SSD 951 SECURE SOFTWARE DEVELOPMENT SECURITY MODELS Dr





































- Slides: 67

SSD 951: SECURE SOFTWARE DEVELOPMENT SECURITY MODELS Dr. Shahriar Bijani Shahed University Fall 2016

SLIDES’ REFERENCES Matt Bishop, Computer Security: Art and Science, Chapters 4 & 5, 2002 -2004. Chris Clifton, CS 526: Information Security course, Purdue university, 2010. William Stallings and Lawrie Brown, Computer Security: Principles and Practice, 3/e, Chapter 13, 2011. Security Models and Architecture, CISSP Exam Preparation, Bernie Eydt, EDS 2

READINGS Matt Bishop, Computer Security: Art and Science, 2002 -2004. � Chapters 4 (4. 1 & 4. 2) � Chapters 5 (5. 1 & 5. 2) William Stallings & Lawrie Brown, Computer Security: Principles and Practice, 3/e, 2011. � Chapter 4 “Access Control Principles” � Chapter 13 “Trusted Computing and Multilevel Security” Sections 13. 1 to 13. 4

SECURITY POLICY What is a security policy? � Defines what it means for a system to be secure Formally: Policy partitions system states into: � Authorized (secure) sates: These are states the system can enter � Unauthorized (nonsecure) sates: If the system enters any of these states, it’s a security violation (a breach of security ) Secure system � Starts in an authorized state � Never enters unauthorized states 4

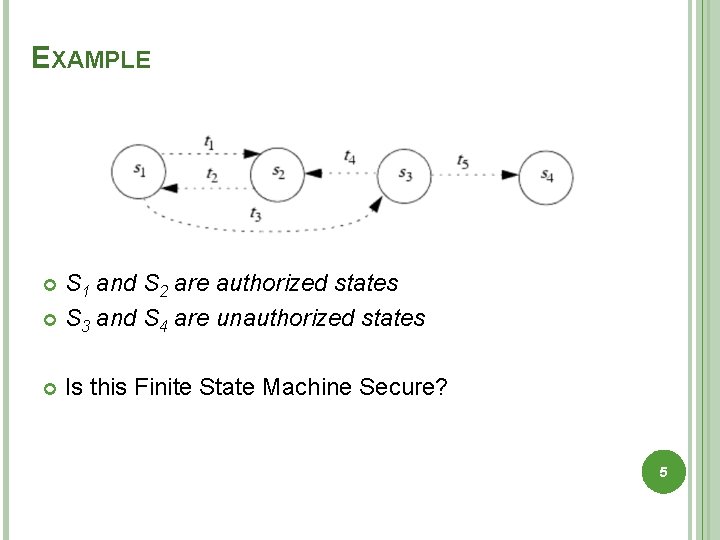
EXAMPLE S 1 and S 2 are authorized states S 3 and S 4 are unauthorized states Is this Finite State Machine Secure? 5

SECURITY MODELS/ POLICY MODELS Abstract description of a policy or class of policies Types of Security Policies � Military (governmental) security policy Policy primarily protecting confidentiality � Commercial security policy Policy primarily protecting integrity � Confidentiality policy Policy protecting only confidentiality � Integrity policy Policy protecting only integrity 6

CONFIDENTIALITY PROPERTY X set of entities, I information I has confidentiality property with respect to X if no x X can obtain information from I I can be disclosed to others Example: � X set of students � I final exam answer key � I is confidential with respect to X if students cannot obtain final exam answer key 7

INTEGRITY PROPERTY X set of entities, I information I has integrity property with respect to X if all x X trust information in I Types of integrity: � trust I, its transportation and protection (data integrity) � I information about origin of something or an identity (origin integrity, authentication) � I resource: means resource functions as it should (assurance) 8

AVAILABILITY PROPERTY X set of entities, I resource I has availability property with respect to X if all x X can access I Types of availability: � traditional: x gets access or not � quality of service: promised a level of access (for example, a specific level of bandwidth) and not meet it, even though some access is achieved 9

QUESTION Policy disallows cheating � Includes copying homework, with or without permission CS class has students do homework on computer Alice forgets to read-protect her homework file Bob copies it Who cheated? � Alice, Bob, or both? 10

ANSWER PART 1 Bob cheated � Policy forbids copying homework assignment � Bob did it � System entered unauthorized state (Bob having a copy of Alice’s assignment) If not explicit in computer security policy, certainly implicit � Not credible that a unit of the university allows something that the university as a whole forbids, unless the unit explicitly says so 11

ANSWER PART #2 Alice didn’t protect her homework � Not required by security policy She didn’t breach security If policy said students had to read-protect homework files, then Alice did breach security � She didn’t do read-protection 12

TYPES OF ACCESS CONTROL POLICIES An access control policy, (e. g. in an authorization database) dictates what types of access, under what circumstances, and by whom are permitted. Types of access control policies: � Discretionary Access Control (DAC) � Originator Controlled Access Control (ORCON) � Mandatory Access Control (MAC) � Role Based Access Control (RBAC) 13

TYPES OF ACCESS CONTROL POLICIES Discretionary Access Control (DAC) AKA identity-based access control (IBAC). � Controls access based on the identity of the requestor and on access rules (authorizations) stating what requestors are (or are not) allowed. � An individual user sets access control mechanism to allow or deny access to an object � data owners can create and modify matrix of subject / object relationships (e. g. , ACLs) � 14

TYPES OF ACCESS CONTROL POLICIES Mandatory Access Control (MAC) A System mechanism controls access to object, and individual cannot alter that access � Rules specify granting of access (also called rule-based access control) � E. g. The operating system enforces MAC. � security labels: shows how sensitive or critical system resources are � security clearances: indicate system entities are eligible to access certain resources � Controls access based on comparing security labels with security clearances. � � “insecure” transactions prohibited regardless of DAC � Cannot enforce MAC rules with DAC security kernel Someone with read access to a file can copy it and build a new “insecure” DAC matrix because he will be an owner of the new file. 15

TYPES OF ACCESS CONTROL POLICIES Role Based Access Control (RBAC) � Controls access based on the roles that users have within the system and on rules stating what accesses are allowed to users in given roles. � Identity governed by the role user assumes � Access is based on a user's job function within the organization � RBAC has become increasingly popular 16

MULTIPLE ACCESS CONTROL POLICIES These three policies are not mutually exclusive. An access control mechanism can employ 2 or 3 of these policies to cover different classes of system resources. 17

MECHANISMS Entity or procedure that enforces some part of the security policy � Access controls (like bits to prevent someone from reading a homework file) � Disallowing people from bringing CDs and USB disks into a computer facility to control what is placed on systems 18

COMPUTER SECURITY MODELS Two fundamental computer security facts: � All complex software systems have eventually revealed flaws or bugs that need to be fixed � It is extraordinarily difficult to build computer hardware/software not vulnerable to security attacks 19

COMPUTER SECURITY MODELS Problems involved both design and implementation Led to development of formal security models Initially funded by US Department of Defense Bell-La. Padula (BLP) model was very influential (1973) 20

TRUST IN FORMAL VERIFICATION Gives formal mathematical proof that given input i, program P produces output o as specified Suppose a security-related program S formally verified to work with operating system O What are the assumptions? 21

TRUST IN FORMAL METHODS Proof has no errors 1. Bugs in automated theorem provers • 2. 3. 4. Preconditions hold in environment in which S is to be used S transformed into executable S whose actions follow source code � Compiler bugs, linker/loader/library problems � Hardware bugs (e. g. Pentium f 00 f bug) Hardware executes S as intended 22

ACCESS CONTROL MODELS Bell-La. Padula Biba Clark-Wilson Chinese Wall 23

BELL-LAPADULA (BLP) MODEL Developed in 1970 s BLP is formal (mathematical) description of access control Three properties: � Discretionary access control (DAC) ds-property (discretionary security) � Mandatory access control (MAC) ss-property (simple security – no “read up”) *-property (star property – no “write down”) A secure system satisfies all of these properties 24

BACKGROUND Clearance An example: levels � Top Secret In-depth background check; highly trusted individual � Secret Routine background check; trusted individual � Sensitive (For Official Use Only) No background check, but limited distribution; minimally trusted individuals May be exempt from disclosure � Unclassified (Public) Unlimited distribution Untrusted individuals 25

BELL-LAPADULA (BLP) MODEL (STEP 1) Security levels arranged in linear ordering � Top Secret: highest � Secret � Confidential � Unclassified: lowest Levels consist of: � Subject has security clearance L(s) = ls � Object has security classification L(o) = lo � Clearance/Classification ordered: li < li+1 � Mandatory access control 26

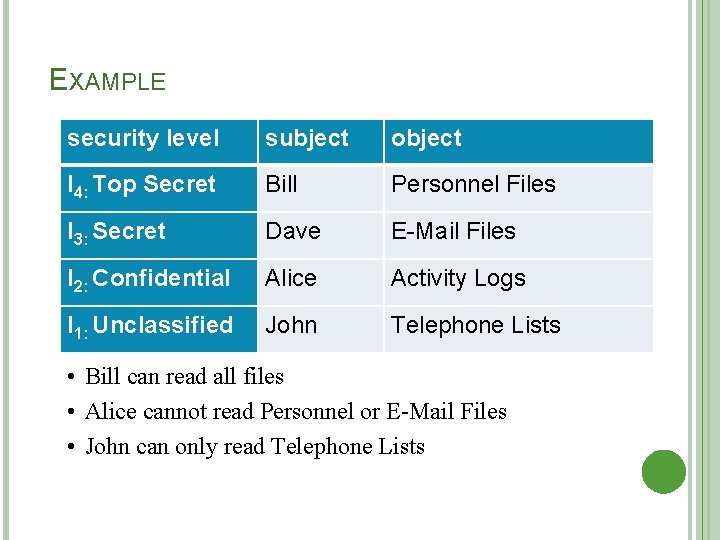
EXAMPLE security level subject object l 4: Top Secret Bill Personnel Files l 3: Secret Dave E-Mail Files l 2: Confidential Alice Activity Logs l 1: Unclassified John Telephone Lists • Bill can read all files • Alice cannot read Personnel or E-Mail Files • John can only read Telephone Lists

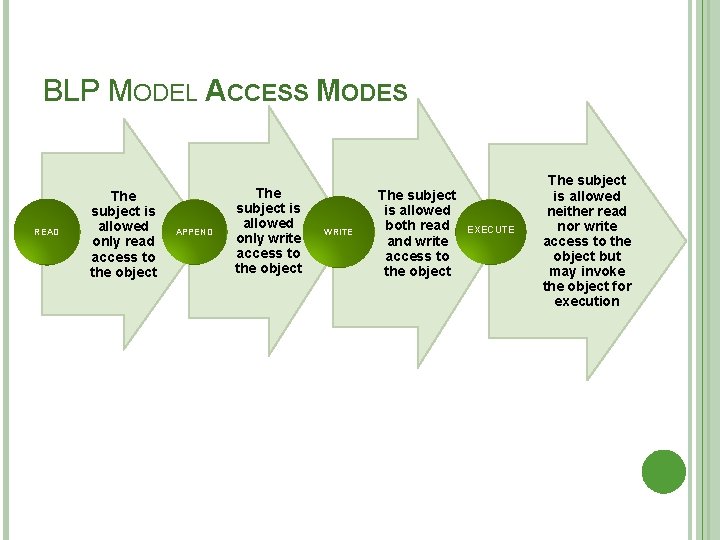
BLP MODEL ACCESS MODES READ The subject is allowed only read access to the object APPEND The subject is allowed only write access to the object WRITE The subject is allowed both read and write access to the object EXECUTE The subject is allowed neither read nor write access to the object but may invoke the object for execution

DISCRETIONARY ACCESS CONTROL • ds-property : An individual (or role) may grant to another individual (or role) access to a document based on the owner’s discretion, constrained by the MAC rules. • A subject can exercise only accesses for which it has the necessary authorization and which satisfy the MAC rules. • A user cannot give away data to unauthorized persons. Slide #5 -29

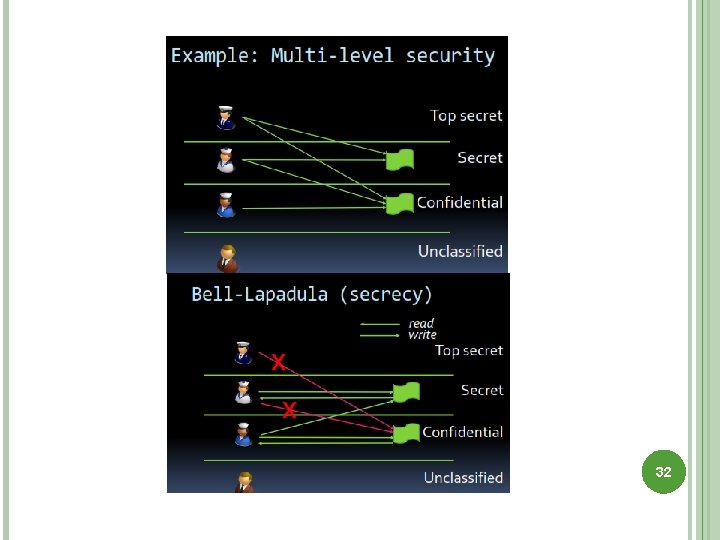
READING INFORMATION Information flows up, not down � “Reads up” disallowed, “reads down” allowed Simple Security Condition (Step 1) � Subject s can read object o iff, L(o) ≤ L(s) and s has permission to read o Note: combines mandatory control (relationship of security levels) and discretionary control (the required permission) � Sometimes called “no reads up” rule 30

WRITING INFORMATION Information flows up, not down � “Writes up” allowed, “writes down” disallowed *-Property (Step 1) � Subject s can write object o iff L(s) ≤ L(o) and s has permission to write o � Sometimes called “no writes down” rule 31

32

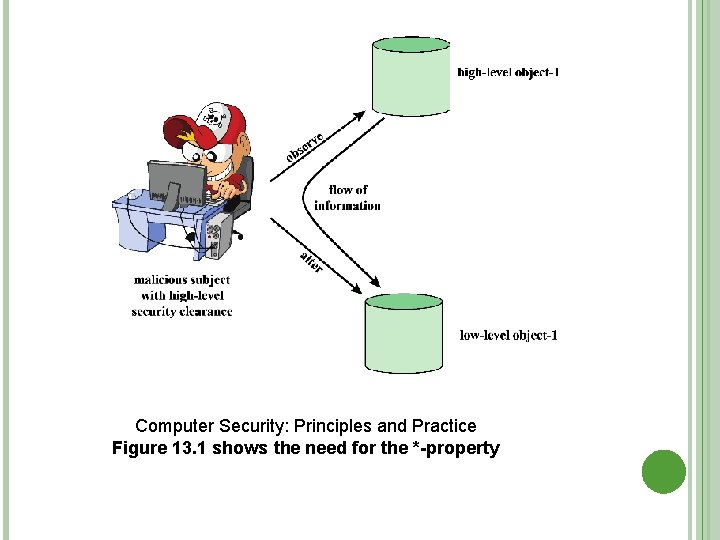
Computer Security: Principles and Practice Figure 13. 1 shows the need for the *-property

BASIC SECURITY THEOREM, STEP 1 If a system is initially in a secure state, and every transition of the system satisfies the security properties, then every state of the system is secure � Proof: induct on the number of transitions 34

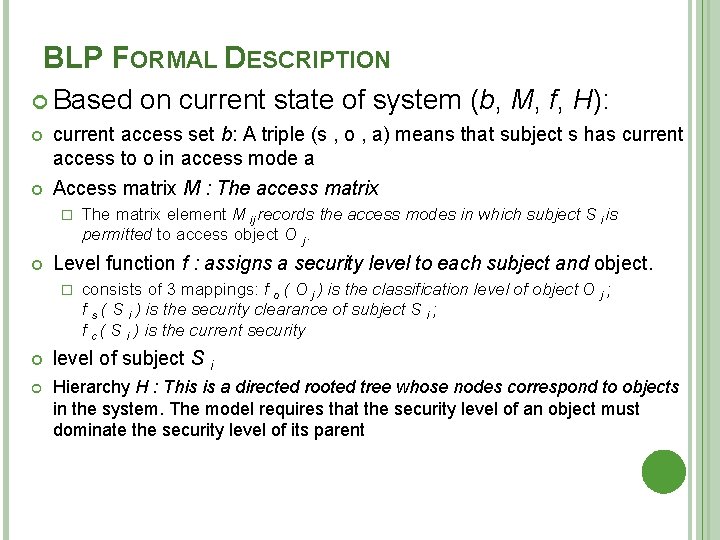
BLP FORMAL DESCRIPTION Based on current state of system (b, M, f, H): current access set b: A triple (s , o , a) means that subject s has current access to o in access mode a Access matrix M : The access matrix � The matrix element M ij records the access modes in which subject S i is permitted to access object O j. Level function f : assigns a security level to each subject and object. � consists of 3 mappings: f o ( O j ) is the classification level of object O j ; f s ( S i ) is the security clearance of subject S i ; f c ( S i ) is the current security level of subject S i Hierarchy H : This is a directed rooted tree whose nodes correspond to objects in the system. The model requires that the security level of an object must dominate the security level of its parent

BLP FORMAL DESCRIPTION Three BLP properties: ss-property: (Si, Oj, read) has fc(Si) ≥ fo(Oj). *-property: (Si, Oj, append) has fc(Si) ≤ fo(Oj) and (Si, Oj, write) has fc(Si) = fo(Oj) ds-property: (Si, Oj, Ax) implies Ax M[Si]

BLP OPERATIONS get access: add (subj, obj, access-mode) to b 1. � release access: remove (subj, obj, access-mode) change object level change current level give access permission: Add an access mode to M 2. 3. 4. 5. � 6. 7. 8. used by a subj to initiate an access to an object used by a subj to grant access to on an obj rescind access permission: reverse of 5 create an object delete a group of objects

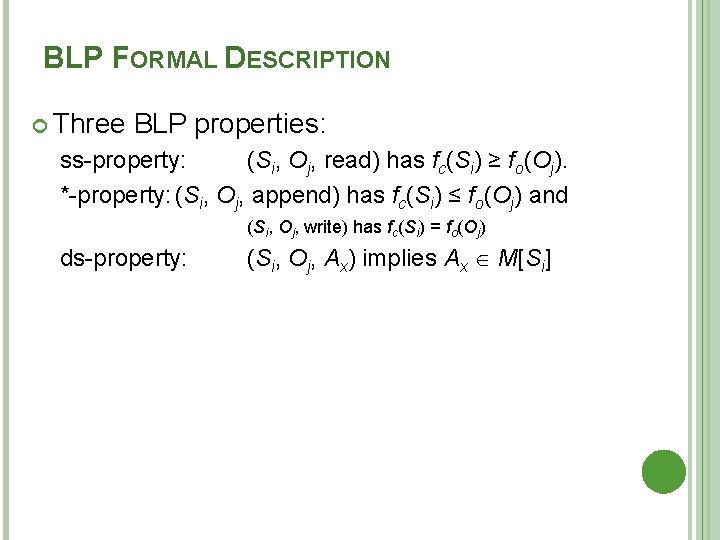
BLP EXAMPLE A role-based access control system Two users: Carla (student) and Dirk (teacher) � Carla (Class: s) � Dirk (Class: T); can also login as a students thus (Class: s) A student role has a lower security clearance A teacher role has a higher security clearance

BLP EXAMPLE Dirk creates f 1; Carla creates f 2 Carla can read/write to f 2 Carla can’t read f 1 Dirk can read/write f 1 Dirk can read f 2 (if perm) Dirk can read/write f 2 only as a stu Dirk reads f 2; want create f 3 (comments) Dirk signs in as a stu (so Carla can read) As a teacher, Dirk cannot create a file at stu classification

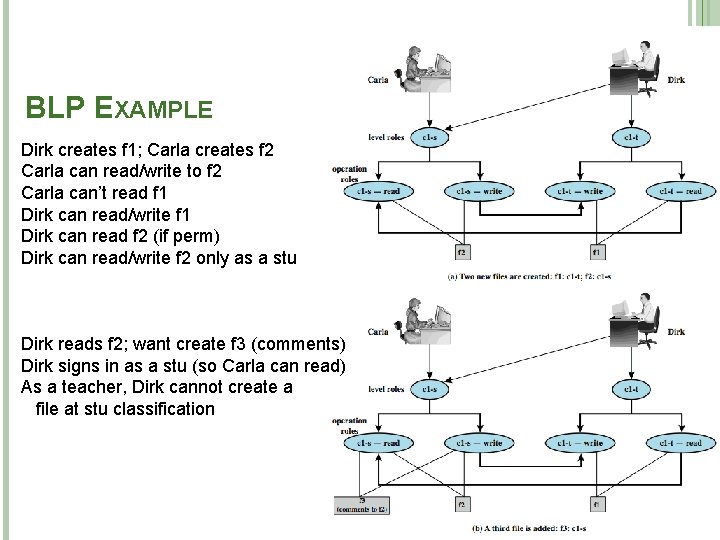
BLP EXAMPLE CONT. Dirk as a teacher creates exam (f 4) Must log in as a teacher to read template Dirk wants to give Carla access to read f 4 Dirk can’t do that; an admin must do An admin downgrades f 4 class to c 1 -s

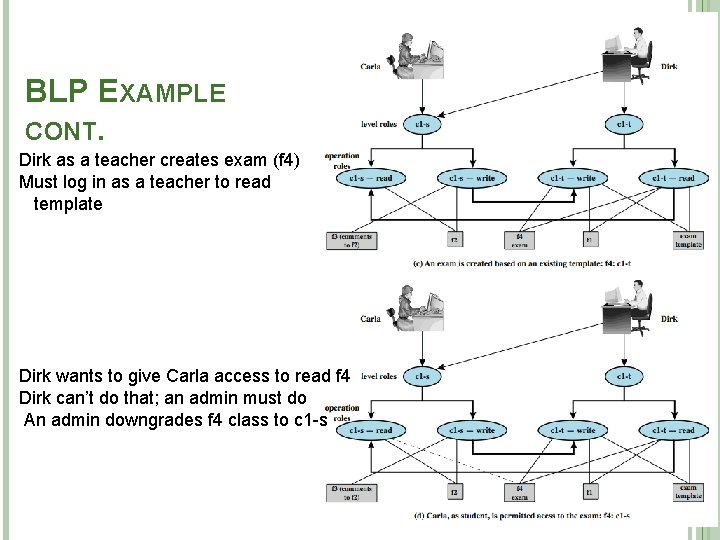
BLP EXAMPLE CONT. Carla writes answers to f 5 (at c 1 -t level) -- An example of write up Dirk can read f 5

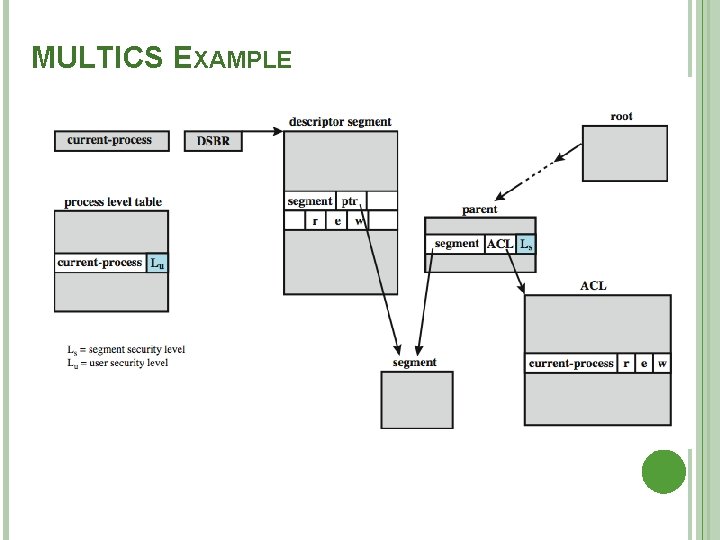
MULTICS EXAMPLE

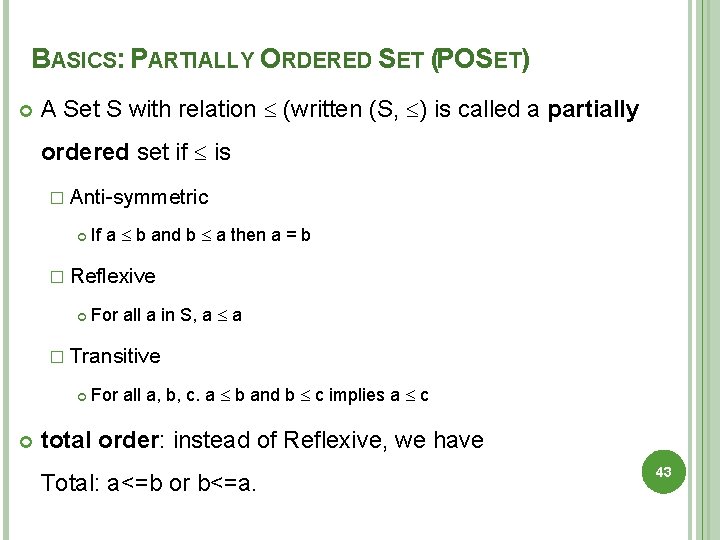
BASICS: PARTIALLY ORDERED SET (POSET) A Set S with relation (written (S, ) is called a partially ordered set if is � Anti-symmetric If a b and b a then a = b � Reflexive For all a in S, a a � Transitive For all a, b, c. a b and b c implies a c total order: instead of Reflexive, we have Total: a<=b or b<=a. 43

BACKGROUND: POSET EXAMPLES Natural numbers with less than (total order) Sets under the subset relation (partially order) Natural numbers ordered by divisibility (partially order) 44

BACKGROUND: LATTICE Partially ordered set (S, ) and two operations: � greatest lower bound (glb X) Greatest element less than all elements of set X � least upper bound (lub X) Least element greater than all elements of set X Every lattice has � bottom (glb L) a least element � top (lub L) a greatest element 45

BACKGROUND: LATTICE EXAMPLES Natural numbers in an interval (0. . n) with less than � Also the linear order of clearances (U FOUO S TS) The powerset of a set of generators under inclusion � E. g. Powerset of security categories {NUC, Crypto, ASI, EUR} The divisors of a natural number under divisibility 46

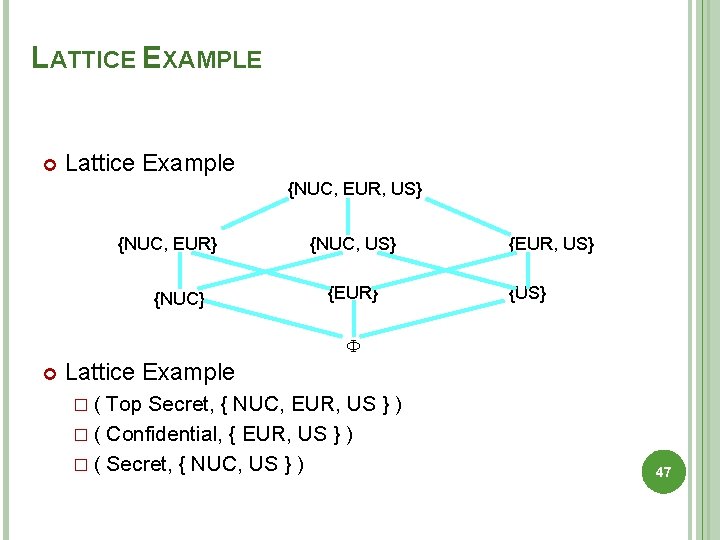
LATTICE EXAMPLE Lattice Example {NUC, EUR, US} {NUC, EUR} {NUC, US} {EUR, US} {US} Lattice Example � ( Top Secret, { NUC, EUR, US } ) � ( Confidential, { EUR, US } ) � ( Secret, { NUC, US } ) 47

BELL-LAPADULA MODEL (STEP 2) Total order of classifications not flexible enough Solution: Categories �S can access O if C(O) C(S) Combining with clearance: � (L, C) dominates (L’, C’) L’ = L and C’ C � Induces lattice instead of levels Expand notion of security level to include categories Security level is (clearance, category set) 48

LEVELS AND LATTICES dom (dominates) relation (L, C) dom (L , C ) iff L ≤ L and C C Examples � (Top Secret, {NUC, ASI}) dom (Secret, {NUC}) � (Secret, {NUC, EUR}) dom (Confidential, {NUC, EUR}) � (Top Secret, {NUC}) dom (Confidential, {EUR}) Let K be set of clearances, C set of categories. Set of security levels L = K C, dom form lattice � lub(L) = (max(L), C) � glb(L) = (min(L), ) 49

LEVELS AND ORDERING Security levels partially ordered � Any pair of security levels may (or may not) be related by dom “dominates” serves the role of “greater than” in step 1 � But “greater than” is a total ordering, 50

READING INFORMATION Information flows up, not down � “Reads up” disallowed, “reads down” allowed Simple Security Condition (Step 2) � Subject s can read object o iff L(s) dom L(o) and s has permission to read o Note: combines mandatory control (relationship of security levels) and discretionary control (the required permission) � Sometimes called “no reads up” rule 51

WRITING INFORMATION Information flows up, not down � “Writes up” allowed, “writes down” disallowed *-Property (Step 2) � Subject s can write object o iff L(o) dom L(s) and s has permission to write o � Sometimes called “no writes down” rule 52

BASIC SECURITY THEOREM (STEP 2) If a system is initially in a secure state, and every transition of the system satisfies the security properties (step 2) then every state of the system is secure � Proof: induct on the number of transitions 53

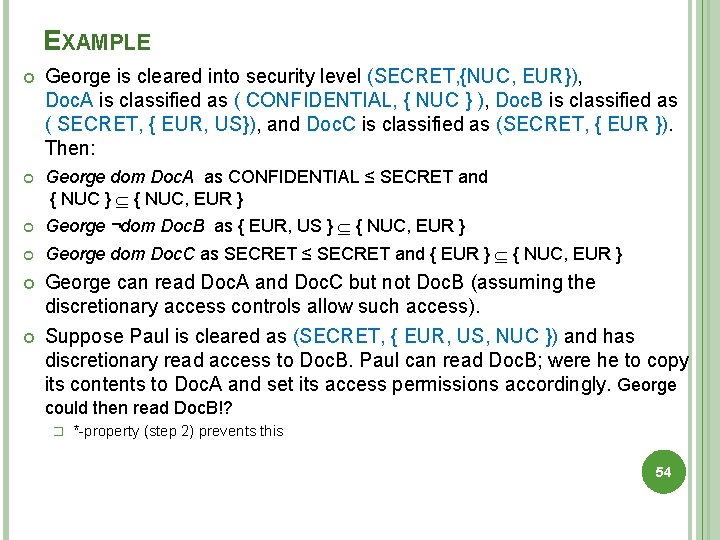
EXAMPLE George is cleared into security level (SECRET, {NUC, EUR}), Doc. A is classified as ( CONFIDENTIAL, { NUC } ), Doc. B is classified as ( SECRET, { EUR, US}), and Doc. C is classified as (SECRET, { EUR }). Then: George dom Doc. A as CONFIDENTIAL ≤ SECRET and { NUC } { NUC, EUR } George ¬dom Doc. B as { EUR, US } { NUC, EUR } George dom Doc. C as SECRET ≤ SECRET and { EUR } { NUC, EUR } George can read Doc. A and Doc. C but not Doc. B (assuming the discretionary access controls allow such access). Suppose Paul is cleared as (SECRET, { EUR, US, NUC }) and has discretionary read access to Doc. B. Paul can read Doc. B; were he to copy its contents to Doc. A and set its access permissions accordingly. George could then read Doc. B!? � *-property (step 2) prevents this 54

PROBLEM Colonel has (Secret, {NUC, EUR}) clearance Major has (Secret, {EUR}) clearance � Major can talk to colonel (“write up” or “read down”) � Colonel cannot talk to major (“read up” or “write down”) Not Desired! 55

SOLUTION Define maximum, current levels for subjects � maxlevel(s) dom curlevel(s) Example � Treat Major as an object (Colonel is writing to him) � Colonel has maxlevel (Secret, { NUC, EUR }) � Colonel sets curlevel to (Secret, { EUR }) � Now L(Major) dom curlevel(Colonel) Colonel can write to Major without violating “no writes down” 56

SYSTEMS BUILT ON BELL-LAPADULA (BLP) BLP was a simple model A goal: it could be enforced by simple mechanisms File system access control was the obvious choice Multics (1965) implemented BLP Unix inherited its discretionary AC from Multics 57

LIMITATIONS TO THE BLP MODEL Many operations that are in fact secure will be disallowed by the model …

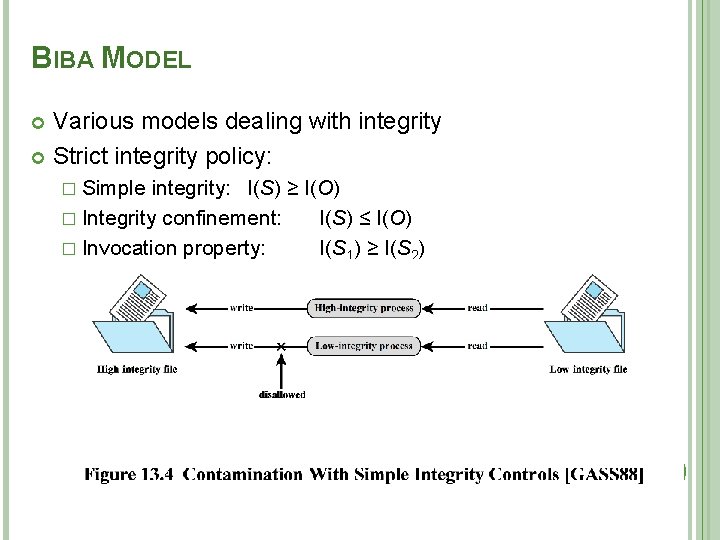
BIBA MODEL Similar to BLP but focus is on integrity, not confidentiality Result is to turn the BLP model upside down � High integrity subjects cannot read lower integrity objects (no “read down”) � Subjects cannot move low integrity data to high-integrity environment (no “write up”) 59

BIBA MODEL Various models dealing with integrity Strict integrity policy: � Simple integrity: I(S) ≥ I(O) � Integrity confinement: I(S) ≤ I(O) � Invocation property: I(S 1) ≥ I(S 2) 60

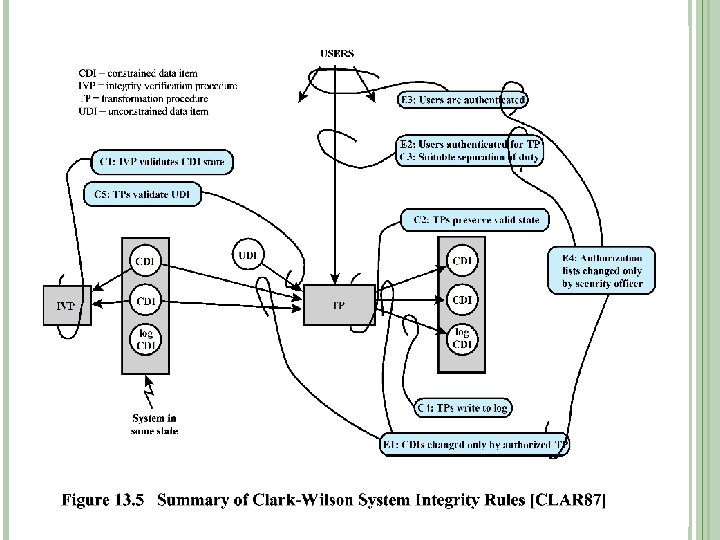
CLARK-WILSON MODEL Reviews distinction between military and commercial policy � Military policy focus on confidentiality � Commercial policy focus on integrity Mandatory commercial controls typically involve who gets to do what type of transaction rather than who sees what � Example: cut a check above a certain dollar amount 61

CLARK-WILSON MODEL (CONTINUED) Two types of objects: � Constrained Data Items (CDIs) � Unconstrained Data Items (UDIs) Two types of transactions on CDIs in model � Integrity Verification Procedures (IVPs) � Transformation Procedures (TPs) IVPs certify that TPs on CDIs result in valid state All TPs must be certified to result in valid transformation 62

CLARK-WILSON MODEL (CONTINUED) System maintains list of valid relations of the form: {User. ID, TP, CDI/UDI} Only permitted manipulation of CDI is via an authorized TP If a TP takes a UDI as an input, then it must result in a proper CDI or the TP will be rejected Additional requirements � Auditing: TPs must write to an append-only CDI (log) � Separation of duties 63


CLARK-WILSON VERSUS BIBA In Biba’s model, UDI to CDI conversion is performed by trusted subject only (e. g. , a security officer), but this is problematic for data entry function. In Clark-Wilson, TPs are specified for particular users and functions. Biba’s model does not offer this level of granularity. 65

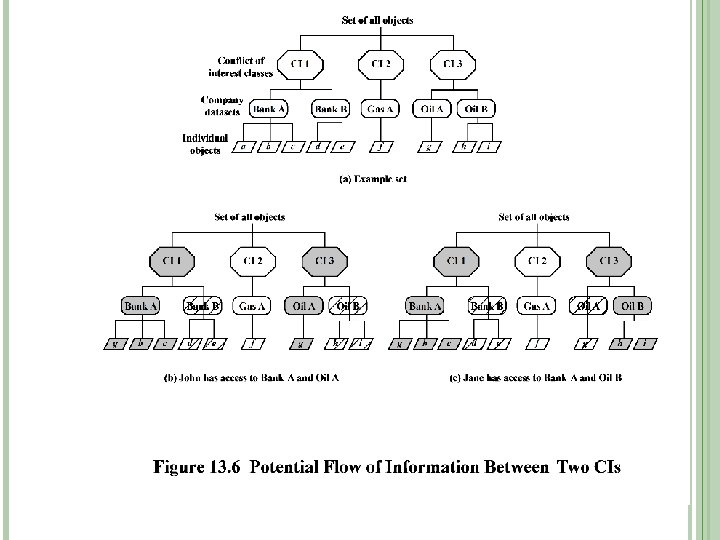
CHINESE WALL Focus is on conflicts of interest. Principle: Users should not access the confidential information of both a client organization and one or more of its competitors. How it works � Users have no “wall” initially. � Once any given file is accessed, files with competitor information become inaccessible. � Unlike other models, access control rules change with user behavior 66
