Incident Reporting Systems for information security Summary Incident









- Slides: 14

Incident Reporting Systems for information security

Summary Incident reporting is • • • (probably) important (everybody else does it) seemingly not very widespread tough to do successfully not well researched easier with the right tools

Problem Why reporting? • Information security complexity rising • Number of events and incidents rising Why is it difficult? • Social and organizational issues prevent information sharing

Possible aid • • A starting point given by F. O. Sveen et al. Basis in safety practices Well established field of research System dynamics for modelling • Can we use this in information security?

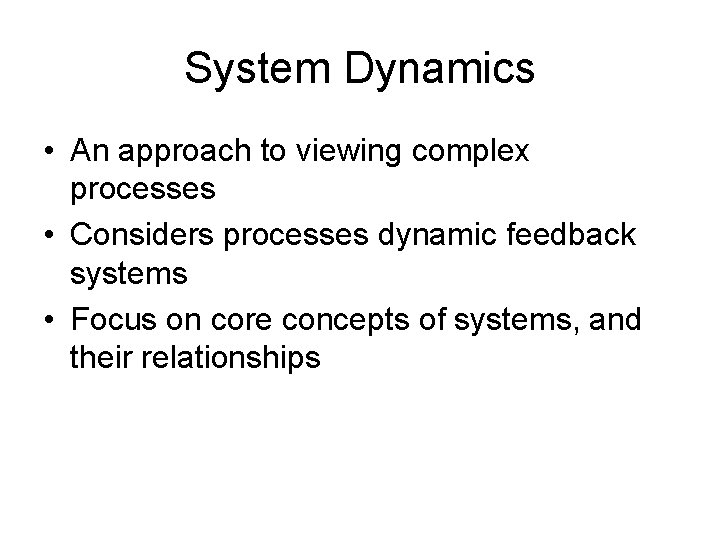
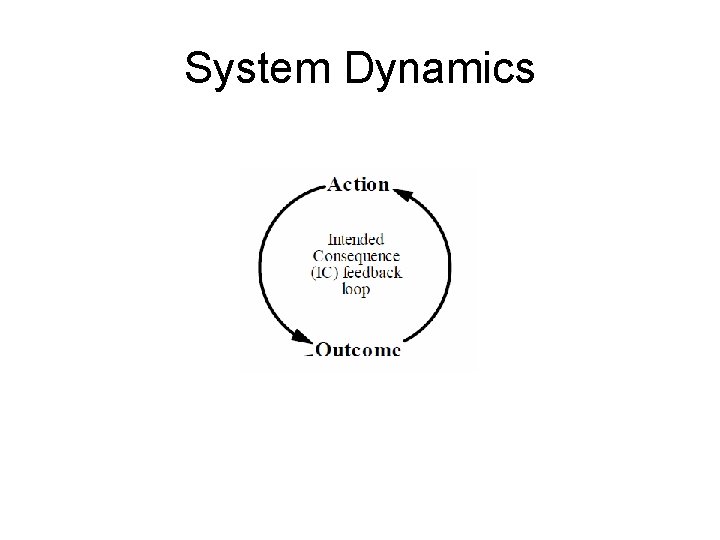
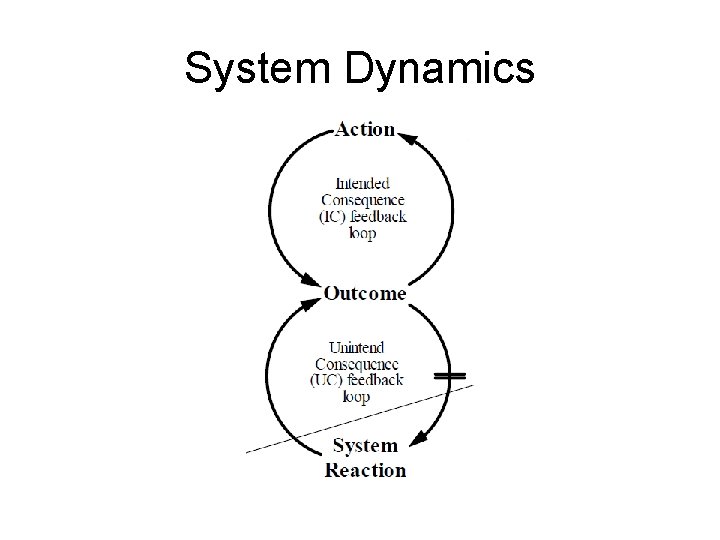
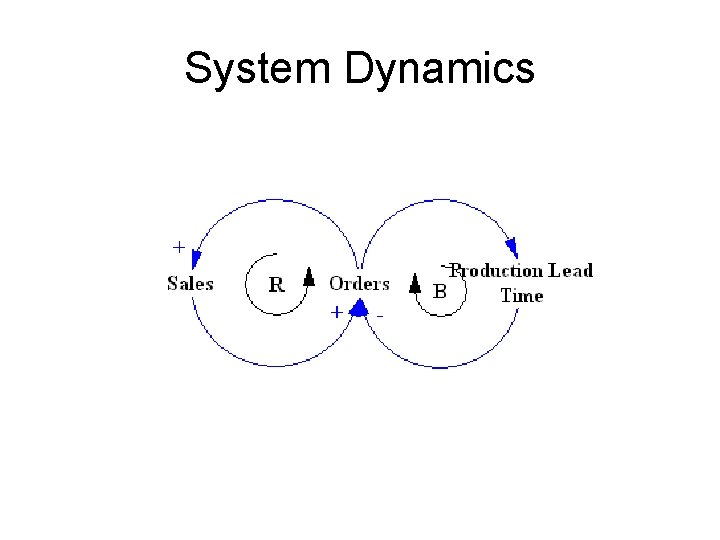
System Dynamics • An approach to viewing complex processes • Considers processes dynamic feedback systems • Focus on core concepts of systems, and their relationships

System Dynamics

System Dynamics

System Dynamics

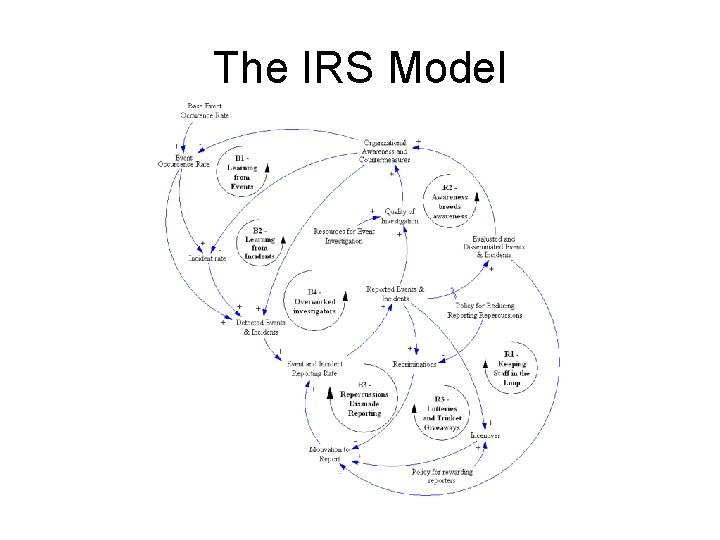
The IRS Model

The IRS Model • • • Events are reported Reports are investigated Lessons learned fed back to organization Awareness is raised Future events are prevented Punishment, incentives and perceived usefulness affect motivation to report

The IRS Model • Model based on safety systems • Are safety and security incidents similar? • Is building reporting culture met with similar challenges? • Can the IRS Model be used in information security?

Case • Health care institution • Established practices in safety reporting • Has recently implemented information security reporting (into same system) • How well does that work? • Do assumptions from the IRS model fit in?

Preliminary findings • Theory studies: little theory/publication on information security incident reporting. • Incidents and events are not the same as in safety • Information security has more deliberate, external events, this can reduce benefits. • Events and incidents do not necessarily have the same causes

Preliminary findings • Interview results pending • Attempt to gauge how well the IRS Model’s assumptions match those of a real -life implemented system. • Ultimate goal to tune model to be a basis for developing information security IRS