Tiny Sec Link Layer Security Architecture for Wireless














- Slides: 28

Tiny. Sec : Link Layer Security Architecture for Wireless Sensor Networks Chris Karlof : : Naveen Sastry : : David Wagner Presented by Anil Karamchandani 10/01/2007 1

What is ? ? ? Tiny OS Link layer Tiny Sec Wireless Sensor Network 2

Contents • • • Motivation & Tiny. Sec Contributions by the paper. Difference between Sensor Networks and Other Networks. Security threats in WSN. What is Tiny. Sec and its goal. Why Link Architecture. Design Goals. Security Primitive. Design of Tiny. Sec. Modes of Encryption and their drawbacks. Security Analysis of Tiny. Sec. Implementation and Evaluation. 3

What was the motivation ? ? ? • Sensor Networks : Resource Constraint networks , small memory , weak processor , limited energy , less Bandwidth. • 80 % of all 802. 11 wireless networks operate in the clear i. e. without cryptographic protection • Need for an architecture which could change things around. – Tiny. Sec • SW / HW 4

Contributions of this paper • To introduce Tiny. Sec as a protocol for link layer cryptography in Sensor Networks. • To Measure the bandwidth , latency and energy costs of Tiny. Sec. • To encourage people to volunteer and perform research in further higher level of protocols. 5

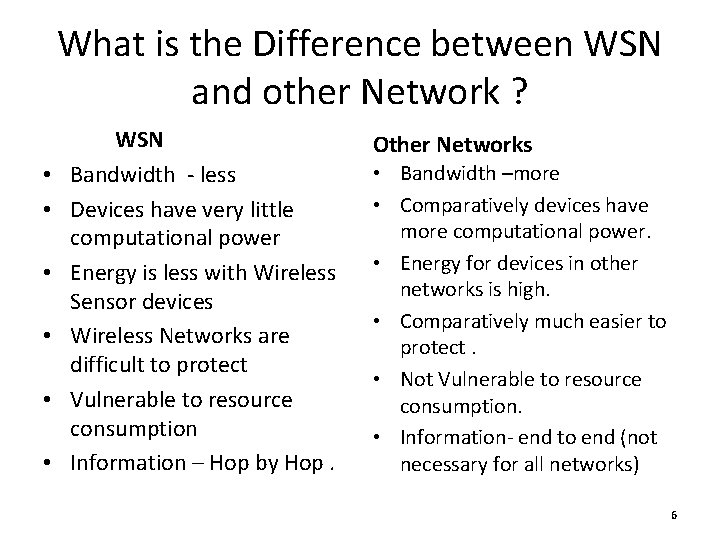
What is the Difference between WSN and other Network ? • • • WSN Bandwidth - less Devices have very little computational power Energy is less with Wireless Sensor devices Wireless Networks are difficult to protect Vulnerable to resource consumption Information – Hop by Hop. Other Networks • Bandwidth –more • Comparatively devices have more computational power. • Energy for devices in other networks is high. • Comparatively much easier to protect. • Not Vulnerable to resource consumption. • Information- end to end (not necessary for all networks) 6

Security Threats in WSN • WSN are difficult to protect. • WSN are in a Broadcast medium • WSN are vulnerable to resource consumption attacks. • Intruders can waste network bandwidth 7

What is Tiny. Sec and its Goal … • Lightweight link layer Security Mechanism for Sensor Networks. • Goal : Is to minimize the overhead with reasonable protection from – Energy – Bandwidth – Latency 8

Why Link Architecture ? ? ? • Conventional networks – authenticity and integrity , confidentiality – end to end mechanism (SSH , SSL). • End to end Security is vulnerable to DOS (Denial of Attacks). • Message integrity should not be checked at the end alone. 9

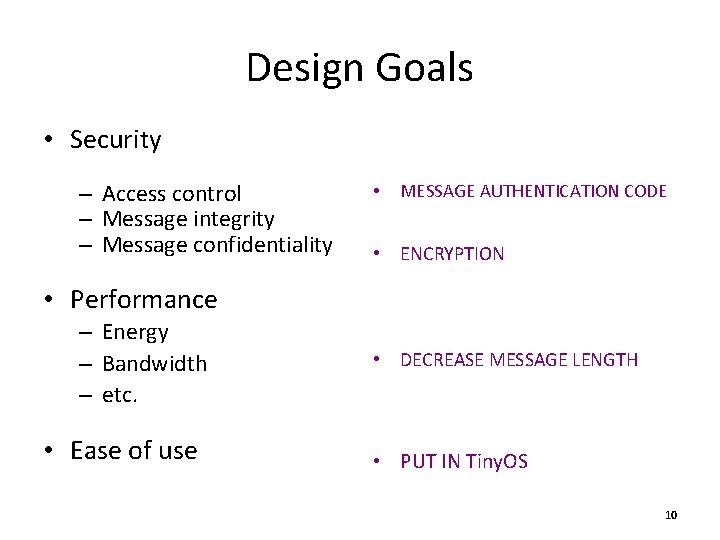
Design Goals • Security – Access control – Message integrity – Message confidentiality • MESSAGE AUTHENTICATION CODE • ENCRYPTION • Performance – Energy – Bandwidth – etc. • Ease of use • DECREASE MESSAGE LENGTH • PUT IN Tiny. OS 10

Security Primitive • Message Authentication code – A cryptographic checksum for checking the message integrity - MAC 11

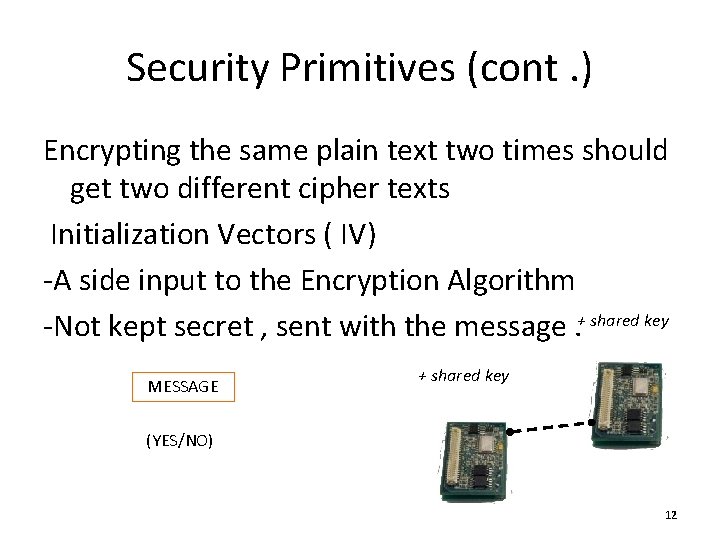
Security Primitives (cont. ) Encrypting the same plain text two times should get two different cipher texts Initialization Vectors ( IV) -A side input to the Encryption Algorithm -Not kept secret , sent with the message. + shared key MESSAGE + shared key (YES/NO) 12

Why design Tiny. Sec ? ? • Why Design Tiny. Sec when existing protocols are present. - IPSec , SSL / SSH are too heavy weight to be used in Sensor Networks. -The packet format adds many bytes of overhead and they were not being designed to built on WSN. 13

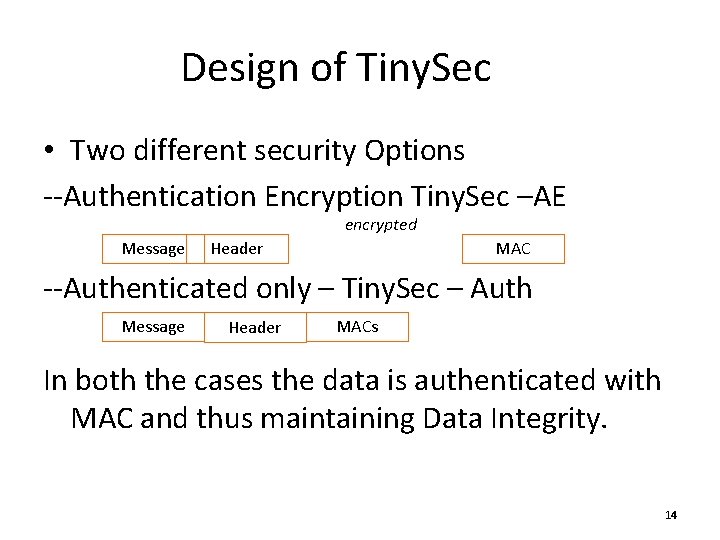
Design of Tiny. Sec • Two different security Options --Authentication Encryption Tiny. Sec –AE encrypted Message Header MAC --Authenticated only – Tiny. Sec – Auth Message Header MACs In both the cases the data is authenticated with MAC and thus maintaining Data Integrity. 14

How can we Encrypt ? ? • Requirements for encryption – To select an encryption scheme CIPHER BLOCK CHAINING : CBC – To specify the IV format – 8 Byte IV format 15

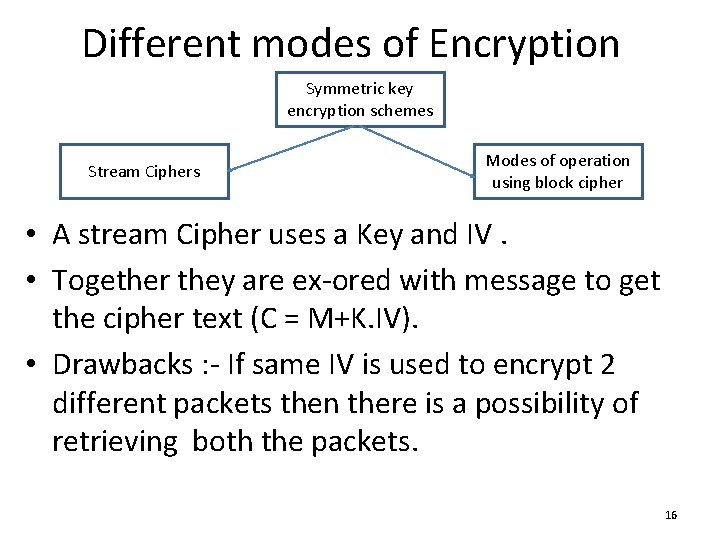
Different modes of Encryption Symmetric key encryption schemes Stream Ciphers Modes of operation using block cipher • A stream Cipher uses a Key and IV. • Together they are ex-ored with message to get the cipher text (C = M+K. IV). • Drawbacks : - If same IV is used to encrypt 2 different packets then there is a possibility of retrieving both the packets. 16

What is CBC mode of Encryption? ? • Link – • In (CBC) mode, each block of plaintext is XORed with the previous ciphertext block before being encrypted. • This way, each ciphertext block is dependent on all plaintext blocks processed up to that point. 17

Drawbacks of CBC Mode. • Given two plaintexts P and P’. If the IV used for the two plaintexts are same then there exists a possibility that the length of the longest shared message is shared / known. 18

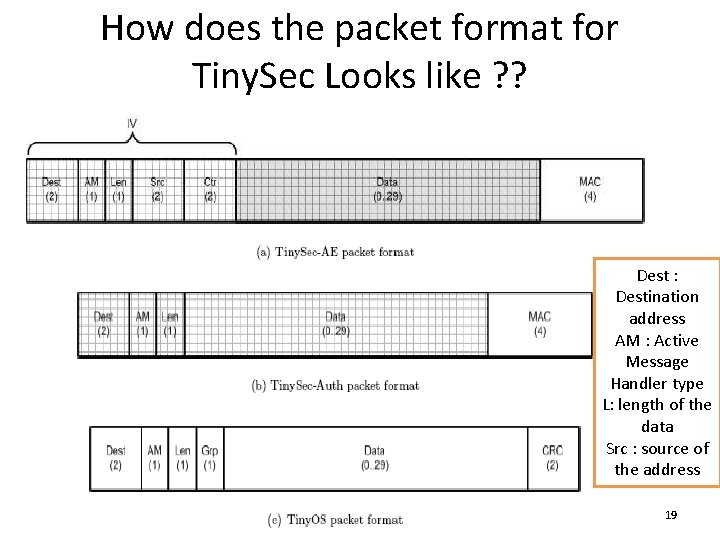
How does the packet format for Tiny. Sec Looks like ? ? Dest : Destination address AM : Active Message Handler type L: length of the data Src : source of the address 19

Security Analysis of Tiny. Sec Message Integrity and Authenticity • Security of a CBC –MAC is proportional to the length of the MAC. • Choice of 4 bytes MAC ? ? 20

Implementation of Tiny. Sec • • • Implemented on Berkeley Sensor Nodes Integrated into TOSSIM simulator 3000 Lines of nes. C code Works in FIFO format Thus Tiny. Sec has got 2 priority Schedulers 21

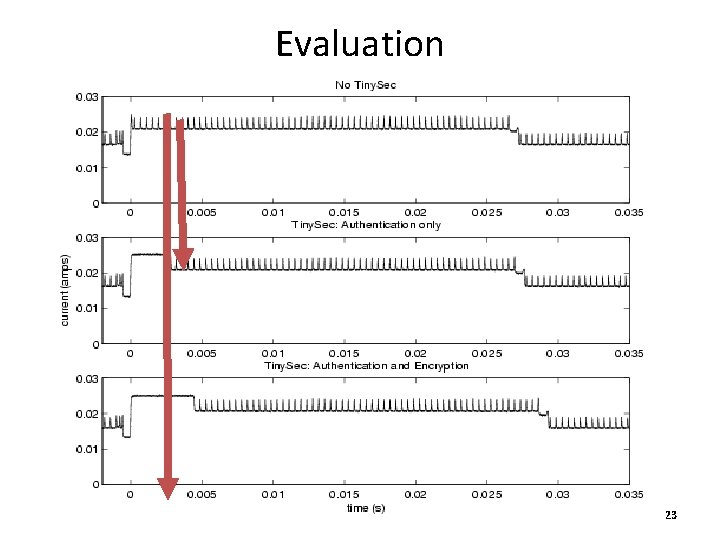
Evaluation • Energy Consumption • Power Consumption • Bandwidth - Energy : 24 bytes of data was transmitted 22

Evaluation 23

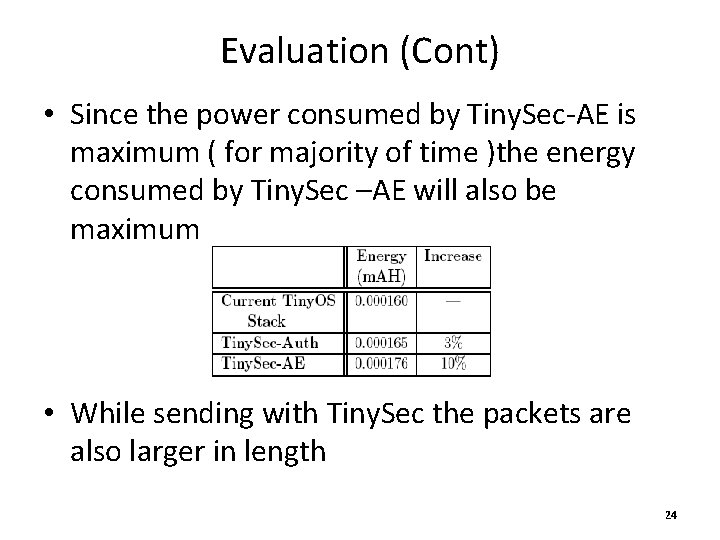
Evaluation (Cont) • Since the power consumed by Tiny. Sec-AE is maximum ( for majority of time )the energy consumed by Tiny. Sec –AE will also be maximum • While sending with Tiny. Sec the packets are also larger in length 24

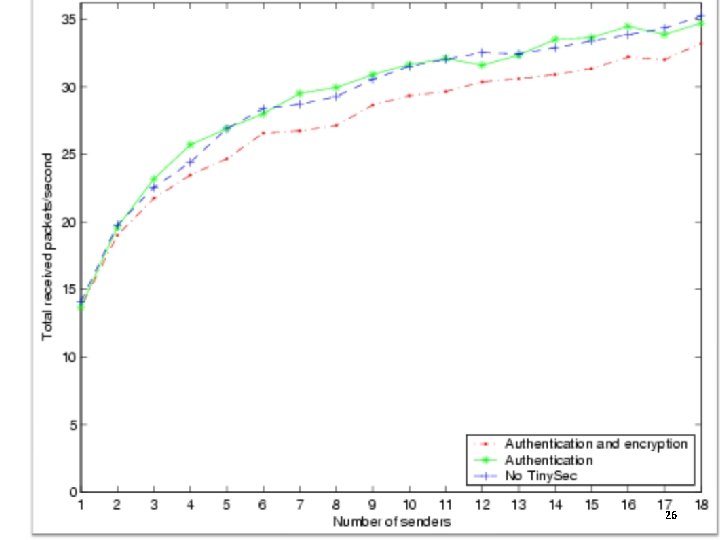
Bandwidth • To measure Bandwidth- 24 bytes packets were sent using Tiny. OS , Tiny. Sec –Auth , Tiny-Auth Enc. • Measured the number of packets that were successfully received. 25

26

Conclusions • We have learnt that there are design vulnerabilities in the conventional protocols for sensor networks. • Tiny. Sec addresses this with extreme careful design and takes advantage of the limitations of Sensor Networks 27

References • http: //www. webopedia. com/quick_ref/OSI_L ayers. asp • http: //camars. kaist. ac. kr/~hyoon/courses/cs 7 10_2004_fall/rhoyo. ppt • http: //en. wikipedia. org/wiki/Block_cipher_m odes_of_operation#Cipherblock_chaining_. 28 CBC. 29 28