OMAM and PEI Prof Ravi Sandhu Ravi Sandhu

- Slides: 12

OM-AM and PEI Prof. Ravi Sandhu © Ravi Sandhu 1

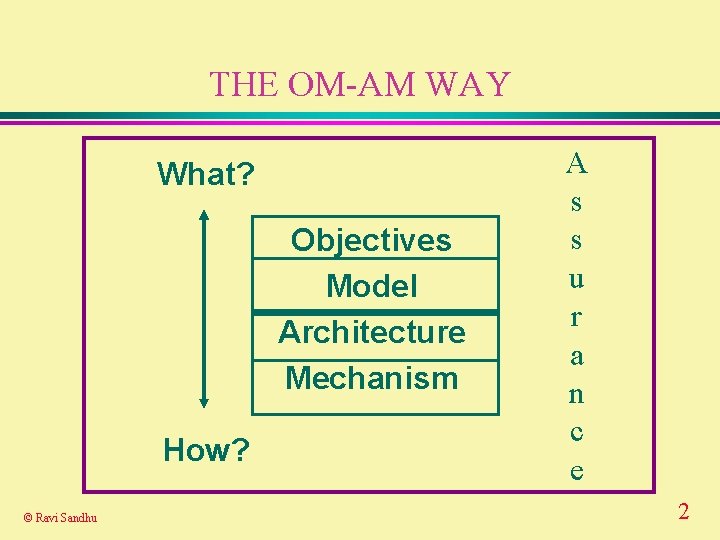
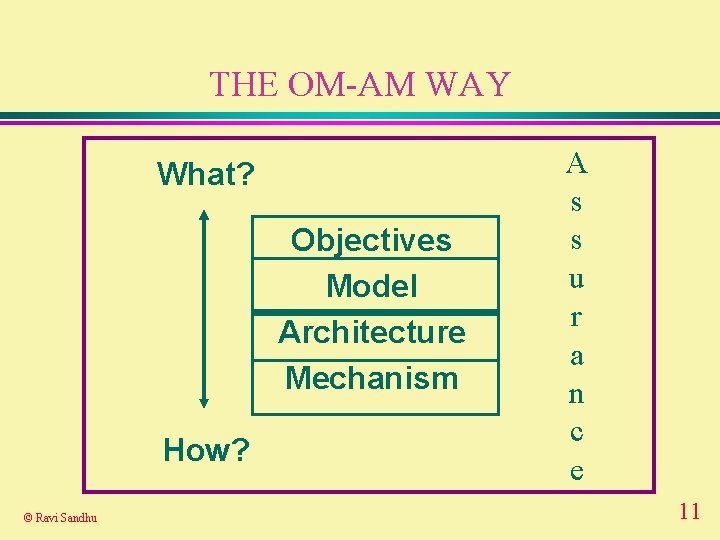
THE OM-AM WAY What? Objectives Model Architecture Mechanism How? © Ravi Sandhu A s s u r a n c e 2

LAYERS AND LAYERS Multics rings v Layered abstractions v Waterfall model v Network protocol stacks v Napolean layers v Ro. Fi layers v OM-AM v etcetera v © Ravi Sandhu 3

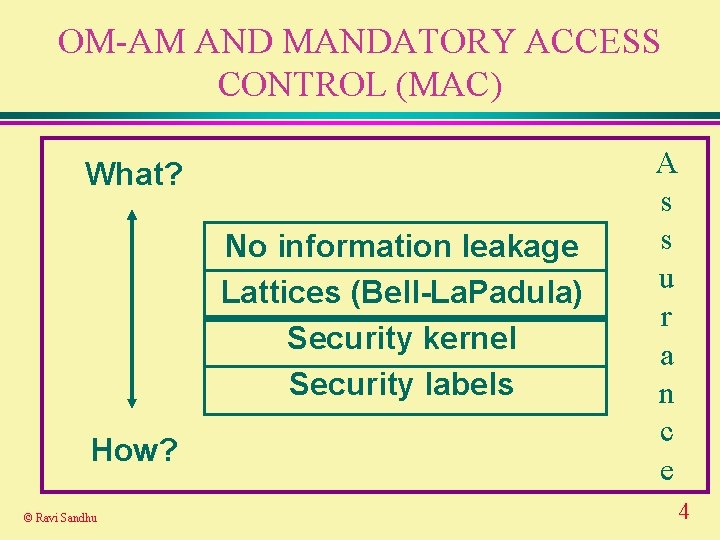
OM-AM AND MANDATORY ACCESS CONTROL (MAC) What? No information leakage Lattices (Bell-La. Padula) Security kernel Security labels How? © Ravi Sandhu A s s u r a n c e 4

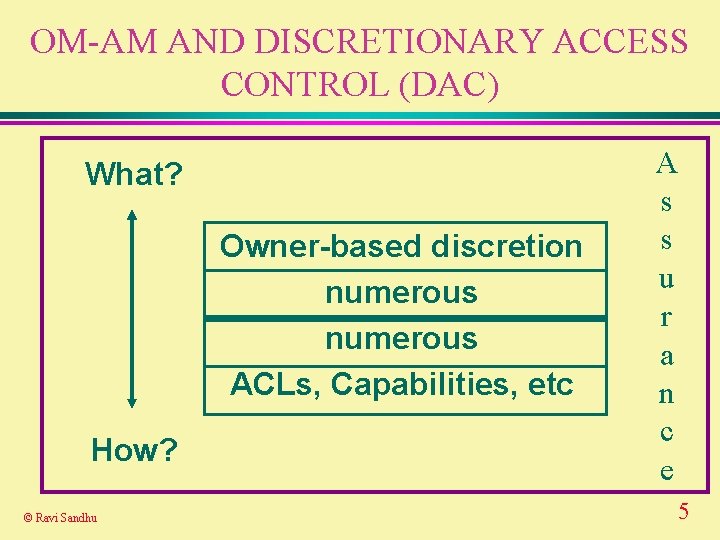
OM-AM AND DISCRETIONARY ACCESS CONTROL (DAC) What? Owner-based discretion numerous ACLs, Capabilities, etc How? © Ravi Sandhu A s s u r a n c e 5

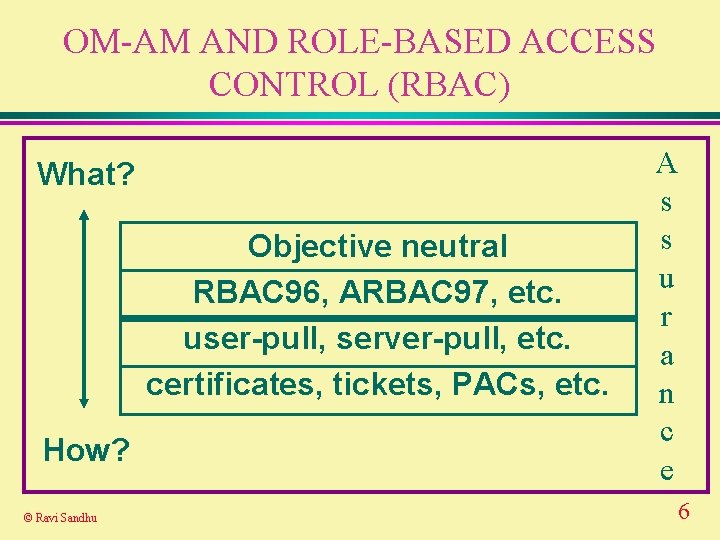
OM-AM AND ROLE-BASED ACCESS CONTROL (RBAC) What? Objective neutral RBAC 96, ARBAC 97, etc. user-pull, server-pull, etc. certificates, tickets, PACs, etc. How? © Ravi Sandhu A s s u r a n c e 6

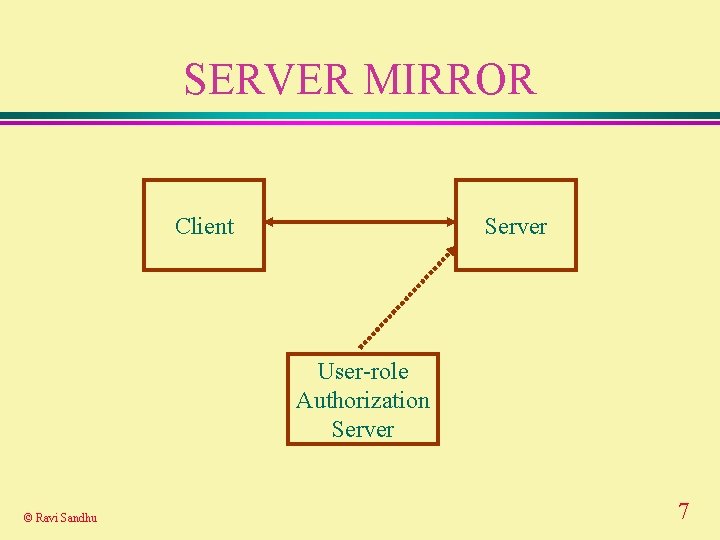
SERVER MIRROR Client Server User-role Authorization Server © Ravi Sandhu 7

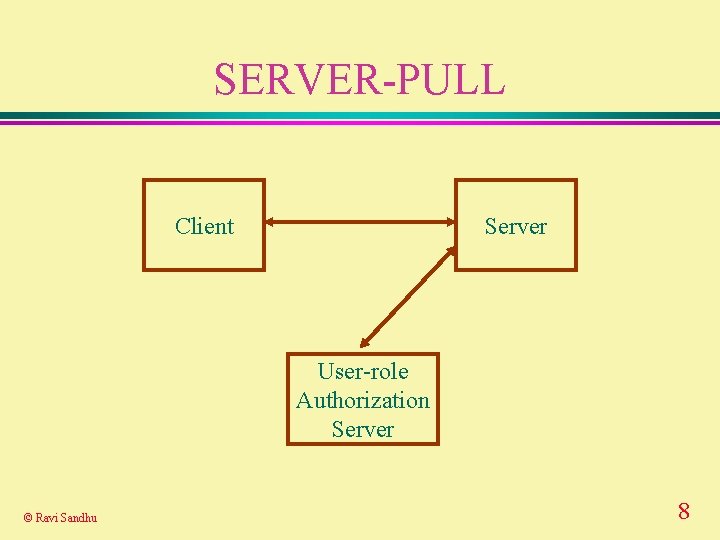
SERVER-PULL Client Server User-role Authorization Server © Ravi Sandhu 8

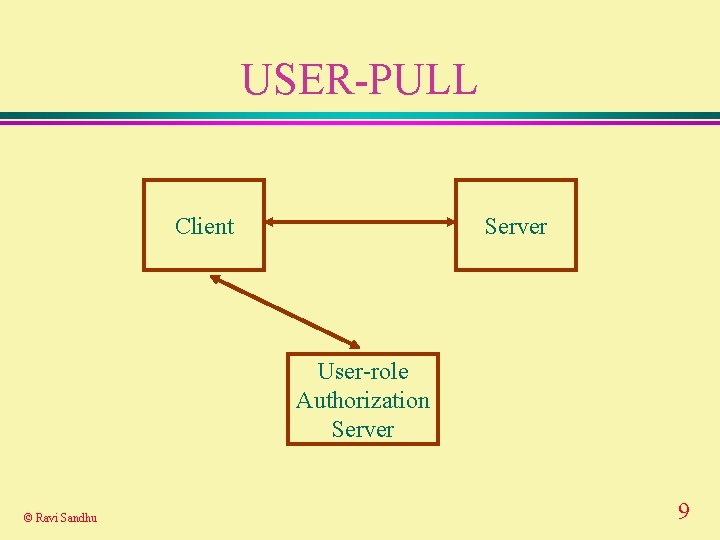
USER-PULL Client Server User-role Authorization Server © Ravi Sandhu 9

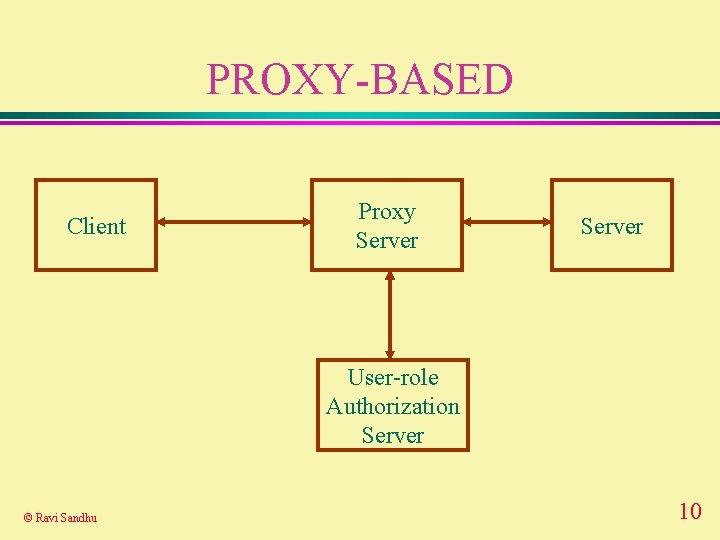
PROXY-BASED Client Proxy Server User-role Authorization Server © Ravi Sandhu 10

THE OM-AM WAY What? Objectives Model Architecture Mechanism How? © Ravi Sandhu A s s u r a n c e 11

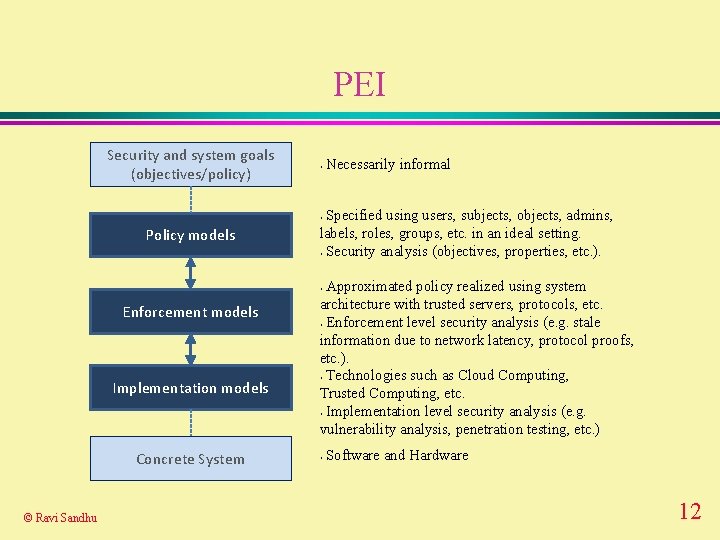
PEI Security and system goals (objectives/policy) • Necessarily informal Specified using users, subjects, objects, admins, labels, roles, groups, etc. in an ideal setting. • Security analysis (objectives, properties, etc. ). • Policy models Approximated policy realized using system architecture with trusted servers, protocols, etc. • Enforcement level security analysis (e. g. stale information due to network latency, protocol proofs, etc. ). • Technologies such as Cloud Computing, Trusted Computing, etc. • Implementation level security analysis (e. g. vulnerability analysis, penetration testing, etc. ) • Enforcement models Implementation models Concrete System © Ravi Sandhu • Software and Hardware 12
 Dr ravi sandhu
Dr ravi sandhu Of mice and men--study questions answers chapter 3
Of mice and men--study questions answers chapter 3 Loneliness similes
Loneliness similes Of mice and men chapter questions
Of mice and men chapter questions Winkle sandhu
Winkle sandhu Ravi and minu architects
Ravi and minu architects Viabilidad de un proyecto educativo ejemplo
Viabilidad de un proyecto educativo ejemplo Institucional ss.cc.
Institucional ss.cc. Dimension convivencial
Dimension convivencial Qualificatori pei
Qualificatori pei Esempio verifica pei
Esempio verifica pei Pei tong primary school teachers
Pei tong primary school teachers Im pei pronunciation
Im pei pronunciation