Tiny Sec A Link Layer Security Architecture for















- Slides: 28

Tiny. Sec: A Link Layer Security Architecture for Wireless Sensor Networks Seetha Manickam Modified by Sarjana Singh

Overview Ø Motivation Ø Tiny. Sec-Introduction Ø Sensor Networks Security threats and Need for link layer security architecture design Ø Design goals Ø Tiny sec Design Ø Security Analysis of Tinysec Ø Performance Evaluation of Tiny Sec Ø Conclusion

Motivation • Sensor networks : Resource constraint networks – small memories, weak processors, limited energy. • Conventional security protocols (802. 11 b , 802. 15. 4 are found to be insecure , adds lot of overhead (16 -32 bytes) ). • Need for a new security architecture for sensor networks –TINYSEC.

TINYSEC • Light weight and efficient generic link layer security package. • Developers can easily integrate into sensor network applications. • A research platform that is easily extensible and has been incorporated into higher level protocols.

Security threats in Sensor Networks • Use of wireless communications -In a broadcast medium, adversaries can easily eavesdrop on, intercept, inject and alter transmitted data. • Adversaries can Interact with networks from a distance by expensive radio transceivers and powerful workstations. • Resource consumption attacks: Adversaries can repeatedly send packets to drain nodes battery and waste network bandwidth, can steal nodes. • However , these threats are not addressed. Focus is on guaranteeing message authenticity, integrity and confidentiality.

Motivation for Link layer security in Sensor Networks • End-End security Mechanisms : Suitable only for conventional networks using end-end communications where intermediate routers only need to view the message headers. • BUT, in Sensor networks In-network processing is done to avoid redundant messages-Requires intermediate nodes to have access to whole message packets and just not the headers as in conventional networks. . . contd. .

Motivation for Link layer security in Sensor Networks • Why end-end security mechanisms not suitable for sensor networks? • If message integrity checked only at the destination, the networks may route packets injected by an adversary many hops before they are detected. This will waste precious energy. • A link layer security mechanism can detect unauthorized packets when they are first injected onto the network.

Design Goals • Security Goals • Performance Goals • Usability Goals

Security Goals • A link layer security protocol should satisfy three basic security properties: • Access control and Message integrity -prevent unauthorized parties from participating • Confidentiality - keeping information secret form unauthorized parties • Explicit omission: Replay protection -an adversary eavesdropping a legitimate message sent between 2 authorized parties and replays it at a some time later

Performance goals • A system using cryptography will incur increased overhead in length of the message. • Increased message length results-decreased message throughput -increased latency -Increased Power Consumption( Sensor Networks )

Usability Goals • Security Platform- Higher level security protocols can use Tinysec to create secure pair wise communication between neighboring nodes. • To reduce the effort, Tiny. Sec should provide proper interfaces • Transparency- Should be transparent to the user • Portability- Should fit into the radio stack so that porting the radio stack from one platform to another is easy.

Security Primitives • Message Authentication code - A cryptographic checksum for checking the message integrity • Initialization vector (IV) -A side input to the encryption algorithm. - Provides Semantic Security

TINYSEC-DESIGN Two Security Options 1. Authentication Encryption (Tinysec-AE) 2. Authentication only (Tinysec-Au) • Encryption : Ø Specifying the IV format Ø Selecting an encryption Scheme( CBC)

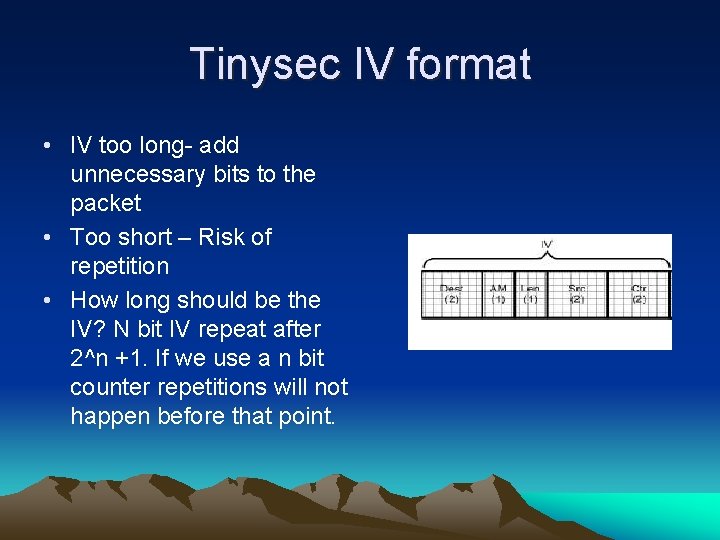
Tinysec IV format • IV too long- add unnecessary bits to the packet • Too short – Risk of repetition • How long should be the IV? N bit IV repeat after 2^n +1. If we use a n bit counter repetitions will not happen before that point.

Encryption schemes • CBC is the most appropriate scheme for sensor networks –why? • Works better with repeated IVs. • IVs can be pre encrypted for use since it is proved that CBS mode is highly secure with non repeated IVS. • One drawback- Message expansion • Use Cipher text stealing-Cipher text length=plaintext length

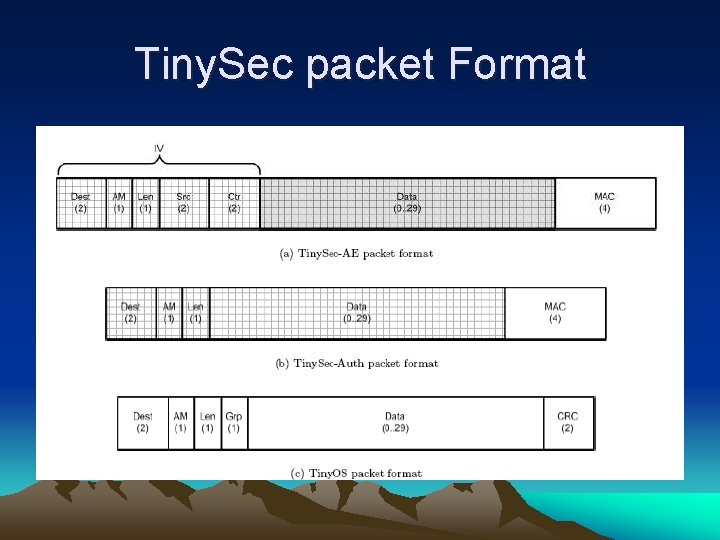
Tiny. Sec packet Format

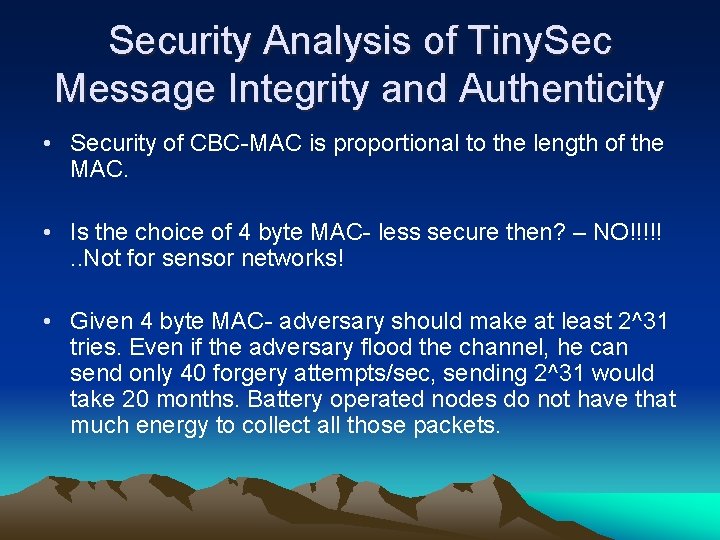
Security Analysis of Tiny. Sec Message Integrity and Authenticity • Security of CBC-MAC is proportional to the length of the MAC. • Is the choice of 4 byte MAC- less secure then? – NO!!!!!. . Not for sensor networks! • Given 4 byte MAC- adversary should make at least 2^31 tries. Even if the adversary flood the channel, he can send only 40 forgery attempts/sec, sending 2^31 would take 20 months. Battery operated nodes do not have that much energy to collect all those packets.

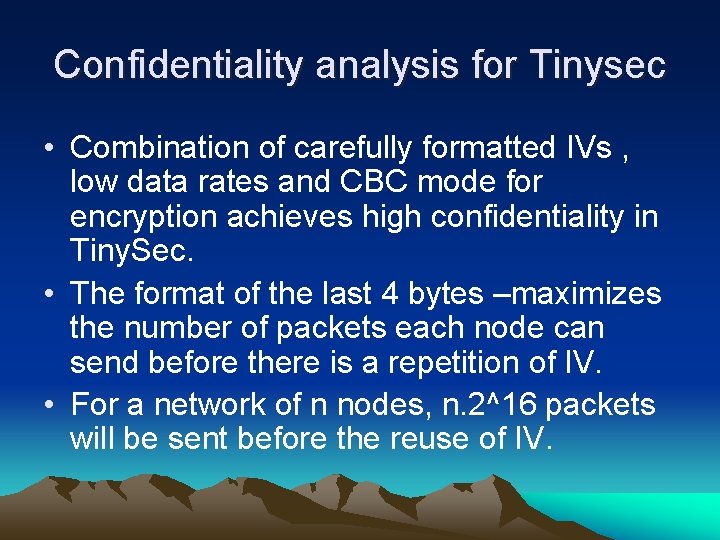
Confidentiality analysis for Tinysec • Combination of carefully formatted IVs , low data rates and CBC mode for encryption achieves high confidentiality in Tiny. Sec. • The format of the last 4 bytes –maximizes the number of packets each node can send before there is a repetition of IV. • For a network of n nodes, n. 2^16 packets will be sent before the reuse of IV.

Keying Mechanisms • Appropriate keying mechanism for a particular network depends on several factors. • Tinysec key- A pair of skipjack key-one for authentication, one or encryption. • Simplest keying mechanism: Use a single key for the entire network, Preload the key before deployment. -Adversary can compromise on node and get the key. .

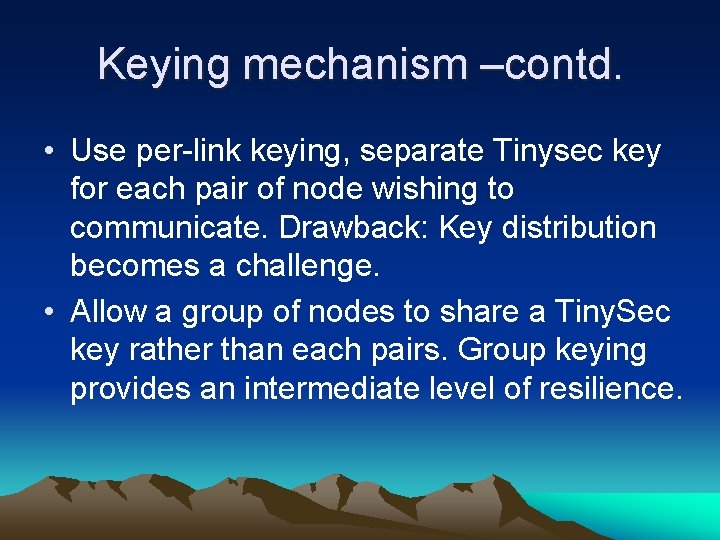
Keying mechanism –contd. • Use per-link keying, separate Tinysec key for each pair of node wishing to communicate. Drawback: Key distribution becomes a challenge. • Allow a group of nodes to share a Tiny. Sec key rather than each pairs. Group keying provides an intermediate level of resilience.

Implementation of Tiny. Sec • • Implemented on Berkeley sensor nodes. Integrated into TOSSIM simulator. 3000 lines of nes. C code. Tiny. OS 1. 1. 2 radio stack modified to incorporate Tiny. Sec. • Level of protection can be included in the data payload.

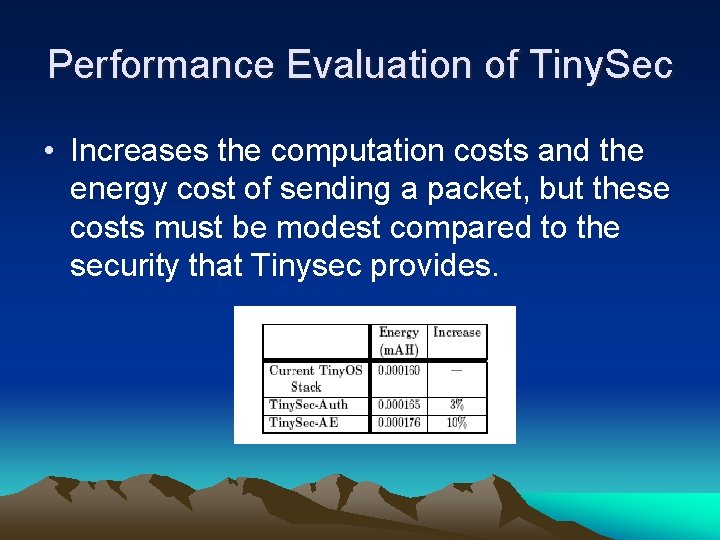
Performance Evaluation of Tiny. Sec • Increases the computation costs and the energy cost of sending a packet, but these costs must be modest compared to the security that Tinysec provides.

Cipher Performance

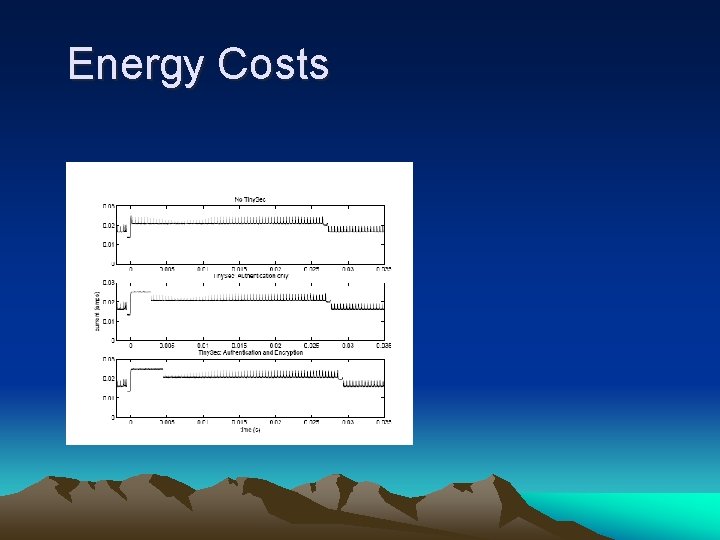
Energy Costs

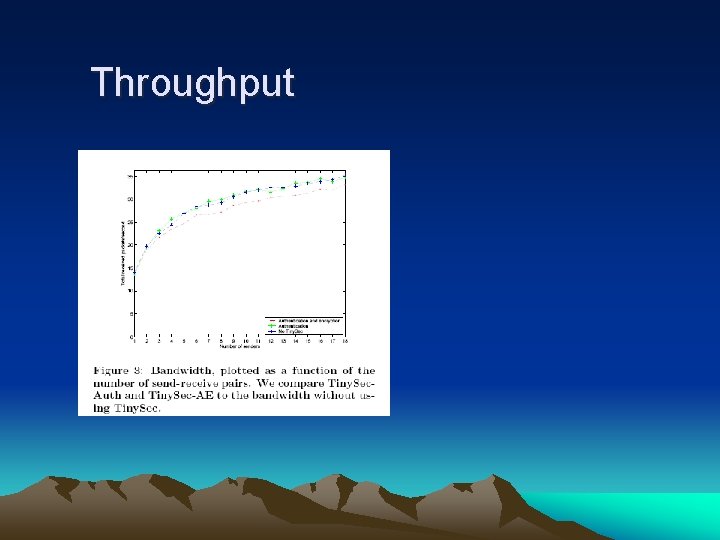
Throughput

Performance summary • The energy, bandwidth and latency overhead –all are less than 10% by using Tinysec. • Overhead-due to the increased packet size for cryptography. • Tinysec is very competitive with other solutions. • Tinysec has gathered a number of external users.

Conclusions • We have learnt that there are design vulnerabilities in the conventional protocols for sensor networks. • Conventional protocols tend to be conservative in their security guarantees, typically adding 16 -32 bytes of overhead. • Tinysec addresses these with extreme careful design and takes advantages of the limitations of sensor networks.

References Source : http: //www. ece. mtu. edu/ee/faculty/cchigan/EE 59 70 -Seminar/Tiny. Sec. ppt