University of Florida Incident Tracking and Reporting Kathy



















- Slides: 25

University of Florida Incident Tracking and Reporting Kathy Bergsma kbergsma@ufl. edu

About UF n Land-grant institution n n Research, education, and extension Over 50, 000 students Over 50, 000 network nodes First dedicated IT security position in 1999. Now 4 FTE.

Your Institution n How many are from institutions with greater than 30, 000 students? Is your institution de-centralized? Does your institution… n n have incident response standards and procedures? track IT contacts? track incidents? deliver incident reports?

Contact Tracking n Contact database n n n Network managers Server managers Information Security Managers Information Security Administrators Much more

UF Incident Response Standard http: //www. it. ufl. edu/policies/security/uf-it-sec-incidentresponse-rewrite. html n An incident is “an event that impacts or has the potential to impact the confidentiality, availability, or integrity of UF IT resources. ” n Describes eight incident response steps from discovery to resolution n Establishes UF Incident Response Team and their responsibility n Defines Unit responsibility n Specific procedures for each incident type

Incident Identification Sources n n IDS Email abuse complaints Flow data Honeypots

Incident Tracking n Critical fields tracked n n n IP address Unit Incident type Incident severity Time to contain Time to resolve

Ticket Creation n Manual: Web form interface to Remedy on the backend. Some fields such as contacts are automatically populated Semi automated: Batch processing scripts for ircbots or IP lists Fully automated: Daedalus home-grown automated ticket creation.

Daedalus n Message processor using threat configs n Input n n IDS event Flow event Email notification Output n n Remedy ticket Email notification

Incident Resolution n n Daily reports to UF incident response team identifying open tickets Bi-weekly automated reminders about open tickets to ticket owners

Vulnerability Detection n n Continuous Nessus top-20 scans Results tracked in SQL No Remedy ticket because next scan will usually identify resolution Recidivism reports identify unresolved vulnerabilities.

Incident Reports n Cover letter includes n n n Request to update contact information List and description of graphs General campus trends Link to detailed ticket information Confidentiality statement Periodic survey of report value

Incident Reports n Each of the following graphs compares the unit to the 5 most active units: n n n Number of incidents adjusted for unit size Average number of days to contain incidents Number of critical vulnerabilities adjusted for unit size

Incident Reports n n Number of each incident type Comparison of current semester to same semester last year of: n n n Number of incidents Average days to contain Number of critical vulnerabilities








Executive Incident Summary n Table listing all units n n n Total Number of Incidents Containment Time Total Number of Vulnerabilities

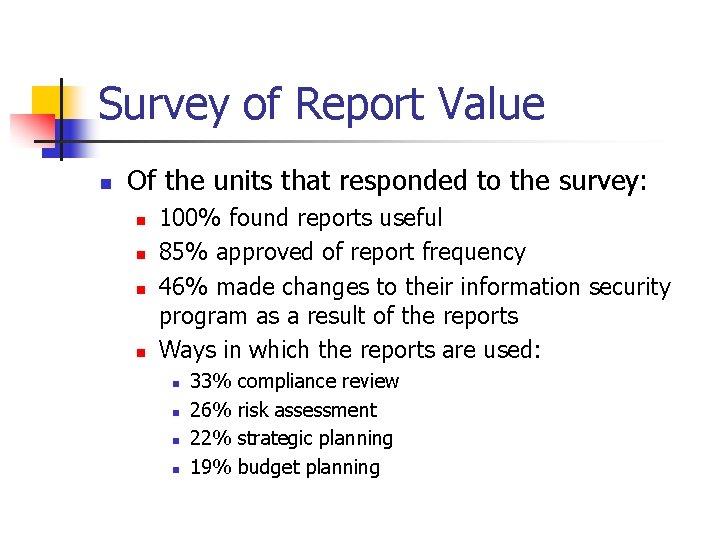
Survey of Report Value n Of the units that responded to the survey: n n 100% found reports useful 85% approved of report frequency 46% made changes to their information security program as a result of the reports Ways in which the reports are used: n n 33% 26% 22% 19% compliance review risk assessment strategic planning budget planning

Survey of Report Value n Cause of incident increase or decrease: n n n n 34% 21% 14% 10% awareness and training policy and procedures security infrastructure security staff other 100% were familiar with UF policy Degree of policy compliance n n n 57% very compliant 36% mostly compliant 7% somewhat compliant

Questions? Thank you, Kathy Bergsma kbergsma@ufl. edu
 Incident objectives that drive incident operations
Incident objectives that drive incident operations Wisconsin incident tracking system
Wisconsin incident tracking system Dru driscoll
Dru driscoll Sentinal event
Sentinal event 12vac35-105-160
12vac35-105-160 Riskman
Riskman Riskman meaning
Riskman meaning Origami risk login
Origami risk login Quantros incident reporting system
Quantros incident reporting system Patient safety incident policy
Patient safety incident policy Ahca airs login
Ahca airs login Scheda incident reporting
Scheda incident reporting Hse accident reporting flow chart
Hse accident reporting flow chart Hcsis provider directory
Hcsis provider directory Ics 400: advanced ics for complex incidents-aberdeen
Ics 400: advanced ics for complex incidents-aberdeen Quantros incident reporting system
Quantros incident reporting system Ahca adverse incident reporting
Ahca adverse incident reporting Florida state computer science
Florida state computer science University of florida rolling admissions
University of florida rolling admissions Board of governors state university system of florida
Board of governors state university system of florida Pcb 3703c ucf
Pcb 3703c ucf Usf grad admissions
Usf grad admissions Fau registrar office
Fau registrar office Florida occupational therapy association
Florida occupational therapy association Jay ritter university of florida
Jay ritter university of florida Biographical page of passport india
Biographical page of passport india

















































