Unit 7 Organisational Systems Security Unit 7 Task























- Slides: 26

Unit 7: Organisational Systems Security Unit 7 - Task 1

Malicious Damage Using any type of electronic device which can store sensitive or important information always has risks included. One of these potential threats happen to be malicious damage. Malicious damage is when a person or group decide to vandalise or destroy something that doesn’t belong to them with intent of doing something bad. This includes physical hardware as well as software. An example would be destroying a keyboard that belongs to a company. This is malicious damage as they didn’t give consent for you to damage it, and they are doing it with ill intent. Potential Threats Many types of malicious data exist, however for pretty much all of them, there is a way to counter it. An example would be if someone is going to destroy something, a camera would be able to give away their identity, or if someone wanted to steal data from home, they can be traced down from their IP address and also have their identity revealed

Threats Related to ecommerce Threats related to e-commerce are threats that are based around electronic issues, such as phishing. Phishing is an issue where your data isn’t safe enough and someone can steal it and use it to ransom your data for money. It can also be used to sell to other companies for money. This can be caused by accidentally too, such as making an easy password or giving incorrect information on the system. One way to prevent issues with e-commerce is to have a hierarchical system where the people at the top get the most access while newer members or less important members of the company get lower access levels, ensuring that no sensitive data is released without permission. Potential Threats Another way to prevent accidental threats to ecommerce is to ensure that the password safe. An example is making sure that the passwords have at least 1 capital letter, 1 number, and one symbol such as “. , ? !”. This works as the combination of those 3 things makes it difficult for someone to be able to hack into an account.

Counterfeit Goods When a device or product becomes famous, they tend to get a lot of people trying to copy their products and make money. Of course, the counterfeit isn’t as good as the original, but if it is sold, they make a large profit. An example would be someone selling a PC claiming that it is made by Dell, along with a dell case, however the CPU, Ram and harddisk inside are really bad quality due to being placed there personally by the person selling it. The seller gains money by these products which means that the customers end up losing money. Some companies have specific symbols or materials to try prevent people from copying their products, however people’s ingenuity help them find a way to make profit either way Potential Threats Counterfeit Goods are found everywhere, in fact, recently, counterfeit trading has risen up to 3. 3% of the world trade and is still rising! If you’ve ever copied a film off a CD or DVD, and distributed it, you’ve given away a counterfeit software since it isn’t the original CD/DVD.

Technical failures Technical Failures can be accidental or intentional. Both can lead to massive repercussions, for instance if a company bought a software from someone and one of the lines in the code had an issue that someone could exploit, it could result in the code being used against the company and they end up losing money. One way to stop this is to pay people to try hack into the system and find any unintentional cracks in the system and fix them. However if the technical failure was intentional, then the person who did it probably has a plan to try gain money by exploiting the issue. This could cause the company to lose a lot of money and important data. Potential Threats There can be two types of technical failures; One is technical hardware failure, while the other is technical software failure. The technical hardware failure is an issue where the equipment inside the product have flaws that could be unknown or known by the manufacturer. Technical software failure is when there is an issue with the code of a software which could lead to issues arising. These may also be known or unknown by the creator of the software.

Human Errors Humans are by no means perfect, we all make mistakes. Some mistakes are smaller than others and cause less repercussions, however sometimes mistakes could cause the downfall of a massive company. An error in the code could allow someone to get into the system and find sensitive data, while an error in the placement of hardware could cause something to overheat and end up exploding. The first one may cause a lot of problems but compared to the hardware mistakes which could cause physical harm to people, it’s lot less dangerous. Potential Threats Mistakes can be prevented by having people check on the code or hardware after it’s all finished. I think checking it 3 times with 3 different people would be best as you get to see it from 3 different angles.

Theft of equipment Computers tend to be more expensive gadgets and attract the eyes of many thieves. Having one stolen from you could cause a loss of up to £ 2000. What could be worse is if you haven’t backed up your data, you could lose all the data that was on the PC. This could also be dangerous if you have sensitive data on it. To prevent the data being stolen, you could have a password and if it fails to be put in 5 times, the data should get deleted. However the loss of a PC is still expensive and to prevent it you must have security around the building such as cameras and security guards. Potential Threats You can also use a tracking software so that the PC is able to be located if stolen. This will help retrieve your PC and catch the thief at the same time. Data could also be encrypted to protect it from being used against you.

Internal The internal malicious damage could be either an internal attack or an internal accident. An accident could be caused by human error which could allow people to be able to view private information such as a customers username and password. An attack on the other hand is intentional as the person who causes it is trying to either steal data or spread it for malicious purposes. Internal malicious damage doesn’t only happen on electronic devices, it could also happen through paper documents or receipts. For example, if you lost a document that was important to the company and ended up giving away someone's credentials, this classifies as an internal accident Malicious damage One way to prevent internet malicious damage would be to have an hierarchical access system where the higher access you have, the more information you can view. This also prevents moles from being able to access data.

external External malicious damage is similar to internal malicious damage, there is also external accidents and external attacks. External accidents are caused by something outside of the company, for example the weather could be an external accident if a storm or hurricane causes a power outage and results in a loss of data. If the company doesn’t have a backup, they could end up losing a lot of important information and could even corrupt some of the software. External attacks on the other hand are malicious attacks by hackers that wish to steal or ransom information for money or for their own means. Malicious damage Hackers can be stopped by having really good security such as encrypting passwords and making sure that there are security questions which only employers are able to answer personally.

Access causing damage can be described as someone ramming into your pc information, like planting viruses and causing data to be corrupted or lost. Hackers who do this could also be trying to erase an evidence of their involvement. The viruses also spread to other devices, and could cost a lot to repair them all. There are different types of viruses, but two that cause damage are Trojans and worms. Trojans trick people into logging in on a fake site, and could end up changing your password completely, which means you could lose all your data and access to your accounts/computer. Worms on the other hand infects a computer and replicates itself and spreads through the system or network. It could also end up causing the same damage as a virus. Malicious damage The best way to prevent viruses is to have really good security, good enough to block all incoming threats that could cause you to lose money or lose important data. Also having a frequent backup occurring helps you prevent data loss. You could also have some hackers come in and try to hack into your system and tell you the issues and how to fix them, this allows you to see the flaws within your own systems.

Access without damage - Phishing is trying to get into someone personal information to try and make money. The hacker could be trying to ransom the information to make some money, depending on how important and private the information is. These usually appear in the spam or junk mails and are asking for peoples information. An example would be getting an email from someone you don’t know asking you to confirm your account details as it may be under a security threat, and taking you to an unknown page which looks similar to the original. This gives the hacker your account details and they could end up changing your password, eventually locking you out of your own account. Malicious damage

Access without damage - piggybacking Piggybacking is using someone else's internet without their permission. This is a threat as they could end up downloading illegal software on your internet which will eventually be traced up to you. Not only that, but your internet will also be slowed down as it’s using more bandwidth. Preventing this isn’t too hard as long you have a good password and your network should also be secure. This will make it harder for people to get into your internet and even if they do, it will make it more difficult to see your personal data. Malicious damage

Website defacements are usually harmless. This is when someone gains unauthorised access to administrator levels and changes the visual representation of a website. This doesn’t cause much harm and is usually done by people as a joke. One of the ways to prevent this is to have good security and making sure that everyone has certain access levels. Threats related to ecommerce However, sometimes website defacements can be used to distract a company from a virus or any other threats and divert their attention, allowing the virus to corrupt important information.

Control of access to data via third party suppliers This is when a third party source has access to the company’s data. This can be very dangerous as if the third party was hacked, the data within the company can be accessed by those hackers. This can be prevented by ensuring that the third party source is very secure and also removing the third parties that no longer require access to the data. This is similar to lending your key to your friend, if the key is stolen from your friend, the thief could access your house. This could cause severe issues as the data/items could be ransomed. Threats related to ecommerce

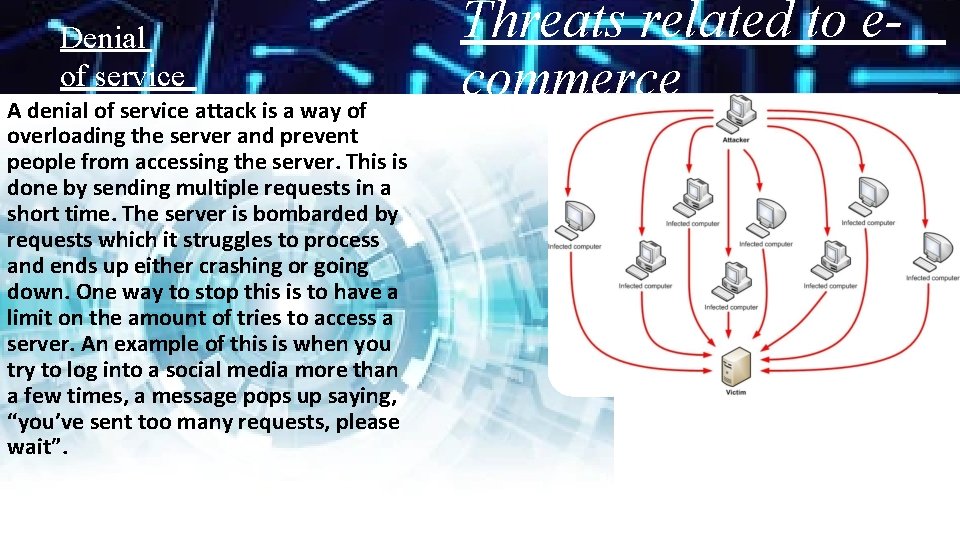
Denial of service A denial of service attack is a way of overloading the server and prevent people from accessing the server. This is done by sending multiple requests in a short time. The server is bombarded by requests which it struggles to process and ends up either crashing or going down. One way to stop this is to have a limit on the amount of tries to access a server. An example of this is when you try to log into a social media more than a few times, a message pops up saying, “you’ve sent too many requests, please wait”. Threats related to ecommerce

Products at risk Software and DVD’s are vulnerable to being reproduced into various copies and sold or distributed. This usually means that the company earns less money and it could also give bad reputation to the company as the software/DVD may have a virus as it isn’t secure. This can be prevented by ensuring that there is a encryption on the software/DVD to prevent copying and distributing it. Counterfeit goods

Distribution mechanisms are a way around having to spend your own money to buy products. They usually involve people sharing their own copies. This was made illegal due to the fact that there was a massive loss of profit and if someone was caught distributing the products without permission, there would be a fine. An example of this is 123 movies which allowed everyone to watch any movie for free. This server would usually shut down due to it being illegal, and a new one would be set up soon. The files can also damage the users computer as it is not secure. Counterfeit Goods

Loss of service can occur because of any of these attacks. This can cause the servers that the company relies on heavily to shut down. This will mean that not only the users will be shut out, but so will the staff. Nobody will be able to access the server and therefore the company will not be able to run. This may cause setbacks as the reputation of the company will also drop Organisational Impact

Loss of business/income If the company is attacked any of the data is corrupted or lost. This may cause the reputation of the company to fall, causing many to leave them. This means there will be a loss of income. It could also cause a loss of user’s information which means they will lose all records of the customers being with them. The effects of this may also dramatically reduce their income. Nowadays, all information is stored electronically to ensure that they are safe. To ensure that it isn’t lost during an attack, backups are quite important and help prevent loss of data. Organisational Impacts

Increased cost Once a company is attacked and fails to defend against it, they will usually end up losing a lot of customers. This then results in a loss of income. However to prevent the same attack occurring twice, a company must pay more for a better security system. This means that they need more money. The company would then increase the prices to allow them to afford the better security software. This may increase the loss of customers. Therefore putting the company in a massive predicament. Organisational Impacts

Poor image The image of a company is really important to ensure that the company grows. However if a company were to be attacked and lose data, the reputation of the company would drop. This means they would have less customers thinking about joining them. It could also cause existing customers to ask for their information to be removed and to leave the company’s services. This means they would earn less income, and have lower security, which could eventually cause a company to shut down. Organisational Impacts

Confidentiality The confidentiality of a customer is one of the most important aspects of a business. To ensure the customers safety, none of their details must be leaked. One way to prevent this is to have a hierarchical system where only those at the top are able to view such sensitive information. This will prevent those who do not have permission or a high enough access level to be able to view the information. Another thing to ensure is that even if someone is able to view the information due to their access level being high enough, the system should record who and when it was viewed by. This will ensure that if the information is leaked, the culprit will be easily found. The information should not be used for purposes other than the company’s services. Information Security

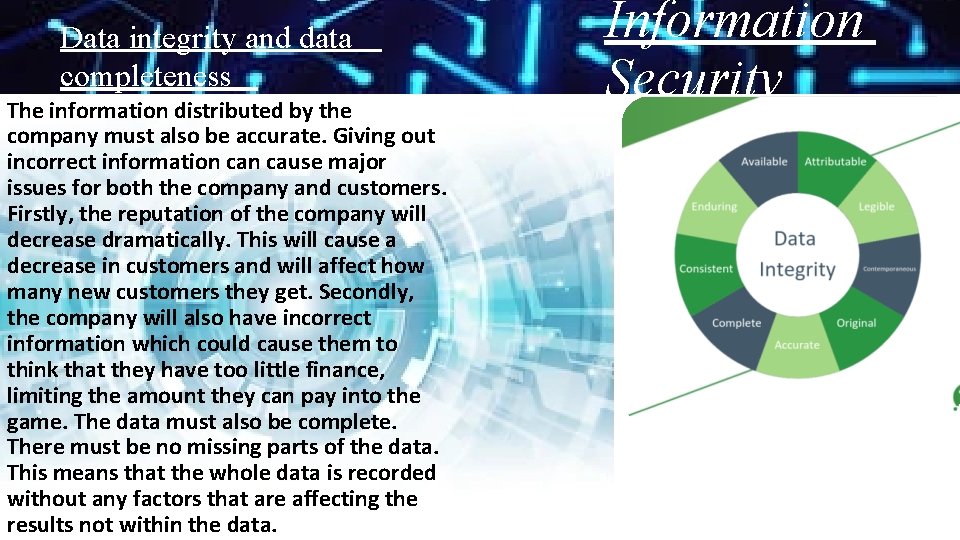
Data integrity and data completeness The information distributed by the company must also be accurate. Giving out incorrect information cause major issues for both the company and customers. Firstly, the reputation of the company will decrease dramatically. This will cause a decrease in customers and will affect how many new customers they get. Secondly, the company will also have incorrect information which could cause them to think that they have too little finance, limiting the amount they can pay into the game. The data must also be complete. There must be no missing parts of the data. This means that the whole data is recorded without any factors that are affecting the results not within the data. Information Security

Access to data should be regularly monitored to ensure that only people who have received certain permission to view specific data can view it when necessary. This prevents people from looking at sensitive data which they are not supposed to be able to view. This is important because if someone data is leaked, it can cause serious repercussions to both the customer and the company. An example of ensuring that the access to data is safe is by making sure that if someone no longer needs to look at the data, their permissions to view it are taken away. Information Security

Examples • Target – Malicious damage (Internal) https: //www. nytimes. com/2017/05/23/business/target-security-breach-settlement. html • European bank – Malicious damage (External) https: //www. bbc. co. uk/news/topics/cp 3 mvpdp 1 r 2 t/cyber-attacks • Mirai Botnet – Do. S https: //krebsonsecurity. com/tag/mirai-botnet/ • ILOVEYOU – access causing damage https: //www. computerhope. com/vinfo/iloveyou. htm • Russian Spyware – access without damage https: //www. cnbc. com/2014/03/07/suspected-russianspyware-in-europe-us-attacks. html • Google Docs - Phishing https: //www. bbc. co. uk/news/business-39798022

Examples • NHS – Website Defacement https: //www. bbc. co. uk/news/technology-43812539 • Under armour – Third party access https: //www. forbes. com/sites/paullamkin/2018/03/30/underarmour-admits-huge-myfitnesspal-data-hack/#3110069 acc 54 • Counterfeit goods – Products at risk https: //www. theguardian. com/money/2018/dec/03/christmasshoppers-warned-over-rise-in-fake-goods-counterfeits • Three – Loss of service https: //www. bbc. co. uk/news/technology-50080876