Unit 7 Organisational Systems Security Task 3 Muhammad























- Slides: 26

Unit 7 - Organisational Systems Security Task 3 Muhammad Zakaria

Security Policies and Guidelines • Disaster recover policies are mainly utilised by ensuing policies which have been put into place by precise instructions when recovering from disaster it can be produced by various ways such as internal internet cyber attacks on the pc or other ways. When focusing on the disaster you generally want to protect your property and avoid this by any faults made by humans and things to do with natural disasters. • In some cases this can happen through failure to comply with equipment as this can also cause disruption with computer and PCs.

Updating of the security procedures • In companies they should always have a up to date software so that they have the latest features as this also keeps the PC trendy. The company should have an automatic system which updates the software such as on a mac they always have a new IOS, this is updated because it may make the PC more faster and also helps with anti-virus as it keeps bugs away. • This also prevents the PC from coming into contact with any hackers as it gives the PC a protective shield to stay away.

Scheduling of security audits • The security audits are generally completed as a result for the corporate networks as well as the configurations of the PC have been approved and completed. Sometimes, the security audits may be done by unknown companies which are through third party applications, they have the security teams which are internally in the computer, sometimes this can be covered through them. • In some scenarios companies tend to use the IP address where they may insert this, and this allows them to know the susceptibility of the computer. • In this article I learnt more about the issues based with third party apps: https: //uk. norton. com/internetsecurity-mobile-the-risks-of-third-party-app-stores. html

Codes Of Conduct – I used this website which talks about data analytics https: //www. research-live. com/article/news/new-mrs-code-of-conduct-launched/id/5059582 • Software acquisition and installation policy: The reason why this is thru is simply to preclude third party application that may be attempted by the employees. In a work environment, some employees may want to download a game onto the computer to play during their lunch break, however they can not go ahead with it as this policy is in place and stands. • Email Usage Policy: The reason why the email policy is in place is to make sure no one in the company is being framed for phishing and for any online hackers who may want to get into the companies software and make fake emails, making it seem its sent by the company. • Internet usage policy: The internet usage policies are enforced to make sure in a work environment, employees are only accessing appropriate websites and nothing outside the companies interest.

Codes Of Conduct • Risk management: The reason why this is carried out is for the identity of an organisation to not be leaked. The policy includes protecting the companies reputation. • Budget setting: The reason why there is a budget policies in to make sure the company can control their costs and doing overspend on things they need. For instance money will be set aside for certain things so that the company don’t overspend for things they may not need. • Surveillance policy: This policy is enforced to make sure the company have good security and nothing is leaked out of the environment.

Employment contracts and security • Hiring Policies: This is normally utilised in the hiring process in a HR department. This means that for certain jobs they may require you to have gone to university and got a degree in a relevant course. • In some cases some employees may take on candidates with no experience and few qualifications, this is to invest in their staff as they may provide them and send them on training where they will achieve qualifications and they’ll also get support with experience.

Separation of duties • The reason why this is enforced is to make sure that companies have more than one person working on a task as with two or three people there is no reason to make errors. • This also, helps with any faults as one person wont be stressed if anything goes wrong as it will be harsh to blame one person. • Therefore this policy is for the protection of staff members to make sure they don’t feel alone.

Ensuring compliance • When ensuring the compliance this means the regulatory for companies making sure things are operating and the employees need to comply with the rules and regulations over wise this can cause problems such as prosecutions and court order which can escalate enormously. • Also, in companies its very important for the company to train their staff well as they represent the organisation and any rules they break wont only affect them but has huge impact on the company.

Disciplinary Procedure • The disciplinary procedure is applied to employees when they may not follow company instructions and fail to comply with the code of conduct, this can result to many consequences. • Usually, in work places there are rules and regulations which employees know and understand they must follow, they may also sign contracts to prove they have read the contracts. However, when they don’t follow the rules this can result them in losing their jobs or be given a warning followed up by a meeting with head manager.

Training and communicating with staff • This is very significant for a work place to run, staff should have good communication skills and build a healthy relationship with their staff members. • In work places, weekly or monthly 1 -2 -1 s should be done in order for employers to know what's going through their employees mind, also for things like personal development, as this is a good opportunity for managers to know whether they want to send them employers out for more work and become higher within the field of work. • Also, if an employee is new, managers should make sure to check on their staff and see how they’re finding it.

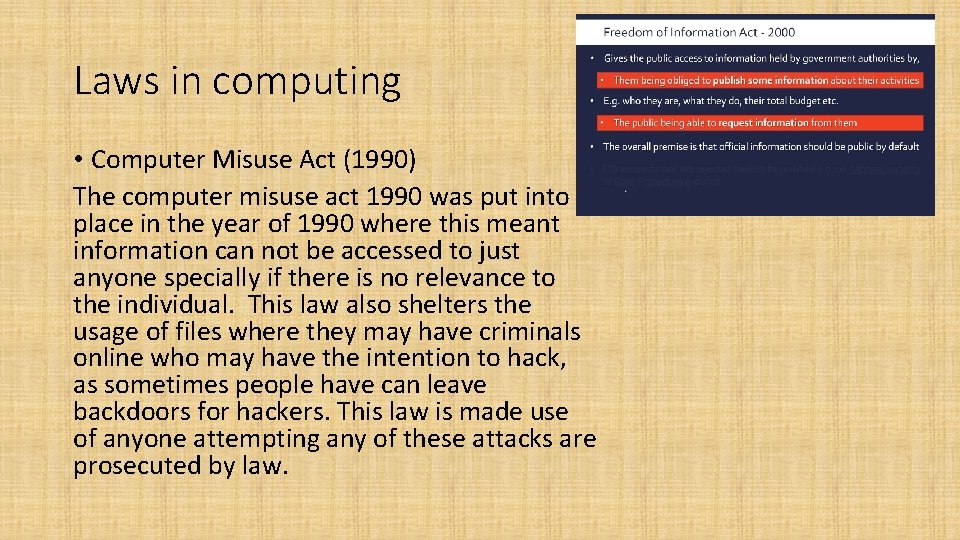
Laws in computing • Computer Misuse Act (1990) The computer misuse act 1990 was put into place in the year of 1990 where this meant information can not be accessed to just anyone specially if there is no relevance to the individual. This law also shelters the usage of files where they may have criminals online who may have the intention to hack, as sometimes people have can leave backdoors for hackers. This law is made use of anyone attempting any of these attacks are prosecuted by law.

Designs and the patents act (1988) • This law can benefit everyone in terms of ensuring people who may have work they created by themselves isn’t just taken and also allows them to have control on who have access onto the work individuals have created. • This law helps people get recognition because if someone creates a game for an example this means their one is the original however if someone creates something similar but with the exact same concept then this means this is copyright, therefore the person will have to reach out to the creator and ask for permission, also promote the original person as this was their work, which has been further produced.

Privacy and compensation requirements of the data protection act (1984, 1998, 2000) • The data protection act is like a barrier which can help keeping the equilibrium between rights of companies and the individuals. • This keeps data protected and doesn’t allow just anyone have access to data, this law is quite basic however still protects data from the outside world. • The rulings of this are fairly and lawfully processed, information is not kept longer than necessary and the individual is asked if they want data deleted.

Copy Rights • Open source – this a software which works with copyright, this is generally exposed to use as there is no charge to access this. • As this is a open source this means that the software can almost be modified by anyone or also unmodified. • However this open source follows a number of 10 rules which must be follow for the software licensers. • Approved Components. Developer Downloads. Code Reuse. Commercial Apps. Third Party Libraries. Outsourced Development.

Freeware • The freeware software is another software which can be accessed through the public as it is free. • However Freeware is also developed through the copyrighted users which means the owner of this has great authority to change the coding and can do whatever with the distribution. • This has a shared developer where the code and data is open through the redistribution and makes use of collaboration.

Shareware • The shareware is a software which has also been dispersed free of charge however you can not access the full package and software as you only get a taste through downloading the trial which may last a month however you need to pay for the actual software. • For instance there is Norton Anti-virus who may protect your computer up to 30 days however after that you need to pay. Sometimes this can be very beneficial as the antivirus can run a test through the system to check for any bugs using the trial.

Commercial Software • The commercial software is generally the exact contrary of the freeware software. The commercial software is the created for the sales of male whilst focusing the purpose of commercial. • The commercial software's are proprietary which have the closed source coding's. There are lots of different operating system which are open sourced for instance Linux is one which works with different software's. • You can purchase this however just like any other software you get a free trial then are required to purchased if you please to do.

Ethical decision making • There is a concept of having freedom of information versus person privacy which means individuals are required to have privacy as there can be implication which lead to effecting information as well as exposing the company including the staff. • This can be when companies may want to take pictures of their staff and upload online in order to show the company is diverse and for people to know who the staff members are within the company.

Permissions to use photographs or videos • In business companies sometimes they may have signs up where you cant take pictures as there is a strict policy due to confidentiality. For instance in business environments as they’re strictly for work they may not want visitors to take pictures in safety for staff members but also you can never be sure where the image will send up. • Also, if you was to enter a business meeting and general meetup with clients you may not be allowed to video record the meetings as there may be a write up of a plan which can not leave the environment and must only stay within that environment.

CCTV footage • In most places, there are CCTV cameras located in various destinations, this is for the safety of the environment as security guards may not be able to be in multiple places at the same time, however having cameras protects the environment from anyone causing disruption • Also, sometimes CCTVs can help with scaring visitors from not following the environmental guidelines as if they do anything illegal, the camera will be taking note and there will be proof of the evidence.

Professional Bodies • Business Software Alliance – This firstly originated through Microsoft who released this in the years of 1998. The reason why this was developed was to eliminate the chances for software piracy, this was made by the producers of the BSA. • The Business Software Alliance is also collaborated with the Apple, Microsoft and Adobe which encourages the use of copyrighted software's. • This is also beneficial as it indorses the use of blowing the whistle.

Federation Against Software Theft (FAST) • The federation against software theft was one of the worldwide first organisation which indorses the use which is legal for the software as this also covers the property rights that are intellectual based of the publishers for software's. • The company was acknowledged by the British Computing Society as this has been efficacious due to the fact that the location was in the Parliament which then made huge effect on changing for the law of copyright act.

British Computing Society (BCS) • The British Computing Society is a verified charity which in 1984 has been fused with the Royal Charter. The BCS was originally brought out in 1957. • The role of this company is to promote studying and expand individual knowledge in the computer technology industry which they can be up to date with todays society in the computing field.

Association of computing machinery (ACM) • The association of the computing machinery is a organisation which is a non profit based company who has been apart of the technology industry for many years. The company is based in the states USA, New York City where they have at least over 100, 000 members in the company.

Conclusion • After reviewing all of the security tools that can be used to protect our computers and software, I think anti-virus software extremely useful when protecting our software's as this allows us to be aware of what things are harmful for the PC. Also, things like Norton even though they can be price effective it is worth it when you have a business or even personal computer in order to protected your devices. • Another way I think should be utilised the most also is things like having physical security which includes having security cameras that way you can protect your computer and also you will have security footage and evidence of who has been in your things and been touching things without your permission. • Focusing on all the strategies, it is important to make sure businesses are up to date with the laws and making sure the rules and regulations are applied for their safety. The British Computing Society should be used and implemented in all companies to do with technology. • I think as a world we should try to understand the mind of a hacker and companies should spend money on sophisticated training to learn how to hack, the reason why I believe this can be very beneficial is that if companies know how to hack then you will know what to look out for when hackers come to attack.