WHAT IS A COMPUTER NETWORK A computer network




























- Slides: 55


WHAT IS A COMPUTER NETWORK? A computer network is a group of computers that share information across wireless or wired technology. Computer networks used to only be available for corporations but they are affordable for small businesses and individuals. A network allows sharing of resources and data among interconnected devices. The different kinds of networks are LAN, WLAN

A server is a a software program, or the computer on which a program runs, it provides a specific kind of service to client software running on the same computer or other computers on a network. TYPES OF SERVERS File servers- Allows people to save and load files Application Servers- It deals with the distribution of application software to each computer. Printer servers-It ensures the printing of devices on the network in a queue. Proxy Servers- It is used as a buffer between the WANs and LANs.

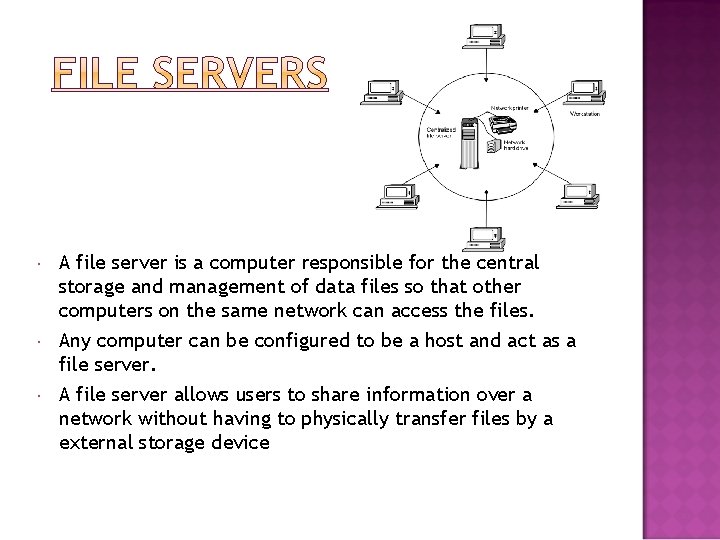
A file server is a computer responsible for the central storage and management of data files so that other computers on the same network can access the files. Any computer can be configured to be a host and act as a file server. A file server allows users to share information over a network without having to physically transfer files by a external storage device

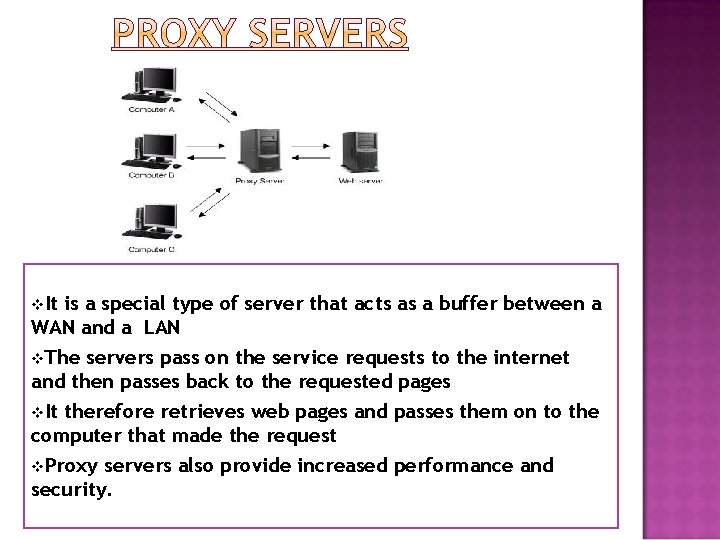
v. It is a special type of server that acts as a buffer between a WAN and a LAN v. The servers pass on the service requests to the internet and then passes back to the requested pages v. It therefore retrieves web pages and passes them on to the computer that made the request v. Proxy servers also provide increased performance and security.

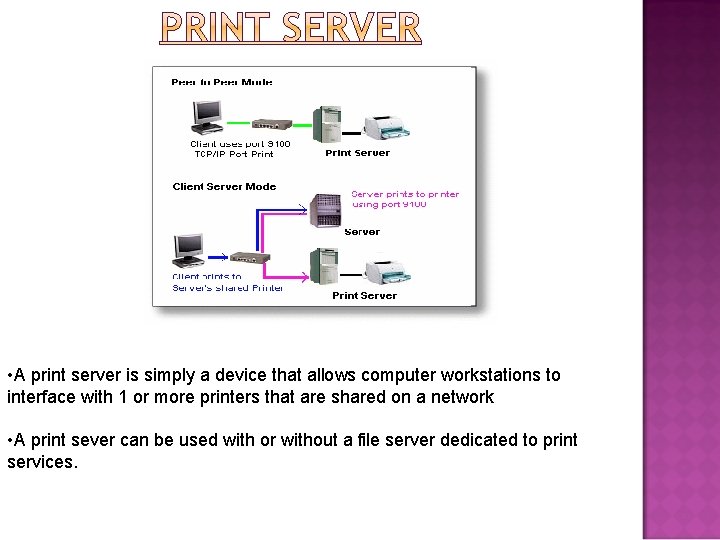
• A print server is simply a device that allows computer workstations to interface with 1 or more printers that are shared on a network • A print sever can be used with or without a file server dedicated to print services.

Devices and software can be shared. All users can access and update files from anywhere on the network. Data and software can be stored centrally thus preventing loss of data or software. Network security can ensure that only authorised users with an identity user name and password can access data.

DISADVANTAGES OF NETWORKING Networks can be expensive to install and operate. Server breakdowns cause the whole network to stop working. Security must be of the highest level possible to ensure that unauthorised access and infection by computer viruses are prevented.

DIFFERENT TYPES OF NETWORK

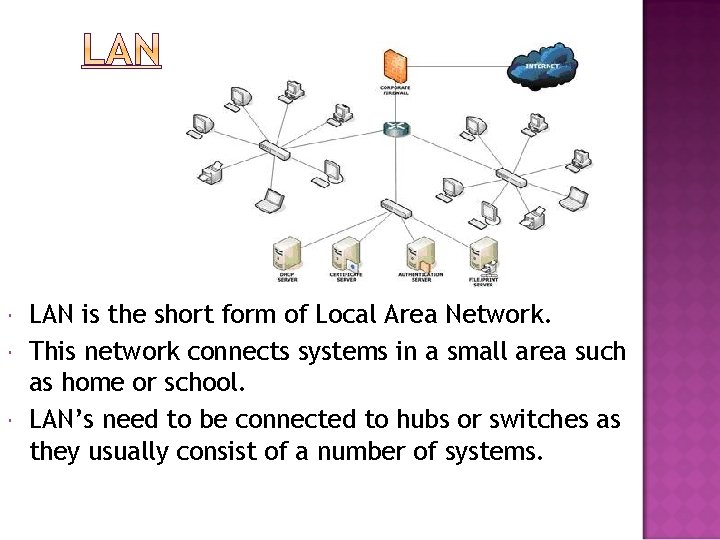
LAN is the short form of Local Area Network. This network connects systems in a small area such as home or school. LAN’s need to be connected to hubs or switches as they usually consist of a number of systems.

The resources can be shared. Facilitates communication between users A network administrator is present to control and monitor all the aspects of the network. Viruses can spread easily throughout the network. The development of printer queues can be frustrating. Slower access to external networks. If the main server breaks down the whole system comes to a standstill. Increased security risk as compared to stand alone systems.

RING NETWORK BUS NETWORK STAR NETWORK TREE NETWORK

N A L W

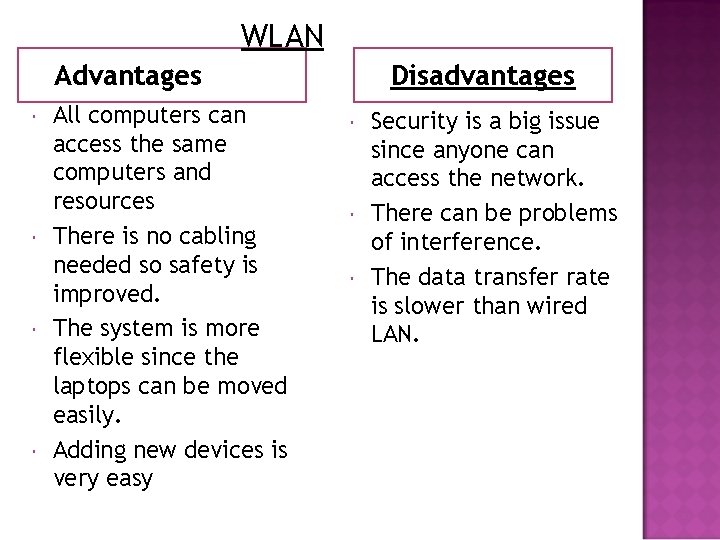
WLAN WLAN is the short form of Wireless Local Area Network They are similar to LAN but do not use wires. Access points are connected into the wired network at fixed locations. The AP uses spread spectrum technology which is a radio frequency with a range of about 30 to 50 mtrs.

WLAN Advantages All computers can access the same computers and resources There is no cabling needed so safety is improved. The system is more flexible since the laptops can be moved easily. Adding new devices is very easy Disadvantages Security is a big issue since anyone can access the network. There can be problems of interference. The data transfer rate is slower than wired LAN.

N A W

WAN is the short form of Wide Area Network Connects different LAN’s thorough a router or a modem. It requires additional hardwares such as routers, modems and proxy servers to a LAN. Used for connecting different locations so that users in a location can communicate with users of other locations.

W i F i

A wireless LAN (WLAN) is a LAN that uses radio signals (Wi. Fi) to connect computers instead of cables. Wi- Fi hotspots are places where you can access wi -fi. They exist in public places. Its is possible to logon unless they are password protected. The practice of driving around in a car looking for unsecured Wi. Fi spots is known as war driving. It poses a security threat.

h t o o t e u l B

Bluetooth is an example of wireless personal area network. It is designed for very shortrange connections. Bluetooth devices contain small, lowpower radio transmitters and receivers. It provides links between mobile phones, computers and handheld devices. The range is about 10 metres.

k r o w t e N ices v e D • NIC • Modems • Network Hubs • Switches • Bridges • Routers

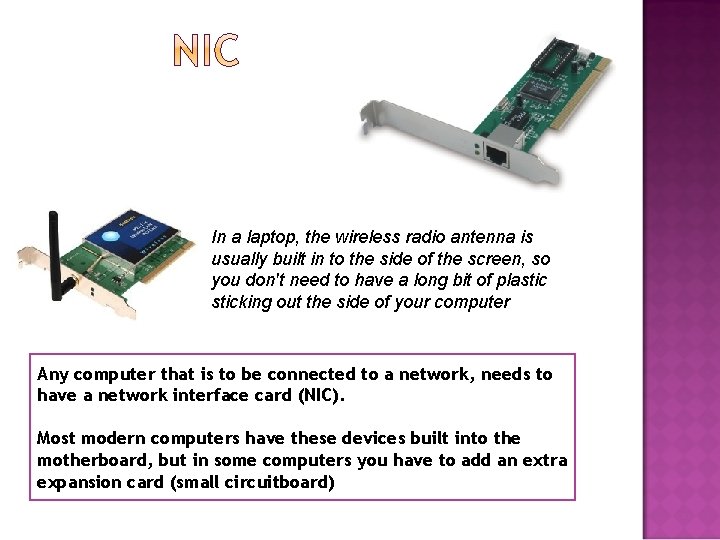
In a laptop, the wireless radio antenna is usually built in to the side of the screen, so you don't need to have a long bit of plasticking out the side of your computer Any computer that is to be connected to a network, needs to have a network interface card (NIC). Most modern computers have these devices built into the motherboard, but in some computers you have to add an extra expansion card (small circuitboard)

To connect together different devices to make up a network, you need cables. Cables are still used in most networks, rather than using only wireless, because they can carry much more data per second, and are more secure (less open to hacking)

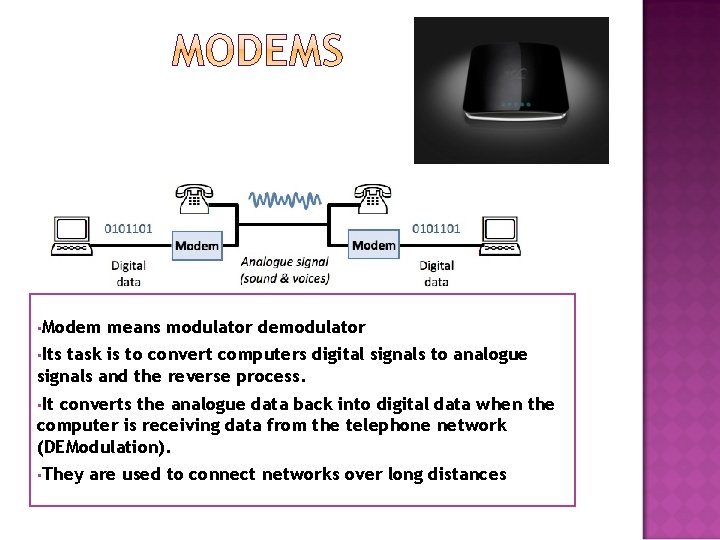
• Modem means modulator demodulator • Its task is to convert computers digital signals to analogue signals and the reverse process. • It converts the analogue data back into digital data when the computer is receiving data from the telephone network (DEModulation). • They are used to connect networks over long distances

Asymmetric Digital Subscriber Line ADSL MODEM DIAL UP MODEM They operate at a speed of 60 kbps(kilobits per second). It is the slowest type of connection. The telephone line is tied up while a dial up modem is in operation. They are the fastest download atleast 11, 000 kbps. The telephone linea are not tied up Due to good speed VOIP can be used.

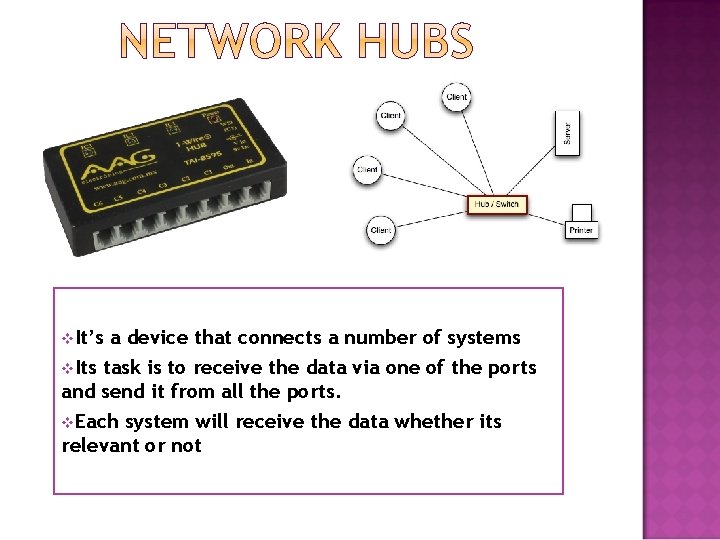
k r o w t e N s b u H

v. It’s a device that connects a number of systems v. Its task is to receive the data via one of the ports and send it from all the ports. v. Each system will receive the data whether its relevant or not

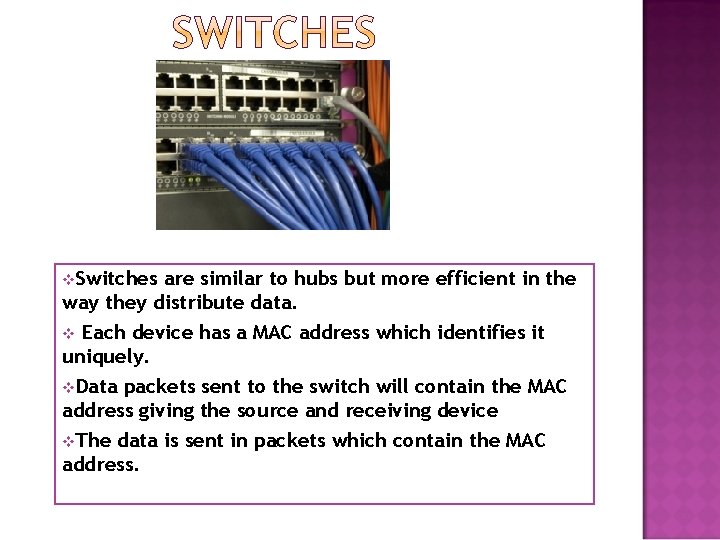
i Sw s e h c t

v. Switches are similar to hubs but more efficient in the way they distribute data. Each device has a MAC address which identifies it uniquely. v. Data packets sent to the switch will contain the MAC address giving the source and receiving device v. The data is sent in packets which contain the MAC address. v

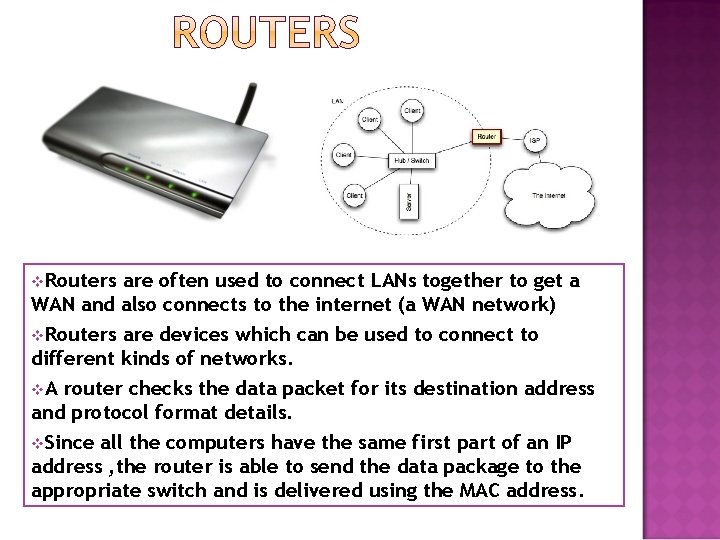
o R s r e t u

v. Routers are often used to connect LANs together to get a WAN and also connects to the internet (a WAN network) v. Routers are devices which can be used to connect to different kinds of networks. v. A router checks the data packet for its destination address and protocol format details. v. Since all the computers have the same first part of an IP address , the router is able to send the data package to the appropriate switch and is delivered using the MAC address.

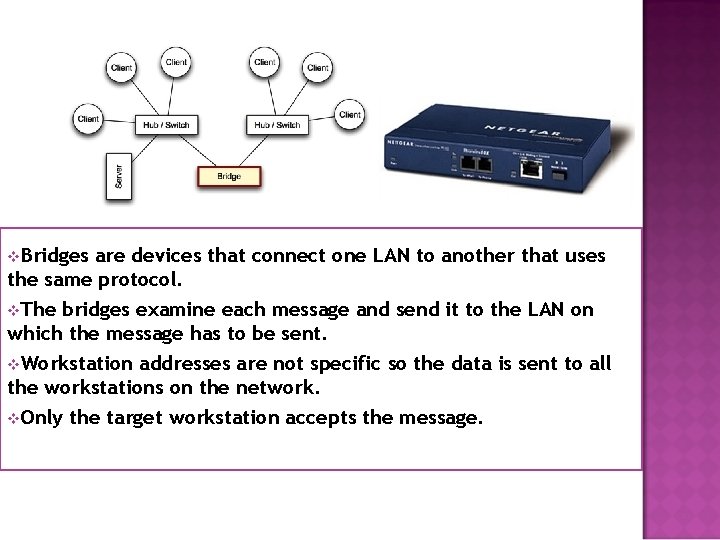
I R B S E G D

v. Bridges are devices that connect one LAN to another that uses the same protocol. v. The bridges examine each message and send it to the LAN on which the message has to be sent. v. Workstation addresses are not specific so the data is sent to all the workstations on the network. v. Only the target workstation accepts the message.

IN T E N R E T

v. It is a wide collection of networks which allows the user to send, receive emails, chat or browse the world wide web. v. WEBSITE it is a collection of web pages linked together. v. URL It stands for Uniform Resource Locator. It is the address of a website. Protocol: //site address/path/filename Ex: - http: //www. google. com v. HYPERLINK it allows us to navigate to another page.

TYPE OF ACCESS DESCRIPTION DIAL UP (DIAL UP MODEM This is the slowest connection. User connects to the internet via a telephone by dialing the no. given by the ISP. The phone line is tied up in this access. Cable internet access Local cable T. V. operators give the user access to the internet through their network using a cable network modem. Internet access via DSL(Broadband modem) the fastest download speed is obtained by DSL.

R T IN T E AN

v. It is a computer network based on the internet technology that is designed to meet the internal needs of for sharing the information within a single organization. v Reasons for using the intranet. 1. Safer since there is less chance of external hacking. 2. It prevents employees from accessing unwanted websites. 3. Companies can ensure that the informtion available to the employees are specific to their needs. 4. It is easier to send out sensitive messages that will remain only within the company.

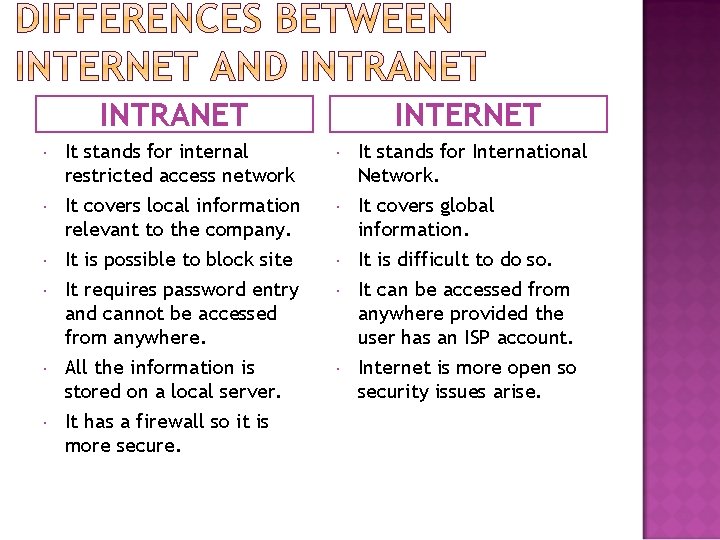
INTRANET INTERNET It stands for internal restricted access network It stands for International Network. It covers local information relevant to the company. It is possible to block site It requires password entry and cannot be accessed from anywhere. All the information is stored on a local server. It has a firewall so it is more secure. It covers global information. It is difficult to do so. It can be accessed from anywhere provided the user has an ISP account. Internet is more open so security issues arise.

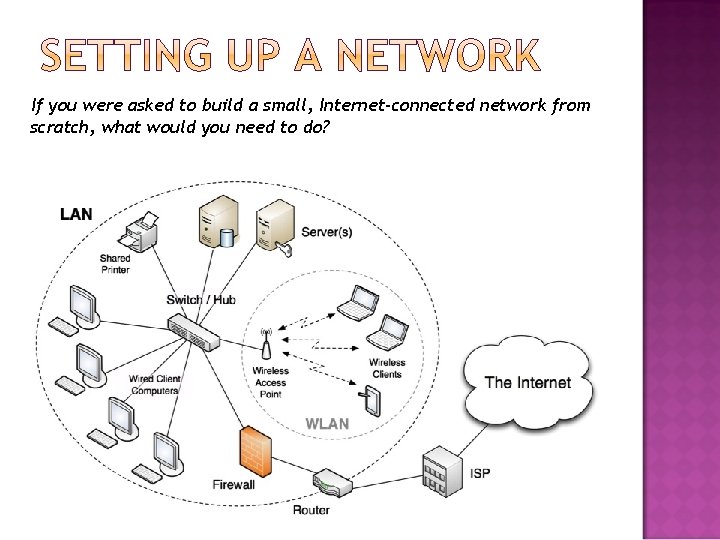
If you were asked to build a small, Internet-connected network from scratch, what would you need to do?

You would need to buy some hardware: • One or more switches / hubs - to link devices together • Network cables to connect devices to the switch, etc. • A separate wireless access point (or this could be part of the switch) - to allow wireless devices (e. g. laptops or smart-phones) to join the network • A router to connect your LAN to the Internet (WAN) • A firewall to protect your network from hackers • Possibly a bridge if you already have a section of network and you want your new network to connect to it • Server(s) to manage network functions such as network security, network file storage, shared resources (such as printers) You would need to organize some other things: • Set up an account with an Internet Service Provider (ISP) • Get an Internet connection installed from the ISP to your location • Configure various bits of hardware and software so that everything worked with the network

v. The main issues pertaining to security are: v. User ID v. Password v. Encryption v. Authentication Technique

A network allows a person who does to have physical access to your computer (they are not sitting in front of it) to gain access all the same. If your computer is connected to a network, other people can connect to your computer. A person who gains unauthorised access to a computer system is often called a hacker Preventing Unauthorised Access v. Physical Security The first thing to make sure of is that no unauthorised people can physically access (sit down in front of) any of the computers on your network v. Use a Username and Have a Good Password The most common way to protect your computer’s data is to setup user accounts with usernames and passwords. Anyone not having a username, or not knowing the correct password will be denied access. For this to be effective passwords must be chosen that are not easy to guess. Passwords should be a random combination of lowercase letters, uppercase letters and numbers (and symbols if this is allowed) v. Always Install and Use a Firewall is a device, or a piece of software that is placed between your computer / LAN and the rest of the network / WAN

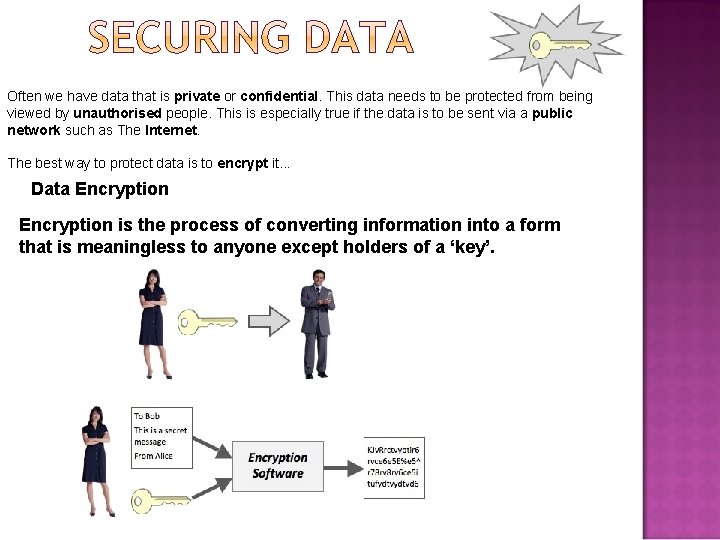
Often we have data that is private or confidential. This data needs to be protected from being viewed by unauthorised people. This is especially true if the data is to be sent via a public network such as The Internet. The best way to protect data is to encrypt it. . . Data Encryption is the process of converting information into a form that is meaningless to anyone except holders of a ‘key’.


There are many ways in which a person can prove who they are. This is called as authentication. Most commonly adopted techniques are: • Something you know- password etc. • Something belonging to you- bank card • Something unique to you- finger print, retina scan

The main methods of communication in a network are: • Fax • Email • VOIP • Video Conferencing

• It stands for facsimile. • Documents are electronically scanned and sent to the receiver’s end. • They are converted to a bitmap image. • It is transmitted as a series of electrical signals • The receiving fax machine converts the electronic image and prints it out on paper.

• It is an electronic method of sending data. ADVANTAGES • Speed is very good • Low costs since envelopes, stamps paper etc are not needed. • No need to leave home. DISADVANTAGES • Higher risk of virus attack • Email address has to be correct • Inability to send bulky object via emails.

• It is a method of communication between people at two separate locations. This is done in real time. HARDWARE USED: • Webcams • Monitors • TV screens • Microphones • Speakers. SOFTWARE USED • CODEC- It converts and compresses analogue data into digital data to send • Echo cancellation software- It synchronizes the communication

ADVANTAGES • Reduces cost of travelling • Savings due to cut on overnight stays. DISADVANTAGES • Time differences between countries become an issue. • There can be a time lag.

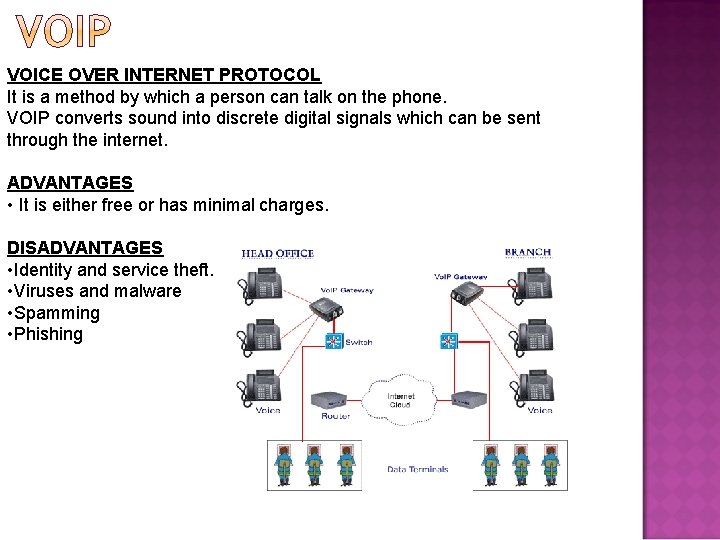
VOICE OVER INTERNET PROTOCOL It is a method by which a person can talk on the phone. VOIP converts sound into discrete digital signals which can be sent through the internet. ADVANTAGES • It is either free or has minimal charges. DISADVANTAGES • Identity and service theft. • Viruses and malware • Spamming • Phishing


Q 1. Name two network devices that could be used to connect a LAN to a WAN Q 2 Describe the differences between a WAN and a LAN Q 3 Tick three essential components of a computer to be used in a video conferencing system • Graph plotter • Trackerball • Microphone • Speakers • Optical mark reader • Web cam Q 4 Many schools use both an Intranet and the Internet. Give three differences between an Intranet and the Internet.