Access Control Convergence Challenges and Opportunities Ravi Sandhu






- Slides: 30

Access Control Convergence: Challenges and Opportunities Ravi Sandhu Executive Director and Chief Scientist Professor of Computer Science Lutcher Brown Chair in Cyber Security International Conference on Information Systems Security December 2020 ravi. sandhu@utsa. edu www. ics. utsa. edu www. profsandhu. com © Ravi Sandhu World-Leading Research with Real-World Impact! 1

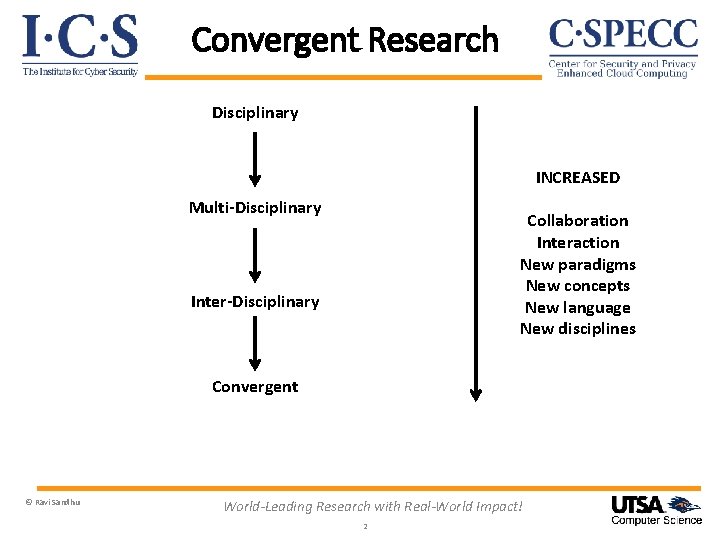
Convergent Research Disciplinary INCREASED Multi-Disciplinary Collaboration Interaction New paradigms New concepts New language New disciplines Inter-Disciplinary Convergent © Ravi Sandhu World-Leading Research with Real-World Impact! 2

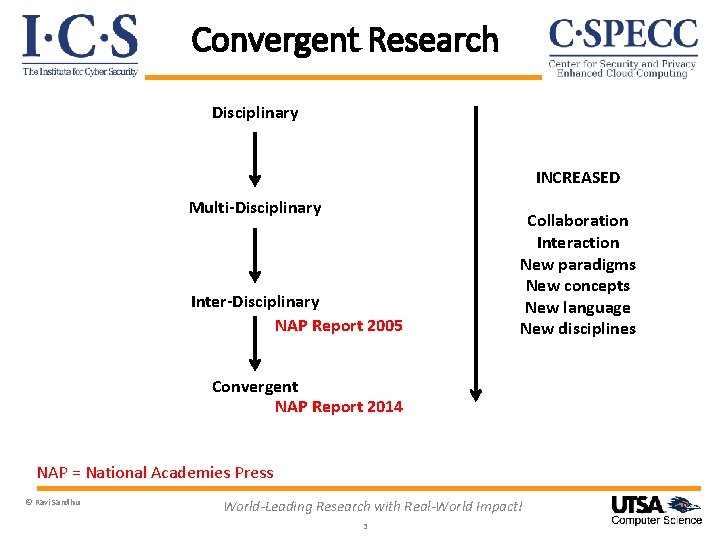
Convergent Research Disciplinary INCREASED Multi-Disciplinary Inter-Disciplinary NAP Report 2005 Collaboration Interaction New paradigms New concepts New language New disciplines Convergent NAP Report 2014 NAP = National Academies Press © Ravi Sandhu World-Leading Research with Real-World Impact! 3

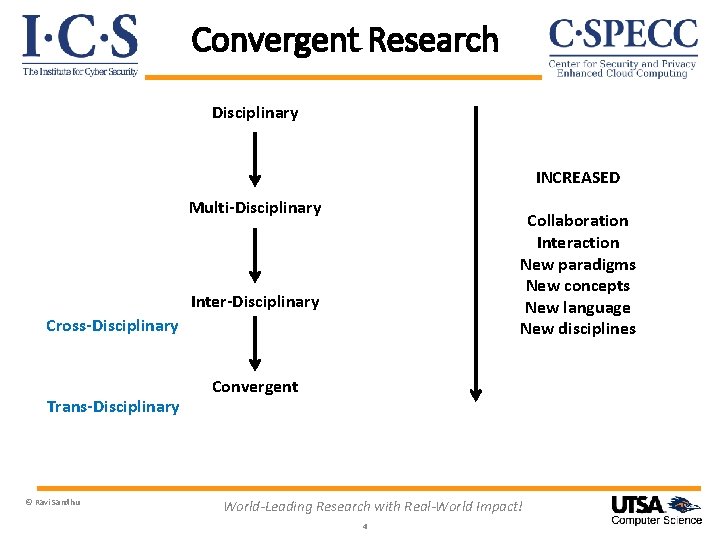
Convergent Research Disciplinary INCREASED Multi-Disciplinary Collaboration Interaction New paradigms New concepts New language New disciplines Inter-Disciplinary Cross-Disciplinary Trans-Disciplinary © Ravi Sandhu Convergent World-Leading Research with Real-World Impact! 4

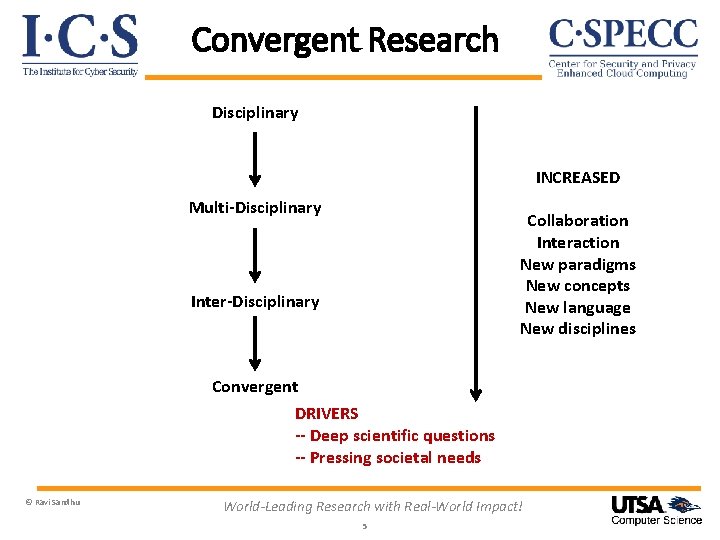
Convergent Research Disciplinary INCREASED Multi-Disciplinary Collaboration Interaction New paradigms New concepts New language New disciplines Inter-Disciplinary Convergent DRIVERS -- Deep scientific questions -- Pressing societal needs © Ravi Sandhu World-Leading Research with Real-World Impact! 5

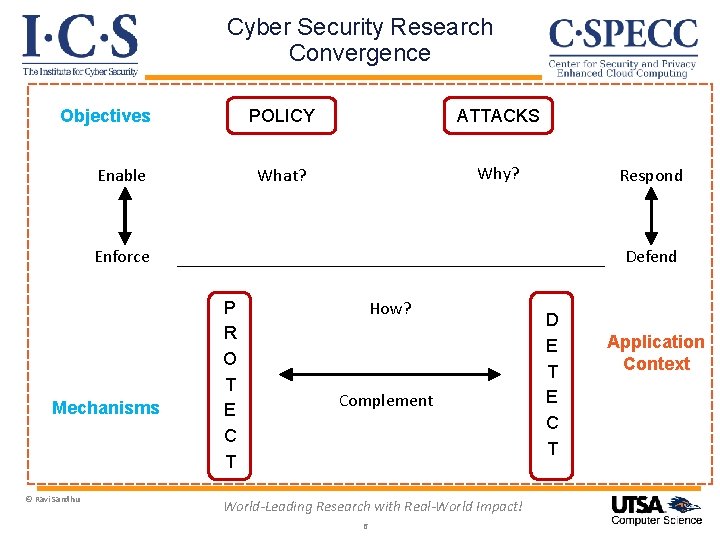
Cyber Security Research Convergence Objectives Enable POLICY ATTACKS What? Why? Respond Enforce Mechanisms © Ravi Sandhu Defend P R O T E C T How? Complement World-Leading Research with Real-World Impact! 6 D E T E C T Application Context

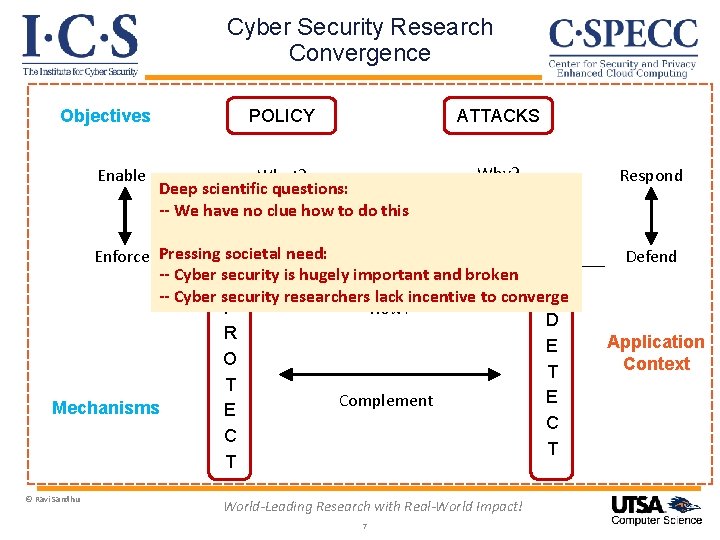
Cyber Security Research Convergence Objectives Enable POLICY ATTACKS What? Deep scientific questions: -- We have no clue how to do this Why? Enforce Pressing societal need: -- Cyber security is hugely important and broken -- Cyber security researchers lack incentive to converge P How? D R E O T T E Complement Mechanisms E C C T T © Ravi Sandhu World-Leading Research with Real-World Impact! 7 Respond Defend Application Context

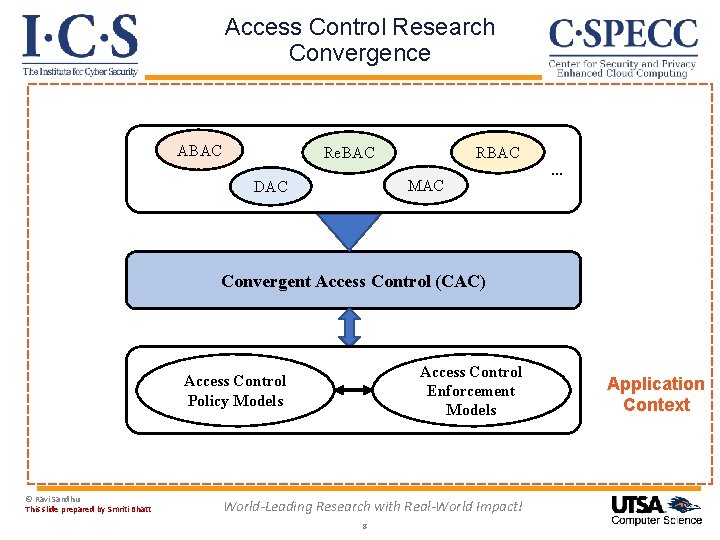
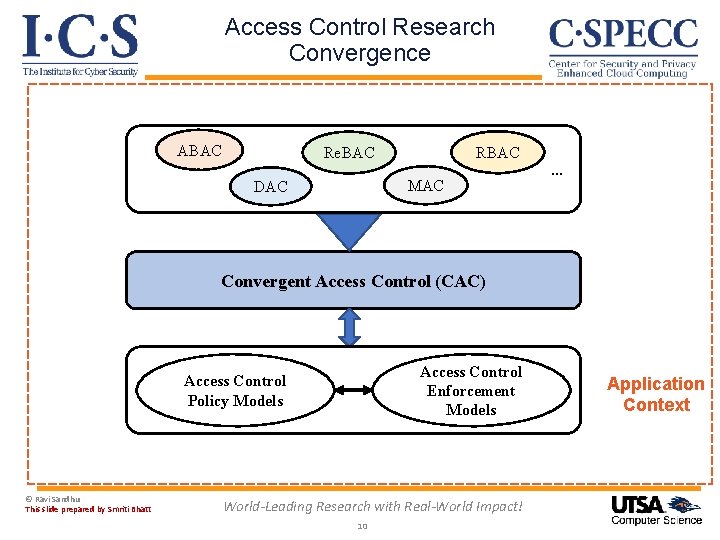
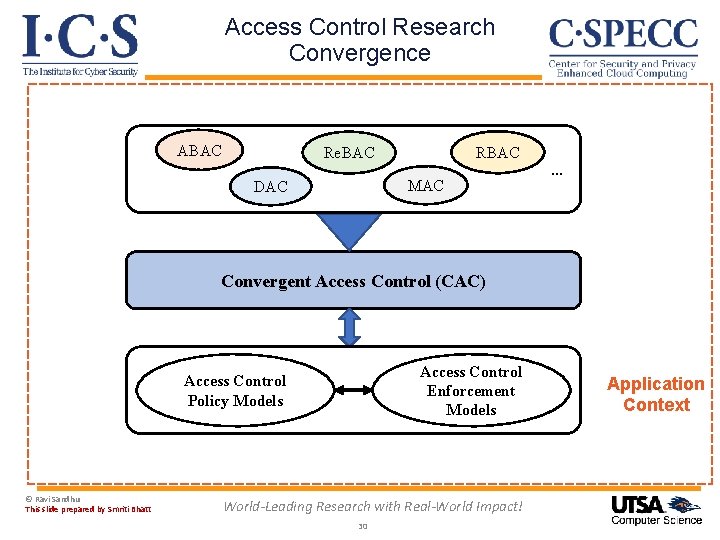
Access Control Research Convergence ABAC Re. BAC MAC DAC … Convergent Access Control (CAC) Access Control Enforcement Models Access Control Policy Models © Ravi Sandhu This slide prepared by Smriti Bhatt World-Leading Research with Real-World Impact! 8 Application Context

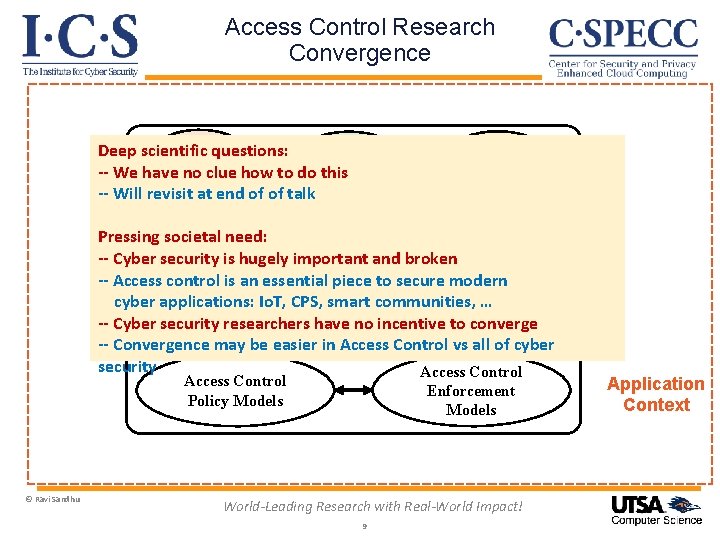
Access Control Research Convergence ABAC Deep scientific questions: Re. BAC -- We have no clue how to do this DAC -- Will revisit at end of of talk RBAC MAC … Pressing societal need: -- Cyber security is hugely important and broken -- Access control Convergent is an essential piece. Control to secure modern Access (CAC) cyber applications: Io. T, CPS, smart communities, … -- Cyber security researchers have no incentive to converge -- Convergence may be easier in Access Control vs all of cyber security Access Control Policy Models © Ravi Sandhu Enforcement Models World-Leading Research with Real-World Impact! 9 Application Context

Access Control Research Convergence ABAC Re. BAC MAC DAC … Convergent Access Control (CAC) Access Control Enforcement Models Access Control Policy Models © Ravi Sandhu This slide prepared by Smriti Bhatt World-Leading Research with Real-World Impact! 10 Application Context

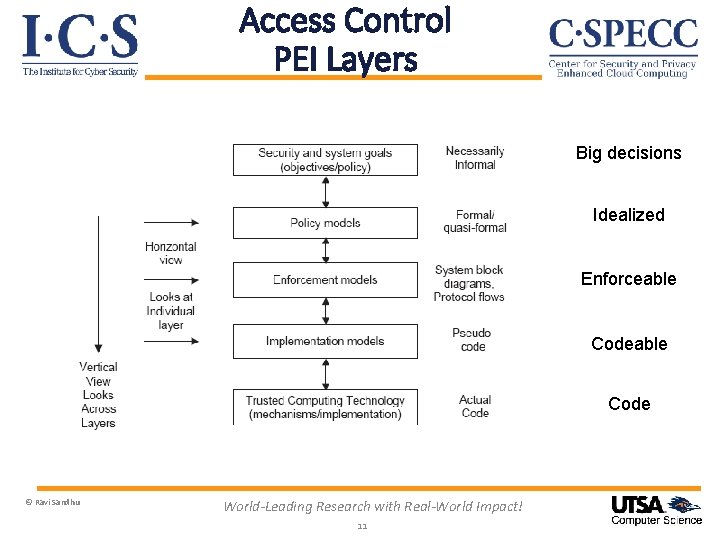
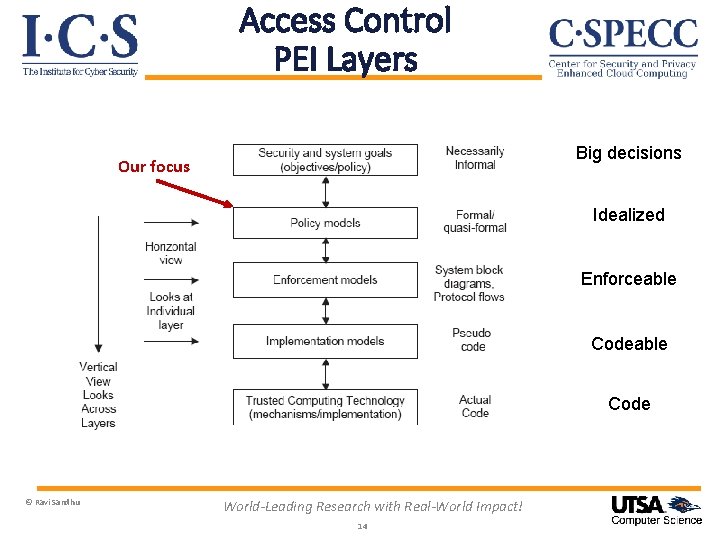
Access Control PEI Layers Big decisions Idealized Enforceable Code © Ravi Sandhu World-Leading Research with Real-World Impact! 11

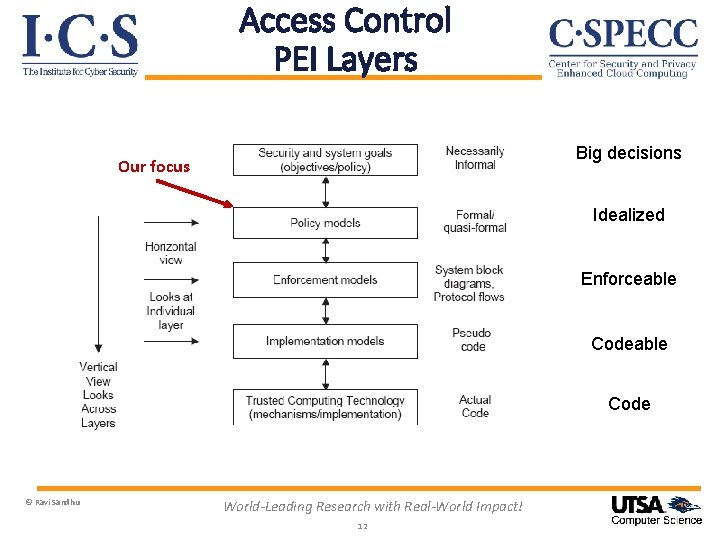
Access Control PEI Layers Big decisions Our focus Idealized Enforceable Code © Ravi Sandhu World-Leading Research with Real-World Impact! 12

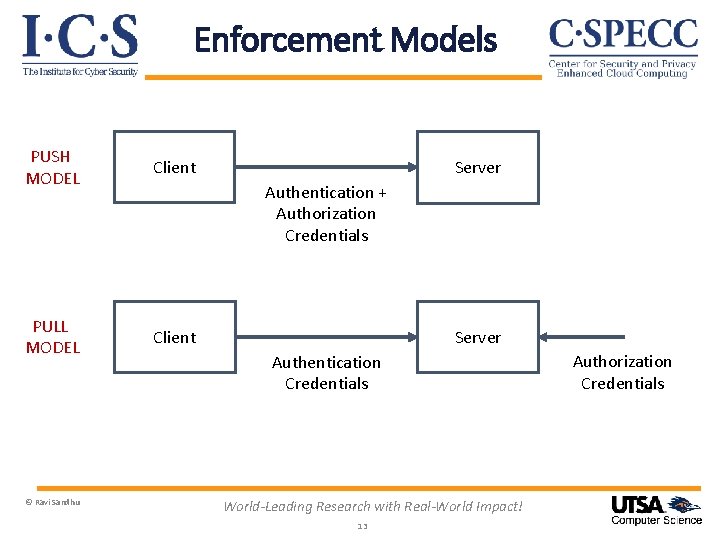
Enforcement Models PUSH MODEL Client PULL MODEL Client © Ravi Sandhu Server Authentication + Authorization Credentials Server Authentication Credentials World-Leading Research with Real-World Impact! 13 Authorization Credentials

Access Control PEI Layers Big decisions Our focus Idealized Enforceable Code © Ravi Sandhu World-Leading Research with Real-World Impact! 14

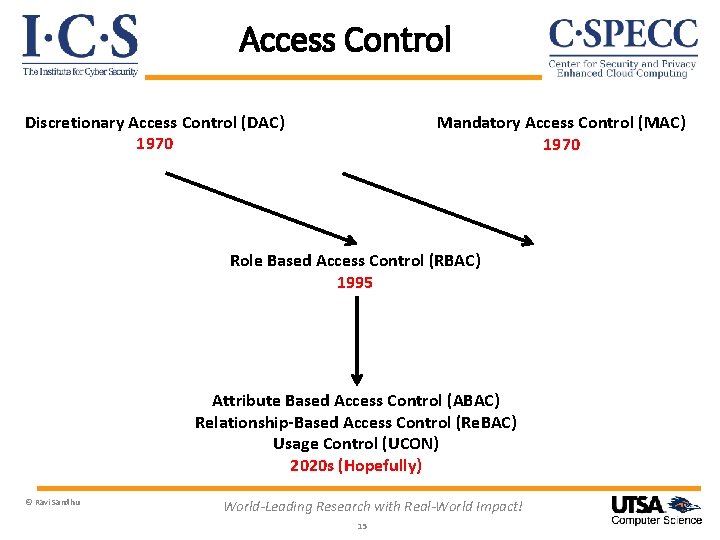
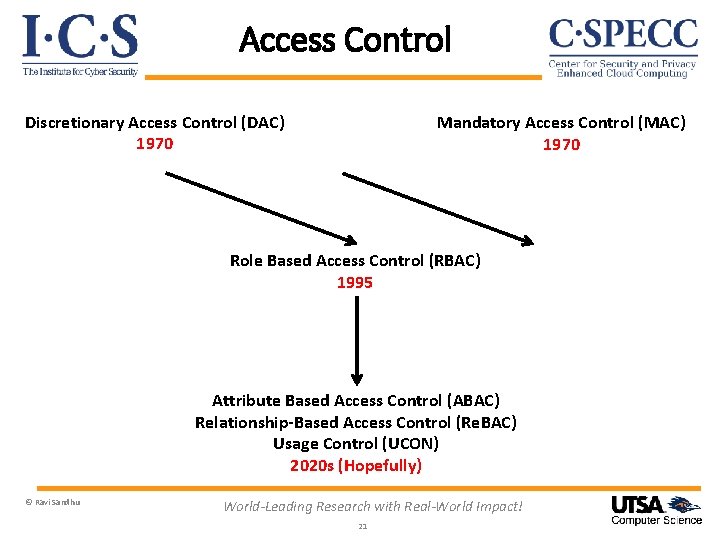
Access Control Discretionary Access Control (DAC) 1970 Mandatory Access Control (MAC) 1970 Role Based Access Control (RBAC) 1995 Attribute Based Access Control (ABAC) Relationship-Based Access Control (Re. BAC) Usage Control (UCON) 2020 s (Hopefully) © Ravi Sandhu World-Leading Research with Real-World Impact! 15

Discretionary Access Control (DAC) Ø Core concept: Custodian of information determines access Ø Core drawback: Does not protect copies Therefore OK for integrity but not for confidentiality Ø Sophistication: Delegation of custody Denials or negative rights © Ravi Sandhu World-Leading Research with Real-World Impact! 16

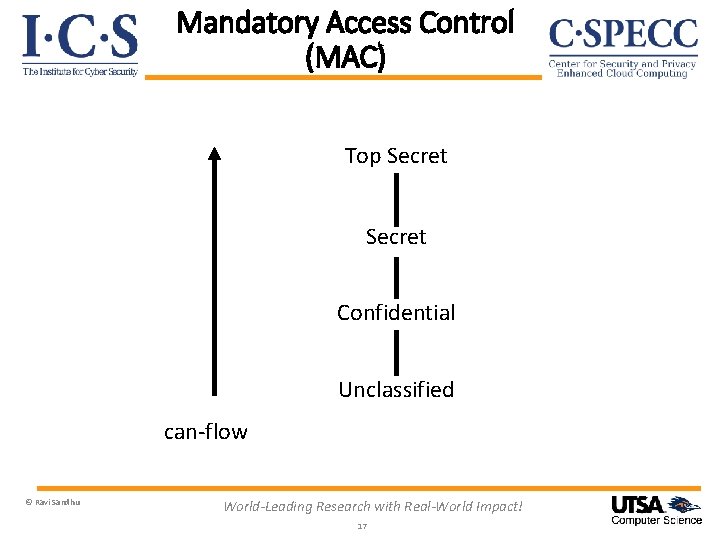
Mandatory Access Control (MAC) Top Secret Confidential Unclassified can-flow © Ravi Sandhu World-Leading Research with Real-World Impact! 17

Mandatory Access Control (MAC) Ø Core concept: Extend control to copies by means of security labels Ø Core drawback: Covert/side channels bypass MAC Inference not prevented Too strict Too reductionist Ø Sophistication: Dynamic labels © Ravi Sandhu World-Leading Research with Real-World Impact! 18

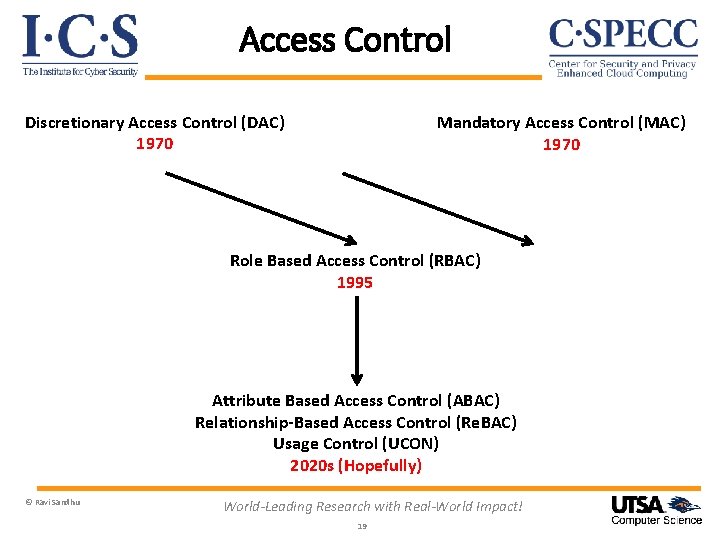
Access Control Discretionary Access Control (DAC) 1970 Mandatory Access Control (MAC) 1970 Role Based Access Control (RBAC) 1995 Attribute Based Access Control (ABAC) Relationship-Based Access Control (Re. BAC) Usage Control (UCON) 2020 s (Hopefully) © Ravi Sandhu World-Leading Research with Real-World Impact! 19

Role-Based Access Control (RBAC) Ø Core concept: Roles determine everything Ø Core drawback: Roles are a natural concept for human users But not so natural for: Information objects Io. T things Contextual attributes Ø Sophistication: Role hierarchies Role constraints © Ravi Sandhu World-Leading Research with Real-World Impact! 20

Access Control Discretionary Access Control (DAC) 1970 Mandatory Access Control (MAC) 1970 Role Based Access Control (RBAC) 1995 Attribute Based Access Control (ABAC) Relationship-Based Access Control (Re. BAC) Usage Control (UCON) 2020 s (Hopefully) © Ravi Sandhu World-Leading Research with Real-World Impact! 21

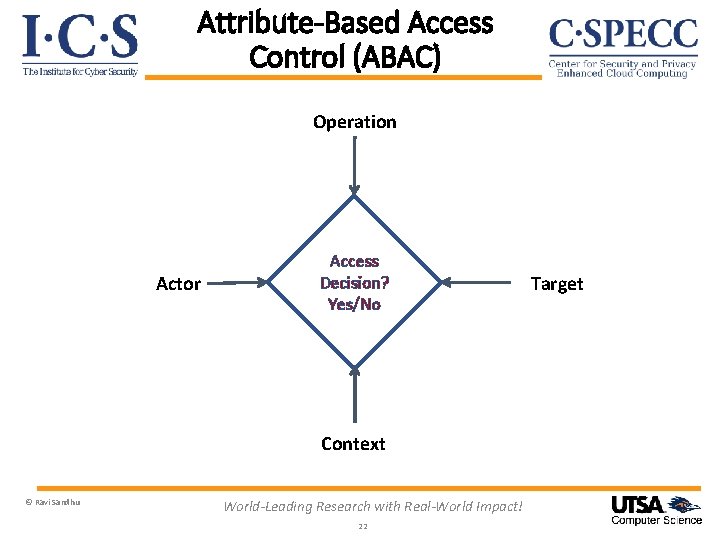
Attribute-Based Access Control (ABAC) Operation Actor Access Decision? Yes/No Context © Ravi Sandhu World-Leading Research with Real-World Impact! 22 Target

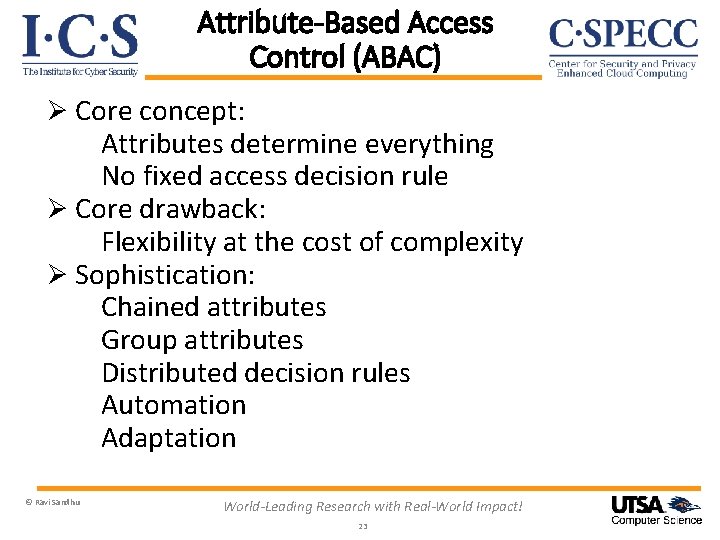
Attribute-Based Access Control (ABAC) Ø Core concept: Attributes determine everything No fixed access decision rule Ø Core drawback: Flexibility at the cost of complexity Ø Sophistication: Chained attributes Group attributes Distributed decision rules Automation Adaptation © Ravi Sandhu World-Leading Research with Real-World Impact! 23

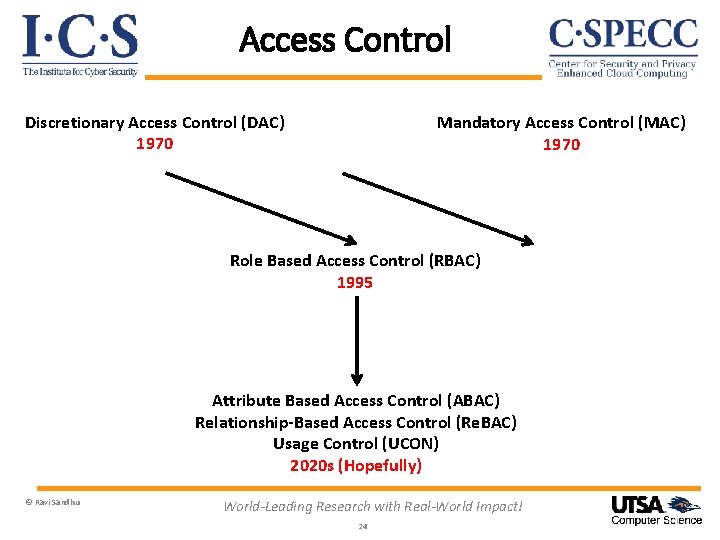
Access Control Discretionary Access Control (DAC) 1970 Mandatory Access Control (MAC) 1970 Role Based Access Control (RBAC) 1995 Attribute Based Access Control (ABAC) Relationship-Based Access Control (Re. BAC) Usage Control (UCON) 2020 s (Hopefully) © Ravi Sandhu World-Leading Research with Real-World Impact! 24

Access Control: Where Are We? Ø Rich set of building blocks: DAC, MAC, RBAC, ABAC, Re. BAC, UCON Ø We have some understanding of the relationships amongst these © Ravi Sandhu World-Leading Research with Real-World Impact! 25

Access Control: What Next? Ø Rich set of building blocks: DAC, MAC, RBAC, ABAC, Re. BAC, UCON Ø We have some understanding of the relationships amongst these Ø Do we need more building blocks? Ø We have very little understanding of synergy amongst these © Ravi Sandhu World-Leading Research with Real-World Impact! 26

Access Control: What Next? Ø Rich set of building blocks: DAC, MAC, RBAC, ABAC, Re. BAC, UCON Ø We have some understanding of the relationships amongst these Ø Do we need more building blocks? Ø We have very little understanding of synergy amongst these © Ravi Sandhu Deep scientific question for convergent research World-Leading Research with Real-World Impact! 27

Access Control: What Next? Ø Rich set of building blocks: DAC, MAC, RBAC, ABAC, Re. BAC, UCON Ø We have some understanding of the relationships amongst these Ø Do we need more building blocks? Ø We have very little understanding of synergy amongst these Pressing societal need? © Ravi Sandhu Deep scientific question for convergent research World-Leading Research with Real-World Impact! 28

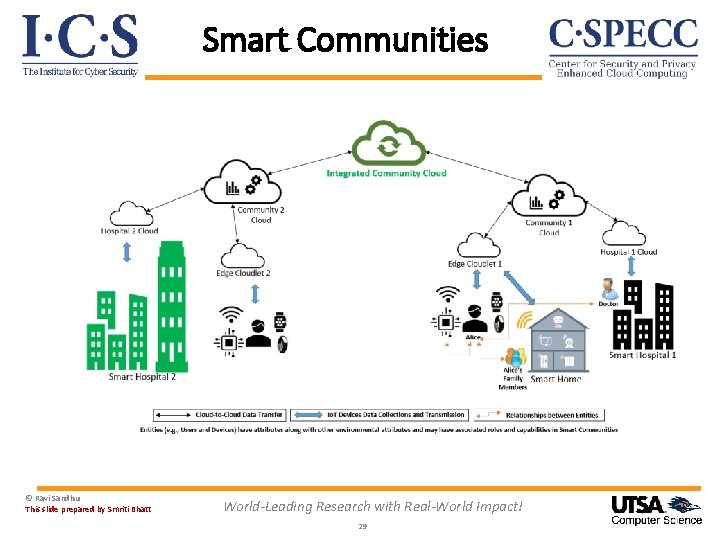
Smart Communities © Ravi Sandhu This slide prepared by Smriti Bhatt World-Leading Research with Real-World Impact! 29

Access Control Research Convergence ABAC Re. BAC MAC DAC … Convergent Access Control (CAC) Access Control Enforcement Models Access Control Policy Models © Ravi Sandhu This slide prepared by Smriti Bhatt World-Leading Research with Real-World Impact! 30 Application Context