Unit 7 Organisational Systems Security Security Policies and



























- Slides: 31

Unit 7 Organisational Systems Security

Security Policies and Guidelines

Disaster Recovery Policies Disaster recovery policies are a set of procedures or rules that allow the recovery of a system after a natural disaster or a disaster caused by human error.

Updating of security procedures It is important to make sure that all computers in a network have up to date security software such as antivirus so that new viruses for example aren’t able to bypass the network’s defences.

Scheduling of security audits Scheduling security audits makes sure that the systems security is preserved. This can be done by testing the computers in a network to find out which ones are susceptible to malware then action can be taken to strengthen the security systems.

Codes of conduct Email Usage policy: It is important to educate employees of the potential threats when using emails. Phishing is a very common way that hackers try to cause malicious damage by trying to replicate an authentic email however they will put a link that usually contains malware to retrieve/corrupt data. Internet Usage policy: These are a set of policies that tell employees to refrain from browsing certain websites whilst using the company computers such as social media as they can contain material that is illegal or bad for the company image and can also contain other threats such as phishing and malware. Software acquisition and installation policy: This is done to stop employees from downloading and installing third party software's to once again prevent harmful malware entering the computer network which can cause a lot of damage to the systems.

Codes of conduct Surveillance policy: This is to make sure that there is reliable surveillance environment inside the company and that the company meets the requirements of the Workplace Surveillance Legislation. Risk management: This is basically trying to locate potential weaknesses in security and trying to prevent future security breaches. It is important to identify and analyse the risks involved with trying to take administrative actions with regards to keeping your organization protected. Budget setting: This is to make sure that money is designated proportionally to all the different departments of a company so that too much money isn’t wasted on one specific thing which can negatively impact all the other departments.

Employment Contracts and Security

Hiring Policies These are set in place to make sure that only qualified people are able to get the job. However, In some cases companies may want to prioritize hiring existing employees for other jobs in order to save time and human resources.

Separation of Duties Essentially, the concept of this is to assign more than 1 person for a specific task to prevent theft or fraud and also to be able to review the task to look out for errors.

Ensuring compliance including disciplinary procedures Compliance is necessary as changes can happen frequently with the law and failure to comply can cause the company fines and perhaps even prosecution. Disciplinary procedures can be taken for employees that do not comply for example salary deductions.

Training and communicating with staff as to their responsibilities Employees should be trained to the required standard and should be well informed of their responsibilities. Communication is also necessary so feedback can be given.

Laws

Computer misuse act 1990 This law prhobits unauthorised access to computer programs/data including unauthorised modification of them. And unauthorised access with criminal intent.

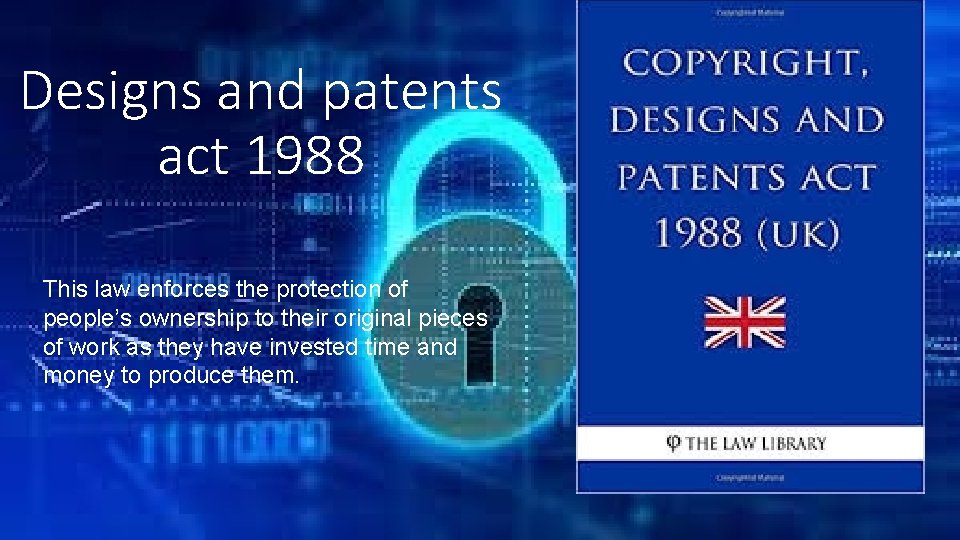
Designs and patents act 1988 This law enforces the protection of people’s ownership to their original pieces of work as they have invested time and money to produce them.

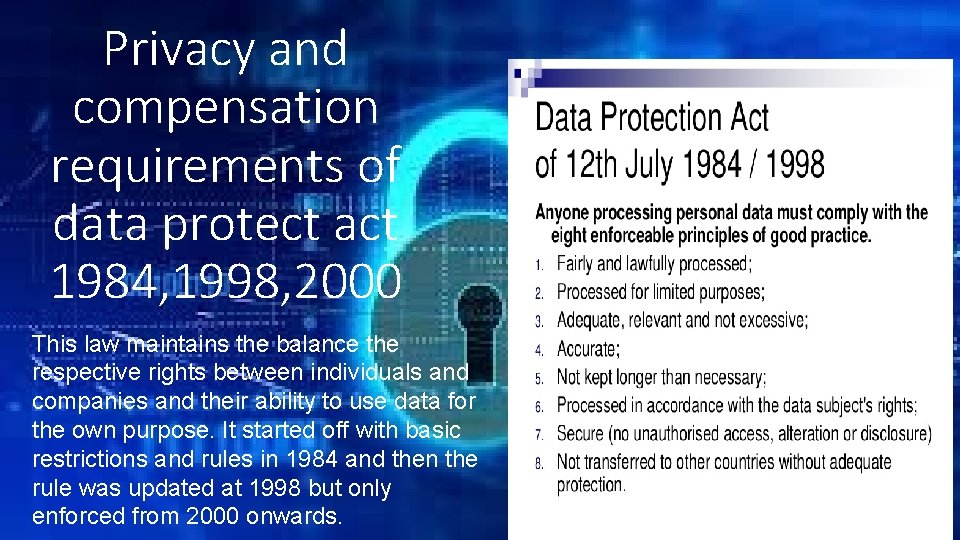
Privacy and compensation requirements of data protect act 1984, 1998, 2000 This law maintains the balance the respective rights between individuals and companies and their ability to use data for the own purpose. It started off with basic restrictions and rules in 1984 and then the rule was updated at 1998 but only enforced from 2000 onwards.

Copyright

Open source This is a type of copyright that is open to use and widely accessible and can be altered by anyone. There are no limitations of what can be done with software of this kind however it has to meet the criteria's of open software licence in order for a licence to be given.

Freeware This type of software is also widely and freely available to the public however it is copyrighted by its owner and cannot be modified or sold.

Shareware This is software that is available to the public for free but for a limited amount of time so that they user can decide whether or not to purchase the full version.

Commercial software This kind of software is available for mass distribution but is usually not free however once the user purchases this they can then modify it and re-sell it as they wish.

Ethical Decision Making

Freedom of information versus personal privacy It is important to understand what kind of information you’re putting out on the internet such as social media as some of it can be stolen from you as you don’t actually own the platforms. However, if you do keep important things private then you have the right for that information to not be retrieved.

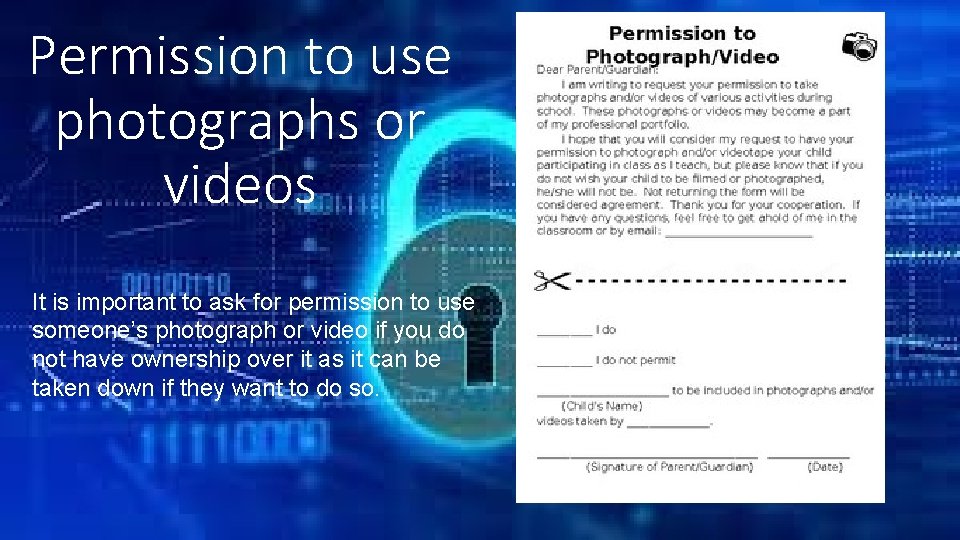
Permission to use photographs or videos It is important to ask for permission to use someone’s photograph or video if you do not have ownership over it as it can be taken down if they want to do so.

CCTV Footage This is a very important surveillance device and can be used to prosecute malicious damage such as theft of equipment however it is crucial that employees’ have their privacy in places like toilets.

Professional Bodies

Organisations: BSA This software company works with software licencing companies and they mainly focus on dealing with issues or limitations that happen with systems by helping out with audit tools.

Federation against software theft This organisation’s main focus is to deal with software piracy of all different kinds and will prosecute companies and individuals who partake in software piracy.

British computing society This organisation is a charity that tries to promote the study of computing and to increase the general stand of education regarding ICT for everyone in the UK.

Association of computing machinery This organisation is the worlds biggest educational and scientific computing society which tries to bring everyone in the field together to try to share resources and fix some of the problems that exist within the field.

Evaluate the security policies used in an organisation