SP 24 S 045 Secure Share Point Development


















![[Dll. Import("advapi 32. dll")] public static extern uint Event. Activity. Id. Control(uint control. Code, [Dll. Import("advapi 32. dll")] public static extern uint Event. Activity. Id. Control(uint control. Code,](https://slidetodoc.com/presentation_image_h/819bc0628488233cb343680904dcb944/image-40.jpg)









- Slides: 60

#SP 24 S 045 Secure Share. Point Development Eli Robillard Share. Point Server MVP Canada, EDT (GMT -5: 00) April 16 th /17 th, 2014

#SP 24 S 045 Join the conversation! #SP 24 S 045 @erobillard

#SP 24 S 045 Eli Robillard MNP LLP Senior Manager, Share. Point Consulting E-mail Eli. Robillard@MNP. ca Twitter @erobillard Blog weblogs. asp. net/erobillard Eli is a ten-time Microsoft MVP (2 x ASP. NET, 8 x Share. Point Server) and Senior Manager of MNP’s Share. Point Consulting Practice. As a thought leader and community builder, Eli co-founded the ASPInsiders, launched the Toronto Share. Point User Group in 2005, launched the first free Saturday event in 2007, co-authored Professional Share. Point 2007 Development and served as technical editor of Professional Share. Point 2010 Development (Wrox Press). For over 65 years, MNP LLP has forged strong relationships with businesses across Canada through its consulting, advisory, and accounting practices.

#SP 24 S 045 Security at development time is rapidly becoming “conventional wisdom” Forrester Research – “…those practicing SDL specifically reported visibly better ROI results than the overall population. ” Aberdeen Group – “…realized a very strong 4. 0 -times return on their annual investments” “…higher than that of both the find and fix and defend and defer approaches. ” Ponemon Institute – “…a decrease in revenue that results from both the loss of customer trust and loyalty and the inability to deliver services and products. ” Roadmap to Secure Energy Delivery Systems – “…Vendors should employ best product development practices, such as the security development lifecycle (SDL) created by Microsoft in 2002. ”


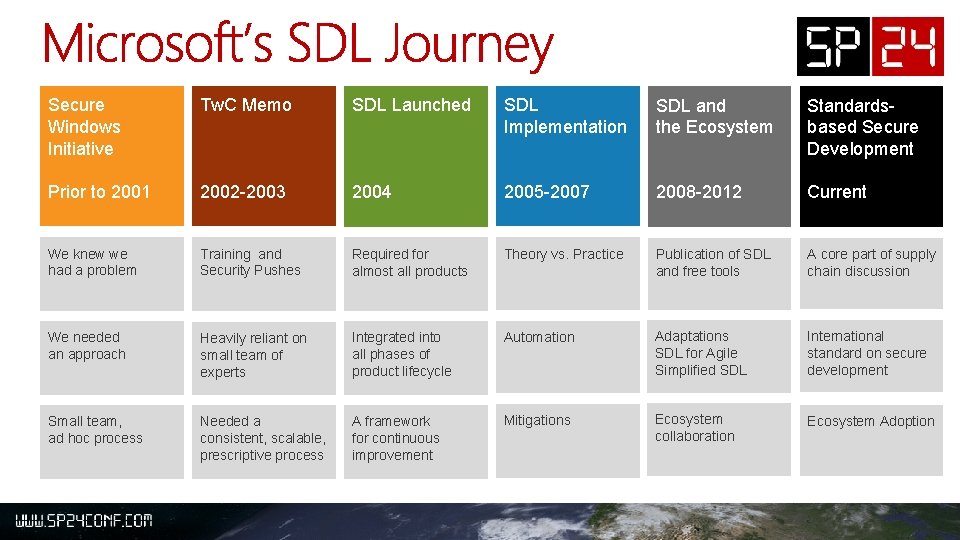
Secure Windows Initiative Tw. C Memo SDL Launched SDL Implementation SDL and the Ecosystem Standardsbased Secure Development Prior to 2001 2002 -2003 2004 2005 -2007 2008 -2012 Current We knew we had a problem Training and Security Pushes Required for almost all products Theory vs. Practice Publication of SDL and free tools A core part of supply chain discussion We needed an approach Heavily reliant on small team of experts Integrated into all phases of product lifecycle Automation Adaptations SDL for Agile Simplified SDL International standard on secure development Small team, ad hoc process Needed a consistent, scalable, prescriptive process A framework for continuous improvement Mitigations Ecosystem collaboration Ecosystem Adoption

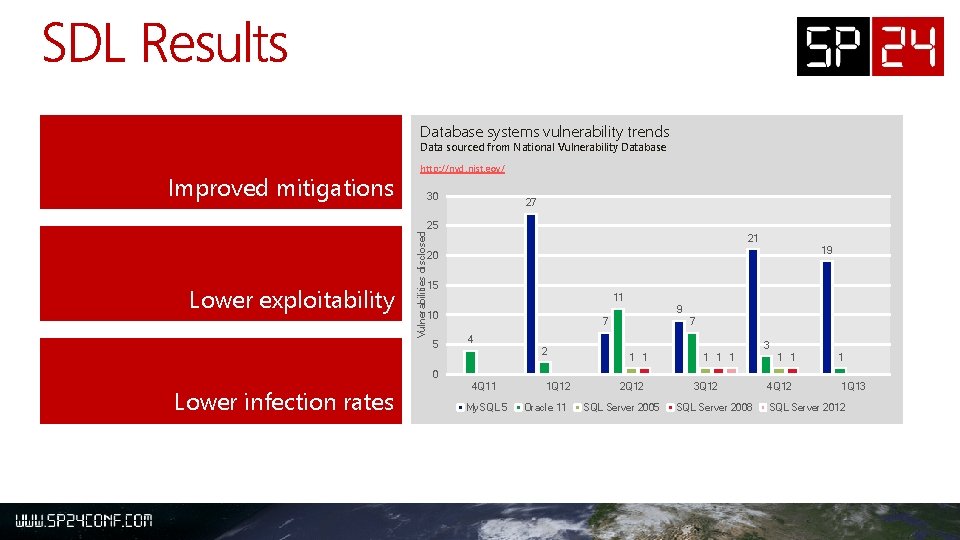
Database systems vulnerability trends Data sourced from National Vulnerability Database Lower exploitability 30 Vulnerabilities disclosed Improved mitigations http: //nvd. nist. gov/ 27 25 21 19 20 15 11 9 10 5 7 7 4 2 3 1 1 1 1 0 Lower infection rates 4 Q 11 My. SQL 5 1 Q 12 Oracle 11 2 Q 12 SQL Server 2005 3 Q 12 SQL Server 2008 4 Q 12 1 Q 13 SQL Server 2012

#SP 24 S 045 Clear Concise Actionable

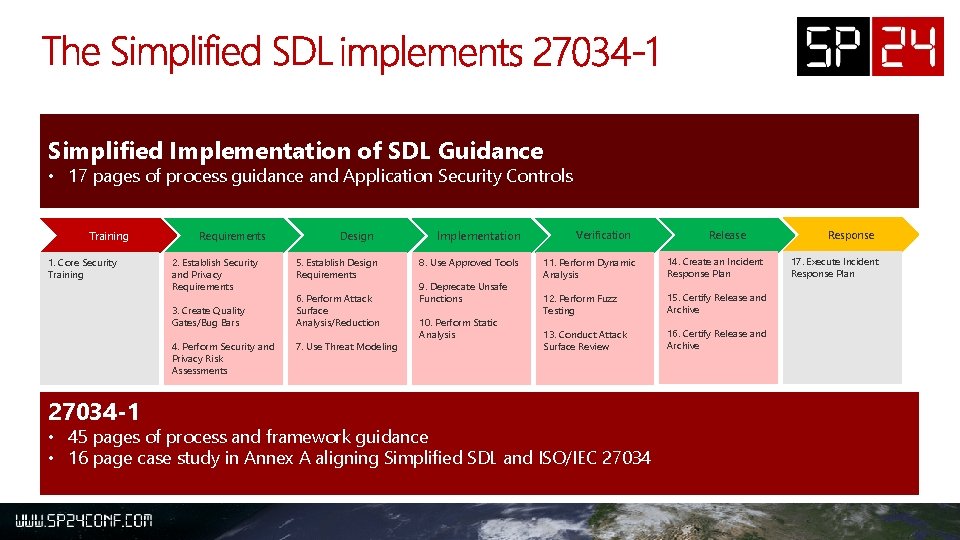
Simplified Implementation of SDL Guidance • 17 pages of process guidance and Application Security Controls Training 1. Core Security Training Requirements 2. Establish Security and Privacy Requirements 3. Create Quality Gates/Bug Bars 4. Perform Security and Privacy Risk Assessments 27034 -1 Design 5. Establish Design Requirements 6. Perform Attack Surface Analysis/Reduction 7. Use Threat Modeling Implementation 8. Use Approved Tools 9. Deprecate Unsafe Functions 10. Perform Static Analysis Verification Release 11. Perform Dynamic Analysis 14. Create an Incident Response Plan 12. Perform Fuzz Testing 15. Certify Release and Archive 13. Conduct Attack Surface Review 16. Certify Release and Archive • 45 pages of process and framework guidance • 16 page case study in Annex A aligning Simplified SDL and ISO/IEC 27034 Response 17. Execute Incident Response Plan


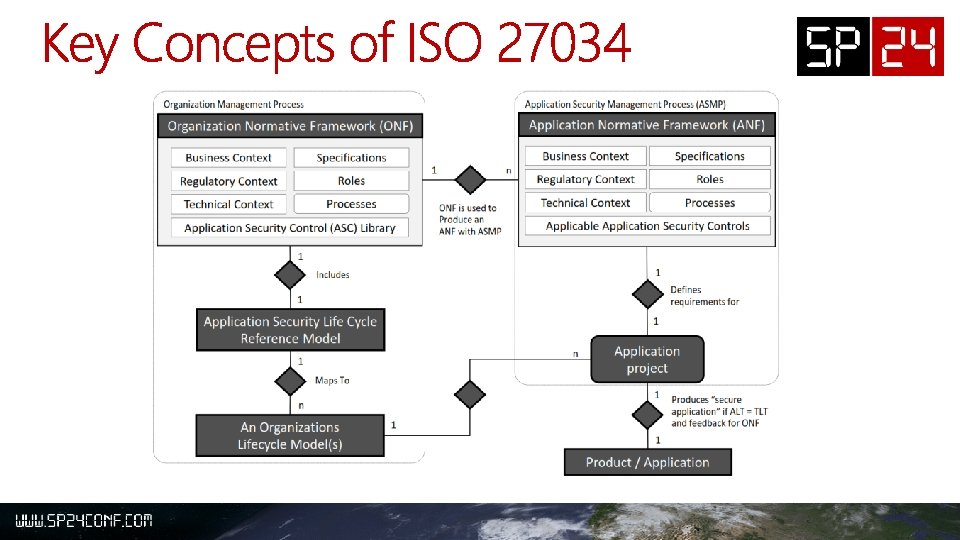
Business Context • Application Security Policies • Standards • Best Practices Business Context • Context of the application in the business Regulatory Context • Professional Standards • Laws • Regulations Regulatory Context • Applicable standards, laws, and regulations Technical Context • Platforms, Technologies • Methodologies Specifications • Functional Requirements • Service Catalogue Technical Context Specifications • Share. Point • ASP. NET and IIS • Windows Server • Integration points • Network Services: • Context of the Application in the Service Catalogue • Security Requirements • Security Roles • Roles • Responsibilities • Qualifications Roles • Governance Model Processes • Processes related to application security Processes • ONF Processes relevant to the application • Peer Review • Automated Testing • Penetration Testing Application Security Controls • Catalogue of Threats and Countermeasures Application Security Controls • Training • Requirements • Design • Implementation • Verification • Release • Checklists and Review Documents

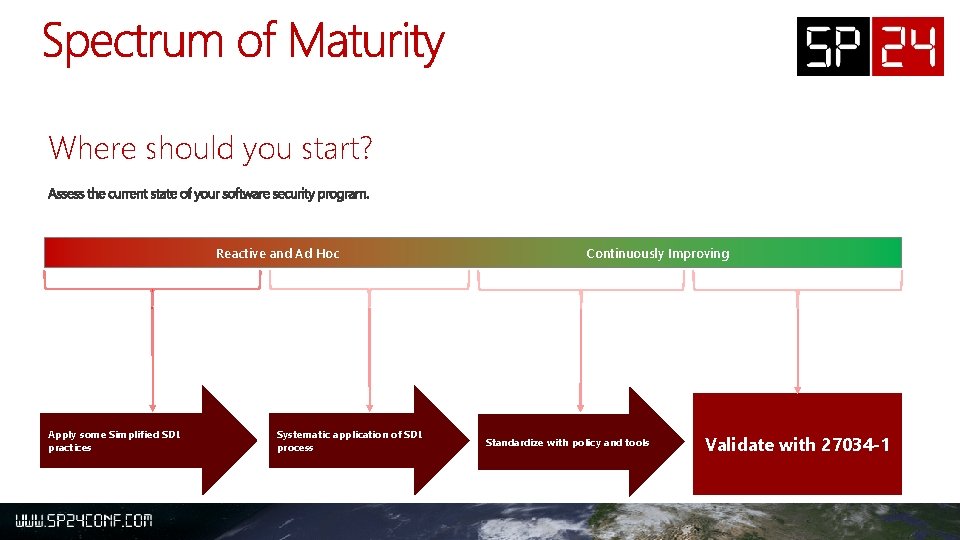
Where should you start? Reactive and Ad Hoc Apply some Simplified SDL practices Systematic application of SDL process Continuously Improving Standardize with policy and tools Validate with 27034 -1

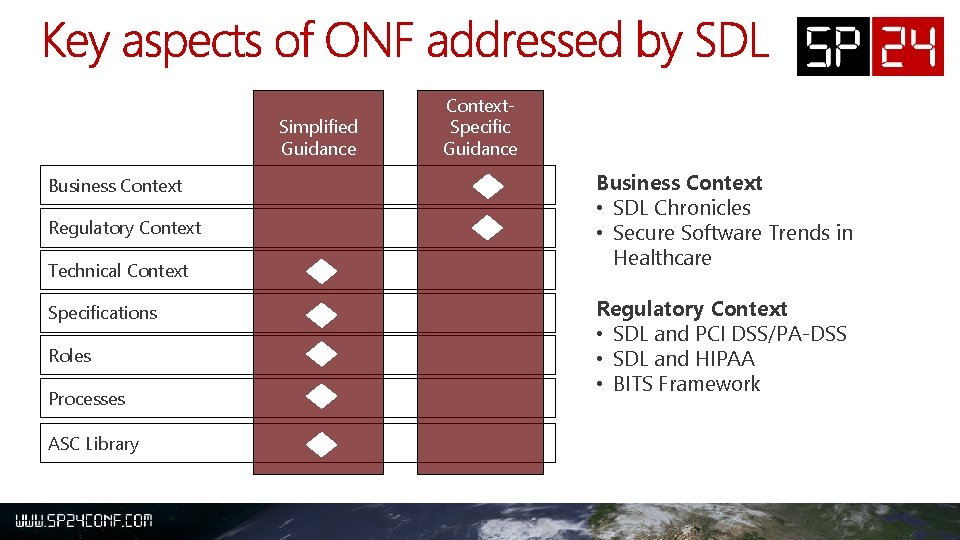
Simplified Guidance Business Context Regulatory Context Technical Context Specifications Roles Processes ASC Library Context. Specific Guidance Business Context • SDL Chronicles • Secure Software Trends in Healthcare Regulatory Context • SDL and PCI DSS/PA-DSS • SDL and HIPAA • BITS Framework

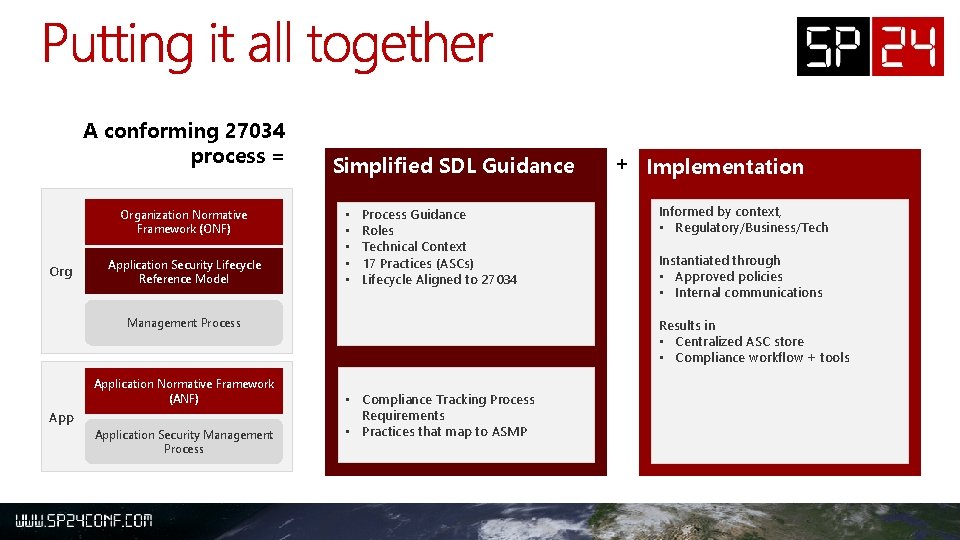
A conforming 27034 process = Organization Normative Framework (ONF) Org Application Security Lifecycle Reference Model Simplified SDL Guidance • • • Process Guidance Roles Technical Context 17 Practices (ASCs) Lifecycle Aligned to 27034 Management Process Application Normative Framework (ANF) Application Security Management Process + Implementation Informed by context, • Regulatory/Business/Tech Instantiated through • Approved policies • Internal communications Results in • Centralized ASC store • Compliance workflow + tools • Compliance Tracking Process Requirements • Practices that map to ASMP

#SP 24 S 045

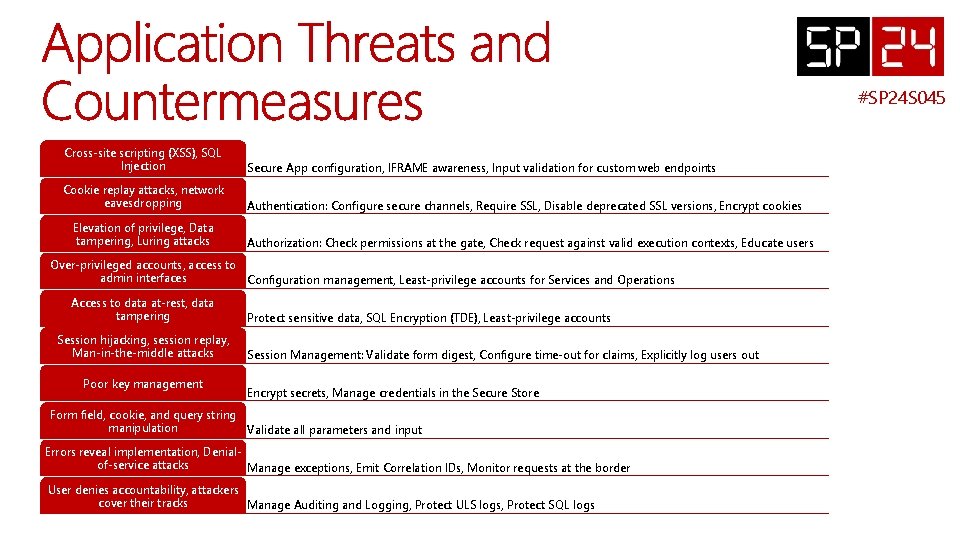
#SP 24 S 045 Cross-site scripting (XSS), SQL Injection Secure App configuration, IFRAME awareness, Input validation for custom web endpoints Cookie replay attacks, network eavesdropping Authentication: Configure secure channels, Require SSL, Disable deprecated SSL versions, Encrypt cookies Elevation of privilege, Data tampering, Luring attacks Authorization: Check permissions at the gate, Check request against valid execution contexts, Educate users Over-privileged accounts, access to admin interfaces Configuration management, Least-privilege accounts for Services and Operations Access to data at-rest, data tampering Session hijacking, session replay, Man-in-the-middle attacks Poor key management Protect sensitive data, SQL Encryption (TDE), Least-privilege accounts Session Management: Validate form digest, Configure time-out for claims, Explicitly log users out Encrypt secrets, Manage credentials in the Secure Store Form field, cookie, and query string manipulation Validate all parameters and input Errors reveal implementation, Denialof-service attacks Manage exceptions, Emit Correlation IDs, Monitor requests at the border User denies accountability, attackers cover their tracks Manage Auditing and Logging, Protect ULS logs, Protect SQL logs

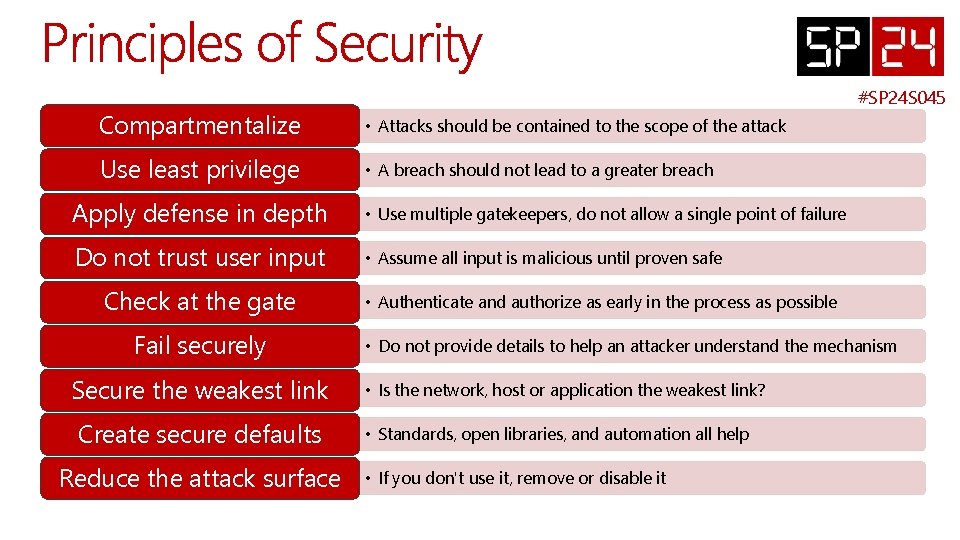
#SP 24 S 045 Compartmentalize • Attacks should be contained to the scope of the attack Use least privilege • A breach should not lead to a greater breach Apply defense in depth • Use multiple gatekeepers, do not allow a single point of failure Do not trust user input • Assume all input is malicious until proven safe Check at the gate Fail securely Secure the weakest link Create secure defaults Reduce the attack surface • Authenticate and authorize as early in the process as possible • Do not provide details to help an attacker understand the mechanism • Is the network, host or application the weakest link? • Standards, open libraries, and automation all help • If you don't use it, remove or disable it


#SP 24 S 045 It is easy to identify Share. Point sites • Promiscuous headers • Identifiable UI Elements Share. Point is susceptible to known ASP. NET exploits • Be aware, some need faster action than others • Java. Script injection is most common • IFRAME click-jacking is possible by default Share. Point is susceptible to known Share. Point exploits • • • Files, pages, cookies and history may be cached on the user's system Static assets in the Share. Point hive do not require authorization Any code – i. e. any web part – in the GAC can be used on any site Any application page in the hive is accessible from every application and site Web and WCF services are visible for all sites

#SP 24 S 045 http: //technet. microsoft. com/en-us/security/bulletin

http: //technet. microsoft. com/enus/security/bulletin/ms 13 -024

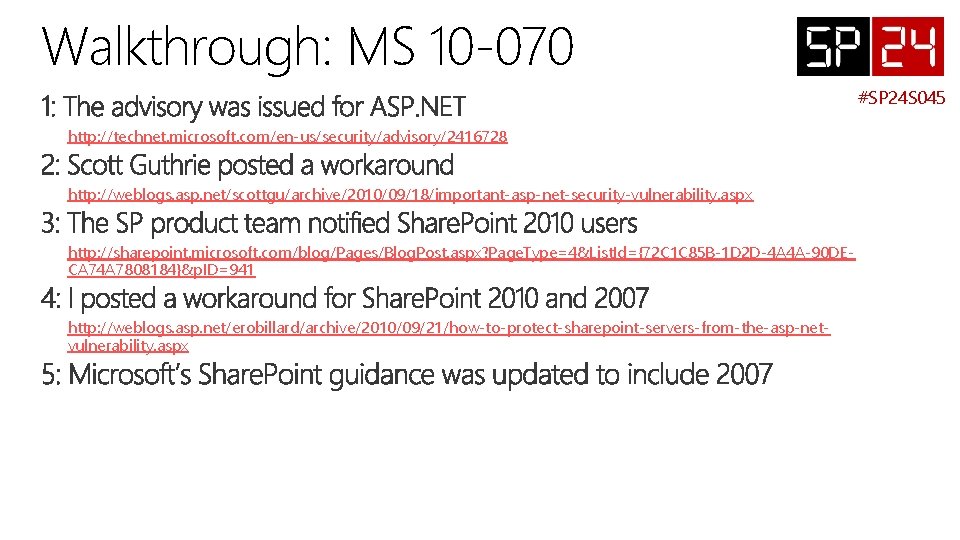
Walkthrough: MS 10 -070 #SP 24 S 045 http: //technet. microsoft. com/en-us/security/advisory/2416728 http: //weblogs. asp. net/scottgu/archive/2010/09/18/important-asp-net-security-vulnerability. aspx http: //sharepoint. microsoft. com/blog/Pages/Blog. Post. aspx? Page. Type=4&List. Id={72 C 1 C 85 B-1 D 2 D-4 A 4 A-90 DECA 74 A 7808184}&p. ID=941 http: //weblogs. asp. net/erobillard/archive/2010/09/21/how-to-protect-sharepoint-servers-from-the-asp-netvulnerability. aspx

#SP 24 S 045

#SP 24 S 045

#SP 24 S 045

#SP 24 S 045

#SP 24 S 045

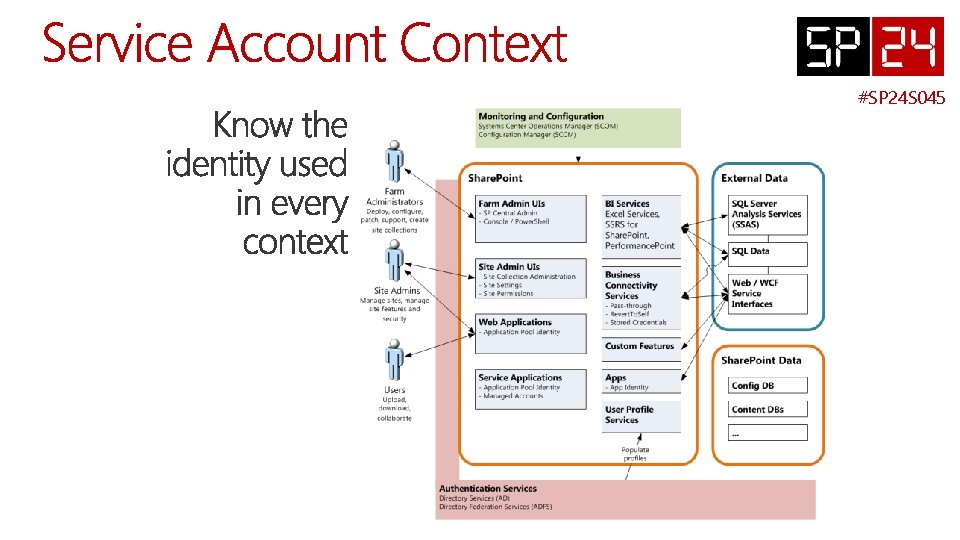
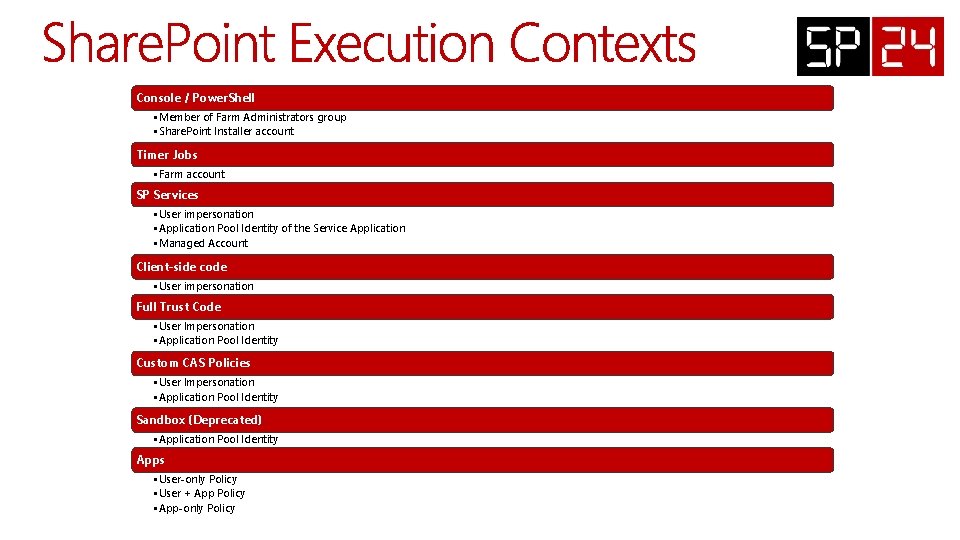
Console / Power. Shell • Member of Farm Administrators group • Share. Point Installer account Timer Jobs • Farm account SP Services • User impersonation • Application Pool Identity of the Service Application • Managed Account Client-side code • User impersonation Full Trust Code • User Impersonation • Application Pool Identity Custom CAS Policies • User Impersonation • Application Pool Identity Sandbox (Deprecated) • Application Pool Identity Apps • User-only Policy • User + App Policy • App-only Policy



Keeping Share. Point Secure


SPWeb web = site. Open. Web(); // do stuff with web my. Web. Dispose(); using (SPWeb web = site. Open. Web()) { // do stuff with web }

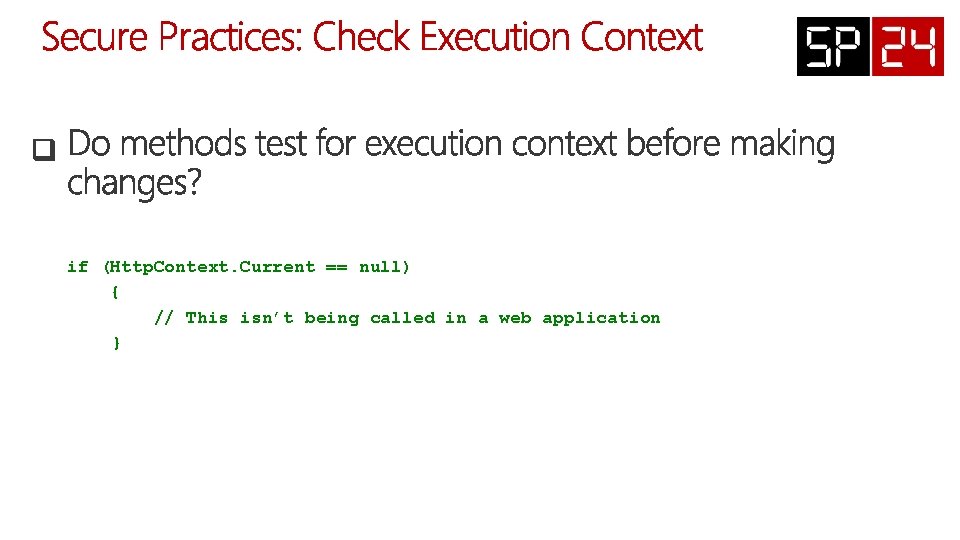
if (Http. Context. Current == null) { // This isn’t being called in a web application }

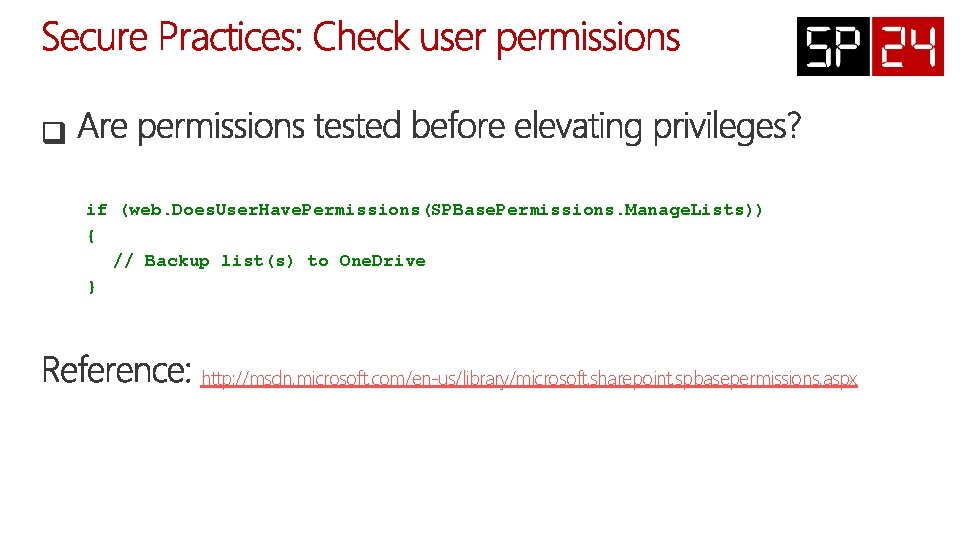
if (web. Does. User. Have. Permissions(SPBase. Permissions. Manage. Lists)) { // Backup list(s) to One. Drive } http: //msdn. microsoft. com/en-us/library/microsoft. sharepoint. spbasepermissions. aspx

/// Anti. Xss. Html. Encode(my. String) Anti. Xss. URLEncode(my. String)

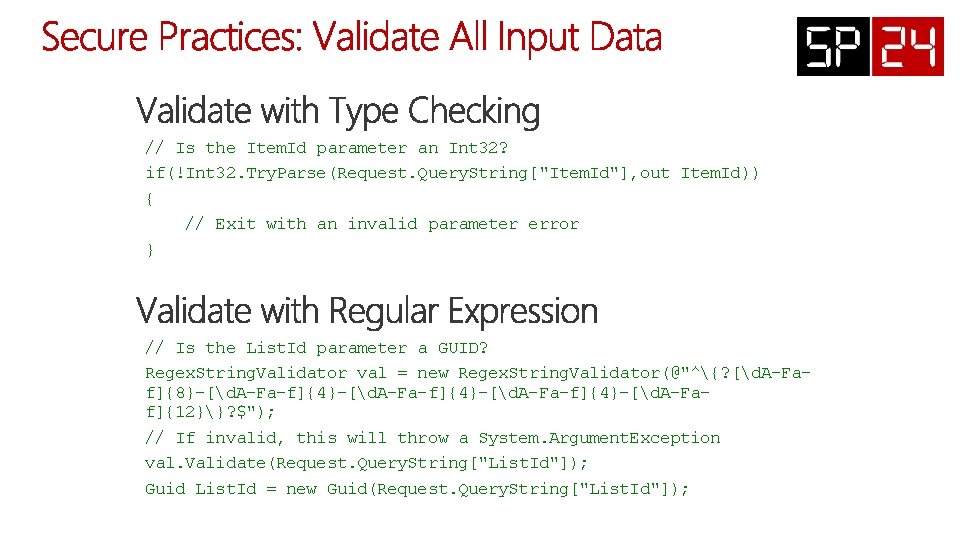
// Is the Item. Id parameter an Int 32? if(!Int 32. Try. Parse(Request. Query. String["Item. Id"], out Item. Id)) { // Exit with an invalid parameter error } // Is the List. Id parameter a GUID? Regex. String. Validator val = new Regex. String. Validator(@"^{? [d. A-Faf]{8}-[d. A-Fa-f]{4}-[d. A-Faf]{12}}? $"); // If invalid, this will throw a System. Argument. Exception val. Validate(Request. Query. String["List. Id"]); Guid List. Id = new Guid(Request. Query. String["List. Id"]);

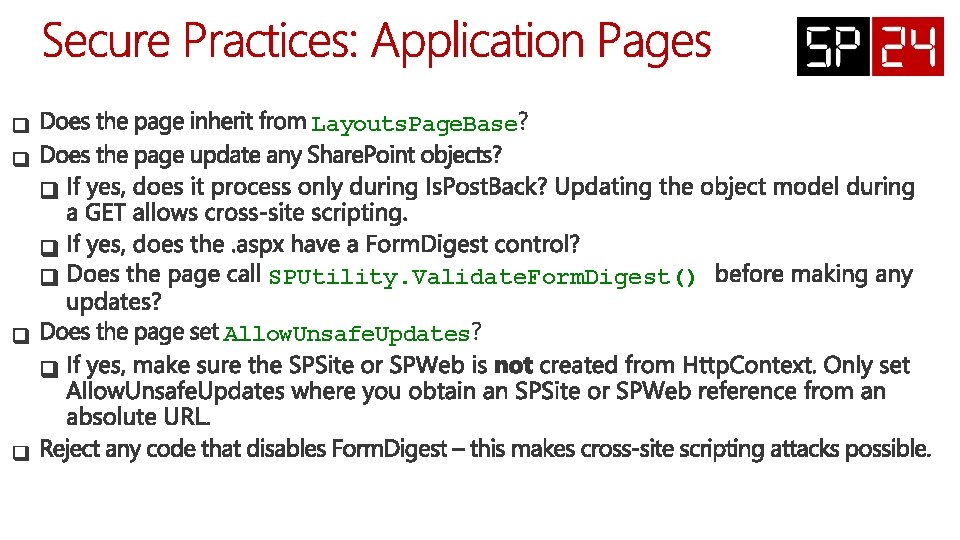
Layouts. Page. Base SPUtility. Validate. Form. Digest() Allow. Unsafe. Updates

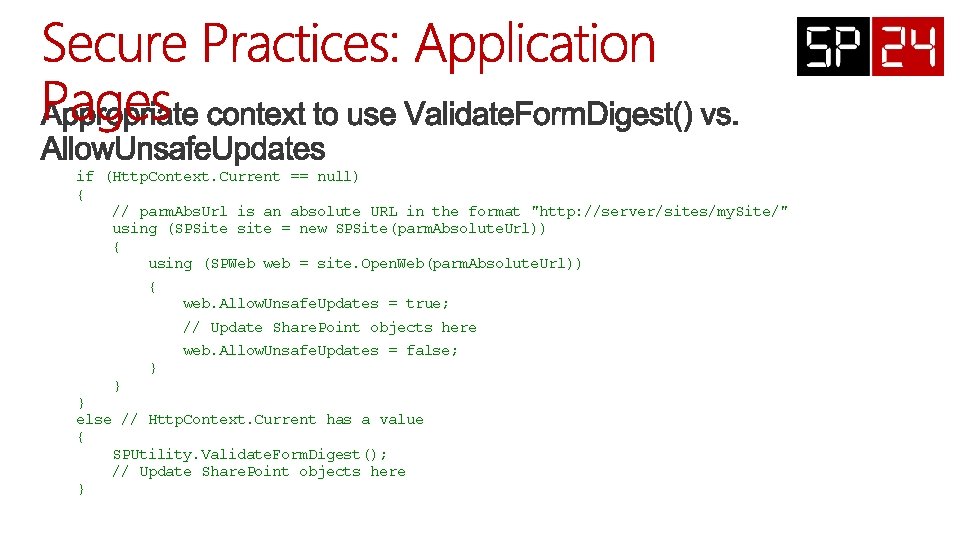
if (Http. Context. Current == null) { // parm. Abs. Url is an absolute URL in the format "http: //server/sites/my. Site/" using (SPSite site = new SPSite(parm. Absolute. Url)) { using (SPWeb web = site. Open. Web(parm. Absolute. Url)) { web. Allow. Unsafe. Updates = true; // Update Share. Point objects here web. Allow. Unsafe. Updates = false; } } } else // Http. Context. Current has a value { SPUtility. Validate. Form. Digest(); // Update Share. Point objects here }
![Dll Importadvapi 32 dll public static extern uint Event Activity Id Controluint control Code [Dll. Import("advapi 32. dll")] public static extern uint Event. Activity. Id. Control(uint control. Code,](https://slidetodoc.com/presentation_image_h/819bc0628488233cb343680904dcb944/image-40.jpg)
[Dll. Import("advapi 32. dll")] public static extern uint Event. Activity. Id. Control(uint control. Code, ref Guid activity. Id); public const uint EVENT_ACTIVITY_CTRL_GET_ID = 1; // … // And then use it in code like this: try { // code block goes here } catch { Guid g = Guid. Empty; Event. Activity. Id. Control(EVENT_ACTIVITY_CTRL_GET_ID, ref g); this. Controls. Add(new Label { Text = string. Format("An error occurred with Correlation ID {0}", g) }); }

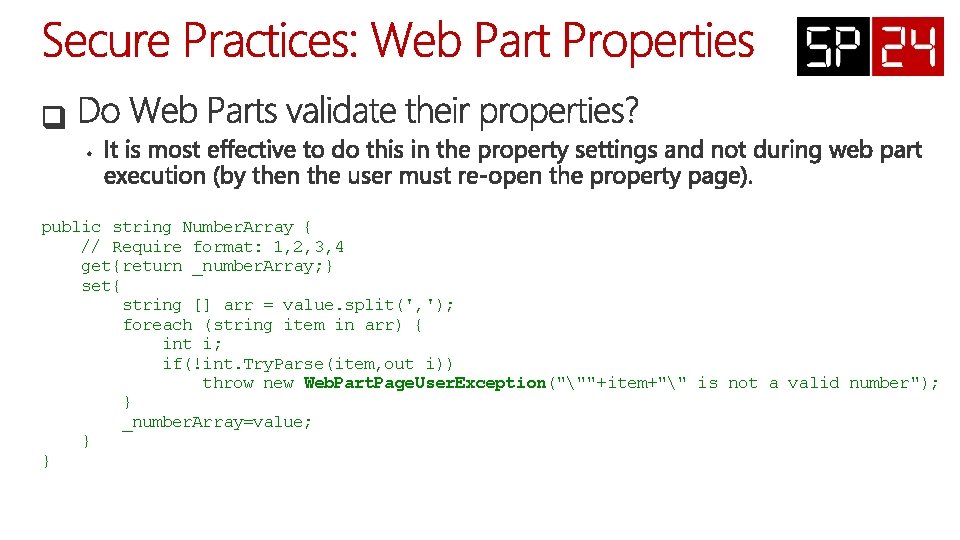
public string Number. Array { // Require format: 1, 2, 3, 4 get{return _number. Array; } set{ string [] arr = value. split(', '); foreach (string item in arr) { int i; if(!int. Try. Parse(item, out i)) throw new Web. Part. Page. User. Exception("""+item+"" is not a valid number"); } _number. Array=value; } }


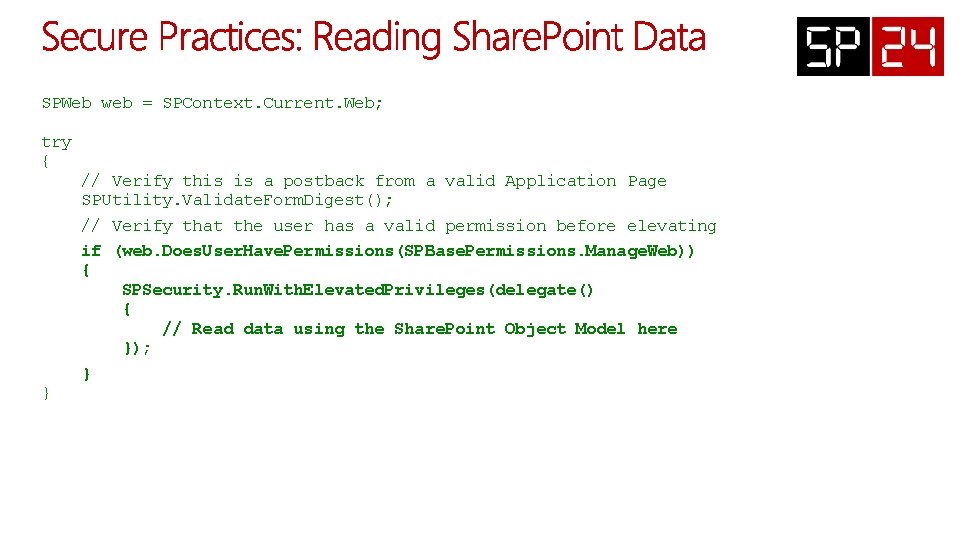
SPWeb web = SPContext. Current. Web; try { } // Verify this is a postback from a valid Application Page SPUtility. Validate. Form. Digest(); // Verify that the user has a valid permission before elevating if (web. Does. User. Have. Permissions(SPBase. Permissions. Manage. Web)) { SPSecurity. Run. With. Elevated. Privileges(delegate() { // Read data using the Share. Point Object Model here }); }

// Update a Share. Point property using (SPSite elevated. Site = Litware. Security. Share. Point. Security. Get. Elevated. Site(web. Site) { // Update data using Share. Point object model here. } The secret sauce: Get. Elevated. Site first tries site. System. Account. User. Token. If that doesn’t work it falls back to RWEP() to Get. System. Token(). It then returns an elevated SPSite using this token. Get the source: http: //www. danlarson. com/elevated-privilege-with-spsite/

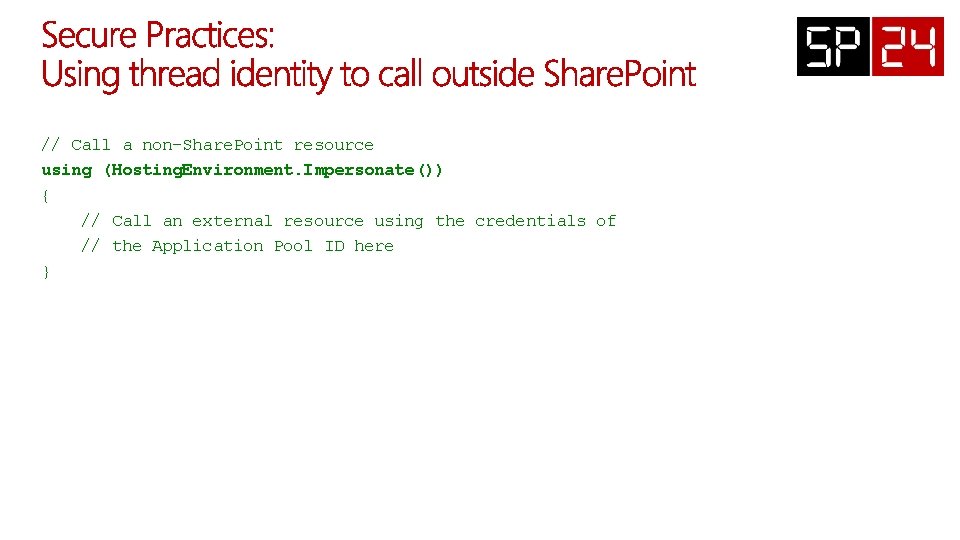
// Call a non-Share. Point resource using (Hosting. Environment. Impersonate()) { // Call an external resource using the credentials of // the Application Pool ID here }



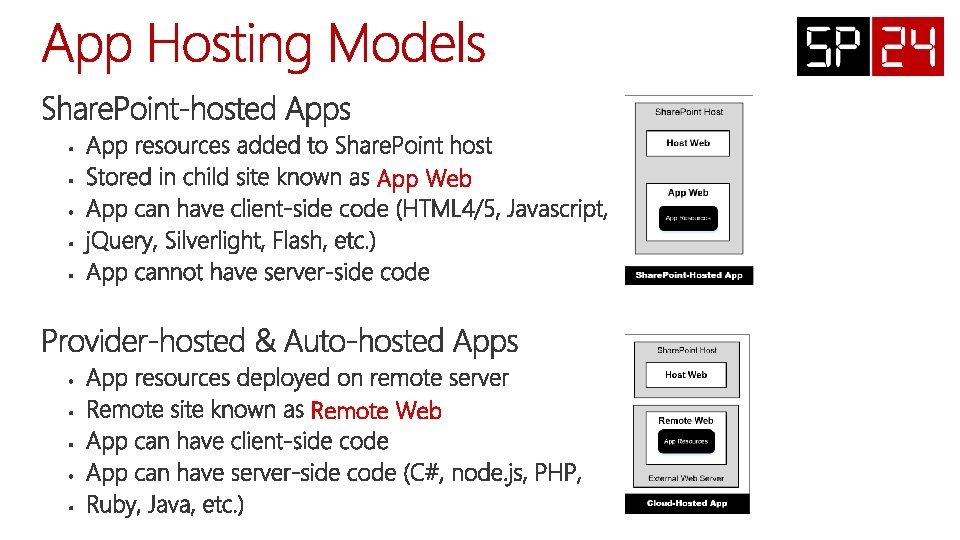
App Web Remote Web

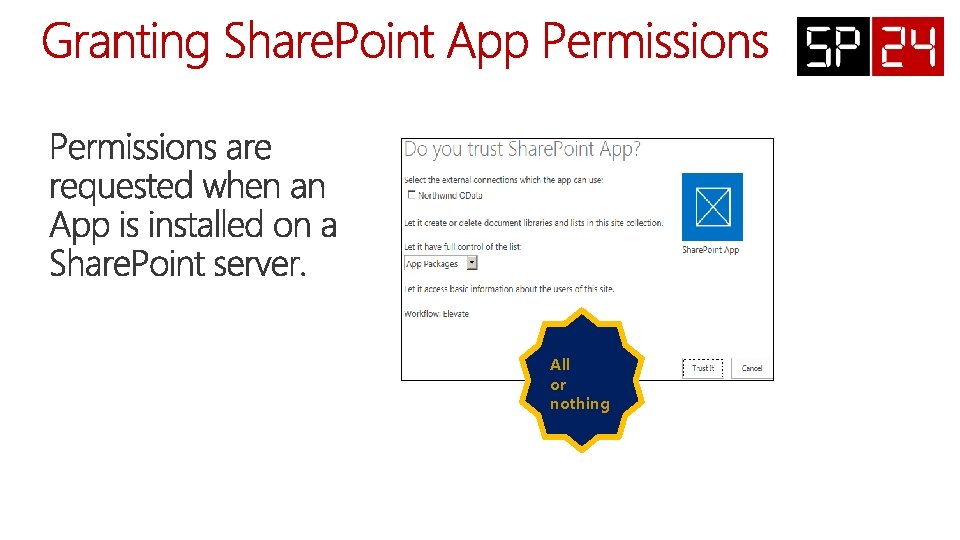
All or nothing

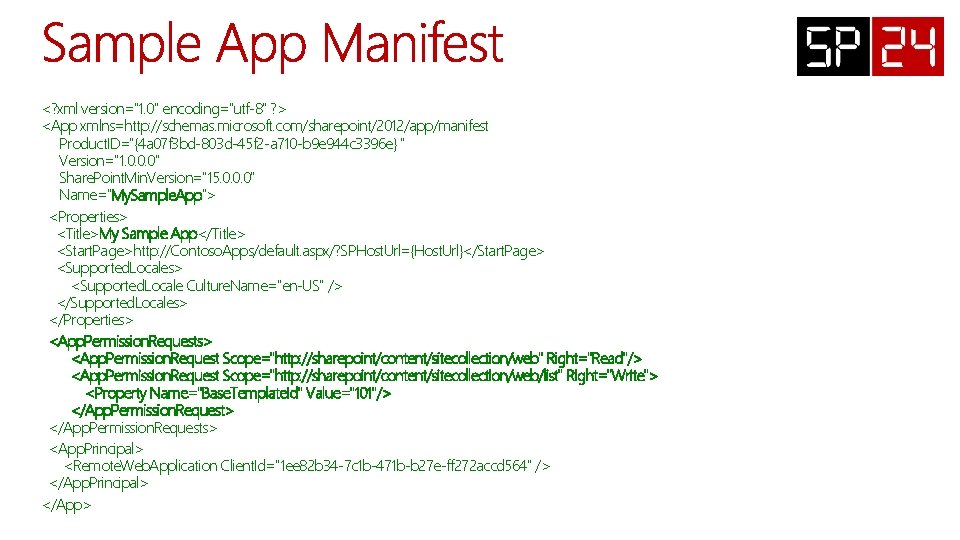
<? xml version="1. 0" encoding="utf-8" ? > <App xmlns=http: //schemas. microsoft. com/sharepoint/2012/app/manifest Product. ID="{4 a 07 f 3 bd-803 d-45 f 2 -a 710 -b 9 e 944 c 3396 e} " Version="1. 0. 0. 0" Share. Point. Min. Version="15. 0. 0. 0" Name="My. Sample. App"> <Properties> <Title>My Sample App</Title> <Start. Page>http: //Contoso. Apps/default. aspx/? SPHost. Url={Host. Url}</Start. Page> <Supported. Locales> <Supported. Locale Culture. Name="en-US" /> </Supported. Locales> </Properties> <App. Permission. Request Scope="http: //sharepoint/content/sitecollection/web" Right="Read"/> <App. Permission. Request Scope="http: //sharepoint/content/sitecollection/web/list" Right="Write"> <Property Name="Base. Template. Id" Value="101"/> </App. Permission. Requests> <App. Principal> <Remote. Web. Application Client. Id="1 ee 82 b 34 -7 c 1 b-471 b-b 27 e-ff 272 accd 564" /> </App. Principal> </App>

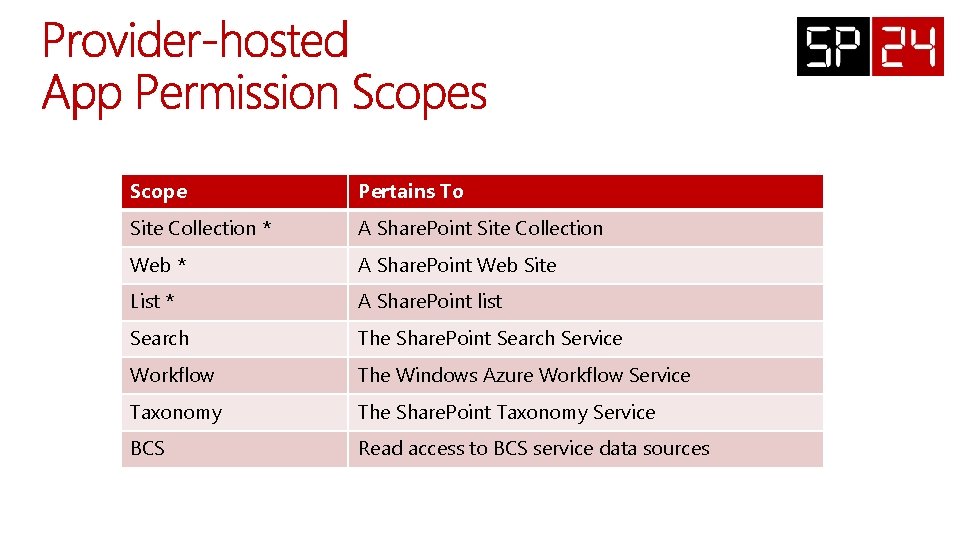
Scope Pertains To Site Collection * A Share. Point Site Collection Web * A Share. Point Web Site List * A Share. Point list Search The Share. Point Search Service Workflow The Windows Azure Workflow Service Taxonomy The Share. Point Taxonomy Service BCS Read access to BCS service data sources

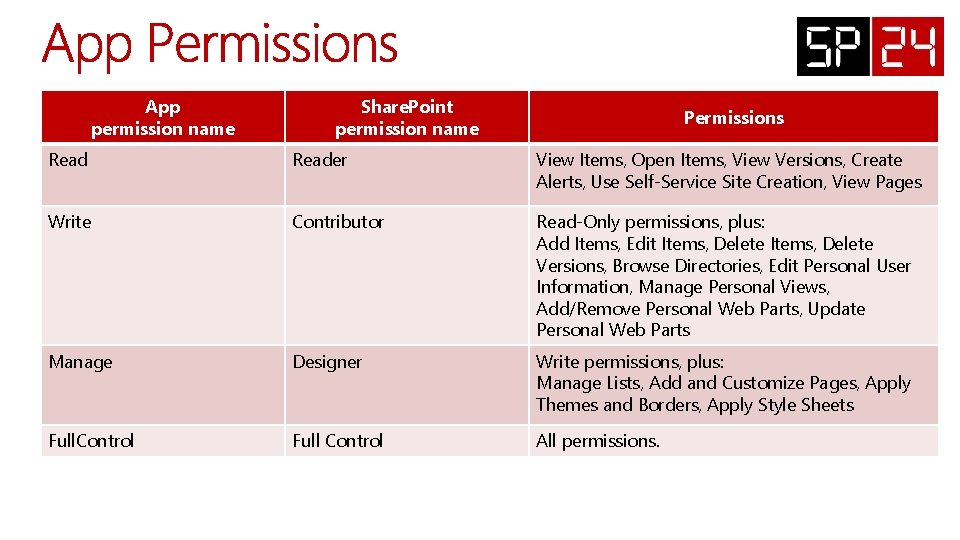
App permission name Share. Point permission name Permissions Reader View Items, Open Items, View Versions, Create Alerts, Use Self-Service Site Creation, View Pages Write Contributor Read-Only permissions, plus: Add Items, Edit Items, Delete Versions, Browse Directories, Edit Personal User Information, Manage Personal Views, Add/Remove Personal Web Parts, Update Personal Web Parts Manage Designer Write permissions, plus: Manage Lists, Add and Customize Pages, Apply Themes and Borders, Apply Style Sheets Full. Control Full Control All permissions.

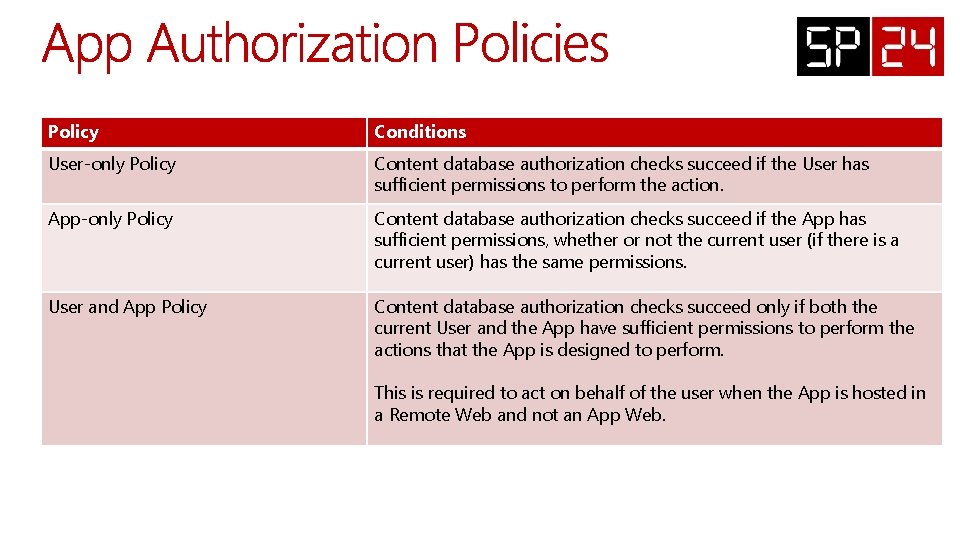
Policy Conditions User-only Policy Content database authorization checks succeed if the User has sufficient permissions to perform the action. App-only Policy Content database authorization checks succeed if the App has sufficient permissions, whether or not the current user (if there is a current user) has the same permissions. User and App Policy Content database authorization checks succeed only if both the current User and the App have sufficient permissions to perform the actions that the App is designed to perform. This is required to act on behalf of the user when the App is hosted in a Remote Web and not an App Web.



#SP 24 S 045

#SP 24 S 045

Eli Robillard MNP LLP Senior Manager, Share. Point Consulting E-mail Eli. Robillard@mnp. ca Twitter @erobillard Blog weblogs. asp. net/erobillard #SP 24 S 045

#SP 24 S 045

#SP 24 S 045