Security Architecture Models The security architecture of an











- Slides: 29

Security Architecture & Models “The security architecture of an information system is fundamental to enforcing an organization’s information security policy. ”

Computer Architecture o o CPU, control bus Memory: n o cache, RAM, DRAM, ROM CPU: n n n Instruction cycle: fetch & execute Pipelining, CISC, RISC, Multi-tasking, Multi-Processing I/O: programmed I/O, DMA, Interrupts

Software o Languages n n n 1 GL: 2 GL: 3 GL: 4 GL: 5 GL: machine language Assembly language FORTRAN, BASIC, PL/1, C, etc NATURAL, FOCUS, SQL Prolog, LISP, other AI languages

Open & Closed Systems o Open: n n n o Vendor independent Designed & written by “outsiders” Subject to review & evaluation by outside parties not company insiders Closed n n Vendor dependent Not typically compatible with other systems

Distributed Architecture o Migration from centralized to client/server n n n n User is also admin, programmer & operator Desktops can contain sensitive, at risk, info Users might lack security awareness Desktop can provide avenue into “trusted” networks Modems, PDAs, USB drives can be attached easily Downloading from Internet can produce disasters Desktops are hard to protect physically Lack of proper backup

Security mechanisms for Distributed Environments o o o o o Email & upload/download policies Robust access controls (biometrics &/or 2 tier controls) GUIs to restrict access to “real” system File Encryption & cipher tools for email Users with limited “rights” Separation of processes into privileged & non-privileged Lock desktops, enable tampering logging Enable remote logging Centralized backup

Protection Mechanisms o o Protection Domain: execution & memory space assigned to each process Abstraction ie objects & OOP Security Labels: classification for access control Security Modes: A system operates in different modes with users having different rights depending on the security label the object being processed has

Rings or layers of security o o OS kernel is usually inner most circle Processes & users are closer or further from the center depending on classification and need

Recovery Procedures o o o Should not provide opportunity for violations of system’s security policy Fault-tolerant: computer system fails but network continues to opperate Failsafe system: hardware or software failure causes “controlled” shutdown Fail-soft or resilient: non-critical processing is discontinued but network or computer continues in degraded mode Failover: switching to duplicate systems in case of failure

Assurance o o Degree of confidence in the satisfaction of security needs. Following slides provide an overview of guidelines & standards that help evaluate security aspects of a system

Assurance: Evaluation Criteria o o o Trusted Computer Evaluation Criteria (TCSEC) Basic control objectives are: security policy, assurance & accountability Assurance levels are: D (minimal protection), C (discretionary), B (manditory), & A (Verified)

Assurance: Certification & Accreditation o o o Formal methods provide for an authority that takes responsibility for system security Certification: comprhensive eval of system security Accreditation: format declaration

Certification & Accreditation o o Responsibility (i. e. blame) requires Formal methods Certification n o Accreditation n o Comprehensive eval of technical & non-technical security features Formal declaration by Designated Authority stating that system is approved to opperate in particular security mode Rechecked after defined period of time

U. S. Defense Accreditation Process o o Phase 1: understand mission, environment, & architecture to determine security requirements Phase 2: create SSAA an evolving, binding security agreement. SSAA becomes baseline security agreement Phase 3: Validation: check compliance Phase 4: Post Accreditation

U. S. Defense Types of Accreditation o o o Site: evaluates a single site Type: evaluates an app or system distributed to a number of locations System: evaluates a major app or support system

Systems Security Engineering Capability Maturity Mdl (SSE-CMM) o 1. 2. 3. 4. If you can guarantee process you can guarantee the product Describes essential characteristics of security engineering process Captures industry best practices Accepted ways of defining practices and improving capability Provides measures of growth in capability

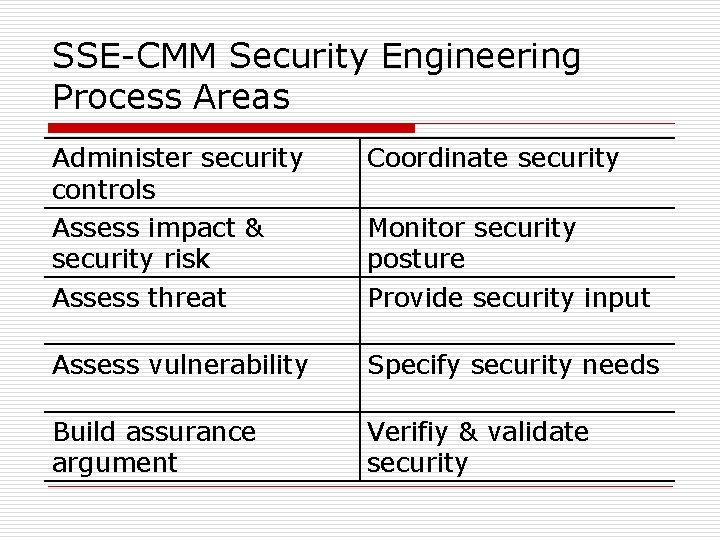
SSE-CMM Security Engineering Process Areas Administer security controls Assess impact & security risk Assess threat Coordinate security Assess vulnerability Specify security needs Build assurance argument Verifiy & validate security Monitor security posture Provide security input

Information Security Models o Used to formalize security policy o Three types of models 1. 2. 3. Access control models Integrity models Information flow models

Access control models o Access Matrix n o Take-Grant Model n o Access rights for subjects to objects Directed graph to specify rights that a subject can take or grant from or to another subject Bell-La. Padula Model n n Department of Defense Deals only with confidentiality not integrity or availability

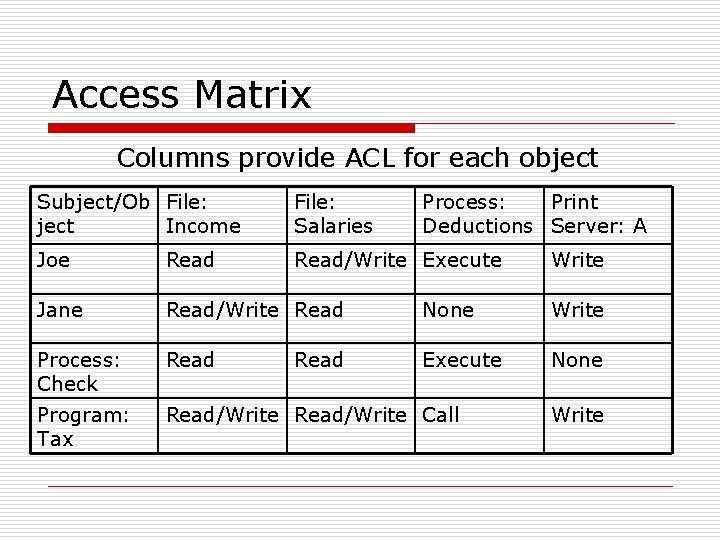
Access Matrix Columns provide ACL for each object Subject/Ob File: ject Income File: Salaries Joe Read/Write Execute Jane Read/Write Read None Write Process: Check Read Execute None Program: Tax Read/Write Call Read Process: Print Deductions Server: A Write

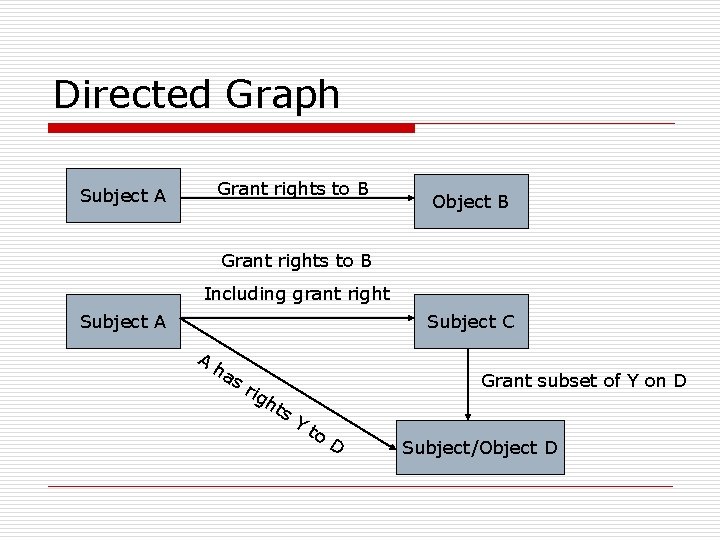
Directed Graph Grant rights to B Subject A Object B Grant rights to B Including grant right Subject A Subject C A ha sr igh ts Grant subset of Y on D Y to D Subject/Object D

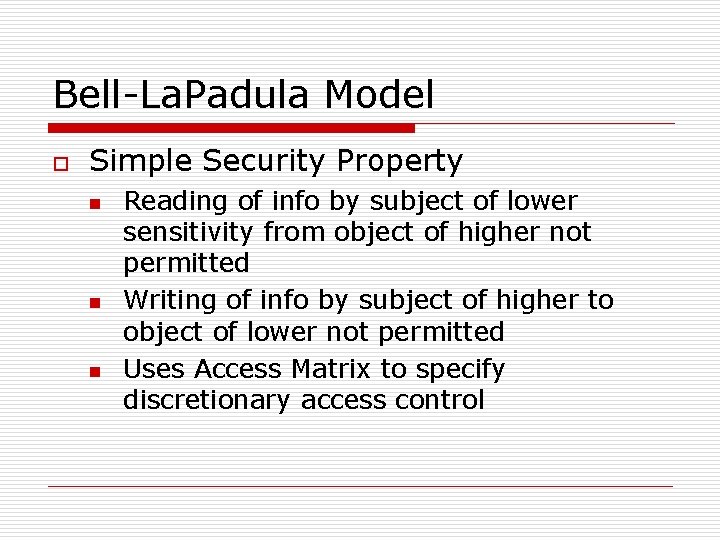
Bell-La. Padula Model o Simple Security Property n n n Reading of info by subject of lower sensitivity from object of higher not permitted Writing of info by subject of higher to object of lower not permitted Uses Access Matrix to specify discretionary access control

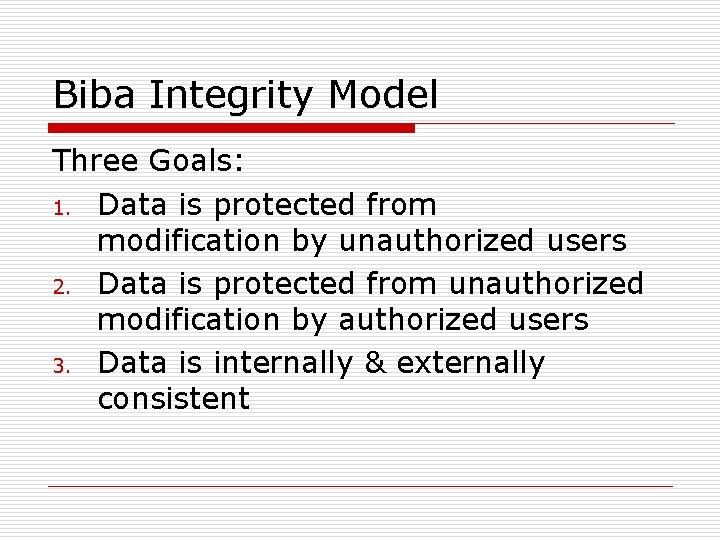
Integrity Models o o o Sometimes integrity is as or more important than confidentiality Biba Integrity Model Clark-Wilson Integrity Model

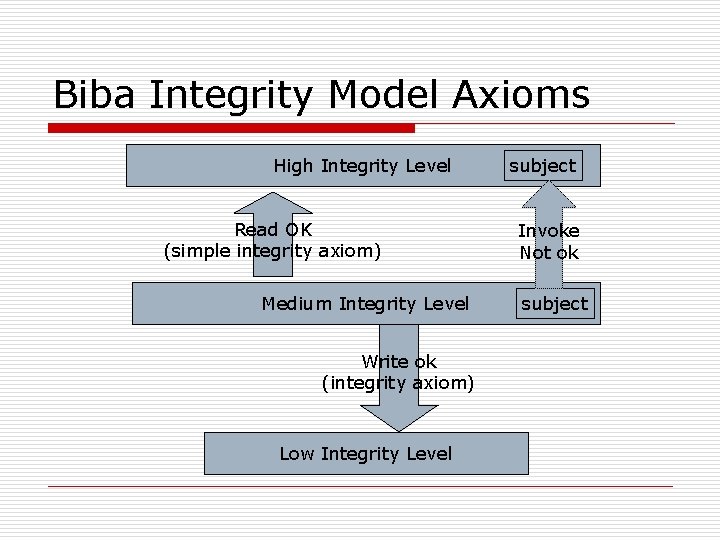
Biba Integrity Model Three Goals: 1. Data is protected from modification by unauthorized users 2. Data is protected from unauthorized modification by authorized users 3. Data is internally & externally consistent

Biba Integrity Model Axioms High Integrity Level Read OK (simple integrity axiom) Medium Integrity Level Write ok (integrity axiom) Low Integrity Level subject Invoke Not ok subject

Clark-Wilson Integrity Model o o o Real world model Constrained data item (CDI): object whose integrity is to be preserved Integrity Verification Procedure: confirms that all CDIs are in valid states of integrity Transformation Procedure: assures that well formed manipulations are used to change CDIs Unconstrained data item

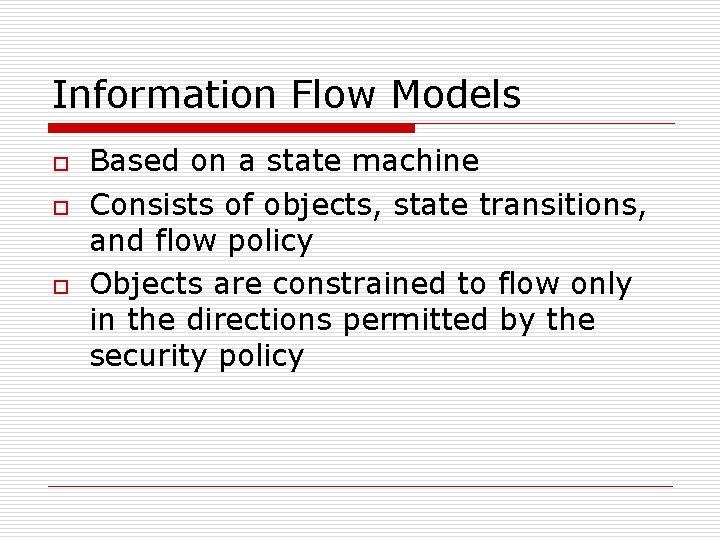
Information Flow Models o o o Based on a state machine Consists of objects, state transitions, and flow policy Objects are constrained to flow only in the directions permitted by the security policy

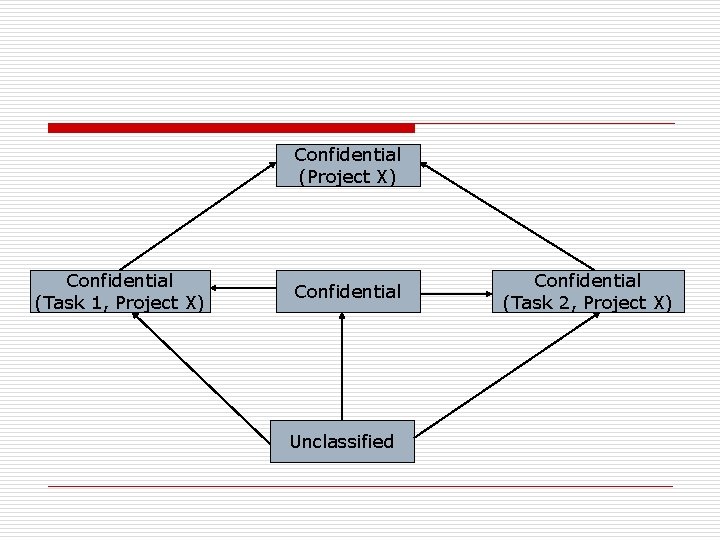
Confidential (Project X) Confidential (Task 1, Project X) Confidential Unclassified Confidential (Task 2, Project X)

Composition Theories o o o Systems are usually built by combining smaller systems Therefore must consider whether security of component systems are maintained when combined into larger systems Types of constructs n n n Cascading: input to one sys is from another Feedback: loop one to second back to one Hookup: system that communicates with both internal & external systems