1 TOPIC THE CHINESE WALL LATTICE Ravi Sandhu





- Slides: 19

1 TOPIC THE CHINESE WALL LATTICE Ravi Sandhu

2 CHINESE WALL POLICY • Example of a commercial security policy for confidentiality • Mixture of free choice (discretionary) and mandatory controls • Requires some kind of dynamic labelling • Introduced by Brewer-Nash in Oakland '89

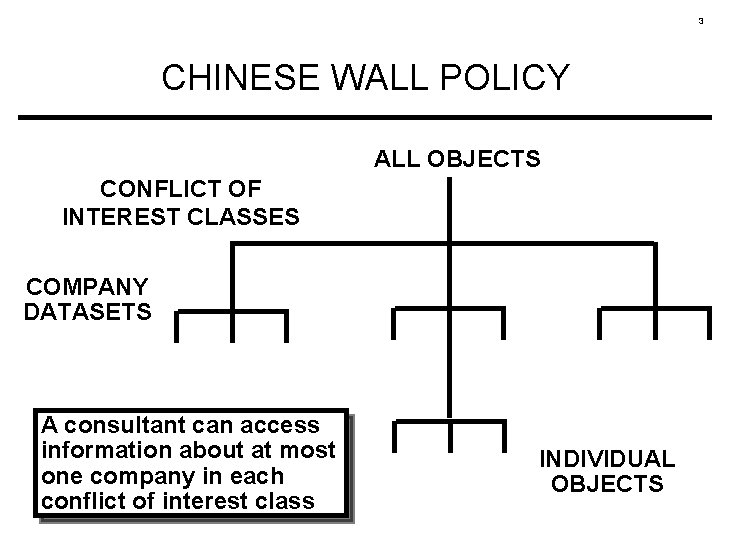
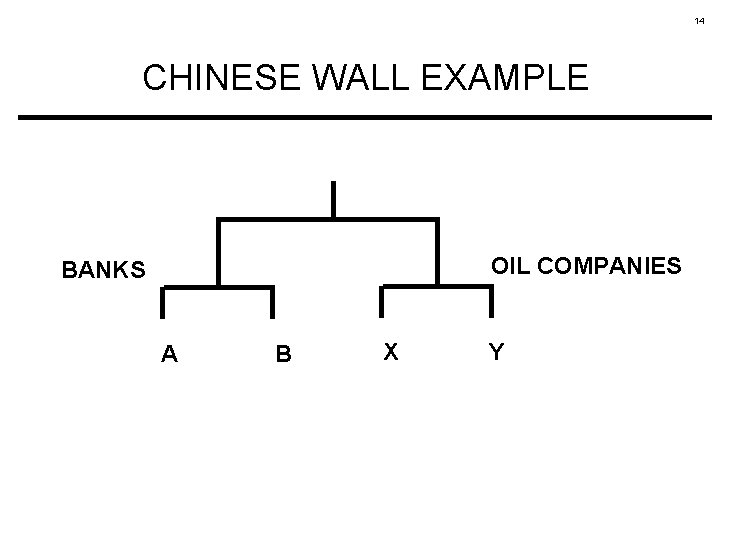
3 CHINESE WALL POLICY ALL OBJECTS CONFLICT OF INTEREST CLASSES COMPANY DATASETS A consultant can access information about at most one company in each conflict of interest class INDIVIDUAL OBJECTS

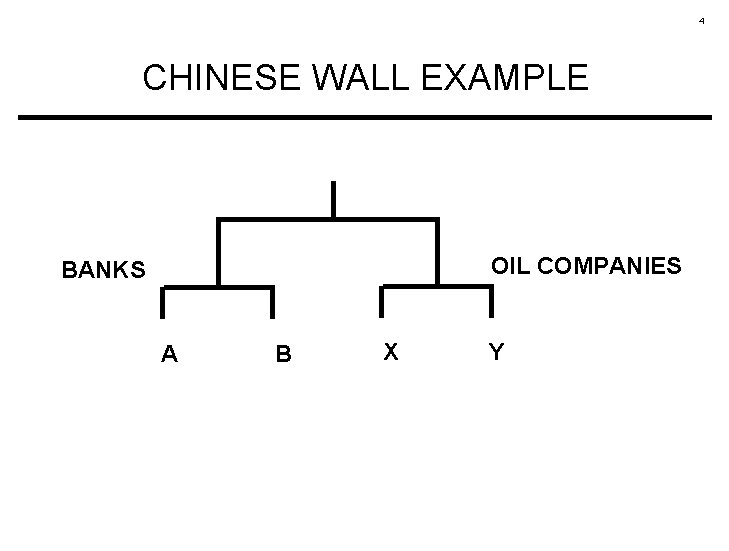
4 CHINESE WALL EXAMPLE OIL COMPANIES BANKS A B X Y

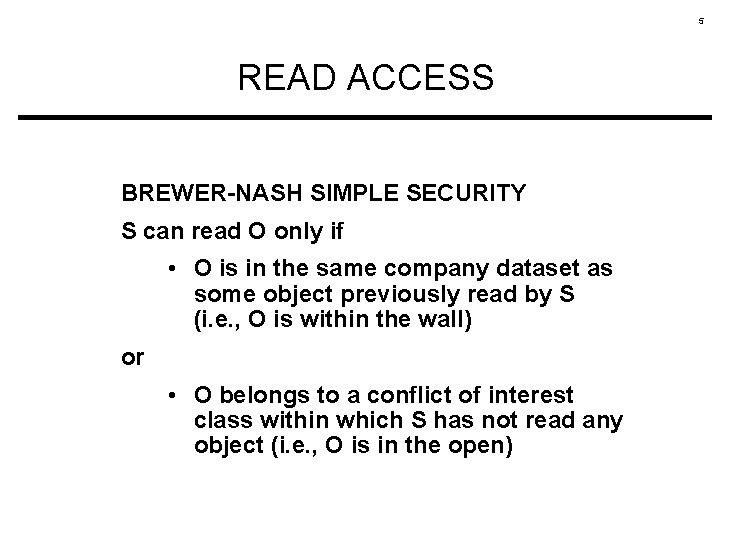
5 READ ACCESS BREWER-NASH SIMPLE SECURITY S can read O only if • O is in the same company dataset as some object previously read by S (i. e. , O is within the wall) or • O belongs to a conflict of interest class within which S has not read any object (i. e. , O is in the open)

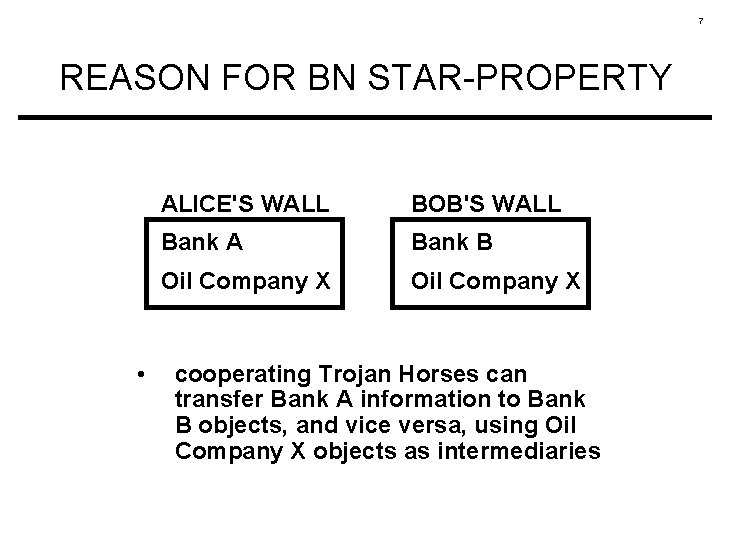
6 WRITE ACCESS BREWER-NASH STAR-PROPERTY S can write O only if • S can read O by the simple security rule and • no object can be read which is in a different company dataset to the one for which write access is requested

7 REASON FOR BN STAR-PROPERTY • ALICE'S WALL BOB'S WALL Bank A Bank B Oil Company X cooperating Trojan Horses can transfer Bank A information to Bank B objects, and vice versa, using Oil Company X objects as intermediaries

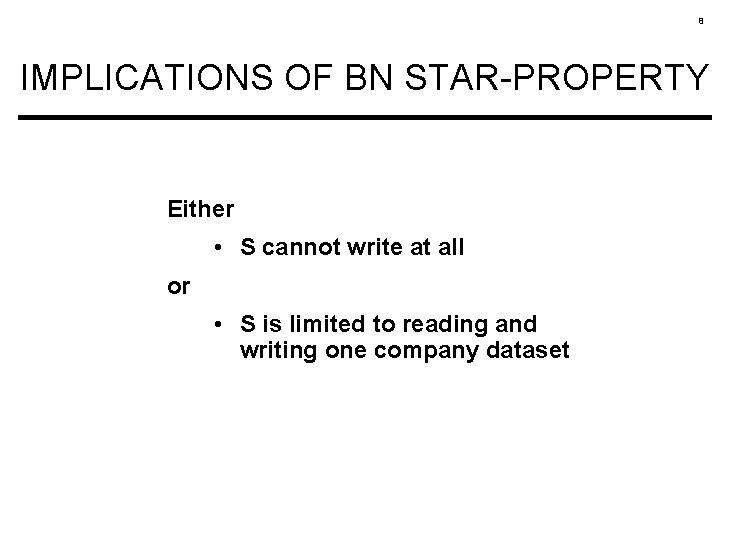
8 IMPLICATIONS OF BN STAR-PROPERTY Either • S cannot write at all or • S is limited to reading and writing one company dataset

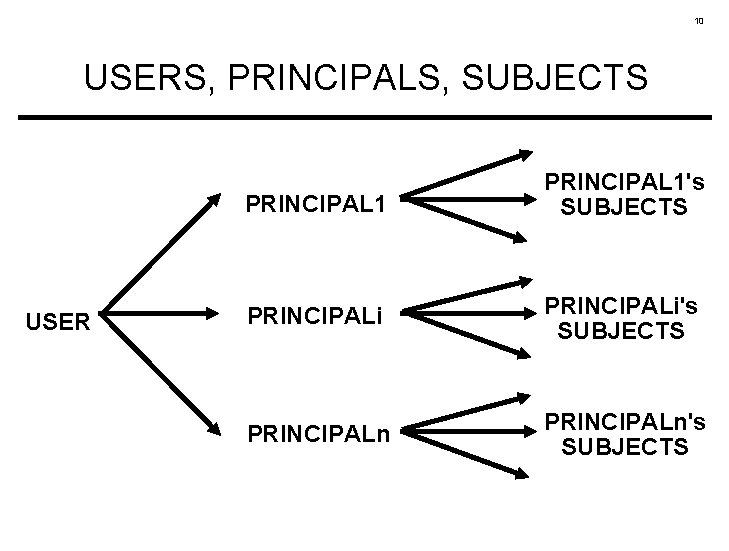
9 WHY THIS IMPASSE? Failure to clearly distinguish user labels from subject labels.

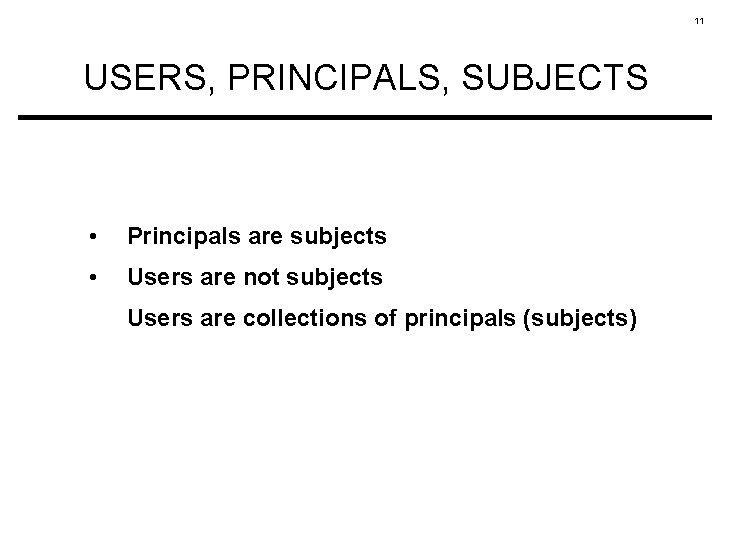
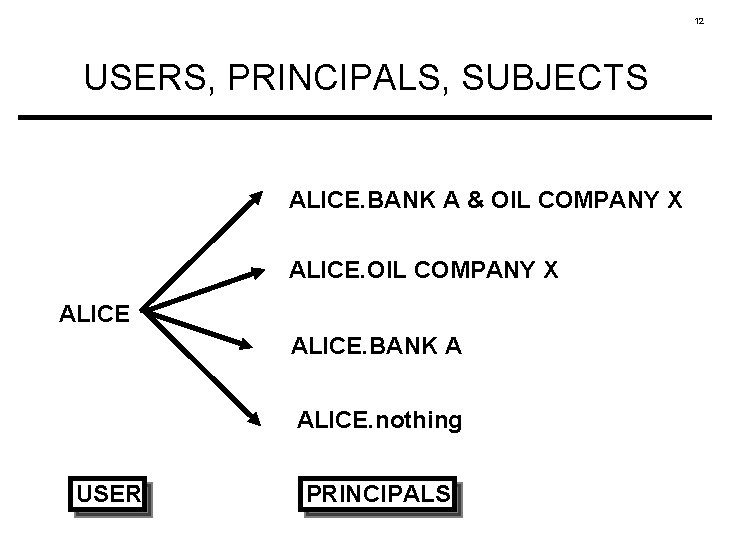
10 USERS, PRINCIPALS, SUBJECTS USER PRINCIPAL 1's SUBJECTS PRINCIPALi's SUBJECTS PRINCIPALn's SUBJECTS

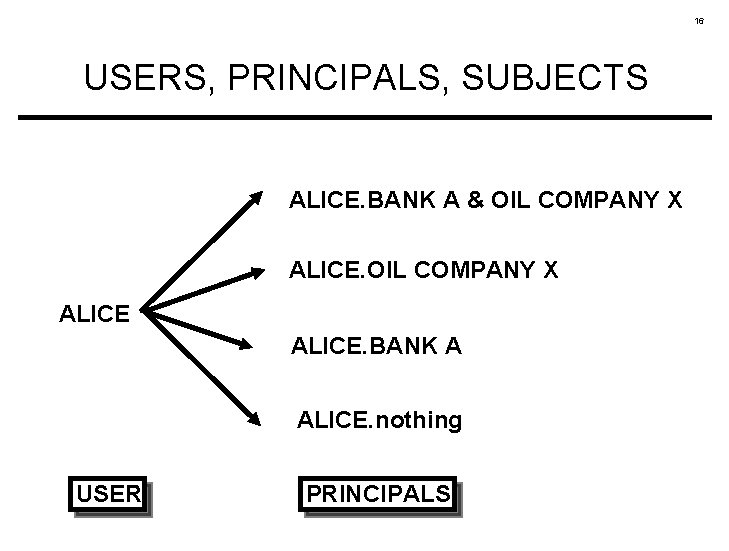
11 USERS, PRINCIPALS, SUBJECTS • Principals are subjects • Users are not subjects Users are collections of principals (subjects)

12 USERS, PRINCIPALS, SUBJECTS ALICE. BANK A & OIL COMPANY X ALICE. BANK A ALICE. nothing USER PRINCIPALS

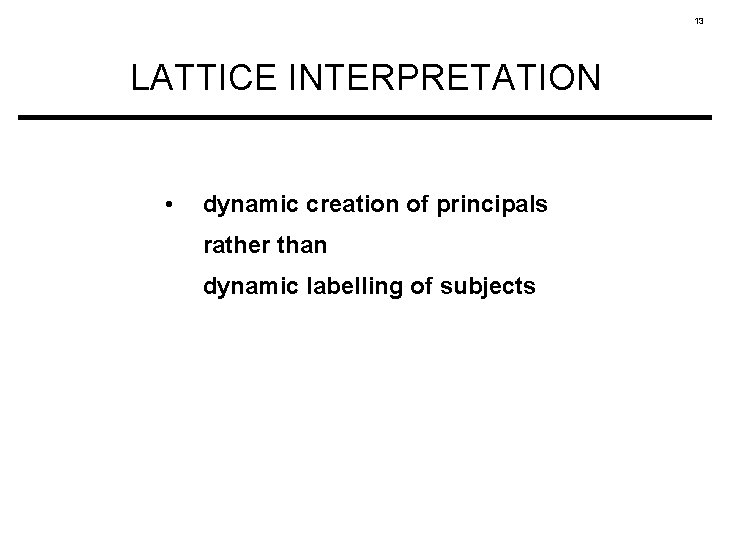
13 LATTICE INTERPRETATION • dynamic creation of principals rather than dynamic labelling of subjects

14 CHINESE WALL EXAMPLE OIL COMPANIES BANKS A B X Y

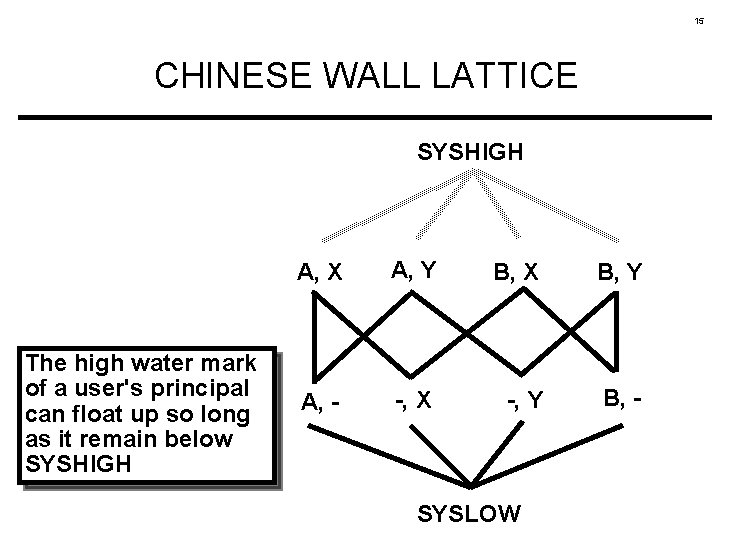
15 CHINESE WALL LATTICE SYSHIGH The high water mark of a user's principal can float up so long as it remain below SYSHIGH A, X A, Y B, X B, Y A, - -, X -, Y B, - SYSLOW

16 USERS, PRINCIPALS, SUBJECTS ALICE. BANK A & OIL COMPANY X ALICE. BANK A ALICE. nothing USER PRINCIPALS

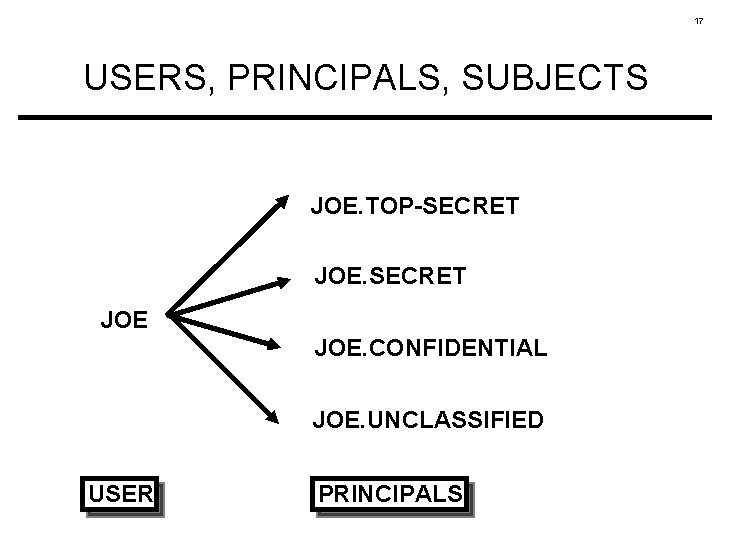
17 USERS, PRINCIPALS, SUBJECTS JOE. TOP-SECRET JOE. CONFIDENTIAL JOE. UNCLASSIFIED USER PRINCIPALS

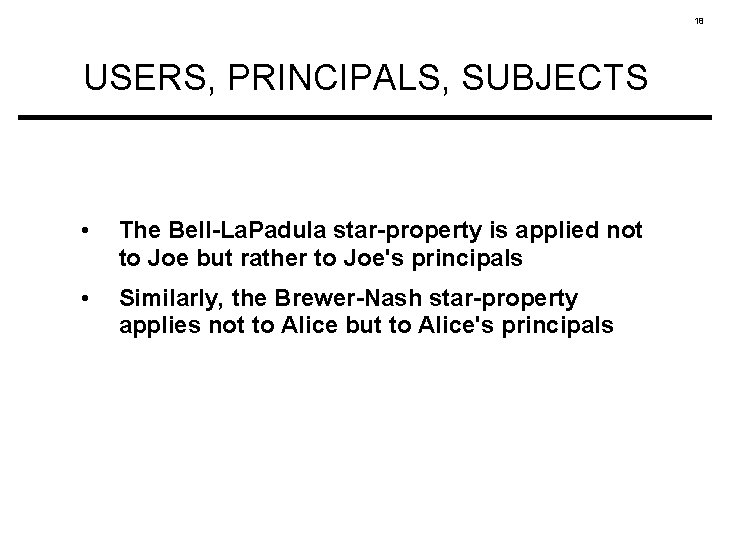
18 USERS, PRINCIPALS, SUBJECTS • The Bell-La. Padula star-property is applied not to Joe but rather to Joe's principals • Similarly, the Brewer-Nash star-property applies not to Alice but to Alice's principals

19 CONCLUSION • The Chinese Wall policy is just another lattice-based information flow policy • To properly understand enforce Information Security policies we must distinguish between • policy applied to users, and • policy applied to principals and subjects
 Dr ravi sandhu
Dr ravi sandhu Winkle sandhu
Winkle sandhu Lattice lattice
Lattice lattice Anglo chinese school
Anglo chinese school Brewer-nash model (chinese wall)
Brewer-nash model (chinese wall) Chinese wall model
Chinese wall model Chinese wall model
Chinese wall model Chinese wall model
Chinese wall model Chinese wall model
Chinese wall model Chinese wall model
Chinese wall model Chinese wall model
Chinese wall model Wall to wall chris brown
Wall to wall chris brown One and a half brick wall
One and a half brick wall The wall of ovary develops into wall of fruit called
The wall of ovary develops into wall of fruit called Members used to carry wall loads over wall openings
Members used to carry wall loads over wall openings Sound walls vs word walls
Sound walls vs word walls Narrow topic examples
Narrow topic examples Paragraph writing strategy
Paragraph writing strategy Ravi patki
Ravi patki Ravi rajapakse
Ravi rajapakse