Data Link Layer 1 Data Link Layer Functionality












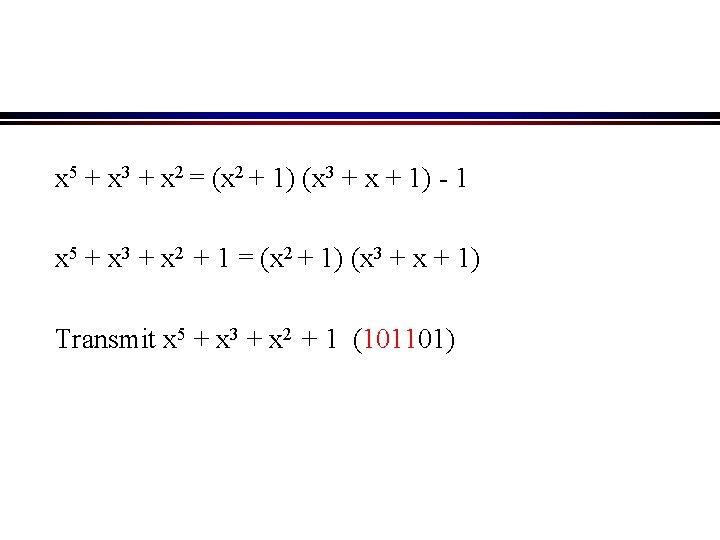
























- Slides: 96

Data Link Layer

1. Data Link Layer Functionality l Recall: n Frame creation n Error detection and/or correction n Flow control Creating the illusion of a reliable link

2. Modes of Operation Simplex l Half Duplex l Full Duplex l

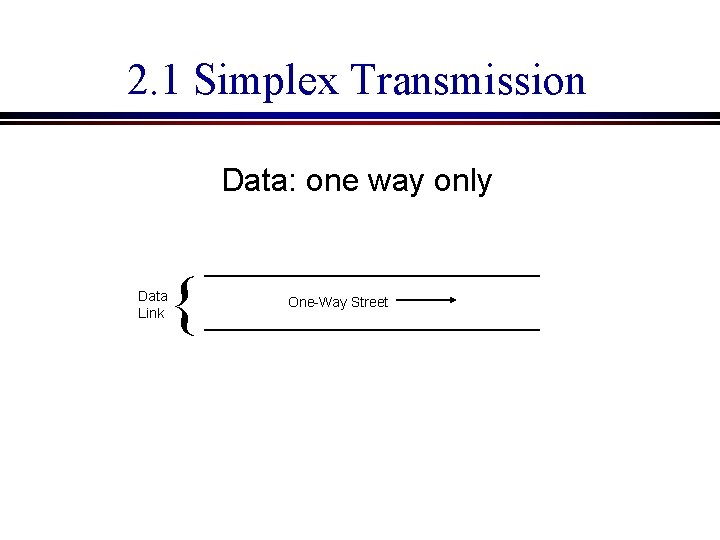
2. 1 Simplex Transmission Data: one way only Data Link { One-Way Street

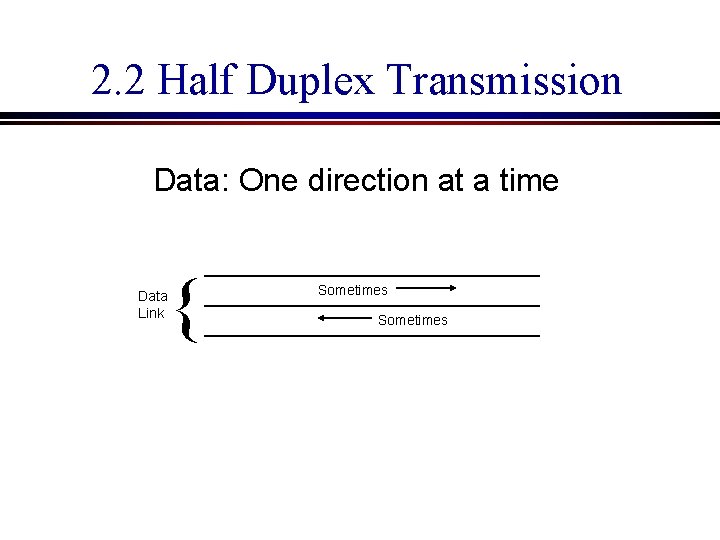
2. 2 Half Duplex Transmission Data: One direction at a time Data Link { Sometimes

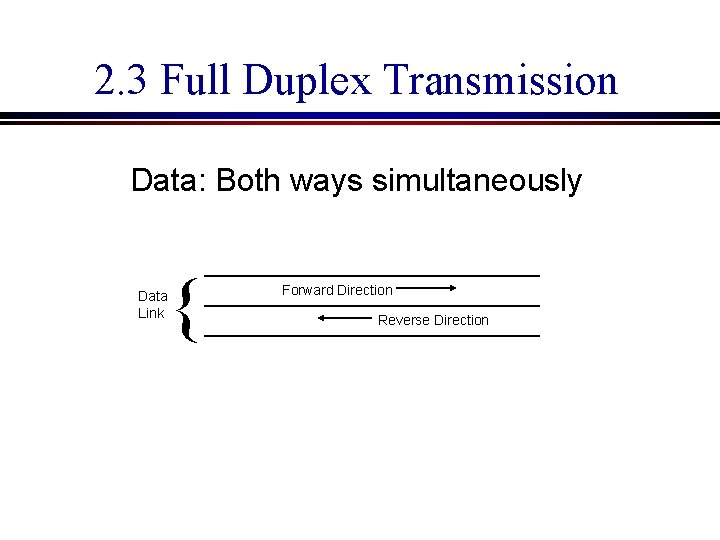
2. 3 Full Duplex Transmission Data: Both ways simultaneously Data Link { Forward Direction Reverse Direction

3. Framing The data unit at the data link layer is the “frame” l A frame is a group of bits, typically in sequence l Issues: l n Frame creation n Frame delineation

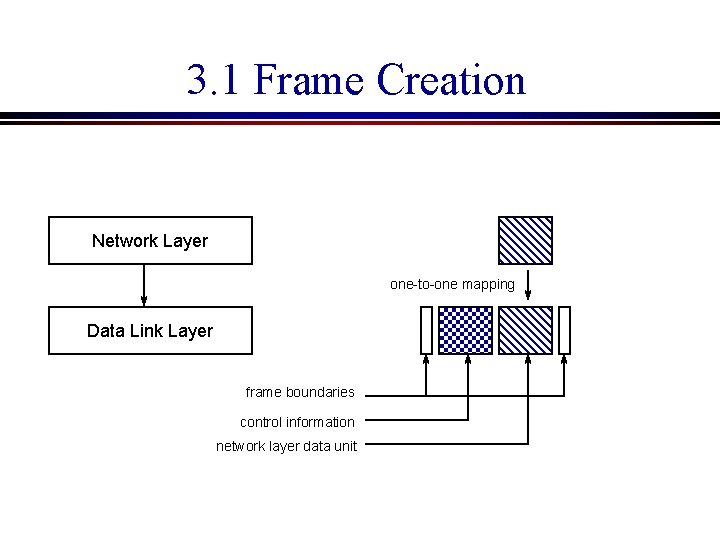
3. 1 Frame Creation Network Layer one-to-one mapping Data Link Layer frame boundaries control information network layer data unit

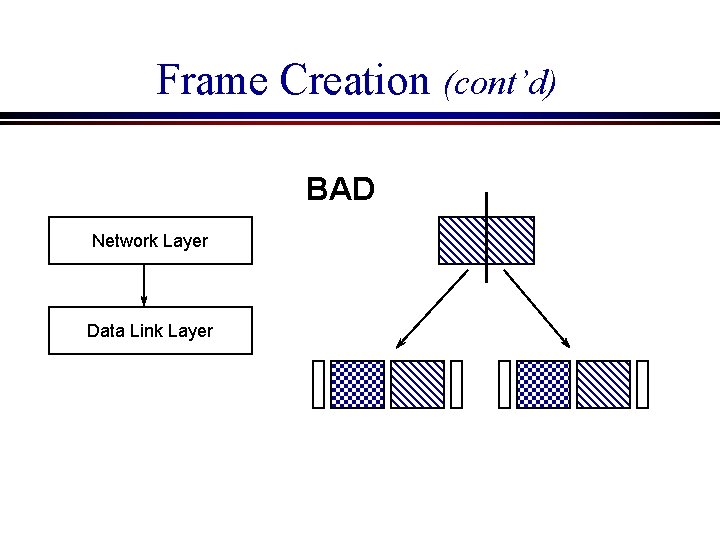
Frame Creation (cont’d) BAD Network Layer Data Link Layer

3. 2 Frame Delineation l How to tell when a new frame starts: n Character count n Frame tags with character stuffing n Frame tags with bit stuffing

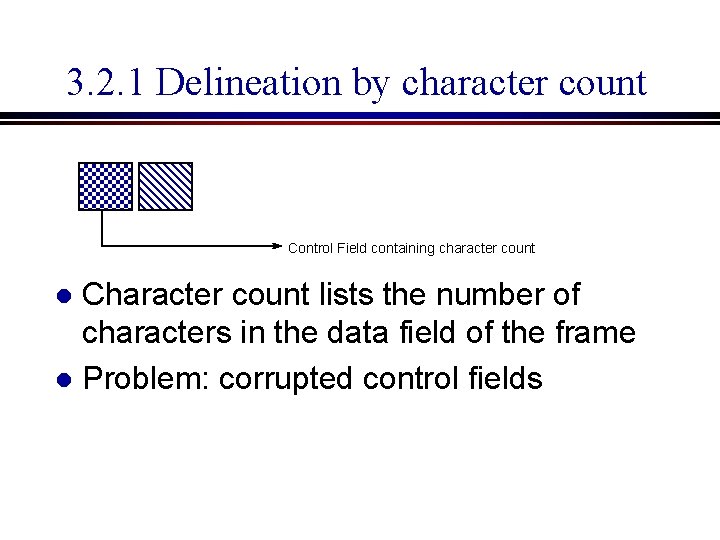
3. 2. 1 Delineation by character count Control Field containing character count Character count lists the number of characters in the data field of the frame l Problem: corrupted control fields l

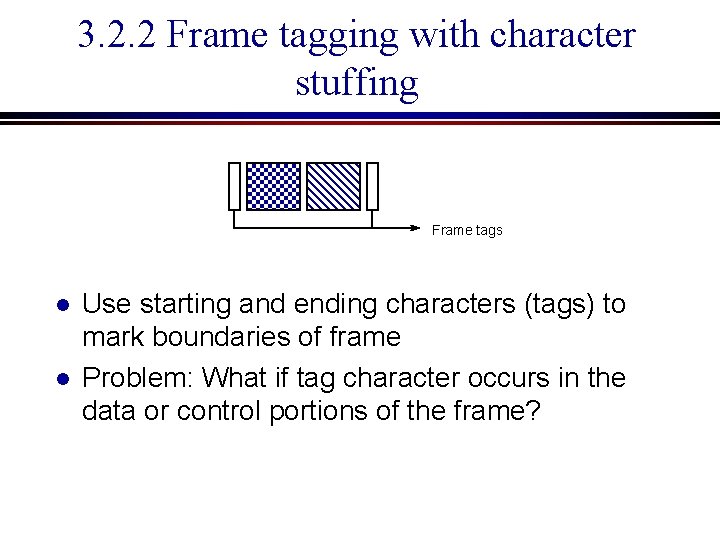
3. 2. 2 Frame tagging with character stuffing Frame tags l l Use starting and ending characters (tags) to mark boundaries of frame Problem: What if tag character occurs in the data or control portions of the frame?

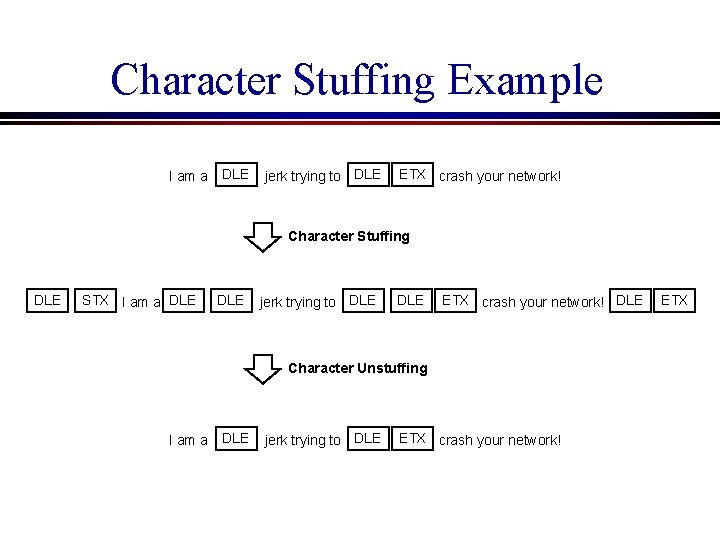
Character stuffing l Insert extra escape characters when a tag appears in data field DLE STX Start Tag DLE ETX End Tag DLE Character Stuffed DLE code

Character Stuffing Example I am a DLE jerk trying to DLE ETX crash your network! Character Stuffing DLE STX I am a DLE jerk trying to DLE ETX crash your network! DLE Character Unstuffing I am a DLE jerk trying to DLE ETX crash your network! ETX

3. 2. 3 Frame tagging with bit stuffing Bit strings may be used instead of character sequences to delineate frames l More efficient l

Bit stuffing Each frame begins with a start and end bit sequence, e. g. , 01111110 l When sender’s data link layer sees five 1’s in a row, it stuffs a zero bit l The receiver “unstuffs” a zero after five consecutive 1’s. l

Bit Stuffing Example 00110010111111100010100 Bit Stuffing 0111111000110010111110110001010001111110 Bit Unstuffing 00110010111111100010100

4. Error Control No physical link is perfect l Bits will be corrupted l We can either: l n detect errors and request retransmission n or correct errors without retransmission

4. 1 Error Detection Parity bits l Polynomial codes or checksums l

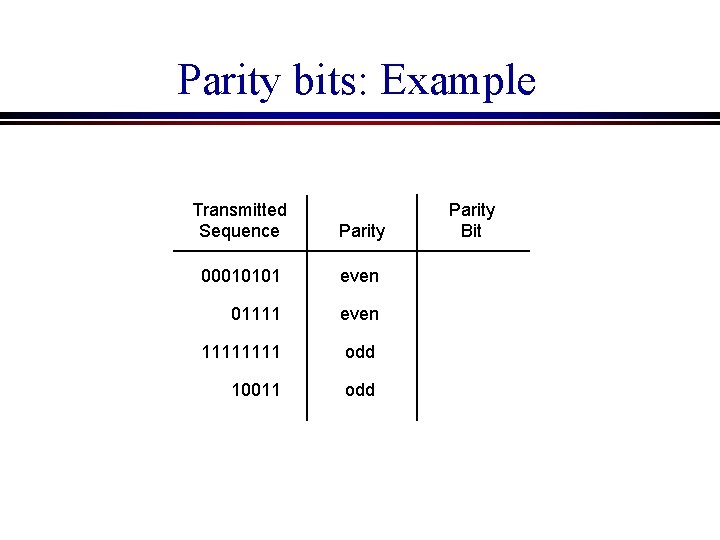
4. 1. 1 Parity bits Append a single parity bit to a sequence of bits l If using “odd” parity, the parity bit is chosen to make the total number of 1’s in the bit sequence odd. l If “even” parity, the parity bit makes the total number of 1’s in the bit sequence even l

Parity bits: Example Transmitted Sequence Parity 00010101 even 01111 even 1111 odd 10011 odd Parity Bit

Parity Bits Only detects when there an odd number of bit errors l Does not detect an even number of bit errors l It also has high overhead; it requires 1 extra bit for every several bits transmitted l

4. 1. 2 Polynomial Codes l l Can detect errors on large chunks of data Has low overhead More robust than parity bit Requires the use of a “code polynomial” n Example: x 2 + 1

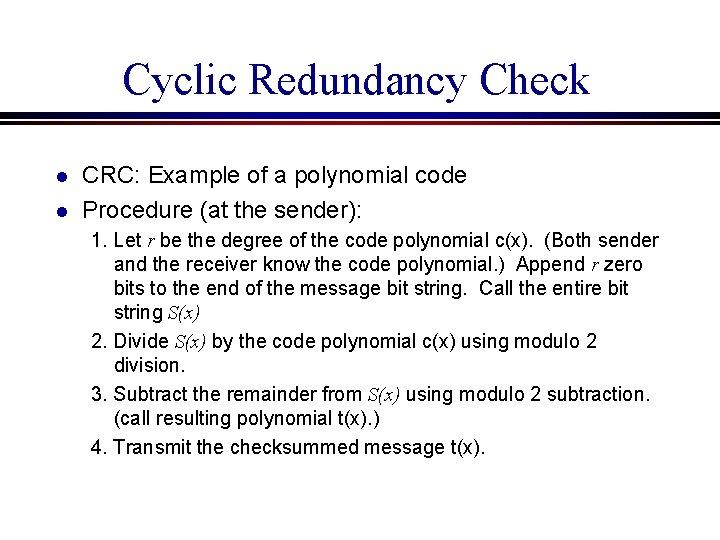
Cyclic Redundancy Check l l CRC: Example of a polynomial code Procedure (at the sender): 1. Let r be the degree of the code polynomial c(x). (Both sender and the receiver know the code polynomial. ) Append r zero bits to the end of the message bit string. Call the entire bit string S(x) 2. Divide S(x) by the code polynomial c(x) using modulo 2 division. 3. Subtract the remainder from S(x) using modulo 2 subtraction. (call resulting polynomial t(x). ) 4. Transmit the checksummed message t(x).

Background l l s(x) = f(x)c(x) + remainder s(x) - remainder = f(x)c(x) = t(x) sender transmits t(x) n note that t(x) is divisible by c(x) n if the received sequence at the receiver is not divisible by c(x), error has occurred n

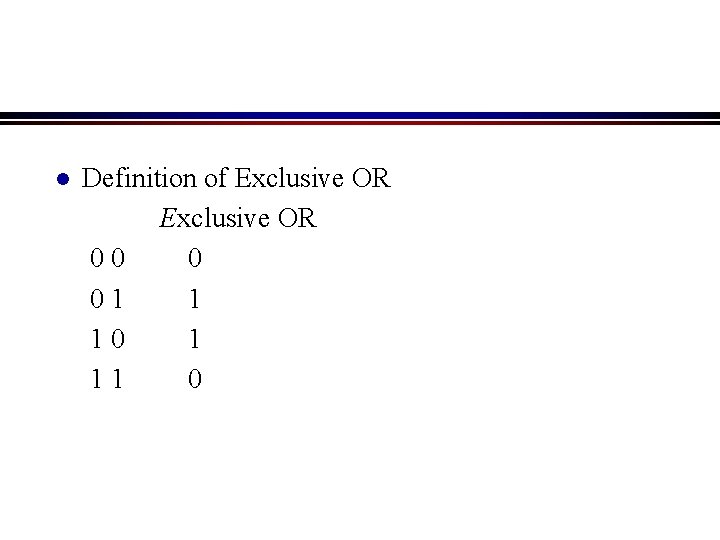
l Modulo 2 calculation Addition and subtraction are identical to EXCLUSIVE OR. No carries take mudulo 2 addition of 1010 and 0110 t(x) = 1 x x 3 + 0 x x 2 + 1 x x + 0 = x 3 + x + e(x) = 0 x x 3 + 1 x x 2 + 1 x x + 0 = x 2 + x 1 x x 3 + 1 x x 2 + 0 x x + 0 = x 3 + x 2 l

l Definition of Exclusive OR 00 0 01 1 10 1 11 0

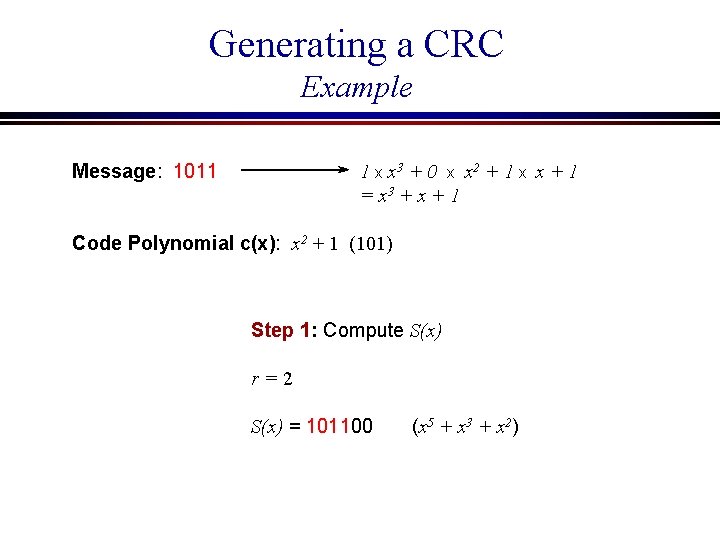
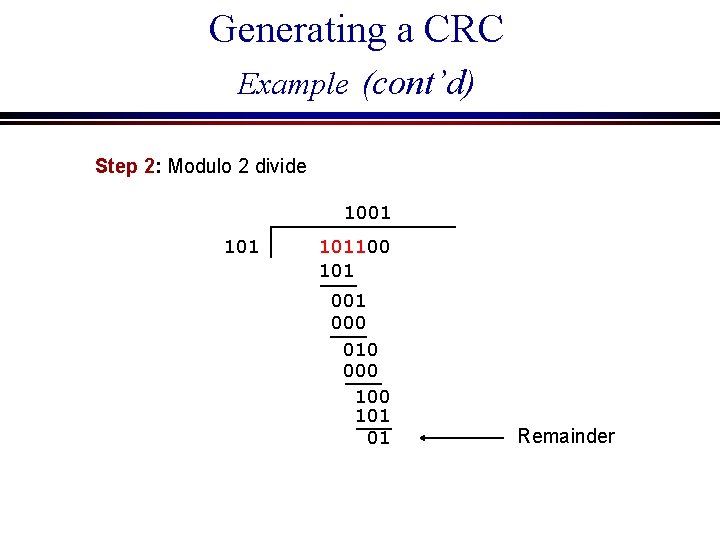
Generating a CRC Example Message: 1011 1 x x 3 + 0 x x 2 + 1 x x + 1 = x 3 + x + 1 Code Polynomial c(x): x 2 + 1 (101) Step 1: Compute S(x) r=2 S(x) = 101100 (x 5 + x 3 + x 2)

Generating a CRC Example (cont’d) Step 2: Modulo 2 divide 1001 101100 101 000 010 000 101 01 Remainder

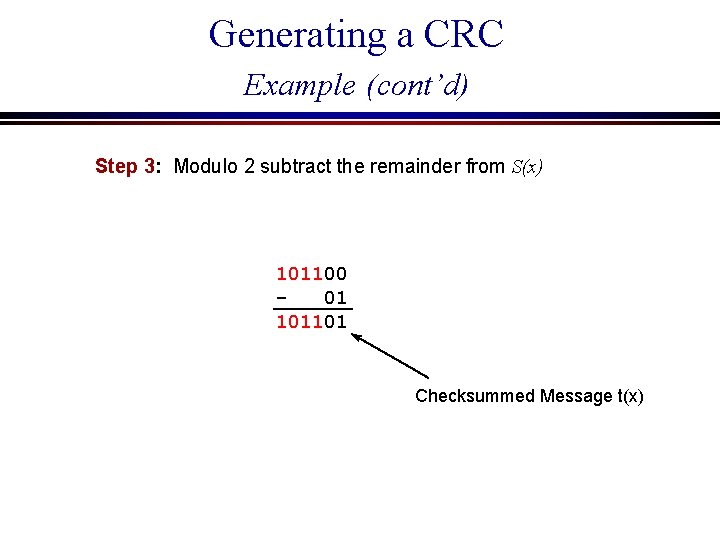
Generating a CRC Example (cont’d) Step 3: Modulo 2 subtract the remainder from S(x) 101100 01 101101 Checksummed Message t(x)
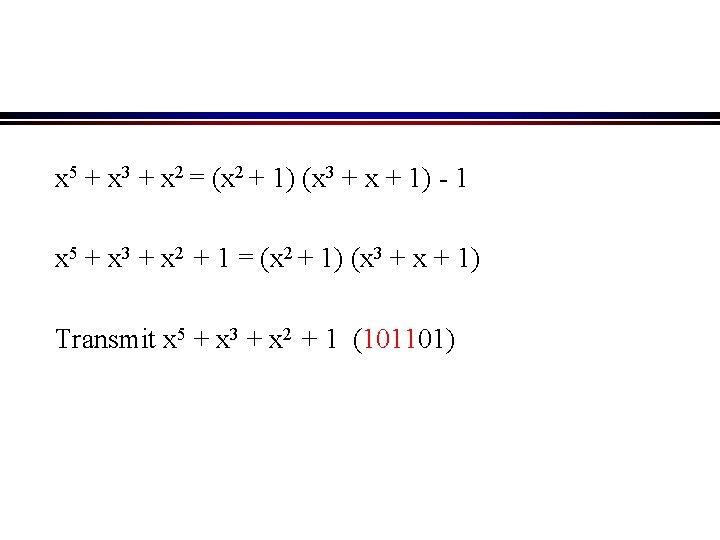
x 5 + x 3 + x 2 = (x 2 + 1) (x 3 + x + 1) - 1 x 5 + x 3 + x 2 + 1 = (x 2 + 1) (x 3 + x + 1) Transmit x 5 + x 3 + x 2 + 1 (101101)

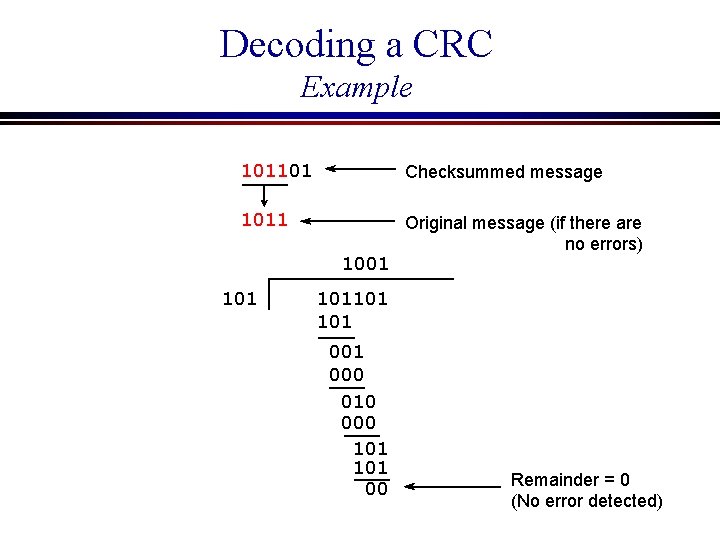
Decoding a CRC l Procedure (at the receiver) n Divide the received message by the code polynomial c(x) using modulo 2 division. If the remainder is zero, there is no error detected.

Decoding a CRC Example 101101 Checksummed message 1011 Original message (if there are no errors) 1001 101101 001 000 010 000 101 00 Remainder = 0 (No error detected)

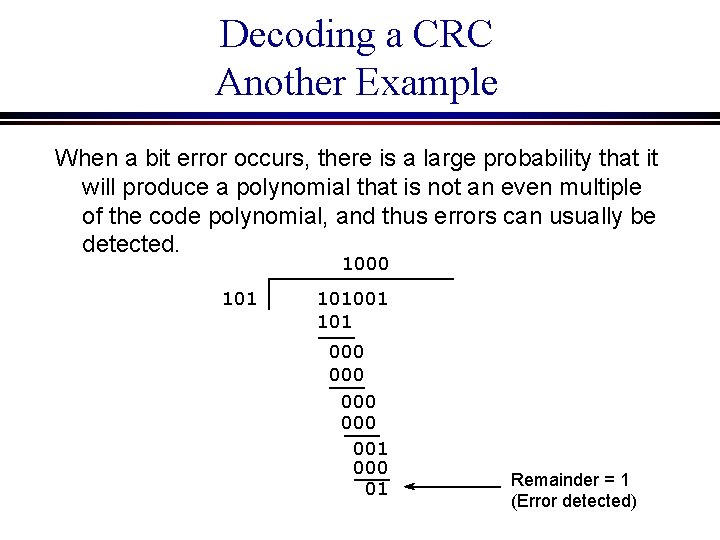
Decoding a CRC Another Example When a bit error occurs, there is a large probability that it will produce a polynomial that is not an even multiple of the code polynomial, and thus errors can usually be detected. 1000 101001 101 000 000 001 000 01 Remainder = 1 (Error detected)

Assume errors occurred, and the receiver received t(x) + e(x). l Receiver calculates [t(x) + e(x)]/c(x). l n t(x)/c(x); divisible (remainder of zero) n e(x)/c(x); if errors (e(x)) correspond to polynomials containing c(x) as a factor, this will result zero remainder. (These errors are not detected. ) All the other errors are detected.

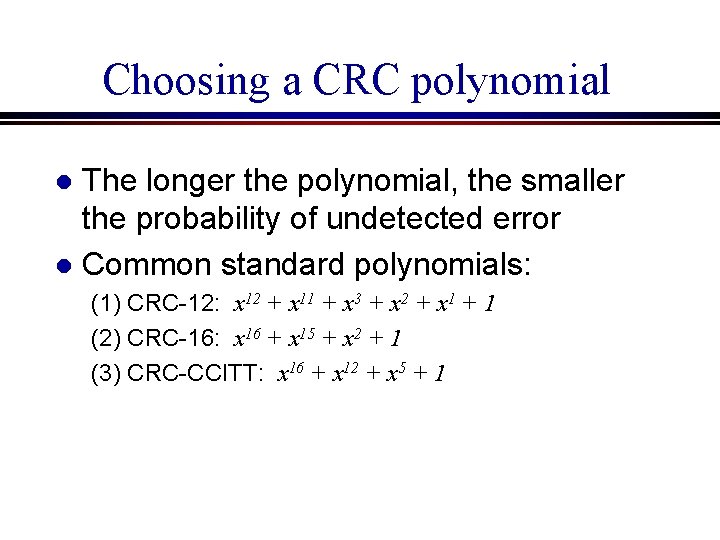
Choosing a CRC polynomial The longer the polynomial, the smaller the probability of undetected error l Common standard polynomials: l (1) CRC-12: x 12 + x 11 + x 3 + x 2 + x 1 + 1 (2) CRC-16: x 16 + x 15 + x 2 + 1 (3) CRC-CCITT: x 16 + x 12 + x 5 + 1

4. 2 Error Correction Parity bits and polynomial codes catch errors, but can we correct them without retransmitting information? l Yes, using Hamming Codes l

Hamming Codes Hamming codes, like polynomial codes, are appended to the transmitted message l Hamming codes, unlike polynomial codes, contain the information necessary to locate a single bit error l

Calculating a Hamming Code l Procedure: Place message bits in their non-power-of-two Hamming positions n Build a table listing the binary representation each of the message bit positions n Calculate the check bits n

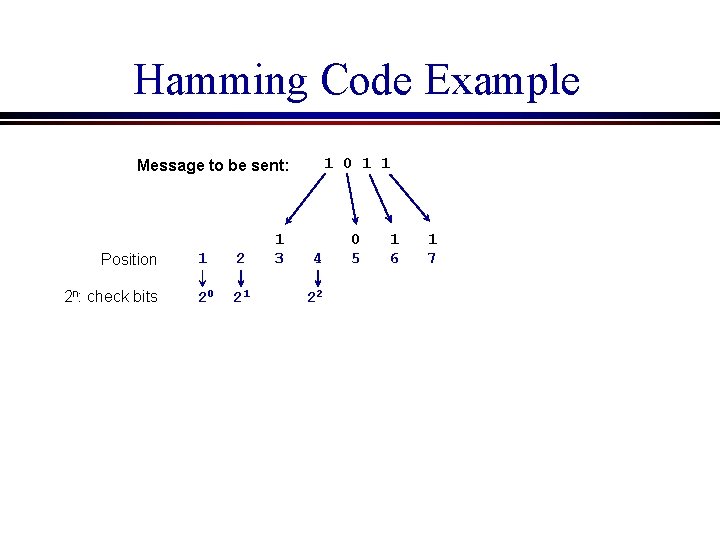
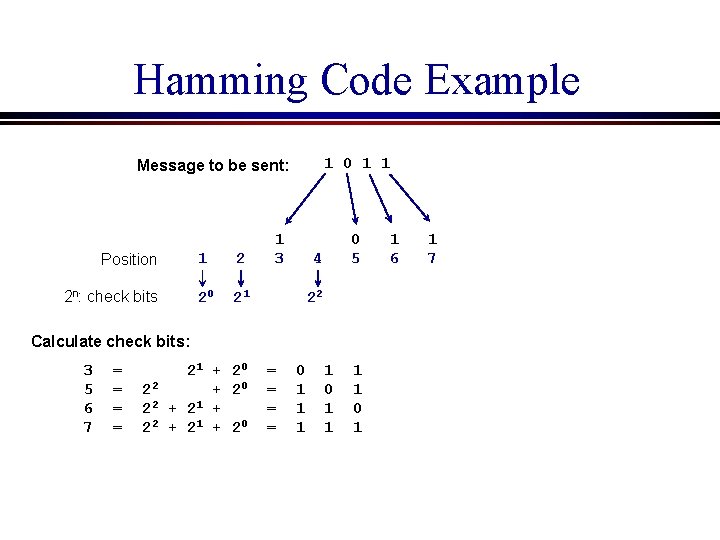
Hamming Code Example 1 0 1 1 Message to be sent: Position 2 n: check bits 1 2 20 21 1 3 4 22 0 5 1 6 1 7

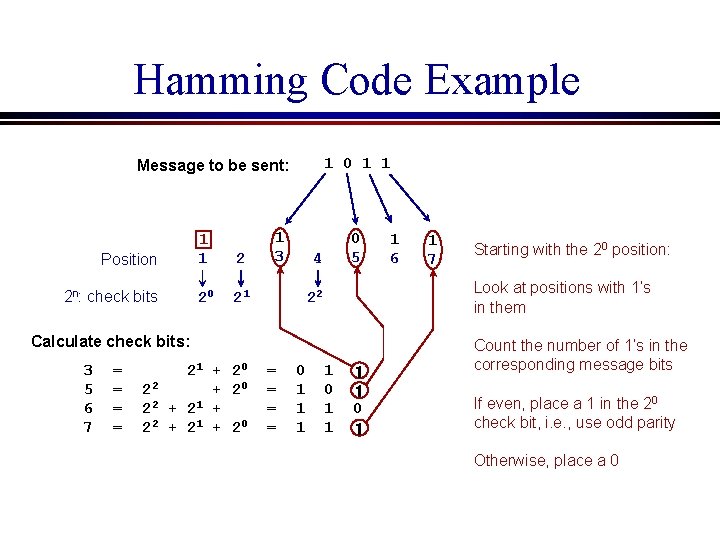
Hamming Code Example 1 0 1 1 Message to be sent: Position 2 n: check bits 1 2 20 21 1 3 0 5 4 22 Calculate check bits: 3 5 6 7 = = 21 + 20 22 + 20 2 2 + 21 + 20 = = 0 1 1 1 1 0 1 1 6 1 7

Hamming Code Example 1 0 1 1 Message to be sent: Position 2 n: check bits 1 1 2 20 21 1 3 0 5 4 = = 21 + 20 22 + 20 2 2 + 21 + 20 = = 0 1 1 7 Starting with the 20 position: Look at positions with 1’s in them 22 Calculate check bits: 3 5 6 7 1 6 1 0 1 1 1 1 0 1 1 Count the number of 1’s in the corresponding message bits If even, place a 1 in the 20 check bit, i. e. , use odd parity Otherwise, place a 0

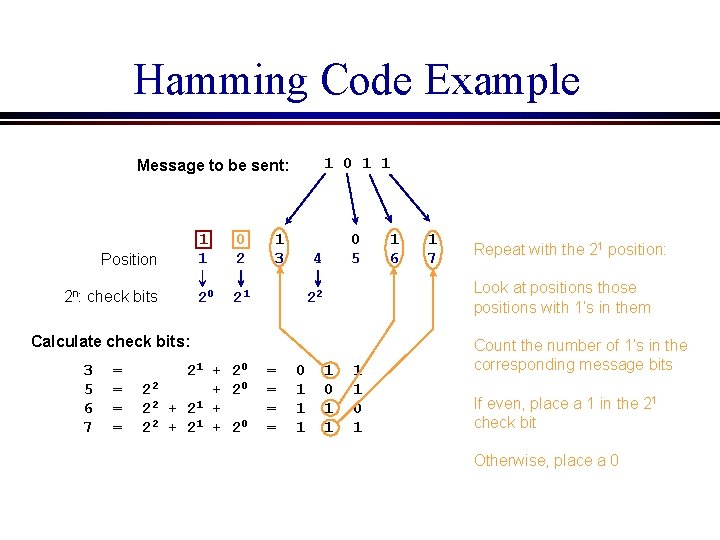
Hamming Code Example 1 0 1 1 Message to be sent: Position 2 n: check bits 1 1 0 2 20 21 1 3 0 5 4 = = 21 + 20 22 + 20 2 2 + 21 + 20 = = 0 1 1 7 Repeat with the 21 position: Look at positions those positions with 1’s in them 22 Calculate check bits: 3 5 6 7 1 6 1 0 1 Count the number of 1’s in the corresponding message bits If even, place a 1 in the 21 check bit Otherwise, place a 0

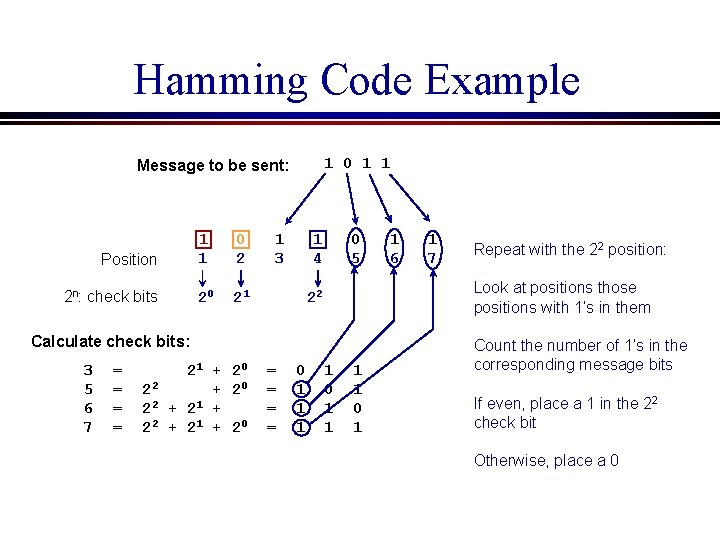
Hamming Code Example 1 0 1 1 Message to be sent: Position 2 n: check bits 1 1 0 2 20 21 1 4 1 3 0 5 = = 21 + 20 22 + 20 2 2 + 21 + 20 = = 0 1 1 7 Repeat with the 22 position: Look at positions those positions with 1’s in them 22 Calculate check bits: 3 5 6 7 1 6 1 0 1 Count the number of 1’s in the corresponding message bits If even, place a 1 in the 22 check bit Otherwise, place a 0

Hamming Code Example Original message = 1011 Sent message = 1011011 Now, how do we check for a single-bit error in the sent message using the Hamming code?

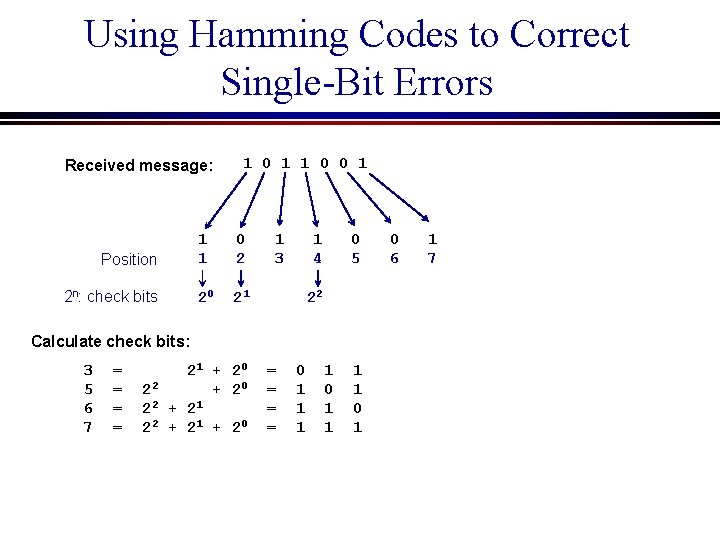
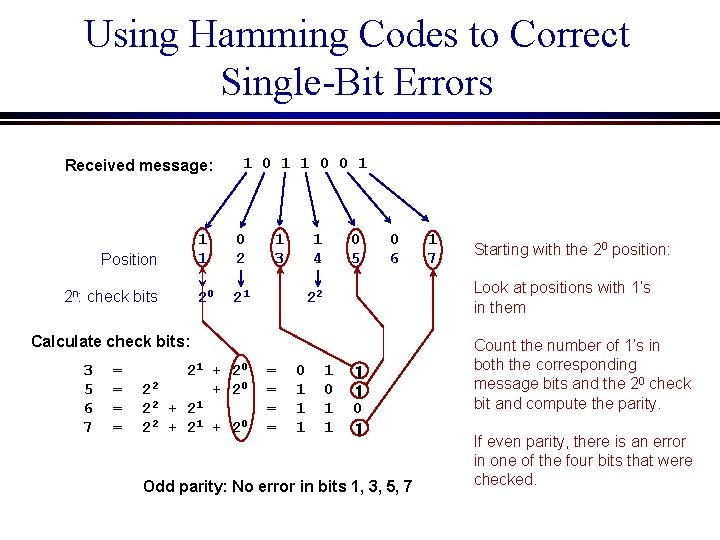
Using Hamming Codes to Correct Single-Bit Errors Received message: Position 2 n: check bits 1 0 1 1 0 0 1 1 1 0 2 20 21 1 3 1 4 0 5 22 Calculate check bits: 3 5 6 7 = = 21 + 20 22 + 20 2 2 + 21 + 20 = = 0 1 1 1 1 0 1 0 6 1 7

Using Hamming Codes to Correct Single-Bit Errors Received message: Position 2 n: check bits 1 0 1 1 0 0 1 1 1 0 2 20 21 1 3 1 4 0 5 0 6 = = 21 + 20 22 + 20 2 2 + 21 + 20 = = 0 1 1 1 Starting with the 20 position: Look at positions with 1’s in them 22 Calculate check bits: 3 5 6 7 1 0 1 1 1 1 0 1 1 Odd parity: No error in bits 1, 3, 5, 7 Count the number of 1’s in both the corresponding message bits and the 20 check bit and compute the parity. If even parity, there is an error in one of the four bits that were checked.

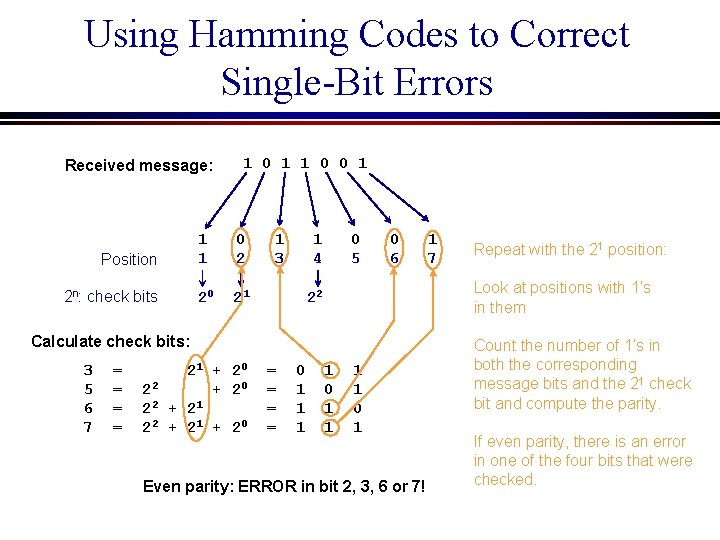
Using Hamming Codes to Correct Single-Bit Errors Received message: Position 2 n: check bits 1 0 1 1 0 0 1 1 1 0 2 20 21 1 3 1 4 0 5 0 6 = = 21 + 20 22 + 20 2 2 + 21 + 20 = = 0 1 1 1 Repeat with the 21 position: Look at positions with 1’s in them 22 Calculate check bits: 3 5 6 7 1 0 1 Even parity: ERROR in bit 2, 3, 6 or 7! Count the number of 1’s in both the corresponding message bits and the 21 check bit and compute the parity. If even parity, there is an error in one of the four bits that were checked.

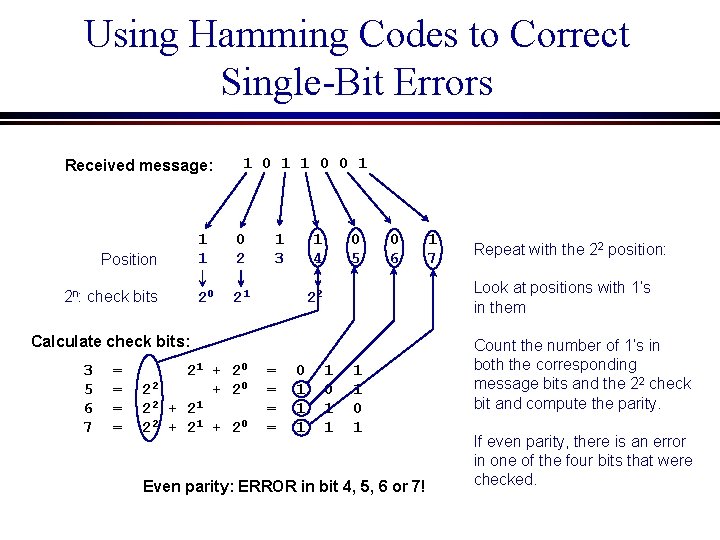
Using Hamming Codes to Correct Single-Bit Errors Received message: Position 2 n: check bits 1 0 1 1 0 0 1 1 1 0 2 20 21 1 3 1 4 0 5 0 6 = = 21 + 20 22 + 20 2 2 + 21 + 20 = = 0 1 1 1 Repeat with the 22 position: Look at positions with 1’s in them 22 Calculate check bits: 3 5 6 7 1 0 1 Even parity: ERROR in bit 4, 5, 6 or 7! Count the number of 1’s in both the corresponding message bits and the 22 check bit and compute the parity. If even parity, there is an error in one of the four bits that were checked.

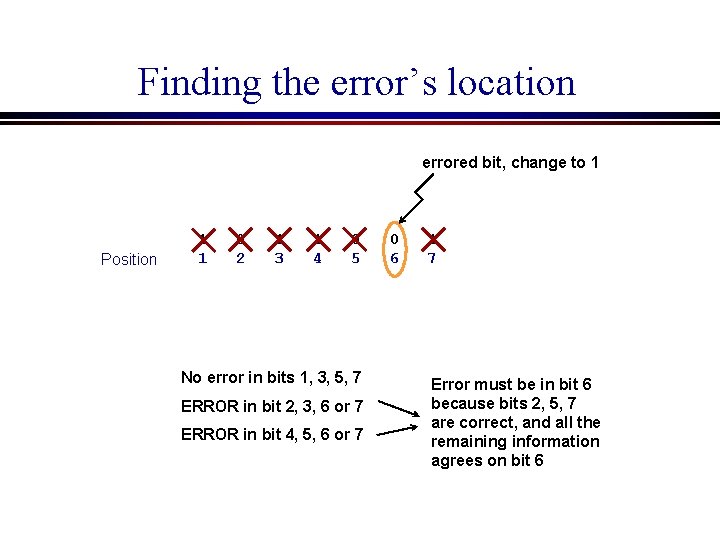
Finding the error’s location Position 1 1 0 2 1 3 1 4 0 5 0 6 1 7

Finding the error’s location Position 1 1 0 2 1 3 1 4 0 5 No error in bits 1, 3, 5, 7 0 6 1 7

Finding the error’s location errored bit, change to 1 Position 1 1 0 2 1 3 1 4 0 5 No error in bits 1, 3, 5, 7 ERROR in bit 2, 3, 6 or 7 ERROR in bit 4, 5, 6 or 7 0 6 1 7 Error must be in bit 6 because bits 2, 5, 7 are correct, and all the remaining information agrees on bit 6

Finding the error’s location An Easier Alternative to the Last Slide 3 5 6 7 = = 21 + 20 22 + 20 2 2 + 21 + 20 E = error in column NE = no error in column = = 0 1 1 1 1 0 1 E E NE 1 1 0 =6

Hamming Codes Hamming codes can be used to locate and correct a single-bit error l If more than one bit is in error, then a Hamming code cannot correct it l Hamming codes, like parity bits, are only useful on short messages l

5. Flow Control What happens if the sender tries to transmit faster than the receiver can accept? l Data will be lost unless flow control is implemented l

Controlling the Flow of Data Slow Joe Fast Frank

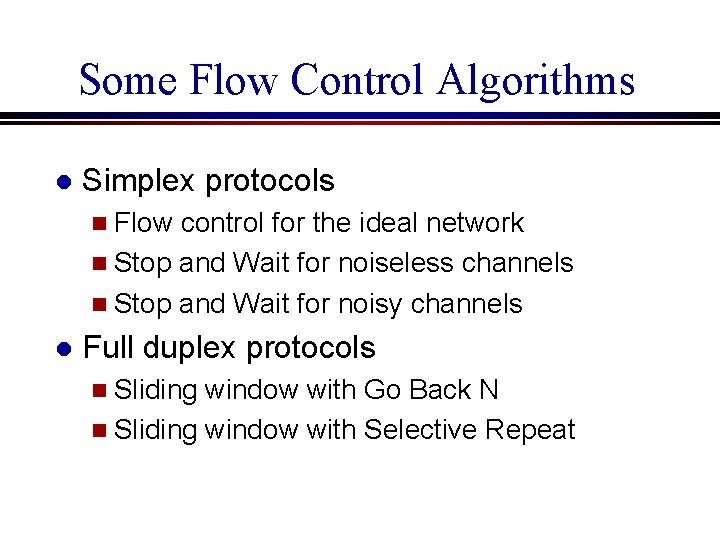
Some Flow Control Algorithms l Simplex protocols n Flow control for the ideal network n Stop and Wait for noiseless channels n Stop and Wait for noisy channels l Full duplex protocols n Sliding window with Go Back N n Sliding window with Selective Repeat

5. 1 Simplex Flow Control Data only flows in one direction l Acknowledgement stream may flow in the other direction l

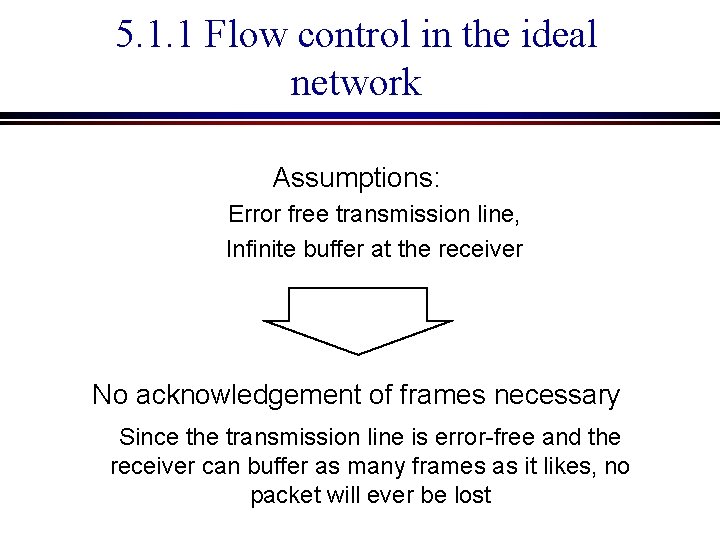
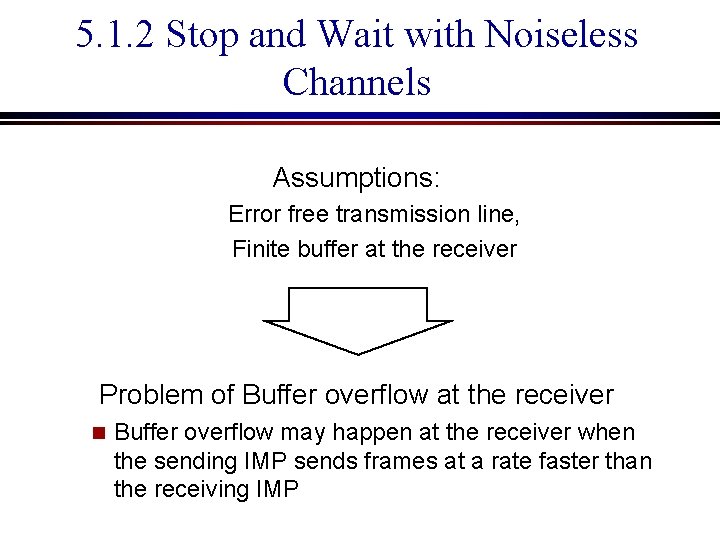
5. 1. 1 Flow control in the ideal network Assumptions: Error free transmission line, Infinite buffer at the receiver No acknowledgement of frames necessary Since the transmission line is error-free and the receiver can buffer as many frames as it likes, no packet will ever be lost

Flow control in the ideal network (cont’d) Slow Joe Fast Frank Infinite bucket

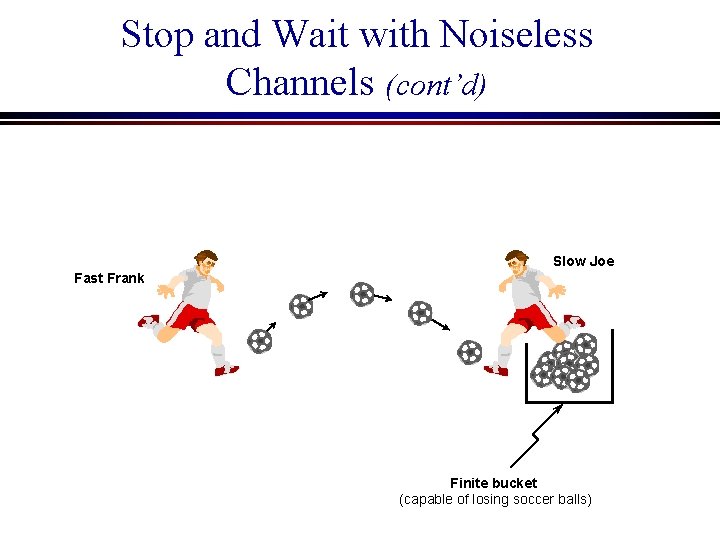
5. 1. 2 Stop and Wait with Noiseless Channels Assumptions: Error free transmission line, Finite buffer at the receiver Problem of Buffer overflow at the receiver n Buffer overflow may happen at the receiver when the sending IMP sends frames at a rate faster than the receiving IMP

Stop and Wait with Noiseless Channels (cont’d) Slow Joe Fast Frank Finite bucket (capable of losing soccer balls)

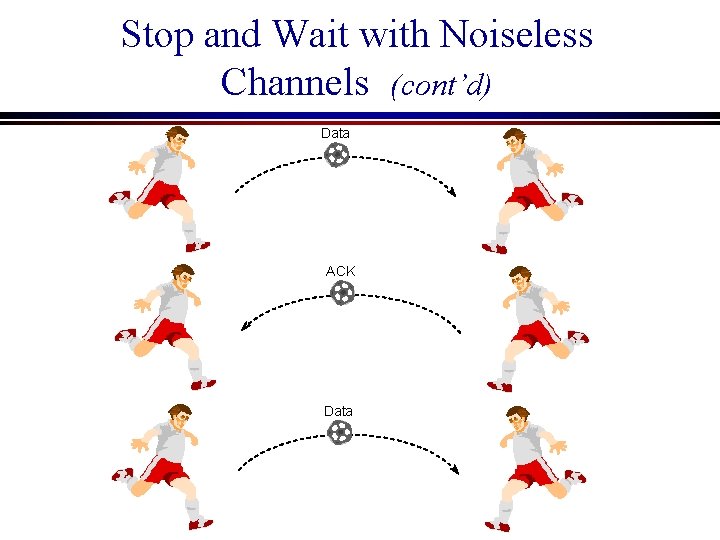
Stop and Wait with Noiseless Channels (cont’d) l Solution: Stop-and-Wait n The receiver sends an acknowledgement frame telling the sender to transmit the next data frame. n The sender waits for the ACK, and if the ACK comes, it transmits the next data frame.

Stop and Wait with Noiseless Channels (cont’d) Data ACK Data

Stop and Wait (cont’d) l l Note that we assume an error-free transmission line and hence, ACK frames will not be lost. In this protocol, there are two types of frames: data frames and ACK frames. The ACK frames don’t contain any particular information, since only the arrival of the ACK frame at the sender is important.

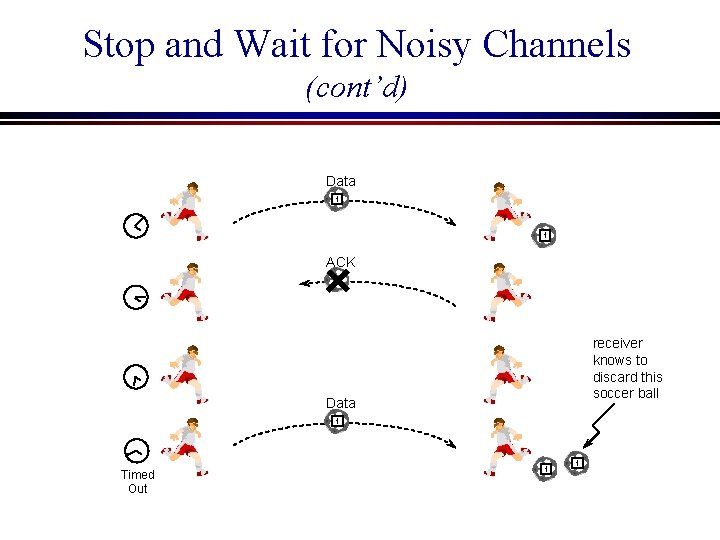
5. 1. 3 Stop and Wait for Noisy Channels Assumptions: Transmission line may cause errors, Finite buffer at the receiver ACK frames may now be lost

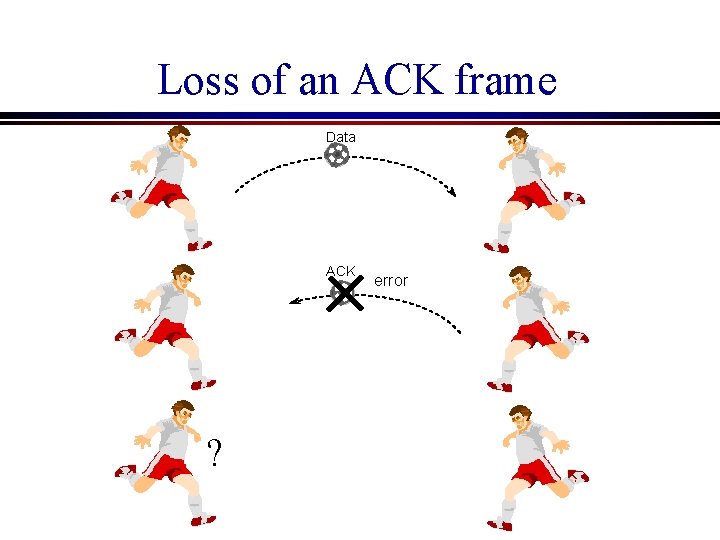
Problems introduced by a noisy line Problem 1: Loss of an ACK frame n Since the transmission line is not error-free, an ACK frame may be lost, causing the data sender to wait indefinitely

Loss of an ACK frame Data ACK ? error

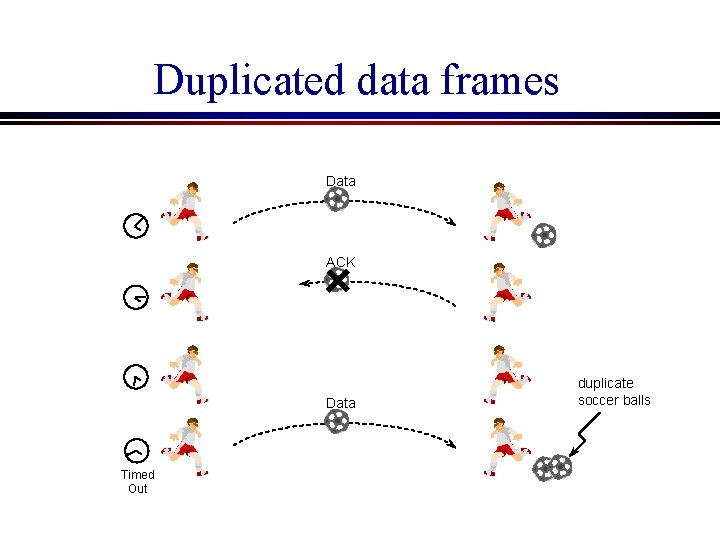
Problems introduced by a noisy line Can we solve problem 1 by introducing a timeout period for the sender? Yes, but. . . Problem 2: Duplicated frames n If the ACK frame for a certain data frame is lost, the sender will retransmit the same frame after a timeout period, and the receiver will then have two copies of the same frame

Duplicated data frames Data ACK Data Timed Out duplicate soccer balls

Stop and Wait for Noisy Channels (cont’d) l Solution: n The sender uses a timer to retransmit data frames when an ACK has not arrived n The sender includes a frame sequence number with each frame to distinguish one from another. Thus, the receiver knows when it has received duplicate frames.

Stop and Wait for Noisy Channels (cont’d) Data 1 1 ACK receiver knows to discard this soccer ball Data 1 Timed Out 1 1

5. 2 Full Duplex Flow Control Protocols Data frames are transmitted in both directions Sliding Window Flow Control Protocols

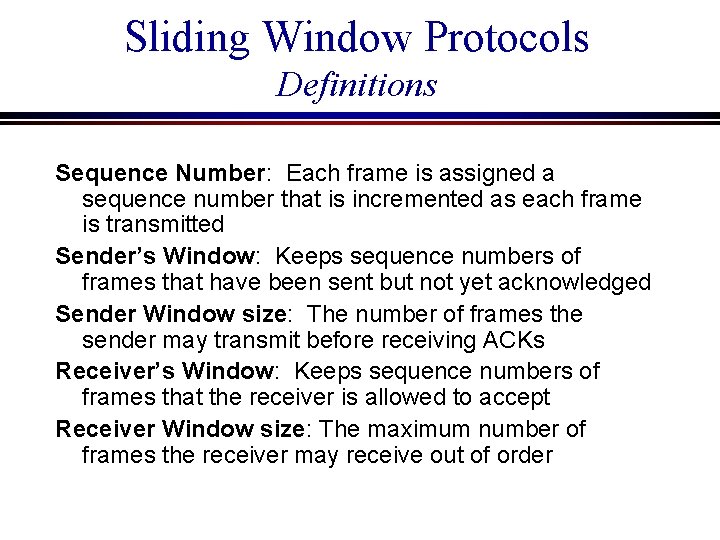
Sliding Window Protocols Definitions Sequence Number: Each frame is assigned a sequence number that is incremented as each frame is transmitted Sender’s Window: Keeps sequence numbers of frames that have been sent but not yet acknowledged Sender Window size: The number of frames the sender may transmit before receiving ACKs Receiver’s Window: Keeps sequence numbers of frames that the receiver is allowed to accept Receiver Window size: The maximum number of frames the receiver may receive out of order

Sliding Window Protocols General Remarks l The sending and receiving windows do not have to be the same size l Any frame which falls outside the receiving window is discarded at the receiver l Unlike the sender’s window, the receiver’s window always remains at its initial size

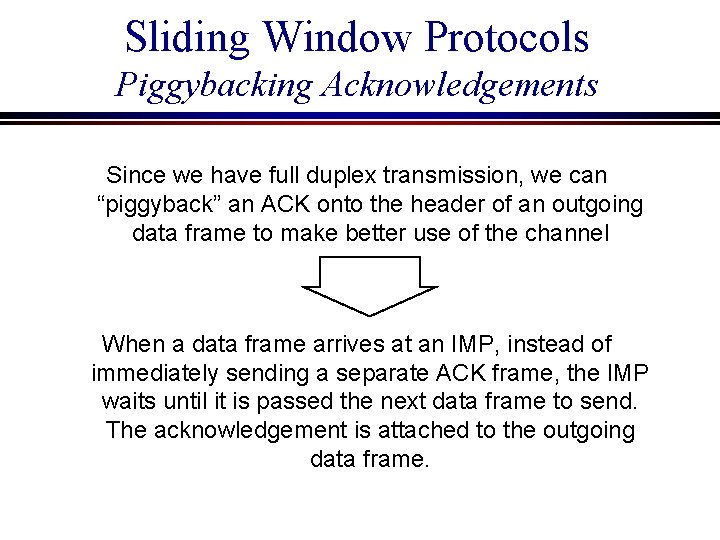
Sliding Window Protocols Piggybacking Acknowledgements Since we have full duplex transmission, we can “piggyback” an ACK onto the header of an outgoing data frame to make better use of the channel When a data frame arrives at an IMP, instead of immediately sending a separate ACK frame, the IMP waits until it is passed the next data frame to send. The acknowledgement is attached to the outgoing data frame.

5. 2. 1 Simple Sliding Window with Window Size of 1 A sliding window with a maximum window size of 1 frame 7 0 6 1 5 2 4 3 Window for a 3 -bit sequence number

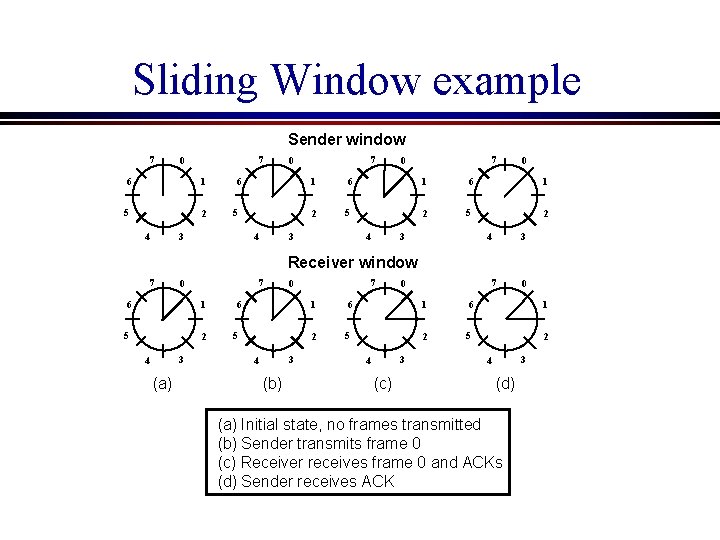
Sliding Window example Sender window 7 7 0 6 1 5 2 6 1 5 3 4 7 0 2 6 1 5 3 4 0 2 3 4 Receiver window 7 7 0 6 1 5 2 3 4 (a) 7 0 6 1 5 2 3 4 (b) 7 0 6 1 5 2 3 4 (c) 0 6 1 5 2 3 4 (d) (a) Initial state, no frames transmitted (b) Sender transmits frame 0 (c) Receiver receives frame 0 and ACKs (d) Sender receives ACK

Simple Sliding Window with Window size 1 (cont’d) This protocol behaves identically to stop and wait for a noisy channel

5. 2. 2 Sliding Window with Window Size W With a window size of 1, the sender waits for an ACK before sending another frame With a window size of W, the sender can transmit up to W frames before “being blocked” We call using larger window sizes Pipelining

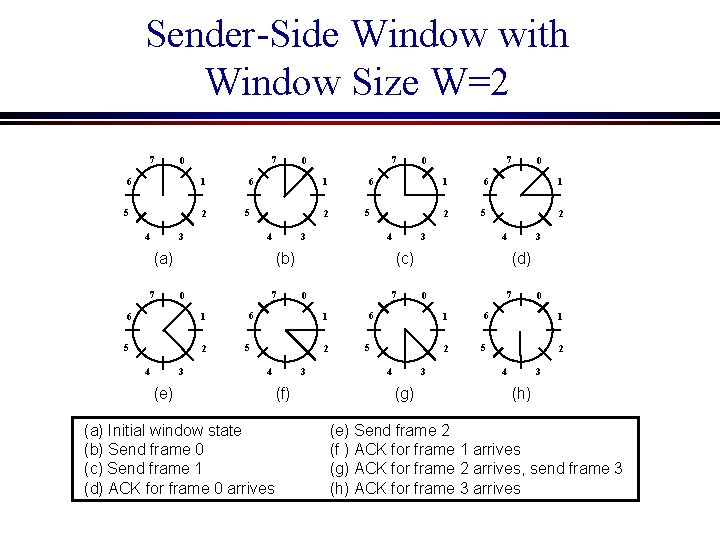
Sender-Side Window with Window Size W=2 7 7 0 6 1 5 2 6 1 5 3 4 2 6 7 1 5 2 3 4 1 5 2 6 7 1 5 2 3 4 (e) (a) Initial window state (b) Send frame 0 (c) Send frame 1 (d) ACK for frame 0 arrives (f) 1 5 2 (d) 7 0 6 1 5 2 3 4 (g) 3 4 (c) 0 0 6 3 4 (b) 0 7 0 6 3 4 (a) 7 7 0 0 6 1 5 2 3 4 (h) (e) Send frame 2 (f ) ACK for frame 1 arrives (g) ACK for frame 2 arrives, send frame 3 (h) ACK for frame 3 arrives

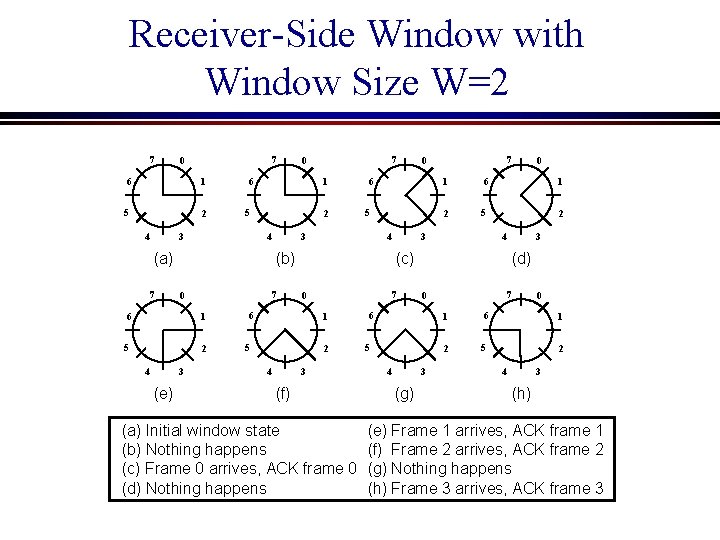
Receiver-Side Window with Window Size W=2 7 7 0 6 1 5 2 6 1 5 3 4 2 6 7 1 5 2 3 4 (e) 1 5 2 6 7 1 5 2 3 4 1 5 2 (f) (a) Initial window state (b) Nothing happens (c) Frame 0 arrives, ACK frame 0 (d) Nothing happens (d) 7 0 6 1 5 2 3 4 (g) 3 4 (c) 0 0 6 3 4 (b) 0 7 0 6 3 4 (a) 7 7 0 0 6 1 5 2 3 4 (h) (e) Frame 1 arrives, ACK frame 1 (f) Frame 2 arrives, ACK frame 2 (g) Nothing happens (h) Frame 3 arrives, ACK frame 3

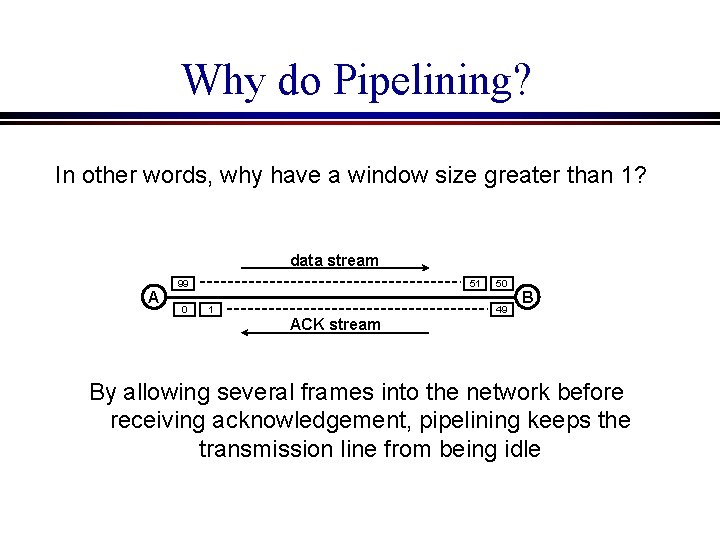
Why do Pipelining? In other words, why have a window size greater than 1? data stream A 99 0 51 1 50 49 B ACK stream By allowing several frames into the network before receiving acknowledgement, pipelining keeps the transmission line from being idle

What about Errors? What if a data or acknowledgement frame is lost when using a sliding window protocol? Two Solutions: Go Back N Selective Repeat

l One very important note about acknowledgement n Ack for frame n = I am expecting frame n+1 (not “I received fame n”)

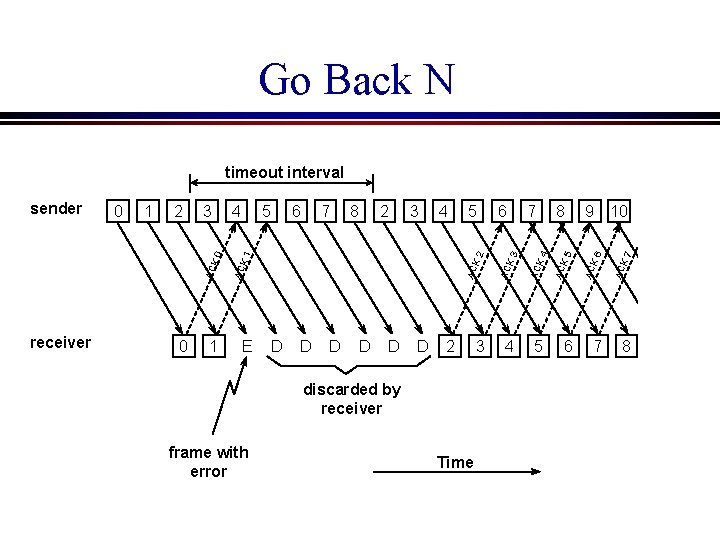
5. 2. 3 Sliding Window with Go Back N l l When the receiver notices a missing or erroneous frame, it simply discards all frames with greater sequence numbers and sends no ACK The sender will eventually time out and retransmit all the frames in its sending window

Go Back N E 6 7 8 2 3 4 5 D D D 2 discarded by receiver frame with error Time 3 6 7 4 5 8 9 10 AC K 7 1 5 AC K 6 4 AC K 5 0 3 AC K 4 2 AC K 2 1 AC K 3 receiver 0 AC K 1 sender AC K 0 timeout interval 6 7 8 9 10

Go Back N (cont’d) Go Back N can recover from erroneous or missing packets But… It is wasteful. If there a lot of errors, the sender will spend most of its time retransmitting useless information

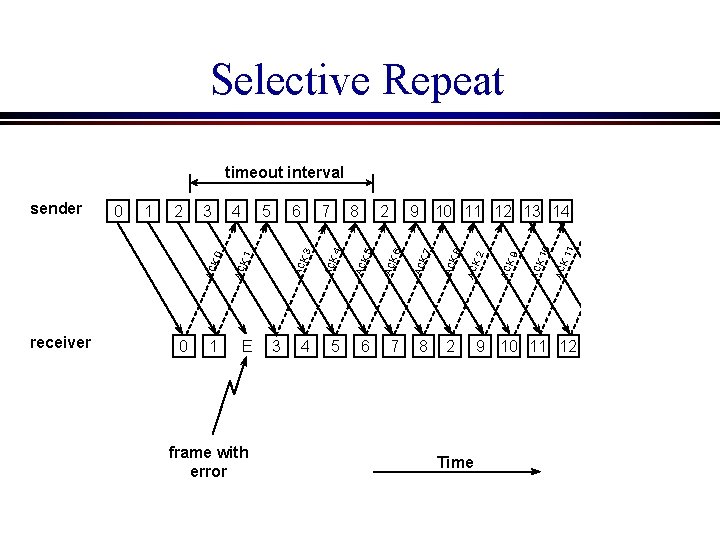
5. 2. 4 Sliding Window with Selective Repeat The sender retransmits only the frame with errors l The receiver stores all the correct frames that arrive following the bad one. (Note that this requires a significant amount of buffer space at the receiver. ) l When the sender notices that something is wrong, it just retransmits the one bad frame, not all its successors.

Selective Repeat E frame with error 3 Time 3 AC K 1 2 2 8 AC K 1 7 1 6 AC K 1 5 9 10 11 12 13 14 0 4 2 AC K 1 8 AC K 9 7 AC K 2 6 AC K 8 1 5 AC K 7 4 AC K 6 0 3 AC K 5 2 AC K 4 1 AC K 3 receiver 0 AC K 1 sender AC K 0 timeout interval 9 10 11 12 13 14

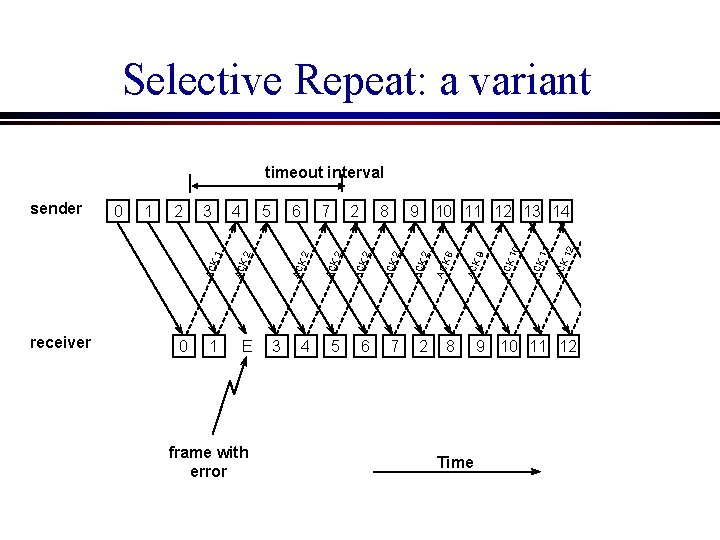
Selective Repeat: a variant E frame with error 3 Time 3 8 AC K 1 2 2 7 AC K 1 6 2 5 AC K 1 4 1 9 10 11 12 13 14 AC K 1 8 0 2 AC K 1 7 AC K 9 6 AC K 8 1 5 AC K 2 4 AC K 2 0 3 AC K 2 2 AC K 2 1 AC K 2 receiver 0 AC K 2 sender AC K 1 timeout interval 9 10 11 12 13 14

l In this scheme, every time a receiver receives a frame, it sends an acknowledgement which contains the sequence number of the next frame expected

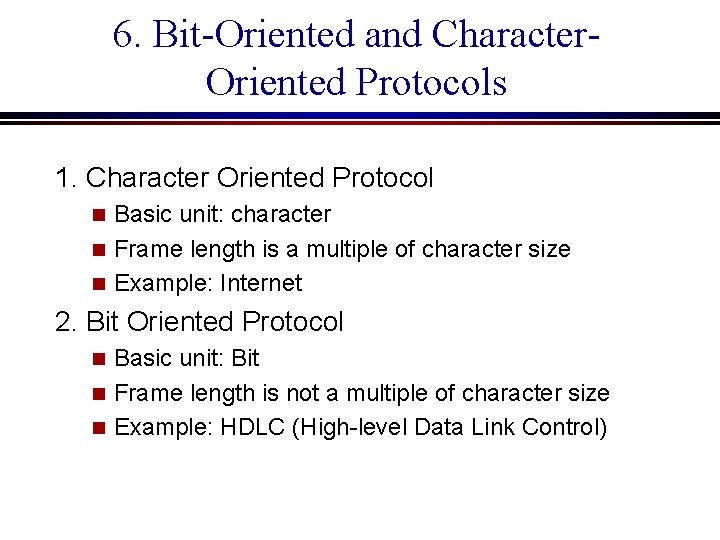
6. Bit-Oriented and Character. Oriented Protocols 1. Character Oriented Protocol Basic unit: character n Frame length is a multiple of character size n Example: Internet n 2. Bit Oriented Protocol Basic unit: Bit n Frame length is not a multiple of character size n Example: HDLC (High-level Data Link Control) n

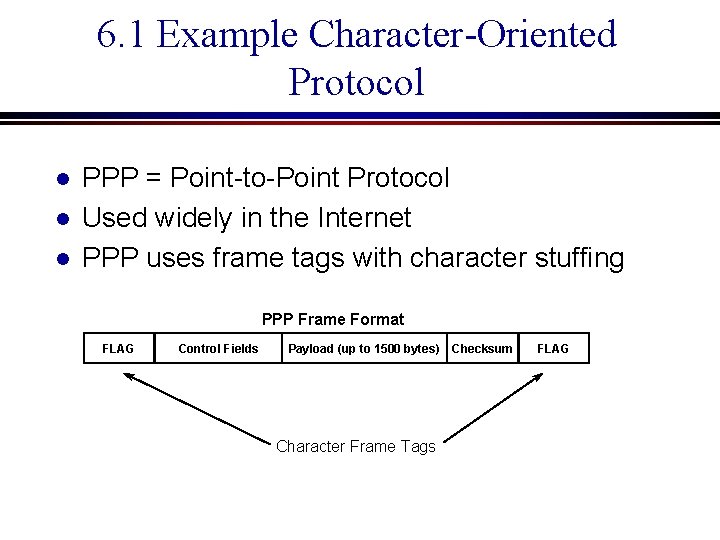
6. 1 Example Character-Oriented Protocol l PPP = Point-to-Point Protocol Used widely in the Internet PPP uses frame tags with character stuffing PPP Frame Format FLAG Control Fields Payload (up to 1500 bytes) Character Frame Tags Checksum FLAG

Character Oriented Protocols (cont’d) With character oriented protocols, a frame is composed of characters in some character code (e. g. , ASCII, EBCDIC, UNICODE) A computer with 9 -bit characters cannot send arbitrary messages in ASCII code. They must be chopped and repacked into units of 8 bits. Bit oriented protocols do not require such chopping up and repackaging of characters.

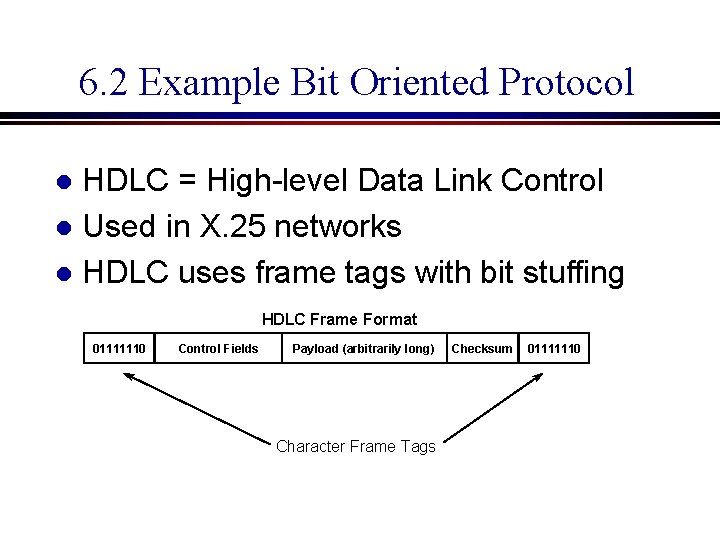
6. 2 Example Bit Oriented Protocol HDLC = High-level Data Link Control l Used in X. 25 networks l HDLC uses frame tags with bit stuffing l HDLC Frame Format 01111110 Control Fields Payload (arbitrarily long) Character Frame Tags Checksum 01111110