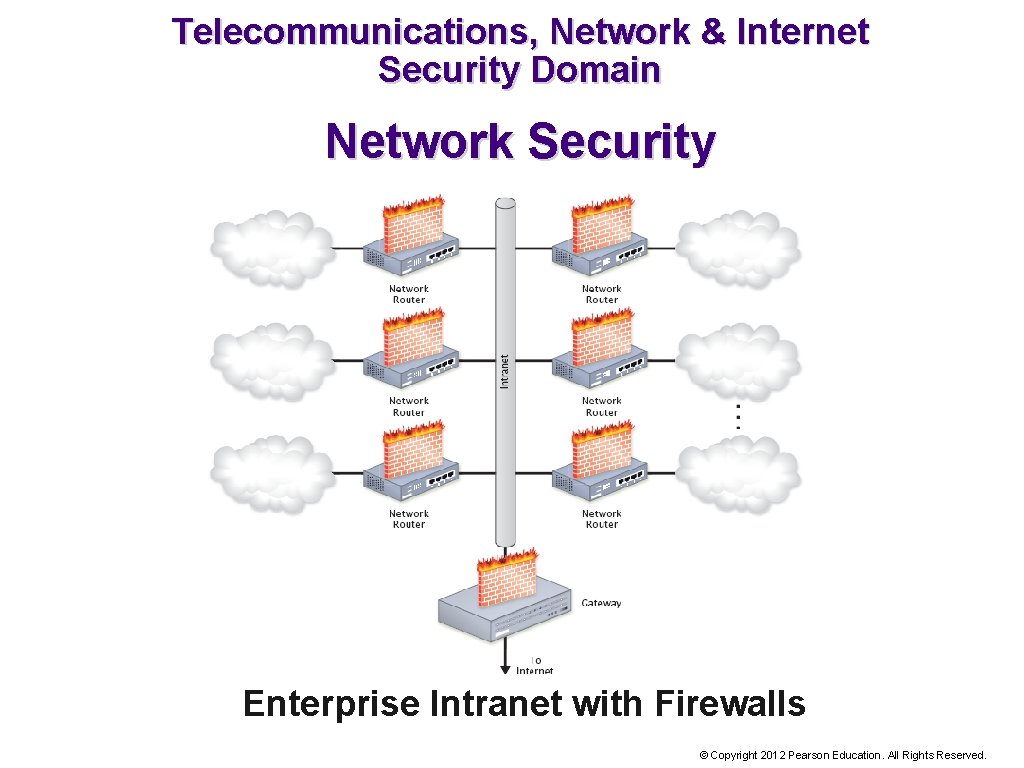
What is the Telecommunications, Network and Internet Security Domain? This domain covers security for telecommunications, networks, and the Internet. Telecommunications, networks, and the Internet all relate to data transmission. © Copyright 2012 Pearson Education. All Rights Reserved.

Telecommunications, Network & Internet Security Domain Network Security Cyberattacks often target network access points (NAP) because they offer access to the network. Routers, bridges, and gateways are access points to the network. Firewalls (software programs) that control traffic between two networks can be installed on these routing devices to prevent unauthorized access. © Copyright 2012 Pearson Education. All Rights Reserved.

Telecommunications, Network & Internet Security Domain Network Security Enterprise Intranet with Firewalls © Copyright 2012 Pearson Education. All Rights Reserved.

Telecommunications, Network & Internet Security Domain Internet Security Firewalls play an important role in e-commerce. If the website server is behind a high-security firewall, the website cannot be accessed by the general public. If the website is in front of the enterprise firewall, then hackers may deface the website. To address this dilemma, an enterprise places its web servers behind a low-level security firewall which is the first firewall to the outside world. Another high-level security firewall is located behind the web servers. © Copyright 2012 Pearson Education. All Rights Reserved.

Telecommunications, Network & Internet Security Domain Internet Security Demilitarized zone (DMZ) is the area between the first and second firewall. E-Commerce Architecture Using Firewalls and DMZ © Copyright 2012 Pearson Education. All Rights Reserved.

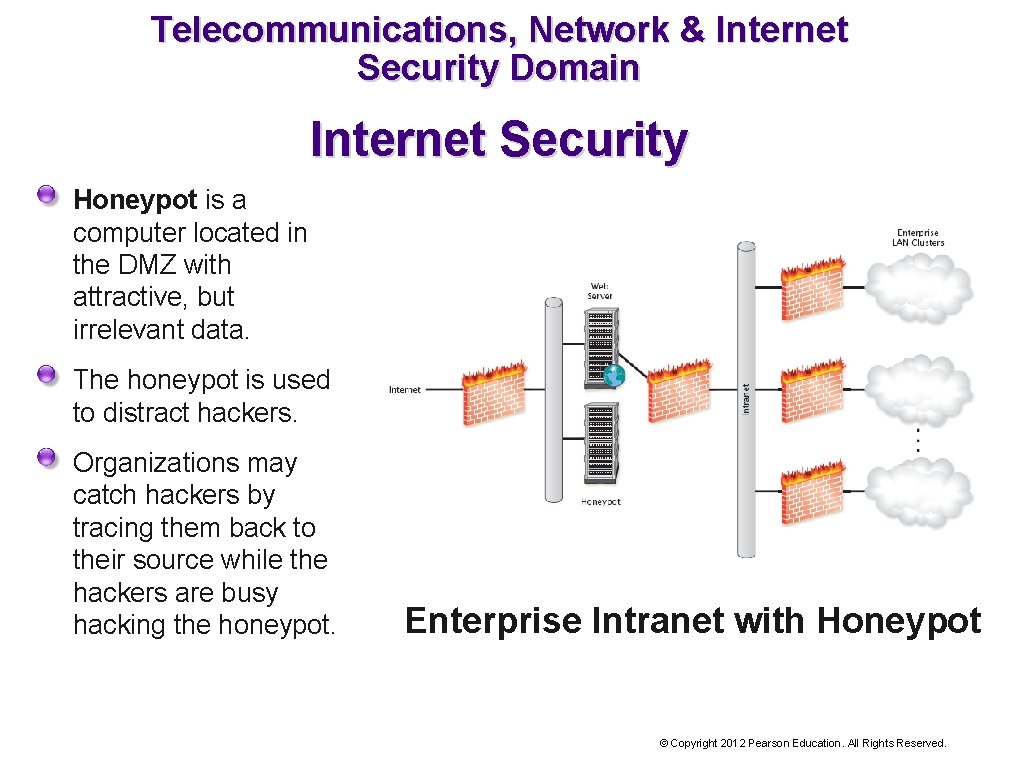
Telecommunications, Network & Internet Security Domain Internet Security Honeypot is a computer located in the DMZ with attractive, but irrelevant data. The honeypot is used to distract hackers. Organizations may catch hackers by tracing them back to their source while the hackers are busy hacking the honeypot. Enterprise Intranet with Honeypot © Copyright 2012 Pearson Education. All Rights Reserved.

What is the Control Access Domain? The control access domain addresses security for access to the enterprise system, including computers, networks, routers and databases. Access control threats include: Network sniffers that examines traffic on the network Phishing to obtain confidential information Identify theft © Copyright 2012 Pearson Education. All Rights Reserved.

Access Control Domain Access Control Principles Security principles for access control include: Identification Authentication Authorization Accountability For a user to be allowed access to a secured system (computers and network) the user should be identified, authenticated, and then authorized to access the system. © Copyright 2012 Pearson Education. All Rights Reserved.

Access Control Domain Password Management To identify users, usernames and passwords may be required to log in to the system. Password management involves: Number of passwords a user has How frequently the password must be changed Password format including length and type (e. g. , alphanumeric) Number of incorrect login attempts © Copyright 2012 Pearson Education. All Rights Reserved.

Access Control Domain Password Management Dynamic password: a password that is used once and then changed. Token device (TD): Is a hardware device containing a password generator protocol. Creates a new password each time the token is used. Eliminates the need for the user to memorize a continually changing password. Single sign-on (SSO): permits the user to use one username and password to log into various systems. © Copyright 2012 Pearson Education. All Rights Reserved.

Access Control Domain Biometric Access Biometrics is an access method which identifies the user by analyzing his/her personal attributes. Biometrics include: fingerprints face recognition retina scans palm scans © Copyright 2012 Pearson Education. All Rights Reserved.

Access Control Domain Intrusion Prevention Systems Intrusion prevention systems (IPS) attempt to prevent cyberattacks from occurring. Intrusion detection systems (IDS) are inadequate because the attack has already occurred. IPS can include sniffers used by the enterprise to detect malicious messages on its own network. The message can be destroyed before causing harm. © Copyright 2012 Pearson Education. All Rights Reserved.

What is the Operations Security Domain? Operations security refers to activities and procedures required to keep information technology running securely IT security management includes responsibility for maintaining security devices and software, such as virus detection, firewalls, Intrusion Prevention Systems (IPS), and Intrusion Detection Systems (IDS). Security assessment is carried out on a scheduled basis to evaluate the security of the various components of the enterprise system. IT security operational responsibilities relate to how the enterprise system operates. It includes input/output controls, accounting for software licenses, training for all employees regarding security procedures, conducting vulnerability checks, and developing contingency plans for cyberattacks. © Copyright 2012 Pearson Education. All Rights Reserved.

What is the Physical and Environmental Security Domain? The physical and environmental security domain addresses the physical security of information technology components, such as hardware and software. Physical threats include natural environmental disasters, such as fire and flood, supply system threats, man-made threats, and politically motivated threats. © Copyright 2012 Pearson Education. All Rights Reserved.

What is the Application Security Domain? The application security domain addresses security and controls for application software, including input, processing, and output. Application software includes accounting and spreadsheet software that accounting professionals use daily. © Copyright 2012 Pearson Education. All Rights Reserved.

Application Security Domain Malware (malicious software) is spread throughout an enterprise system by email, fake advertisements, Internet downloads, and shared drives. Malware includes: Viruses Bots Worms Logic bombs Trojan horses Spam © Copyright 2012 Pearson Education. All Rights Reserved.

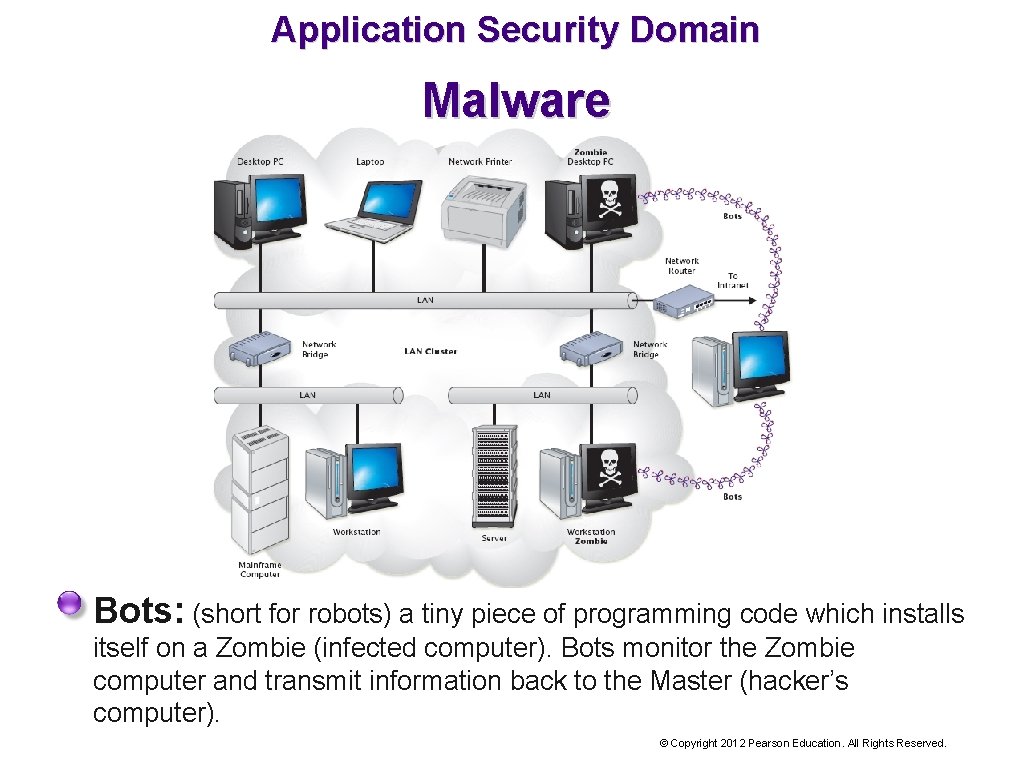
Application Security Domain Malware Bots: (short for robots) a tiny piece of programming code which installs itself on a Zombie (infected computer). Bots monitor the Zombie computer and transmit information back to the Master (hacker’s computer). © Copyright 2012 Pearson Education. All Rights Reserved.

Application Security Domain Malware Viruses: a small computer program that infects other application software by attaching to and disrupting the application’s function. Antivirus software can detect and remove viruses. Logic bombs: malware that executes when a specified event happens within the computer, as for example, when the user logs into his or her bank account. Trojan horses: malware disguised as a legitimate program that may be downloaded and installed by users without realizing it is a virus. Spam: malware sent by email. Spam can be a virus, bot, logic bomb, worm, or Trojan horse. © Copyright 2012 Pearson Education. All Rights Reserved.

What is the Business Continuity and Disaster Recovery Domain? This domain addresses an enterprise’s business continuity and disaster recovery plan. The goals of a disaster recovery plan include: Minimize disruption, damage, and loss from a disaster Provide a temporary method for processing business and accounting transactions Resume normal operations quickly © Copyright 2012 Pearson Education. All Rights Reserved.

Business Continuity and Disaster Recovery Domain Backup Methods Accounting data backups are critical and should be scheduled on a regular basis. Grandfather-Father-Son method involves making multiple backups, one each day, for example. Monday backup (Grandfather) Tuesday backup (Father) Wednesday backup (Son) and so on. . © Copyright 2012 Pearson Education. All Rights Reserved.

Business Continuity and Disaster Recovery Domain Backup Facilities Backup facilities can include: Reciprocal agreements between organizations can be used to provide backup services. Internal sites can be used by large organizations with multiple locations. Hot site is a commercial disaster recovery service that can be leased by an enterprise to provide IT services in the event of a disaster, fully operational in a few hours. Warm site is a commercial disaster recovery service that is only partially configured with some equipment and may take a few days to be operational. Cold site is a commercial disaster recovery service providing air conditioning, wiring, and plumbing, but no IT equipment, taking several days to be operational. © Copyright 2012 Pearson Education. All Rights Reserved.

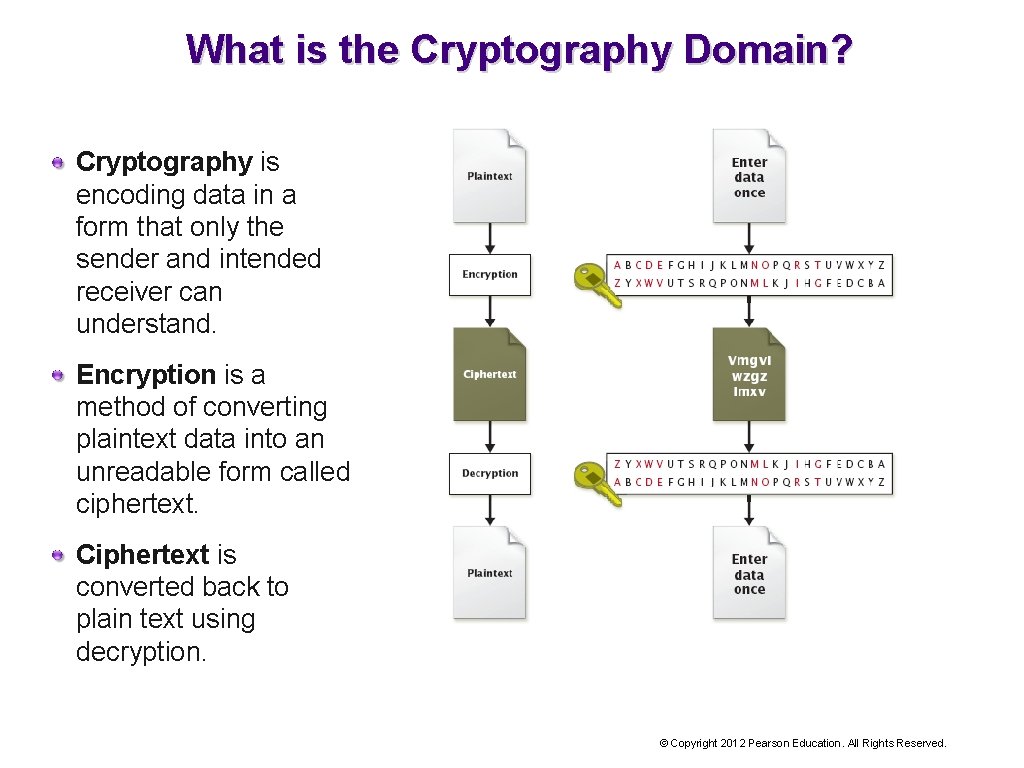
What is the Cryptography Domain? Cryptography is encoding data in a form that only the sender and intended receiver can understand. Encryption is a method of converting plaintext data into an unreadable form called ciphertext. Ciphertext is converted back to plain text using decryption. © Copyright 2012 Pearson Education. All Rights Reserved.

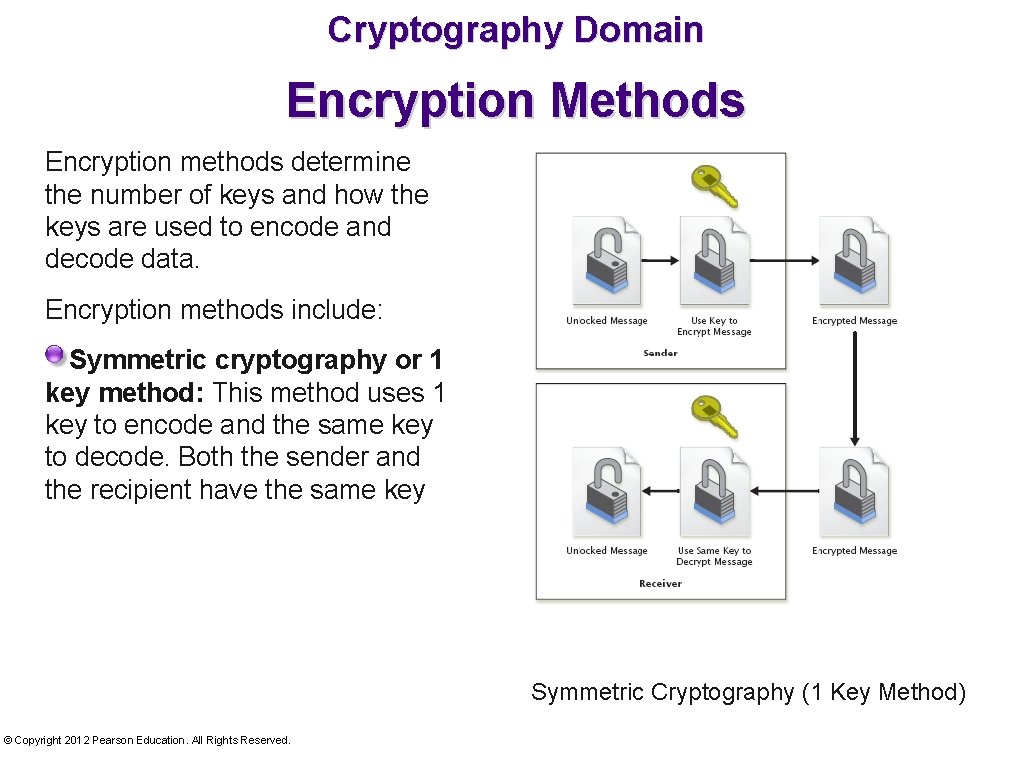
Cryptography Domain Encryption Methods Encryption methods determine the number of keys and how the keys are used to encode and decode data. Encryption methods include: Symmetric cryptography or 1 key method: This method uses 1 key to encode and the same key to decode. Both the sender and the recipient have the same key Symmetric Cryptography (1 Key Method) © Copyright 2012 Pearson Education. All Rights Reserved.

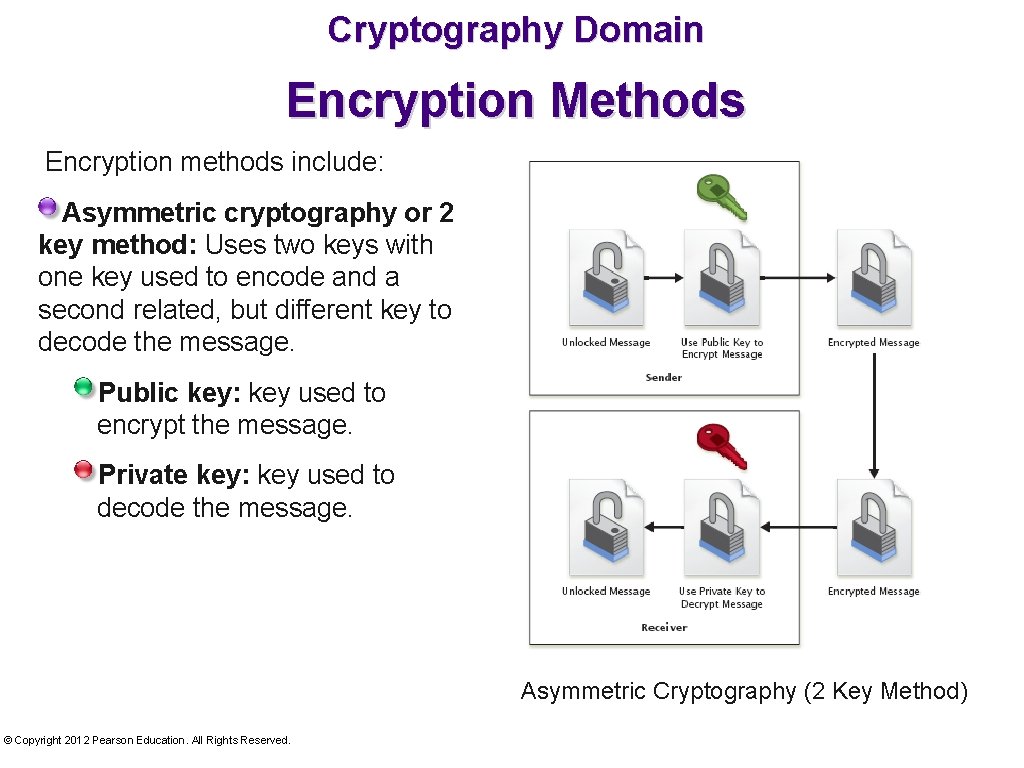
Cryptography Domain Encryption Methods Encryption methods include: Asymmetric cryptography or 2 key method: Uses two keys with one key used to encode and a second related, but different key to decode the message. Public key: key used to encrypt the message. Private key: key used to decode the message. Asymmetric Cryptography (2 Key Method) © Copyright 2012 Pearson Education. All Rights Reserved.

Cryptography Domain Encryption Methods Encryption methods include: Digital envelope or 3 key method: combines symmetric and asymmetric cryptography. The intended recipient’s key is transmitted using the 2 Key method in a digital envelope. © Copyright 2012 Pearson Education. All Rights Reserved.

Cryptography Domain Encryption Methods Encryption is a useful tool for protecting data in transit and when stored in databases. As encryption tools have improved, crackers (high-level hackers) use more sophisticated techniques to bypass data encryption. Example: malware that captures keystrokes for data as the user is entering the data into the computer screen. Data is captured by the cracker before there is a chance for it to be encrypted. © Copyright 2012 Pearson Education. All Rights Reserved.

© Copyright 2012 Pearson Education. All Rights Reserved.
 Chapter 31 societies at crossroads
Chapter 31 societies at crossroads Crossroads quilt pattern meaning
Crossroads quilt pattern meaning What is an archetype
What is an archetype Crossroads archetype examples
Crossroads archetype examples The helpers archetype examples
The helpers archetype examples Character color archetypes
Character color archetypes Why do geographers call arabia a crossroads location
Why do geographers call arabia a crossroads location Crossroads of the world middle east
Crossroads of the world middle east Crossroads turning points
Crossroads turning points Crossroads bank for social security
Crossroads bank for social security Dr rick griffith
Dr rick griffith Children is countable or uncountable
Children is countable or uncountable Crossroads international church singapore
Crossroads international church singapore Crossroads hotel lilongwe
Crossroads hotel lilongwe Chapter 7 accounting information systems
Chapter 7 accounting information systems Chapter 7 accounting information systems
Chapter 7 accounting information systems Accounting information system chapter 1
Accounting information system chapter 1 Core concepts of accounting information systems
Core concepts of accounting information systems Accounting information system شرح
Accounting information system شرح Tactical accounting and financial information system
Tactical accounting and financial information system Chapter 7 accounting information systems
Chapter 7 accounting information systems Accounting information systems marshall b romney
Accounting information systems marshall b romney Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Lp html
Lp html Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Voi kéo gỗ như thế nào
Voi kéo gỗ như thế nào Thang điểm glasgow
Thang điểm glasgow Chúa sống lại
Chúa sống lại Kể tên các môn thể thao
Kể tên các môn thể thao Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công thức tiính động năng
Công thức tiính động năng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Cách giải mật thư tọa độ
Cách giải mật thư tọa độ 101012 bằng
101012 bằng Phản ứng thế ankan
Phản ứng thế ankan Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thể thơ truyền thống
Thể thơ truyền thống Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng xinh xinh thế chỉ nói điều hay thôi
Cái miệng xinh xinh thế chỉ nói điều hay thôi Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Nguyên nhân của sự mỏi cơ sinh 8
Nguyên nhân của sự mỏi cơ sinh 8 đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Thế nào là giọng cùng tên?
Thế nào là giọng cùng tên? Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Fecboak
Fecboak Thẻ vin
Thẻ vin đại từ thay thế
đại từ thay thế điện thế nghỉ
điện thế nghỉ Tư thế ngồi viết
Tư thế ngồi viết










































































