Tiny Sec A Link Layer Security Architecture for













- Slides: 29

Tiny. Sec: A Link Layer Security Architecture for Wireless Sensor Networks C. Karlof, N. Sastry, D. Wagner SPINS: Security Protocol for Sensor Networks A. Perrig, R. Szewczyk, V. Wen, D. Culler, J. D. Tygar

Sensor Networks n n Many important applications, e. g. , habitat monitoring, rescue operation, battle field monitoring Without adequate security, wide deployment might be impossible n n Severe energy, resource constraints Take advantage of the constraints n n Even a powerful adversary is limited to a small number of packets per unit time to inject or eavesdrop due to the limited wireless bandwidth, e. g. , 19. 2 Kbps Software implementation is possible

Motivation for Link Layer Security n End-to-end security, e. g. , SSH, SSL, or IPSec, in conventional networks n n n Message integrity is only checked at the destination Dominant traffic is end-to-end Dominant traffic is many-to-one in sensor networks n n Intermediate nodes need to access and aggregate data End-to-end security is subject to Do. S attacks n Relay a packet injected by an adversary wasting energy

Non-Issues n Denial of Service Attacks n n n Jamming Resource Consumption Attacks Wormhole attacks … Physical Tampering

Design Goals n Message authentication (integrity) n n MAC (Message Authentication Code): Secure checksum Confidentiality n Encryption n n Symmetric key system Tiny. Sec uses a network-wide master key and message authentication key SNEP of SPINS adopts a secret key between the base station and a sensor node Optional

Authenticity & Confidentiality: SNEP (Part of SPINS) n n Replay protection Semantic security n Encrypting the same plaintex twice should give two different cyphertexts n Use a unique IV (Initialization Vector) for each invocation of the encryption algorithm Weak freshness n Just order the messages, but cannot guarantee A is responding to B’s request Low communication overhead n Counter values kept at each end point; no need to include in each message

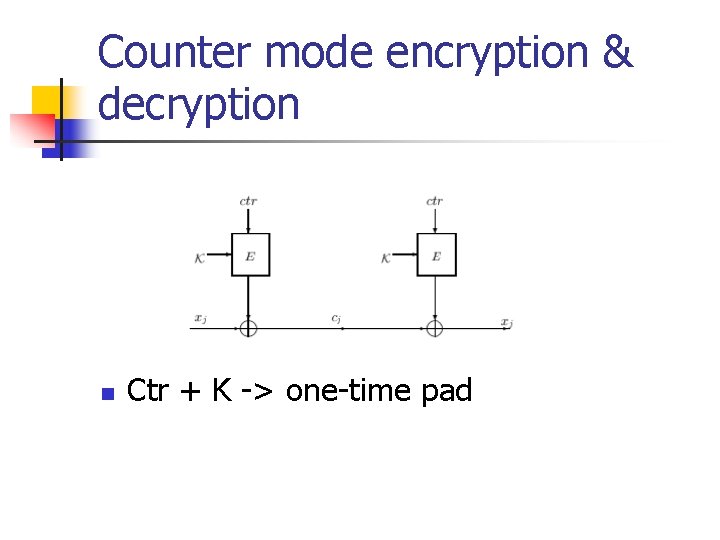
Counter mode encryption & decryption n Ctr + K -> one-time pad

CBC MAC n Same code for encryption & MAC n n Save storage Semantic security: IV, e. g. , counter, is not reused

Strong freshness n Strong freshness, e. g. , for counter synchronization

Tiny. Sec Design Goals n Efficiency n n Ease of Use n n n Minimal communication, computation & memory overhead 50% - 80% of 802. 11 networks without any cryptographic protection Tyny. Sec= true in the Makefile Right set of APIs Easy to use & customize considering the application needs Portability n Included in Tiny. OS (& TOSSIM) n Tiny. OS runs on a number of platforms including Texas Instruments, Atmel, Intel x 86, and Strong. Arm

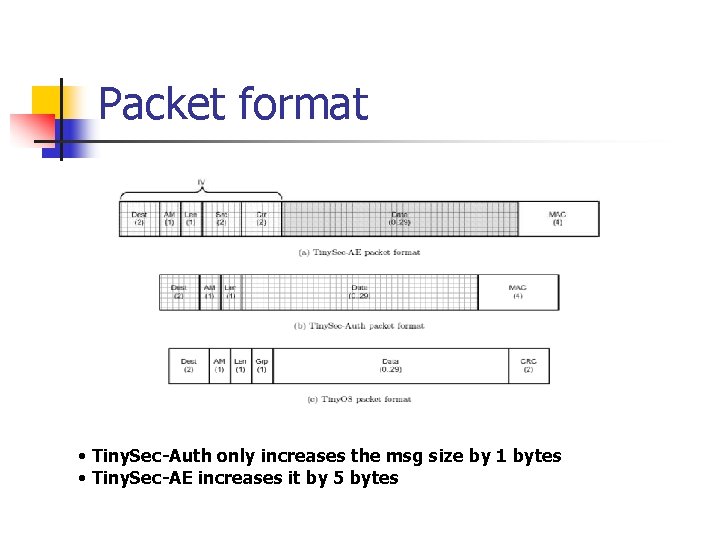
Tiny. Sec Design n Tiny. Sec-AE: Authenticated encryption n n Encrypt the payload and compute the MAC over the packet header and encrypted data Tiny. Sec-Auth: Authentication only n Authenticate the entire packet with a MAC, but the data is not encrypted

Packet format • Tiny. Sec-Auth only increases the msg size by 1 bytes • Tiny. Sec-AE increases it by 5 bytes

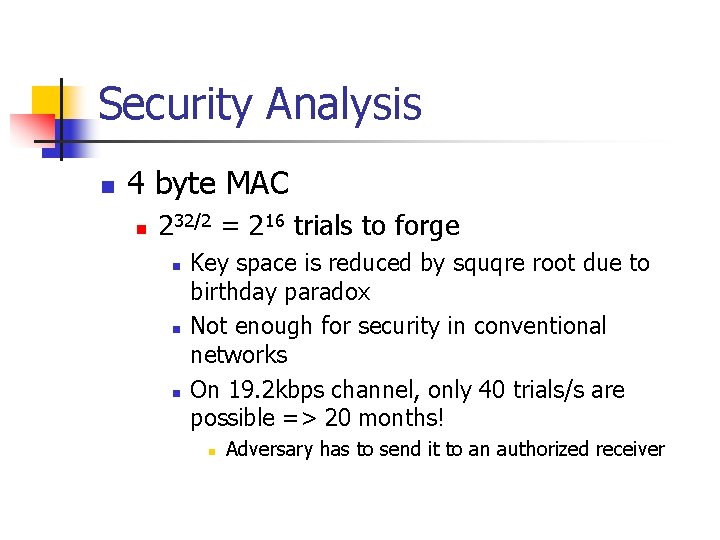
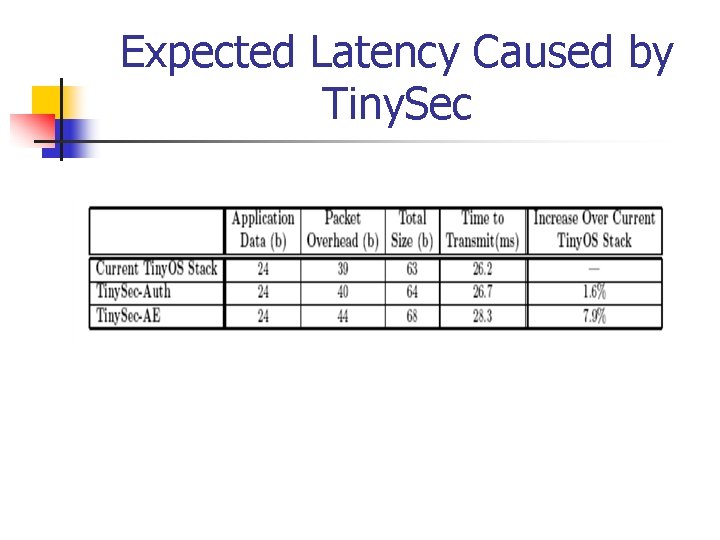
Security Analysis n 4 byte MAC n 232/2 = 216 trials to forge n n n Key space is reduced by squqre root due to birthday paradox Not enough for security in conventional networks On 19. 2 kbps channel, only 40 trials/s are possible => 20 months! n Adversary has to send it to an authorized receiver

n Confidentiality n n Counter If there are n nodes and 16 bit counter is used, an instance of IV is reused after n*216 packets n 19. 2 Kbps, one packet per minute per node n n IV is reused after 45 days Redistribute a new symmetric key

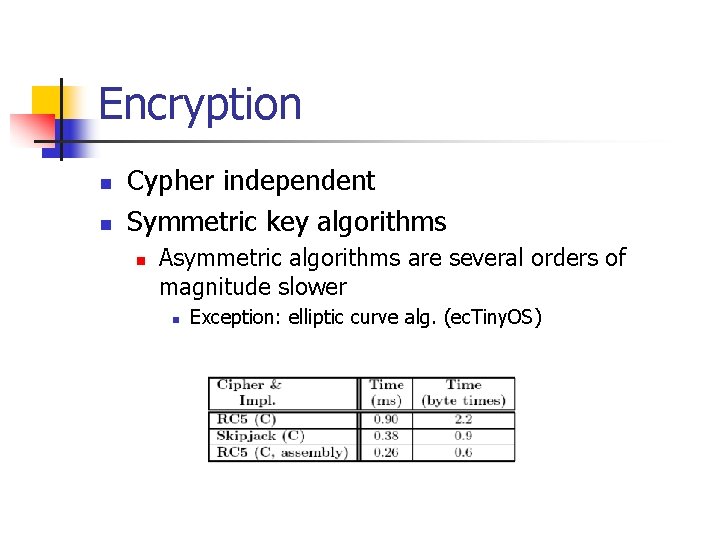
Encryption n n Cypher independent Symmetric key algorithms n Asymmetric algorithms are several orders of magnitude slower n Exception: elliptic curve alg. (ec. Tiny. OS)

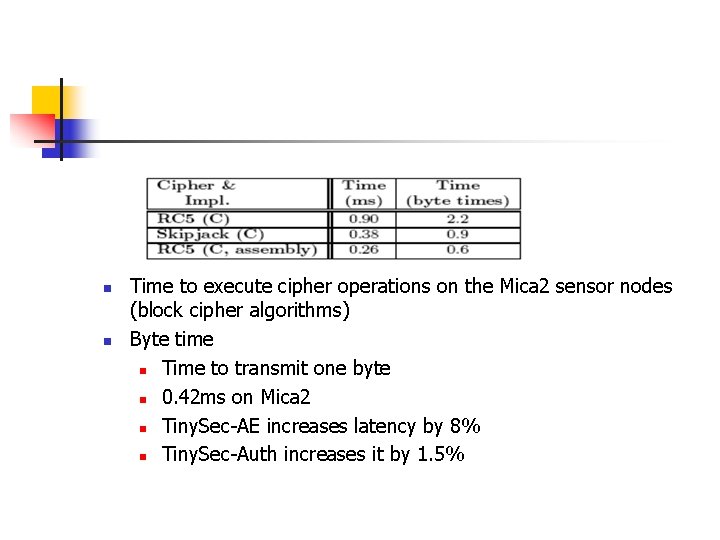
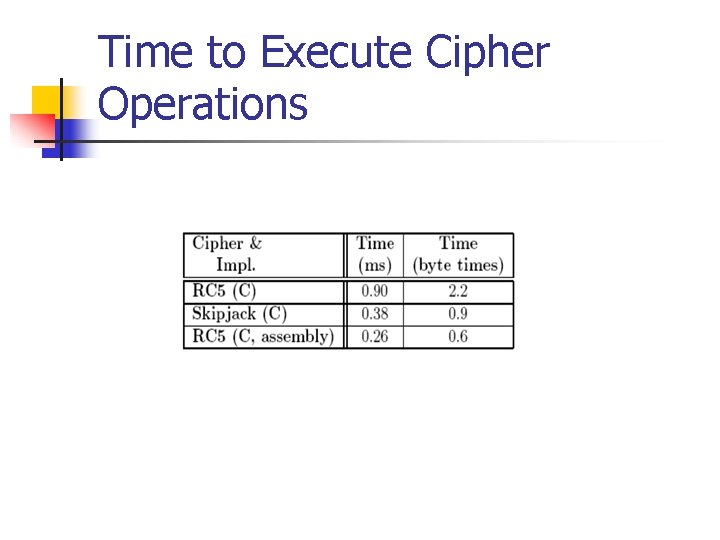
n n Time to execute cipher operations on the Mica 2 sensor nodes (block cipher algorithms) Byte time n Time to transmit one byte n 0. 42 ms on Mica 2 n Tiny. Sec-AE increases latency by 8% n Tiny. Sec-Auth increases it by 1. 5%

Keying Mechanism n n Determine how cryptographic keys are distributed and shared throughout the network Use different keys for different applications n n Network-wide keying n n n Simple Vulnerable to node capture Per-link keying n n Use separate keys for encryption and message authentication Graceful degradation in the presence of compromised nodes Key distribution protocol is needed Passive participation & local broadcast are impossible Per-group keying n n n Graceful degradation in the presence of compromised nodes Key distribution is required Supports passive participation & local broadcast

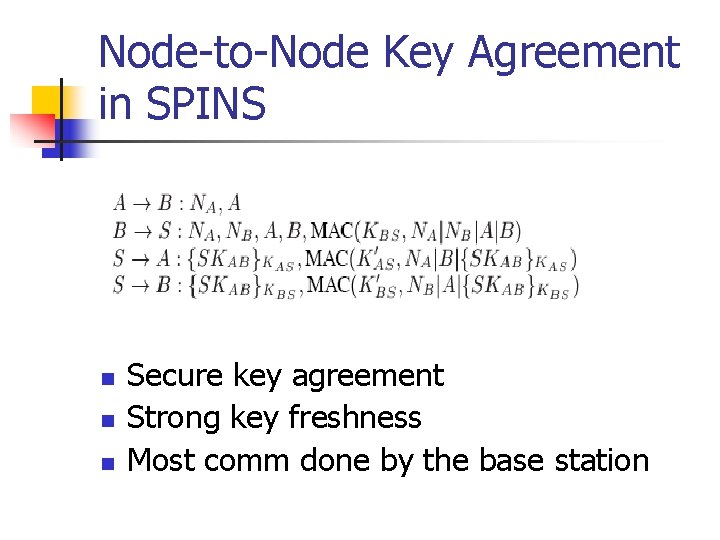
Node-to-Node Key Agreement in SPINS n n n Secure key agreement Strong key freshness Most comm done by the base station

Authenticated Broadcast in SPINS - u. TESLA n n Generally, authenticated broadcast requires an asymmetric mechanism Symmetric schemes are not secure n n Any receiver with the MAC key can impersonate Asymmetric schemes are too expensive n Requires 50 – 1000 bytes/packet for signature

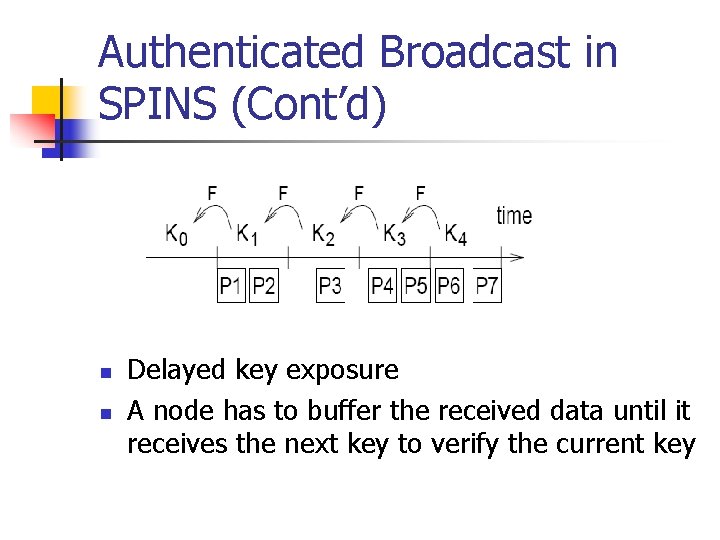
Authenticated Broadcast in SPINS (Cont’d) n n Delayed key exposure A node has to buffer the received data until it receives the next key to verify the current key

Authenticated Broadcast in SPINS (Cont’d) n n n Sender chooses the last key Kn randomly and generate successive keys by successively applying a one way function F, e. g. , MD 5 In time interval t, sender uses Kt to authenticate the message Sender releases Kt after intervals after the end of the time interval t

Implementation n n Tiny. Sec in 3000 lines of nes. C code Requires 728 bytes of RAM and 7146 bytes of program space n n n 256 bytes of RAM & 8152 bytes of ROM Modify Tiny. OS 1. 1. 2 radio stack to redirect byte level radio events to the Tiny. Sec. M module Modification of the scheduler n n n Signal Tiny. Sec. M when the MAC layer successfully acquires the channel Begin the cryptographic computations Assign high priority to cryptographic operations

Evaluation n Packet size increase n n Fixed Extra computation time & energy needed for cryptography n Vary depending on implementation

Expected Latency Caused by Tiny. Sec

Time to Execute Cipher Operations

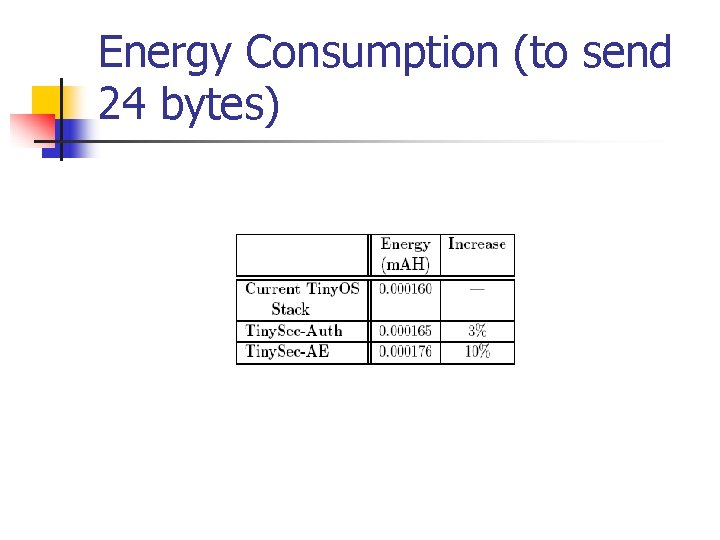
Energy Consumption (to send 24 bytes)

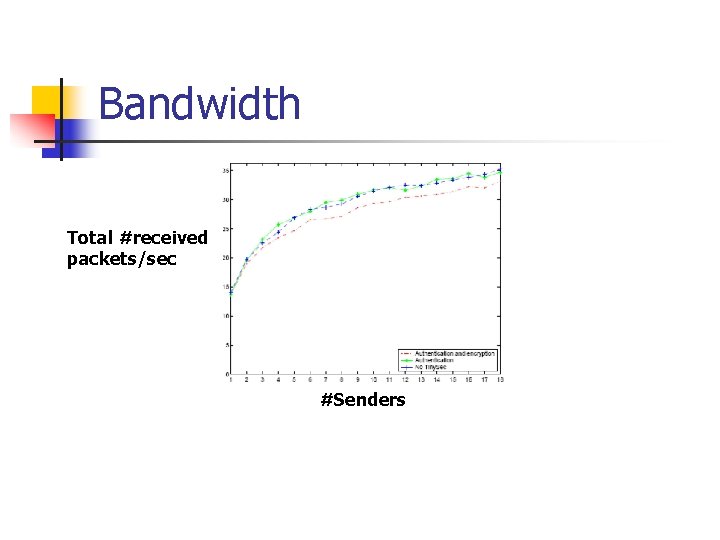
Bandwidth Total #received packets/sec #Senders

End-to-end latency E 2 E delay (ms) #hops

Questions?