1 TOPIC CLARKWILSON MODEL Ravi Sandhu 2 CLARKWILSON







- Slides: 9

1 TOPIC CLARK-WILSON MODEL Ravi Sandhu

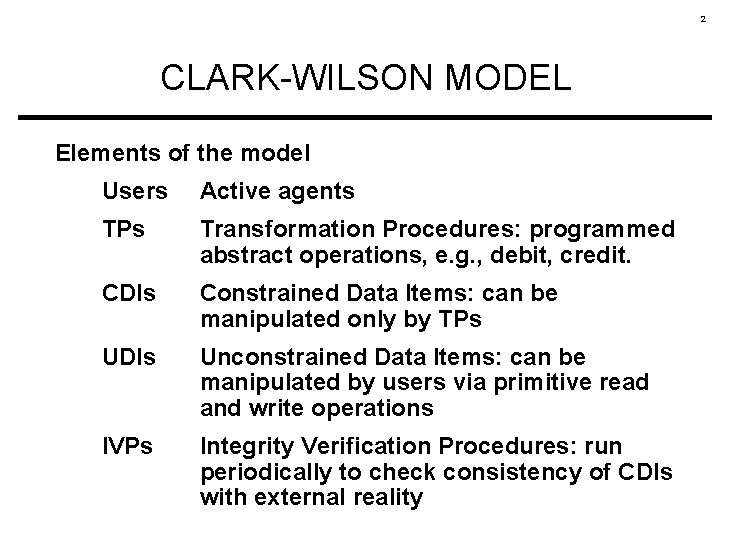
2 CLARK-WILSON MODEL Elements of the model Users Active agents TPs Transformation Procedures: programmed abstract operations, e. g. , debit, credit. CDIs Constrained Data Items: can be manipulated only by TPs UDIs Unconstrained Data Items: can be manipulated by users via primitive read and write operations IVPs Integrity Verification Procedures: run periodically to check consistency of CDIs with external reality

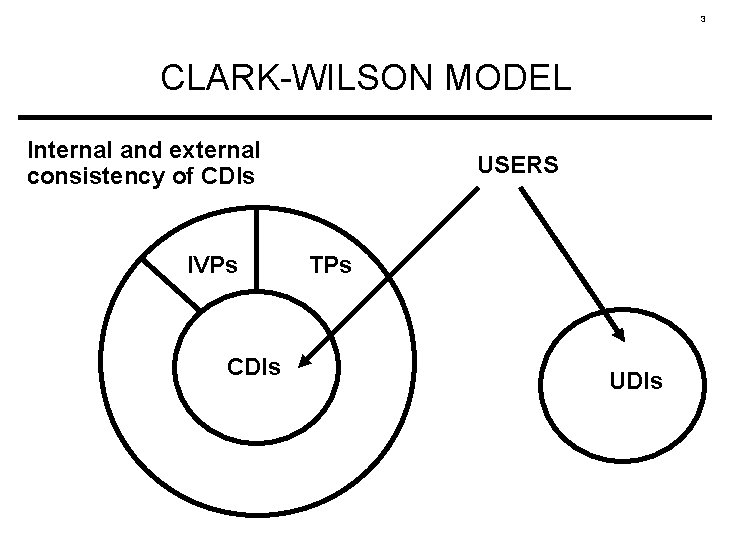
3 CLARK-WILSON MODEL Internal and external consistency of CDIs IVPs CDIs USERS TPs UDIs

4 CLARK-WILSON RULES C 1 C 2 C 3 C 4 C 5 IVPs validate CDI state TPs preserve valid state Suitable (static) separation of duties TPs write to log TPs validate UDIs E 1 E 2 E 3 E 4 CDIs changed only by authorized TP Users authorized to TP and CDI Users are authenticated Authorizations changed only by security officer

5 CERTIFICATION RULES C 1 IVPs are certified to be correct, i. e. , they ensure that all CDIs are in a valid state C 2 All TPs are certified to be correct, i. e. , they preserve the validity and correctness of CDIs. Each TP is certified to execute on particular sets of CDIs. C 3 The relations in E 2 are certified to meet separation of duties requirements C 4 All TPs must be certified to write to an append only CDI (the log) all information necessary to permit reconstruction of the operation C 5 Every TP that takes a UDI as input must be certified to produce a valid CDI or no CDI for all possible values of the UDI

6 ENFORCEMENT RULES E 1 The system maintains (and enforces) a list of all CDIs for which each TP is certified. Each TP is only allowed to operate on CDIs for which it is certified E 2 The system maintains (and enforces) a list of relations of the form: (User. ID, TPi, (CDIa, CDIb, CDIc, . . )) relating a user, a TP, and the data objects that TP may reference on behalf of that user. E 3 All users are authenticated by the system E 4 Only the agent permitted to certify entities may change the lists in E 1 and E 2. An agent that can certify a TP cannot have execute rights for that TP.

7 CLARK-WILSON ASSESSMENT • Too static • Too centralized: security-officer is God and nobody else can change any authorization • Has had a beneficial effect in convincing the mainstream security community that there is more to integrity than Biba

8 RELATIONSHIP OF ACCESS CONTROL MODELS TO CLARK-WILSON • Enforcement Rules Easily expressed • Certification Rules Outside the scope of access control

9 REFERENCES • Clark, D. D. and Wilson, D. R. "A Comparison of Commercial and Military Computer Security Policies. " Proc. IEEE Symposium on Security and Privacy, Oakland, CA, 1987, pages 184 -194. The original Clark-Wilson paper. Subsequently Clark and Wilson have stated that the Commercial-Military dichotomy in the title was a mistake. The real issue is integrity versus confidentiality. • Lee, T. M. P. "Using Mandatory Integrity to Enforce "Commercial" Security. " Proc. IEEE Symposium on Security and Privacy, Oakland, CA, 1988, pages 140 -146. Schockley, W. R. "Implementing the Clark/Wilson Integrity Policy Using Current Technology. " Proc. 11 th NBS-NCSC National Computer Security Conference, 29 -37 (1988). Two independent attempts to implement Clark-Wilson using a Biba lattice. Due to Biba-BLP equivalence the same constructions can be done in a BLP lattice. • Sandhu, R. S. "Transaction Control Expressions for Separation of Duties. " Proc. Aerospace Computer Security Applications Conference, 282 -286 (1988). Going beyond Clark-Wilson to do dynamic separation of duties.