To Filter or to Authorize NetworkLayer Do S





























- Slides: 43

“To Filter or to Authorize: Network-Layer Do. S Defense Against Multimillion-node Botnets” Xin Liu, Xiaowei Yang, Yanbin Lu Department of Computer Science, University of California, Irvine Published: SIGCOMM 2008 Conference Presented by: Christopher Daiello Presented on: March 26, 2009 CAP 6135 Malware and Software Vulnerability Analysis (Spring 2009) Professor: Dr. Cliff Zou

Outline Motivation / Strategy n Stop. It Summery n Stop. It Design n Prototype Experiment n Defense Solution Comparison n Review n References n

Motivation n n Botnets continue to be a rising threat. In September 2007, the Storm botnet alone reached 50 million compromised hosts. If each host sends one full packet (1500 bytes), a 10 million botnet would exceed 120 Gbps, enough to take down any site on the internet. Many solutions have been proposed to combat this problem, however there lacks a consensus on how to build a Do. S resistant network.

Botnet Defensive Strategies n Capability Approach n n Receiver controls the traffic it receives. Explicitly authorizes the traffic it receives. Popular capability-based systems: TVA and Portcullis Filter Approach n n n Receiver allows all traffic until it detects a problem. Receiver limits attack traffic by dynamically installing filters. Popular filter-based systems: AITF and Pushback

Which strategy is more effective? Capability Design vs Filter Design? n Current filter-based solutions have limitations that prevent a fair comparison. n AITF verifies filter install requests with a 3 -way handshake. Verification communication may get blocked by attack traffic. n Pushback uses rate limiting (instead of completely blocking) to combat attack traffic. n

Stop. It Summery

Stop. It Filter-based approach design. n Closed-control and open-service architecture. n Allows any receiver to block undesirable traffic. n Mitigates link congestion. n Resistant to filter exhaustion attacks. n Resistant to bandwidth flooding attacks that could prevent the installation of filters. n

Stop. It Design Assumptions Secure Intra-AS Communication – Communication between components within the AS (Autonomous System) is secured. n Attack Traffic Classification – Target systems can identify when they are being attacked. n Feasible – Design is efficient enough to operate on current routers. Public key cryptography is not used at packet forwarding due to high processing costs. n

Stop. It Goals n n Effective Filtering – Filters installed to protect a host machine should not prevent other hosts from communicating with legitimate sources. Secure the defense system itself! n n n Strategic attacks – Attacks aimed to defeat or abuse the system Destination Flood Attacks – Flood the system with traffic to suppress communication. Link Flood Attacks – Congest a link to disrupt communications between systems that share that link.

Stop. It Goals Fail-Safe – System should provide degraded service in the event filters fail to mitigate attack traffic. n Incremental Deployment – System should support incremental deployment and give immediate results to early adopters. n

Stop. It Design

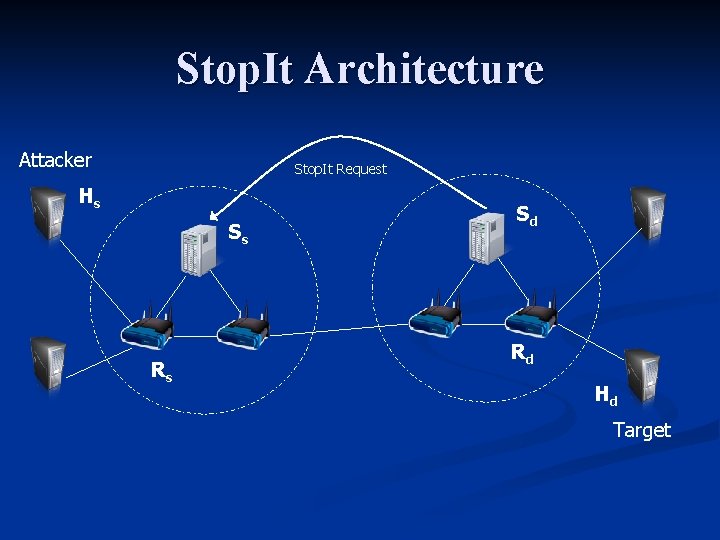
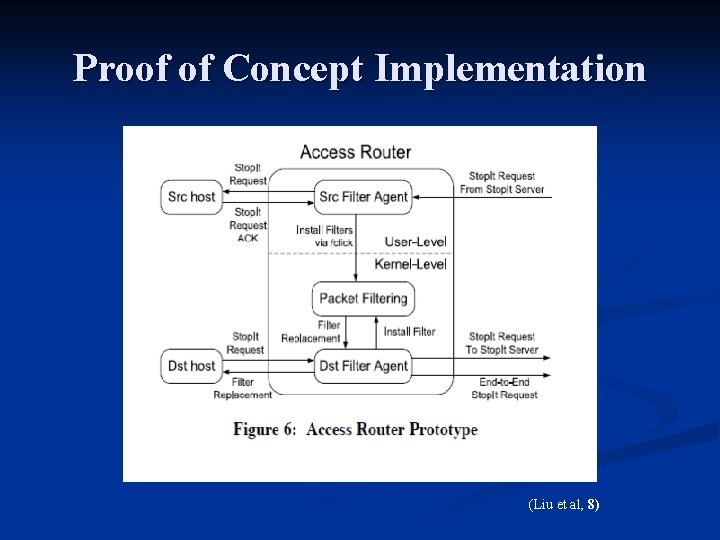
Stop. It Architecture n Infrastructure Service n n n Open-services : any host co-located with the server may request services. Hosts request Stop. It to block attacking traffic. Filter-based implementation n n Source and destination address used to create the filter. Attack traffic is blocked for a period of time Tb. Attack traffic confirmed before the installation of blocking filters. Filter aggregation – compromised hosts share a common address space.

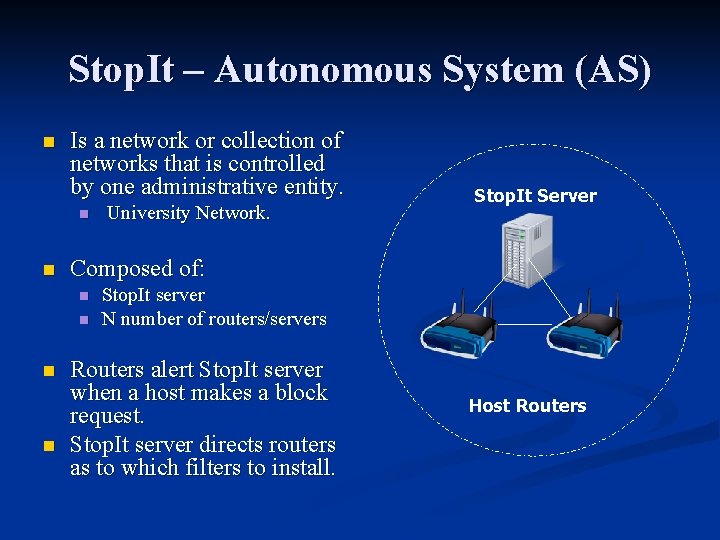
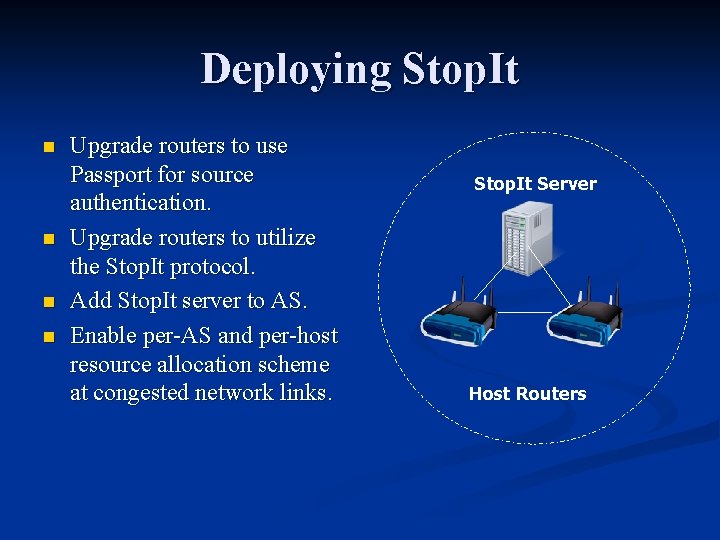
Stop. It – Autonomous System (AS) n Is a network or collection of networks that is controlled by one administrative entity. n n Composed of: n n University Network. Stop. It Server Stop. It server N number of routers/servers Routers alert Stop. It server when a host makes a block request. Stop. It server directs routers as to which filters to install. Host Routers

Stop. It Communication n Stop. It servers communicate with each other to alert of a potential attacking host. Each Stop. It server knows the address of other Stop. It servers. n Stop. It design uses BGP (Border Gateway Protocol) to publish the address of each Stop. It server. n Stop. It implements its own IP protocol for communication between servers and AS routers. n

Stop. It Architecture Attacker Stop. It Request Hs Ss Rs Sd Rd Hd Target

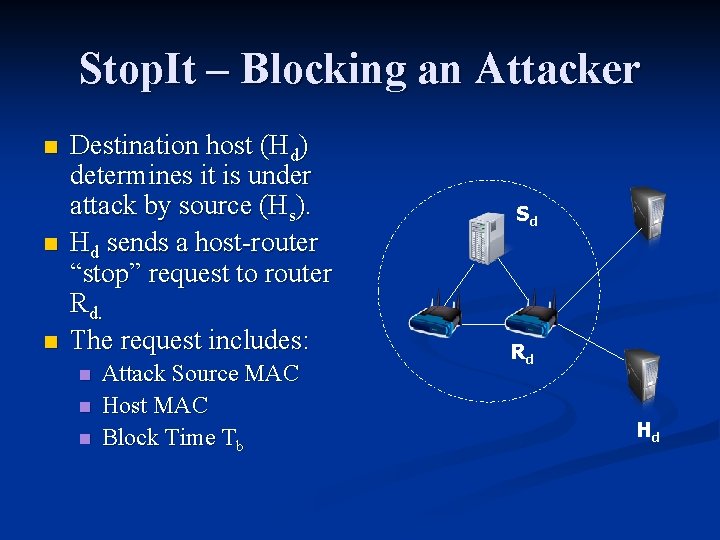
Stop. It – Blocking an Attacker n n n Destination host (Hd) determines it is under attack by source (Hs). Hd sends a host-router “stop” request to router Rd. The request includes: n n n Attack Source MAC Host MAC Block Time Tb Sd Rd Hd

Stop. It - Blocking an Attacker n n n Router Rd verifies the that Hs is in fact attacking Hd. Upon confirmation, Rd sends a router-server request to local AS Stop. It server (Sd). Sd sends an inter-domain stop request to the Stop. It server in the same AS where Hs is located. Sd Rd Hd

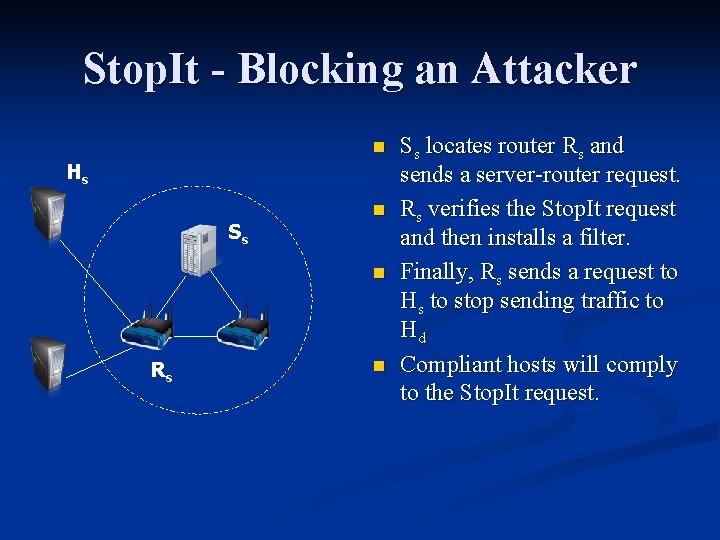
Stop. It - Blocking an Attacker n Hs Ss n n Rs n Ss locates router Rs and sends a server-router request. Rs verifies the Stop. It request and then installs a filter. Finally, Rs sends a request to Hs to stop sending traffic to Hd Compliant hosts will comply to the Stop. It request.

Securing Stop. It n Basic Stop. It Architecture Vulnerabilities Source address spoofing – attacker may spoof address to avoid detection / filtering. n Resource Exhaustion n n Flood filtering requests to overload Stop. It server and routers n Exhaust router’s filters – no more filters available to block Do. S attacks. n Block legitimate traffic – compromised Stop. It server requests filters for legitimate traffic.

Source Authentication n n Stop. It utilizes Passport to prevent source address spoofing. Passport uses symmetric key cryptography. Authentication overhead is equivalent to the authentication used in capability-based system. Border routers at the destination AS verify the source AS before the packet enters the network. Pair-wise keys between two AS are exchanged during the BGP announcement.

Closed Control n Routers receive Stop. It requests from: Local nodes to the AS n Another Stop. It server. n This prevents stop request floods from unknown sources. n If the request is ultimately classified as attack traffic, the router can make a stop request. n

Packet Floods Flooding a common link between two domains could potentially suppress Stop. It requests from being received. n Routers have knowledge of Stop. It server addresses via BGP. n Routers Separate Stop. It requests from other traffic n Fair Queuing n Hierarchical Rate Limiting n

Confirming Attacks n What happens when a destination is compromised? n n n Host may initiate filters to block legitimate traffic to other co-located hosts. Exhaust a source router’s filters so that attack traffic can successfully suppress hosts. Who needs to be verified? n n n Destination Router Source

Confirming Attacks n Destination Router Confirmation Router, Rd checks internal flow cache upon receiving a stop request from Hd n If Hd received traffic recently from Hs the router will install a local filter. n Router sends a Stop. It request directly to Hs n If Hs does not comply, Rd notifies the local Stop. It server of the attacking traffic. n

Confirming Attacks n Source Router Confirmation Source Routers Rs also use a flow cache to confirm a legitimate stop request n Rs installs filters to block the misbehaving host. n Verification protects the source from invalid filter requests from a compromised Hd or another Stop. It server. n

Non-Stop. It Enabled Sources n Stop. It can only block attack traffic at a source when the source implements Stop. It. n n n Sources using Passport only. n n n Attack traffic blocked at the destination router. Attack mitigated with queuing or rate limiting. Destination AS can confirm source of attacking traffic. Passport prevents source from using address spoofing. Sources have incentive to implement Stop. It to isolate possible congestion from compromised hosts.

Deploying Stop. It n n Upgrade routers to use Passport for source authentication. Upgrade routers to utilize the Stop. It protocol. Add Stop. It server to AS. Enable per-AS and per-host resource allocation scheme at congested network links. Stop. It Server Host Routers

Prototype Experiment

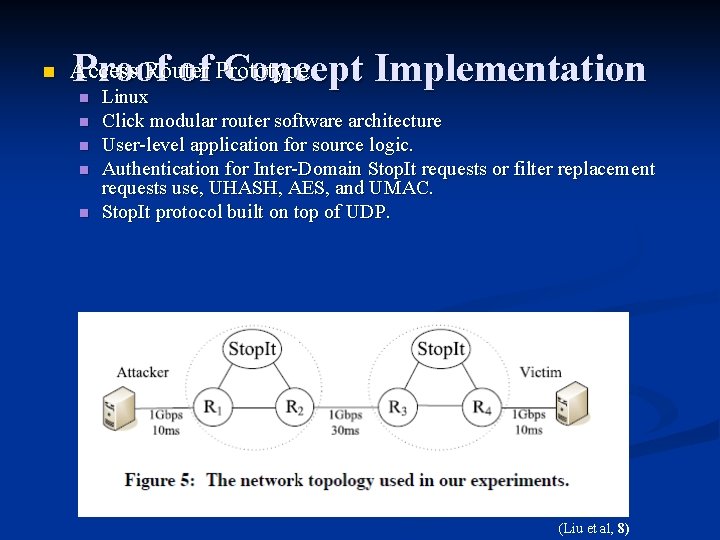
n Proof of Concept Implementation Access Router Prototype n n n Linux Click modular router software architecture User-level application for source logic. Authentication for Inter-Domain Stop. It requests or filter replacement requests use, UHASH, AES, and UMAC. Stop. It protocol built on top of UDP. (Liu et al, 8)

Proof of Concept Implementation (Liu et al, 8)

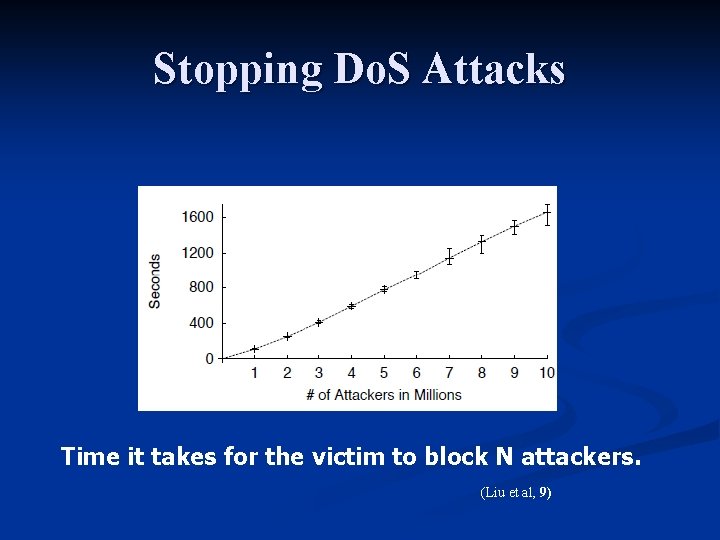
Stopping Do. S Attacks n Scenario Inputs Destination router filters : 256 K n End-to-End Stop. It requests : 3 n n For confirming an actual attack Attacker host simulates 1 to 10 million attackers n Each attack repeats 10 times. n

Stopping Do. S Attacks Time it takes for the victim to block N attackers. (Liu et al, 9)

Defense Solution Comparison

Comparing Anti-Do. S Solutions n n Stop. It design implemented in ns-2 : The Network Simulator Stop. It tested against: n n n AITF, Pushback (capability-based) TVA, TVA+, and Portcullis (filter-based) Scenario topology created from BGP table dump. n n Used 1/20 of topology due to ns-2 limitations. 2/3 AS have attacking hosts, non-uniformly distributed.

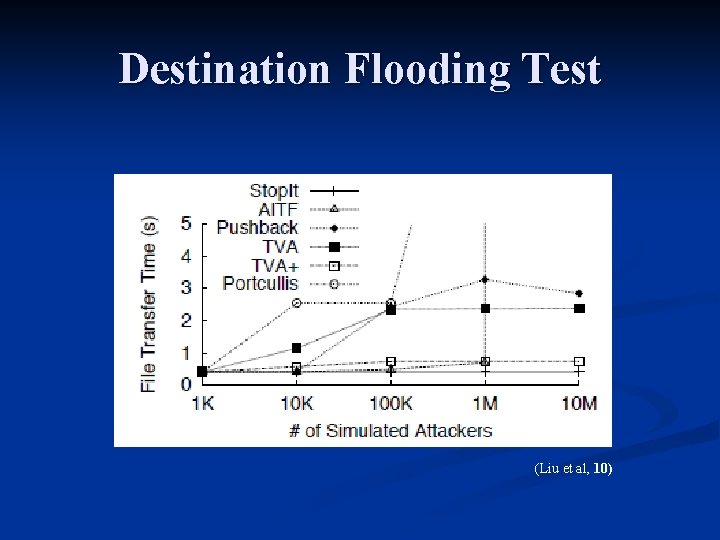
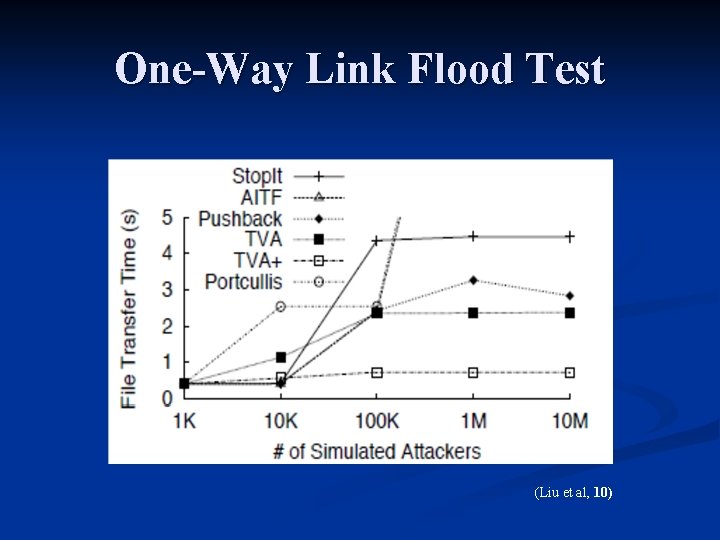
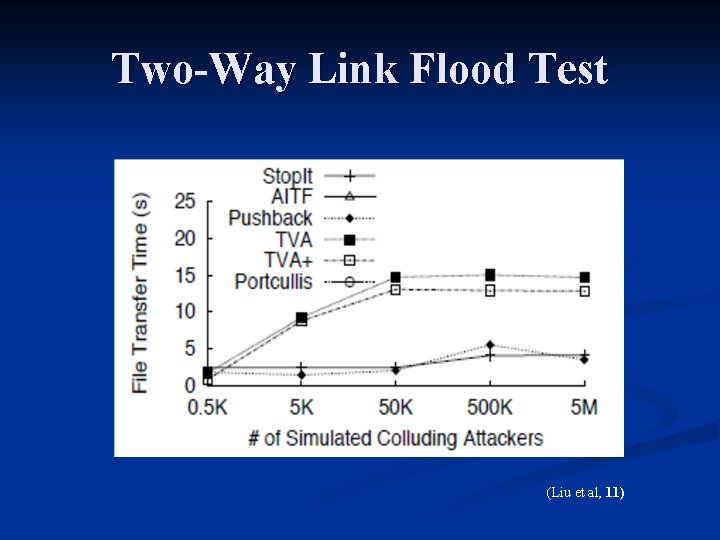
Comparing Anti-Do. S Solutions n Test three types of attacks: Destination Flooding n One-Way Link Flooding n Two-Way Link Flooding n n Testing Metric TCP Transfer performance n Legitimate user sends one 20 KB transfer to the designated victim. n TCP transfer is aborted after 25 seconds. n

Destination Flooding Test (Liu et al, 10)

One-Way Link Flood Test (Liu et al, 10)

Two-Way Link Flood Test (Liu et al, 11)

Comparison Summery Stop. It design outperforms many of the currently existing Do. S defense architectures. n Stop. It does not outperform capability based solutions in all types of Do. S attacks. n Neither solution, filter or capability, has shown a definitive edge over the other. n The best solution maybe a hybrid design. n

Contributions A thorough analysis of the Do. S problem domain. n A complete high level design to a potential solution for destination and link flood Do. S attacks. n A convincing comparison between Stop. It and other currently available filter/capability solutions. n

Weaknesses n n Description of prototype implementation was fairly brief. Prototype testing only utilized one host to simulate multiple attackers. Larger scale testing should be conducted. Internet wide deployment will make updating software challenging. Software must remain backwards compatible with earlier versions. Full deployment of solution required to fully realize the benefits of the Stop. It design.

Future Enhancements n Complete another iteration of prototype development. Implement the Stop. It protocol as intended, as an IP protocol. n Test on a larger network infrastructure. n

References 1. 2. 3. 4. Border Gateway Protocol (BGP). Cisco. http: //www. cisco. com/en/US/docs/internetworking/technology/handbook/bgp. ht ml The Network Simulator – ns-2. http: //www. isi. edu/nsnam/ns/ Autonomous System (Internet). Wikipedia. http: //en. wikipedia. org/wiki/Autonomous_system_(Internet) Liu, Xin; Yang, Xiaowei; Lu, Yanbin; “To Filter or to Authorize: Network-Layer Do. S Defense Against Multimillion-node Botnets”. SIGCOMM ’ 08. August 1722, 2008.