Simulation of Network Attacks on SCADA Systems Rohan



- Slides: 22

Simulation of Network Attacks on SCADA Systems Rohan Chabukswar, Bruno Sinopoli, Gabor Karsai, Annarita Giani, Himanshu Neema, Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010

Outline l Introduction – l C 2 Wind. Tunnel – – l Security of SCADA Systems Testbed Design Testbed Implementaion Simulation Example – – System Model and Attacks Observations and Conclusions "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 2

SCADA Systems l Supervisory Control and Data Acquisition – l Manage and control critical infrastructure Gas utilities, power plants, oil refineries, power utilities, chemical plants, water management, traffic control systems "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 3

SCADA Security l l Potential damage to critical infrastructure and loss of life Components have decades-long lifetimes – l l Legacy systems designed without security as a priority Upgrades may cause unacceptable downtime Real life examples exist – Recent Stuxnet worm targeted SCADA systems monitoring nuclear facilities in Iran "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 4

Outline l Introduction – l C 2 Wind. Tunnel – – l Security of SCADA Systems Testbed Design Testbed Implementaion Simulation Example – – System Model and Attacks Observations and Conclusions "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 5

Testbed Design Goals l l Assess vulnerabilities of current SCADA systems in a realistic setting Allow testing of novel architectural and technological solutions for next generation SCADA Provide an open-source, highly flexible testbed for the industrial control community Should be modular, easily reconfigurable, and accurate "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 6

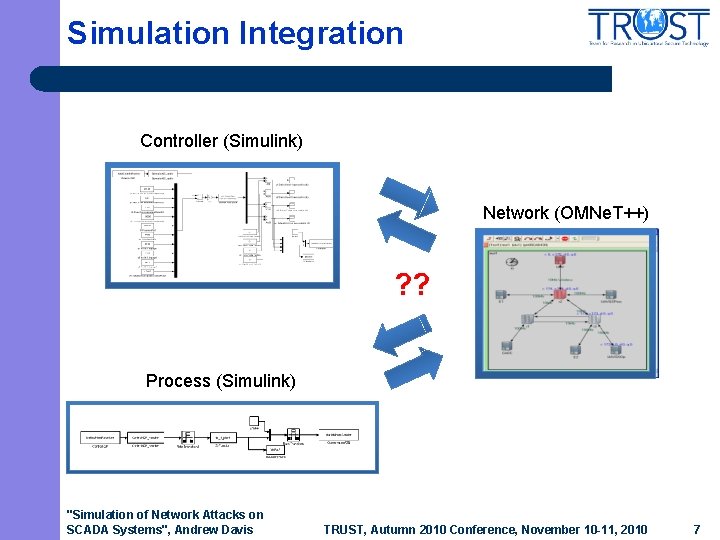
Simulation Integration Controller (Simulink) Network (OMNe. T++) ? ? Process (Simulink) "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 7

Integration Challenges l Modeling network effects at packet level – – – l Allows high fidelity simulation of network effects Requires transferring time-stamped data among simulations with precise time synchronization Requires discrete event model of network Different simulation time models – – – Network uses discrete event simulator Control and process use continuous time simulators Consistent global time must be maintained to prevent breach of causality "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 8

High Level Architecture l Handles time-stamped data transfer – – l Defines a global object model Uses publish and subscribe architecture to transmit time-stamped data Handles time management among diverse time models – – Directs progression of each simulation’s local time No simulation can receive events in its past "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 9

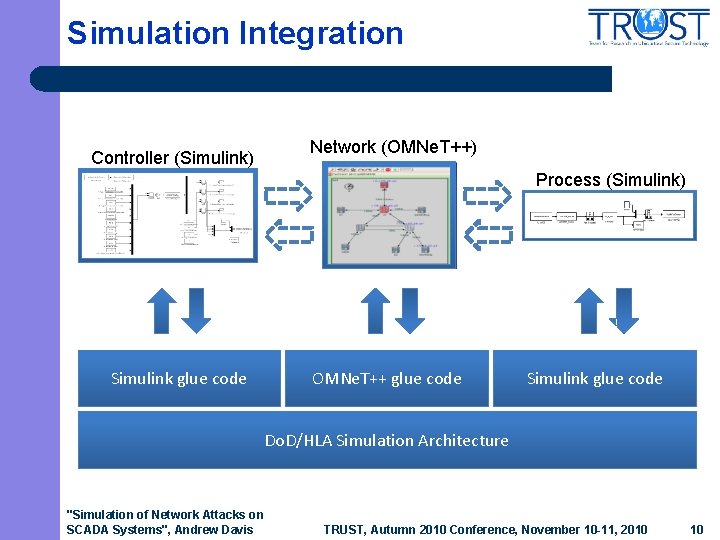
Simulation Integration Controller (Simulink) Network (OMNe. T++) Process (Simulink) Simulink glue code OMNe. T++ glue code Simulink glue code Do. D/HLA Simulation Architecture "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 10

Integration Code Generation l Integration of federates modeled with GME, a general purpose graphical modeling tool – – – l Federates and object model Publish and subscribe relationships Timing parameters C 2 Wind. Tunnel includes code generators to facilitate integration of federates – – – HLA FED file Simulation engine to HLA glue code Simplified interaction publish & subscribe "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 11

Recent Work l Extended network integration – – l Endpoint nodes specified in integration model allowing transparent data flow from HLA to network Code generated for data-type based routing of information through the network Integrates with the INET framework to allow network modeling without concern for federation level details Restructured HLA-to-network interface to support newest version of the po. RTIco RTI New Windows installer simplifies setup – Available on project wiki "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 12

Outline l Introduction – l C 2 Wind. Tunnel – – l Security of SCADA Systems Testbed Design Testbed Implementaion Simulation Example – – System Model and Attacks Observations and Conclusions "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 13

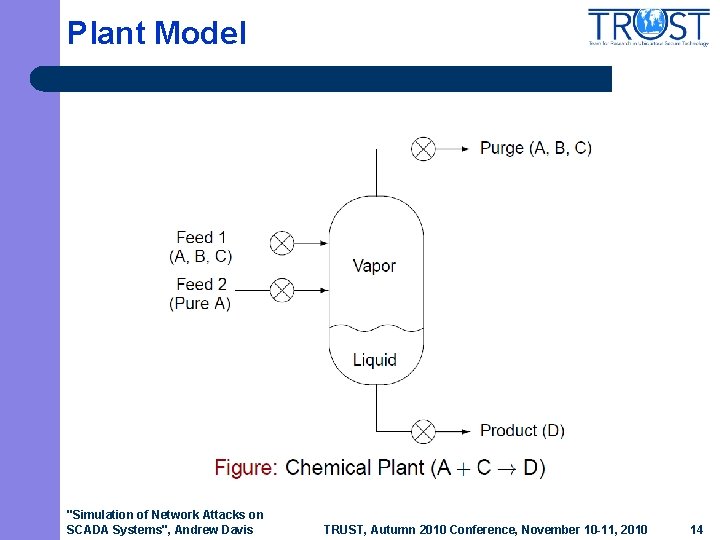
Plant Model "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 14

Control Problem l Objectives – – l Maintain production rate by controlling valves Minimize operating cost (function of purge loss of A and C) Restrictions – – Operating pressure below shutdown limit of 3 MPa Flows have a maximum at their saturation points "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 15

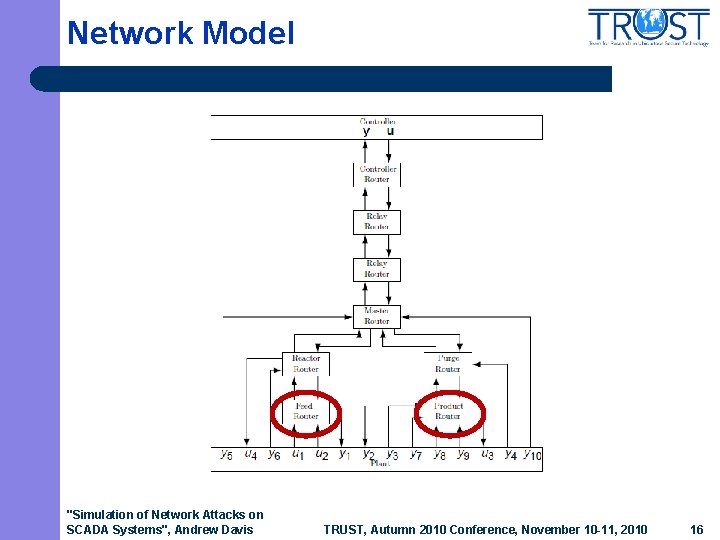
Network Model "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 16

Attacks l l DDOS attacks are simulated on system, targeting various routers Saturated with external communication requests from large number of zombie nodes Process nodes connecting to attacked routers sustain 100% packet loss for the duration of the attack Controller, feed and product routers are attacked from 30 -second mark to 60 -second mark out of simulation time of 150 seconds "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 17

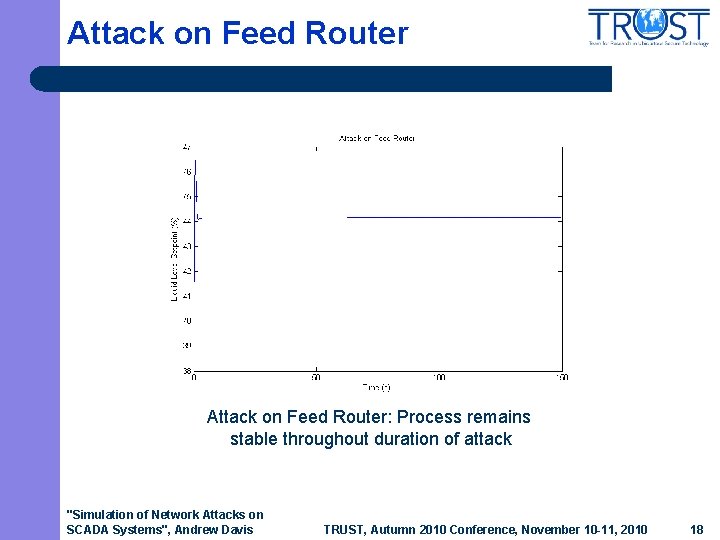
Attack on Feed Router: Process remains stable throughout duration of attack "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 18

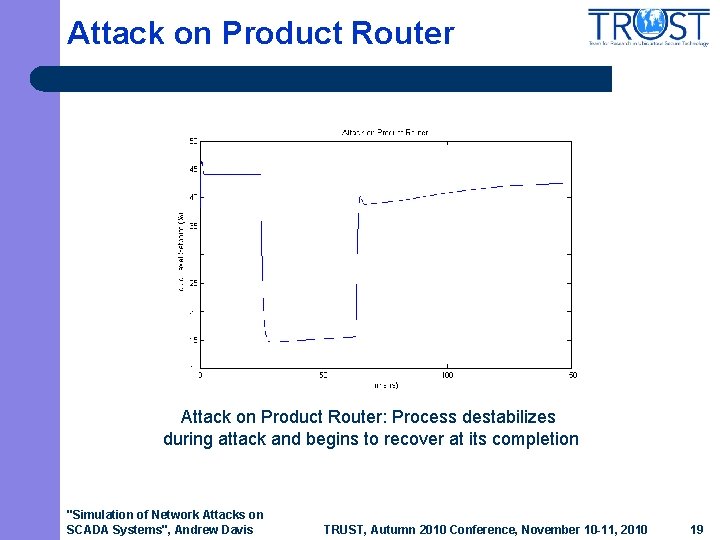
Attack on Product Router: Process destabilizes during attack and begins to recover at its completion "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 19

Conclusions l l l Effects of each individual attack are hard to predict and compare analytically For a complicated system, calculating effects would require intensive analytical computations, could be intractable Simulation is the best way to estimate effects, to implement and compare network configurations and redundancies "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 20

Future Work l l l Simulation can be used to develop and evaluate more robust control algorithms Extend testing to other common network security attacks Investigate distinguishing process faults from network attacks "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 21

Acknowledgements l This work was supported in part by TRUST (Team for Research in Ubiquitous Secure Technology), which receives support from the National Science Foundation (NSF award number CCF-0424422) and the following organizations: AFOSR (#FA 9550 -06 -1 -0244), BT, Cisco, Do. Co. Mo USA Labs, EADS, ESCHER, HP, IBM, i. CAST, Intel, Microsoft, ORNL, Pirelli, Qualcomm, Sun, Symantec, TCS, Telecom Italia and United Technologies. "Simulation of Network Attacks on SCADA Systems", Andrew Davis TRUST, Autumn 2010 Conference, November 10 -11, 2010 22