Maintenance Release 1 2 5 Cisco 300 Series






- Slides: 19

Maintenance Release 1. 2. 5 Cisco 300 Series Switches Ivor Diedricks Sr. Product Manager © 2011 Cisco and/or its affiliates. All rights reserved.

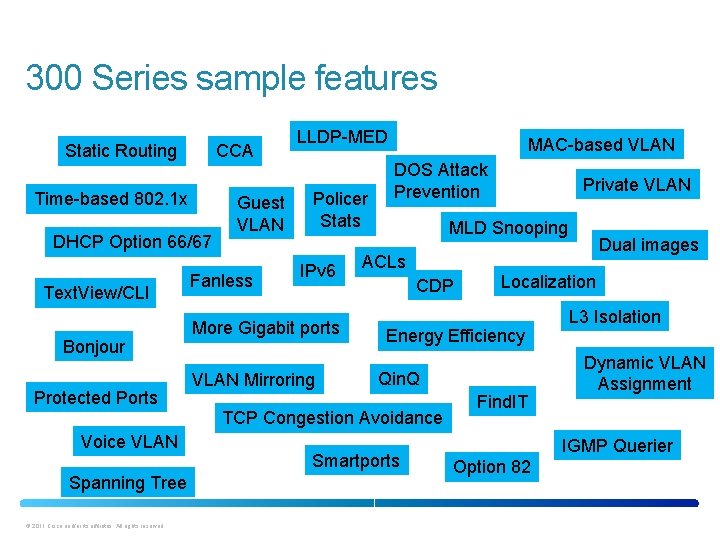
300 Series sample features Static Routing CCA Time-based 802. 1 x DHCP Option 66/67 Text. View/CLI Bonjour Protected Ports Guest VLAN Fanless LLDP-MED Policer Stats IPv 6 More Gigabit ports VLAN Mirroring MAC-based VLAN DOS Attack Prevention MLD Snooping ACLs CDP Qin. Q Spanning Tree © 2011 Cisco and/or its affiliates. All rights reserved. Smartports Dual images Localization Energy Efficiency TCP Congestion Avoidance Voice VLAN Private VLAN Find. IT L 3 Isolation Dynamic VLAN Assignment IGMP Querier Option 82

300 series enhancements in version 1. 2. 5 • Extend the already feature-rich Security capabilities Add support for Denial-of-Service Attack Prevention capabilities Secures file transfers to/from the switch Secure mechanism to handle sensitive data (passwords/keys, etc) on the switch as well as populating it to other switches. Secure Auto-configuration of the switches • Extend the time-based capabilities of the switches Deliver network access for users, devices, applications on a time schedule Time-based ACLs and port operation • Extend the Green energy savings capabilities of the switches Disable LEDs • Enhanced visibility to help troubleshooting and enables billing Support for Radius Accounting © 2011 Cisco and/or its affiliates. All rights reserved.

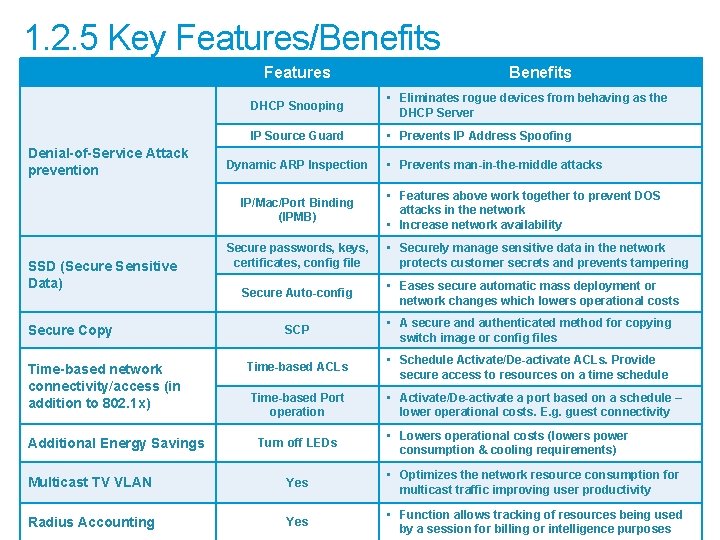
1. 2. 5 Key Features/Benefits Features Denial-of-Service Attack prevention DHCP Snooping • Eliminates rogue devices from behaving as the DHCP Server IP Source Guard • Prevents IP Address Spoofing Dynamic ARP Inspection IP/Mac/Port Binding (IPMB) SSD (Secure Sensitive Data) Secure Copy Time-based network connectivity/access (in addition to 802. 1 x) Additional Energy Savings Benefits Secure passwords, keys, certificates, config file Secure Auto-config • Prevents man-in-the-middle attacks • Features above work together to prevent DOS attacks in the network • Increase network availability • Securely manage sensitive data in the network protects customer secrets and prevents tampering • Eases secure automatic mass deployment or network changes which lowers operational costs SCP • A secure and authenticated method for copying switch image or config files Time-based ACLs • Schedule Activate/De-activate ACLs. Provide secure access to resources on a time schedule Time-based Port operation Turn off LEDs • Activate/De-activate a port based on a schedule – lower operational costs. E. g. guest connectivity • Lowers operational costs (lowers power consumption & cooling requirements) Multicast TV VLAN Yes • Optimizes the network resource consumption for multicast traffic improving user productivity Radius Accounting Yes • Function allows tracking of resources being used by a session for billing or intelligence purposes © 2011 Cisco and/or its affiliates. All rights reserved.

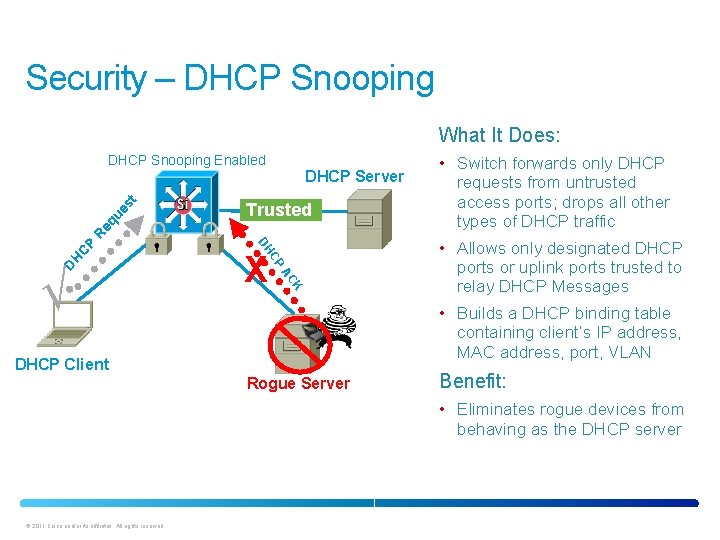
Security – DHCP Snooping What It Does: DHCP Server Trusted AC DH CP K √ X • Switch forwards only DHCP requests from untrusted access ports; drops all other types of DHCP traffic • Allows only designated DHCP DH CP Re qu es t DHCP Snooping Enabled ports or uplink ports trusted to relay DHCP Messages • Builds a DHCP binding table containing client’s IP address, MAC address, port, VLAN DHCP Client Rogue Server Benefit: • Eliminates rogue devices from behaving as the DHCP server © 2011 Cisco and/or its affiliates. All rights reserved.

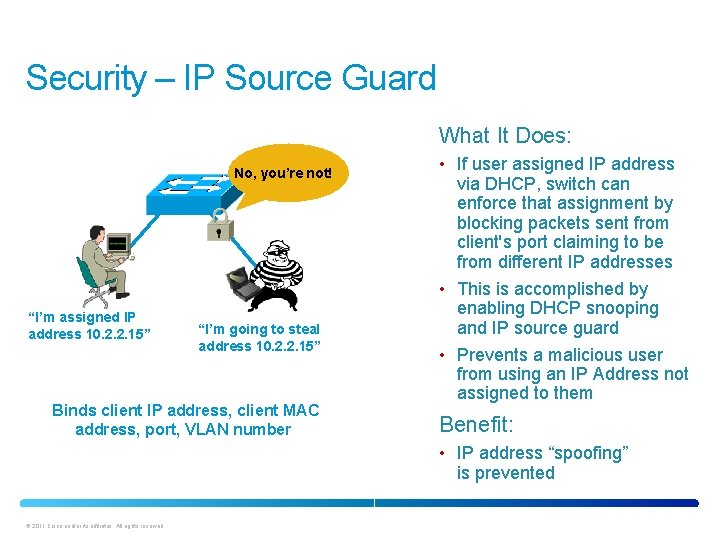
Security – IP Source Guard What It Does: No, you’re not! “I’m assigned IP address 10. 2. 2. 15” “I’m going to steal address 10. 2. 2. 15” Binds client IP address, client MAC address, port, VLAN number • If user assigned IP address via DHCP, switch can enforce that assignment by blocking packets sent from client's port claiming to be from different IP addresses • This is accomplished by enabling DHCP snooping and IP source guard • Prevents a malicious user from using an IP Address not assigned to them Benefit: • IP address “spoofing” is prevented © 2011 Cisco and/or its affiliates. All rights reserved.

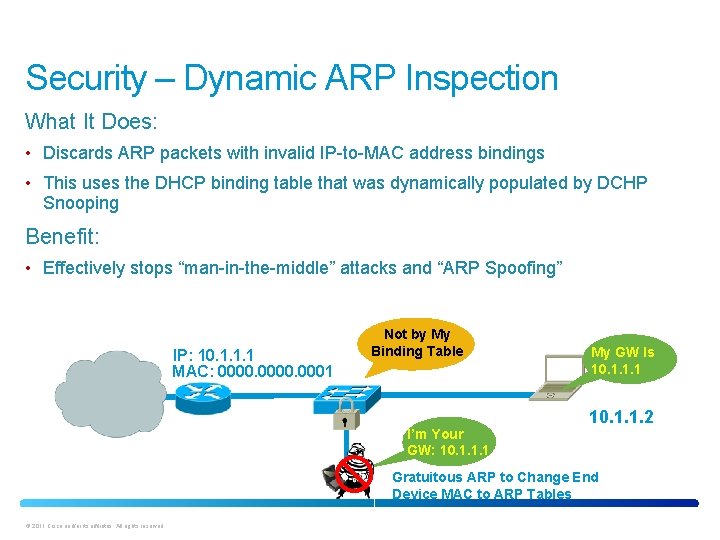
Security – Dynamic ARP Inspection What It Does: • Discards ARP packets with invalid IP-to-MAC address bindings • This uses the DHCP binding table that was dynamically populated by DCHP Snooping Benefit: • Effectively stops “man-in-the-middle” attacks and “ARP Spoofing” IP: 10. 1. 1. 1 MAC: 0000. 0001 Not by My Binding Table I’m Your GW: 10. 1. 1. 1 My GW Is 10. 1. 1. 1 10. 1. 1. 2 Gratuitous ARP to Change End Device MAC to ARP Tables © 2011 Cisco and/or its affiliates. All rights reserved.

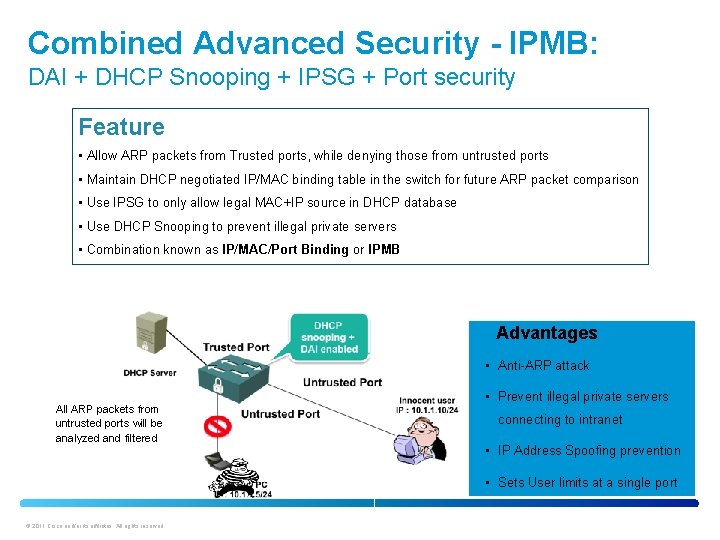
Combined Advanced Security - IPMB: DAI + DHCP Snooping + IPSG + Port security Feature • Allow ARP packets from Trusted ports, while denying those from untrusted ports • Maintain DHCP negotiated IP/MAC binding table in the switch for future ARP packet comparison • Use IPSG to only allow legal MAC+IP source in DHCP database • Use DHCP Snooping to prevent illegal private servers • Combination known as IP/MAC/Port Binding or IPMB Advantages • Anti-ARP attack All ARP packets from untrusted ports will be analyzed and filtered • Prevent illegal private servers connecting to intranet • IP Address Spoofing prevention • Sets User limits at a single port © 2011 Cisco and/or its affiliates. All rights reserved.

Secure Sensitive Data (SSD) - Overview • Architecture that facilitates the protection of sensitive data on a switch • Sensitive data = passwords, keys, passphrases • Makes use of passphrase, product secrets, encryption, access control, and secured user authentication to provide secure solution for managing sensitive data • Protects configuration files containing sensitive data from being tampered with – file integrity control • Also supports zero-touch auto-configuration with sensitive data • SSD enables the secure backup and sharing of configuration files containing sensitive data • SSD permits & denies access to sensitive data – in encrypted & plain text format • SSD permissions are based on user credentials and SSD rules • SSD protects sensitive data on a device with SSD rules, SSD properties, and user authentication • Configuration of SSD rules, SSD properties and user authentication are themselves sensitive data protected by SSD © 2011 Cisco and/or its affiliates. All rights reserved.

Protection Levels • SSD provides administrators with the flexibility to configure the desired level of protection on their sensitive data; - No protection with sensitive data in plaintext - Minimum protection with encryption based on the default passphrase - High level protection with encryption based on user-defined passphrase • SSD grants read permission to sensitive data only to authenticated and authorized users, based on SSD rules • The Switch authenticates and authorizes management access to users through the user authentication process • Only SSD platforms have secrets to be able to decrypt encrypted data of others © 2011 Cisco and/or its affiliates. All rights reserved.

SSD Details • Key – 128 -bits (AES) Generated from passphrase with padding both sides • Also uses non-reversible MD 5 hash to verify config file integrity and SSD control block integrity • SSD Rules Permissions for users/groups Access on a specific channel – Console, SSH, HTTPS, SCP, Telnet, HTTP, etc Can view in Plaintext, Encrypted, or both • Zero touch Auto-config with User-defined passphrase Config file will have User-defined passphrase as Encrypted data Receiving device learns the User-defined passphrase from the config file No need for pre-config of User-defined passphrase on receiving device © 2011 Cisco and/or its affiliates. All rights reserved.

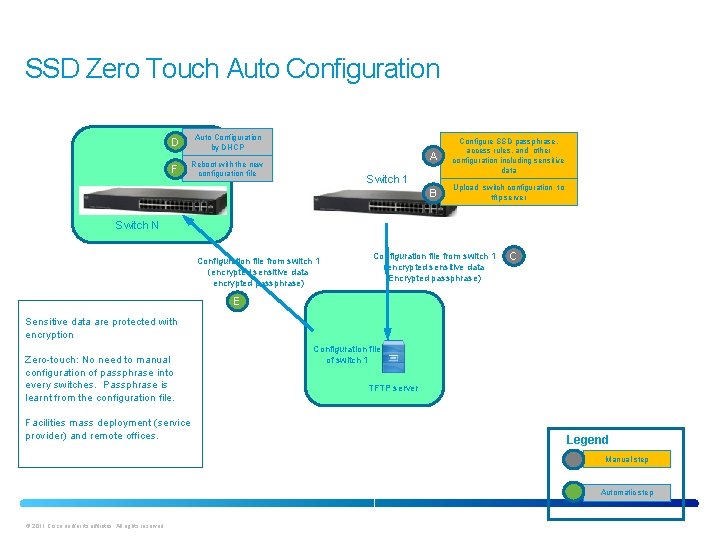
SSD Zero Touch Auto Configuration D Auto Configuration by DHCP F Reboot with the new configuration file A Configure SSD passphrase, access rules, and other configuration including sensitive data B Upload switch configuration to tftp server Switch 1 Switch N Configuration file from switch 1 (encrypted sensitive data encrypted passphrase) Configuration file from switch 1 (encrypted sensitive data Encrypted passphrase) C E Sensitive data are protected with encryption Zero-touch: No need to manual configuration of passphrase into every switches. Passphrase is learnt from the configuration file. Facilities mass deployment (service provider) and remote offices. Configuration file of switch 1 TFTP server Legend Manual step Automatic step © 2011 Cisco and/or its affiliates. All rights reserved.

Time Based Switch operations • Time Based operations are useful when it is needed to restrict traffic/access based on: A certain time range A certain Day A certain Date Periodic settings • Time range supported for multiple capabilities i. e. ACL, 802. 1 x (supported in prior release), Po. E (future release) and Port operation • Time-based ACLs: Restrict traffic based on time schedule For example, user might employ time-based ACLs: To only allow web surfing during a particular time of day Allow access to a particular server only during work hours • Time-based Port Operation Allows the administrator to define days/hours in the week when a port is in ‘up’ state When device clock is not within the time range the port will be shutdown May want to have an Ethernet port in a Guest office only be active during office hours © 2011 Cisco and/or its affiliates. All rights reserved.

Disable port LEDs • The device LEDs (Link, Speed, Po. E) are power consumers • In order to minimize power consumption thereby saving on Operational costs, admin might want to disable port LEDs • This feature allows user to control the LEDs: - Disable the port LEDs when they are not required - Enable the port LEDs if needed for debugging, connecting additional devices etc • The System LED is not impacted © 2011 Cisco and/or its affiliates. All rights reserved.

Multicast TV VLAN • Maximizes network efficiency in the presence of multicast • Reduces duplication of multicast traffic across multiple VLANs in Layer 2 networks by centralizing the distribution of multicast traffic in a single video VLAN • Endpoints live in their isolated VLAN segments while listening for multicast traffic in this VLAN • Similar to MVR (Multicast VLAN Registration) © 2011 Cisco and/or its affiliates. All rights reserved.

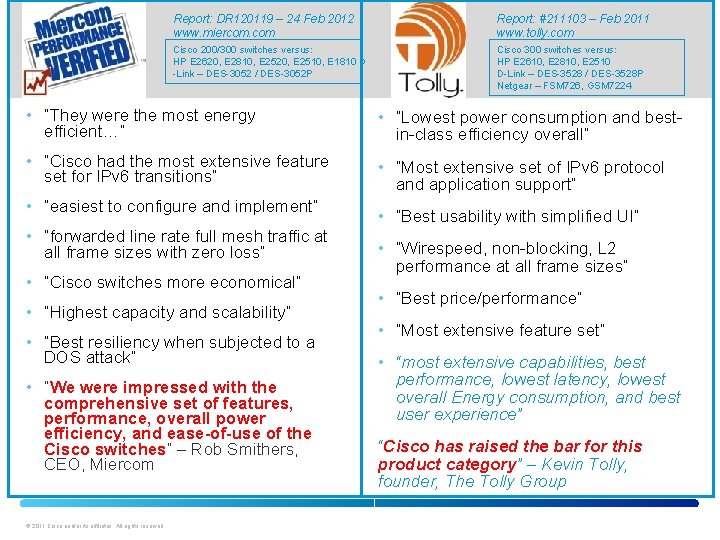
Report: DR 120119 – 24 Feb 2012 www. miercom. com Report: #211103 – Feb 2011 www. tolly. com Cisco 200/300 switches versus: HP E 2620, E 2810, E 2520, E 2510, E 1810 D -Link – DES-3052 / DES-3052 P Cisco 300 switches versus: HP E 2610, E 2810, E 2510 D-Link – DES-3528 / DES-3528 P Netgear – FSM 726, GSM 7224 • “They were the most energy efficient…” • “Cisco had the most extensive feature set for IPv 6 transitions” • “easiest to configure and implement” • “forwarded line rate full mesh traffic at all frame sizes with zero loss” • “Cisco switches more economical” • “Highest capacity and scalability” • “Best resiliency when subjected to a DOS attack” • “We were impressed with the comprehensive set of features, performance, overall power efficiency, and ease-of-use of the Cisco switches” – Rob Smithers, CEO, Miercom © 2011 Cisco and/or its affiliates. All rights reserved. • “Lowest power consumption and best- in-class efficiency overall” • “Most extensive set of IPv 6 protocol and application support” • “Best usability with simplified UI” • “Wirespeed, non-blocking, L 2 performance at all frame sizes” • “Best price/performance” • “Most extensive feature set” • “most extensive capabilities, best performance, lowest latency, lowest overall Energy consumption, and best user experience” “Cisco has raised the bar for this product category” – Kevin Tolly, founder, The Tolly Group

Cisco SMB Switching The leader in Switching solutions for small to medium businesses • Over 20 million Switching ports shipped in the last year Solid market share = right features, price, & reliability for your business • Purpose-built for SMB: Pricing, functionality, and ease that customers are asking for Easy to install and maintain • Part of a complete data, voice and video networking solution Simplified integration for data, voice and video communications needs • Backed by Cisco Comprehensive quality and integration testing works as you expect it to work Superior support better tools, documentation and technical support for Cisco class support © 2011 Cisco and/or its affiliates. All rights reserved.

Resources and URLs • Cisco® 300 Series Switches www. cisco. com/go/300 switches • Partner Central Small Business Switching www. cisco. com/go/smbpartner/switching • Cisco Small Business Support Community https: //www. myciscocommunity. com/community/smallbizsupport • Cisco 300 Series Switches Warranty http: //www. Cisco. com/go/warranty • Cisco Small Business Service www. cisco. com/go/smbservices © 2011 Cisco and/or its affiliates. All rights reserved.

Thank you. © 2011 Cisco and/or its affiliates. All rights reserved.